5957c9dc133a0b0962ea7eb298bde081.ppt
- Количество слайдов: 76
 Using Complementary Research Designs: The Example of Effects of Social Embeddedness on Trust and Cooperation Werner Raub Workshop on Social Theory, Trust, Social Networks, and Social Capital II National Chengchi University – NCCU April 2011
Using Complementary Research Designs: The Example of Effects of Social Embeddedness on Trust and Cooperation Werner Raub Workshop on Social Theory, Trust, Social Networks, and Social Capital II National Chengchi University – NCCU April 2011
 Overview 1. Theory • Trust problems in economic exchange • Embeddedness effects on trust 2. Empirical evidence from studies using different and complementary research designs • A survey on buyer-supplier relations • A vignette study on buyer-supplier relations 1
Overview 1. Theory • Trust problems in economic exchange • Embeddedness effects on trust 2. Empirical evidence from studies using different and complementary research designs • A survey on buyer-supplier relations • A vignette study on buyer-supplier relations 1
 Background: a rational choice perspective on embeddedness effects “… while the assumption of rational action must always be problematic, it is a good working hypothesis that should not easily be abandoned. What looks to the analyst like nonrational behavior may be quite sensible when situational constraints, especially those of embeddedness, are fully appreciated […] My claim here is that however naive that psychology [of rational choice] may be, this is not where the main difficulty lies – it is rather in the neglect of social structure. ” Mark Granovetter (1985) Economic Action and Social Structure: The Problem of Embeddedness 2
Background: a rational choice perspective on embeddedness effects “… while the assumption of rational action must always be problematic, it is a good working hypothesis that should not easily be abandoned. What looks to the analyst like nonrational behavior may be quite sensible when situational constraints, especially those of embeddedness, are fully appreciated […] My claim here is that however naive that psychology [of rational choice] may be, this is not where the main difficulty lies – it is rather in the neglect of social structure. ” Mark Granovetter (1985) Economic Action and Social Structure: The Problem of Embeddedness 2
 Empirical evidence on embeddedness effects from complementary research designs • Aim: use complementary research designs (survey, vignette study, lab experiment) for multiple tests of the same hypotheses (cf. : triangulation, cross validation) • Similar perspective: • Sociology: J. H. Goldthorpe (1996) The Quantitative Analysis of Large-scale Data Sets and Rational Action Theory: For a Sociological Alliance, ESR 12 • Economics: G. W. Harrison & J. L. List (2004) Field Experiments, JEL 42(4) 3
Empirical evidence on embeddedness effects from complementary research designs • Aim: use complementary research designs (survey, vignette study, lab experiment) for multiple tests of the same hypotheses (cf. : triangulation, cross validation) • Similar perspective: • Sociology: J. H. Goldthorpe (1996) The Quantitative Analysis of Large-scale Data Sets and Rational Action Theory: For a Sociological Alliance, ESR 12 • Economics: G. W. Harrison & J. L. List (2004) Field Experiments, JEL 42(4) 3
 Bringing rational choice models and empirical research closer together 4
Bringing rational choice models and empirical research closer together 4
 Some theory 5
Some theory 5
 6
6
 Fritz Stern, Gold and Iron: Bismarck, Bleichröder, and the Building of the German Empire – 1 “In the private banking world of those days, personal ties were of the greatest importance. Common ventures depended on mutual trust, and that trust had to be established by direct personal knowledge. ” (p. 9) 7
Fritz Stern, Gold and Iron: Bismarck, Bleichröder, and the Building of the German Empire – 1 “In the private banking world of those days, personal ties were of the greatest importance. Common ventures depended on mutual trust, and that trust had to be established by direct personal knowledge. ” (p. 9) 7
 Fritz Stern, Gold and Iron: Bismarck, Bleichröder, and the Building of the German Empire – 2 “In Bismarck’s world, then, Bleichröder was a welcome supplement to official channels (…) Bismarck used him freely and continuously as a special emissary, as an additional and informal link to foreign powers and statesmen. Statesmen always like to have a multiplicity of contacts – to solicit reactions, to convey hints, to reinforce threats or allay fears. ” (p. 311) 8
Fritz Stern, Gold and Iron: Bismarck, Bleichröder, and the Building of the German Empire – 2 “In Bismarck’s world, then, Bleichröder was a welcome supplement to official channels (…) Bismarck used him freely and continuously as a special emissary, as an additional and informal link to foreign powers and statesmen. Statesmen always like to have a multiplicity of contacts – to solicit reactions, to convey hints, to reinforce threats or allay fears. ” (p. 311) 8
 Trust Game as a stylized model of exchange Trustor (buyer) Trust No trust Trustee (supplier) Abuse Honor S 1 < P 1 < R 1 P 2 < R 2 < T 2 9
Trust Game as a stylized model of exchange Trustor (buyer) Trust No trust Trustee (supplier) Abuse Honor S 1 < P 1 < R 1 P 2 < R 2 < T 2 9
 Substantive interpretation of the Trust Game for buyer-supplier relations Moves of the trustor (buyer) • No trust: safeguard transaction with an extensive but costly contract • Trust: use less extensive and less costly contractual safeguards Moves of the trustee (supplier) • Honor trust: deliver appropriate quality and deliver in due time • Abuse trust: deliver inferior quality and/or deliver with a delay 10
Substantive interpretation of the Trust Game for buyer-supplier relations Moves of the trustor (buyer) • No trust: safeguard transaction with an extensive but costly contract • Trust: use less extensive and less costly contractual safeguards Moves of the trustee (supplier) • Honor trust: deliver appropriate quality and deliver in due time • Abuse trust: deliver inferior quality and/or deliver with a delay 10
 Extensions of the Trust Game • More than only two moves for trustor and trustee (e. g. , Investment Game) • Incomplete information of the trustor on incentives or opportunities of trustee for abusing trust • Ex post-problems due to incompetence of trustee or unfavorable external contingencies rather than abuse of trust (opportunism) • Incentives and opportunities for “defection” of trustor (e. g. , delayed payment) • Etc. 11
Extensions of the Trust Game • More than only two moves for trustor and trustee (e. g. , Investment Game) • Incomplete information of the trustor on incentives or opportunities of trustee for abusing trust • Ex post-problems due to incompetence of trustee or unfavorable external contingencies rather than abuse of trust (opportunism) • Incentives and opportunities for “defection” of trustor (e. g. , delayed payment) • Etc. 11
 Relation with Stern’s historical study on Bismarck and his banker Bleichröder • Stern claims that interactions between private bankers involve trust problems. • Stern likewise claims that interactions between states and between politicians involve trust problems.
Relation with Stern’s historical study on Bismarck and his banker Bleichröder • Stern claims that interactions between private bankers involve trust problems. • Stern likewise claims that interactions between states and between politicians involve trust problems.
