073bb272eb44b369a0c71c385c9445e8.ppt
- Количество слайдов: 70

V 8 1

Semi Automated Bartering of Digital Goods and Services in Pervasive Environments Olga Ratsimor Doctoral Research Proposal October 25 2005 2

INTRO • • • Presentation Outline Introduction Thesis Statement Motivation Proposed Approach Research Contributions Research Plan & Time. Line Preliminary Work Related Work Summary and Q&A 3
INTRO Pervasive Computing Vision 4

INTRO Issues Affecting Collaboration • No incentive for collaborations • Self-interested personal mobile devices have limited resources • Free Rider Problems in Pervasive Environments • In attempt to conserve its computing resources and power, device drops service requests and other communications from other devices while sending out service discovery requests for its own benefit. • Information Noise Makers and Spammers: • • Spamming and other heavy communication services. Devices must be capable of filtering out “noise“ still being able to collect useful information and discover needed services. 5

INTRO Environmental Limitations • Quality of Services is Unpredictable: • • Received goods and services may not be what originally was expected. Utility function various on perceived context, time, location, etc. • Inefficient Storage of Context Specific Services: • • Many of the services are very context specific and are used only during a particular context. When the user changes context, unused services continue to take up space and resources on the devices. 6

Hypothesis Statement HS The Question : Considering the diversity and the personal nature of devices participating in pervasive environments, is the current model of altruistic ad hoc collaborations still the most effective model to motivate collaborations? The Hypothesis: Bartering can be an effective mechanism to incentivize devices to collaborate and improve the quality of collaborations. The Proposed Approach: • • • Incentive driven collaboration mechanisms Communication model based on bartering Value based view of electronic goods and services 7

MOTIV • • • Presentation Outline Introduction Thesis Statement Motivation Proposed Approach Research Contributions Research Plan & Time. Line Preliminary Work Related Work Summary and Q&A 8
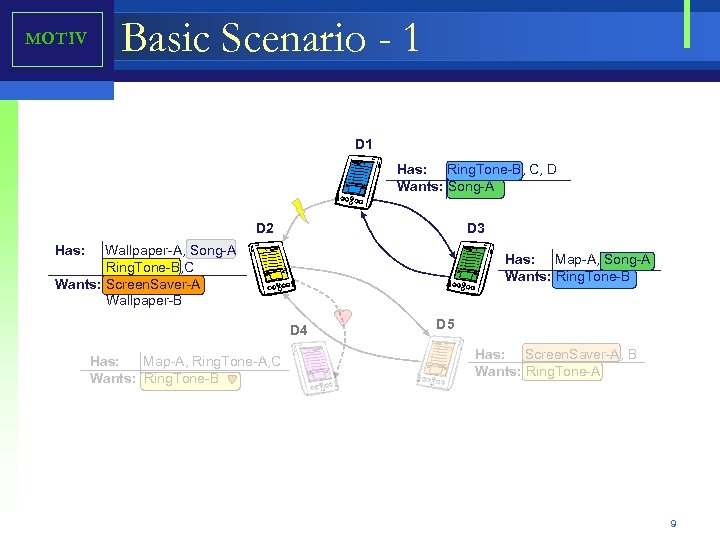
MOTIV Basic Scenario - 1 D 1 Has: Ring. Tone-B, C, D Wants: Song-A D 2 D 3 Has: Wallpaper-A, Song-A Ring. Tone-B, C Wants: Screen. Saver-A Wallpaper-B Has: Map-A, Song-A Wants: Ring. Tone-B D 4 Has: Map-A, Ring. Tone-A, C Wants: Ring. Tone-B D 5 Has: Screen. Saver-A, B Wants: Ring. Tone-A 9
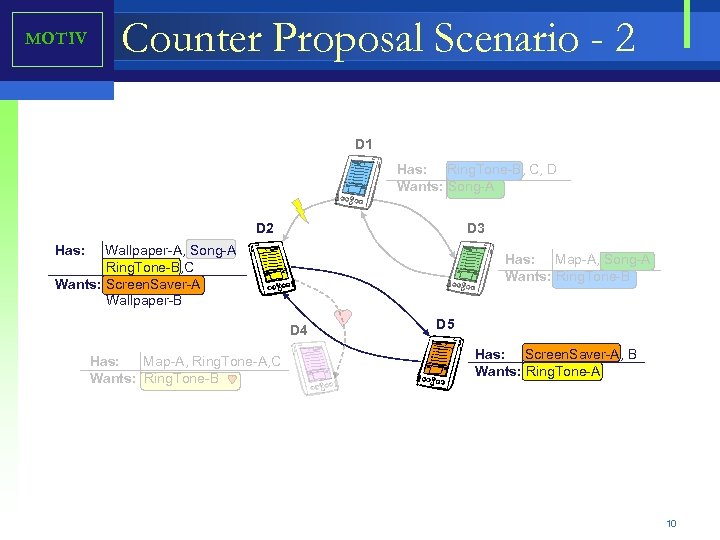
MOTIV Counter Proposal Scenario - 2 D 1 Has: Ring. Tone-B, C, D Wants: Song-A D 2 D 3 Has: Wallpaper-A, Song-A Ring. Tone-B, C Wants: Screen. Saver-A Wallpaper-B Has: Map-A, Song-A Wants: Ring. Tone-B D 4 Has: Map-A, Ring. Tone-A, C Wants: Ring. Tone-B D 5 Has: Screen. Saver-A, B Wants: Ring. Tone-A 10
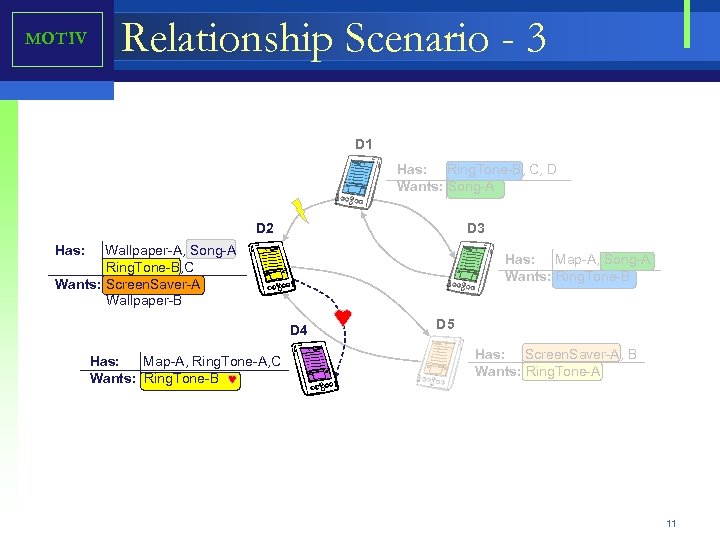
MOTIV Relationship Scenario - 3 D 1 Has: Ring. Tone-B, C, D Wants: Song-A D 2 D 3 Has: Wallpaper-A, Song-A Ring. Tone-B, C Wants: Screen. Saver-A Wallpaper-B Has: Map-A, Song-A Wants: Ring. Tone-B D 4 Has: Map-A, Ring. Tone-A, C Wants: Ring. Tone-B D 5 Has: Screen. Saver-A, B Wants: Ring. Tone-A 11
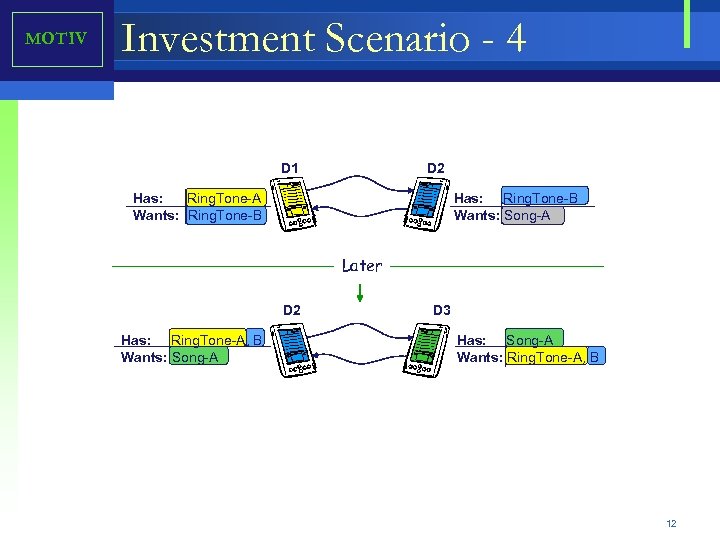
MOTIV Investment Scenario - 4 D 1 D 2 Has: Ring. Tone-A Wants: Ring. Tone-B Has: Ring. Tone-B Wants: Song-A Later D 2 Has: Ring. Tone-A, B Wants: Song-A D 3 Has: Song-A Wants: Ring. Tone-A, B 12
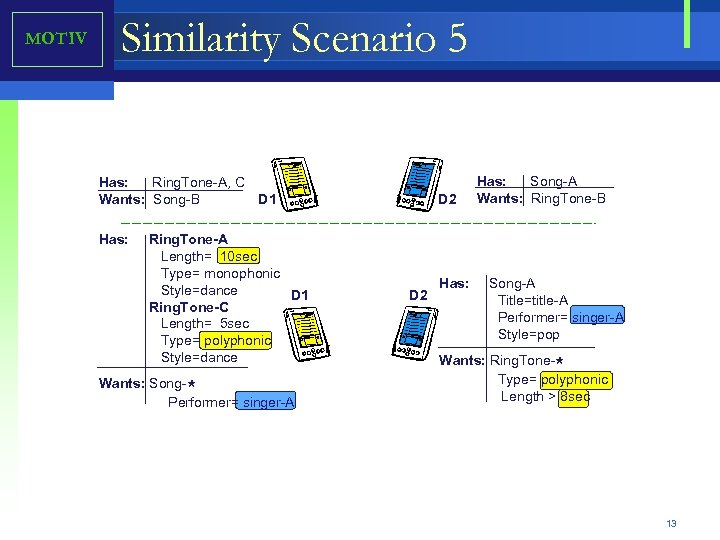
MOTIV Similarity Scenario 5 Has: Ring. Tone-A, C D 1 Wants: Song-B Has: Ring. Tone-A Length= 10 sec Type= monophonic Style=dance D 1 Ring. Tone-C Length= 5 sec Type= polyphonic Style=dance Wants: Song Performer= singer-A * D 2 Has: Song-A Wants: Ring. Tone-B Has: Song-A D 2 Title=title-A Performer= singer-A Style=pop Wants: Ring. Tone Type= polyphonic Length > 8 sec * 13

