c066bebe2b2d7fdc14df3813c2389cc7.ppt
- Количество слайдов: 27
 Unified Access Control Solution Javier López – jlopez@juniper. net Copyright © 2005 Juniper Networks, Inc. Proprietary and Confidential www. juniper. net 1
Unified Access Control Solution Javier López – jlopez@juniper. net Copyright © 2005 Juniper Networks, Inc. Proprietary and Confidential www. juniper. net 1
 AGENDA § SSL VPNs Review § Unified Access Control Solution § Unified Access Control Scenarios § Live Demo Copyright © 2005 Juniper Networks, Inc. Proprietary and Confidential www. juniper. net 2
AGENDA § SSL VPNs Review § Unified Access Control Solution § Unified Access Control Scenarios § Live Demo Copyright © 2005 Juniper Networks, Inc. Proprietary and Confidential www. juniper. net 2
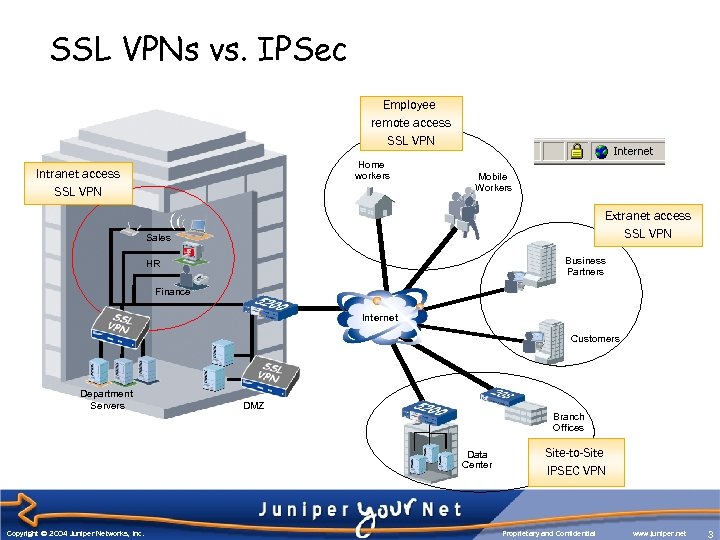 SSL VPNs vs. IPSec Employee remote access SSL VPN Home workers Intranet access SSL VPN Mobile Workers Extranet access SSL VPN Sales Business Partners HR Finance Internet Customers Department Servers DMZ Branch Offices Data Center Copyright © 2004 Juniper Networks, Inc. Site-to-Site IPSEC VPN Proprietary and Confidential www. juniper. net 3
SSL VPNs vs. IPSec Employee remote access SSL VPN Home workers Intranet access SSL VPN Mobile Workers Extranet access SSL VPN Sales Business Partners HR Finance Internet Customers Department Servers DMZ Branch Offices Data Center Copyright © 2004 Juniper Networks, Inc. Site-to-Site IPSEC VPN Proprietary and Confidential www. juniper. net 3
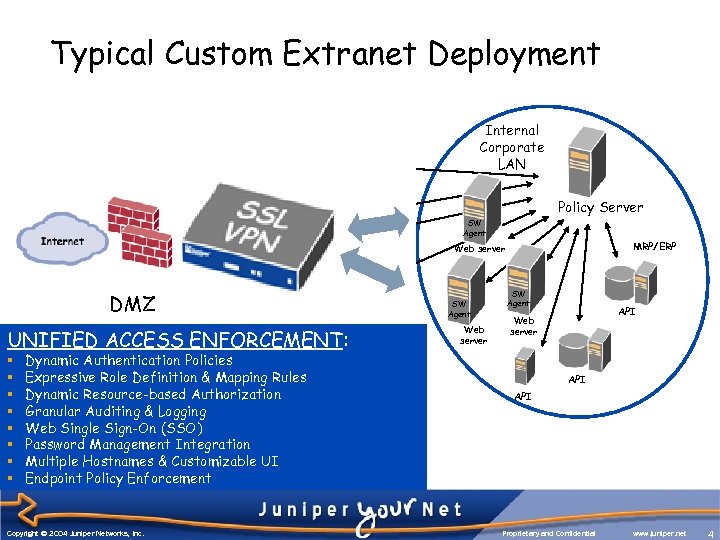 Typical Custom Extranet Deployment SW Agent Web server SW Agent DMZ Web server SW Agent § Dynamic Authentication Policies server § Expressive Role Definition & Mapping Rules §Extensive Deployment Requirements: Dynamic Resource-based Authorization §§Duplication & Migration of Servers into DMZ Granular Auditing & Logging §§Harden OS/Server Farms & Ongoing Patch Maintenance Web Single Sign-On (SSO) §§Maintenance of public facing infrastructure Password Management Integration §§AAA Limitation to only Customizable UI resources Multiple Hostnames & those integrated §§Custom API development for non-Web content Endpoint Policy Enforcement Copyright © 2004 Juniper Networks, Inc. Policy Server SW Agent MRP/ERP Web server Web UNIFIED ACCESS ENFORCEMENT: server Web SW Agent Internal Corporate LAN API SW Agent Web server SW Agent API Web server API Proprietary and Confidential www. juniper. net 4
Typical Custom Extranet Deployment SW Agent Web server SW Agent DMZ Web server SW Agent § Dynamic Authentication Policies server § Expressive Role Definition & Mapping Rules §Extensive Deployment Requirements: Dynamic Resource-based Authorization §§Duplication & Migration of Servers into DMZ Granular Auditing & Logging §§Harden OS/Server Farms & Ongoing Patch Maintenance Web Single Sign-On (SSO) §§Maintenance of public facing infrastructure Password Management Integration §§AAA Limitation to only Customizable UI resources Multiple Hostnames & those integrated §§Custom API development for non-Web content Endpoint Policy Enforcement Copyright © 2004 Juniper Networks, Inc. Policy Server SW Agent MRP/ERP Web server Web UNIFIED ACCESS ENFORCEMENT: server Web SW Agent Internal Corporate LAN API SW Agent Web server SW Agent API Web server API Proprietary and Confidential www. juniper. net 4
