22c514c0ce930fc4ea2c2de58b74e0ed.ppt
- Количество слайдов: 35
 UNDERSTANDING INFORMATION SECURITY VIRUSES, WORMS, HOAXES, And TROJAN HORSES Lee Ratzan, MCP, Ph. D. School of Communication, Information & Library Studies at Rutgers University Lratzan@scils. rutgers. edu
UNDERSTANDING INFORMATION SECURITY VIRUSES, WORMS, HOAXES, And TROJAN HORSES Lee Ratzan, MCP, Ph. D. School of Communication, Information & Library Studies at Rutgers University Lratzan@scils. rutgers. edu
 IT’S A JUNGLE OUT THERE Computer Viruses Network Worms Trojan Horses Logic Bombs Address Book theft Hijacked Home Pages DNS Poisoning Denial of Service Attacks Zombies, IP Spoofing Buffer Overruns Password Grabbers Password Crackers
IT’S A JUNGLE OUT THERE Computer Viruses Network Worms Trojan Horses Logic Bombs Address Book theft Hijacked Home Pages DNS Poisoning Denial of Service Attacks Zombies, IP Spoofing Buffer Overruns Password Grabbers Password Crackers
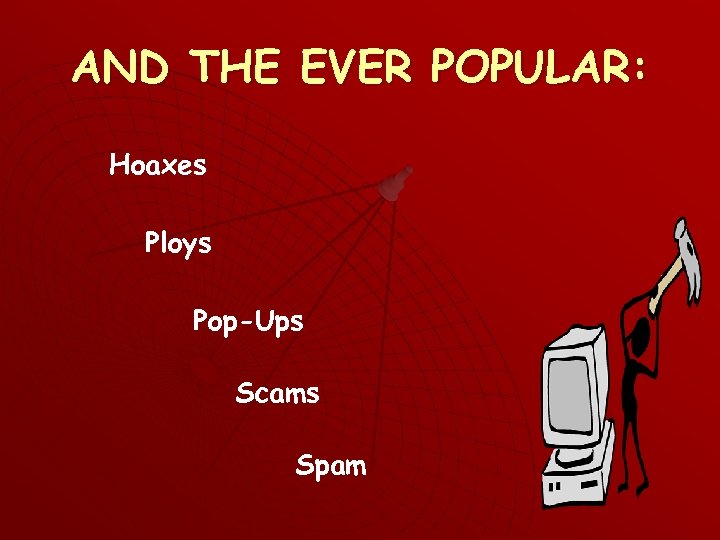 AND THE EVER POPULAR: Hoaxes Ploys Pop-Ups Scams Spam
AND THE EVER POPULAR: Hoaxes Ploys Pop-Ups Scams Spam
 DID YOU KNOW? In 1980 a computer cracked a 3 -character password within one minute. In 1999 a team of computers cracked a 56 character password within one day. In 2004 a computer virus infected 1 million computers within one hour.
DID YOU KNOW? In 1980 a computer cracked a 3 -character password within one minute. In 1999 a team of computers cracked a 56 character password within one day. In 2004 a computer virus infected 1 million computers within one hour.
 DEFINITIONS A computer program Tells a computer what to do and how to do it. Computer viruses, network worms, Trojan Horse These are computer programs.
DEFINITIONS A computer program Tells a computer what to do and how to do it. Computer viruses, network worms, Trojan Horse These are computer programs.
