1bc7aa29c1e59a1ba117b24eb6e2b638.ppt
- Количество слайдов: 29
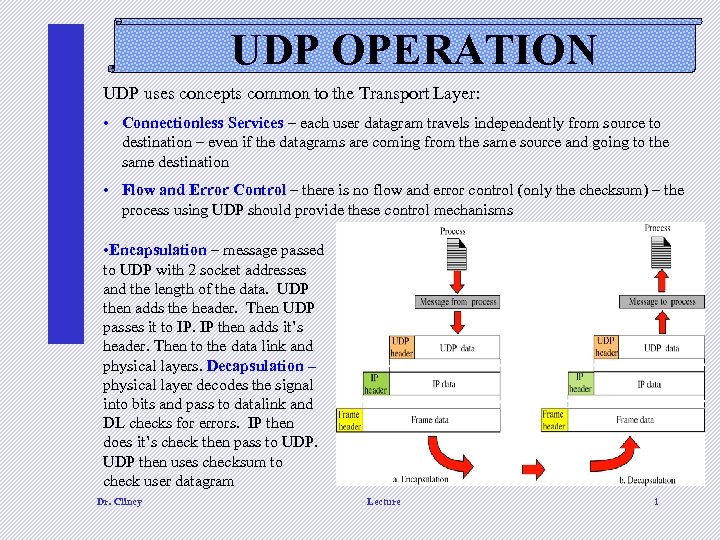 UDP OPERATION UDP uses concepts common to the Transport Layer: • Connectionless Services – each user datagram travels independently from source to destination – even if the datagrams are coming from the same source and going to the same destination • Flow and Error Control – there is no flow and error control (only the checksum) – the process using UDP should provide these control mechanisms • Encapsulation – message passed to UDP with 2 socket addresses and the length of the data. UDP then adds the header. Then UDP passes it to IP. IP then adds it’s header. Then to the data link and physical layers. Decapsulation – physical layer decodes the signal into bits and pass to datalink and DL checks for errors. IP then does it’s check then pass to UDP then uses checksum to check user datagram Dr. Clincy Lecture 1
UDP OPERATION UDP uses concepts common to the Transport Layer: • Connectionless Services – each user datagram travels independently from source to destination – even if the datagrams are coming from the same source and going to the same destination • Flow and Error Control – there is no flow and error control (only the checksum) – the process using UDP should provide these control mechanisms • Encapsulation – message passed to UDP with 2 socket addresses and the length of the data. UDP then adds the header. Then UDP passes it to IP. IP then adds it’s header. Then to the data link and physical layers. Decapsulation – physical layer decodes the signal into bits and pass to datalink and DL checks for errors. IP then does it’s check then pass to UDP then uses checksum to check user datagram Dr. Clincy Lecture 1
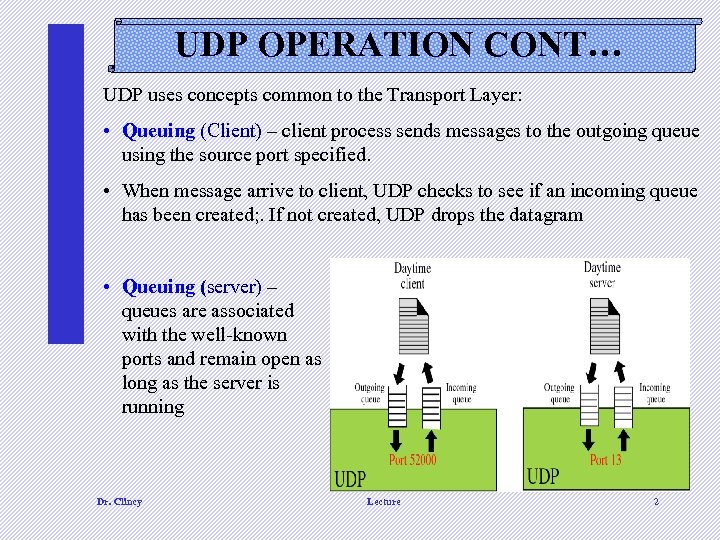 UDP OPERATION CONT… UDP uses concepts common to the Transport Layer: • Queuing (Client) – client process sends messages to the outgoing queue using the source port specified. • When message arrive to client, UDP checks to see if an incoming queue has been created; . If not created, UDP drops the datagram • Queuing (server) – queues are associated with the well-known ports and remain open as long as the server is running Dr. Clincy Lecture 2
UDP OPERATION CONT… UDP uses concepts common to the Transport Layer: • Queuing (Client) – client process sends messages to the outgoing queue using the source port specified. • When message arrive to client, UDP checks to see if an incoming queue has been created; . If not created, UDP drops the datagram • Queuing (server) – queues are associated with the well-known ports and remain open as long as the server is running Dr. Clincy Lecture 2