MOTIV Domain – What are Goods… • Digital Goods • Ring Tones, MP 3 s, Podcasts, Mobile Games, Screen Savers, Wallpaper, Video and Coupons • Low Cost Items • Replicable • Digital Rights Management (DRM) • transfer of ownership • Digital Goods are obtained • • for personal use to be used as token in future bartering 14

MOTIV Double Coincidence of Wants • A barter exchange requires a double coincidence of wants for trade to take place: “An exchange between two parties can only occur if both parties desire what the other is willing to give up” • • The probability that one person has what the other desires is not in our favor. Our model relaxes the constraint • Improves the participation and tolerance levels 15

MOTIV What is Needed? We need to develop: • Define and use Bartering protocols that are aware of personal relationships between the devices and their users’ perceived value of electronic goods and services. • Valuation of electronic goods and services in personalized context conscious manner. 16

Presentation Outline • • • Introduction Thesis Statement Motivation Proposed Approach Research Contributions Research Plan & Time. Line Preliminary Work Related Work Summary and Q&A 17

Bartering Model • Context-based, continuous bartering with peers in pervasive environments • • In order to barter, one has to understand what the items are worth and how much they are worth. One also wants to evaluate who s/he is dealing with. • Difference between community and anonymous P 2 P network 18

Perceived Value • Value in Use - is the value of the particular electronic good or service for the particular user. • Value in Exchange - reflects the potential value of the service against any other service in value -for-value exchanges. 19

Aspects of Value • Systemic Value represents the essence of the digital goods and services • Liquidity reflects the ease with which a service can be acquired or exchanged for any service without a significant loss in value. • • Simplicity and similar value are the key factors. A service is highly liquid if it can be exchanged frequently by many devices for services of a similar value. • Services with higher liquidity index would be in greater demand in the computing environment and could be used by devices as exchange tokens. 20

Aspects of Value • Context Based Value is the value that describes importance of the service or information in a particular context. • Original Cost of the service or information reflects resources or money that had to be spent to initially acquire the services. • Historic Value refers to the historic recorded value for the service of information. • Original Value 21

Aspects of Value • Store of Value refers to how consistently can the service store its value. Services and information value can depreciate or appreciate over time. • Depreciation over time • expiration time and date • limit on replication. • Appreciation over time • Memorabilia • Transaction Cost describes costs involved in searching, bargaining and transferring data and verifying the correctness and finalization of transaction. • Service Maintenance Cost describes the costs associated with keeping the service up to date. • Frequency of Use Valuation - service that is frequently used have greater value 22
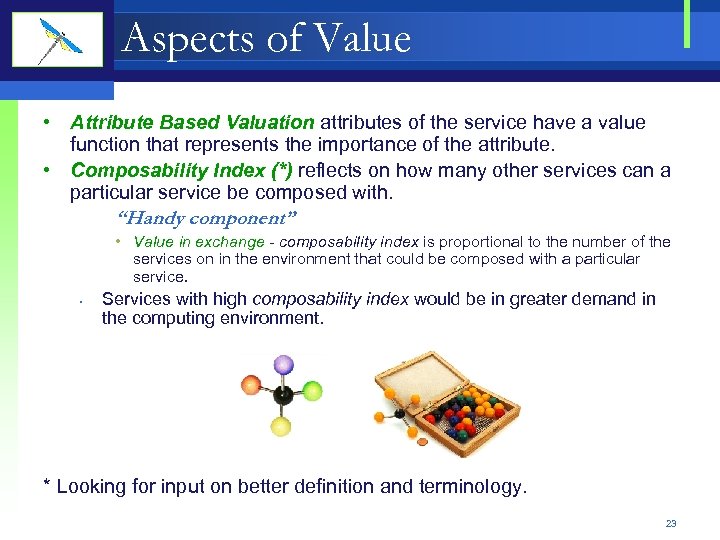
Aspects of Value • Attribute Based Valuation attributes of the service have a value function that represents the importance of the attribute. • Composability Index (*) reflects on how many other services can a particular service be composed with. “Handy component” • Value in exchange - composability index is proportional to the number of the services on in the environment that could be composed with a particular service. • Services with high composability index would be in greater demand in the computing environment. * Looking for input on better definition and terminology. 23
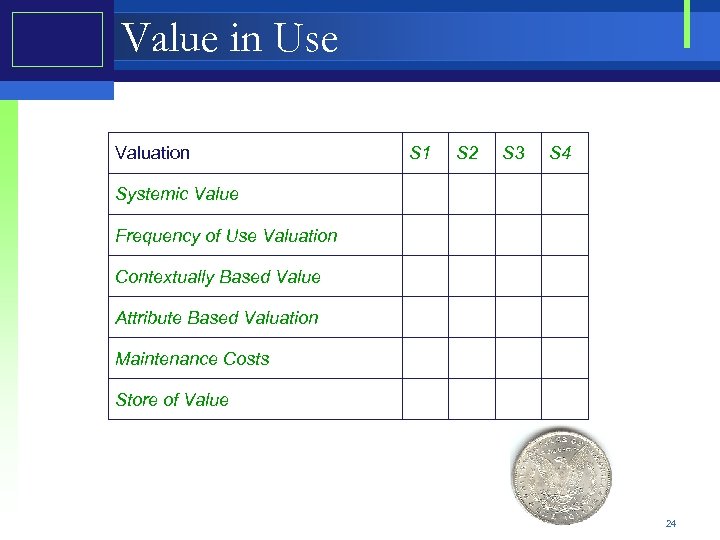
Value in Use Valuation S 1 S 2 S 3 S 4 Systemic Value Frequency of Use Valuation Contextually Based Value Attribute Based Valuation Maintenance Costs Store of Value 24
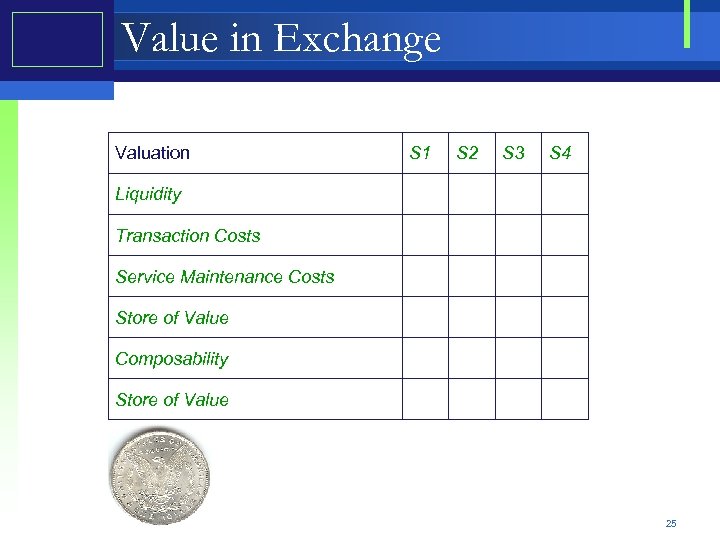
Value in Exchange Valuation S 1 S 2 S 3 S 4 Liquidity Transaction Costs Service Maintenance Costs Store of Value Composability Store of Value 25