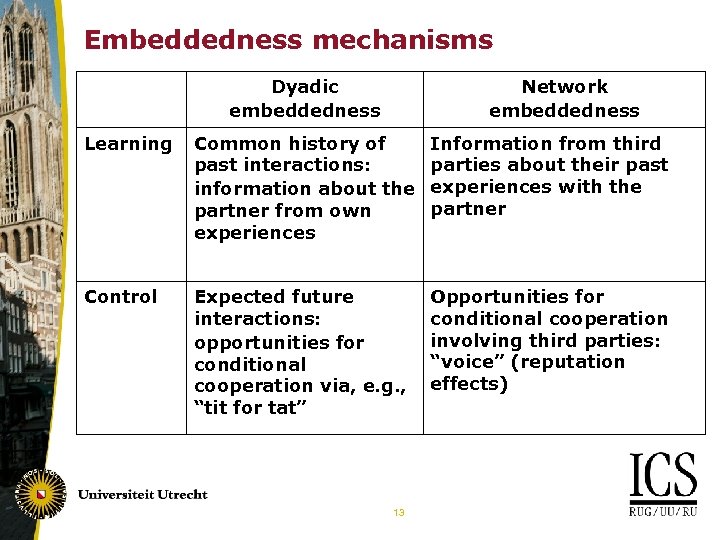 Embeddedness mechanisms Dyadic embeddedness Network embeddedness Learning Common history of past interactions: information about the partner from own experiences Information from third parties about their past experiences with the partner Control Expected future interactions: opportunities for conditional cooperation via, e. g. , “tit for tat” Opportunities for conditional cooperation involving third parties: “voice” (reputation effects) 13
Embeddedness mechanisms Dyadic embeddedness Network embeddedness Learning Common history of past interactions: information about the partner from own experiences Information from third parties about their past experiences with the partner Control Expected future interactions: opportunities for conditional cooperation via, e. g. , “tit for tat” Opportunities for conditional cooperation involving third parties: “voice” (reputation effects) 13
 Research problem • Distinguish between different embeddedness effects • theoretically • empirically • We neglect: • strategic network formation: embeddedness is assumed to be exogenous • “non-selfish utility”: focus on trust as a result of “enlightened self-interest” 14
Research problem • Distinguish between different embeddedness effects • theoretically • empirically • We neglect: • strategic network formation: embeddedness is assumed to be exogenous • “non-selfish utility”: focus on trust as a result of “enlightened self-interest” 14
 Fritz Stern, Gold and Iron: Bismarck, Bleichröder, and the Building of the German Empire – 1 Trust and Embeddedness “In the private banking world of those days, personal ties were of the greatest importance. Common ventures depended on mutual trust, and that trust had to be established by direct personal knowledge. ” (p. 9) Note Stern’s claim: dyadic embeddedness affects trust. 15
Fritz Stern, Gold and Iron: Bismarck, Bleichröder, and the Building of the German Empire – 1 Trust and Embeddedness “In the private banking world of those days, personal ties were of the greatest importance. Common ventures depended on mutual trust, and that trust had to be established by direct personal knowledge. ” (p. 9) Note Stern’s claim: dyadic embeddedness affects trust. 15
 Fritz Stern, Gold and Iron: Bismarck, Bleichröder, and the Building of the German Empire – 2 Trust and Embeddedness “In Bismarck’s world, then, Bleichröder was a welcome supplement to official channels (…) Bismarck used him freely and continuously as a special emissary, as an additional and informal link to foreign powers and statesmen. Statesmen always like to have a multiplicity of contacts – to solicit reactions, to convey hints, to reinforce threats or allay fears. ” (p. 311) Note Stern’s claim: Network embeddedness allows for learning and control (informal reciprocity). 16
Fritz Stern, Gold and Iron: Bismarck, Bleichröder, and the Building of the German Empire – 2 Trust and Embeddedness “In Bismarck’s world, then, Bleichröder was a welcome supplement to official channels (…) Bismarck used him freely and continuously as a special emissary, as an additional and informal link to foreign powers and statesmen. Statesmen always like to have a multiplicity of contacts – to solicit reactions, to convey hints, to reinforce threats or allay fears. ” (p. 311) Note Stern’s claim: Network embeddedness allows for learning and control (informal reciprocity). 16
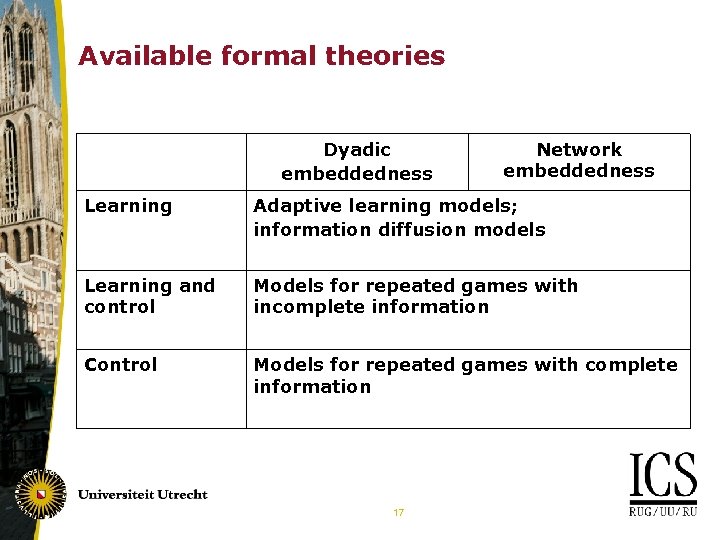 Available formal theories Dyadic embeddedness Network embeddedness Learning Adaptive learning models; information diffusion models Learning and control Models for repeated games with incomplete information Control Models for repeated games with complete information 17
Available formal theories Dyadic embeddedness Network embeddedness Learning Adaptive learning models; information diffusion models Learning and control Models for repeated games with incomplete information Control Models for repeated games with complete information 17
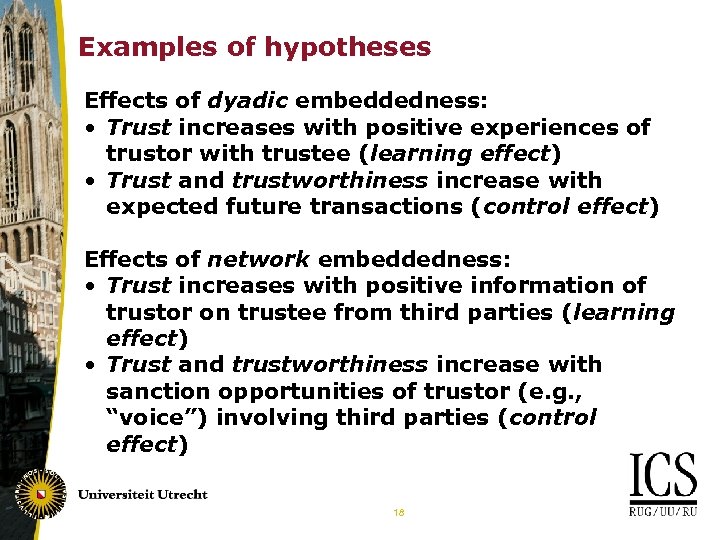 Examples of hypotheses Effects of dyadic embeddedness: • Trust increases with positive experiences of trustor with trustee (learning effect) • Trust and trustworthiness increase with expected future transactions (control effect) Effects of network embeddedness: • Trust increases with positive information of trustor on trustee from third parties (learning effect) • Trust and trustworthiness increase with sanction opportunities of trustor (e. g. , “voice”) involving third parties (control effect) 18
Examples of hypotheses Effects of dyadic embeddedness: • Trust increases with positive experiences of trustor with trustee (learning effect) • Trust and trustworthiness increase with expected future transactions (control effect) Effects of network embeddedness: • Trust increases with positive information of trustor on trustee from third parties (learning effect) • Trust and trustworthiness increase with sanction opportunities of trustor (e. g. , “voice”) involving third parties (control effect) 18
 Empirical evidence 19
Empirical evidence 19
 Evidence from a survey, a lab experiment, and a vignette study Advantages Disadvantages Survey Actual interactions Measurement problems; less control over variables Lab experiment Control over incentives and embeddedness variables Abstract; external validity Vignette study Less abstract than lab experiments; control over variables Hypothetical interactions; lack of “incentive compatibility” 20
Evidence from a survey, a lab experiment, and a vignette study Advantages Disadvantages Survey Actual interactions Measurement problems; less control over variables Lab experiment Control over incentives and embeddedness variables Abstract; external validity Vignette study Less abstract than lab experiments; control over variables Hypothetical interactions; lack of “incentive compatibility” 20
 Evidence on effects of dyadic embeddedness: A survey on IT-transactions More information: • Batenburg, Raub & Snijders (2003) Contacts and Contracts: Dyadic Embeddedness and the Contractual Behavior of Firms, Research in the Sociology of Organizations 20: 135188 21
Evidence on effects of dyadic embeddedness: A survey on IT-transactions More information: • Batenburg, Raub & Snijders (2003) Contacts and Contracts: Dyadic Embeddedness and the Contractual Behavior of Firms, Research in the Sociology of Organizations 20: 135188 21
 A survey on IT-transactions Data on the purchase of hard- and software, standard and complex products • ca 1000 transactions (“Trust Games”) • ca 800 buyers (trustors): Dutch SMEs • 600+ suppliers (trustees) • various replications and extensions of the study in the Netherlands and Germany 22