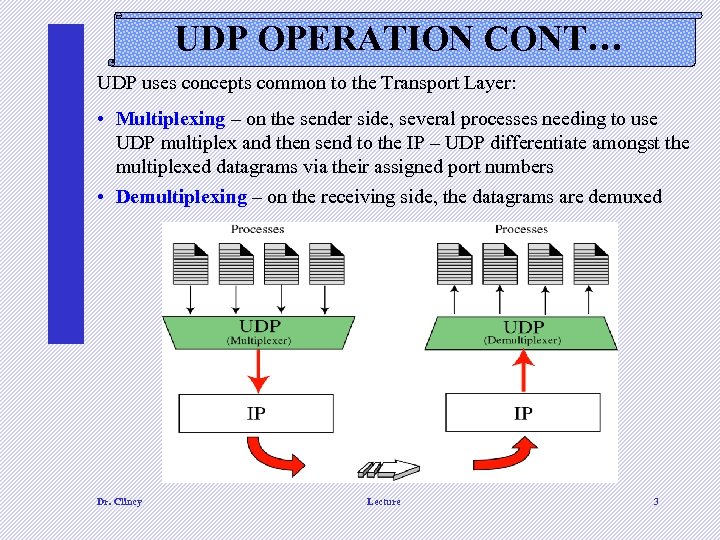 UDP OPERATION CONT… UDP uses concepts common to the Transport Layer: • Multiplexing – on the sender side, several processes needing to use UDP multiplex and then send to the IP – UDP differentiate amongst the multiplexed datagrams via their assigned port numbers • Demultiplexing – on the receiving side, the datagrams are demuxed Dr. Clincy Lecture 3
UDP OPERATION CONT… UDP uses concepts common to the Transport Layer: • Multiplexing – on the sender side, several processes needing to use UDP multiplex and then send to the IP – UDP differentiate amongst the multiplexed datagrams via their assigned port numbers • Demultiplexing – on the receiving side, the datagrams are demuxed Dr. Clincy Lecture 3
 Transmission Control Protocol (TCP) Dr. Clincy Lecture 4
Transmission Control Protocol (TCP) Dr. Clincy Lecture 4
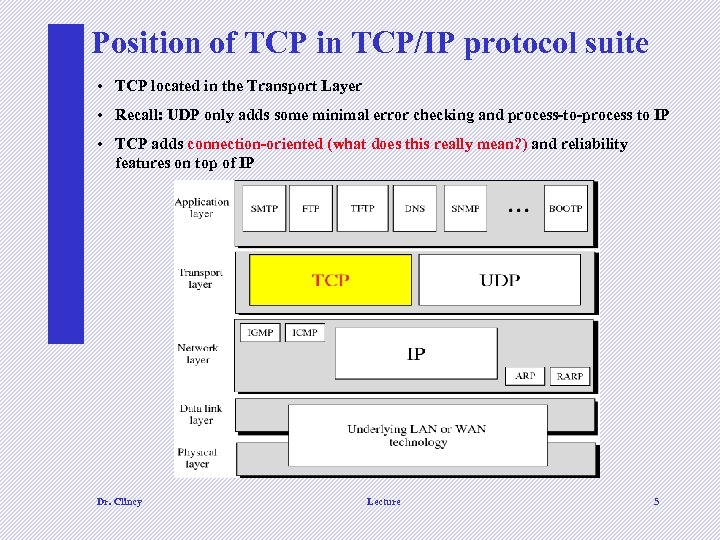 Position of TCP in TCP/IP protocol suite • TCP located in the Transport Layer • Recall: UDP only adds some minimal error checking and process-to-process to IP • TCP adds connection-oriented (what does this really mean? ) and reliability features on top of IP Dr. Clincy Lecture 5
Position of TCP in TCP/IP protocol suite • TCP located in the Transport Layer • Recall: UDP only adds some minimal error checking and process-to-process to IP • TCP adds connection-oriented (what does this really mean? ) and reliability features on top of IP Dr. Clincy Lecture 5
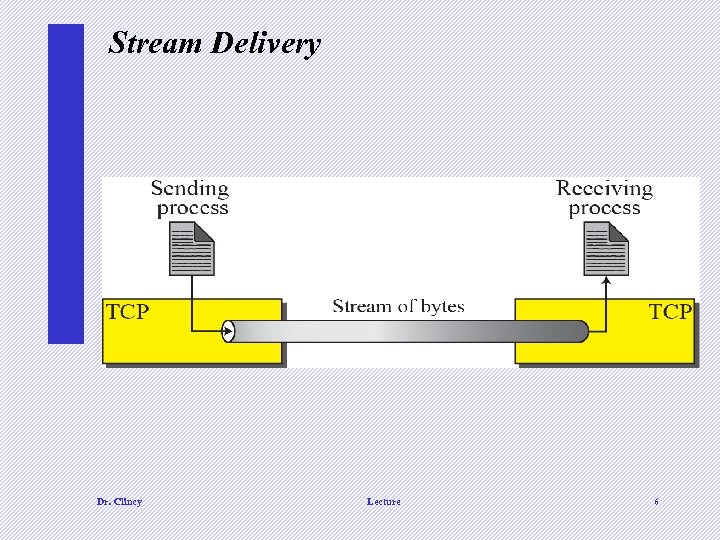 Stream Delivery Dr. Clincy Lecture 6
Stream Delivery Dr. Clincy Lecture 6
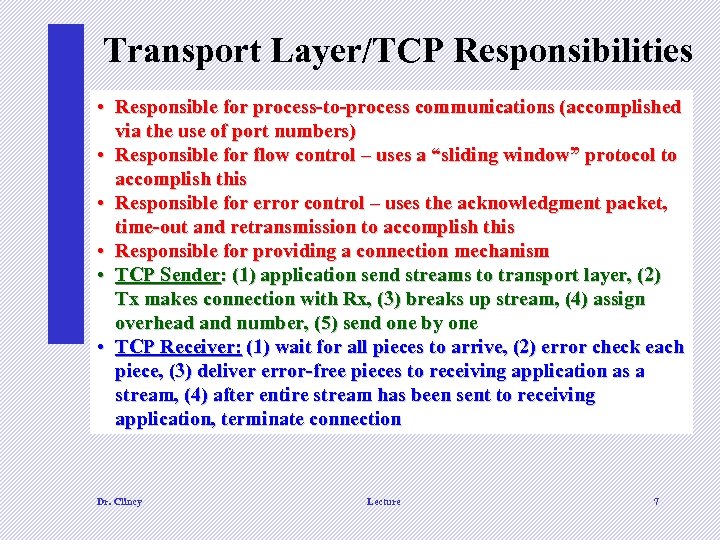 Transport Layer/TCP Responsibilities • Responsible for process-to-process communications (accomplished via the use of port numbers) • Responsible for flow control – uses a “sliding window” protocol to accomplish this • Responsible for error control – uses the acknowledgment packet, time-out and retransmission to accomplish this • Responsible for providing a connection mechanism • TCP Sender: (1) application send streams to transport layer, (2) Tx makes connection with Rx, (3) breaks up stream, (4) assign overhead and number, (5) send one by one • TCP Receiver: (1) wait for all pieces to arrive, (2) error check each piece, (3) deliver error-free pieces to receiving application as a stream, (4) after entire stream has been sent to receiving application, terminate connection Dr. Clincy Lecture 7
Transport Layer/TCP Responsibilities • Responsible for process-to-process communications (accomplished via the use of port numbers) • Responsible for flow control – uses a “sliding window” protocol to accomplish this • Responsible for error control – uses the acknowledgment packet, time-out and retransmission to accomplish this • Responsible for providing a connection mechanism • TCP Sender: (1) application send streams to transport layer, (2) Tx makes connection with Rx, (3) breaks up stream, (4) assign overhead and number, (5) send one by one • TCP Receiver: (1) wait for all pieces to arrive, (2) error check each piece, (3) deliver error-free pieces to receiving application as a stream, (4) after entire stream has been sent to receiving application, terminate connection Dr. Clincy Lecture 7