Relationships • Exploit relationships between groups of devices • • Self Devices - are personal devices that belong to a single user. Sibling Devices - are devices of users that are very close. Friendly Devices - are devices that belong to the different users that frequently come in contact and collaborate with one another. Strangers Devices - are devices that just meet and are most likely will never come in contact again. • Siblings and Strangers are special cases of friendliness. • Unfriendly Devices - are devices that are actively uncooperative • Trust could also be used to determine the level of cooperation • Other Social Networks • Linked In & Orkut 26
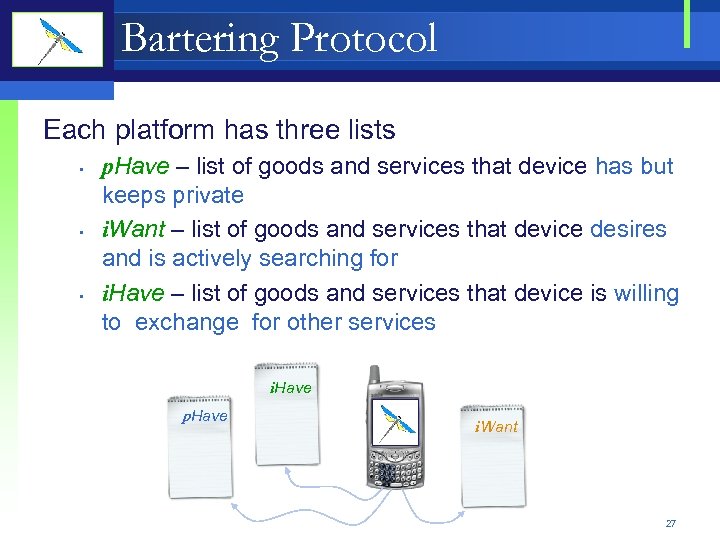
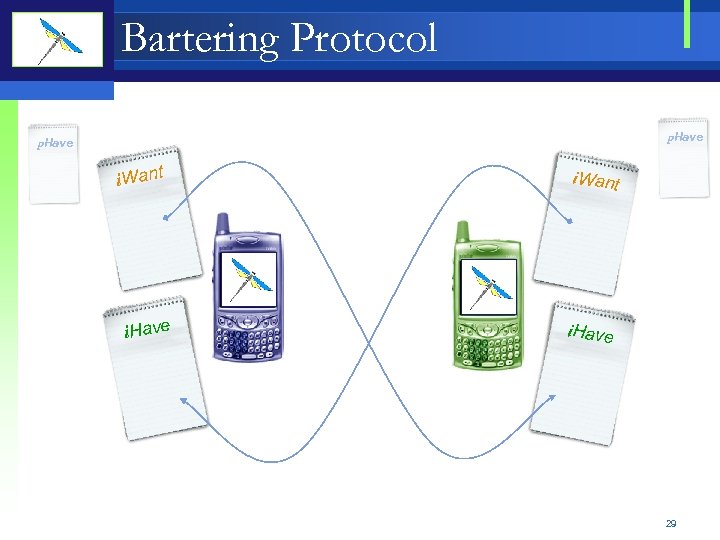
Bartering Protocol Each platform has three lists • • • p. Have – list of goods and services that device has but keeps private i. Want – list of goods and services that device desires and is actively searching for i. Have – list of goods and services that device is willing to exchange for other services i. Have p. Have i. Want 27

Bartering Protocol i. Want List and i. Have List will contain value based descriptions of each goods and services • Value in Use and Value in Exchange Focus Factor – how much should the device Focus on the service • focus factor in i. Want list– represents the intensity of the search for the desired good or service • focus factor in i. Have List - represents actively does the device advertise the presence of the good or service. i. Have p. Have i. Want 28
Bartering Protocol p. Have i. Want i. Have 29
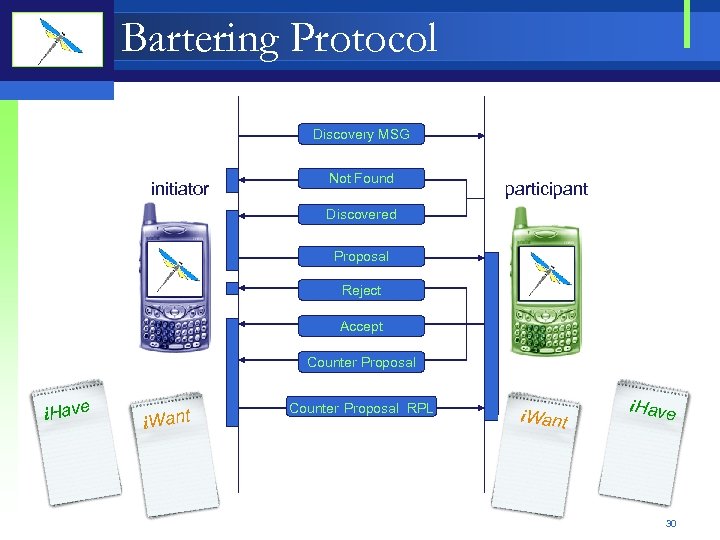
Bartering Protocol Discovery MSG initiator Not Found participant Discovered Proposal Reject Accept Counter Proposal i. Have i. Want Counter Proposal RPL i. Want i. Have 30
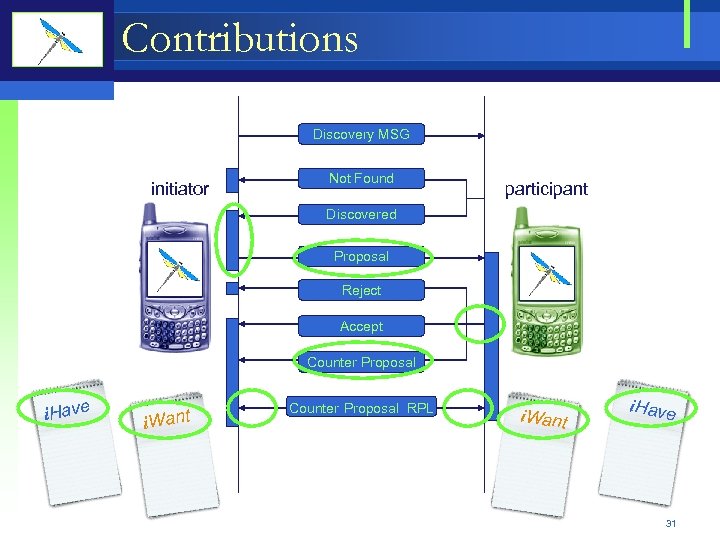
Contributions Discovery MSG initiator Not Found participant Discovered Proposal Reject Accept Counter Proposal i. Have i. Want Counter Proposal RPL i. Want i. Have 31

