Mod 3 - MVA Defense-in-Depth Windows Security.pptx
- Количество слайдов: 20
 Understanding your enemy!
Understanding your enemy!
 Module 1: Today’s Threat Landscape Module 2: Key Principles of Security Module 3: Understanding your enemy! Module 4: Phases of Hackers Lunch Break Module 5: What motivates hackers? Module 6: Pass the Hash Module 7: Windows Security Capabilities and Tools
Module 1: Today’s Threat Landscape Module 2: Key Principles of Security Module 3: Understanding your enemy! Module 4: Phases of Hackers Lunch Break Module 5: What motivates hackers? Module 6: Pass the Hash Module 7: Windows Security Capabilities and Tools
 Keep In Mind! There is no way to STOP a Hacker, you can only make their job HARDER !
Keep In Mind! There is no way to STOP a Hacker, you can only make their job HARDER !
 DEMO How do we get tricked?
DEMO How do we get tricked?
 The Art of War “If you know the enemy and know yourself, you need not fear the result of a hundred battles. If you know yourself but not the enemy, for every victory gained you will also suffer a defeat. If you know neither the enemy nor yourself, you will succumb in every battle. ” – Sun Tzu
The Art of War “If you know the enemy and know yourself, you need not fear the result of a hundred battles. If you know yourself but not the enemy, for every victory gained you will also suffer a defeat. If you know neither the enemy nor yourself, you will succumb in every battle. ” – Sun Tzu
 Knowing Yourself • Accurately assess your own skills. • Possess detailed documentation of your network. • Understand the level of organizational support you receive.
Knowing Yourself • Accurately assess your own skills. • Possess detailed documentation of your network. • Understand the level of organizational support you receive.
