69f59388fe79c1bc4007d50a83e890e6.ppt
- Количество слайдов: 48
 Virtual Machines Supporting Changing Technology and New Applications Computing Frontiers May 2005 J. E. Smith VMs (c) 2005, J. E. Smith
Virtual Machines Supporting Changing Technology and New Applications Computing Frontiers May 2005 J. E. Smith VMs (c) 2005, J. E. Smith
 Introduction Why are virtual machines interesting? They involve computer architecture in a pure sense They allow transcending of interfaces (which often seem to be an obstacle to innovation) They enable innovation in flexible, adaptive software & hardware, security, network computing (and others) Virtualization technologies will be a key part of most future computer systems VMs (c) 2005, J. E. Smith 2
Introduction Why are virtual machines interesting? They involve computer architecture in a pure sense They allow transcending of interfaces (which often seem to be an obstacle to innovation) They enable innovation in flexible, adaptive software & hardware, security, network computing (and others) Virtualization technologies will be a key part of most future computer systems VMs (c) 2005, J. E. Smith 2
 Outline q q q q Virtualization The Architecture of Virtual Machines Emulation Enhancing Security The Grid Portable Environments Co-Designed VMs (c) 2005, J. E. Smith 3
Outline q q q q Virtualization The Architecture of Virtual Machines Emulation Enhancing Security The Grid Portable Environments Co-Designed VMs (c) 2005, J. E. Smith 3
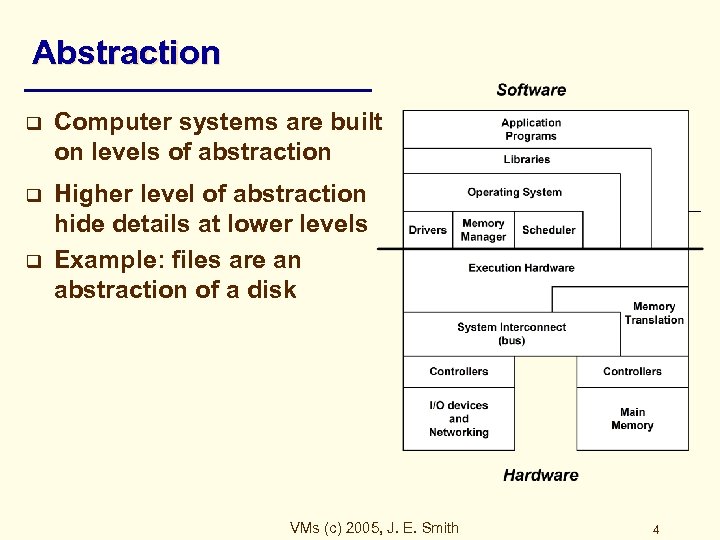 Abstraction q q q Computer systems are built on levels of abstraction Higher level of abstraction hide details at lower levels Example: files are an abstraction of a disk file abstraction VMs (c) 2005, J. E. Smith 4
Abstraction q q q Computer systems are built on levels of abstraction Higher level of abstraction hide details at lower levels Example: files are an abstraction of a disk file abstraction VMs (c) 2005, J. E. Smith 4
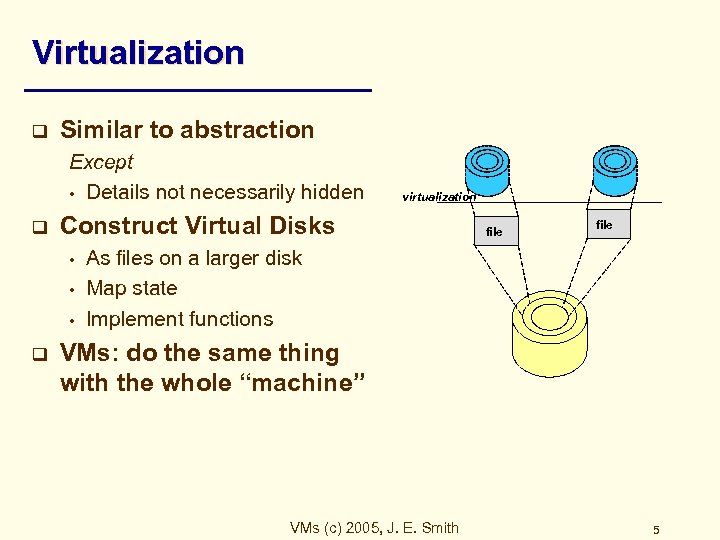 Virtualization q Similar to abstraction Except • Details not necessarily hidden q Construct Virtual Disks • • • q virtualization file As files on a larger disk Map state Implement functions VMs: do the same thing with the whole “machine” VMs (c) 2005, J. E. Smith 5
Virtualization q Similar to abstraction Except • Details not necessarily hidden q Construct Virtual Disks • • • q virtualization file As files on a larger disk Map state Implement functions VMs: do the same thing with the whole “machine” VMs (c) 2005, J. E. Smith 5
 The Family of Virtual Machines There are lots of “virtual machines” Including things not called “virtual machines” IBM EL IA-32 VM/370 Java HP Dynamo VMware products Transmeta Crusoe “The subjects of virtual machines and emulators have been treated as entirely separate. … they have much in common. Not only do the usual implementations have many shared characteristics, but this commonality extends to theoretical concepts on which they are based” -- Efrem G. Wallach, 1973 VMs (c) 2005, J. E. Smith 6
The Family of Virtual Machines There are lots of “virtual machines” Including things not called “virtual machines” IBM EL IA-32 VM/370 Java HP Dynamo VMware products Transmeta Crusoe “The subjects of virtual machines and emulators have been treated as entirely separate. … they have much in common. Not only do the usual implementations have many shared characteristics, but this commonality extends to theoretical concepts on which they are based” -- Efrem G. Wallach, 1973 VMs (c) 2005, J. E. Smith 6
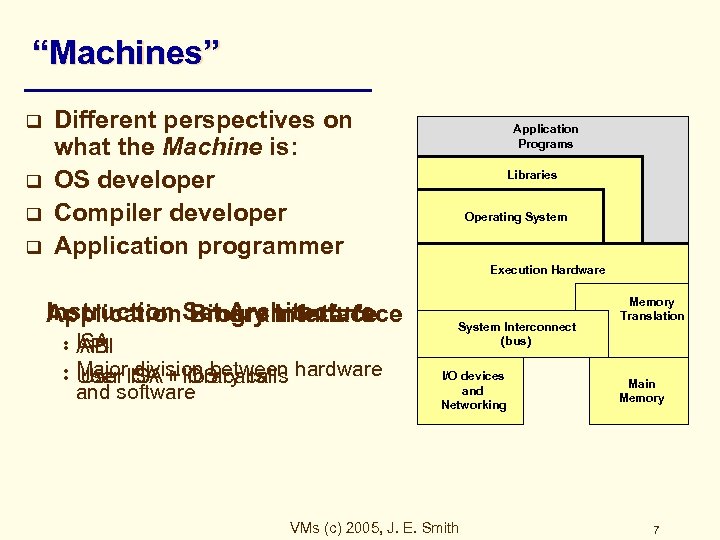 “Machines” q q Different perspectives on what the Machine is: OS developer Compiler developer Application programmer Application Programs Libraries Operating System Execution Hardware Instruction Set Architecture Application Binary Interface Program Interface • • ISA API ABI Major. ISA + library calls hardware User ISA + OS calls User division between and software System Interconnect (bus) I/O devices and Networking VMs (c) 2005, J. E. Smith Memory Translation Main Memory 7
“Machines” q q Different perspectives on what the Machine is: OS developer Compiler developer Application programmer Application Programs Libraries Operating System Execution Hardware Instruction Set Architecture Application Binary Interface Program Interface • • ISA API ABI Major. ISA + library calls hardware User ISA + OS calls User division between and software System Interconnect (bus) I/O devices and Networking VMs (c) 2005, J. E. Smith Memory Translation Main Memory 7