Contributions • Bartering Reasoner that answers the following questions: • • • What do I want, what do I offer ? (not interested…) Who do I want to barter with? What do I offer in return? What do I offer them? (What’s the offer? ) Do I accept, Do I reject, or Do I counterpropose? Do we have a deal? 32

Contributions • Development of value based descriptions for electronic goods and services. • Development and implementation of a framework that employs and manages valuations. • Development and implementation of bartering protocols / strategies that take: • Relationships-Based Bartering • Service Attribute Bartering • Demonstration of P 2 P environment that incentivizes collaboration. 33

PLAN • • Presentation Outline Introduction Motivation Proposed Approach Research Contributions Research Plan & Time. Line Preliminary Work Related Work Summary and Q&A 34

PLAN Tasks A. Value based descriptions for services and electronic goods B. Management component that employs these descriptions C. Bartering support engine D. Bartering protocols and strategies. • • Analysis of effectiveness of these protocols and strategies Incorporate and study effects of DRM E. Demonstration of P 2 P environment that incentivizes collaboration F. Analysis and Evaluation 35
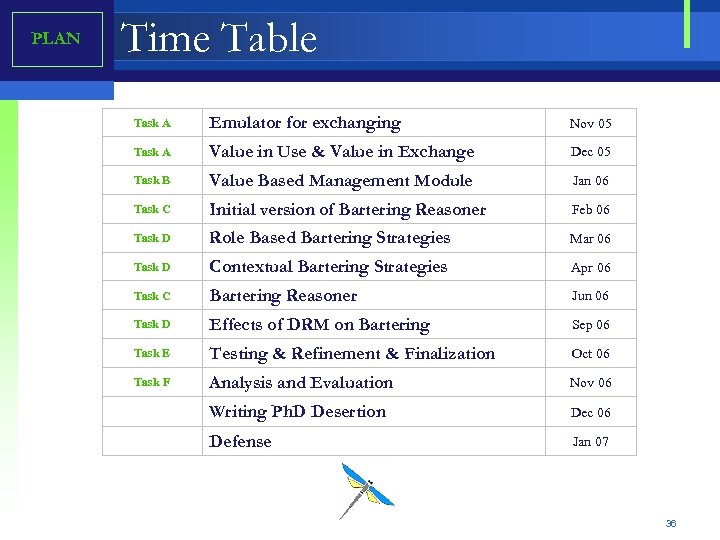
PLAN Time Table Task A Emulator for exchanging Nov 05 Task A Value in Use & Value in Exchange Dec 05 Task B Value Based Management Module Jan 06 Task C Initial version of Bartering Reasoner Feb 06 Task D Role Based Bartering Strategies Mar 06 Task D Contextual Bartering Strategies Apr 06 Task C Bartering Reasoner Jun 06 Task D Effects of DRM on Bartering Sep 06 Task E Testing & Refinement & Finalization Oct 06 Task F Analysis and Evaluation Nov 06 Writing Ph. D Desertion Dec 06 Defense Jan 07 36

PW • • Presentation Outline Introduction Motivation Proposed Approach Research Contributions Research Plan & Time. Line Preliminary Work Related Work Summary and Q&A 37

PW Preliminary Work • Allia - Policy-Based Alliance Formation for Agents in Ad-Hoc Environments • Agents 2 Go - An Infrastructure for Location. Dependent Service Discovery in The Mobile Electronic Commerce Environment • Numi - Using Peer-to-Peer Data Routing for Infrastructure-Based Wireless Networks • e. Ncentive - A Framework for Intelligent Marketing in Mobile Peer-To-Peer Environments • e. Ncentive +True. Bahn - m. Commerce and Trust 38

PW Preliminary Work Publications • Olga Ratsimor, Anupam Joshi, Timothy Finin, Yelena Yesha, e. Ncentive: A Framework for Intelligent Marketing in Mobile Peer-To-Peer Environments, The 5 th International Conference on Electronic Commerce (ICEC), October 2003 • Olga Ratsimor, Anupam Joshi, Timothy Finin, Yelena Yesha, Intelligent Ad Hoc Marketing within Hotspot Networks, Technical Report, Nov 2003 • Olga Ratsimor, Dipanjan Chakraborty, Deepali Khushraj, Anugeetha Kunjithapatham, Anupam Joshi, Timothy Finin, Yelena Yesha Service Discovery in Agent-based Pervasive Computing Environments, Journal on Mobile Networking and Applications (MONET), Special issue on Mobile and Pervasive Commerce. 2003. • Sethuram Balaji Kodeswaran, Olga Ratsimor, Anupam Joshi, Timothy Finin, Yelena Yesha, Numi: A Framework for Collaborative Data Management in a Network of Info. Stations, UMBC SRC, November 2002 • Olga Ratsimor, Dipanjan Chakraborty, Sovrin Tolia, Deepali Kushraj, Anugeetha Kunjithapatham, Gaurav Gupta, Anupam Joshi, Timothy Finin, Allia: Alliance-based Service Discovery for Ad-Hoc Environments, Paper, ACM Mobile Commerce Workshop, September, 2002. • Tim Finin, Anupam Joshi, Lalana Kagal, Olga Ratsimor, Sasikanth Avancha, Vlad Korolev, Harry Chen, Filip Perich, R. Scott Cost, Intelligent Agents for Mobile and Embedded Devices, International Journal on Cooperative. Information Systems, 2002. • Sethuram Balaji Kodeswaran, Olga Ratsimor, Anupam Joshi, Timothy Finin, Yelena Yesha, Using Peer-to-Peer Data Routing for Infrastructure-based Wireless Networks , IEEE International Conference on Pervasive Computing and Communications (Per. Com), March 2003. • Timothy Finin, Anupam Joshi, Lalana Kagal, Olga Ratsimor, Vlad Korolev, and Harry Chen, Information Agents for Mobile and Embedded Devices, Paper, Fifth International Workshop Cooperative Information Agents, Modena, Italy, September, 2001. • Olga Ratsimor, Sethuram Balaji Kodeswaran, Anupam Joshi, Timothy Finin, Yelena Yesha, Combining Infrastructure and Ad hoc Collaboration For Data Management in Mobile Wireless Networks, Workshop on "Ad hoc Communications and Collaboration in Ubiquitous Computing Environments", November 2002. • Olga Ratsimor, Vladimir Korolev, Anupam Joshi, and Timothy Finin, Agents 2 Go: An Infrastructure for Location. Dependent Service Discovery in the Mobile Electronic Commerce Environment, Paper, ACM Mobile Commerce Workshop, July, 2001. 39

