934af8879e594ac6adbbfae692c9506a.ppt
- Количество слайдов: 26

Using Instruction Block Signatures to Counter Code Injection Attacks Milena Milenković, Aleksandar Milenković, Emil Jovanov The University of Alabama in Huntsville Email: {milenkm | milenka | jovanov}@ece. uah. edu
st r 2, (r 3) mul r 3, 3 st r 2, (r 3) ld r 1, (r 3) add r 1, r 2 jmp (r 1) Introduction n n Most of today’s computing platforms connected to the Internet security is a critical issue Even more so in the future One of the major security problems: the execution of the unauthorized code Attack examples: n n La. CASA buffer overflow (heap, stack) format string attack WASSA 2004 2

st r 2, (r 3) mul r 3, 3 st r 2, (r 3) ld r 1, (r 3) add r 1, r 2 jmp (r 1) Introduction n n La. CASA Available chip area: predominantly used for faster execution Dedicated processor resources should be used to provide more secure execution Hardware-supported techniques: lower overhead We propose processor extensions that allow execution of trusted instructions only, by verifying instruction block signatures WASSA 2004 3

st r 2, (r 3) mul r 3, 3 st r 2, (r 3) ld r 1, (r 3) add r 1, r 2 jmp (r 1) Overview n n n La. CASA Introduction Related work Processor extensions for trusted instruction execution Preliminary results Conclusion WASSA 2004 4