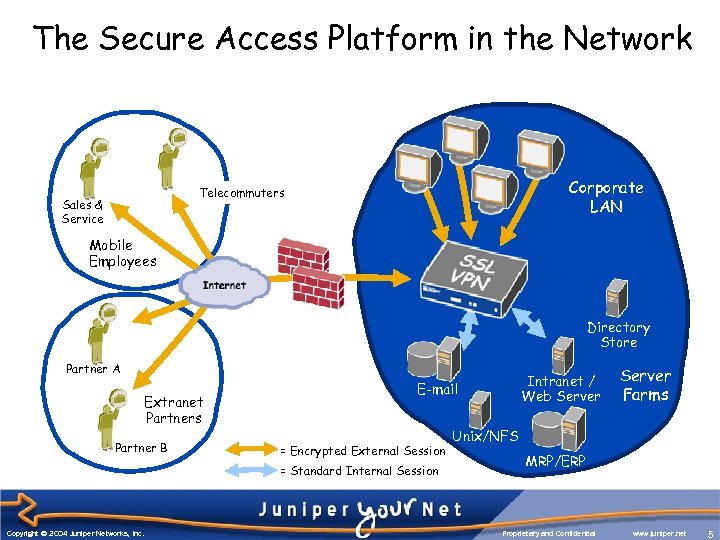 The Secure Access Platform in the Network Corporate LAN Telecommuters Sales & Service Mobile Employees Directory Store Partner A Extranet Partners Partner B = Encrypted External Session = Standard Internal Session Copyright © 2004 Juniper Networks, Inc. Intranet / Web Server E-mail Server Farms Unix/NFS MRP/ERP Proprietary and Confidential www. juniper. net 5
The Secure Access Platform in the Network Corporate LAN Telecommuters Sales & Service Mobile Employees Directory Store Partner A Extranet Partners Partner B = Encrypted External Session = Standard Internal Session Copyright © 2004 Juniper Networks, Inc. Intranet / Web Server E-mail Server Farms Unix/NFS MRP/ERP Proprietary and Confidential www. juniper. net 5
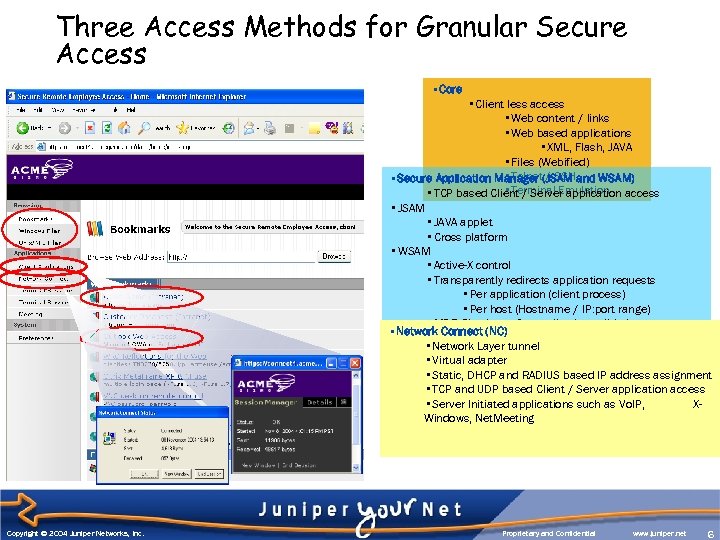 Three Access Methods for Granular Secure Access • Core • Client less access • Web content / links • Web based applications • XML, Flash, JAVA • Files (Webified) • Telnet / SSH • Secure Application Manager (JSAM and WSAM) • Terminal Emulation • TCP based Client / Server application access • JSAM • JAVA applet • Cross platform • WSAM • Active-XCore control • Transparently redirects application requests Access • Per application (client process) • Per host (Hostname / IP: port range) • MD 5 Checksum for application validation • Network Connect 2 K/XP/98 • Windows (NC) • Network Layer tunnel • Pocket PC (Win CE) • Virtual adapter • Static, DHCP and RADIUS based IP address assignment • TCP and UDP based Client / Server application access • Server Initiated applications such as Vo. IP, XWindows, Net. Meeting Copyright © 2004 Juniper Networks, Inc. Proprietary and Confidential www. juniper. net 6
Three Access Methods for Granular Secure Access • Core • Client less access • Web content / links • Web based applications • XML, Flash, JAVA • Files (Webified) • Telnet / SSH • Secure Application Manager (JSAM and WSAM) • Terminal Emulation • TCP based Client / Server application access • JSAM • JAVA applet • Cross platform • WSAM • Active-XCore control • Transparently redirects application requests Access • Per application (client process) • Per host (Hostname / IP: port range) • MD 5 Checksum for application validation • Network Connect 2 K/XP/98 • Windows (NC) • Network Layer tunnel • Pocket PC (Win CE) • Virtual adapter • Static, DHCP and RADIUS based IP address assignment • TCP and UDP based Client / Server application access • Server Initiated applications such as Vo. IP, XWindows, Net. Meeting Copyright © 2004 Juniper Networks, Inc. Proprietary and Confidential www. juniper. net 6
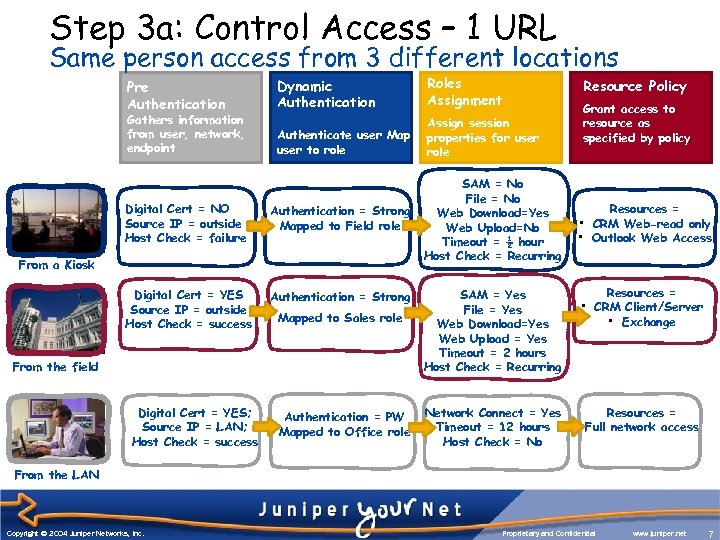 Step 3 a: Control Access – 1 URL Same person access from 3 different locations Pre Authentication Gathers information from user, network, endpoint Dynamic Authentication Roles Assignment Authenticate user Map user to role Assign session properties for user role Digital Cert = NO Source IP = outside Host Check = failure Authentication = Strong Mapped to Field role Digital Cert = YES Source IP = outside Host Check = success Authentication = Strong From a Kiosk Mapped to Sales role From the field Digital Cert = YES; Source IP = LAN; Host Check = success Authentication = PW Mapped to Office role SAM = No File = No Web Download=Yes Web Upload=No Timeout = ½ hour Host Check = Recurring SAM = Yes File = Yes Web Download=Yes Web Upload = Yes Timeout = 2 hours Host Check = Recurring Network Connect = Yes Timeout = 12 hours Host Check = No Resource Policy Grant access to resource as specified by policy • • Resources = CRM Web-read only Outlook Web Access • Resources = CRM Client/Server • Exchange Resources = Full network access From the LAN Copyright © 2004 Juniper Networks, Inc. Proprietary and Confidential www. juniper. net 7