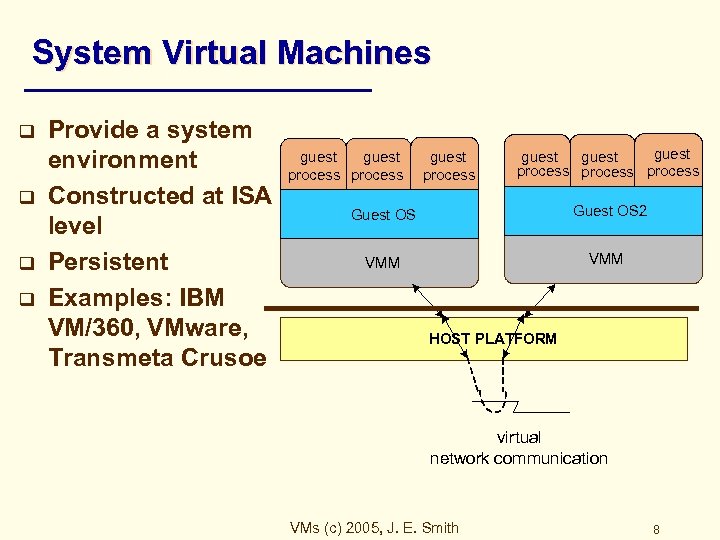 System Virtual Machines q q Provide a system environment Constructed at ISA level Persistent Examples: IBM VM/360, VMware, Transmeta Crusoe guest process guest process Guest OS 2 VMM HOST PLATFORM virtual network communication VMs (c) 2005, J. E. Smith 8
System Virtual Machines q q Provide a system environment Constructed at ISA level Persistent Examples: IBM VM/360, VMware, Transmeta Crusoe guest process guest process Guest OS 2 VMM HOST PLATFORM virtual network communication VMs (c) 2005, J. E. Smith 8
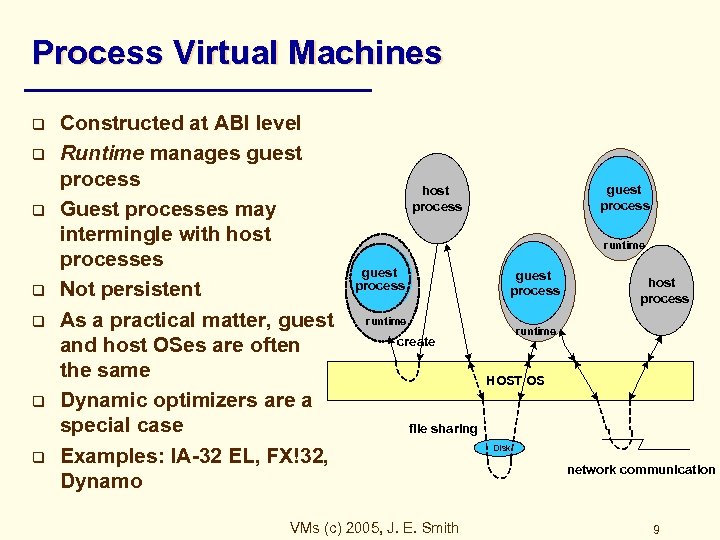 Process Virtual Machines q q q q Constructed at ABI level Runtime manages guest process Guest processes may intermingle with host processes Not persistent As a practical matter, guest and host OSes are often the same Dynamic optimizers are a special case Examples: IA-32 EL, FX!32, Dynamo guest process host process runtime guest process runtime host process runtime create HOST OS file sharing VMs (c) 2005, J. E. Smith Disk network communication 9
Process Virtual Machines q q q q Constructed at ABI level Runtime manages guest process Guest processes may intermingle with host processes Not persistent As a practical matter, guest and host OSes are often the same Dynamic optimizers are a special case Examples: IA-32 EL, FX!32, Dynamo guest process host process runtime guest process runtime host process runtime create HOST OS file sharing VMs (c) 2005, J. E. Smith Disk network communication 9
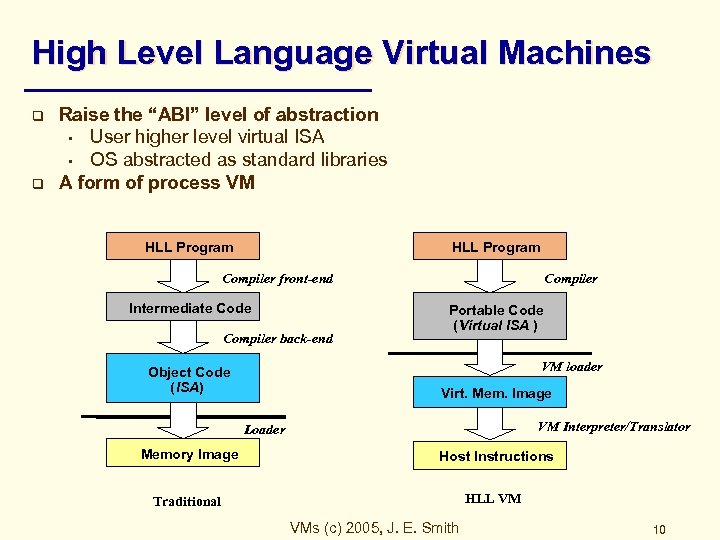 High Level Language Virtual Machines q q Raise the “ABI” level of abstraction • User higher level virtual ISA • OS abstracted as standard libraries A form of process VM HLL Program Compiler front-end Intermediate Code Compiler back-end Compiler Portable Code (Virtual ISA ) VM loader Object Code (ISA) Virt. Mem. Image VM Interpreter/Translator Loader Memory Image Host Instructions Traditional HLL VM VMs (c) 2005, J. E. Smith 10
High Level Language Virtual Machines q q Raise the “ABI” level of abstraction • User higher level virtual ISA • OS abstracted as standard libraries A form of process VM HLL Program Compiler front-end Intermediate Code Compiler back-end Compiler Portable Code (Virtual ISA ) VM loader Object Code (ISA) Virt. Mem. Image VM Interpreter/Translator Loader Memory Image Host Instructions Traditional HLL VM VMs (c) 2005, J. E. Smith 10
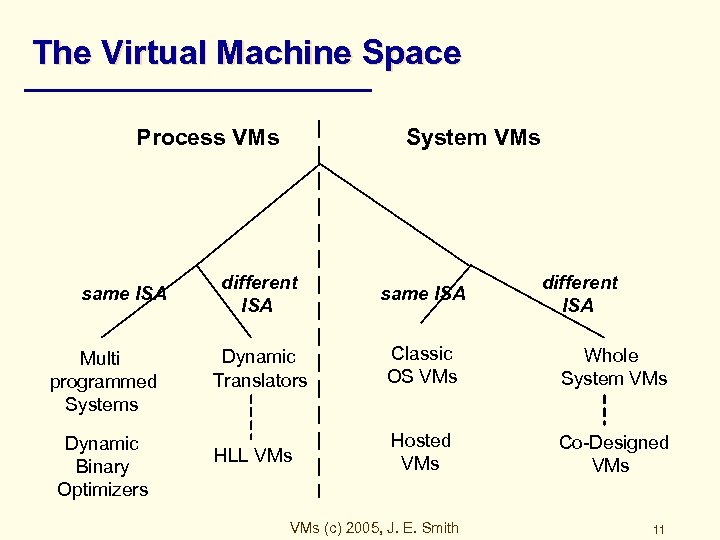 The Virtual Machine Space Process VMs same ISA Multi programmed Systems Dynamic Binary Optimizers System VMs different ISA same ISA Dynamic Translators Classic OS VMs Whole System VMs HLL VMs Hosted VMs Co-Designed VMs (c) 2005, J. E. Smith different ISA 11
The Virtual Machine Space Process VMs same ISA Multi programmed Systems Dynamic Binary Optimizers System VMs different ISA same ISA Dynamic Translators Classic OS VMs Whole System VMs HLL VMs Hosted VMs Co-Designed VMs (c) 2005, J. E. Smith different ISA 11
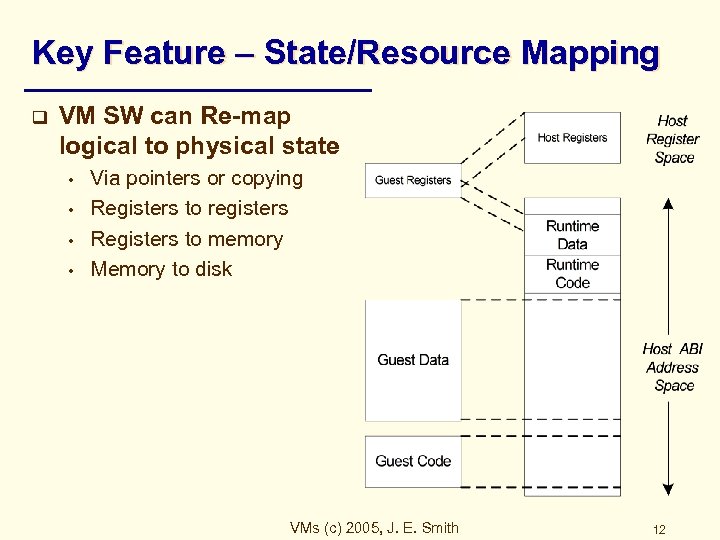 Key Feature – State/Resource Mapping q VM SW can Re-map logical to physical state • • Via pointers or copying Registers to registers Registers to memory Memory to disk VMs (c) 2005, J. E. Smith 12
Key Feature – State/Resource Mapping q VM SW can Re-map logical to physical state • • Via pointers or copying Registers to registers Registers to memory Memory to disk VMs (c) 2005, J. E. Smith 12
 Key Feature – Emulation q Interpretation • q Binary translation and code caching • • • q Software loop decodes and dispatches each instruction Translate blocks of instructions at a time Hold translated blocks in code cache With same-ISA scanning/patching is an alternative Staged Emulation • • Emulation techniques invoked in staged manner Based on performance tradeoffs VMs (c) 2005, J. E. Smith 13
Key Feature – Emulation q Interpretation • q Binary translation and code caching • • • q Software loop decodes and dispatches each instruction Translate blocks of instructions at a time Hold translated blocks in code cache With same-ISA scanning/patching is an alternative Staged Emulation • • Emulation techniques invoked in staged manner Based on performance tradeoffs VMs (c) 2005, J. E. Smith 13
 Code Caches q Contain • • • q Basic blocks Superblocks (one entrance, multiple exits) Optimized Superblocks A base technology for many VMs • • • Dynamic binary translators: Intel IA-32 EL, Compaq FX!32 Dynamic binary optimizers: Dynamo family Co-designed virtual machines: Transmeta, IBM DAISY High performance Java virtual machines System VMs with “inefficiently virtualizable” ISAs “Sandboxing” secure VMs (x 86 Dynamo. RIO) VMs (c) 2005, J. E. Smith 14