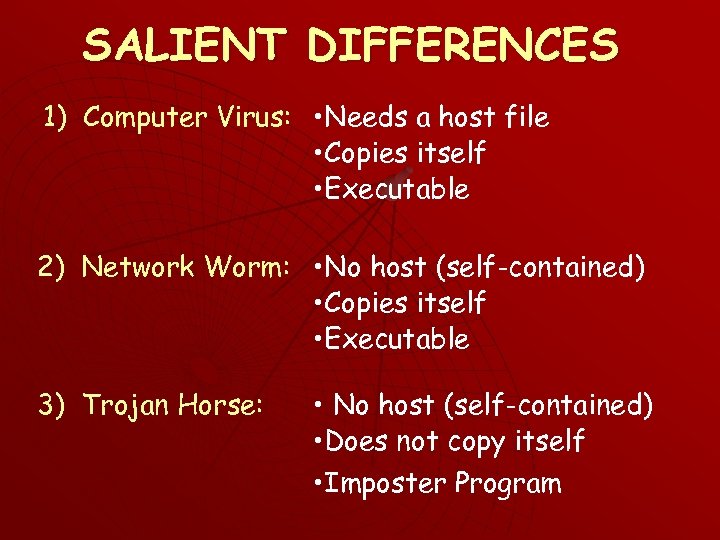 SALIENT DIFFERENCES 1) Computer Virus: • Needs a host file • Copies itself • Executable 2) Network Worm: • No host (self-contained) • Copies itself • Executable 3) Trojan Horse: • No host (self-contained) • Does not copy itself • Imposter Program
SALIENT DIFFERENCES 1) Computer Virus: • Needs a host file • Copies itself • Executable 2) Network Worm: • No host (self-contained) • Copies itself • Executable 3) Trojan Horse: • No host (self-contained) • Does not copy itself • Imposter Program
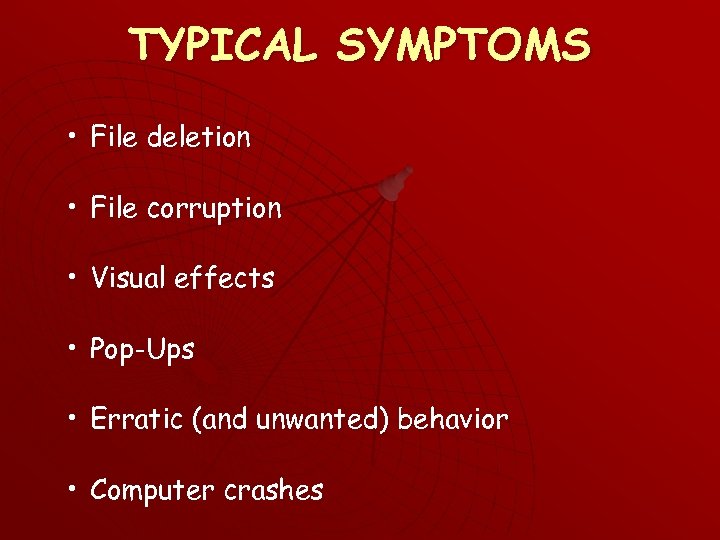 TYPICAL SYMPTOMS • File deletion • File corruption • Visual effects • Pop-Ups • Erratic (and unwanted) behavior • Computer crashes
TYPICAL SYMPTOMS • File deletion • File corruption • Visual effects • Pop-Ups • Erratic (and unwanted) behavior • Computer crashes
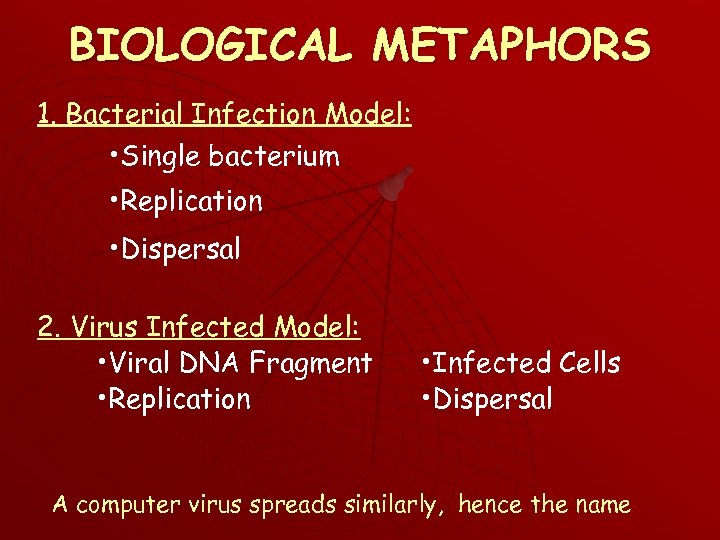 BIOLOGICAL METAPHORS 1. Bacterial Infection Model: • Single bacterium • Replication • Dispersal 2. Virus Infected Model: • Viral DNA Fragment • Replication • Infected Cells • Dispersal A computer virus spreads similarly, hence the name
BIOLOGICAL METAPHORS 1. Bacterial Infection Model: • Single bacterium • Replication • Dispersal 2. Virus Infected Model: • Viral DNA Fragment • Replication • Infected Cells • Dispersal A computer virus spreads similarly, hence the name
 WHY DO WE HAVE THIS PROBLEM? Software companies rush products to the consumer market (“No program should go online before its time…”) u Recycling old code reduces development time, but perpetuates old flaws. u
WHY DO WE HAVE THIS PROBLEM? Software companies rush products to the consumer market (“No program should go online before its time…”) u Recycling old code reduces development time, but perpetuates old flaws. u
 AND A FEW MORE REASONS u. Market share is more important than security u. Interface design is more important than security u. New feature designs are more important than security u. Ease of use is more important than security
AND A FEW MORE REASONS u. Market share is more important than security u. Interface design is more important than security u. New feature designs are more important than security u. Ease of use is more important than security
 HACKER MOTIVATIONS Attack the Evil Empire (Microsoft) Display of dominance Showing off, revenge Misdirected creativity Embezzlement, greed “Who knows what evil lurks in the hearts of men? ”
HACKER MOTIVATIONS Attack the Evil Empire (Microsoft) Display of dominance Showing off, revenge Misdirected creativity Embezzlement, greed “Who knows what evil lurks in the hearts of men? ”
 NETWORKED SYSTEMS VS SECURED SYSTEMS Some platforms are more secure than others NETWORKS SECURITY Open Communication Closed Communication Full Access Full Lockdown Managers must strike a balance
NETWORKED SYSTEMS VS SECURED SYSTEMS Some platforms are more secure than others NETWORKS SECURITY Open Communication Closed Communication Full Access Full Lockdown Managers must strike a balance
 POPULAR FALLACIES u. If I never log off then my computer can never get a virus u. If I lock my office door then my computer can never get a virus u. Companies create viruses so they can sell anti-virus software u. Microsoft me will protect will ISP me? My ct rote p
POPULAR FALLACIES u. If I never log off then my computer can never get a virus u. If I lock my office door then my computer can never get a virus u. Companies create viruses so they can sell anti-virus software u. Microsoft me will protect will ISP me? My ct rote p
