e35308a9c0556a4608ed2221760c660b.ppt
- Количество слайдов: 23

URSA: Providing Ubiquitous and Robust Security Support for MANET Jiejun Kong, Petros Zerfos, Haiyun Luo, Songwu Lu, Lixia Zhang University of California, Los Angeles {jkong, pzerfos, hluo, slu, lixia}@cs. ucla. edu

Outline ¨ Mobile Ad-hoc Network (MANET) ¨ Design goals & challenges ¨ Problems of conventional approaches ¨ Our approach – Network protocols – Cryptographic algorithms ¨ Implementation & simulations ¨ Conclusions
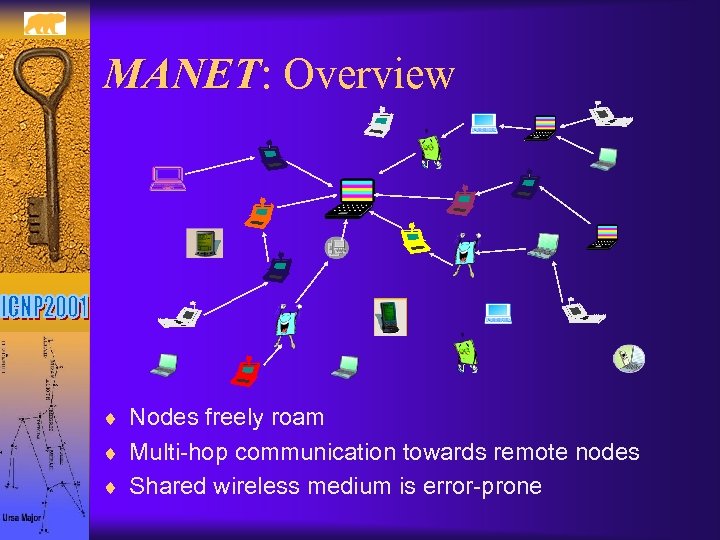
MANET: Overview MANET ¨ Nodes freely roam ¨ Multi-hop communication towards remote nodes ¨ Shared wireless medium is error-prone

Security Supports for MANET ¨ Security Supports – Authentication – Service availability – Message privacy – Message integrity – Non-repudiation ¨ More difficult than the wired scenarios – Mobility – State constantly changes – Security threats over vulnerable wireless links
Design Challenges ¨ Security breach – Vulnerable wireless links – Occasional break-ins may be inevitable over long time ¨ Service ubiquity in presence of mobility – Anywhere, anytime availability ¨ Network dynamics – Wireless channel errors – Node failures – Node join/leave ¨ Network scale
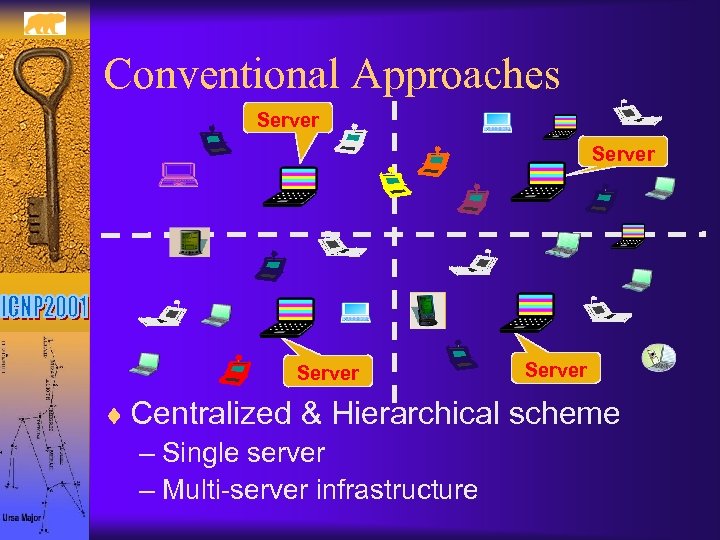
Conventional Approaches Server ¨ Centralized & Hierarchical scheme – Single server – Multi-server infrastructure
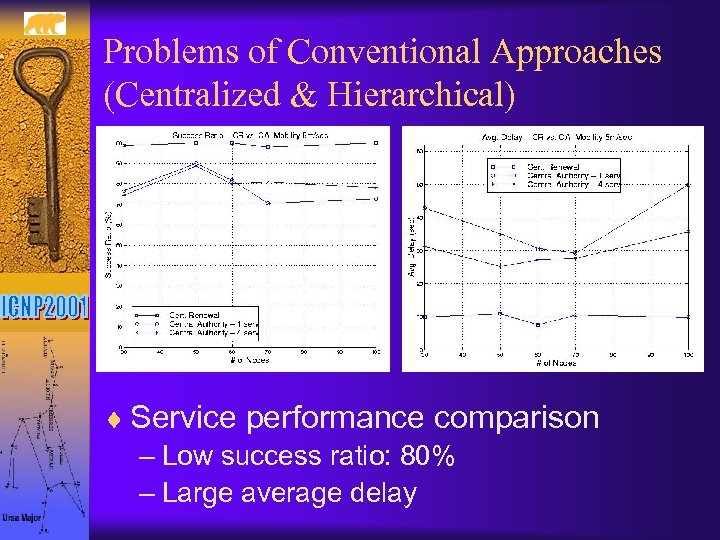
Problems of Conventional Approaches (Centralized & Hierarchical) ¨ Service performance comparison – Low success ratio: 80% – Large average delay
Our Approach ¨ Ubiquitous and robust service provision in the presence of random mobility ¨ Localized algorithms and protocols ¨ One-hop wireless communication