Step 3 a: Control Access – 1 URL Same person access from 3 different locations Pre Authentication Gathers information from user, network, endpoint Dynamic Authentication Roles Assignment Authenticate user Map user to role Assign session properties for user role Digital Cert = NO Source IP = outside Host Check = failure Authentication = Strong Mapped to Field role Digital Cert = YES Source IP = outside Host Check = success Authentication = Strong From a Kiosk Mapped to Sales role From the field Digital Cert = YES; Source IP = LAN; Host Check = success Authentication = PW Mapped to Office role SAM = No File = No Web Download=Yes Web Upload=No Timeout = ½ hour Host Check = Recurring SAM = Yes File = Yes Web Download=Yes Web Upload = Yes Timeout = 2 hours Host Check = Recurring Network Connect = Yes Timeout = 12 hours Host Check = No Resource Policy Grant access to resource as specified by policy • • Resources = CRM Web-read only Outlook Web Access • Resources = CRM Client/Server • Exchange Resources = Full network access From the LAN Copyright © 2004 Juniper Networks, Inc. Proprietary and Confidential www. juniper. net 7
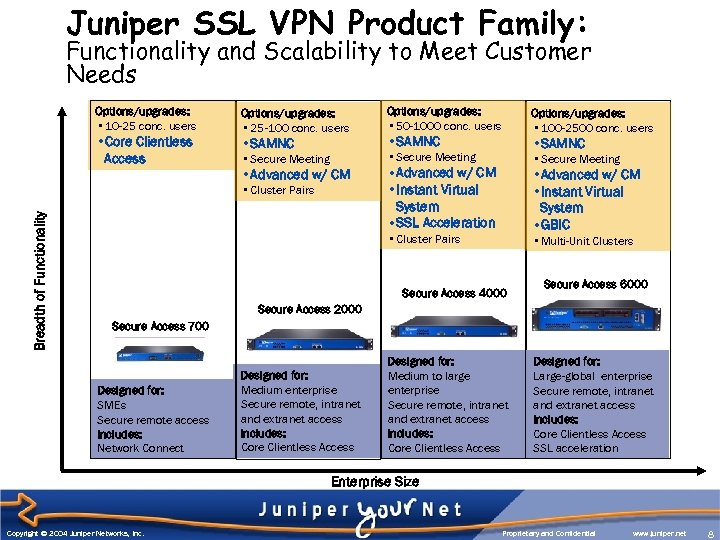 Juniper SSL VPN Product Family: Functionality and Scalability to Meet Customer Needs Options/upgrades: • 10 -25 conc. users • Core Clientless Access Options/upgrades: • 25 -100 conc. users • SAMNC Options/upgrades: • 100 -2500 conc. users • SAMNC • Secure Meeting • Advanced w/ CM • Cluster Pairs Breadth of Functionality Options/upgrades: • 50 -1000 conc. users • Secure Meeting • Advanced w/ CM • Instant Virtual System • SSL Acceleration • Advanced w/ CM • Instant Virtual System • GBIC • Cluster Pairs • Multi-Unit Clusters Secure Access 4000 Secure Access 6000 Secure Access 2000 Secure Access 700 Designed for: SMEs Secure remote access Includes: Network Connect Designed for: Medium enterprise Secure remote, intranet and extranet access Includes: Core Clientless Access Designed for: Medium to large enterprise Secure remote, intranet and extranet access Includes: Core Clientless Access Designed for: Large-global enterprise Secure remote, intranet and extranet access Includes: Core Clientless Access SSL acceleration Enterprise Size Copyright © 2004 Juniper Networks, Inc. Proprietary and Confidential www. juniper. net 8
Juniper SSL VPN Product Family: Functionality and Scalability to Meet Customer Needs Options/upgrades: • 10 -25 conc. users • Core Clientless Access Options/upgrades: • 25 -100 conc. users • SAMNC Options/upgrades: • 100 -2500 conc. users • SAMNC • Secure Meeting • Advanced w/ CM • Cluster Pairs Breadth of Functionality Options/upgrades: • 50 -1000 conc. users • Secure Meeting • Advanced w/ CM • Instant Virtual System • SSL Acceleration • Advanced w/ CM • Instant Virtual System • GBIC • Cluster Pairs • Multi-Unit Clusters Secure Access 4000 Secure Access 6000 Secure Access 2000 Secure Access 700 Designed for: SMEs Secure remote access Includes: Network Connect Designed for: Medium enterprise Secure remote, intranet and extranet access Includes: Core Clientless Access Designed for: Medium to large enterprise Secure remote, intranet and extranet access Includes: Core Clientless Access Designed for: Large-global enterprise Secure remote, intranet and extranet access Includes: Core Clientless Access SSL acceleration Enterprise Size Copyright © 2004 Juniper Networks, Inc. Proprietary and Confidential www. juniper. net 8