A survey on IT-transactions Data on the purchase of hard- and software, standard and complex products • ca 1000 transactions (“Trust Games”) • ca 800 buyers (trustors): Dutch SMEs • 600+ suppliers (trustees) • various replications and extensions of the study in the Netherlands and Germany 22
 Survey: variables and measurements I • Trust of buyer: “Lack of trust” measured by buyer’s costly INVESTMENTS IN CONTRACTING with supplier (person-days and departments involved, financial and legal clauses and technical specifications included in contract) • Dyadic learning: (positive) experiences of buyer from previous transactions with supplier – PAST • Dyadic control: expectations of buyer on future transactions with supplier – FUTURE 23
Survey: variables and measurements I • Trust of buyer: “Lack of trust” measured by buyer’s costly INVESTMENTS IN CONTRACTING with supplier (person-days and departments involved, financial and legal clauses and technical specifications included in contract) • Dyadic learning: (positive) experiences of buyer from previous transactions with supplier – PAST • Dyadic control: expectations of buyer on future transactions with supplier – FUTURE 23
 Survey: variables and measurements II • Control variables: • Transaction characteristics (e. g. , specific investments, uncertainty, volume) • Marginal costs of contracting • Characteristics of buyer and supplier, including respondent characteristics 24
Survey: variables and measurements II • Control variables: • Transaction characteristics (e. g. , specific investments, uncertainty, volume) • Marginal costs of contracting • Characteristics of buyer and supplier, including respondent characteristics 24
 Investments in contracting: assumptions I • IT transactions are associated with risks • Focus on risks of the buyer (such as delayed delivery, inferior quality etc. ) due to: • opportunistic behavior of supplier • incompetence of supplier • external contingencies • Contracting as a device to mitigate risks: • reduction of incentives for opportunistic behavior of supplier • compensation for buyer if risks “materialize” 25
Investments in contracting: assumptions I • IT transactions are associated with risks • Focus on risks of the buyer (such as delayed delivery, inferior quality etc. ) due to: • opportunistic behavior of supplier • incompetence of supplier • external contingencies • Contracting as a device to mitigate risks: • reduction of incentives for opportunistic behavior of supplier • compensation for buyer if risks “materialize” 25
 Investments in contracting: assumptions II Core assumptions for deriving hypotheses: • Investments in contracting are costly and actors will economize on these costs • Investments in contracting will increase in risks 26
Investments in contracting: assumptions II Core assumptions for deriving hypotheses: • Investments in contracting are costly and actors will economize on these costs • Investments in contracting will increase in risks 26
 Hypotheses on effects of dyadic embeddedness I Effects of a positive past relationship: • Dyadic learning: reduced probability of supplier incompetence • Also: mutual relationship specific investments • Availability of costless safeguards from prior transactions (e. g. , reuse of contract for a prior transaction) • Good working relations between employees of the two firms Decreasing investments in contracting 27
Hypotheses on effects of dyadic embeddedness I Effects of a positive past relationship: • Dyadic learning: reduced probability of supplier incompetence • Also: mutual relationship specific investments • Availability of costless safeguards from prior transactions (e. g. , reuse of contract for a prior transaction) • Good working relations between employees of the two firms Decreasing investments in contracting 27
 Hypotheses on effects of dyadic embeddedness II Two effects of expected future transactions: • Reciprocity effect: conditional cooperation becomes an alternative for costly investments in contracting è Decreasing investments in contracting • Reusability effect: investments in contracting can be (partly) reused for future transactions (e. g. , reuse of adapted version of the contract) Increasing investments in contracting Note: reusability effect larger when contractual safeguards are not yet available, i. e. , larger for transactions without prior business between buyer and supplier 28
Hypotheses on effects of dyadic embeddedness II Two effects of expected future transactions: • Reciprocity effect: conditional cooperation becomes an alternative for costly investments in contracting è Decreasing investments in contracting • Reusability effect: investments in contracting can be (partly) reused for future transactions (e. g. , reuse of adapted version of the contract) Increasing investments in contracting Note: reusability effect larger when contractual safeguards are not yet available, i. e. , larger for transactions without prior business between buyer and supplier 28
 Hypotheses on effects of dyadic embeddedness III Without additional assumptions on strength of reciprocity effect and reusability effect: no hypothesis on main effect of FUTURE on INVESTMENTS IN CONTRACTING è Due to larger reusability effect for transactions without prior business between buyer and supplier: negative interaction effect PAST x FUTURE on INVESTMENTS IN CONTRACTING (dyadic control) 29
Hypotheses on effects of dyadic embeddedness III Without additional assumptions on strength of reciprocity effect and reusability effect: no hypothesis on main effect of FUTURE on INVESTMENTS IN CONTRACTING è Due to larger reusability effect for transactions without prior business between buyer and supplier: negative interaction effect PAST x FUTURE on INVESTMENTS IN CONTRACTING (dyadic control) 29
 Survey: empirical evidence on effects of dyadic embeddedness • Robust result for various statistical models, for alternative operationalizations of variables, and controlling for transaction characteristics, marginal costs of contracting, and characteristics of buyer and supplier: INVESTMENTS IN CONTRACTING decrease with: • PAST: positive past experiences of buyer • PAST x FUTURE: expected future transactions if positive past experiences exist Support for hypotheses on dyadic learning and control effects 30
Survey: empirical evidence on effects of dyadic embeddedness • Robust result for various statistical models, for alternative operationalizations of variables, and controlling for transaction characteristics, marginal costs of contracting, and characteristics of buyer and supplier: INVESTMENTS IN CONTRACTING decrease with: • PAST: positive past experiences of buyer • PAST x FUTURE: expected future transactions if positive past experiences exist Support for hypotheses on dyadic learning and control effects 30
