 Useful Types of Constraints (cont. )
Useful Types of Constraints (cont. )
 Constraints
Constraints
 Access Constraints for Programs
Access Constraints for Programs
 Generic Constraints
Generic Constraints
 Useful Types of Constraints
Useful Types of Constraints
 Operation of ARP
Operation of ARP
 ARP Cache Poisoning
ARP Cache Poisoning
 Unsolicited ARP Response
Unsolicited ARP Response
 Malformed ARP Request
Malformed ARP Request
 Bogus Response
Bogus Response
 Bogus Requests and Responses
Bogus Requests and Responses
 Gratuitous ARP
Gratuitous ARP
 An ARP specification
An ARP specification
 Monitoring for Intrusions
Monitoring for Intrusions
 ARP Monitor Implementation
ARP Monitor Implementation
 Security Threats
Security Threats
 Centrality Analysis
Centrality Analysis
 Verification
Verification
 Reasoning About the Constraints
Reasoning About the Constraints
 Reason from bottom up: an Example
Reason from bottom up: an Example
 Automated Response to Attacks
Automated Response to Attacks
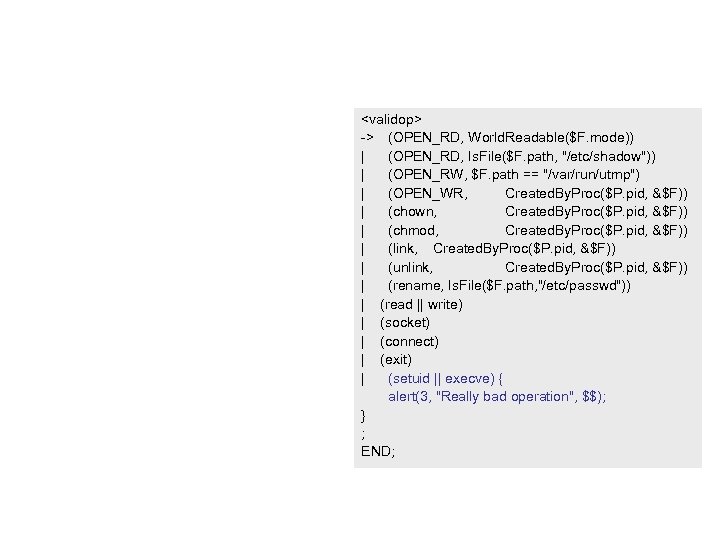 -> (OPEN_RD, World. Readable($F. mode)) | (OPEN_RD, Is. File($F. path, "/etc/shadow")) | (OPEN_RW, $F. path == "/var/run/utmp") | (OPEN_WR, Created. By. Proc($P. pid, &$F)) | (chown, Created. By. Proc($P. pid, &$F)) | (chmod, Created. By. Proc($P. pid, &$F)) | (link, Created. By. Proc($P. pid, &$F)) | (unlink, Created. By. Proc($P. pid, &$F)) | (rename, Is. File($F. path, "/etc/passwd")) | (read || write) | (socket) | (connect) | (exit) | (setuid || execve) { alert(3, "Really bad operation", $$); } ; END;