st r 2, (r 3) mul r 3, 3 st r 2, (r 3) ld r 1, (r 3) add r 1, r 2 jmp (r 1) Related Work n Two categories of defense techniques: n n La. CASA Software-based n Static: detect defects in the code in compile-time n Dynamic: detect/prevent attacks in run-time With hardware support WASSA 2004 5
st r 2, (r 3) mul r 3, 3 st r 2, (r 3) ld r 1, (r 3) add r 1, r 2 jmp (r 1) Related Work n Static software techniques n n n Dynamic software techniques n n n La. CASA Completely automated tools for code analysis n Precise but not scalable n Lightweight but imprecise Programmer-assisted tools Augment the code for run-time attack detection and/or prevention n Compilers, safe language dialects, binary modification Monitoring program behavior n System calls, performance monitoring registers Code and address obfuscation n Randomized virtual addresses, code scrambling WASSA 2004 6
st r 2, (r 3) mul r 3, 3 st r 2, (r 3) ld r 1, (r 3) add r 1, r 2 jmp (r 1) Related Work n n Software-based techniques: performance overhead, false positives/negatives Defense with hardware support n n n La. CASA Xu et al. (2002), Lee at al. (2003), Ozdaganoglu et al. (2003): Secure stack Kirovski et al. (2002): Secure Program Execution Framework (SPEF): code transformed using a secret processor key Suh et al. (2004): Prevent any change in control flow based on data from “spurious” channels WASSA 2004 7