 Evidence on effects of dyadic embeddedness: A vignette study on buyer-supplier relations More information: • Buskens & Raub (2002) Embedded Trust, Advances in Group Processes 19: 167 -202 31
Evidence on effects of dyadic embeddedness: A vignette study on buyer-supplier relations More information: • Buskens & Raub (2002) Embedded Trust, Advances in Group Processes 19: 167 -202 31
 Data: a vignette study on buyersupplier relations • Respondents: 40 purchase managers of Dutch medium-sized and large companies • Judgments on 348 virtual transactions (= vignettes; 8 -10 vignettes per respondent) • Data on • transaction management • transaction characteristics • dyadic embeddedness • network embeddedness • characteristics of purchase managers 32
Data: a vignette study on buyersupplier relations • Respondents: 40 purchase managers of Dutch medium-sized and large companies • Judgments on 348 virtual transactions (= vignettes; 8 -10 vignettes per respondent) • Data on • transaction management • transaction characteristics • dyadic embeddedness • network embeddedness • characteristics of purchase managers 32
 vignette number: xxx The transaction concerns a product: - about which your firm has only very limited expertise. - for which there are no alternative suppliers on the market. a transaction: - with a small volume, namely, less than US$ 5. 000, = on a yearly basis. - where extra investments by your firm are not necessary. a supplier: - from the Netherlands. - from whom your firm knows some business partners, but your firm does not do business with them. - with whom your firm has had a relationship in which minor problems sometimes occurred. - with whom your firm expects to do business for a long period. Example of a vignette 33
vignette number: xxx The transaction concerns a product: - about which your firm has only very limited expertise. - for which there are no alternative suppliers on the market. a transaction: - with a small volume, namely, less than US$ 5. 000, = on a yearly basis. - where extra investments by your firm are not necessary. a supplier: - from the Netherlands. - from whom your firm knows some business partners, but your firm does not do business with them. - with whom your firm has had a relationship in which minor problems sometimes occurred. - with whom your firm expects to do business for a long period. Example of a vignette 33
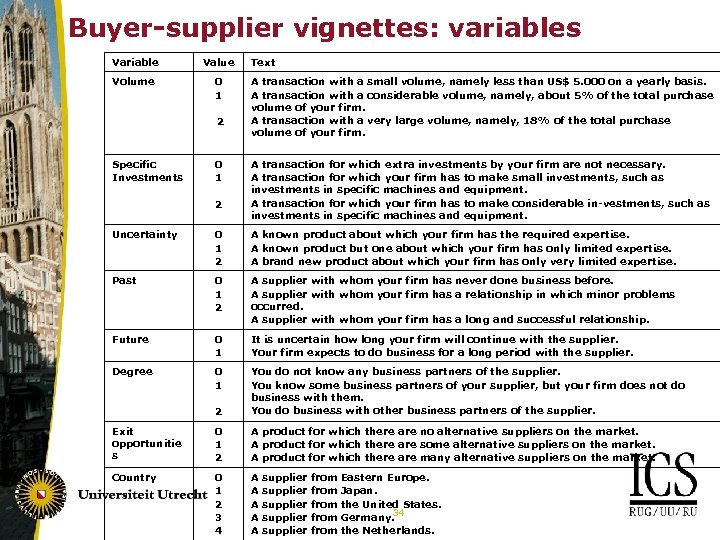 Buyer-supplier vignettes: variables Variable Value Volume 0 1 2 Specific Investments 0 1 2 Text A transaction with a small volume, namely less than US$ 5. 000 on a yearly basis. A transaction with a considerable volume, namely, about 5% of the total purchase volume of your firm. A transaction with a very large volume, namely, 18% of the total purchase volume of your firm. A transaction for which extra investments by your firm are not necessary. A transaction for which your firm has to make small investments, such as investments in specific machines and equipment. A transaction for which your firm has to make considerable in-vestments, such as investments in specific machines and equipment. Uncertainty 0 1 2 A known product about which your firm has the required expertise. A known product but one about which your firm has only limited expertise. A brand new product about which your firm has only very limited expertise. Past 0 1 2 A supplier with whom your firm has never done business before. A supplier with whom your firm has a relationship in which minor problems occurred. A supplier with whom your firm has a long and successful relationship. Future 0 1 It is uncertain how long your firm will continue with the supplier. Your firm expects to do business for a long period with the supplier. Degree 0 1 2 You do not know any business partners of the supplier. You know some business partners of your supplier, but your firm does not do business with them. You do business with other business partners of the supplier. Exit opportunitie s 0 1 2 A product for which there are no alternative suppliers on the market. A product for which there are some alternative suppliers on the market. A product for which there are many alternative suppliers on the market. Country 0 1 2 3 4 A A A supplier supplier from from Eastern Europe. Japan. the United States. 34 Germany. the Netherlands.
Buyer-supplier vignettes: variables Variable Value Volume 0 1 2 Specific Investments 0 1 2 Text A transaction with a small volume, namely less than US$ 5. 000 on a yearly basis. A transaction with a considerable volume, namely, about 5% of the total purchase volume of your firm. A transaction with a very large volume, namely, 18% of the total purchase volume of your firm. A transaction for which extra investments by your firm are not necessary. A transaction for which your firm has to make small investments, such as investments in specific machines and equipment. A transaction for which your firm has to make considerable in-vestments, such as investments in specific machines and equipment. Uncertainty 0 1 2 A known product about which your firm has the required expertise. A known product but one about which your firm has only limited expertise. A brand new product about which your firm has only very limited expertise. Past 0 1 2 A supplier with whom your firm has never done business before. A supplier with whom your firm has a relationship in which minor problems occurred. A supplier with whom your firm has a long and successful relationship. Future 0 1 It is uncertain how long your firm will continue with the supplier. Your firm expects to do business for a long period with the supplier. Degree 0 1 2 You do not know any business partners of the supplier. You know some business partners of your supplier, but your firm does not do business with them. You do business with other business partners of the supplier. Exit opportunitie s 0 1 2 A product for which there are no alternative suppliers on the market. A product for which there are some alternative suppliers on the market. A product for which there are many alternative suppliers on the market. Country 0 1 2 3 4 A A A supplier supplier from from Eastern Europe. Japan. the United States. 34 Germany. the Netherlands.
 Buyer-supplier vignettes: variables and measurements I • Trust of buyer: “Lack of trust” measured for each vignette by buyer’s costly INVESTMENTS IN CONTRACTING with supplier (duration of negotiation with supplier and departments of buyer involved in negotiations) • Dyadic learning: (positive) experiences of buyer from previous transactions with supplier – PAST • Dyadic control: expectations of buyer on future transactions with supplier – FUTURE 35