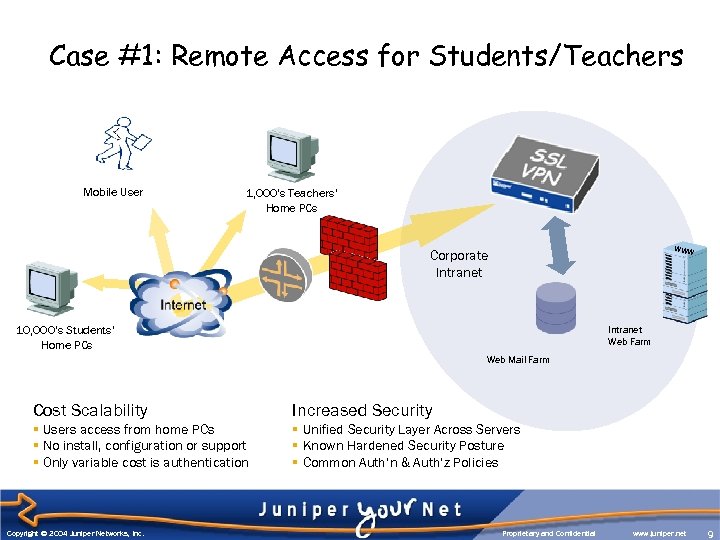 Case #1: Remote Access for Students/Teachers Mobile User 1, 000’s Teachers’ Home PCs WWW Corporate Intranet WWW 10, 000’s Students’ Home PCs Intranet Web Farm Web Mail Farm Cost Scalability Increased Security § Users access from home PCs § No install, configuration or support § Only variable cost is authentication § Unified Security Layer Across Servers § Known Hardened Security Posture § Common Auth’n & Auth’z Policies Copyright © 2004 Juniper Networks, Inc. Proprietary and Confidential www. juniper. net 9
Case #1: Remote Access for Students/Teachers Mobile User 1, 000’s Teachers’ Home PCs WWW Corporate Intranet WWW 10, 000’s Students’ Home PCs Intranet Web Farm Web Mail Farm Cost Scalability Increased Security § Users access from home PCs § No install, configuration or support § Only variable cost is authentication § Unified Security Layer Across Servers § Known Hardened Security Posture § Common Auth’n & Auth’z Policies Copyright © 2004 Juniper Networks, Inc. Proprietary and Confidential www. juniper. net 9
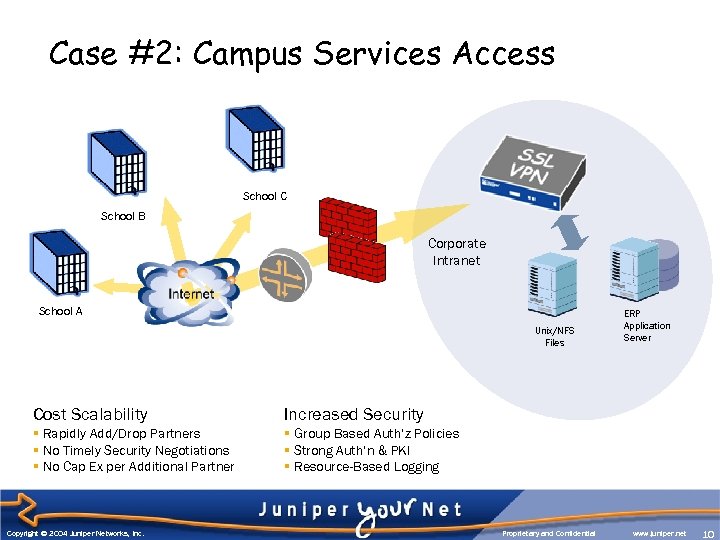 Case #2: Campus Services Access School C School B Corporate Intranet School A Unix/NFS Files Cost Scalability Increased Security § Rapidly Add/Drop Partners § No Timely Security Negotiations § No Cap Ex per Additional Partner ERP Application Server § Group Based Auth’z Policies § Strong Auth’n & PKI § Resource-Based Logging Copyright © 2004 Juniper Networks, Inc. Proprietary and Confidential www. juniper. net 10
Case #2: Campus Services Access School C School B Corporate Intranet School A Unix/NFS Files Cost Scalability Increased Security § Rapidly Add/Drop Partners § No Timely Security Negotiations § No Cap Ex per Additional Partner ERP Application Server § Group Based Auth’z Policies § Strong Auth’n & PKI § Resource-Based Logging Copyright © 2004 Juniper Networks, Inc. Proprietary and Confidential www. juniper. net 10
 AGENDA § SSL VPNs Review § Unified Access Control Solution § Unified Access Control Scenarios § Live Demo Copyright © 2005 Juniper Networks, Inc. Proprietary and Confidential www. juniper. net 11
AGENDA § SSL VPNs Review § Unified Access Control Solution § Unified Access Control Scenarios § Live Demo Copyright © 2005 Juniper Networks, Inc. Proprietary and Confidential www. juniper. net 11
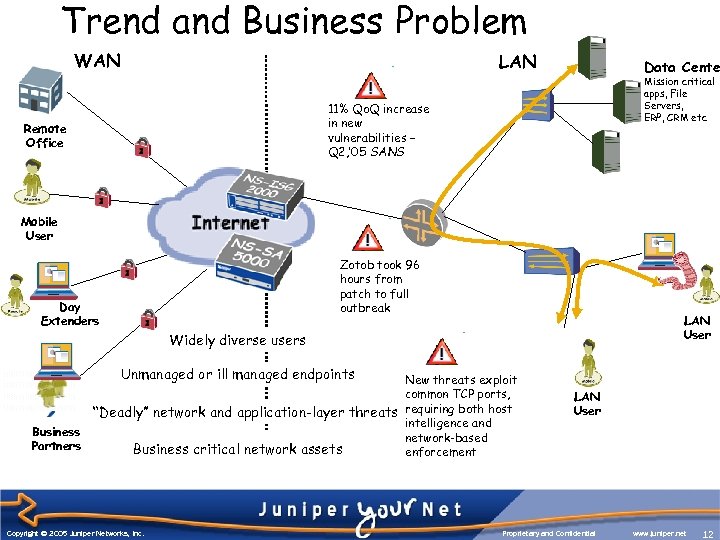 Trend and Business Problem WAN LAN Data Cente Mission critical apps, File Servers, ERP, CRM etc 11% Qo. Q increase in new vulnerabilities – Q 2, ’ 05 SANS Remote Office Mobile User Zotob took 96 hours from patch to full outbreak Day Extenders LAN User Widely diverse users Unmanaged or ill managed endpoints Business Partners New threats exploit common TCP ports, “Deadly” network and application-layer threats requiring both host intelligence and network-based Business critical network assets enforcement Copyright © 2005 Juniper Networks, Inc. LAN User Proprietary and Confidential www. juniper. net 12