 AND A FEW MORE…. u. I got this disc from my (mother, boss, friend) so it must be okay u. You cannot get a virus by opening an attachment from someone you know u. But u. I I only downloaded one file am too smart to fall for a scam u. You u. My can catch a cold from a computer virus friend who knows a lot about computers showed me this really cool site…
AND A FEW MORE…. u. I got this disc from my (mother, boss, friend) so it must be okay u. You cannot get a virus by opening an attachment from someone you know u. But u. I I only downloaded one file am too smart to fall for a scam u. You u. My can catch a cold from a computer virus friend who knows a lot about computers showed me this really cool site…
 THINGS THE LIBRARY CAN DO ACTION PLAN: • Designate security support staff (and fund them) • Make security awareness a corporate priority (and educate your staff) • Enable real-time protection • Update all vendor security patches • Subscribe to several security alert bulletins
THINGS THE LIBRARY CAN DO ACTION PLAN: • Designate security support staff (and fund them) • Make security awareness a corporate priority (and educate your staff) • Enable real-time protection • Update all vendor security patches • Subscribe to several security alert bulletins
 • Periodically reboot or re-load all computers • Control, limit or block all downloads and installs • Install anti-virus software on computers (keep it current) “It takes a carpenter to build a house but one jackass can knock it down” (Variously attributed to Mark Twain, Harry Truman, Senator Sam Rayburn)
• Periodically reboot or re-load all computers • Control, limit or block all downloads and installs • Install anti-virus software on computers (keep it current) “It takes a carpenter to build a house but one jackass can knock it down” (Variously attributed to Mark Twain, Harry Truman, Senator Sam Rayburn)
 WHAT CAN THE LIBRARIAN DO? Set bookmarks to authoritative: • anti-virus Web pages • virus hoax Web pages • public free anti-virus removal tools Provide patrons with: up-to-date information about viruses, etc. Confirm: that desktops have the latest anti-virus updates
WHAT CAN THE LIBRARIAN DO? Set bookmarks to authoritative: • anti-virus Web pages • virus hoax Web pages • public free anti-virus removal tools Provide patrons with: up-to-date information about viruses, etc. Confirm: that desktops have the latest anti-virus updates
 BACK IT UP Offline copies: Grandfather/son (monthly/weekly/daily) u u. Online copies: Shared network drive u. Changes only: Incremental/differential u. Do not back up a file on the same disc as the original! u. Assume every disc, CD, etc is suspect, no matter who gave it to you “Doveryay, No Proveryay” (Trust but Verify)
BACK IT UP Offline copies: Grandfather/son (monthly/weekly/daily) u u. Online copies: Shared network drive u. Changes only: Incremental/differential u. Do not back up a file on the same disc as the original! u. Assume every disc, CD, etc is suspect, no matter who gave it to you “Doveryay, No Proveryay” (Trust but Verify)
 MACHINE INFECTED? ACTION PLAN: 1) Write down the error or alert message 2) verbatim • inform your tech support team • quarantine the machine 2) Look up the message in an authoritative anti-virus site (demo) • diagnose the problem • take recommended remedial action
MACHINE INFECTED? ACTION PLAN: 1) Write down the error or alert message 2) verbatim • inform your tech support team • quarantine the machine 2) Look up the message in an authoritative anti-virus site (demo) • diagnose the problem • take recommended remedial action