Buyer-supplier vignettes: variables and measurements I • Trust of buyer: “Lack of trust” measured for each vignette by buyer’s costly INVESTMENTS IN CONTRACTING with supplier (duration of negotiation with supplier and departments of buyer involved in negotiations) • Dyadic learning: (positive) experiences of buyer from previous transactions with supplier – PAST • Dyadic control: expectations of buyer on future transactions with supplier – FUTURE 35
 Buyer-supplier vignettes: variables and measurements II • Control variables: • Transaction characteristics (e. g. , specific investments, uncertainty, volume) • Characteristics of buyer and supplier, including respondent characteristics (e. g. , experience with transactions like described on vignettes) 36
Buyer-supplier vignettes: variables and measurements II • Control variables: • Transaction characteristics (e. g. , specific investments, uncertainty, volume) • Characteristics of buyer and supplier, including respondent characteristics (e. g. , experience with transactions like described on vignettes) 36
 Buyer-supplier vignettes and survey on IT-transactions • Note: Vignette study on buyer-supplier relations and survey on IT-transaction allow to test same hypotheses on effects of dyadic embeddedness with two different but complementary data sets based on different designs 37
Buyer-supplier vignettes and survey on IT-transactions • Note: Vignette study on buyer-supplier relations and survey on IT-transaction allow to test same hypotheses on effects of dyadic embeddedness with two different but complementary data sets based on different designs 37
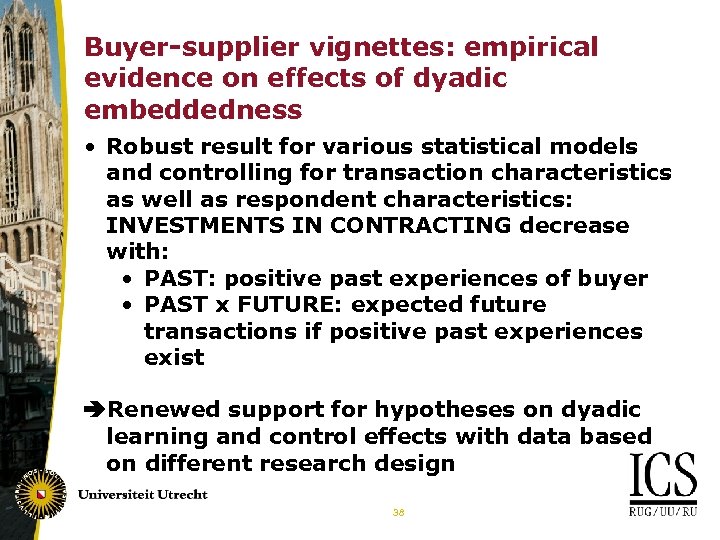 Buyer-supplier vignettes: empirical evidence on effects of dyadic embeddedness • Robust result for various statistical models and controlling for transaction characteristics as well as respondent characteristics: INVESTMENTS IN CONTRACTING decrease with: • PAST: positive past experiences of buyer • PAST x FUTURE: expected future transactions if positive past experiences exist Renewed support for hypotheses on dyadic learning and control effects with data based on different research design 38
Buyer-supplier vignettes: empirical evidence on effects of dyadic embeddedness • Robust result for various statistical models and controlling for transaction characteristics as well as respondent characteristics: INVESTMENTS IN CONTRACTING decrease with: • PAST: positive past experiences of buyer • PAST x FUTURE: expected future transactions if positive past experiences exist Renewed support for hypotheses on dyadic learning and control effects with data based on different research design 38
 Evidence on effects of network embeddedness: survey on IT-transactions More information: • Rooks, Raub & Tazelaar (2006) Ex Post Problems in Buyer-Supplier Transactions, Journal of Management and Governance 10: 239 -276 39
Evidence on effects of network embeddedness: survey on IT-transactions More information: • Rooks, Raub & Tazelaar (2006) Ex Post Problems in Buyer-Supplier Transactions, Journal of Management and Governance 10: 239 -276 39
 Survey: variables and measurements III • Network embeddedness: • DEGREE: ties of buyer with other buyers of supplier • SECTOR DENSITY: contacts among firms in business sector of buyer • VISIBILITY of supplier in the market (as assessed by buyer) • Note: these are indicators for network learning as well as network control opportunities (“voice opportunities”) of buyer 40
Survey: variables and measurements III • Network embeddedness: • DEGREE: ties of buyer with other buyers of supplier • SECTOR DENSITY: contacts among firms in business sector of buyer • VISIBILITY of supplier in the market (as assessed by buyer) • Note: these are indicators for network learning as well as network control opportunities (“voice opportunities”) of buyer 40
 Survey: variables and measurements IV • Trustworthiness of supplier: • PERFORMANCE of supplier, e. g. , delivery in due time, quality of product, quality of aftersales service (Rooks et al. (2006): EX POST PROBLEMS instead of PERFORMANCE) 41
Survey: variables and measurements IV • Trustworthiness of supplier: • PERFORMANCE of supplier, e. g. , delivery in due time, quality of product, quality of aftersales service (Rooks et al. (2006): EX POST PROBLEMS instead of PERFORMANCE) 41
 Survey: empirical evidence on effects of network embeddedness on trustworthiness of supplier • Robust result for various statistical models and controlling for transaction characteristics, buyer’s INVESTMENTS IN CONTRACTING, and characteristics of buyer and supplier: PERFORMANCE of supplier increases (i. e. , EX POST PROBLEMS decrease) with network embeddedness (DEGREE, SECTOR DENSITY, VISIBILITY) Support for hypotheses on network control effects on supplier (trustee) behavior 42
Survey: empirical evidence on effects of network embeddedness on trustworthiness of supplier • Robust result for various statistical models and controlling for transaction characteristics, buyer’s INVESTMENTS IN CONTRACTING, and characteristics of buyer and supplier: PERFORMANCE of supplier increases (i. e. , EX POST PROBLEMS decrease) with network embeddedness (DEGREE, SECTOR DENSITY, VISIBILITY) Support for hypotheses on network control effects on supplier (trustee) behavior 42
 Survey: empirical evidence on effects of network embeddedness on trust of buyer • Robust result for various statistical models, for alternative operationalizations of variables, and controlling for transaction characteristics, marginal costs of contracting, and characteristics of buyer and supplier: network embeddedness (DEGREE, SECTOR DENSITY, VISIBILITY) has no effect on buyer’s INVESTMENTS IN CONTRACTING No support for hypotheses on network learning or control effects on buyer (trustor) behavior 43
Survey: empirical evidence on effects of network embeddedness on trust of buyer • Robust result for various statistical models, for alternative operationalizations of variables, and controlling for transaction characteristics, marginal costs of contracting, and characteristics of buyer and supplier: network embeddedness (DEGREE, SECTOR DENSITY, VISIBILITY) has no effect on buyer’s INVESTMENTS IN CONTRACTING No support for hypotheses on network learning or control effects on buyer (trustor) behavior 43
 Puzzle • Suppliers seemingly react to incentives from network embeddedness (suppliers seemingly take reputation effects of their performance into account). • How to explain that buyers seemingly do not anticipate on this feature? • Data and/or measurement problems (including sample selectivity and endogeneity of network embeddedness)? • Lack of “strategic rationality”? 44