Code Caches q Contain • • • q Basic blocks Superblocks (one entrance, multiple exits) Optimized Superblocks A base technology for many VMs • • • Dynamic binary translators: Intel IA-32 EL, Compaq FX!32 Dynamic binary optimizers: Dynamo family Co-designed virtual machines: Transmeta, IBM DAISY High performance Java virtual machines System VMs with “inefficiently virtualizable” ISAs “Sandboxing” secure VMs (x 86 Dynamo. RIO) VMs (c) 2005, J. E. Smith 14
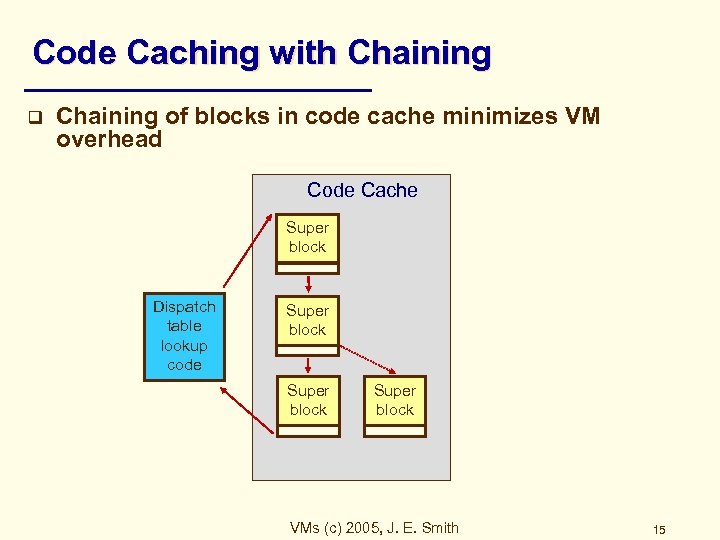 Code Caching with Chaining q Chaining of blocks in code cache minimizes VM overhead Code Cache Super block Dispatch table lookup code Super block VMs (c) 2005, J. E. Smith 15
Code Caching with Chaining q Chaining of blocks in code cache minimizes VM overhead Code Cache Super block Dispatch table lookup code Super block VMs (c) 2005, J. E. Smith 15
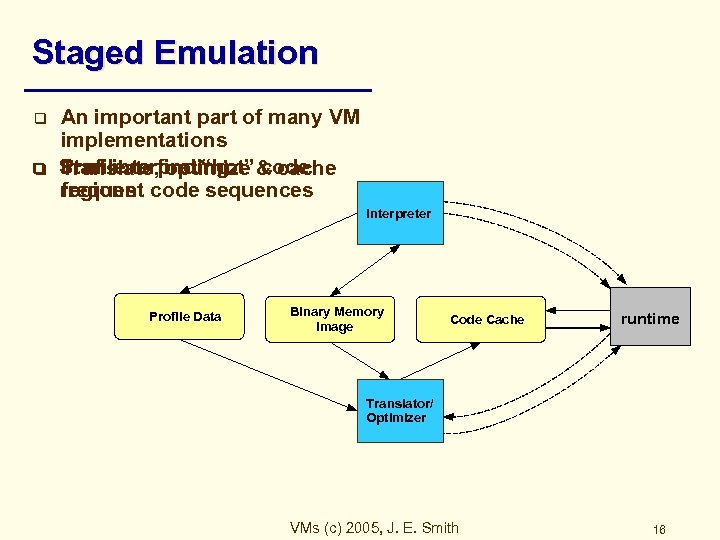 Staged Emulation q q q An important part of many VM implementations Start interpreting & cache Profile to find “hot” code Translate, optimize regions code sequences frequent Interpreter Profile Data Binary Memory Image Code Cache runtime Translator/ Optimizer VMs (c) 2005, J. E. Smith 16
Staged Emulation q q q An important part of many VM implementations Start interpreting & cache Profile to find “hot” code Translate, optimize regions code sequences frequent Interpreter Profile Data Binary Memory Image Code Cache runtime Translator/ Optimizer VMs (c) 2005, J. E. Smith 16
 Key Feature – VMM/Runtime Control q Interpretation • • q Binary translation and code caching • • • q Fine grain control Every dynamic instruction “inspected” before execution Coarser grain control Every static instruction inspected before execution Jumps to VM SW can be inserted anywhere Protection levels • • • Very coarse grain control Every resource-related instruction trapped by protection system Otherwise, use interpretation/translation techniques Used in system VMs to manage resource mappings VMs (c) 2005, J. E. Smith 17
Key Feature – VMM/Runtime Control q Interpretation • • q Binary translation and code caching • • • q Fine grain control Every dynamic instruction “inspected” before execution Coarser grain control Every static instruction inspected before execution Jumps to VM SW can be inserted anywhere Protection levels • • • Very coarse grain control Every resource-related instruction trapped by protection system Otherwise, use interpretation/translation techniques Used in system VMs to manage resource mappings VMs (c) 2005, J. E. Smith 17
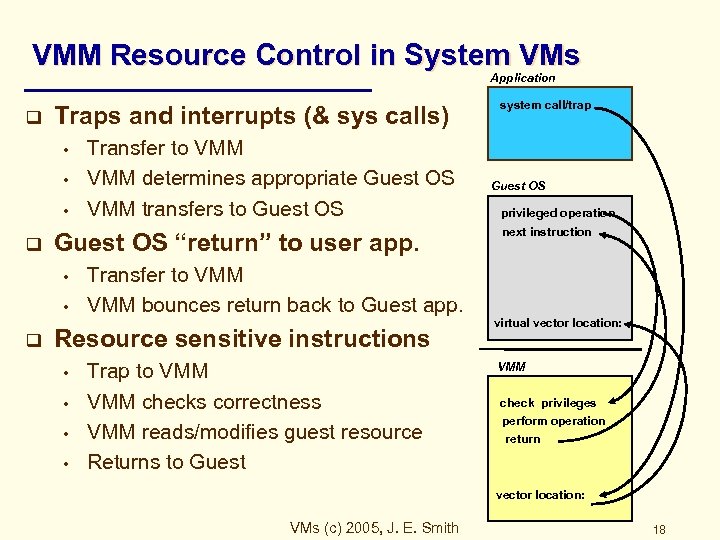 VMM Resource Control in System VMs Application q Traps and interrupts (& sys calls) • • • q Guest OS “return” to user app. • • q Transfer to VMM determines appropriate Guest OS VMM transfers to Guest OS Transfer to VMM bounces return back to Guest app. Resource sensitive instructions • • Trap to VMM checks correctness VMM reads/modifies guest resource Returns to Guest system call/trap Guest OS privileged operation next instruction virtual vector location: VMM check privileges perform operation return vector location: VMs (c) 2005, J. E. Smith 18
VMM Resource Control in System VMs Application q Traps and interrupts (& sys calls) • • • q Guest OS “return” to user app. • • q Transfer to VMM determines appropriate Guest OS VMM transfers to Guest OS Transfer to VMM bounces return back to Guest app. Resource sensitive instructions • • Trap to VMM checks correctness VMM reads/modifies guest resource Returns to Guest system call/trap Guest OS privileged operation next instruction virtual vector location: VMM check privileges perform operation return vector location: VMs (c) 2005, J. E. Smith 18
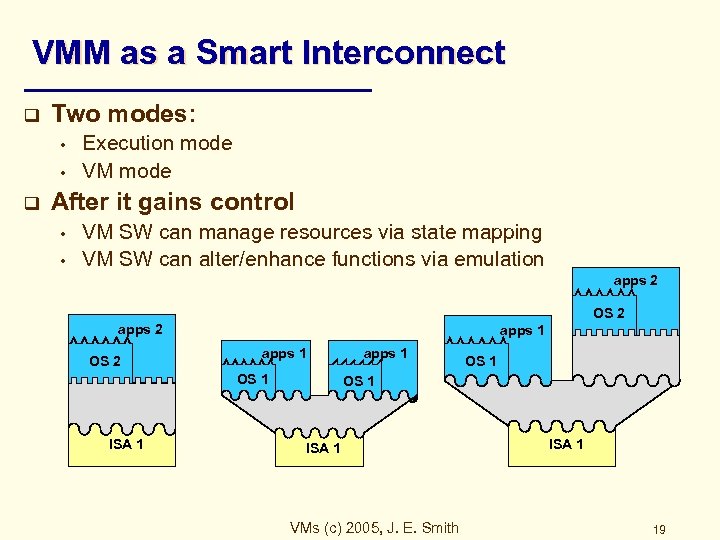 VMM as a Smart Interconnect q Two modes: • • q Execution mode VM mode After it gains control • • VM SW can manage resources via state mapping VM SW can alter/enhance functions via emulation apps 2 OS 2 apps 1 OS 1 ISA 1 VMs (c) 2005, J. E. Smith ISA 1 19
VMM as a Smart Interconnect q Two modes: • • q Execution mode VM mode After it gains control • • VM SW can manage resources via state mapping VM SW can alter/enhance functions via emulation apps 2 OS 2 apps 1 OS 1 ISA 1 VMs (c) 2005, J. E. Smith ISA 1 19
 Security q Many security threats • q Worms, viruses, Trojan horses, etc. Typical attack – get access to privileged part of system • • Often with little effort Compromised passwords “Easy” passwords Mechanically repeated efforts Exploit weakness in system software Unchecked accesses to system data structures Can get control in privileged state by causing overflows VMs (c) 2005, J. E. Smith 20