PW Agents 2 Go • Location dependent services discovery • Location dependent information retrieval • Distributed services • • Service information is distributed and grouped by regions. Information about the restaurant is stored locally. • Automatic location detection • Cell tower ids are mapped to the geographical region name. • Service provider representation • • Service Agents reside at the service provider locations. Restaurant Agents reside at the restaurant locations. 40
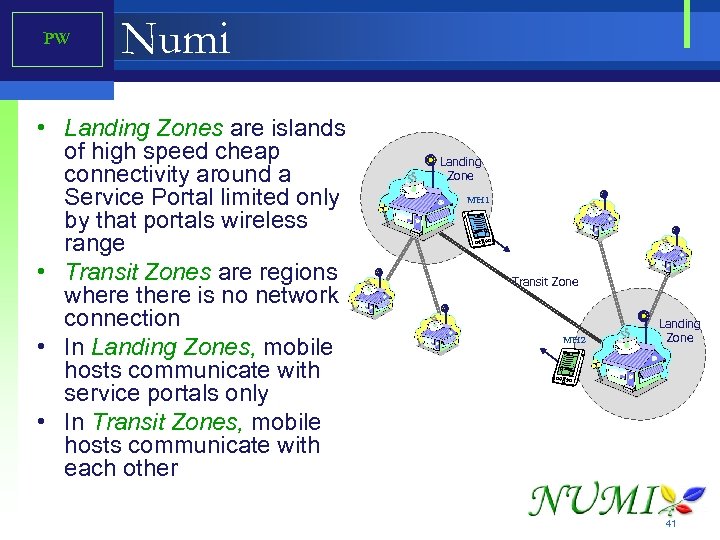
PW Numi • Landing Zones are islands of high speed cheap connectivity around a Service Portal limited only by that portals wireless range • Transit Zones are regions where there is no network connection • In Landing Zones, mobile hosts communicate with service portals only • In Transit Zones, mobile hosts communicate with each other Landing Zone MH 1 Transit Zone MH 2 Landing Zone 41

PW e. Ncentive • e. Ncentive is a framework that facilitates peer • • to peer mobile marketing in pervasive environments Mobile users collect promotions, advertisements, coupons and other discount information User preferences effect adds collection and distribution Mobile users market that information to other users in the network Active distributors are rewarded • Incentives for distribution are proportional to the amount of advertisements effectively distributed by the user • Wide choice of Reward Models 42
PW Mobility Coordinator 43

PW e. Ncentive PDA Interface 44
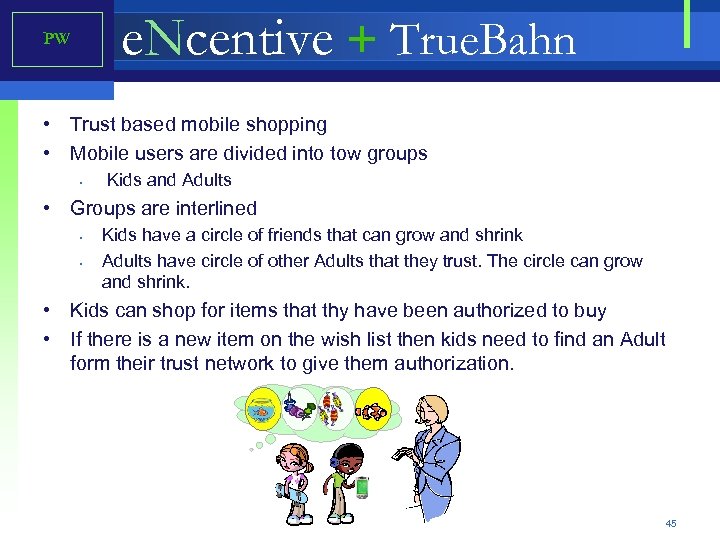
e. Ncentive + True. Bahn PW • Trust based mobile shopping • Mobile users are divided into tow groups • Kids and Adults • Groups are interlined • • Kids have a circle of friends that can grow and shrink Adults have circle of other Adults that they trust. The circle can grow and shrink. • Kids can shop for items that thy have been authorized to buy • If there is a new item on the wish list then kids need to find an Adult form their trust network to give them authorization. 45
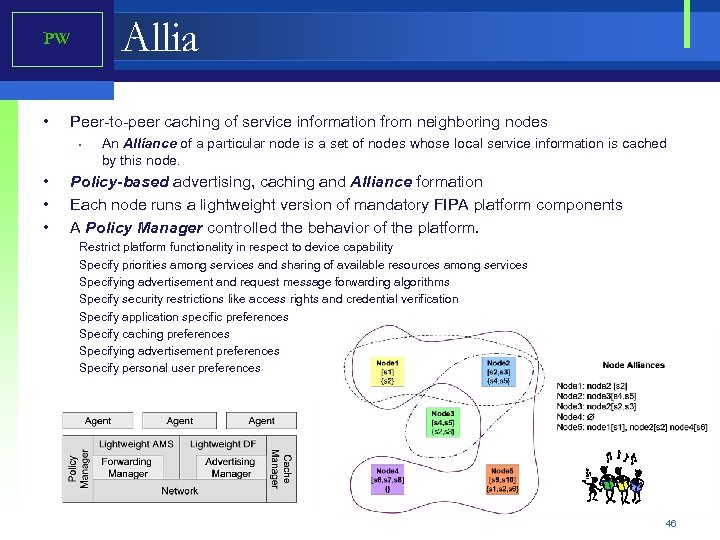
Allia PW • Peer-to-peer caching of service information from neighboring nodes • • An Alliance of a particular node is a set of nodes whose local service information is cached by this node. Policy-based advertising, caching and Alliance formation Each node runs a lightweight version of mandatory FIPA platform components A Policy Manager controlled the behavior of the platform. Restrict platform functionality in respect to device capability Specify priorities among services and sharing of available resources among services Specifying advertisement and request message forwarding algorithms Specify security restrictions like access rights and credential verification Specify application specific preferences Specify caching preferences Specifying advertisement preferences Specify personal user preferences 46

RW • • Presentation Outline Introduction Motivation Proposed Approach Research Contributions Research Plan & Time. Line Preliminary Work Related Work Summary and Q&A 47

RW • • • Related Work Context-aware Computing P 2 P File Sharing Mobile P 2 PSystems m. Commerce Electronic Goods and Services 48

Context-aware Computing RW • Ambient Services • l-commerece marketplace • Context Mediation • Valuation of context information • my. Campus • • • e. Wallet manages user’s context Personal resources are modeled as semantic web services Context management includes privacy management 49

P 2 P File Sharing RW Mojo Nation $ $ $ Internal currency call Mojo was used to purchasing files from other peers Users could earned Mojo currency through sharing their disk space, processing power, bandwidth … Central bank cleared transactions Karma - Economic Framework for P 2 P Resource Sharing $ $ Internal currency called Karma used a secure exchange mechanism to prevent counterfeiting of Karma currency Framework used anti-inflation deflation mechanism to regulates currency in the system. Framework used peer-to-peer scheme for tracking currency transfers 50

Mobile P 2 P Computing RW • Infostations • • “any time, anywhere” connectivity data hoarding in mobile environments • Proem – Wearable Computing • • • Wearable communities Augmenting face to face interactions personal “digital sphere” • Mogatu - Serendipitous Query Routing and Processing • • Personal user profiles Caching and replication algorithms 51

m. Commerece RW • Easi. Shop • • • Cross merchant product comparison shopping Shopping mobile agent Market Place is a meeting point of shopping and retailer agents • i. Clouds • • • Mobile Advertising Anonymous bonus points i. Have and i. Want List 52

Summary Semi Automated Bartering of Digital Goods and Services in Pervasive Environments 53