Puzzle • Suppliers seemingly react to incentives from network embeddedness (suppliers seemingly take reputation effects of their performance into account). • How to explain that buyers seemingly do not anticipate on this feature? • Data and/or measurement problems (including sample selectivity and endogeneity of network embeddedness)? • Lack of “strategic rationality”? 44
 Another summary of the puzzle • Trustee reacts to trustor’s opportunities for • dyadic control and • network control • Focal trustor reacts to her own opportunities for dyadic control: she seemingly anticipates that trustee anticipates on effects of his present behavior on future behavior of focal trustor • Focal trustor does not react to her own opportunities for network control: she seemingly does not anticipate that trustee also anticipates on effects of his present behavior on future behavior of other trustors 45
Another summary of the puzzle • Trustee reacts to trustor’s opportunities for • dyadic control and • network control • Focal trustor reacts to her own opportunities for dyadic control: she seemingly anticipates that trustee anticipates on effects of his present behavior on future behavior of focal trustor • Focal trustor does not react to her own opportunities for network control: she seemingly does not anticipate that trustee also anticipates on effects of his present behavior on future behavior of other trustors 45
 Another vignette experiment: buying a used car More information: • Buskens, V. & J. Weesie (2000) An Experiment on the Effects of Embeddedness in Trust Situations: Buying a Used Car, Rationality and Society 12: 227 -253 46
Another vignette experiment: buying a used car More information: • Buskens, V. & J. Weesie (2000) An Experiment on the Effects of Embeddedness in Trust Situations: Buying a Used Car, Rationality and Society 12: 227 -253 46
 Buying a used car • Buyer chooses between trust or no trust (buy or not buy). • Trust gives the dealer the opportunity to honor or abuse trust (sell a decent or inferior car). In both situations he is better off than when trust would not be placed • Buyer gains from honored trust, but regrets trust if trust is abused. • Dealer earns an extra profit from abusing trust (too much money for a bad car). 47
Buying a used car • Buyer chooses between trust or no trust (buy or not buy). • Trust gives the dealer the opportunity to honor or abuse trust (sell a decent or inferior car). In both situations he is better off than when trust would not be placed • Buyer gains from honored trust, but regrets trust if trust is abused. • Dealer earns an extra profit from abusing trust (too much money for a bad car). 47
 Variables to be manipulated and related hypotheses Dyadic Embeddedness Network Embeddedness Learning Prior buyer’s experiences Prior third-party experiences Control Buyer’s sanction opportunities Sanction opportunities w. r. t. third parties • Trust increases with • positive own experiences (dyad) • expected future transactions (dyad) • positive information from third parties (network) • sanction opportunities w. r. t. third parties (network) 48
Variables to be manipulated and related hypotheses Dyadic Embeddedness Network Embeddedness Learning Prior buyer’s experiences Prior third-party experiences Control Buyer’s sanction opportunities Sanction opportunities w. r. t. third parties • Trust increases with • positive own experiences (dyad) • expected future transactions (dyad) • positive information from third parties (network) • sanction opportunities w. r. t. third parties (network) 48
 The set-up of the vignettes • Pairs of vignettes including six variables. • Price • Past (own experience) • Future (own expected future interactions) • Density (general reputation) • Indegree (friends experiences) • Outdegree (own third-party sanction opportunities) • Subjects compare pairs of situations to buy a used car. • Some additional questions. 49
The set-up of the vignettes • Pairs of vignettes including six variables. • Price • Past (own experience) • Future (own expected future interactions) • Density (general reputation) • Indegree (friends experiences) • Outdegree (own third-party sanction opportunities) • Subjects compare pairs of situations to buy a used car. • Some additional questions. 49
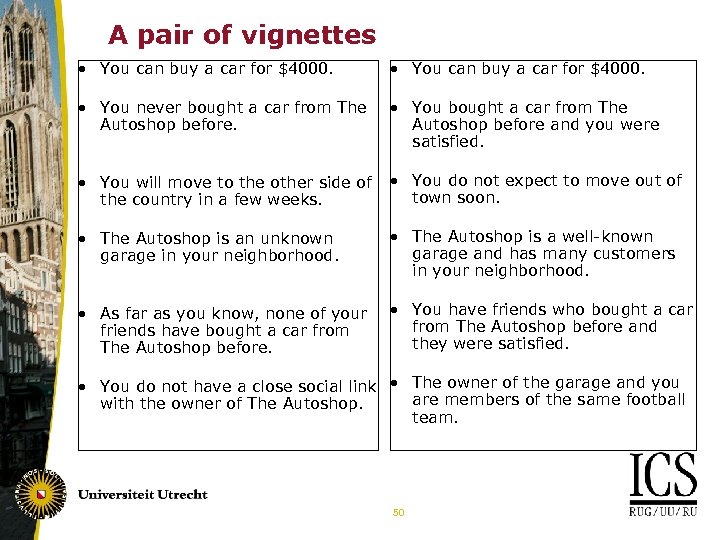 A pair of vignettes • You can buy a car for $4000. • You never bought a car from The Autoshop before. • You bought a car from The Autoshop before and you were satisfied. • You will move to the other side of the country in a few weeks. • You do not expect to move out of town soon. • The Autoshop is an unknown garage in your neighborhood. • The Autoshop is a well-known garage and has many customers in your neighborhood. • As far as you know, none of your friends have bought a car from The Autoshop before. • You have friends who bought a car from The Autoshop before and they were satisfied. • You do not have a close social link • The owner of the garage and you are members of the same football with the owner of The Autoshop. team. 50
A pair of vignettes • You can buy a car for $4000. • You never bought a car from The Autoshop before. • You bought a car from The Autoshop before and you were satisfied. • You will move to the other side of the country in a few weeks. • You do not expect to move out of town soon. • The Autoshop is an unknown garage in your neighborhood. • The Autoshop is a well-known garage and has many customers in your neighborhood. • As far as you know, none of your friends have bought a car from The Autoshop before. • You have friends who bought a car from The Autoshop before and they were satisfied. • You do not have a close social link • The owner of the garage and you are members of the same football with the owner of The Autoshop. team. 50
 Experimental design • Choices of pairs • Price is constant within a pair (only for interactions) • No “ordered” pairs (not too easy) • Between 2 and 4 variables that differ (not too complex) • Ten pairs per subject • Considerable variation in comparisons within subjects • Ultimately 125 students rating 1249 vignettes 51
Experimental design • Choices of pairs • Price is constant within a pair (only for interactions) • No “ordered” pairs (not too easy) • Between 2 and 4 variables that differ (not too complex) • Ten pairs per subject • Considerable variation in comparisons within subjects • Ultimately 125 students rating 1249 vignettes 51
 Statistical model • Random utility model. • Probit model on choices for vignettes. • Independent variables are the differences between the values at the vignettes (0: type of embeddedness to same on two vignettes, 1 or -1: type of embeddedness present on one vignette but not on the other) • Coefficients are interpretable as indicators for the increase in utility assigned to a vignette related to the given type of embeddedness • Standard errors modified for clustering (alternatively multilevel analysis could have been done) 52