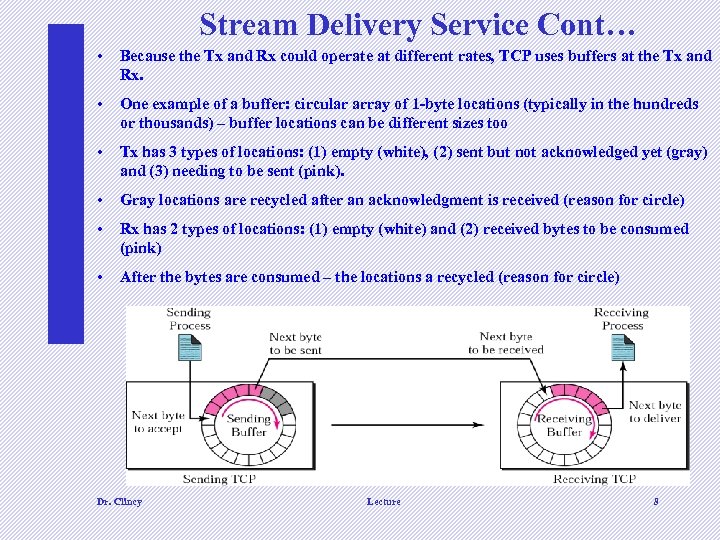 Stream Delivery Service Cont… • Because the Tx and Rx could operate at different rates, TCP uses buffers at the Tx and Rx. • One example of a buffer: circular array of 1 -byte locations (typically in the hundreds or thousands) – buffer locations can be different sizes too • Tx has 3 types of locations: (1) empty (white), (2) sent but not acknowledged yet (gray) and (3) needing to be sent (pink). • Gray locations are recycled after an acknowledgment is received (reason for circle) • Rx has 2 types of locations: (1) empty (white) and (2) received bytes to be consumed (pink) • After the bytes are consumed – the locations a recycled (reason for circle) Dr. Clincy Lecture 8
Stream Delivery Service Cont… • Because the Tx and Rx could operate at different rates, TCP uses buffers at the Tx and Rx. • One example of a buffer: circular array of 1 -byte locations (typically in the hundreds or thousands) – buffer locations can be different sizes too • Tx has 3 types of locations: (1) empty (white), (2) sent but not acknowledged yet (gray) and (3) needing to be sent (pink). • Gray locations are recycled after an acknowledgment is received (reason for circle) • Rx has 2 types of locations: (1) empty (white) and (2) received bytes to be consumed (pink) • After the bytes are consumed – the locations a recycled (reason for circle) Dr. Clincy Lecture 8
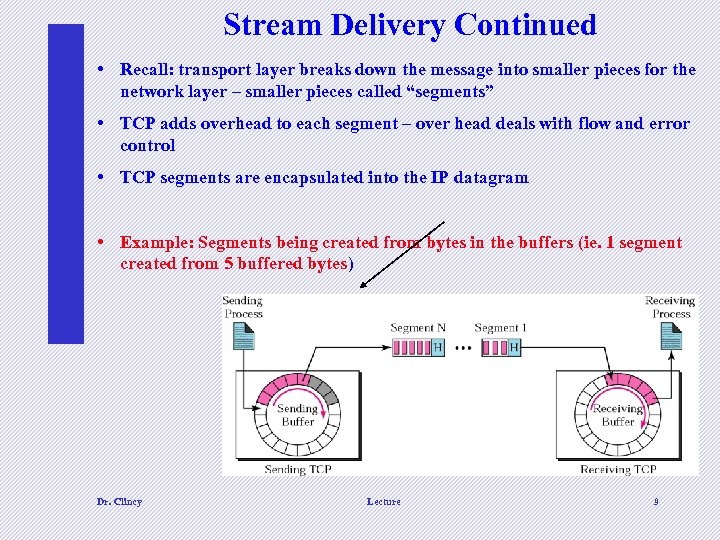 Stream Delivery Continued • Recall: transport layer breaks down the message into smaller pieces for the network layer – smaller pieces called “segments” • TCP adds overhead to each segment – over head deals with flow and error control • TCP segments are encapsulated into the IP datagram • Example: Segments being created from bytes in the buffers (ie. 1 segment created from 5 buffered bytes) Dr. Clincy Lecture 9
Stream Delivery Continued • Recall: transport layer breaks down the message into smaller pieces for the network layer – smaller pieces called “segments” • TCP adds overhead to each segment – over head deals with flow and error control • TCP segments are encapsulated into the IP datagram • Example: Segments being created from bytes in the buffers (ie. 1 segment created from 5 buffered bytes) Dr. Clincy Lecture 9