Q&A Thank You. 54

Backup Slides 55
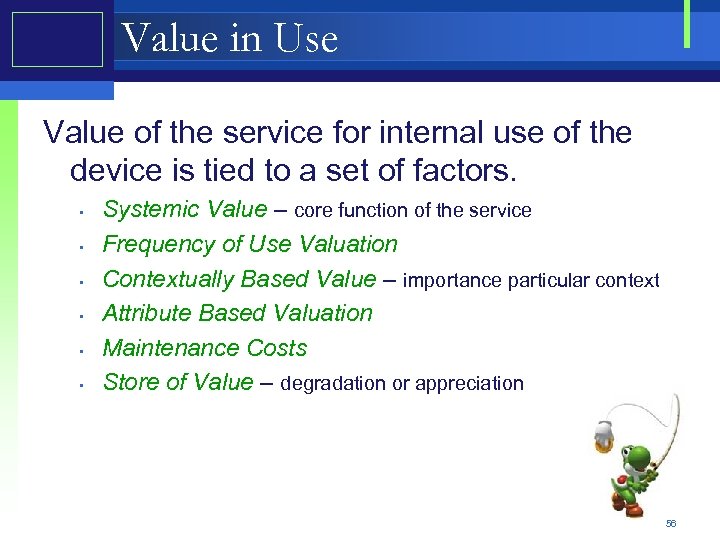
Value in Use Value of the service for internal use of the device is tied to a set of factors. • • • Systemic Value – core function of the service Frequency of Use Valuation Contextually Based Value – importance particular context Attribute Based Valuation Maintenance Costs Store of Value – degradation or appreciation 56