Trend and Business Problem WAN LAN Data Cente Mission critical apps, File Servers, ERP, CRM etc 11% Qo. Q increase in new vulnerabilities – Q 2, ’ 05 SANS Remote Office Mobile User Zotob took 96 hours from patch to full outbreak Day Extenders LAN User Widely diverse users Unmanaged or ill managed endpoints Business Partners New threats exploit common TCP ports, “Deadly” network and application-layer threats requiring both host intelligence and network-based Business critical network assets enforcement Copyright © 2005 Juniper Networks, Inc. LAN User Proprietary and Confidential www. juniper. net 12
 How the Enterprise Infranet works § What Does it Do? • The Enterprise Infranet couples user identity, network identity, and endpoint status with network and endpoint policies. § How Does it do it? • Using a centralized policy management to push policy based on user, endpoint, network, etc to enforcement points throughout the network. Policy management is done by leveraging Dynamic Access Privilege Management (proven by #1 SSL VPN - IVE) • Enforce the policies on different points throughout the network (proven by #1 FW/VPN – Screen. OS) Copyright © 2005 Juniper Networks, Inc. Copyright © 2004 Juniper Networks, Inc. Proprietary and Confidential www. juniper. net 13 13
How the Enterprise Infranet works § What Does it Do? • The Enterprise Infranet couples user identity, network identity, and endpoint status with network and endpoint policies. § How Does it do it? • Using a centralized policy management to push policy based on user, endpoint, network, etc to enforcement points throughout the network. Policy management is done by leveraging Dynamic Access Privilege Management (proven by #1 SSL VPN - IVE) • Enforce the policies on different points throughout the network (proven by #1 FW/VPN – Screen. OS) Copyright © 2005 Juniper Networks, Inc. Copyright © 2004 Juniper Networks, Inc. Proprietary and Confidential www. juniper. net 13 13
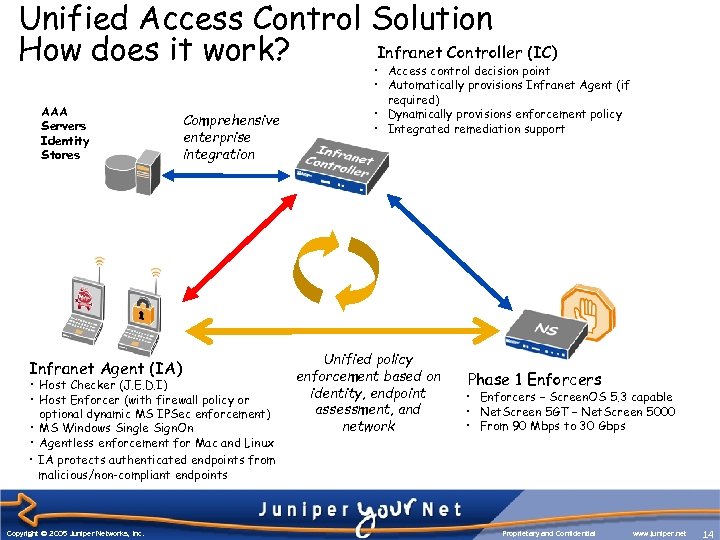 Unified Access Control Solution Infranet Controller (IC) How does it work? AAA Servers Identity Stores Infranet Agent (IA) Comprehensive enterprise integration • Host Checker (J. E. D. I) • Host Enforcer (with firewall policy or optional dynamic MS IPSec enforcement) • MS Windows Single Sign. On • Agentless enforcement for Mac and Linux • IA protects authenticated endpoints from malicious/non-compliant endpoints Copyright © 2005 Juniper Networks, Inc. • Access control decision point • Automatically provisions Infranet Agent (if required) • Dynamically provisions enforcement policy • Integrated remediation support Unified policy enforcement based on identity, endpoint assessment, and network Phase 1 Enforcers • Enforcers – Screen. OS 5. 3 capable • Net. Screen 5 GT – Net. Screen 5000 • From 90 Mbps to 30 Gbps Proprietary and Confidential www. juniper. net 14
Unified Access Control Solution Infranet Controller (IC) How does it work? AAA Servers Identity Stores Infranet Agent (IA) Comprehensive enterprise integration • Host Checker (J. E. D. I) • Host Enforcer (with firewall policy or optional dynamic MS IPSec enforcement) • MS Windows Single Sign. On • Agentless enforcement for Mac and Linux • IA protects authenticated endpoints from malicious/non-compliant endpoints Copyright © 2005 Juniper Networks, Inc. • Access control decision point • Automatically provisions Infranet Agent (if required) • Dynamically provisions enforcement policy • Integrated remediation support Unified policy enforcement based on identity, endpoint assessment, and network Phase 1 Enforcers • Enforcers – Screen. OS 5. 3 capable • Net. Screen 5 GT – Net. Screen 5000 • From 90 Mbps to 30 Gbps Proprietary and Confidential www. juniper. net 14