Security q Many security threats • q Worms, viruses, Trojan horses, etc. Typical attack – get access to privileged part of system • • Often with little effort Compromised passwords “Easy” passwords Mechanically repeated efforts Exploit weakness in system software Unchecked accesses to system data structures Can get control in privileged state by causing overflows VMs (c) 2005, J. E. Smith 20
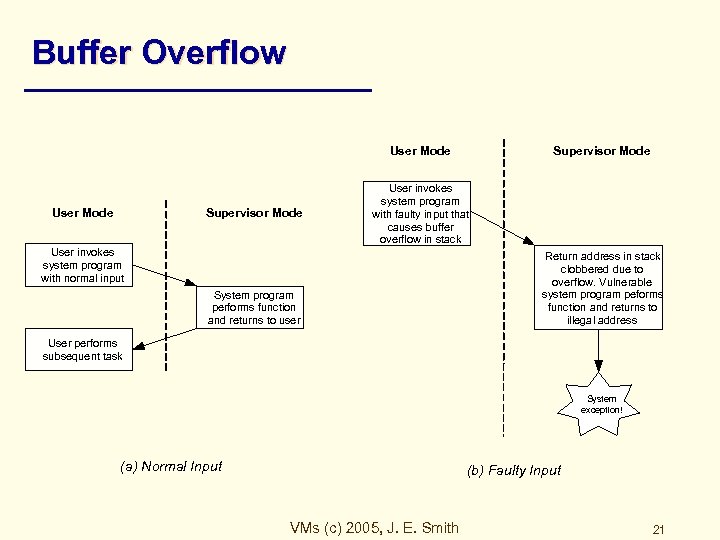 Buffer Overflow User Mode Supervisor Mode User invokes system program with faulty input that causes buffer overflow in stack User invokes system program with normal input System program performs function and returns to user Return address in stack clobbered due to overflow. Vulnerable system program peforms function and returns to illegal address User performs subsequent task System exception! (a) Normal Input (b) Faulty Input VMs (c) 2005, J. E. Smith 21
Buffer Overflow User Mode Supervisor Mode User invokes system program with faulty input that causes buffer overflow in stack User invokes system program with normal input System program performs function and returns to user Return address in stack clobbered due to overflow. Vulnerable system program peforms function and returns to illegal address User performs subsequent task System exception! (a) Normal Input (b) Faulty Input VMs (c) 2005, J. E. Smith 21
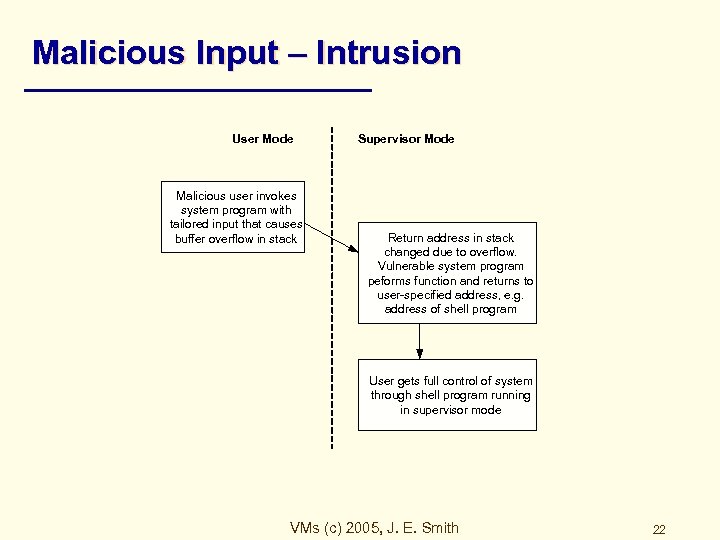 Malicious Input – Intrusion User Mode Malicious user invokes system program with tailored input that causes buffer overflow in stack Supervisor Mode Return address in stack changed due to overflow. Vulnerable system program peforms function and returns to user-specified address, e. g. address of shell program User gets full control of system through shell program running in supervisor mode VMs (c) 2005, J. E. Smith 22
Malicious Input – Intrusion User Mode Malicious user invokes system program with tailored input that causes buffer overflow in stack Supervisor Mode Return address in stack changed due to overflow. Vulnerable system program peforms function and returns to user-specified address, e. g. address of shell program User gets full control of system through shell program running in supervisor mode VMs (c) 2005, J. E. Smith 22
 Intrusion Detection Systems q Isolation is not an option • q Language-level checking • • q Increasing dependence on communication over networks Java, MSIL – range- and type-checking Legacy applications and legacy style not protected Need for Intrusion Detection Systems (IDS) • • • Depend on knowledge of potential attacks Network-based Intrusion Detection Systems (NIDS) Host-based Intrusion Detection Systems (HIDS) VMs (c) 2005, J. E. Smith 23
Intrusion Detection Systems q Isolation is not an option • q Language-level checking • • q Increasing dependence on communication over networks Java, MSIL – range- and type-checking Legacy applications and legacy style not protected Need for Intrusion Detection Systems (IDS) • • • Depend on knowledge of potential attacks Network-based Intrusion Detection Systems (NIDS) Host-based Intrusion Detection Systems (HIDS) VMs (c) 2005, J. E. Smith 23
 Host Intrusion Detection Systems q Directly examine activity on host • • q q Knowledge of host operating system Look for repeated attempts To crack password To access unauthorized files, etc. HIDS has significantly better viewpoint compared to NIDS But HIDS can be disabled by attack • Or can provide misleading information VMs (c) 2005, J. E. Smith 24
Host Intrusion Detection Systems q Directly examine activity on host • • q q Knowledge of host operating system Look for repeated attempts To crack password To access unauthorized files, etc. HIDS has significantly better viewpoint compared to NIDS But HIDS can be disabled by attack • Or can provide misleading information VMs (c) 2005, J. E. Smith 24
 Monitoring and Recovering from Attacks q Importance of understanding attacks • • q To recover from an attack To prevent future attacks Logging • • Save information about critical activity on system Know the events that caused the failure Save checkpoint of state of system Reconstruct the attack from a known good state VMs (c) 2005, J. E. Smith 25
Monitoring and Recovering from Attacks q Importance of understanding attacks • • q To recover from an attack To prevent future attacks Logging • • Save information about critical activity on system Know the events that caused the failure Save checkpoint of state of system Reconstruct the attack from a known good state VMs (c) 2005, J. E. Smith 25