 NUMBERING BYTES • TCP keeps track of segments using numbers relating to the bytes versus the segments • Sequence number and Acknowledgment Number are used and relate to the byte • The start number is randomly generated (versus always being 0) • For example, suppose 1057 is generated and let’s say 6000 bytes need to be sent – the numbering will range from 1057 to 7056 • Byte numbering is also used for flow and error control • After the bytes are numbered, TCP assigns a sequence # to each segment – the sequence # is the first byte number of the segment • The acknowledgment # is sequence # incremented each time a byte is received (ie. take a 4 -byte segment with starting sequence # 11, when byte 11 received, ack #=12, when byte 12 received, ack # = 13, etc. . ) Dr. Clincy Lecture 10
NUMBERING BYTES • TCP keeps track of segments using numbers relating to the bytes versus the segments • Sequence number and Acknowledgment Number are used and relate to the byte • The start number is randomly generated (versus always being 0) • For example, suppose 1057 is generated and let’s say 6000 bytes need to be sent – the numbering will range from 1057 to 7056 • Byte numbering is also used for flow and error control • After the bytes are numbered, TCP assigns a sequence # to each segment – the sequence # is the first byte number of the segment • The acknowledgment # is sequence # incremented each time a byte is received (ie. take a 4 -byte segment with starting sequence # 11, when byte 11 received, ack #=12, when byte 12 received, ack # = 13, etc. . ) Dr. Clincy Lecture 10
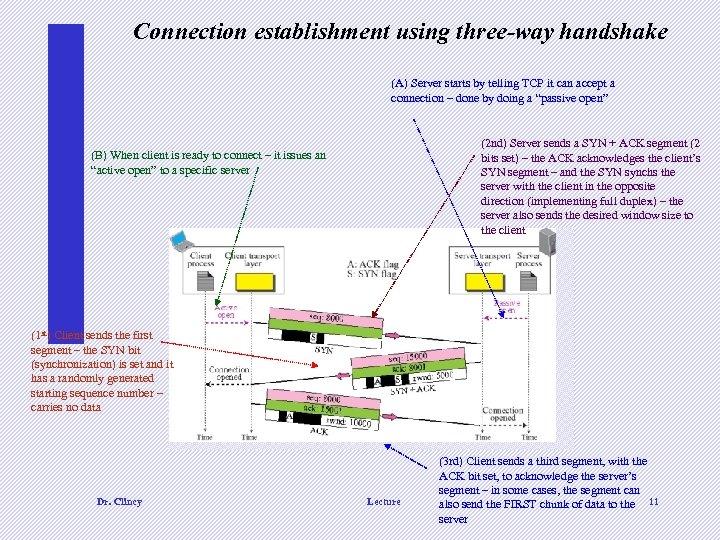 Connection establishment using three-way handshake (A) Server starts by telling TCP it can accept a connection – done by doing a “passive open” (2 nd) Server sends a SYN + ACK segment (2 bits set) – the ACK acknowledges the client’s SYN segment – and the SYN synchs the server with the client in the opposite direction (implementing full duplex) – the server also sends the desired window size to the client (B) When client is ready to connect – it issues an “active open” to a specific server (1 st) Client sends the first segment – the SYN bit (synchronization) is set and it has a randomly generated starting sequence number – carries no data Dr. Clincy Lecture (3 rd) Client sends a third segment, with the ACK bit set, to acknowledge the server’s segment – in some cases, the segment can also send the FIRST chunk of data to the 11 server
Connection establishment using three-way handshake (A) Server starts by telling TCP it can accept a connection – done by doing a “passive open” (2 nd) Server sends a SYN + ACK segment (2 bits set) – the ACK acknowledges the client’s SYN segment – and the SYN synchs the server with the client in the opposite direction (implementing full duplex) – the server also sends the desired window size to the client (B) When client is ready to connect – it issues an “active open” to a specific server (1 st) Client sends the first segment – the SYN bit (synchronization) is set and it has a randomly generated starting sequence number – carries no data Dr. Clincy Lecture (3 rd) Client sends a third segment, with the ACK bit set, to acknowledge the server’s segment – in some cases, the segment can also send the FIRST chunk of data to the 11 server