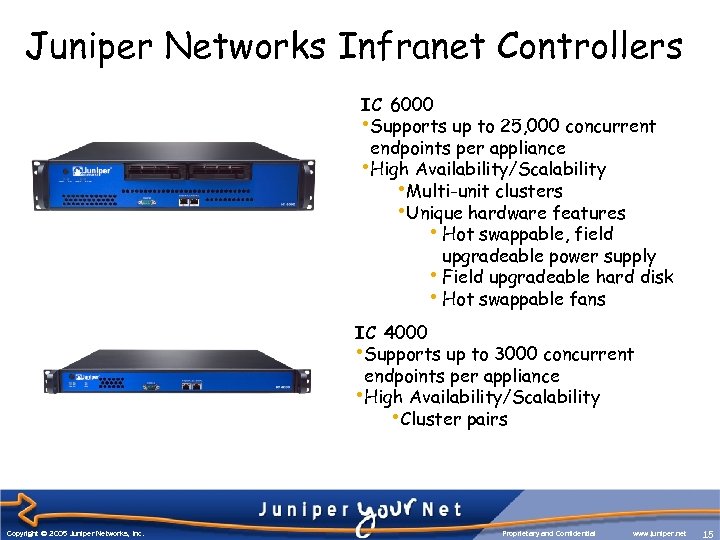 Juniper Networks Infranet Controllers IC 6000 • Supports up to 25, 000 concurrent endpoints per appliance • High Availability/Scalability • Multi-unit clusters • Unique hardware features • Hot swappable, field upgradeable power supply • Field upgradeable hard disk • Hot swappable fans IC 4000 • Supports up to 3000 concurrent endpoints per appliance • High Availability/Scalability • Cluster pairs Copyright © 2005 Juniper Networks, Inc. Proprietary and Confidential www. juniper. net 15
Juniper Networks Infranet Controllers IC 6000 • Supports up to 25, 000 concurrent endpoints per appliance • High Availability/Scalability • Multi-unit clusters • Unique hardware features • Hot swappable, field upgradeable power supply • Field upgradeable hard disk • Hot swappable fans IC 4000 • Supports up to 3000 concurrent endpoints per appliance • High Availability/Scalability • Cluster pairs Copyright © 2005 Juniper Networks, Inc. Proprietary and Confidential www. juniper. net 15
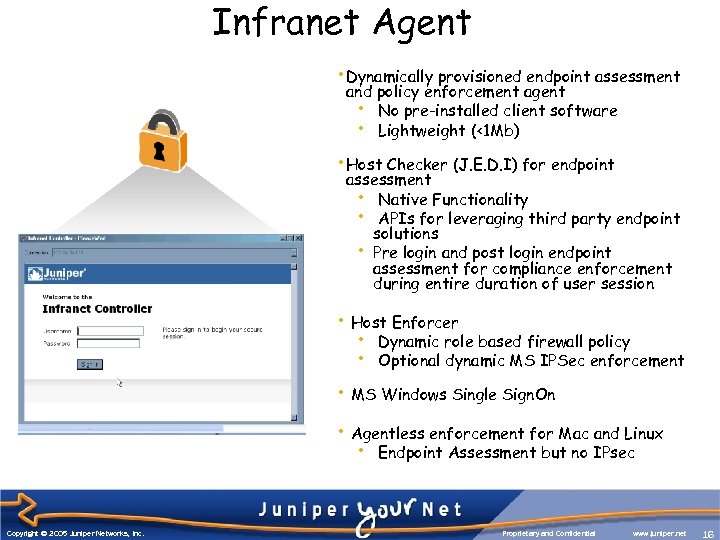 Infranet Agent • Dynamically provisioned endpoint assessment and policy enforcement agent • No pre-installed client software • Lightweight (<1 Mb) • Host Checker (J. E. D. I) for endpoint assessment • Native Functionality • APIs for leveraging third party endpoint solutions • Pre login and post login endpoint assessment for compliance enforcement during entire duration of user session • Host Enforcer • Dynamic role based firewall policy • Optional dynamic MS IPSec enforcement • MS Windows Single Sign. On • Agentless enforcement for Mac and Linux • Endpoint Assessment but no IPsec Copyright © 2005 Juniper Networks, Inc. Proprietary and Confidential www. juniper. net 16
Infranet Agent • Dynamically provisioned endpoint assessment and policy enforcement agent • No pre-installed client software • Lightweight (<1 Mb) • Host Checker (J. E. D. I) for endpoint assessment • Native Functionality • APIs for leveraging third party endpoint solutions • Pre login and post login endpoint assessment for compliance enforcement during entire duration of user session • Host Enforcer • Dynamic role based firewall policy • Optional dynamic MS IPSec enforcement • MS Windows Single Sign. On • Agentless enforcement for Mac and Linux • Endpoint Assessment but no IPsec Copyright © 2005 Juniper Networks, Inc. Proprietary and Confidential www. juniper. net 16
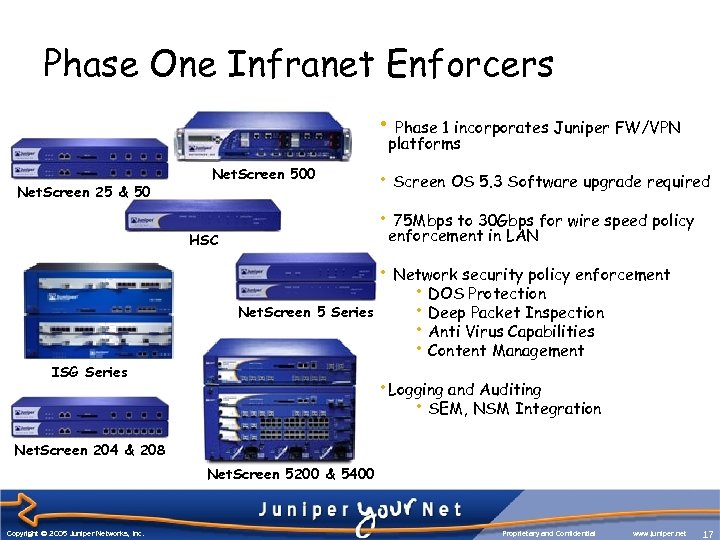 Phase One Infranet Enforcers • Phase 1 incorporates Juniper FW/VPN platforms Net. Screen 25 & 50 Net. Screen 500 • 75 Mbps to 30 Gbps for wire speed policy enforcement in LAN HSC ISG Series • Screen OS 5. 3 Software upgrade required • Network security policy enforcement • DOS Protection Net. Screen 5 Series • Deep Packet Inspection • Anti Virus Capabilities • Content Management • Logging and Auditing • SEM, NSM Integration Net. Screen 204 & 208 Net. Screen 5200 & 5400 Copyright © 2005 Juniper Networks, Inc. Proprietary and Confidential www. juniper. net 17