Value in Exchange Service value in exchange is mainly related to the environmental factors. • • • Liquidity - simplicity and similar value during exchange Transaction Costs Service Maintenance Costs Store of Value Composability 57
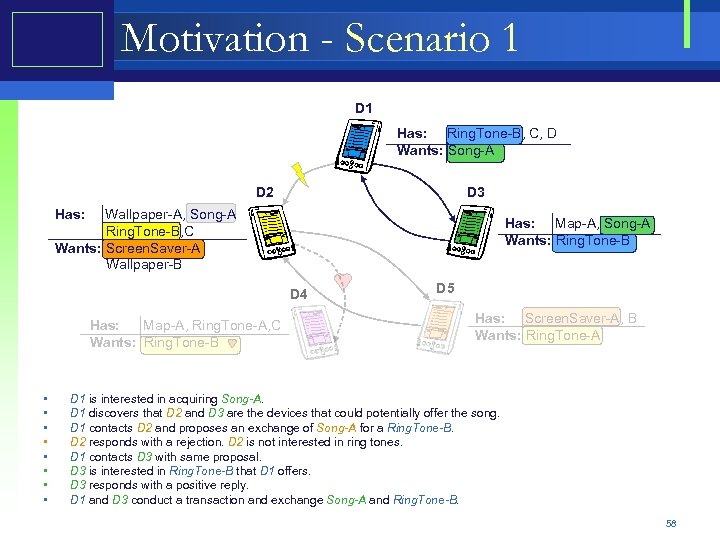
Motivation - Scenario 1 D 1 Has: Ring. Tone-B, C, D Wants: Song-A D 2 D 3 Has: Wallpaper-A, Song-A Ring. Tone-B, C Wants: Screen. Saver-A Wallpaper-B Has: Map-A, Song-A Wants: Ring. Tone-B D 4 Has: Map-A, Ring. Tone-A, C Wants: Ring. Tone-B • • D 5 Has: Screen. Saver-A, B Wants: Ring. Tone-A D 1 is interested in acquiring Song-A. D 1 discovers that D 2 and D 3 are the devices that could potentially offer the song. D 1 contacts D 2 and proposes an exchange of Song-A for a Ring. Tone-B. D 2 responds with a rejection. D 2 is not interested in ring tones. D 1 contacts D 3 with same proposal. D 3 is interested in Ring. Tone-B that D 1 offers. D 3 responds with a positive reply. D 1 and D 3 conduct a transaction and exchange Song-A and Ring. Tone-B. 58
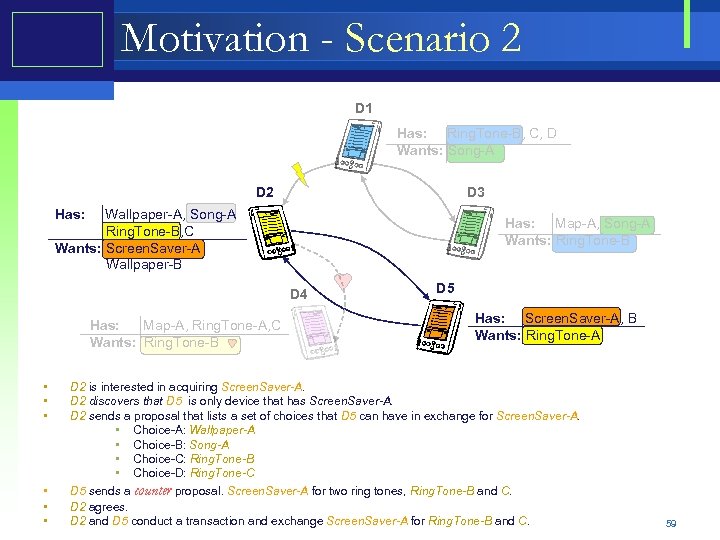
Motivation - Scenario 2 D 1 Has: Ring. Tone-B, C, D Wants: Song-A D 2 D 3 Has: Wallpaper-A, Song-A Ring. Tone-B, C Wants: Screen. Saver-A Wallpaper-B Has: Map-A, Song-A Wants: Ring. Tone-B D 4 Has: Map-A, Ring. Tone-A, C Wants: Ring. Tone-B • • • D 5 Has: Screen. Saver-A, B Wants: Ring. Tone-A D 2 is interested in acquiring Screen. Saver-A. D 2 discovers that D 5 is only device that has Screen. Saver-A. D 2 sends a proposal that lists a set of choices that D 5 can have in exchange for Screen. Saver-A. • Choice-A: Wallpaper-A • Choice-B: Song-A • Choice-C: Ring. Tone-B • Choice-D: Ring. Tone-C D 5 sends a counter proposal. Screen. Saver-A for two ring tones, Ring. Tone-B and C. D 2 agrees. D 2 and D 5 conduct a transaction and exchange Screen. Saver-A for Ring. Tone-B and C. 59
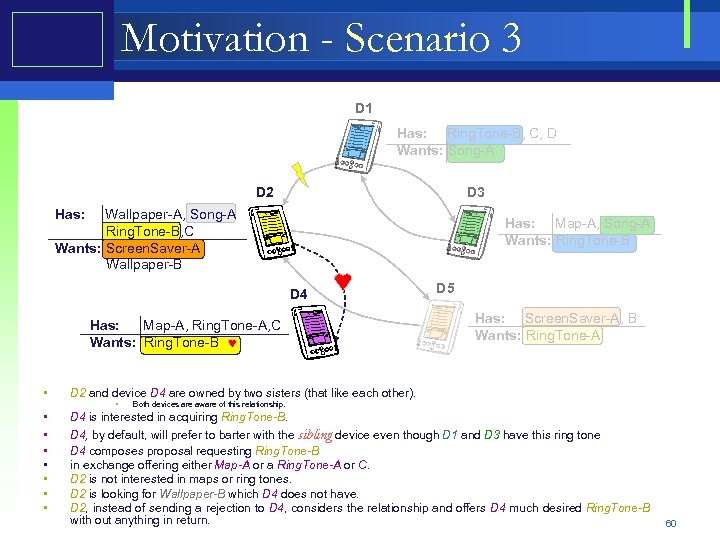
Motivation - Scenario 3 D 1 Has: Ring. Tone-B, C, D Wants: Song-A D 2 D 3 Has: Wallpaper-A, Song-A Ring. Tone-B, C Wants: Screen. Saver-A Wallpaper-B Has: Map-A, Song-A Wants: Ring. Tone-B D 4 Has: Map-A, Ring. Tone-A, C Wants: Ring. Tone-B • • D 5 Has: Screen. Saver-A, B Wants: Ring. Tone-A D 2 and device D 4 are owned by two sisters (that like each other). • Both devices are aware of this relationship. D 4 is interested in acquiring Ring. Tone-B. D 4, by default, will prefer to barter with the sibling device even though D 1 and D 3 have this ring tone D 4 composes proposal requesting Ring. Tone-B in exchange offering either Map-A or a Ring. Tone-A or C. D 2 is not interested in maps or ring tones. D 2 is looking for Wallpaper-B which D 4 does not have. D 2, instead of sending a rejection to D 4, considers the relationship and offers D 4 much desired Ring. Tone-B with out anything in return. 60
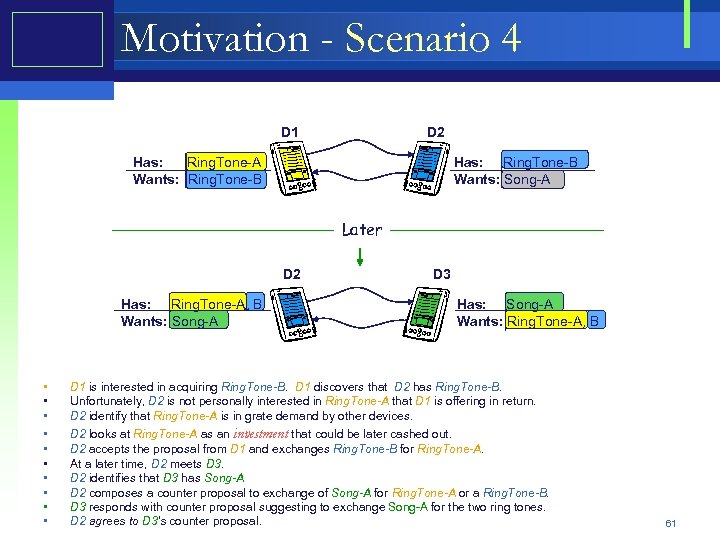
Motivation - Scenario 4 D 1 D 2 Has: Ring. Tone-A Wants: Ring. Tone-B Has: Ring. Tone-B Wants: Song-A Later D 2 Has: Ring. Tone-A, B Wants: Song-A • • • D 3 Has: Song-A Wants: Ring. Tone-A, B D 1 is interested in acquiring Ring. Tone-B. D 1 discovers that D 2 has Ring. Tone-B. Unfortunately, D 2 is not personally interested in Ring. Tone-A that D 1 is offering in return. D 2 identify that Ring. Tone-A is in grate demand by other devices. D 2 looks at Ring. Tone-A as an investment that could be later cashed out. D 2 accepts the proposal from D 1 and exchanges Ring. Tone-B for Ring. Tone-A. At a later time, D 2 meets D 3. D 2 identifies that D 3 has Song-A D 2 composes a counter proposal to exchange of Song-A for Ring. Tone-A or a Ring. Tone-B. D 3 responds with counter proposal suggesting to exchange Song-A for the two ring tones. D 2 agrees to D 3’s counter proposal. 61
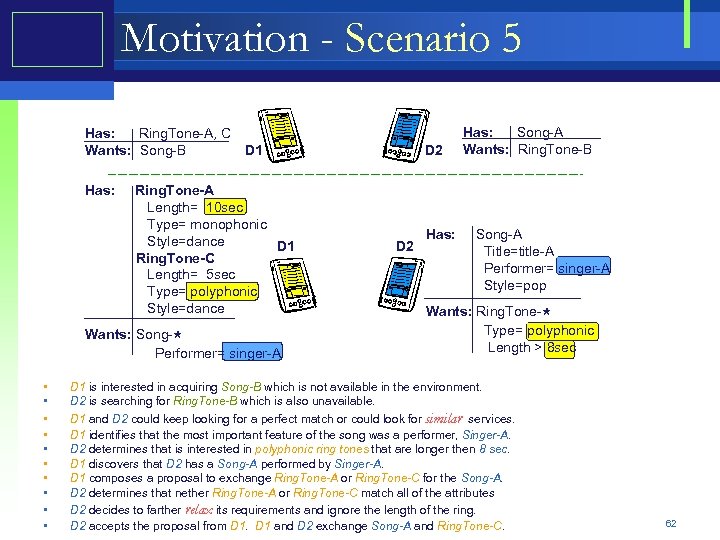