 If appropriate: • Download, install, run the anti-virus removal tool (demo) • Apply all missing critical security patches (demo) 3) Reboot the machine • Run a full system scan before placing the machine back in service
If appropriate: • Download, install, run the anti-virus removal tool (demo) • Apply all missing critical security patches (demo) 3) Reboot the machine • Run a full system scan before placing the machine back in service
 THE HOAX STOPS HERE IF THE MESSAGE: • tells you to do something • tells you to take immediate action • cites a recognizable source to give itself credibility (“Microsoft has warned that…”) • does not originate from a valid computer vendor
THE HOAX STOPS HERE IF THE MESSAGE: • tells you to do something • tells you to take immediate action • cites a recognizable source to give itself credibility (“Microsoft has warned that…”) • does not originate from a valid computer vendor
 AND: • lacks specific verifiable contact information IF IN DOUBT, CHECK IT OUT Confirm the hoax by checking it against authoritative hoax sites Inform other staff so the hoax does not propagate
AND: • lacks specific verifiable contact information IF IN DOUBT, CHECK IT OUT Confirm the hoax by checking it against authoritative hoax sites Inform other staff so the hoax does not propagate
 POPULAR HOAXES INCLUDE: u JDBGMGR (teddy-bear icon) u. NIGERIA u$800 FROM MICROSOFT Tricks users into deleting a file Money scam Pyramid scheme
POPULAR HOAXES INCLUDE: u JDBGMGR (teddy-bear icon) u. NIGERIA u$800 FROM MICROSOFT Tricks users into deleting a file Money scam Pyramid scheme
 STOPPING THE TROJAN HORSE The Horse must be “invited in” …. How does it get in? By: Downloading a file Installing a program Opening an attachment Opening bogus Web pages Copying a file from someone else
STOPPING THE TROJAN HORSE The Horse must be “invited in” …. How does it get in? By: Downloading a file Installing a program Opening an attachment Opening bogus Web pages Copying a file from someone else
 MORE ON THE HORSE……. A Trojan Horse exploits computer ports letting its “friends” enter, and “once a thief gets into your house he opens a rear window for his partners” Security patches often close computer ports and vulnerabilities
MORE ON THE HORSE……. A Trojan Horse exploits computer ports letting its “friends” enter, and “once a thief gets into your house he opens a rear window for his partners” Security patches often close computer ports and vulnerabilities
 NOTE #1 u u u Search engines are NOT reliable sources of virus information Information may be inaccurate, incomplete or out of date Search engines generate huge numbers of indiscriminate hits Some anti-virus Web sites are scams (or contain trojan Horses) u u Go directly to authoritative anti-virus sites
NOTE #1 u u u Search engines are NOT reliable sources of virus information Information may be inaccurate, incomplete or out of date Search engines generate huge numbers of indiscriminate hits Some anti-virus Web sites are scams (or contain trojan Horses) u u Go directly to authoritative anti-virus sites
 NOTE #2 u Computer companies are NOT reliable sources of virus information Computer companies: Usually refer you to an anti-virus vendor uare not in the anti-virus business uthemselves are victims! u
NOTE #2 u Computer companies are NOT reliable sources of virus information Computer companies: Usually refer you to an anti-virus vendor uare not in the anti-virus business uthemselves are victims! u
 ONLINE RESOURCES Authoritative Hoax Information u u securityresponse. symantec. com/avcenter/hoax. html vil. mcafeesecurity. com/vil/hoaxes. asp Authoritative Anti-Virus Vendor Information u u securityresponse. symantec. com/avcenter/vinf odb. html www. mcafeesecurity. com/us/security/vil. htm