Statistical model • Random utility model. • Probit model on choices for vignettes. • Independent variables are the differences between the values at the vignettes (0: type of embeddedness to same on two vignettes, 1 or -1: type of embeddedness present on one vignette but not on the other) • Coefficients are interpretable as indicators for the increase in utility assigned to a vignette related to the given type of embeddedness • Standard errors modified for clustering (alternatively multilevel analysis could have been done) 52
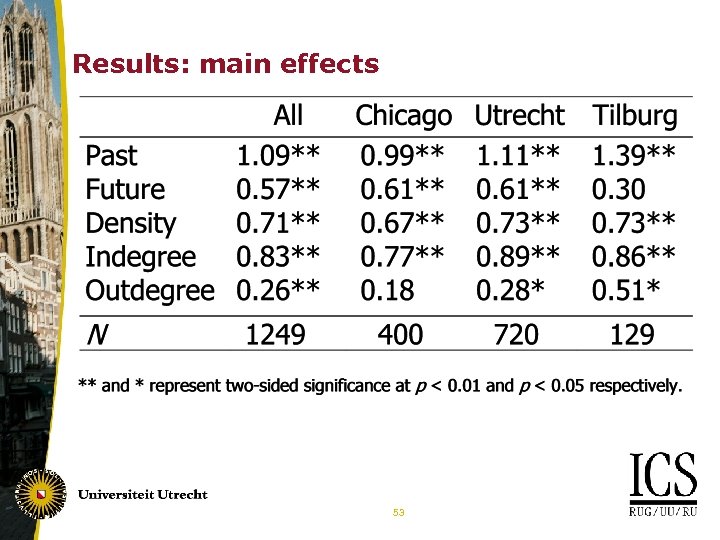 Results: main effects 53
Results: main effects 53
 Results: interaction effects 54
Results: interaction effects 54
 Additional analyses • No differences between sessions • No differences related to timing of a pair of vignettes or time spent on a decision • No effects of age, gender, field of study • Outdegree has larger effect for subjects who are more concerned about “reputation” issues • Subjects with knowledge of game theory tend to value control variables higher 55
Additional analyses • No differences between sessions • No differences related to timing of a pair of vignettes or time spent on a decision • No effects of age, gender, field of study • Outdegree has larger effect for subjects who are more concerned about “reputation” issues • Subjects with knowledge of game theory tend to value control variables higher 55
 Conclusion • Support for main effects of embeddedness • control and learning • dyadic and in networks • No support for interaction effects 56
Conclusion • Support for main effects of embeddedness • control and learning • dyadic and in networks • No support for interaction effects 56
 Discussion • Motivation of behavior (no direct incentives and students might not be experts) • Interpretation of variables • Future: moving has more side-effects than loss of sanction possibilities alone • Possible extension • Similar experiment with experts • Moving to an abstract laboratory experiment 57
Discussion • Motivation of behavior (no direct incentives and students might not be experts) • Interpretation of variables • Future: moving has more side-effects than loss of sanction possibilities alone • Possible extension • Similar experiment with experts • Moving to an abstract laboratory experiment 57
 Overview of Results Buyer-supplier vignettes Used-car vignettes Incentives + Not tested Dyadic learning + + Dyadic control + + learning and control hard to disentangle + Network learning Network control 58 +
Overview of Results Buyer-supplier vignettes Used-car vignettes Incentives + Not tested Dyadic learning + + Dyadic control + + learning and control hard to disentangle + Network learning Network control 58 +
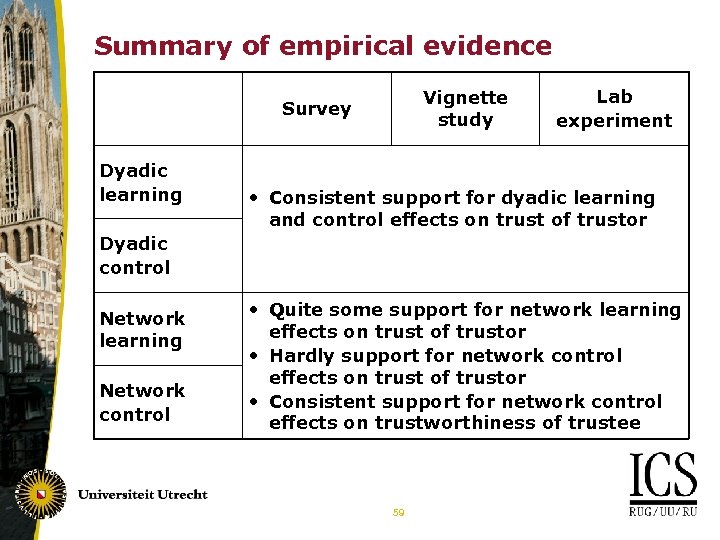 Summary of empirical evidence Vignette study Survey Dyadic learning Lab experiment • Consistent support for dyadic learning and control effects on trust of trustor Dyadic control Network learning Network control • Quite some support for network learning effects on trust of trustor • Hardly support for network control effects on trust of trustor • Consistent support for network control effects on trustworthiness of trustee 59
Summary of empirical evidence Vignette study Survey Dyadic learning Lab experiment • Consistent support for dyadic learning and control effects on trust of trustor Dyadic control Network learning Network control • Quite some support for network learning effects on trust of trustor • Hardly support for network control effects on trust of trustor • Consistent support for network control effects on trustworthiness of trustee 59
 Additional slides 60
Additional slides 60
 Additional slides on survey on IT-transactions 61
Additional slides on survey on IT-transactions 61
 Survey on IT-transactions: data collection I • Nationally representative survey on the purchase of IT-products (hard- and software) by Dutch SMEs • Data collection via buyers • CATI-interview (selection of transaction) • Structured questionnaire, usually administered via site visit • Additional archival information, sometimes including a rough content analysis of contracts • Data quality • total response rate: 58% • non-response not selective • low partial non-response 62
Survey on IT-transactions: data collection I • Nationally representative survey on the purchase of IT-products (hard- and software) by Dutch SMEs • Data collection via buyers • CATI-interview (selection of transaction) • Structured questionnaire, usually administered via site visit • Additional archival information, sometimes including a rough content analysis of contracts • Data quality • total response rate: 58% • non-response not selective • low partial non-response 62
 Survey on IT-transactions: descriptives • ‘Average transaction’: • a product worth 50, 000 US-$ • purchased by a firm with ca 80 employees • negotiating and contracting required ca 5 mendays of buyer’s employees… • and involved ca 2 divisions of buyer’s firm • for about two thirds of buyers, transaction is of ‘great’ or ‘very great’ importance for their IT-situation 63
Survey on IT-transactions: descriptives • ‘Average transaction’: • a product worth 50, 000 US-$ • purchased by a firm with ca 80 employees • negotiating and contracting required ca 5 mendays of buyer’s employees… • and involved ca 2 divisions of buyer’s firm • for about two thirds of buyers, transaction is of ‘great’ or ‘very great’ importance for their IT-situation 63
 Survey on IT-transactions: descriptives Future 64
Survey on IT-transactions: descriptives Future 64
 Survey on IT-transactions: variables I • Transaction characteristics (indicators for trust problems, opportunism problems, and other risks associated with the transaction), e. g. , monitoring problems, switching costs, importance of durability of product, importance of product for profitability buyer, volume of transaction • Costs of contracting E. g. , in-house legal expertise • Dyadic embeddedness • Prior transactions with the supplier (duration, frequency, volume, satisfaction) • Expected future business (frequency, volume) 65
Survey on IT-transactions: variables I • Transaction characteristics (indicators for trust problems, opportunism problems, and other risks associated with the transaction), e. g. , monitoring problems, switching costs, importance of durability of product, importance of product for profitability buyer, volume of transaction • Costs of contracting E. g. , in-house legal expertise • Dyadic embeddedness • Prior transactions with the supplier (duration, frequency, volume, satisfaction) • Expected future business (frequency, volume) 65