 DEMO Microsoft Security Compliance Manager
DEMO Microsoft Security Compliance Manager
 Identifying Your Attacker Understanding Internal Attackers – Higher levels of trust – Physical access to network resources – Human resources protections
Identifying Your Attacker Understanding Internal Attackers – Higher levels of trust – Physical access to network resources – Human resources protections
 Hackers Beware Understanding External Attackers – Novice Attackers – Intermediate Attackers – Advanced Attackers
Hackers Beware Understanding External Attackers – Novice Attackers – Intermediate Attackers – Advanced Attackers
 Why do we get attacked? Top reasons you need to know… – Notoriety, acceptance, and ego – Financial gain – Challenge – Activism – Revenge – Espionage – Information warfare
Why do we get attacked? Top reasons you need to know… – Notoriety, acceptance, and ego – Financial gain – Challenge – Activism – Revenge – Espionage – Information warfare
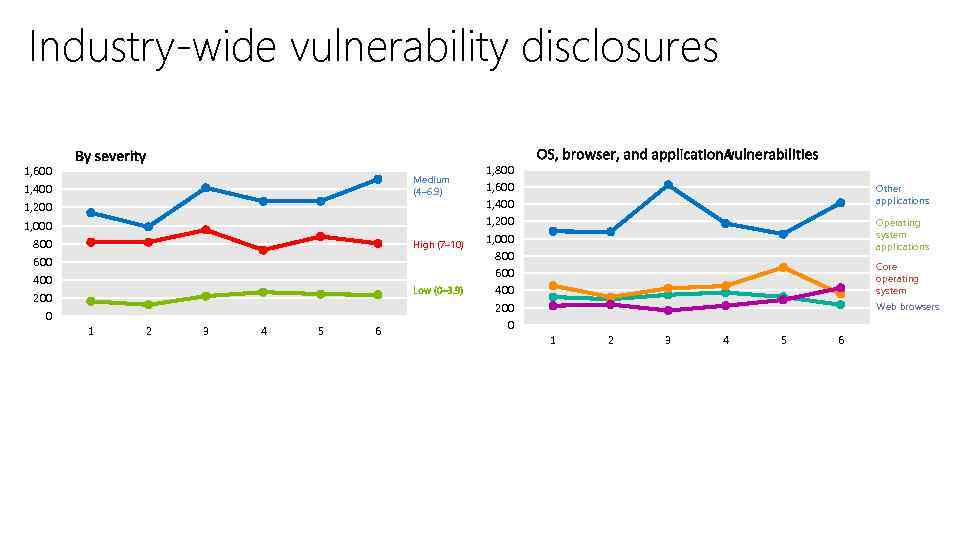 Industry-wide vulnerability disclosures 1, 600 Medium (4– 6. 9) 1, 400 1, 200 1, 000 800 High (7– 10) 600 400 200 0 1 2 3 4 5 6 1, 800 1, 600 1, 400 1, 200 1, 000 800 600 400 200 0 Other applications Operating system applications Core operating system Web browsers 1 2 3 4 5 6
Industry-wide vulnerability disclosures 1, 600 Medium (4– 6. 9) 1, 400 1, 200 1, 000 800 High (7– 10) 600 400 200 0 1 2 3 4 5 6 1, 800 1, 600 1, 400 1, 200 1, 000 800 600 400 200 0 Other applications Operating system applications Core operating system Web browsers 1 2 3 4 5 6