st r 2, (r 3) mul r 3, 3 st r 2, (r 3) ld r 1, (r 3) add r 1, r 2 jmp (r 1) Overview n n n La. CASA Introduction Related work Processor extensions for trusted instruction execution Preliminary results Conclusion WASSA 2004 8
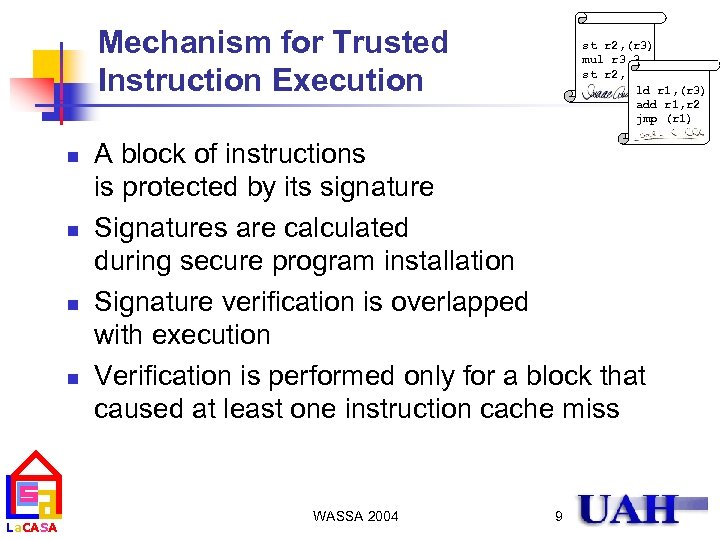
Mechanism for Trusted Instruction Execution n n La. CASA st r 2, (r 3) mul r 3, 3 st r 2, (r 3) ld r 1, (r 3) add r 1, r 2 jmp (r 1) A block of instructions is protected by its signature Signatures are calculated during secure program installation Signature verification is overlapped with execution Verification is performed only for a block that caused at least one instruction cache miss WASSA 2004 9
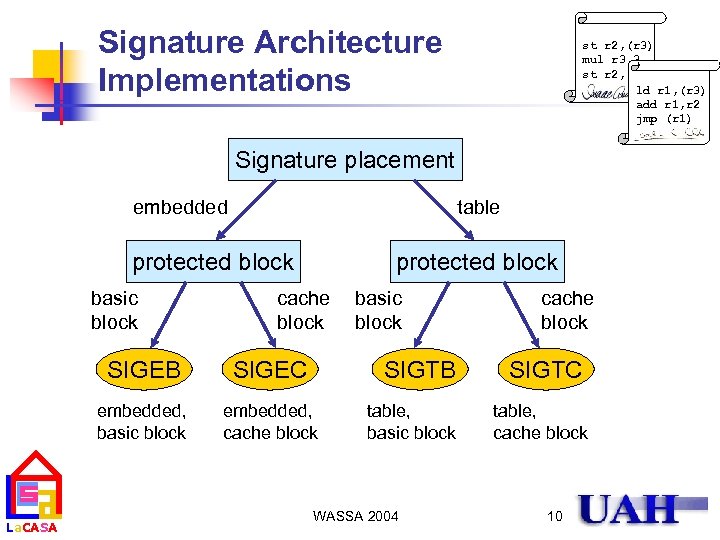
Signature Architecture Implementations st r 2, (r 3) mul r 3, 3 st r 2, (r 3) ld r 1, (r 3) add r 1, r 2 jmp (r 1) Signature placement embedded table protected block basic block protected block cache block SIGEB embedded, basic block La. CASA SIGEC embedded, cache block basic block SIGTB table, basic block WASSA 2004 cache block SIGTC table, cache block 10
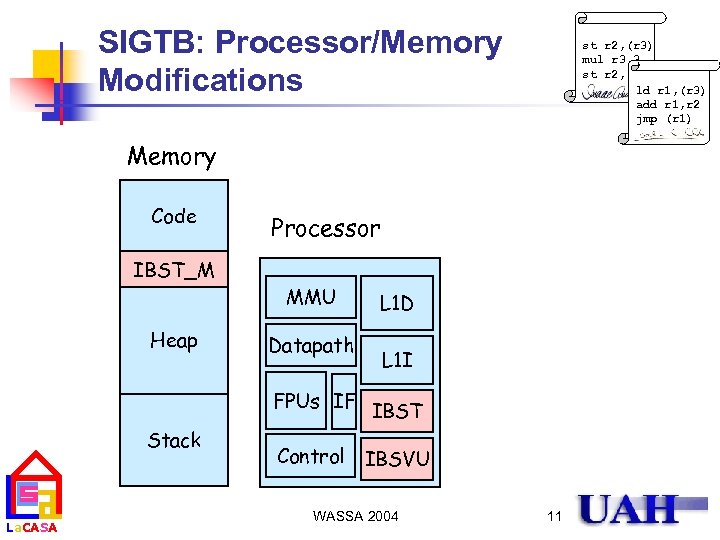
SIGTB: Processor/Memory Modifications st r 2, (r 3) mul r 3, 3 st r 2, (r 3) ld r 1, (r 3) add r 1, r 2 jmp (r 1) Memory Code IBST_M Heap Processor MMU Datapath L 1 D L 1 I FPUs IF IBST Stack La. CASA Control IBSVU WASSA 2004 11
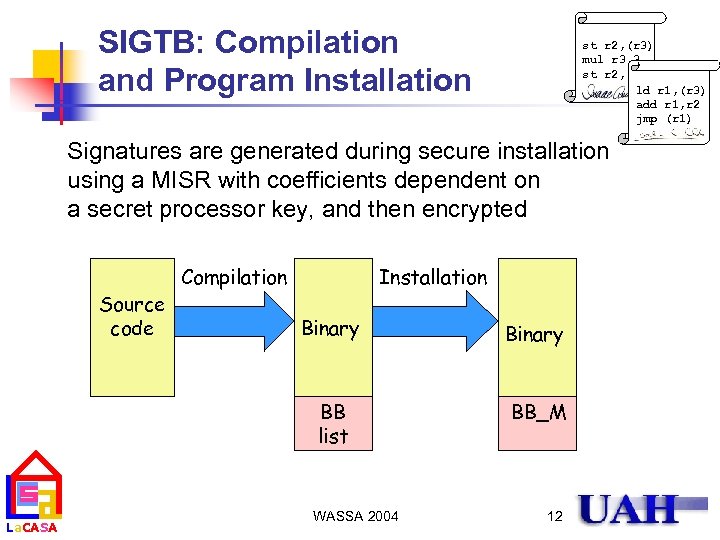