ONLINE RESOURCES Authoritative Hoax Information u u securityresponse. symantec. com/avcenter/hoax. html vil. mcafeesecurity. com/vil/hoaxes. asp Authoritative Anti-Virus Vendor Information u u securityresponse. symantec. com/avcenter/vinf odb. html www. mcafeesecurity. com/us/security/vil. htm
 REFERENCES Authoritative Security Alert Information u securityresponse. symantec. com/ (Symantec) www. microsoft. com/security (Microsoft) u www. apple. com/support/security/ (Apple) u
REFERENCES Authoritative Security Alert Information u securityresponse. symantec. com/ (Symantec) www. microsoft. com/security (Microsoft) u www. apple. com/support/security/ (Apple) u
 Authoritative Anti-Virus Organizations u u u www. cert. org (Computer Emergency Response Team-CMU) www. ciac. org/ciac (CIAC-Department of Energy) www. sans. org/aboutsans. php (Server and Network Security) www. first. org (Forum of Incident Response and Security Teams) www. cirt. rutgers. edu (Computing Incident Response Team-Rutgers)
Authoritative Anti-Virus Organizations u u u www. cert. org (Computer Emergency Response Team-CMU) www. ciac. org/ciac (CIAC-Department of Energy) www. sans. org/aboutsans. php (Server and Network Security) www. first. org (Forum of Incident Response and Security Teams) www. cirt. rutgers. edu (Computing Incident Response Team-Rutgers)
 Authoritative Free Public Anti-Virus Removal Tool Information u u securityresponse. symantec. com/avcenter/tools. list. html vil. nai. com/vil/averttools. asp mssg. rutgers. edu/documentation/viruses (Rutgers) some professional library sites have pointers to reliable anti-virus information
Authoritative Free Public Anti-Virus Removal Tool Information u u securityresponse. symantec. com/avcenter/tools. list. html vil. nai. com/vil/averttools. asp mssg. rutgers. edu/documentation/viruses (Rutgers) some professional library sites have pointers to reliable anti-virus information
 PRINT RESOURCES Allen, Julia, (2001) The CERT Guide to System and Network Security Practices, Addison-Wesley, New York u Crume, Jeff, (2000) Inside Internet Security, Addison-Wesley, New York u Ratzan, Lee, (January 2005) A new role for libraries, SC Magazine (Secure Computing Magazine), page 26 u
PRINT RESOURCES Allen, Julia, (2001) The CERT Guide to System and Network Security Practices, Addison-Wesley, New York u Crume, Jeff, (2000) Inside Internet Security, Addison-Wesley, New York u Ratzan, Lee, (January 2005) A new role for libraries, SC Magazine (Secure Computing Magazine), page 26 u
 u Ratzan, Lee, (2004) Understanding Information Systems, American Library Association, Chicago
u Ratzan, Lee, (2004) Understanding Information Systems, American Library Association, Chicago
 A NEW ROLE FOR LIBRARIES?
A NEW ROLE FOR LIBRARIES?
 THE AUTHOR ACKNOWLEDGES The cooperation of Info. Link (www. infolink. org) for promoting library professional development programs u The Monroe Public Library for the use of its facilities u SC Magazine for publishing an essay on libraries being at the forefront of information security u Lisa De. Bilio for her production of the Power. Point slides. u THANK YOU ALL
THE AUTHOR ACKNOWLEDGES The cooperation of Info. Link (www. infolink. org) for promoting library professional development programs u The Monroe Public Library for the use of its facilities u SC Magazine for publishing an essay on libraries being at the forefront of information security u Lisa De. Bilio for her production of the Power. Point slides. u THANK YOU ALL