Phase One Infranet Enforcers • Phase 1 incorporates Juniper FW/VPN platforms Net. Screen 25 & 50 Net. Screen 500 • 75 Mbps to 30 Gbps for wire speed policy enforcement in LAN HSC ISG Series • Screen OS 5. 3 Software upgrade required • Network security policy enforcement • DOS Protection Net. Screen 5 Series • Deep Packet Inspection • Anti Virus Capabilities • Content Management • Logging and Auditing • SEM, NSM Integration Net. Screen 204 & 208 Net. Screen 5200 & 5400 Copyright © 2005 Juniper Networks, Inc. Proprietary and Confidential www. juniper. net 17
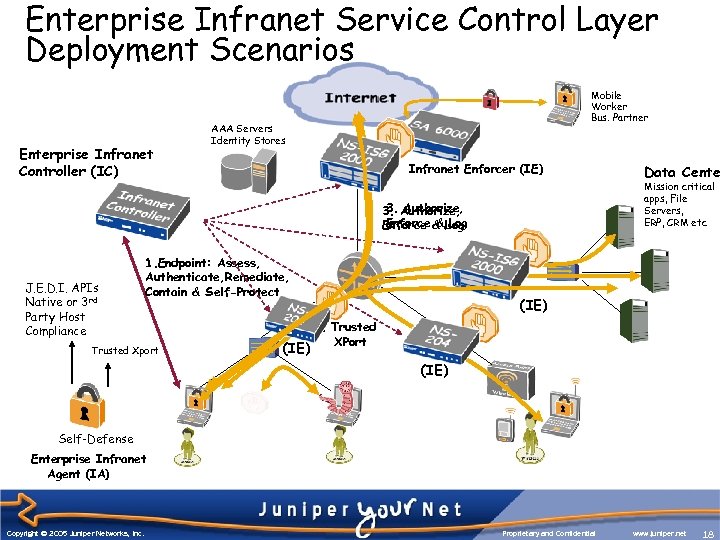 Enterprise Infranet Service Control Layer Deployment Scenarios Enterprise Infranet Controller (IC) Mobile Worker Bus. Partner AAA Servers Identity Stores Infranet Enforcer (IE) Mission critical apps, File Servers, ERP, CRM etc 3. Authorize, Enforce & Log J. E. D. I. APIs Native or 3 rd Party Host Compliance 1. Endpoint: Assess, Authenticate, Remediate, Contain & Self-Protect Trusted Xport (IE) Data Cente (IE) 2. Trusted XPort (IE) Self-Defense Enterprise Infranet Agent (IA) Copyright © 2005 Juniper Networks, Inc. Proprietary and Confidential www. juniper. net 18
Enterprise Infranet Service Control Layer Deployment Scenarios Enterprise Infranet Controller (IC) Mobile Worker Bus. Partner AAA Servers Identity Stores Infranet Enforcer (IE) Mission critical apps, File Servers, ERP, CRM etc 3. Authorize, Enforce & Log J. E. D. I. APIs Native or 3 rd Party Host Compliance 1. Endpoint: Assess, Authenticate, Remediate, Contain & Self-Protect Trusted Xport (IE) Data Cente (IE) 2. Trusted XPort (IE) Self-Defense Enterprise Infranet Agent (IA) Copyright © 2005 Juniper Networks, Inc. Proprietary and Confidential www. juniper. net 18
 AGENDA § SSL VPNs Review § Unified Access Control Solution § Unified Access Control Scenarios § Live Demo Copyright © 2005 Juniper Networks, Inc. Proprietary and Confidential www. juniper. net 19
AGENDA § SSL VPNs Review § Unified Access Control Solution § Unified Access Control Scenarios § Live Demo Copyright © 2005 Juniper Networks, Inc. Proprietary and Confidential www. juniper. net 19
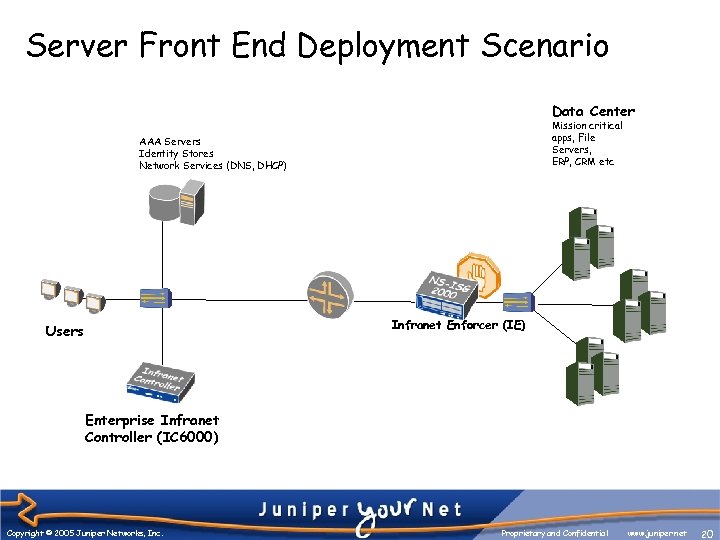 Server Front End Deployment Scenario Data Center Mission critical apps, File Servers, ERP, CRM etc AAA Servers Identity Stores Network Services (DNS, DHCP) Infranet Enforcer (IE) Users Enterprise Infranet Controller (IC 6000) Copyright © 2005 Juniper Networks, Inc. Proprietary and Confidential www. juniper. net 20
Server Front End Deployment Scenario Data Center Mission critical apps, File Servers, ERP, CRM etc AAA Servers Identity Stores Network Services (DNS, DHCP) Infranet Enforcer (IE) Users Enterprise Infranet Controller (IC 6000) Copyright © 2005 Juniper Networks, Inc. Proprietary and Confidential www. juniper. net 20
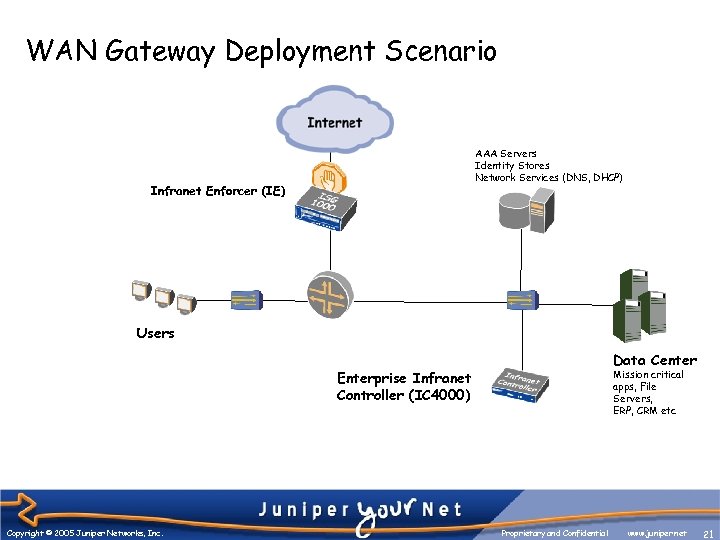 WAN Gateway Deployment Scenario AAA Servers Identity Stores Network Services (DNS, DHCP) Infranet Enforcer (IE) Users Data Center Mission critical apps, File Servers, ERP, CRM etc Enterprise Infranet Controller (IC 4000) Copyright © 2005 Juniper Networks, Inc. Proprietary and Confidential www. juniper. net 21
WAN Gateway Deployment Scenario AAA Servers Identity Stores Network Services (DNS, DHCP) Infranet Enforcer (IE) Users Data Center Mission critical apps, File Servers, ERP, CRM etc Enterprise Infranet Controller (IC 4000) Copyright © 2005 Juniper Networks, Inc. Proprietary and Confidential www. juniper. net 21