SIGTB: Compilation and Program Installation st r 2, (r 3) mul r 3, 3 st r 2, (r 3) ld r 1, (r 3) add r 1, r 2 jmp (r 1) Signatures are generated during secure installation using a MISR with coefficients dependent on a secret processor key, and then encrypted Source code Compilation Installation Binary BB list La. CASA Binary BB_M WASSA 2004 12
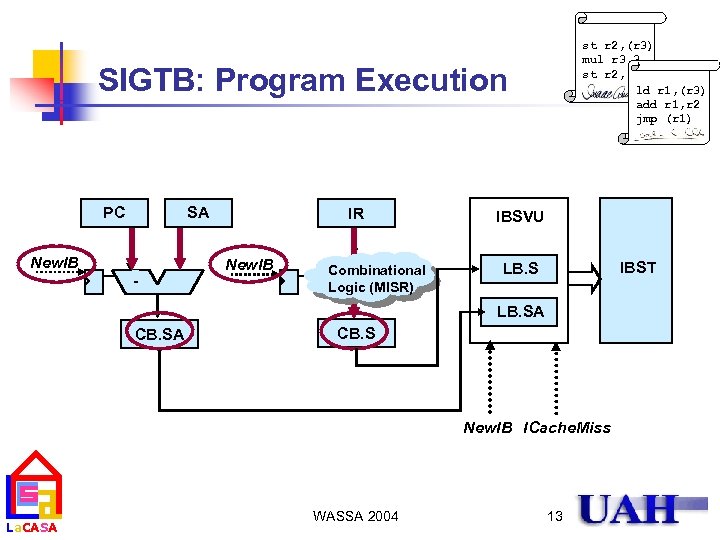
st r 2, (r 3) mul r 3, 3 st r 2, (r 3) ld r 1, (r 3) add r 1, r 2 jmp (r 1) SIGTB: Program Execution PC SA New. IB - IR New. IB Combinational Logic (MISR) IBSVU IBST LB. SA CB. S New. IB ICache. Miss La. CASA WASSA 2004 13
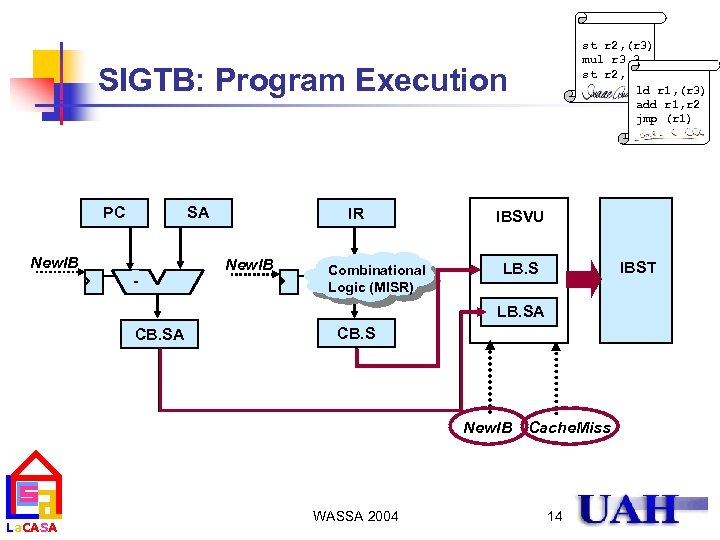
st r 2, (r 3) mul r 3, 3 st r 2, (r 3) ld r 1, (r 3) add r 1, r 2 jmp (r 1) SIGTB: Program Execution PC SA New. IB - IR New. IB Combinational Logic (MISR) IBSVU IBST LB. SA CB. S New. IB ICache. Miss La. CASA WASSA 2004 14
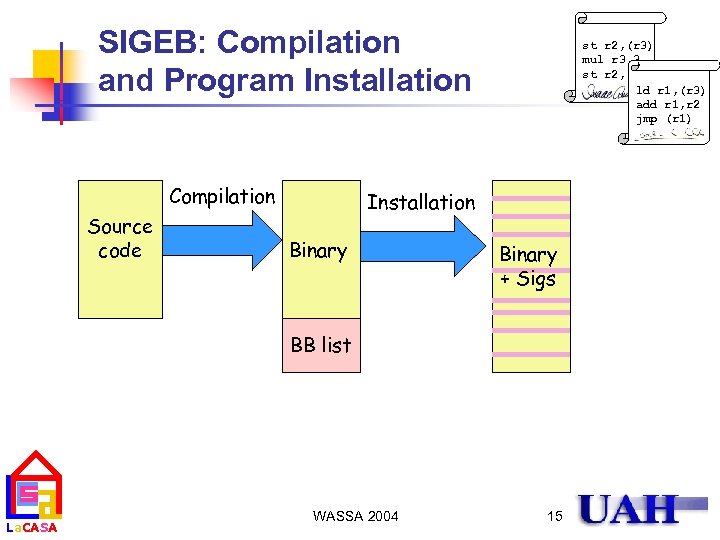
SIGEB: Compilation and Program Installation Compilation Source code st r 2, (r 3) mul r 3, 3 st r 2, (r 3) ld r 1, (r 3) add r 1, r 2 jmp (r 1) Installation Binary + Sigs BB list La. CASA WASSA 2004 15
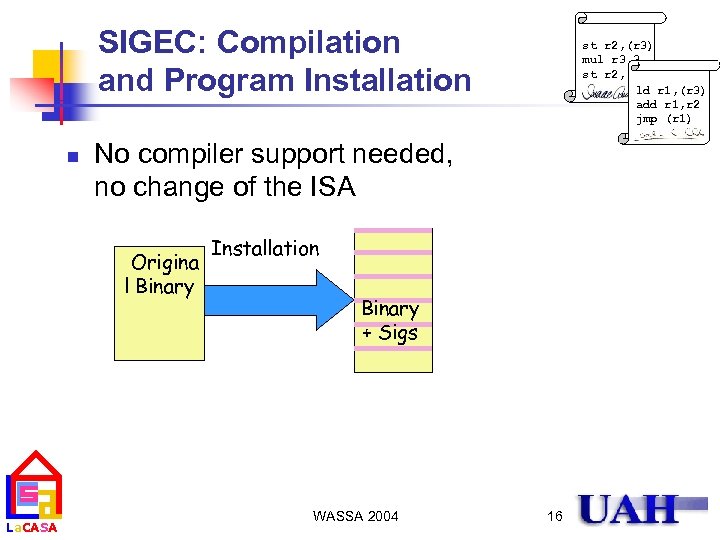
SIGEC: Compilation and Program Installation n No compiler support needed, no change of the ISA Origina l Binary La. CASA st r 2, (r 3) mul r 3, 3 st r 2, (r 3) ld r 1, (r 3) add r 1, r 2 jmp (r 1) Installation Binary + Sigs WASSA 2004 16
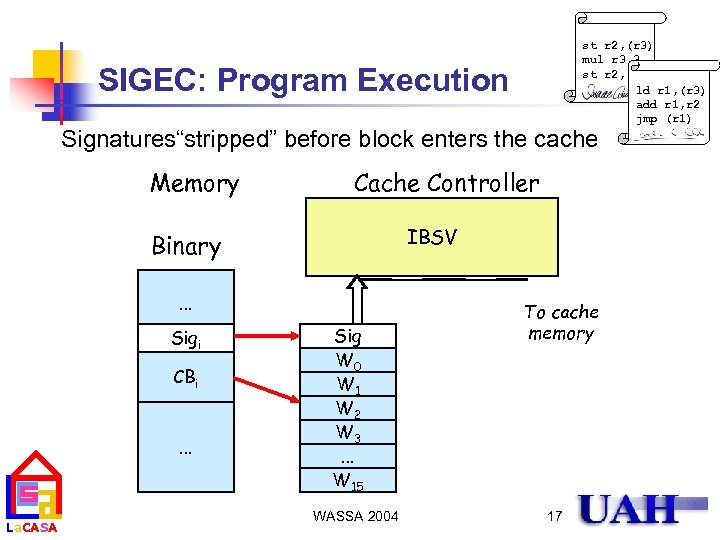