 TCP - FLOW CONTROL • Flow Control – amount of data a Tx sends before receiving an acknowledgment from the Rx • Can send too much and overwhelm routers and etc. . • Can send too little and Tx stays idle too much waiting for acknowledgments • TCP defines a “window” that’s imposed on the buffer of data delivered • A sliding window is used to make transmission more efficient as well as to control the flow of data so that the destination does not become overwhelmed with data. • TCP’s sliding windows are byte oriented. Dr. Clincy Lecture 12
TCP - FLOW CONTROL • Flow Control – amount of data a Tx sends before receiving an acknowledgment from the Rx • Can send too much and overwhelm routers and etc. . • Can send too little and Tx stays idle too much waiting for acknowledgments • TCP defines a “window” that’s imposed on the buffer of data delivered • A sliding window is used to make transmission more efficient as well as to control the flow of data so that the destination does not become overwhelmed with data. • TCP’s sliding windows are byte oriented. Dr. Clincy Lecture 12
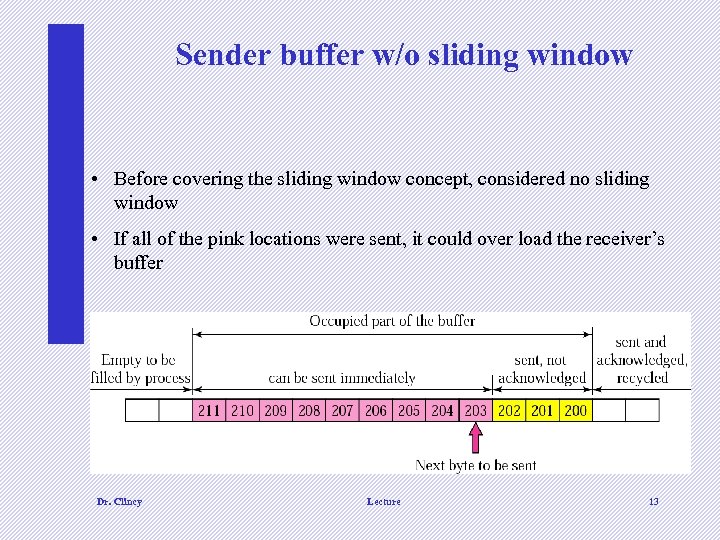 Sender buffer w/o sliding window • Before covering the sliding window concept, considered no sliding window • If all of the pink locations were sent, it could over load the receiver’s buffer Dr. Clincy Lecture 13
Sender buffer w/o sliding window • Before covering the sliding window concept, considered no sliding window • If all of the pink locations were sent, it could over load the receiver’s buffer Dr. Clincy Lecture 13
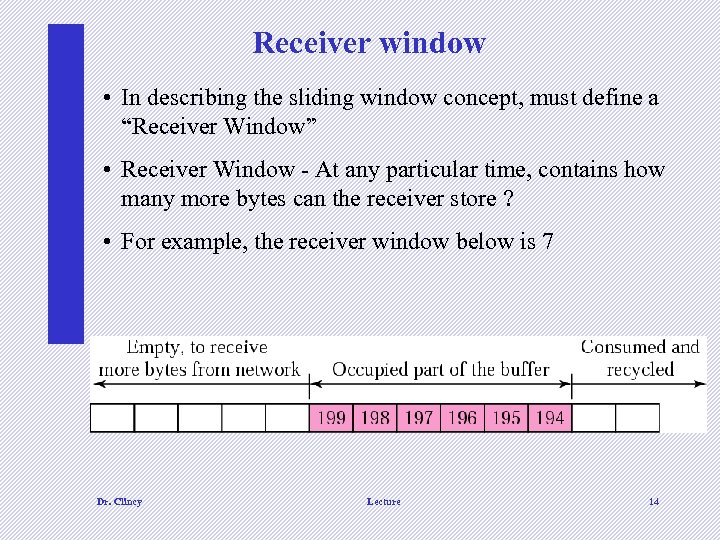 Receiver window • In describing the sliding window concept, must define a “Receiver Window” • Receiver Window - At any particular time, contains how many more bytes can the receiver store ? • For example, the receiver window below is 7 Dr. Clincy Lecture 14
Receiver window • In describing the sliding window concept, must define a “Receiver Window” • Receiver Window - At any particular time, contains how many more bytes can the receiver store ? • For example, the receiver window below is 7 Dr. Clincy Lecture 14
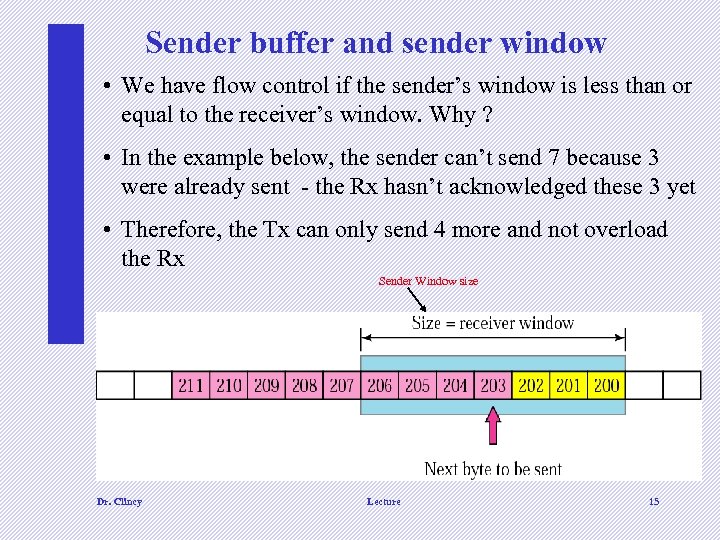 Sender buffer and sender window • We have flow control if the sender’s window is less than or equal to the receiver’s window. Why ? • In the example below, the sender can’t send 7 because 3 were already sent - the Rx hasn’t acknowledged these 3 yet • Therefore, the Tx can only send 4 more and not overload the Rx Sender Window size Dr. Clincy Lecture 15