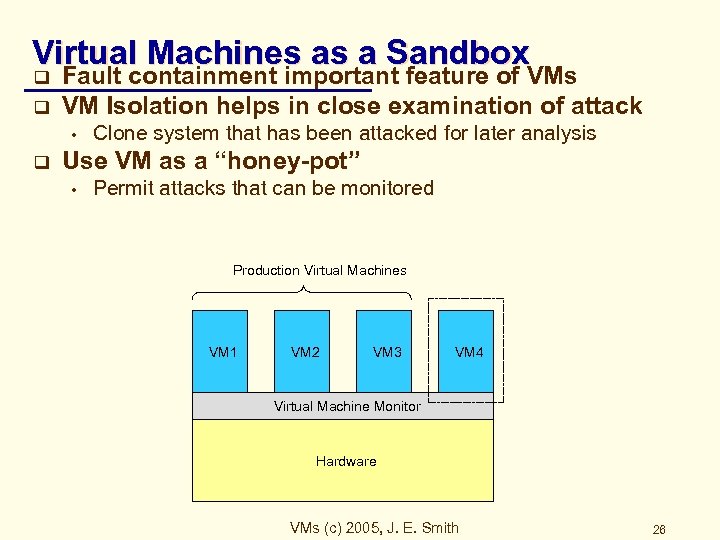 Virtual Machines as a Sandbox q q Fault containment important feature of VMs VM Isolation helps in close examination of attack • q Clone system that has been attacked for later analysis Use VM as a “honey-pot” • Permit attacks that can be monitored Production Virtual Machines VM 1 VM 2 VM 3 VM 4 Virtual Machine Monitor Hardware VMs (c) 2005, J. E. Smith 26
Virtual Machines as a Sandbox q q Fault containment important feature of VMs VM Isolation helps in close examination of attack • q Clone system that has been attacked for later analysis Use VM as a “honey-pot” • Permit attacks that can be monitored Production Virtual Machines VM 1 VM 2 VM 3 VM 4 Virtual Machine Monitor Hardware VMs (c) 2005, J. E. Smith 26
 Virtual Machine for Monitoring q Livewire system (Stanford) • Separates IDS from VMM • IDS configures the VMM to monitor activity at more than the usual points Signature of suspicious activity may be specified • After initialization, IDS enters the picture only in analyzing data from suspicious activity • Feedback – suggest new monitoring based on analysis E. g. monitor system call activity after repeated login attempts • May need knowledge of OS to analyze data, e. g. crash dumps VMs (c) 2005, J. E. Smith 27
Virtual Machine for Monitoring q Livewire system (Stanford) • Separates IDS from VMM • IDS configures the VMM to monitor activity at more than the usual points Signature of suspicious activity may be specified • After initialization, IDS enters the picture only in analyzing data from suspicious activity • Feedback – suggest new monitoring based on analysis E. g. monitor system call activity after repeated login attempts • May need knowledge of OS to analyze data, e. g. crash dumps VMs (c) 2005, J. E. Smith 27
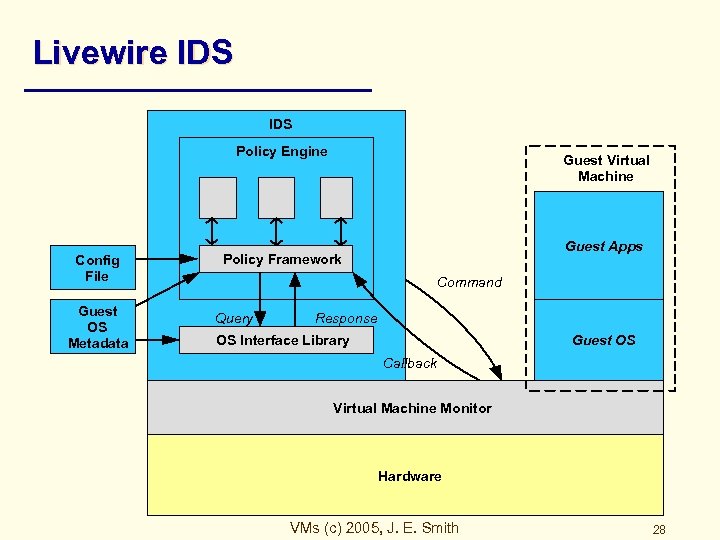 Livewire IDS Policy Engine Guest Virtual Machine Policy Modules Config File Guest OS Metadata Guest Apps Policy Framework Command Query Response OS Interface Library Guest OS Callback Virtual Machine Monitor Hardware VMs (c) 2005, J. E. Smith 28
Livewire IDS Policy Engine Guest Virtual Machine Policy Modules Config File Guest OS Metadata Guest Apps Policy Framework Command Query Response OS Interface Library Guest OS Callback Virtual Machine Monitor Hardware VMs (c) 2005, J. E. Smith 28
 Policy Modules in Livewire q Polling modules • • • q Lie detector module VMM knows hardware state for each virtual machine Lie detector compares this state to the state provided as feedback from intruder User program integrity detector module Compare signatures of memory pages with saved signatures Signature detector module Scan memory with signature of known viruses, Trojan horse programs, etc. Event-driven modules • Memory access enforcer module VMM intercepts attempts to change page access privileges VMs (c) 2005, J. E. Smith 29
Policy Modules in Livewire q Polling modules • • • q Lie detector module VMM knows hardware state for each virtual machine Lie detector compares this state to the state provided as feedback from intruder User program integrity detector module Compare signatures of memory pages with saved signatures Signature detector module Scan memory with signature of known viruses, Trojan horse programs, etc. Event-driven modules • Memory access enforcer module VMM intercepts attempts to change page access privileges VMs (c) 2005, J. E. Smith 29
 Dynamic Binary Rewriting q Program shepherding • q Control execution of program Prevent program from being attacked Prevent program from being launching point for attacks RIO System (MIT) • • Based on Dynamo binary optimization system Target of every control transfer instruction verified Not to unauthorized locations Only to safe locations VMs (c) 2005, J. E. Smith 30
Dynamic Binary Rewriting q Program shepherding • q Control execution of program Prevent program from being attacked Prevent program from being launching point for attacks RIO System (MIT) • • Based on Dynamo binary optimization system Target of every control transfer instruction verified Not to unauthorized locations Only to safe locations VMs (c) 2005, J. E. Smith 30
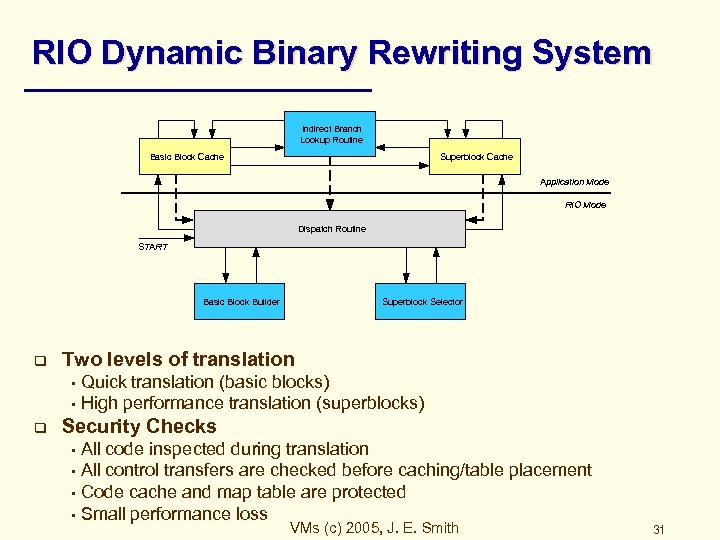 RIO Dynamic Binary Rewriting System Indirect Branch Lookup Routine Basic Block Cache Superblock Cache Application Mode RIO Mode Dispatch Routine START Basic Block Builder q Superblock Selector Two levels of translation Quick translation (basic blocks) • High performance translation (superblocks) • q Security Checks All code inspected during translation • All control transfers are checked before caching/table placement • Code cache and map table are protected • Small performance loss • VMs (c) 2005, J. E. Smith 31