Why this model? ¨ No single point of compromise – Hackers must break into K nodes simultaneously to compromise the system ¨ No single point of Do. S attack & node failure ¨ K offers tradeoff between intrusion tolerance and service availability – K=1, single point of compromise, maximal availability – K=N, single point of Do. S attack, maximal intrusion tolerance

System Overview ¨ Each node carries a verifiable, unforgeable personal certificate ¨ Certificate is signed by network system key SK ¨ Certificate may be issued, renewed, or revoked ¨ Every mobile node periodically renews its certificate ¨ Ubiquitous services enabled by secret sharing

System Components ¨ Certification services – Localized certificate issuing, renewal, revocation ¨ Self-initialization service – To provide a secret share to an entity – To provide scalable proactive secret share update service ¨ Proactive secret share update service – To resist long-term adversaries without changing the shared secret
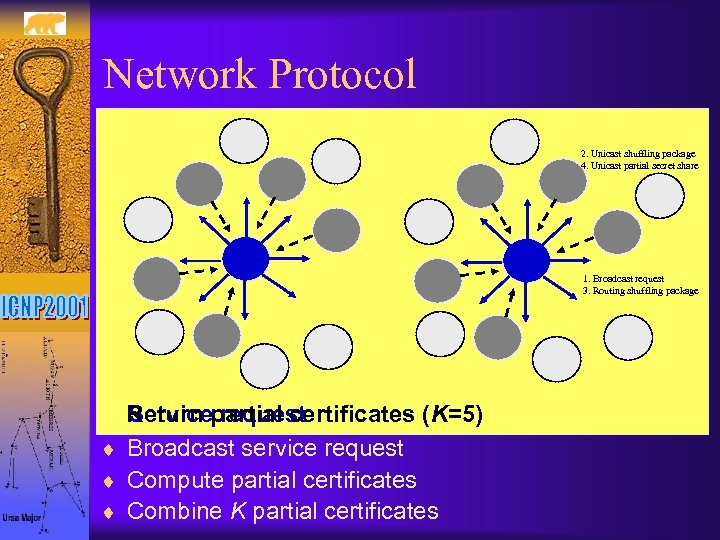
Network Protocol 2. Unicast shuffling package 4. Unicast partial secret share 1. Broadcast request 3. Routing shuffling package Return partial certificates (K=5) Service request ¨ Broadcast service request ¨ Compute partial certificates ¨ Combine K partial certificates