Motivation - Scenario 5 Has: Ring. Tone-A, C D 1 Wants: Song-B Has: Ring. Tone-A Length= 10 sec Type= monophonic Style=dance D 1 Ring. Tone-C Length= 5 sec Type= polyphonic Style=dance Wants: Song Performer= singer-A * • • • D 2 Has: Song-A Wants: Ring. Tone-B Has: Song-A D 2 Title=title-A Performer= singer-A Style=pop Wants: Ring. Tone Type= polyphonic Length > 8 sec D 1 is interested in acquiring Song-B which is not available in the environment. D 2 is searching for Ring. Tone-B which is also unavailable. D 1 and D 2 could keep looking for a perfect match or could look for similar services. D 1 identifies that the most important feature of the song was a performer, Singer-A. D 2 determines that is interested in polyphonic ring tones that are longer then 8 sec. D 1 discovers that D 2 has a Song-A performed by Singer-A. D 1 composes a proposal to exchange Ring. Tone-A or Ring. Tone-C for the Song-A. D 2 determines that nether Ring. Tone-A or Ring. Tone-C match all of the attributes D 2 decides to farther relax its requirements and ignore the length of the ring. D 2 accepts the proposal from D 1 and D 2 exchange Song-A and Ring. Tone-C. * 62
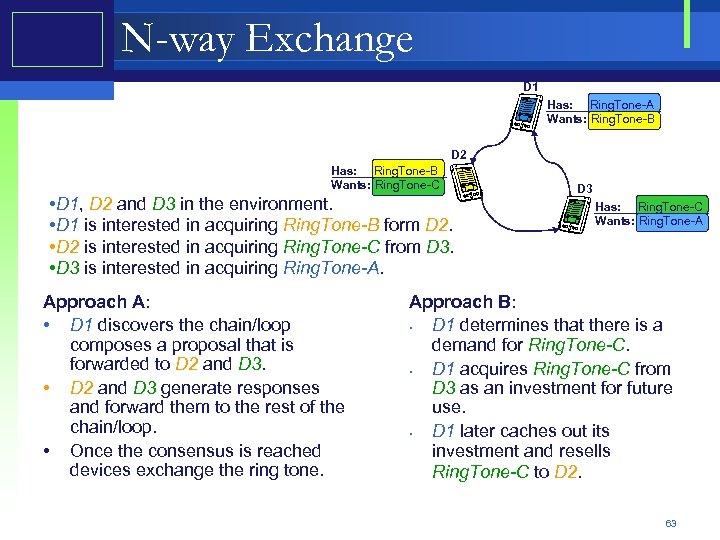
N-way Exchange D 1 Has: Ring. Tone-A Wants: Ring. Tone-B D 2 Has: Ring. Tone-B Wants: Ring. Tone-C • D 1, D 2 and D 3 in the environment. • D 1 is interested in acquiring Ring. Tone-B form D 2. • D 2 is interested in acquiring Ring. Tone-C from D 3. • D 3 is interested in acquiring Ring. Tone-A. Approach A: • D 1 discovers the chain/loop composes a proposal that is forwarded to D 2 and D 3. • D 2 and D 3 generate responses and forward them to the rest of the chain/loop. • Once the consensus is reached devices exchange the ring tone. D 3 Has: Ring. Tone-C Wants: Ring. Tone-A Approach B: • D 1 determines that there is a demand for Ring. Tone-C. • D 1 acquires Ring. Tone-C from D 3 as an investment for future use. • D 1 later caches out its investment and resells Ring. Tone-C to D 2. 63
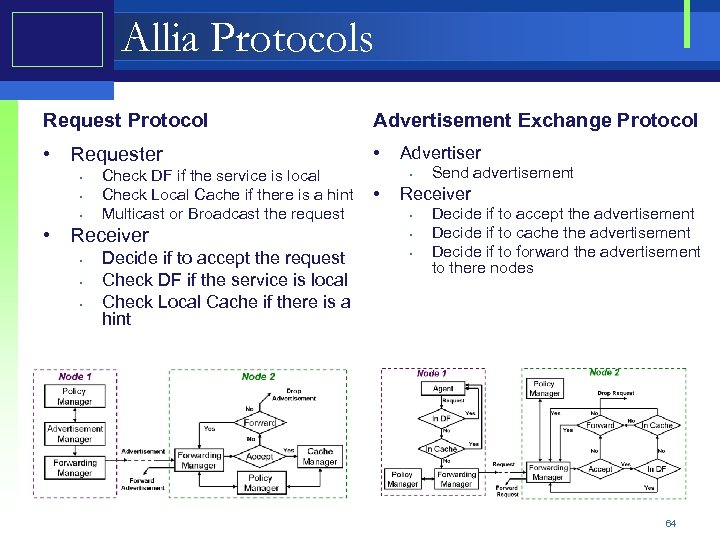
Allia Protocols Request Protocol Advertisement Exchange Protocol • Requester • • Check DF if the service is local Check Local Cache if there is a hint • Multicast or Broadcast the request • Receiver • • • Decide if to accept the request Check DF if the service is local Check Local Cache if there is a hint Advertiser • Send advertisement Receiver • • • Decide if to accept the advertisement Decide if to cache the advertisement Decide if to forward the advertisement to there nodes 64
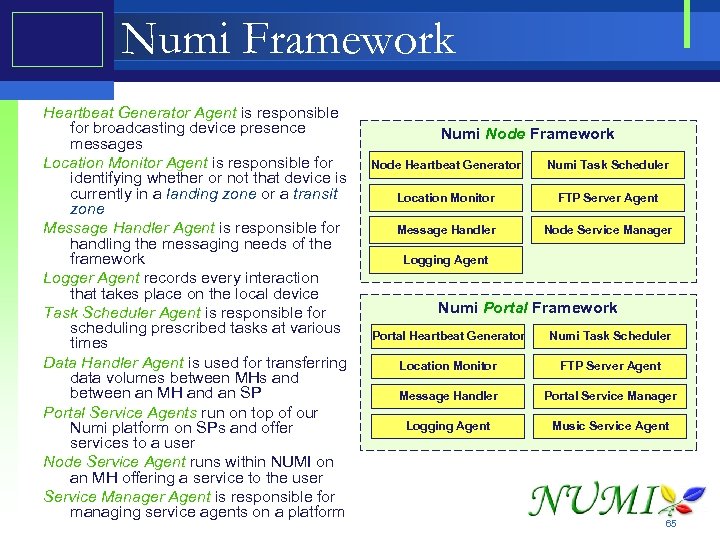
Numi Framework Heartbeat Generator Agent is responsible for broadcasting device presence messages Location Monitor Agent is responsible for identifying whether or not that device is currently in a landing zone or a transit zone Message Handler Agent is responsible for handling the messaging needs of the framework Logger Agent records every interaction that takes place on the local device Task Scheduler Agent is responsible for scheduling prescribed tasks at various times Data Handler Agent is used for transferring data volumes between MHs and between an MH and an SP Portal Service Agents run on top of our Numi platform on SPs and offer services to a user Node Service Agent runs within NUMI on an MH offering a service to the user Service Manager Agent is responsible for managing service agents on a platform Numi Node Framework Node Heartbeat Generator Numi Task Scheduler Location Monitor FTP Server Agent Message Handler Node Service Manager Logging Agent Numi Portal Framework Portal Heartbeat Generator Numi Task Scheduler Location Monitor FTP Server Agent Message Handler Portal Service Manager Logging Agent Music Service Agent 65
Reward Interface 66
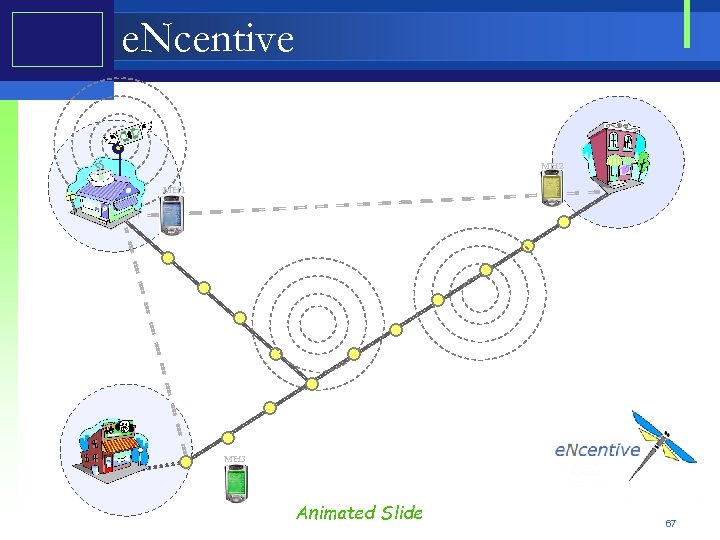
e. Ncentive MH 2 MH 1 MH 3 Animated Slide 67
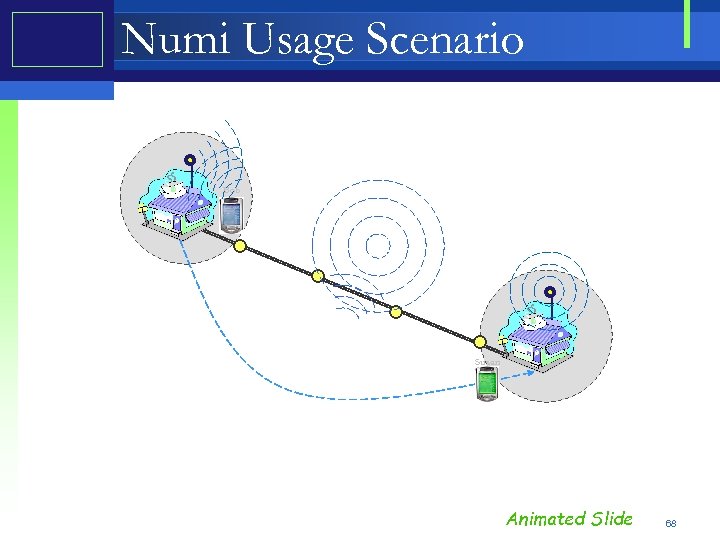
Numi Usage Scenario Bob Susan Animated Slide 68
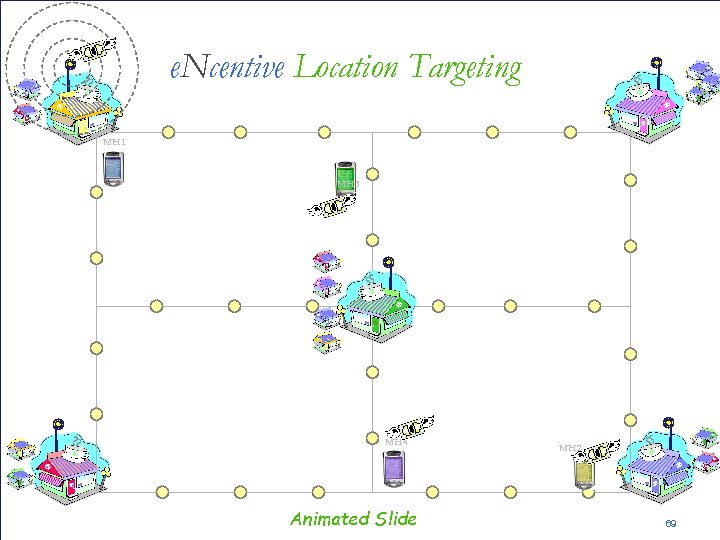
e. Ncentive Location Targeting MH 1 MH 3 MH 4 Animated Slide MH 2 69

70
073bb272eb44b369a0c71c385c9445e8.ppt