RIO Dynamic Binary Rewriting System Indirect Branch Lookup Routine Basic Block Cache Superblock Cache Application Mode RIO Mode Dispatch Routine START Basic Block Builder q Superblock Selector Two levels of translation Quick translation (basic blocks) • High performance translation (superblocks) • q Security Checks All code inspected during translation • All control transfers are checked before caching/table placement • Code cache and map table are protected • Small performance loss • VMs (c) 2005, J. E. Smith 31
 Migration of Computing Environments q Identical environment at any work location • • q Entire state of machine must be transported • • q When moving from one location to another E. g. Home to work and back Effect similar to carrying hardware back and forth Physical security has to be taken care of State of processor resources For OS as well as applications Includes active code and data Concept of a capsule • Compressed information about entire system Can be transported from one location to another VMs (c) 2005, J. E. Smith 32
Migration of Computing Environments q Identical environment at any work location • • q Entire state of machine must be transported • • q When moving from one location to another E. g. Home to work and back Effect similar to carrying hardware back and forth Physical security has to be taken care of State of processor resources For OS as well as applications Includes active code and data Concept of a capsule • Compressed information about entire system Can be transported from one location to another VMs (c) 2005, J. E. Smith 32
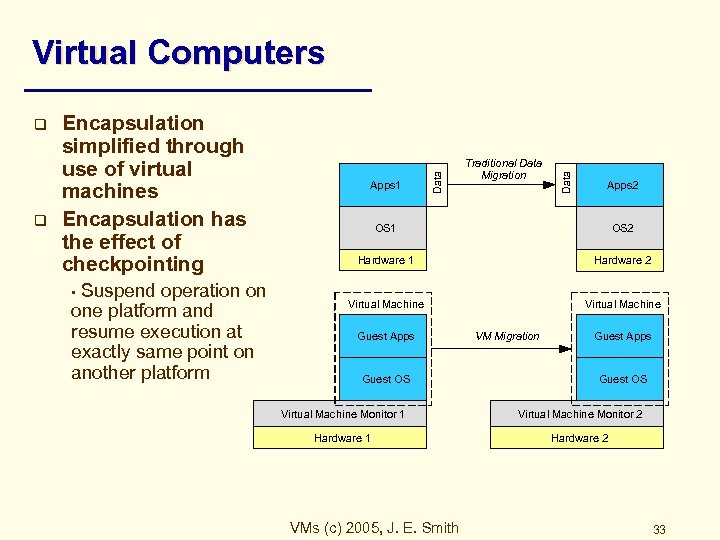 q Encapsulation simplified through use of virtual machines Encapsulation has the effect of checkpointing Suspend operation on one platform and resume execution at exactly same point on another platform • Apps 1 Traditional Data Migration Data q Data Virtual Computers Apps 2 OS 1 OS 2 Hardware 1 Hardware 2 Virtual Machine Guest Apps Guest OS VM Migration Guest Apps Guest OS Virtual Machine Monitor 1 Virtual Machine Monitor 2 Hardware 1 Hardware 2 VMs (c) 2005, J. E. Smith 33
q Encapsulation simplified through use of virtual machines Encapsulation has the effect of checkpointing Suspend operation on one platform and resume execution at exactly same point on another platform • Apps 1 Traditional Data Migration Data q Data Virtual Computers Apps 2 OS 1 OS 2 Hardware 1 Hardware 2 Virtual Machine Guest Apps Guest OS VM Migration Guest Apps Guest OS Virtual Machine Monitor 1 Virtual Machine Monitor 2 Hardware 1 Hardware 2 VMs (c) 2005, J. E. Smith 33
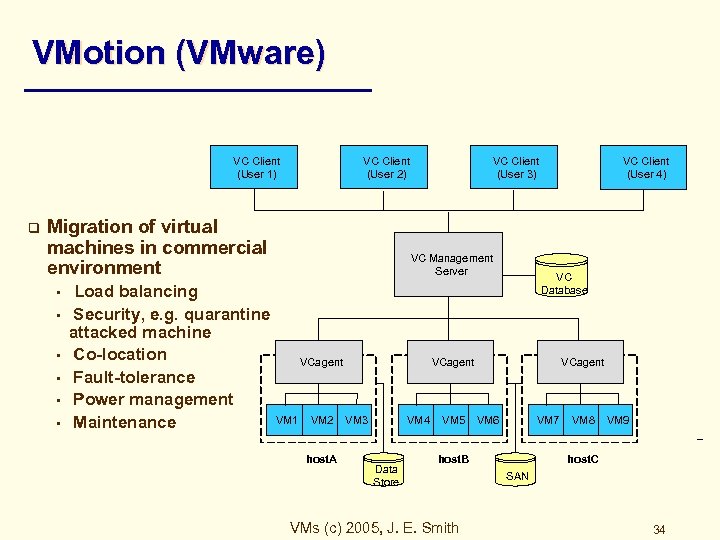 VMotion (VMware) VC Client (User 1) q VC Client (User 2) Migration of virtual machines in commercial environment • • • VC Client (User 3) VC Management Server Load balancing Security, e. g. quarantine attacked machine Co-location VCagent Fault-tolerance Power management VM 1 VM 2 VM 3 Maintenance host. A VC Client (User 4) VC Database VCagent VM 4 Data Store VM 5 VCagent VM 6 VM 7 host. B VMs (c) 2005, J. E. Smith VM 8 VM 9 host. C SAN 34
VMotion (VMware) VC Client (User 1) q VC Client (User 2) Migration of virtual machines in commercial environment • • • VC Client (User 3) VC Management Server Load balancing Security, e. g. quarantine attacked machine Co-location VCagent Fault-tolerance Power management VM 1 VM 2 VM 3 Maintenance host. A VC Client (User 4) VC Database VCagent VM 4 Data Store VM 5 VCagent VM 6 VM 7 host. B VMs (c) 2005, J. E. Smith VM 8 VM 9 host. C SAN 34
 Migration Steps q q Step 1: Ensure that VM is stable on current host Step 2: Perform baseline copy • q q Step 3: Suspend VM on current host Step 4: Perform final copy • q Copy of current memory state and data Send incremental capsule containing changes since baseline copy Step 5: Activate VM on new host VMs (c) 2005, J. E. Smith 35
Migration Steps q q Step 1: Ensure that VM is stable on current host Step 2: Perform baseline copy • q q Step 3: Suspend VM on current host Step 4: Perform final copy • q Copy of current memory state and data Send incremental capsule containing changes since baseline copy Step 5: Activate VM on new host VMs (c) 2005, J. E. Smith 35
 Grids: Virtual Organizations VMs (c) 2005, J. E. Smith 36
Grids: Virtual Organizations VMs (c) 2005, J. E. Smith 36