st r 2, (r 3) mul r 3, 3 st r 2, (r 3) ld r 1, (r 3) add r 1, r 2 jmp (r 1) SIGEC: Program Execution Signatures“stripped” before block enters the cache Memory Cache Controller IBSV Binary. . . Sigi CBi. . . La. CASA Sig W 0 W 1 W 2 W 3. . . W 15 WASSA 2004 To cache memory 17

st r 2, (r 3) mul r 3, 3 st r 2, (r 3) ld r 1, (r 3) add r 1, r 2 jmp (r 1) Overview n n n La. CASA Introduction Related work Processor extensions for trusted instruction execution Preliminary results Conclusion WASSA 2004 18
Preliminary Results: Methodology n n n SPEC CPU 2000 benchmarks SIGTB, SIGEB: functional trace-driven simulator SIGEC: modified Simple. Scalar sim-outorder n n La. CASA st r 2, (r 3) mul r 3, 3 st r 2, (r 3) ld r 1, (r 3) add r 1, r 2 jmp (r 1) latency due to additional memory accesses latency due to TLB misses L 1 cache: 32 K, 64 B line, 4 way, LRU Code expansion effects – not included WASSA 2004 19
Preliminary Results: Measures n SIGTB: Number of IBST misses n n La. CASA IBST miss causes additional memory accesses SIGEB: Number of cache misses n n st r 2, (r 3) mul r 3, 3 st r 2, (r 3) ld r 1, (r 3) add r 1, r 2 jmp (r 1) Signatures are fetched into cache with instructions SIGEC: IPC WASSA 2004 20
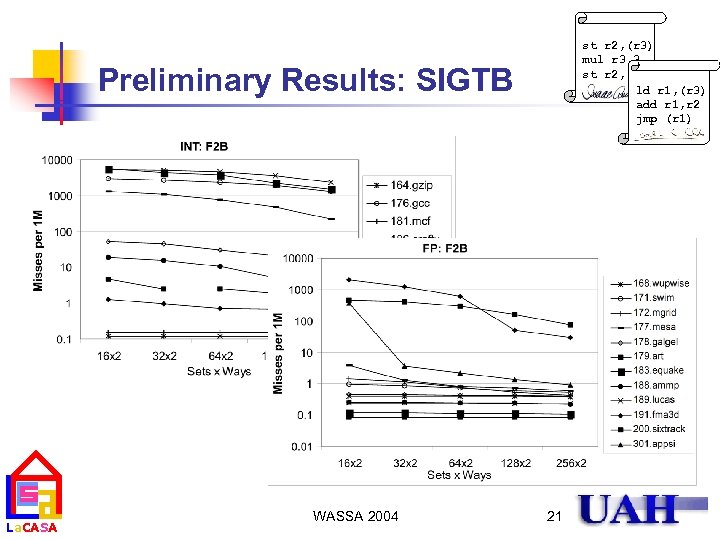
st r 2, (r 3) mul r 3, 3 st r 2, (r 3) ld r 1, (r 3) add r 1, r 2 jmp (r 1) Preliminary Results: SIGTB La. CASA WASSA 2004 21