Sender buffer and sender window • We have flow control if the sender’s window is less than or equal to the receiver’s window. Why ? • In the example below, the sender can’t send 7 because 3 were already sent - the Rx hasn’t acknowledged these 3 yet • Therefore, the Tx can only send 4 more and not overload the Rx Sender Window size Dr. Clincy Lecture 15
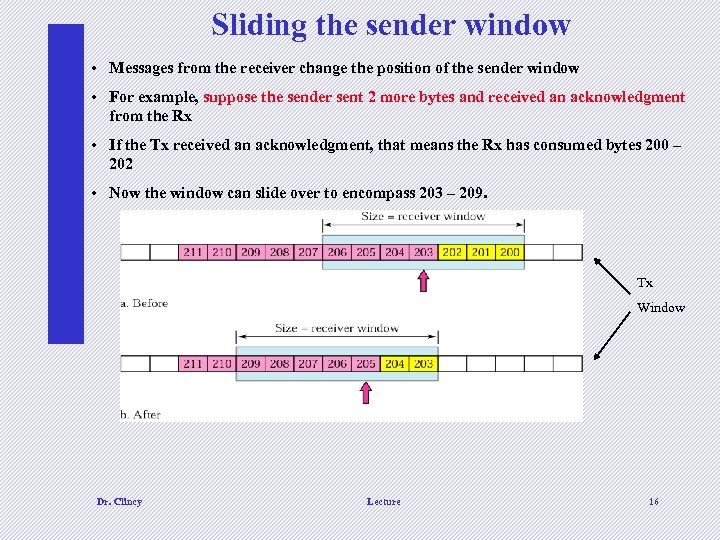 Sliding the sender window • Messages from the receiver change the position of the sender window • For example, suppose the sender sent 2 more bytes and received an acknowledgment from the Rx • If the Tx received an acknowledgment, that means the Rx has consumed bytes 200 – 202 • Now the window can slide over to encompass 203 – 209. Tx Window Dr. Clincy Lecture 16
Sliding the sender window • Messages from the receiver change the position of the sender window • For example, suppose the sender sent 2 more bytes and received an acknowledgment from the Rx • If the Tx received an acknowledgment, that means the Rx has consumed bytes 200 – 202 • Now the window can slide over to encompass 203 – 209. Tx Window Dr. Clincy Lecture 16
 Expanding the sender window If the receiver consumes data faster than it receives, the size of the receiver window expands – this is relayed to the Tx and it’s window is expanded too. Vice versa, If the receiver consumes data slower than it receives, the size of the receiver window shrinks – this is relayed to the Tx and it’s window is reduced too. NOTE: if the Rx is full, the Tx closes it’s window until Rx window is non-zero Dr. Clincy Lecture 17
Expanding the sender window If the receiver consumes data faster than it receives, the size of the receiver window expands – this is relayed to the Tx and it’s window is expanded too. Vice versa, If the receiver consumes data slower than it receives, the size of the receiver window shrinks – this is relayed to the Tx and it’s window is reduced too. NOTE: if the Rx is full, the Tx closes it’s window until Rx window is non-zero Dr. Clincy Lecture 17
 In TCP, the sender window size is totally controlled by the receiver window value. However, the sender’s actual window size can be smaller if there is congestion in the network. Dr. Clincy Lecture 18
In TCP, the sender window size is totally controlled by the receiver window value. However, the sender’s actual window size can be smaller if there is congestion in the network. Dr. Clincy Lecture 18
 Some Points about TCP’s Sliding Windows: 1. The source does not have to send a full window’s worth of data. 2. The size of the window can be increased or decreased by the destination. 3. The destination can send an acknowledgment at any time. Dr. Clincy Lecture 19