Cryptographic Algorithms: Threshold Secret Sharing ¨ Polynomial-based threshold secret sharing – Given a secret d and a random polynomial of degree K-1 f(x) = d + f 1 • x + f 2 • x 2 + …… + f. K-1 • x. K-1 mod n – Each entity vi obtains its secret share “f(vi) mod n” – d can be recovered by Lagrange interpolation ¨ In RSA cryptosystem, the d in the signing key SK=(d, n) is shared and distributed
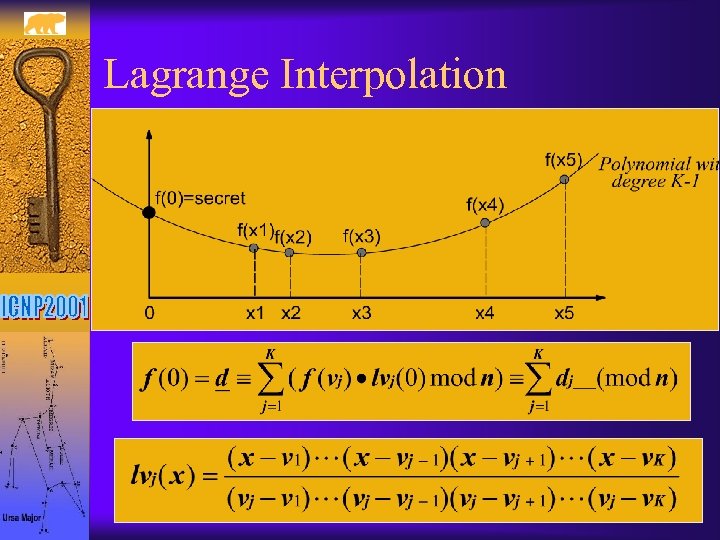
Lagrange Interpolation
Multi-signature ¨ Threshold secret sharing reveals d to a coalition ¨ d is not revealed if partial certificates are used – The cornerstone is the equation Xd 1 • Xd 2 • … • Xd. K = X(d 1 + d 2 + … + d. K) – Each coalition member contributes a signed partial certificate XSKi = (Xdi mod n) which corresponds to an RSA SK-signing in computation – The certification service requester combines K partial-certificates and obtains a correctly-signed certificate XSK = (Xd mod n)
Implementation & Simulation ¨ Implementation in C – Minimized extension: RSA-compatible operations – Optimized for wireless low-end devices • Code size • Instruction set – Coded as value-added plug-in to existing security systems ¨ Simulation in ns-2 – Communication efficiency dimensions: network size (scalability), node mobility, wireless channel errors – Performance metrics: success ratio, average delay, average # of attempts
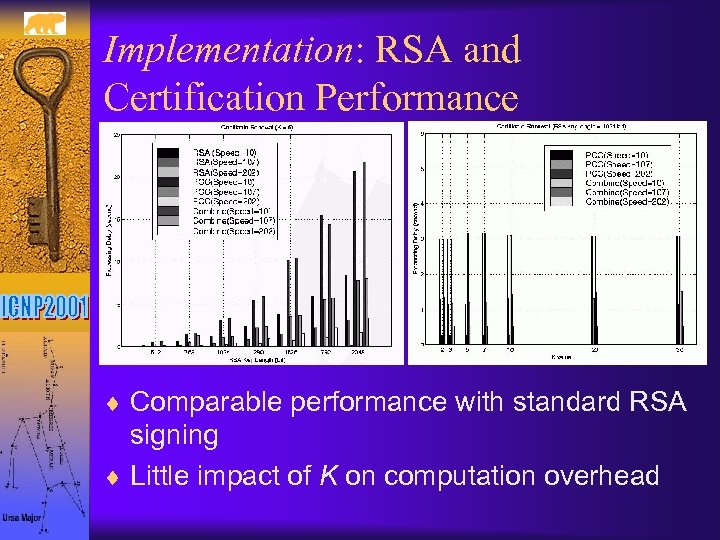
Implementation: RSA and Certification Performance ¨ Comparable performance with standard RSA signing ¨ Little impact of K on computation overhead
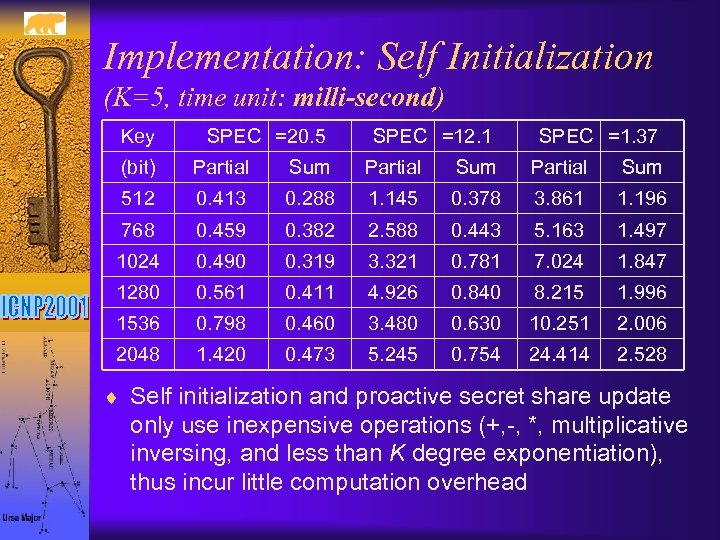