 Comparison with Conventional VMs q q q Efficient utilization of resources • Similar in motivation to original system VMs Sharing of resources • Grid concerned with sharing of content also Not just sharing of resources Distributed control • Grid has global scope Users negotiate with each other to share and use resources Heterogeneous nodes • Nodes in a grid may be different types of machines Adaptation of applications • Applications may need to be adapted for the grid Portability of applications • Conceptually similar to goals of HLL VMs (c) 2005, J. E. Smith 37
Comparison with Conventional VMs q q q Efficient utilization of resources • Similar in motivation to original system VMs Sharing of resources • Grid concerned with sharing of content also Not just sharing of resources Distributed control • Grid has global scope Users negotiate with each other to share and use resources Heterogeneous nodes • Nodes in a grid may be different types of machines Adaptation of applications • Applications may need to be adapted for the grid Portability of applications • Conceptually similar to goals of HLL VMs (c) 2005, J. E. Smith 37
 Role of System VMs in a Grid q Grid has to manage and schedule resources • q However, grid has to deal with heterogeneity • q Like an operating system Accounting, for example, is dependent on accounting policies of each grid participant System VM-based approach • Treat a VM as the unit of transactions on a grid Not tasks, or programs ( Figuieredo and Fortes) VMs (c) 2005, J. E. Smith 38
Role of System VMs in a Grid q Grid has to manage and schedule resources • q However, grid has to deal with heterogeneity • q Like an operating system Accounting, for example, is dependent on accounting policies of each grid participant System VM-based approach • Treat a VM as the unit of transactions on a grid Not tasks, or programs ( Figuieredo and Fortes) VMs (c) 2005, J. E. Smith 38
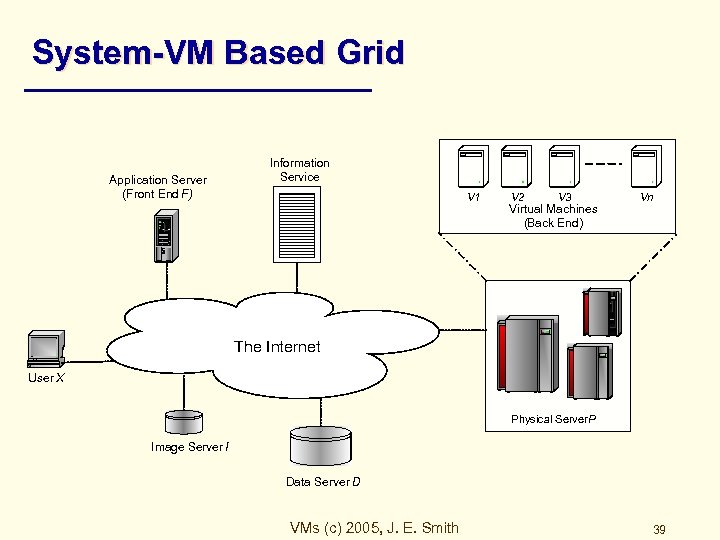 System-VM Based Grid Application Server (Front End F) Information Service V 1 V 2 V 3 Virtual Machines (Back End) Vn The Internet User X Physical Server. P Image Server I Data Server D VMs (c) 2005, J. E. Smith 39
System-VM Based Grid Application Server (Front End F) Information Service V 1 V 2 V 3 Virtual Machines (Back End) Vn The Internet User X Physical Server. P Image Server I Data Server D VMs (c) 2005, J. E. Smith 39
 Advantages of SVM based Approach q User isolation • • q Platform independence • q User specifies type of machine, not actual machine Task management and accounting • q Protect user from host and other users Protect host from users Simplifies allocation and accounting Allocate based on compute requirements Charge based on performance of VM Portability • • Allows applications to be written for execution on the widest range of platforms Eases encapsulation and migration of jobs between nodes on grid; e. g. Java VMs can be migrated VMs (c) 2005, J. E. Smith 40
Advantages of SVM based Approach q User isolation • • q Platform independence • q User specifies type of machine, not actual machine Task management and accounting • q Protect user from host and other users Protect host from users Simplifies allocation and accounting Allocate based on compute requirements Charge based on performance of VM Portability • • Allows applications to be written for execution on the widest range of platforms Eases encapsulation and migration of jobs between nodes on grid; e. g. Java VMs can be migrated VMs (c) 2005, J. E. Smith 40
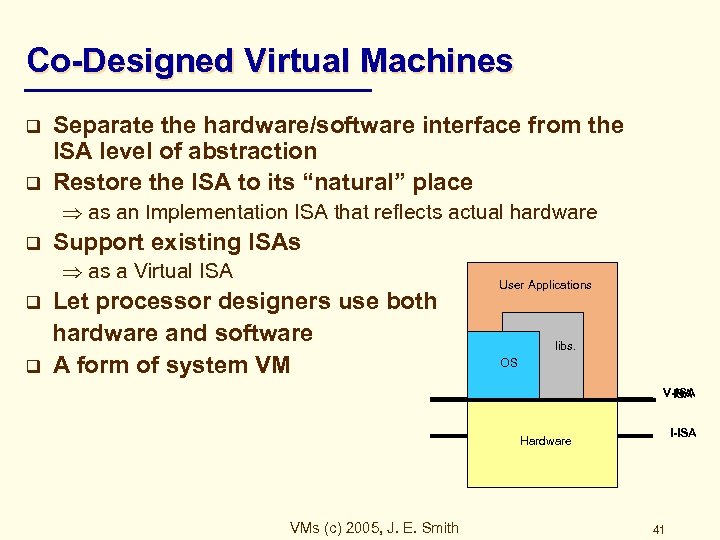 Co-Designed Virtual Machines q q Separate the hardware/software interface from the ISA level of abstraction Restore the ISA to its “natural” place as an Implementation ISA that reflects actual hardware q Support existing ISAs as a Virtual ISA q q Let processor designers use both hardware and software A form of system VM User Applications libs. OS V-ISA Software I-ISA Hardware VMs (c) 2005, J. E. Smith 41
Co-Designed Virtual Machines q q Separate the hardware/software interface from the ISA level of abstraction Restore the ISA to its “natural” place as an Implementation ISA that reflects actual hardware q Support existing ISAs as a Virtual ISA q q Let processor designers use both hardware and software A form of system VM User Applications libs. OS V-ISA Software I-ISA Hardware VMs (c) 2005, J. E. Smith 41
 Co-Designed VMs q Should be of interest to both architects and micro-architects • • Offers opportunities for performance, power saving, fault tolerance and other implementationdependent features Allows transcending conventional ISAs IBM Daisy and Transmeta Crusoe Don’t confuse them with VLIW! “pioneers are the ones with arrows in their backs” VMs (c) 2005, J. E. Smith 42