Some Points about TCP’s Sliding Windows: 1. The source does not have to send a full window’s worth of data. 2. The size of the window can be increased or decreased by the destination. 3. The destination can send an acknowledgment at any time. Dr. Clincy Lecture 19
 SILLY WINDOW SYNDROME • If the Tx application created data slowly, data would be sent in smaller segments – not enough data to create larger segments • If the Rx application consumed data slowly, the data would be sent in smaller segments in not overloading the Rx. • In either case, network capacity efficiency would be reduced – poor use of network capacity • This is called “Silly Window Syndrome” – why is it “silly” ? ? Dr. Clincy Lecture 20
SILLY WINDOW SYNDROME • If the Tx application created data slowly, data would be sent in smaller segments – not enough data to create larger segments • If the Rx application consumed data slowly, the data would be sent in smaller segments in not overloading the Rx. • In either case, network capacity efficiency would be reduced – poor use of network capacity • This is called “Silly Window Syndrome” – why is it “silly” ? ? Dr. Clincy Lecture 20
 Explain the Following How Transport-level flow control works with Data Link-level flow control Dr. Clincy Lecture 21
Explain the Following How Transport-level flow control works with Data Link-level flow control Dr. Clincy Lecture 21
 ERROR CONTROL • TCP provides reliability using error control • TCP can detect corrupted segments, lost segments, out-of-order segments and duplicated segments • TCP also has a mechanism in correcting detected errors Error Detection • Error Detection is achieved through 3 tools: (1) checksum, (2) acknowledgment and (3) time-out • Checksum – checksum is used to determine if a segment is corrupted (recall) – if segment is corrupted, it’s dropped • Acknowledgement – acknowledgement is sent by the Rx when the segment is received • If no acknowledgement is received by the Tx before the time-out timer counts down, then it’s assumed the segment is corrupted or lost Error Correction • Re-transmit if error is detected Dr. Clincy Lecture 22
ERROR CONTROL • TCP provides reliability using error control • TCP can detect corrupted segments, lost segments, out-of-order segments and duplicated segments • TCP also has a mechanism in correcting detected errors Error Detection • Error Detection is achieved through 3 tools: (1) checksum, (2) acknowledgment and (3) time-out • Checksum – checksum is used to determine if a segment is corrupted (recall) – if segment is corrupted, it’s dropped • Acknowledgement – acknowledgement is sent by the Rx when the segment is received • If no acknowledgement is received by the Tx before the time-out timer counts down, then it’s assumed the segment is corrupted or lost Error Correction • Re-transmit if error is detected Dr. Clincy Lecture 22