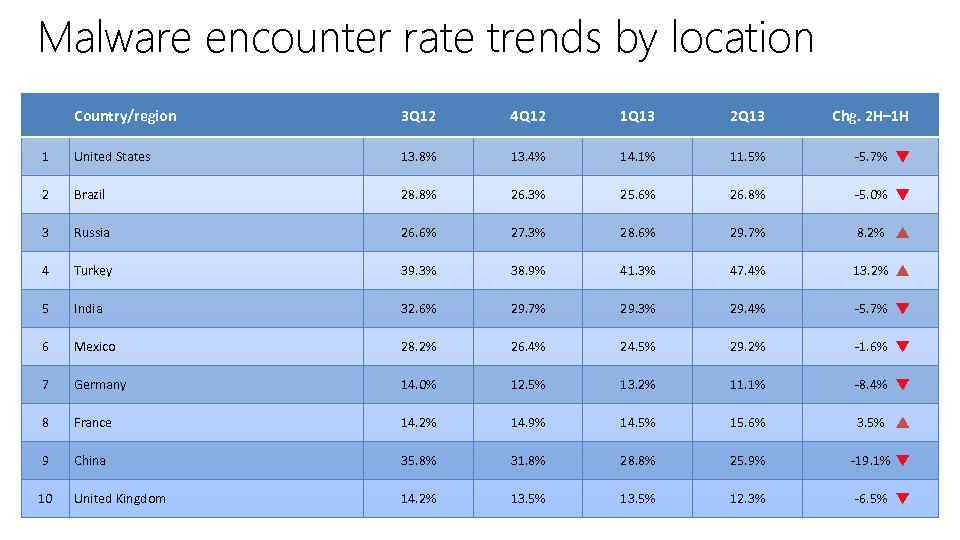 Malware encounter rate trends by location Country/region 3 Q 12 4 Q 12 1 Q 13 2 Q 13 Chg. 2 H– 1 H 1 United States 13. 8% 13. 4% 14. 1% 11. 5% -5. 7% 2 Brazil 28. 8% 26. 3% 25. 6% 26. 8% -5. 0% 3 Russia 26. 6% 27. 3% 28. 6% 29. 7% 8. 2% 4 Turkey 39. 3% 38. 9% 41. 3% 47. 4% 13. 2% 5 India 32. 6% 29. 7% 29. 3% 29. 4% -5. 7% 6 Mexico 28. 2% 26. 4% 24. 5% 29. 2% -1. 6% 7 Germany 14. 0% 12. 5% 13. 2% 11. 1% -8. 4% 8 France 14. 2% 14. 9% 14. 5% 15. 6% 3. 5% 9 China 35. 8% 31. 8% 28. 8% 25. 9% -19. 1% 10 United Kingdom 14. 2% 13. 5% 12. 3% -6. 5%
Malware encounter rate trends by location Country/region 3 Q 12 4 Q 12 1 Q 13 2 Q 13 Chg. 2 H– 1 H 1 United States 13. 8% 13. 4% 14. 1% 11. 5% -5. 7% 2 Brazil 28. 8% 26. 3% 25. 6% 26. 8% -5. 0% 3 Russia 26. 6% 27. 3% 28. 6% 29. 7% 8. 2% 4 Turkey 39. 3% 38. 9% 41. 3% 47. 4% 13. 2% 5 India 32. 6% 29. 7% 29. 3% 29. 4% -5. 7% 6 Mexico 28. 2% 26. 4% 24. 5% 29. 2% -1. 6% 7 Germany 14. 0% 12. 5% 13. 2% 11. 1% -8. 4% 8 France 14. 2% 14. 9% 14. 5% 15. 6% 3. 5% 9 China 35. 8% 31. 8% 28. 8% 25. 9% -19. 1% 10 United Kingdom 14. 2% 13. 5% 12. 3% -6. 5%
 About SIRv 16
About SIRv 16
 Staying ahead of exploits Stay current on security updates Use the newest versions of applications Use the Enhanced Mitigation Experience Toolkit (EMET)
Staying ahead of exploits Stay current on security updates Use the newest versions of applications Use the Enhanced Mitigation Experience Toolkit (EMET)
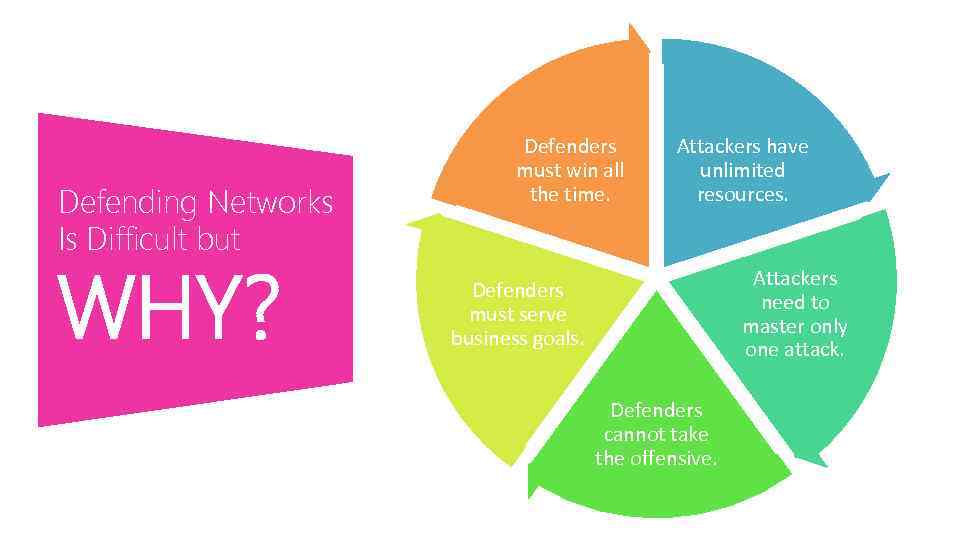 Defending Networks Is Difficult but WHY? Defenders must win all the time. Attackers have unlimited resources. Attackers need to master only one attack. Defenders must serve business goals. Defenders cannot take the offensive.
Defending Networks Is Difficult but WHY? Defenders must win all the time. Attackers have unlimited resources. Attackers need to master only one attack. Defenders must serve business goals. Defenders cannot take the offensive.