Implementation: Self Initialization (K=5, time unit: milli-second) Key SPEC =20. 5 SPEC =12. 1 SPEC =1. 37 (bit) Partial Sum 512 0. 413 0. 288 1. 145 0. 378 3. 861 1. 196 768 0. 459 0. 382 2. 588 0. 443 5. 163 1. 497 1024 0. 490 0. 319 3. 321 0. 781 7. 024 1. 847 1280 0. 561 0. 411 4. 926 0. 840 8. 215 1. 996 1536 0. 798 0. 460 3. 480 0. 630 10. 251 2. 006 2048 1. 420 0. 473 5. 245 0. 754 24. 414 2. 528 ¨ Self initialization and proactive secret share update only use inexpensive operations (+, -, *, multiplicative inversing, and less than K degree exponentiation), thus incur little computation overhead
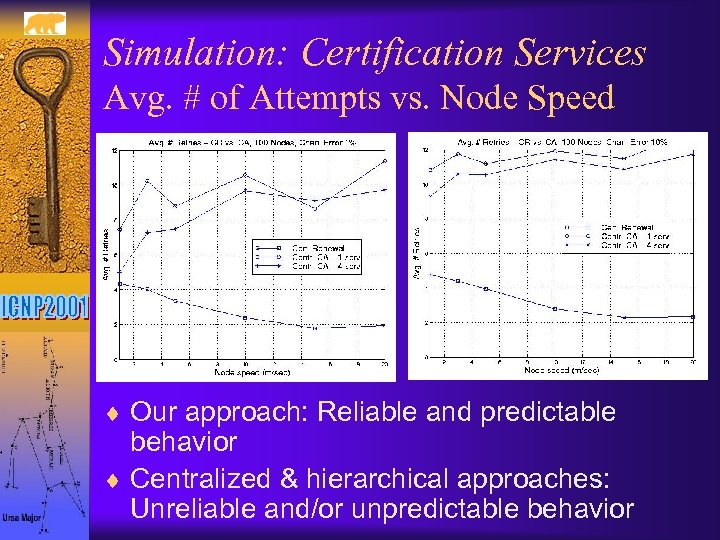
Simulation: Certification Services Avg. # of Attempts vs. Node Speed ¨ Our approach: Reliable and predictable behavior ¨ Centralized & hierarchical approaches: Unreliable and/or unpredictable behavior
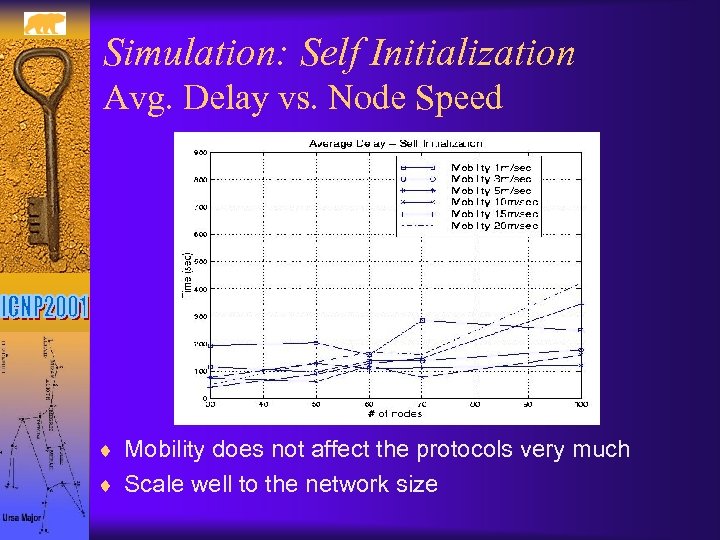
Simulation: Self Initialization Avg. Delay vs. Node Speed ¨ Mobility does not affect the protocols very much ¨ Scale well to the network size
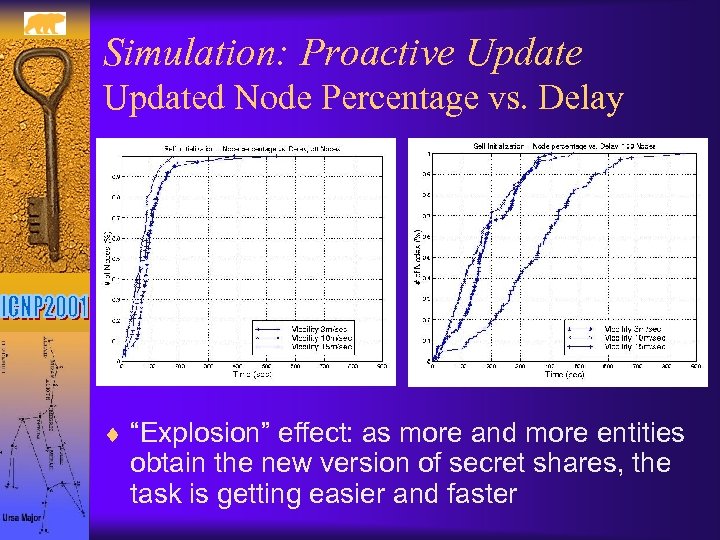
Simulation: Proactive Updated Node Percentage vs. Delay ¨ “Explosion” effect: as more and more entities obtain the new version of secret shares, the task is getting easier and faster

Conclusion ¨ Certification-based approach – Secret sharing – Multi-signature ¨ Localized and distributed protocols – Faster and more robust than other approaches – Service ubiquity – Scalable ¨ Flexible trade-off between intrusion tolerance & service availability

e35308a9c0556a4608ed2221760c660b.ppt