-> (OPEN_RD, World. Readable($F. mode)) | (OPEN_RD, Is. File($F. path, "/etc/shadow")) | (OPEN_RW, $F. path == "/var/run/utmp") | (OPEN_WR, Created. By. Proc($P. pid, &$F)) | (chown, Created. By. Proc($P. pid, &$F)) | (chmod, Created. By. Proc($P. pid, &$F)) | (link, Created. By. Proc($P. pid, &$F)) | (unlink, Created. By. Proc($P. pid, &$F)) | (rename, Is. File($F. path, "/etc/passwd")) | (read || write) | (socket) | (connect) | (exit) | (setuid || execve) { alert(3, "Really bad operation", $$); } ; END;
 Technical Objectives
Technical Objectives
 Technical Approach -Overview
Technical Approach -Overview
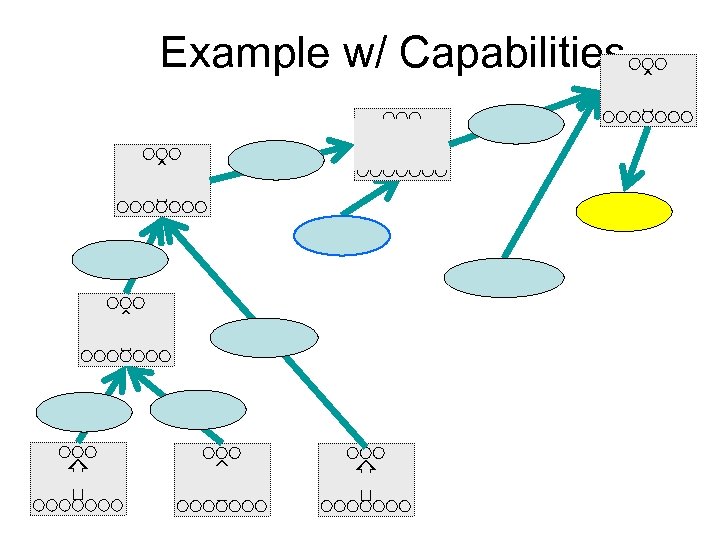 Example w/ Capabilities
Example w/ Capabilities
 Technical Approach -- Details
Technical Approach -- Details
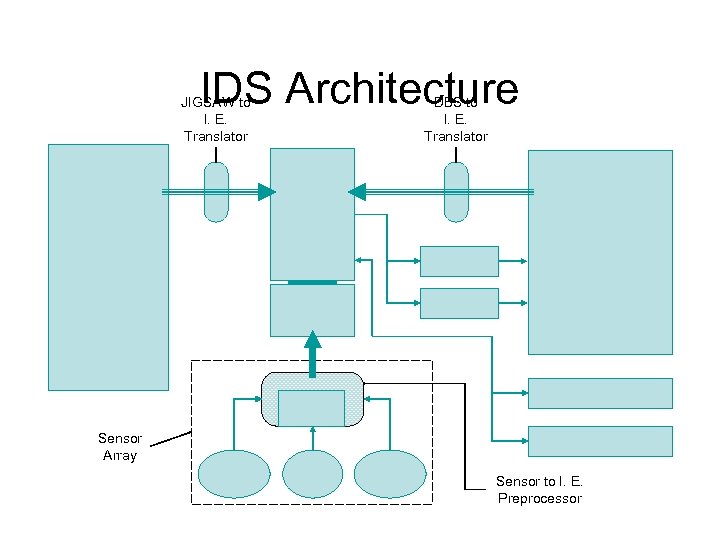 IDS Architecture JIGSAW to I. E. Translator DBS to I. E. Translator Sensor Array Sensor to I. E. Preprocessor
IDS Architecture JIGSAW to I. E. Translator DBS to I. E. Translator Sensor Array Sensor to I. E. Preprocessor
 Detecting Spoofed Packets
Detecting Spoofed Packets
 Motivation
Motivation
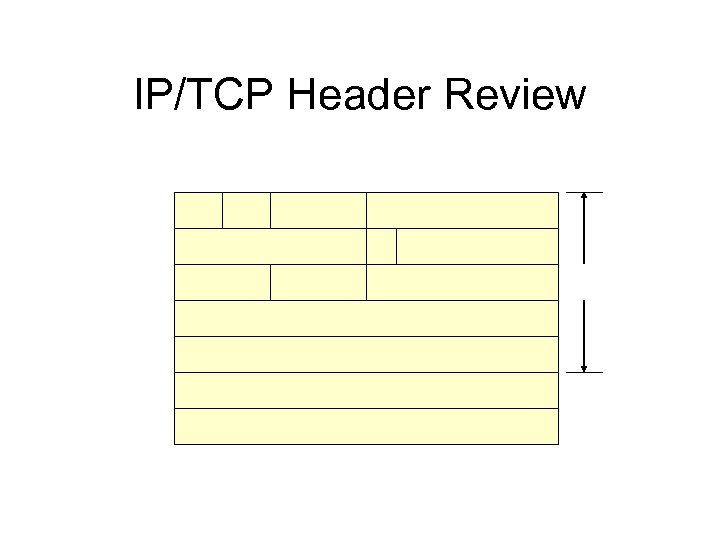 IP/TCP Header Review
IP/TCP Header Review
 IP/TCP Header Review
IP/TCP Header Review
 Significance
Significance
 Detection Methods
Detection Methods
 Conclusion
Conclusion