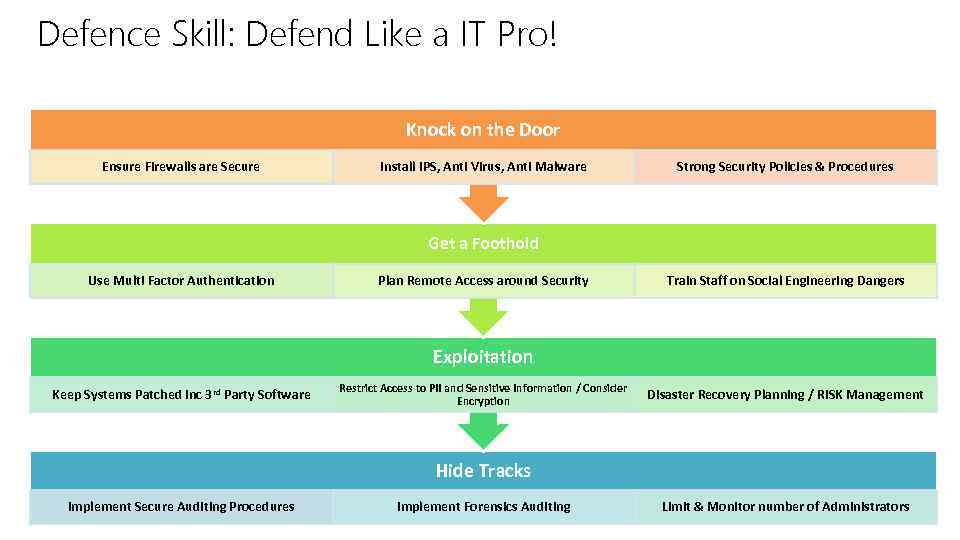 Defence Skill: Defend Like a IT Pro! Knock on the Door Ensure Firewalls are Secure Install IPS, Anti Virus, Anti Malware Strong Security Policies & Procedures Get a Foothold Use Multi Factor Authentication Plan Remote Access around Security Train Staff on Social Engineering Dangers Exploitation Keep Systems Patched inc 3 rd Party Software Restrict Access to PII and Sensitive Information / Consider Encryption Disaster Recovery Planning / RISK Management Hide Tracks Implement Secure Auditing Procedures Implement Forensics Auditing Limit & Monitor number of Administrators
Defence Skill: Defend Like a IT Pro! Knock on the Door Ensure Firewalls are Secure Install IPS, Anti Virus, Anti Malware Strong Security Policies & Procedures Get a Foothold Use Multi Factor Authentication Plan Remote Access around Security Train Staff on Social Engineering Dangers Exploitation Keep Systems Patched inc 3 rd Party Software Restrict Access to PII and Sensitive Information / Consider Encryption Disaster Recovery Planning / RISK Management Hide Tracks Implement Secure Auditing Procedures Implement Forensics Auditing Limit & Monitor number of Administrators
 Connect with the speakers! @Erdal. Ozkaya @Milad. PFE http: //erdalozkaya. com/ https: //www. facebook. com/milad. aslaner
Connect with the speakers! @Erdal. Ozkaya @Milad. PFE http: //erdalozkaya. com/ https: //www. facebook. com/milad. aslaner
 Tech. Net Virtual Labs Deep technical content and free product evaluations Hands-on deep technical labs Free, online, technical courses Download Microsoftware trials today. Find Hand On Labs. Take a free online course. Technet. microsoft. com/evalcenter Technet. microsoft. com/virtuallabs microsoftvirtualacademy. com
Tech. Net Virtual Labs Deep technical content and free product evaluations Hands-on deep technical labs Free, online, technical courses Download Microsoftware trials today. Find Hand On Labs. Take a free online course. Technet. microsoft. com/evalcenter Technet. microsoft. com/virtuallabs microsoftvirtualacademy. com
 © 2013 Microsoft Corporation. All rights reserved. Microsoft, Windows, Office, Azure, System Center, Dynamics and other product names are or may be registered trademarks and/or trademarks in the U. S. and/or other countries. The information herein is for informational purposes only and represents the current view of Microsoft Corporation as of the date of this presentation. Because Microsoft must respond to changing market conditions, it should not be interpreted to be a commitment on the part of Microsoft, and Microsoft cannot guarantee the accuracy of any information provided after the date of this presentation. MICROSOFT MAKES NO WARRANTIES, EXPRESS, IMPLIED OR STATUTORY, AS TO THE INFORMATION IN THIS PRESENTATION.
© 2013 Microsoft Corporation. All rights reserved. Microsoft, Windows, Office, Azure, System Center, Dynamics and other product names are or may be registered trademarks and/or trademarks in the U. S. and/or other countries. The information herein is for informational purposes only and represents the current view of Microsoft Corporation as of the date of this presentation. Because Microsoft must respond to changing market conditions, it should not be interpreted to be a commitment on the part of Microsoft, and Microsoft cannot guarantee the accuracy of any information provided after the date of this presentation. MICROSOFT MAKES NO WARRANTIES, EXPRESS, IMPLIED OR STATUTORY, AS TO THE INFORMATION IN THIS PRESENTATION.