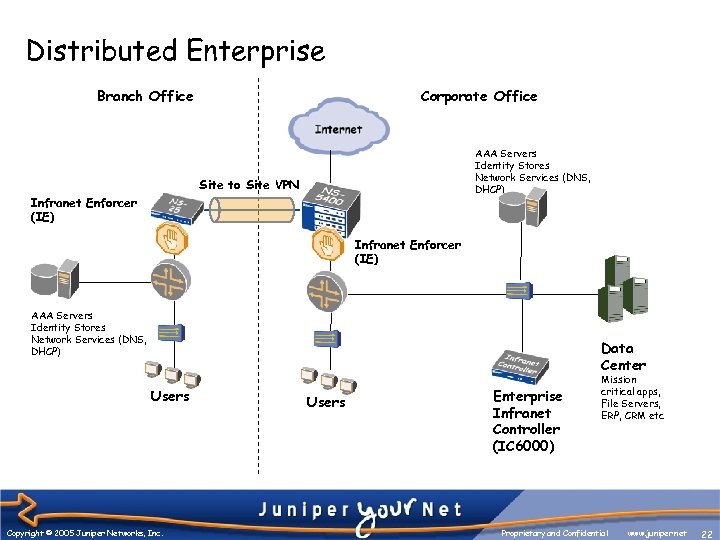 Distributed Enterprise Branch Office Corporate Office AAA Servers Identity Stores Network Services (DNS, DHCP) Site to Site VPN Infranet Enforcer (IE) AAA Servers Identity Stores Network Services (DNS, DHCP) Data Center Users Copyright © 2005 Juniper Networks, Inc. Users Enterprise Infranet Controller (IC 6000) Mission critical apps, File Servers, ERP, CRM etc Proprietary and Confidential www. juniper. net 22
Distributed Enterprise Branch Office Corporate Office AAA Servers Identity Stores Network Services (DNS, DHCP) Site to Site VPN Infranet Enforcer (IE) AAA Servers Identity Stores Network Services (DNS, DHCP) Data Center Users Copyright © 2005 Juniper Networks, Inc. Users Enterprise Infranet Controller (IC 6000) Mission critical apps, File Servers, ERP, CRM etc Proprietary and Confidential www. juniper. net 22
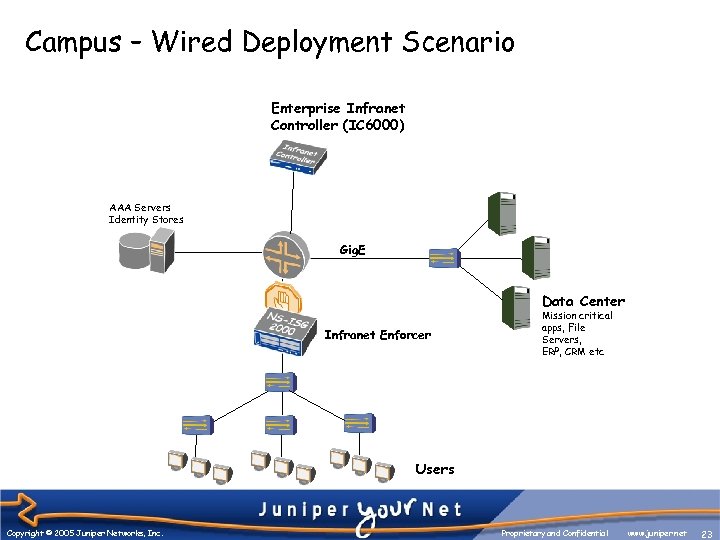 Campus – Wired Deployment Scenario Enterprise Infranet Controller (IC 6000) AAA Servers Identity Stores Gig. E Data Center Infranet Enforcer Mission critical apps, File Servers, ERP, CRM etc Users Copyright © 2005 Juniper Networks, Inc. Proprietary and Confidential www. juniper. net 23
Campus – Wired Deployment Scenario Enterprise Infranet Controller (IC 6000) AAA Servers Identity Stores Gig. E Data Center Infranet Enforcer Mission critical apps, File Servers, ERP, CRM etc Users Copyright © 2005 Juniper Networks, Inc. Proprietary and Confidential www. juniper. net 23
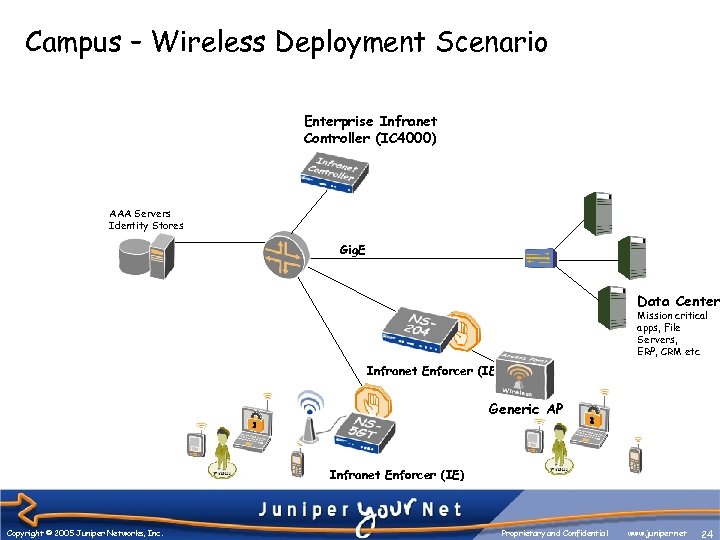 Campus – Wireless Deployment Scenario Enterprise Infranet Controller (IC 4000) AAA Servers Identity Stores Gig. E Data Center Mission critical apps, File Servers, ERP, CRM etc Infranet Enforcer (IE) Generic AP Infranet Enforcer (IE) Copyright © 2005 Juniper Networks, Inc. Proprietary and Confidential www. juniper. net 24
Campus – Wireless Deployment Scenario Enterprise Infranet Controller (IC 4000) AAA Servers Identity Stores Gig. E Data Center Mission critical apps, File Servers, ERP, CRM etc Infranet Enforcer (IE) Generic AP Infranet Enforcer (IE) Copyright © 2005 Juniper Networks, Inc. Proprietary and Confidential www. juniper. net 24
 AGENDA § SSL VPNs Review § Unified Access Control Solution § Unified Access Control Scenarios § Live Demo Copyright © 2005 Juniper Networks, Inc. Proprietary and Confidential www. juniper. net 25
AGENDA § SSL VPNs Review § Unified Access Control Solution § Unified Access Control Scenarios § Live Demo Copyright © 2005 Juniper Networks, Inc. Proprietary and Confidential www. juniper. net 25
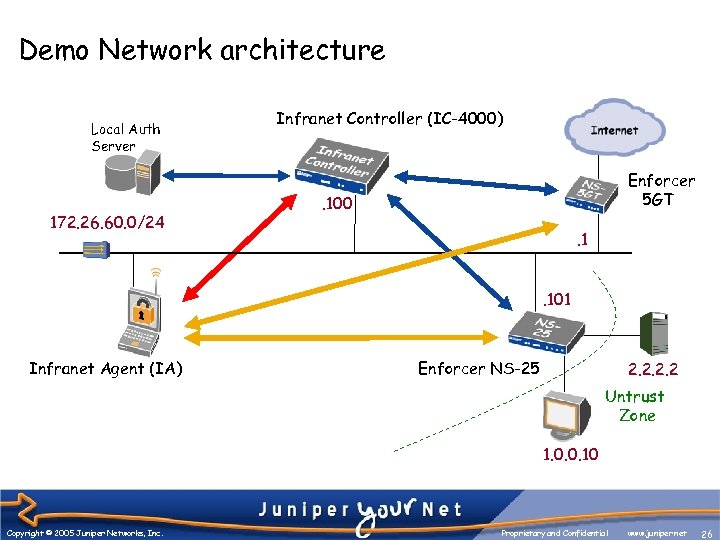 Demo Network architecture Local Auth Server 172. 26. 60. 0/24 Infranet Controller (IC-4000) Enforcer 5 GT . 100. 1. 101 Infranet Agent (IA) Enforcer NS-25 2. 2 Untrust Zone 1. 0. 0. 10 Copyright © 2005 Juniper Networks, Inc. Proprietary and Confidential www. juniper. net 26
Demo Network architecture Local Auth Server 172. 26. 60. 0/24 Infranet Controller (IC-4000) Enforcer 5 GT . 100. 1. 101 Infranet Agent (IA) Enforcer NS-25 2. 2 Untrust Zone 1. 0. 0. 10 Copyright © 2005 Juniper Networks, Inc. Proprietary and Confidential www. juniper. net 26
 Thank You Copyright © 2005 Juniper Networks, Inc. Proprietary and Confidential www. juniper. net 27
Thank You Copyright © 2005 Juniper Networks, Inc. Proprietary and Confidential www. juniper. net 27