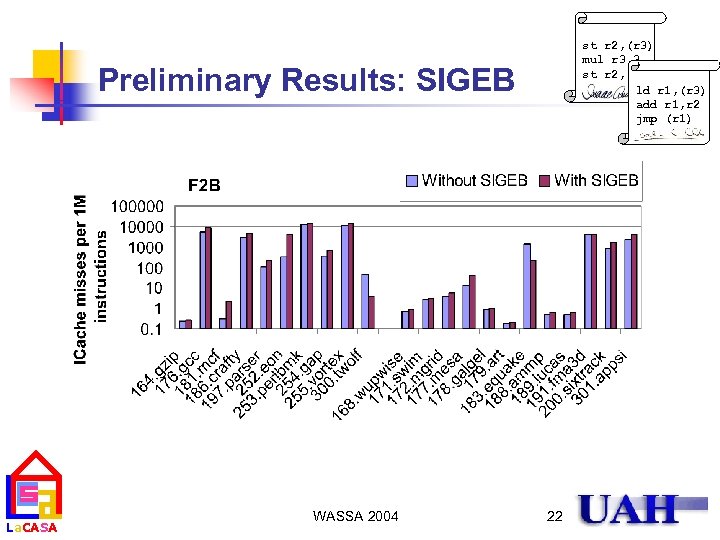
st r 2, (r 3) mul r 3, 3 st r 2, (r 3) ld r 1, (r 3) add r 1, r 2 jmp (r 1) Preliminary Results: SIGEB La. CASA WASSA 2004 22
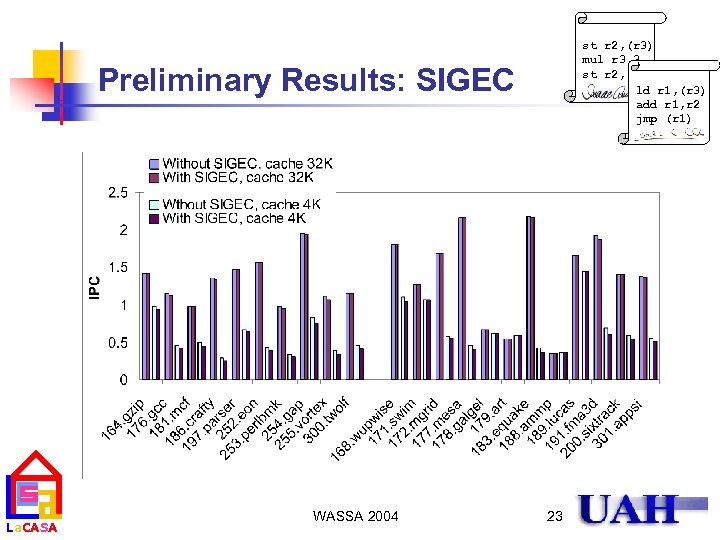
st r 2, (r 3) mul r 3, 3 st r 2, (r 3) ld r 1, (r 3) add r 1, r 2 jmp (r 1) Preliminary Results: SIGEC La. CASA WASSA 2004 23
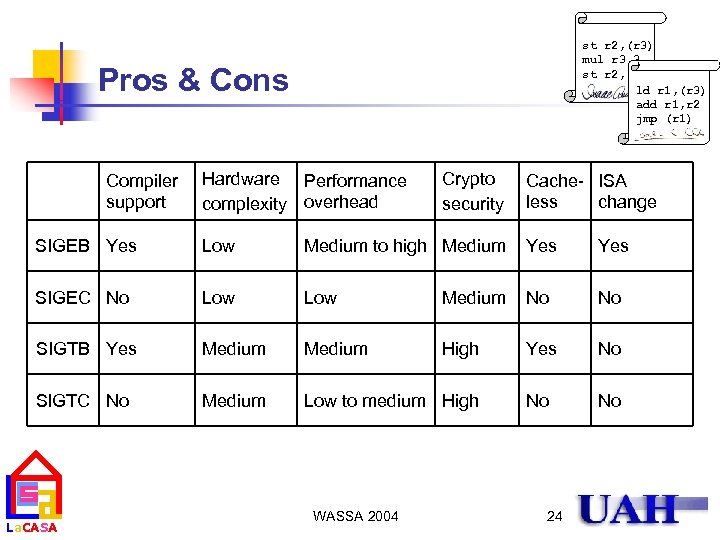
st r 2, (r 3) mul r 3, 3 st r 2, (r 3) ld r 1, (r 3) add r 1, r 2 jmp (r 1) Pros & Cons Compiler support Hardware Performance complexity overhead Crypto security Cache- ISA less change SIGEB Yes Low Medium to high Medium Yes SIGEC No Low Medium No No SIGTB Yes Medium High Yes No SIGTC No Medium Low to medium High No No La. CASA WASSA 2004 24

st r 2, (r 3) mul r 3, 3 st r 2, (r 3) ld r 1, (r 3) add r 1, r 2 jmp (r 1) Overview n n n La. CASA Introduction Related work Processor extensions for trusted instruction execution Preliminary results Conclusion WASSA 2004 25
st r 2, (r 3) mul r 3, 3 st r 2, (r 3) ld r 1, (r 3) add r 1, r 2 jmp (r 1) Conclusion n Contributions: n n Future work n n n La. CASA Proposal of an architecture for trusted program execution Three implementations of the proposed extensions Initial performance evaluation: promising Cycle-by-cycle detailed simulation The effects of signature decryption and context switching Power analysis WASSA 2004 26
934af8879e594ac6adbbfae692c9506a.ppt