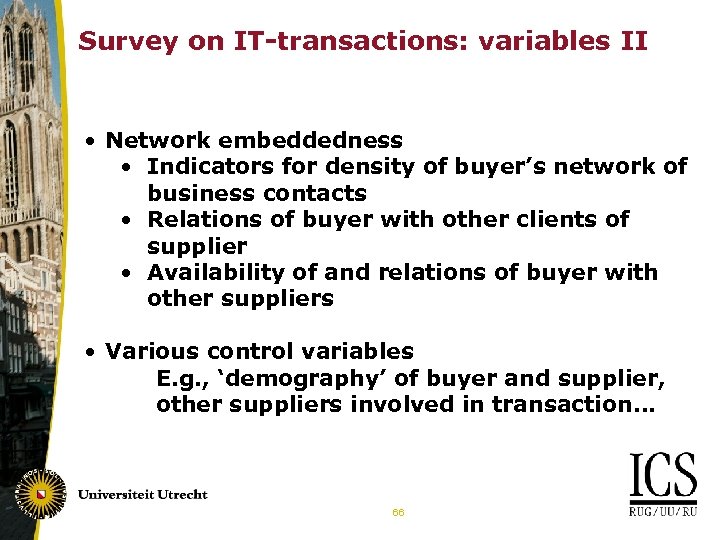 Survey on IT-transactions: variables II • Network embeddedness • Indicators for density of buyer’s network of business contacts • Relations of buyer with other clients of supplier • Availability of and relations of buyer with other suppliers • Various control variables E. g. , ‘demography’ of buyer and supplier, other suppliers involved in transaction… 66
Survey on IT-transactions: variables II • Network embeddedness • Indicators for density of buyer’s network of business contacts • Relations of buyer with other clients of supplier • Availability of and relations of buyer with other suppliers • Various control variables E. g. , ‘demography’ of buyer and supplier, other suppliers involved in transaction… 66
 Survey on IT-transactions: variables III • Ex ante management: search and selection • Investments in search E. g. , mendays, departments involved • Extensive and intensive search E. g. , number and specificity of offers, number and kind of information channels used • Ex ante management: contractual planning • Investments in negotiating and contracting E. g. , mendays, departments involved • Legal, financial, and technical issues addressed during negotiations and in the contract 67
Survey on IT-transactions: variables III • Ex ante management: search and selection • Investments in search E. g. , mendays, departments involved • Extensive and intensive search E. g. , number and specificity of offers, number and kind of information channels used • Ex ante management: contractual planning • Investments in negotiating and contracting E. g. , mendays, departments involved • Legal, financial, and technical issues addressed during negotiations and in the contract 67
 Survey on IT-transactions: variables IV • Ex post management – contract execution • Supplier performance, ex post problems (type and seriousness) • conflict resolution (type and seriousness of sanctions, ‘legal’ vs. ‘extra-legal’) • New business between buyer and supplier after focal transaction 68
Survey on IT-transactions: variables IV • Ex post management – contract execution • Supplier performance, ex post problems (type and seriousness) • conflict resolution (type and seriousness of sanctions, ‘legal’ vs. ‘extra-legal’) • New business between buyer and supplier after focal transaction 68
 Independent Variables Hypothesis 69 Coefficient |t-value|
Independent Variables Hypothesis 69 Coefficient |t-value|
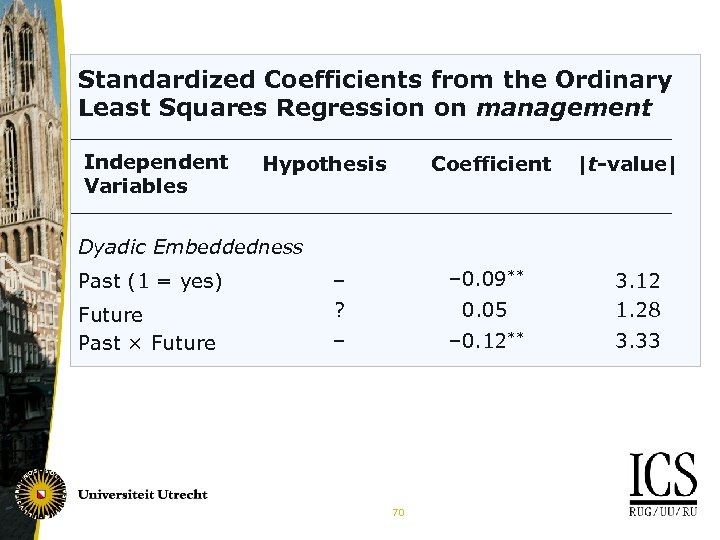 Standardized Coefficients from the Ordinary Least Squares Regression on management Independent Variables Hypothesis Coefficient |t-value| Dyadic Embeddedness Past (1 = yes) Future Past × Future – ? – 0. 09** 0. 05 3. 12 1. 28 – – 0. 12** 3. 33 70
Standardized Coefficients from the Ordinary Least Squares Regression on management Independent Variables Hypothesis Coefficient |t-value| Dyadic Embeddedness Past (1 = yes) Future Past × Future – ? – 0. 09** 0. 05 3. 12 1. 28 – – 0. 12** 3. 33 70
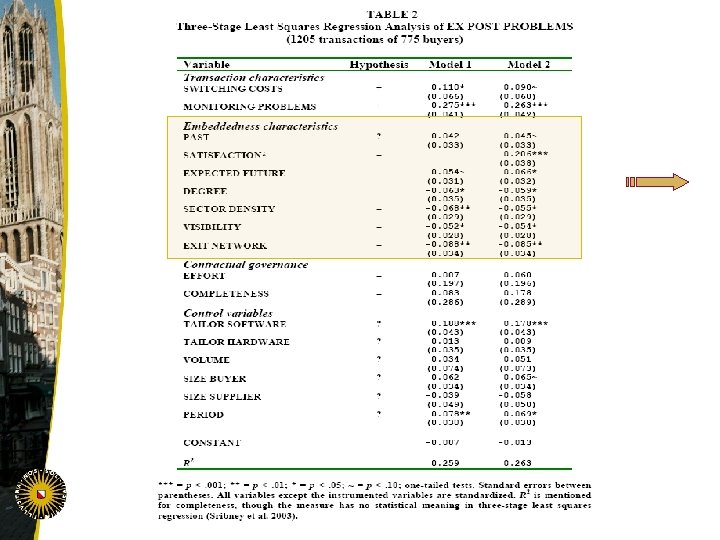
 TABLE 2 Three-Stage Least Squares Regression Analysis of EX POST PROBLEMS (1205 transactions of 775 buyers) Variable Hypothesis Model 1 Model 2 PAST ? -0. 042 (0. 033) SATISFACTION* – EXPECTED FUTURE – 0. 054~ (0. 031) 0. 066* (0. 032) DEGREE – -0. 063* (0. 035) -0. 059* (0. 035) SECTOR DENSITY – -0. 068** (0. 029) -0. 055* (0. 029) VISIBILITY – -0. 052* (0. 028) -0. 054* (0. 028) EXIT NETWORK – -0. 088** (0. 034) -0. 085** (0. 034) Embeddedness characteristics -0. 045~ (0. 033) -0. 206*** (0. 038) 72
TABLE 2 Three-Stage Least Squares Regression Analysis of EX POST PROBLEMS (1205 transactions of 775 buyers) Variable Hypothesis Model 1 Model 2 PAST ? -0. 042 (0. 033) SATISFACTION* – EXPECTED FUTURE – 0. 054~ (0. 031) 0. 066* (0. 032) DEGREE – -0. 063* (0. 035) -0. 059* (0. 035) SECTOR DENSITY – -0. 068** (0. 029) -0. 055* (0. 029) VISIBILITY – -0. 052* (0. 028) -0. 054* (0. 028) EXIT NETWORK – -0. 088** (0. 034) -0. 085** (0. 034) Embeddedness characteristics -0. 045~ (0. 033) -0. 206*** (0. 038) 72
 Survey on IT-transactions: why no effects of network embeddedness on buyer behavior? • Endogeneity of network embeddedness: before buying, buyers search for information on product and supplier, with network embeddedness changing as a by-product of search • Unmeasured variance in the trust problem: network embeddedness seemingly measures a part of the trust problem • Sample selectivity: buyers avoid transactions with “large” trust problems when network embeddedness is low • Supplier effects on investments in contracting: suppliers may contract more “carefully” with wellembedded buyers 73
Survey on IT-transactions: why no effects of network embeddedness on buyer behavior? • Endogeneity of network embeddedness: before buying, buyers search for information on product and supplier, with network embeddedness changing as a by-product of search • Unmeasured variance in the trust problem: network embeddedness seemingly measures a part of the trust problem • Sample selectivity: buyers avoid transactions with “large” trust problems when network embeddedness is low • Supplier effects on investments in contracting: suppliers may contract more “carefully” with wellembedded buyers 73
 Additional slides on vignette study on buyer-supplier relations 74
Additional slides on vignette study on buyer-supplier relations 74
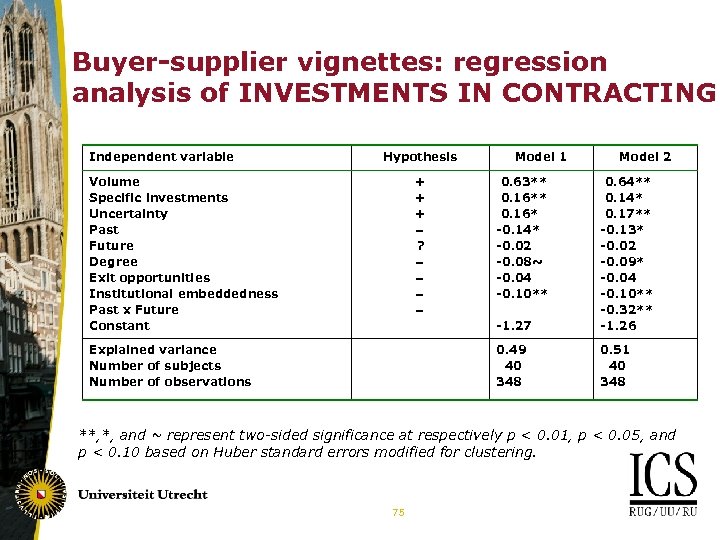 Buyer-supplier vignettes: regression analysis of INVESTMENTS IN CONTRACTING Independent variable Hypothesis Volume Specific investments Uncertainty Past Future Degree Exit opportunities Institutional embeddedness Past x Future Constant + + + ? Model 1 -1. 27 0. 64** 0. 14* 0. 17** -0. 13* -0. 02 -0. 09* -0. 04 -0. 10** -0. 32** -1. 26 0. 49 40 348 Explained variance Number of subjects Number of observations 0. 63** 0. 16* -0. 14* -0. 02 -0. 08~ -0. 04 -0. 10** Model 2 0. 51 40 348 **, *, and ~ represent two-sided significance at respectively p < 0. 01, p < 0. 05, and p < 0. 10 based on Huber standard errors modified for clustering. 75
Buyer-supplier vignettes: regression analysis of INVESTMENTS IN CONTRACTING Independent variable Hypothesis Volume Specific investments Uncertainty Past Future Degree Exit opportunities Institutional embeddedness Past x Future Constant + + + ? Model 1 -1. 27 0. 64** 0. 14* 0. 17** -0. 13* -0. 02 -0. 09* -0. 04 -0. 10** -0. 32** -1. 26 0. 49 40 348 Explained variance Number of subjects Number of observations 0. 63** 0. 16* -0. 14* -0. 02 -0. 08~ -0. 04 -0. 10** Model 2 0. 51 40 348 **, *, and ~ represent two-sided significance at respectively p < 0. 01, p < 0. 05, and p < 0. 10 based on Huber standard errors modified for clustering. 75