Co-Designed VMs q Should be of interest to both architects and micro-architects • • Offers opportunities for performance, power saving, fault tolerance and other implementationdependent features Allows transcending conventional ISAs IBM Daisy and Transmeta Crusoe Don’t confuse them with VLIW! “pioneers are the ones with arrows in their backs” VMs (c) 2005, J. E. Smith 42
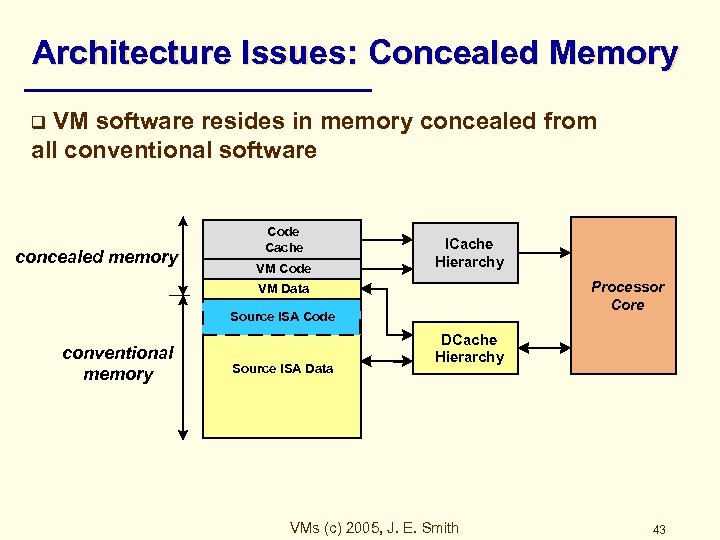 Architecture Issues: Concealed Memory VM software resides in memory concealed from all conventional software q concealed memory Code Cache VM Code ICache Hierarchy Processor Core VM Data Source ISA Code conventional memory Source ISA Data DCache Hierarchy VMs (c) 2005, J. E. Smith 43
Architecture Issues: Concealed Memory VM software resides in memory concealed from all conventional software q concealed memory Code Cache VM Code ICache Hierarchy Processor Core VM Data Source ISA Code conventional memory Source ISA Data DCache Hierarchy VMs (c) 2005, J. E. Smith 43
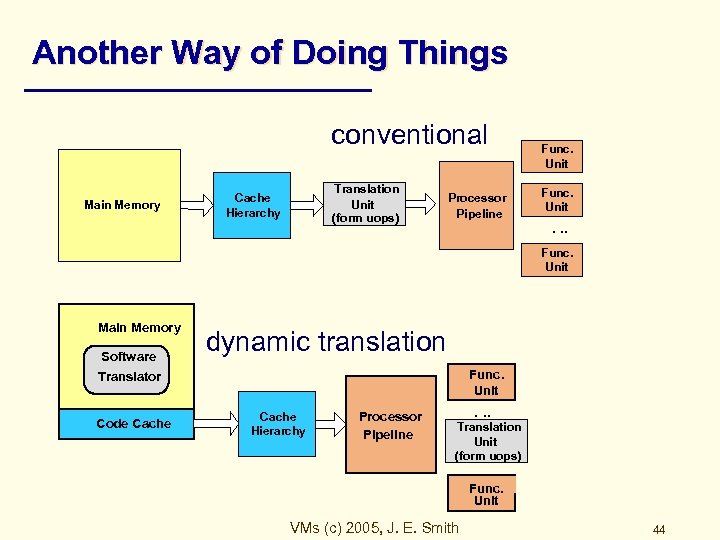 Another Way of Doing Things conventional Main Memory Translation Unit (form uops) Cache Hierarchy Processor Pipeline Func. Unit . . . Func. Unit Main Memory Software dynamic translation Func. Unit Translator Code Cache Hierarchy Processor Pipeline . . . Translation Unit (form uops) Func. Unit VMs (c) 2005, J. E. Smith 44
Another Way of Doing Things conventional Main Memory Translation Unit (form uops) Cache Hierarchy Processor Pipeline Func. Unit . . . Func. Unit Main Memory Software dynamic translation Func. Unit Translator Code Cache Hierarchy Processor Pipeline . . . Translation Unit (form uops) Func. Unit VMs (c) 2005, J. E. Smith 44
 Fused Instruction Set q Co-designed VM x 86 implementation • q Combine pairs of dependent instructions • q For single “unit” for pipeline processing Use VM software to • • • q Shorten and simplify pipeline front-end “Crack” x 86 instructions into RISC-ops Re-order RISC-ops Reassemble into (new) fused pairs Related: Pentium-M fuses in front-end • • Using original x 86 instructions “Reduced Splitting” is more accurate description VMs (c) 2005, J. E. Smith 45
Fused Instruction Set q Co-designed VM x 86 implementation • q Combine pairs of dependent instructions • q For single “unit” for pipeline processing Use VM software to • • • q Shorten and simplify pipeline front-end “Crack” x 86 instructions into RISC-ops Re-order RISC-ops Reassemble into (new) fused pairs Related: Pentium-M fuses in front-end • • Using original x 86 instructions “Reduced Splitting” is more accurate description VMs (c) 2005, J. E. Smith 45
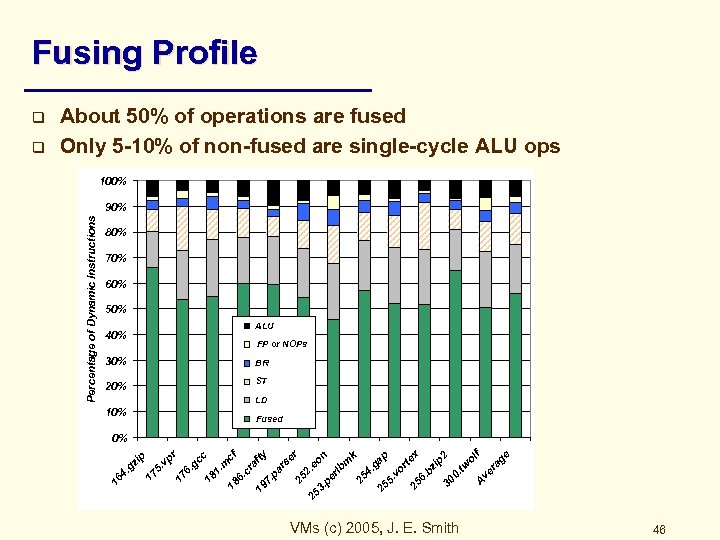 Fusing Profile 100% 90% 80% 70% 60% 50% ALU 40% FP or NOPs 30% BR 20% ST LD 10% Fused vp r 17 6. gc c 18 1. m cf 18 6. cr af 19 ty 7. pa rs er 25 25 2. e o 3. pe n rlb m k 25 4. ga 25 p 5. vo r 25 tex 6. bz ip 2 30 0. tw ol f A ve ra ge 17 5. gz ip 0% 16 4. q About 50% of operations are fused Only 5 -10% of non-fused are single-cycle ALU ops Percentage of Dynamic Instructions q VMs (c) 2005, J. E. Smith 46
Fusing Profile 100% 90% 80% 70% 60% 50% ALU 40% FP or NOPs 30% BR 20% ST LD 10% Fused vp r 17 6. gc c 18 1. m cf 18 6. cr af 19 ty 7. pa rs er 25 25 2. e o 3. pe n rlb m k 25 4. ga 25 p 5. vo r 25 tex 6. bz ip 2 30 0. tw ol f A ve ra ge 17 5. gz ip 0% 16 4. q About 50% of operations are fused Only 5 -10% of non-fused are single-cycle ALU ops Percentage of Dynamic Instructions q VMs (c) 2005, J. E. Smith 46
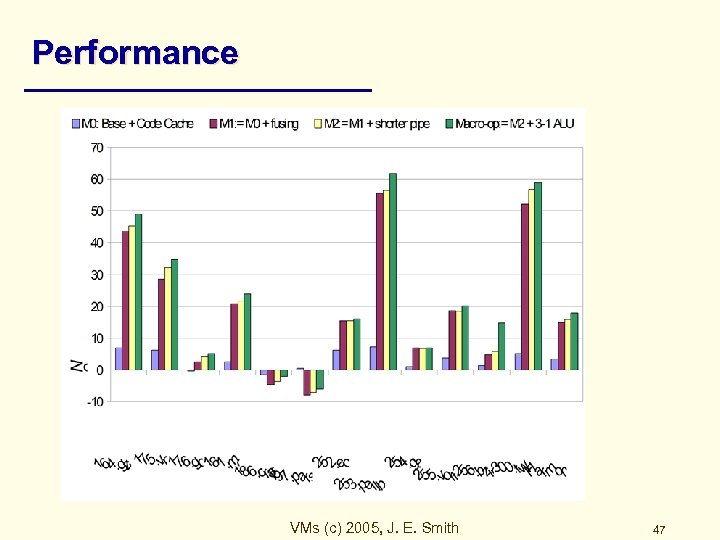 Performance VMs (c) 2005, J. E. Smith 47
Performance VMs (c) 2005, J. E. Smith 47
 Summary q Many types of VMs • q A smart interconnect component • • q But common implementation technologies Should be studied/taught as a discipline on its own Alongside OS, Application SW, HW Many avenues for research • • • Lots of applications Architecture meta-issues – What features of OS, Applications, HW are “VM friendly”? E. g. Goldberg work in early 70 s for system VMs Primitives for supporting VMs (c) 2005, J. E. Smith 48
Summary q Many types of VMs • q A smart interconnect component • • q But common implementation technologies Should be studied/taught as a discipline on its own Alongside OS, Application SW, HW Many avenues for research • • • Lots of applications Architecture meta-issues – What features of OS, Applications, HW are “VM friendly”? E. g. Goldberg work in early 70 s for system VMs Primitives for supporting VMs (c) 2005, J. E. Smith 48