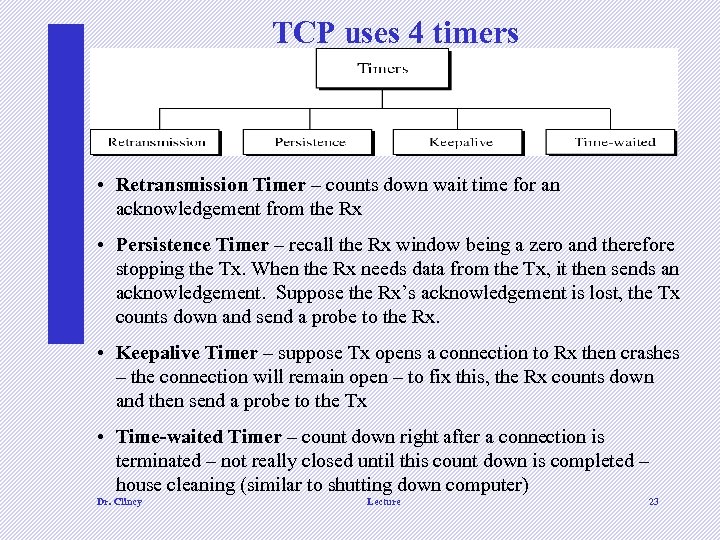 TCP uses 4 timers • Retransmission Timer – counts down wait time for an acknowledgement from the Rx • Persistence Timer – recall the Rx window being a zero and therefore stopping the Tx. When the Rx needs data from the Tx, it then sends an acknowledgement. Suppose the Rx’s acknowledgement is lost, the Tx counts down and send a probe to the Rx. • Keepalive Timer – suppose Tx opens a connection to Rx then crashes – the connection will remain open – to fix this, the Rx counts down and then send a probe to the Tx • Time-waited Timer – count down right after a connection is terminated – not really closed until this count down is completed – house cleaning (similar to shutting down computer) Dr. Clincy Lecture 23
TCP uses 4 timers • Retransmission Timer – counts down wait time for an acknowledgement from the Rx • Persistence Timer – recall the Rx window being a zero and therefore stopping the Tx. When the Rx needs data from the Tx, it then sends an acknowledgement. Suppose the Rx’s acknowledgement is lost, the Tx counts down and send a probe to the Rx. • Keepalive Timer – suppose Tx opens a connection to Rx then crashes – the connection will remain open – to fix this, the Rx counts down and then send a probe to the Tx • Time-waited Timer – count down right after a connection is terminated – not really closed until this count down is completed – house cleaning (similar to shutting down computer) Dr. Clincy Lecture 23
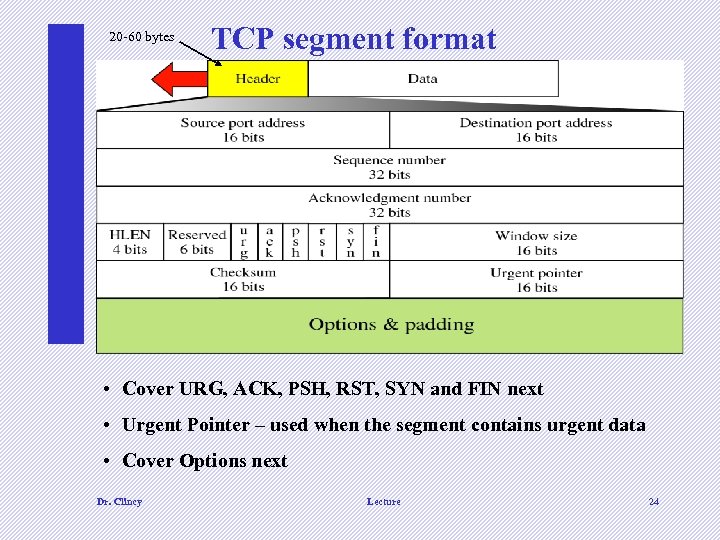 20 -60 bytes TCP segment format • Cover URG, ACK, PSH, RST, SYN and FIN next • Urgent Pointer – used when the segment contains urgent data • Cover Options next Dr. Clincy Lecture 24
20 -60 bytes TCP segment format • Cover URG, ACK, PSH, RST, SYN and FIN next • Urgent Pointer – used when the segment contains urgent data • Cover Options next Dr. Clincy Lecture 24
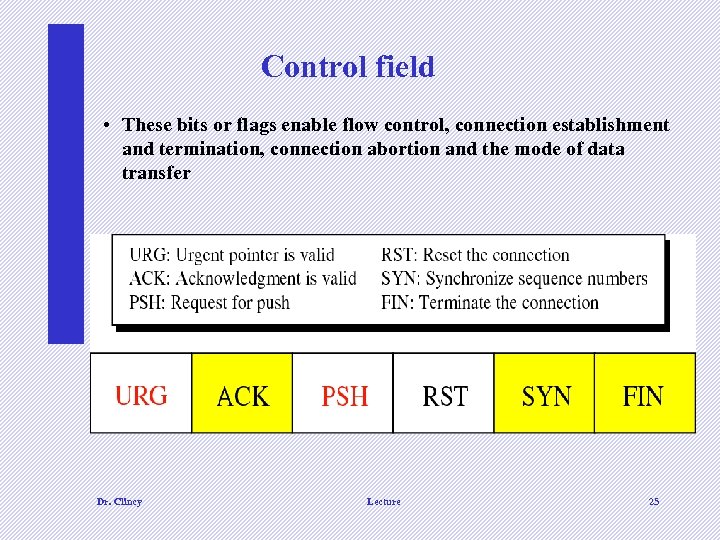 Control field • These bits or flags enable flow control, connection establishment and termination, connection abortion and the mode of data transfer Dr. Clincy Lecture 25
Control field • These bits or flags enable flow control, connection establishment and termination, connection abortion and the mode of data transfer Dr. Clincy Lecture 25
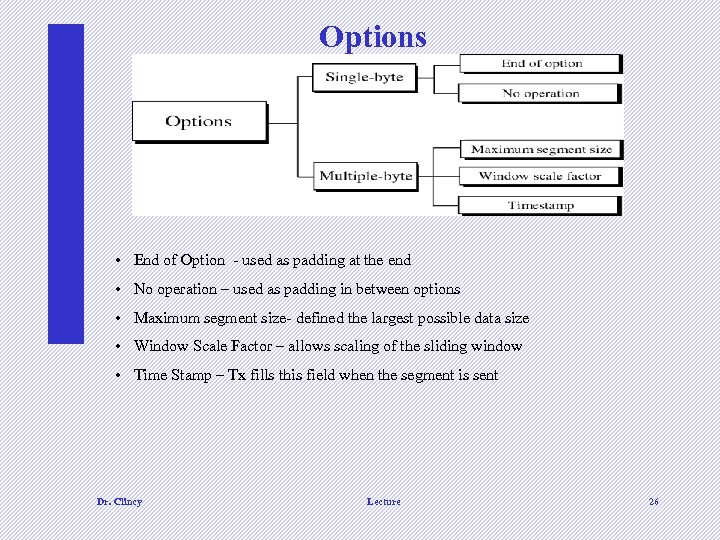 Options • End of Option - used as padding at the end • No operation – used as padding in between options • Maximum segment size- defined the largest possible data size • Window Scale Factor – allows scaling of the sliding window • Time Stamp – Tx fills this field when the segment is sent Dr. Clincy Lecture 26
Options • End of Option - used as padding at the end • No operation – used as padding in between options • Maximum segment size- defined the largest possible data size • Window Scale Factor – allows scaling of the sliding window • Time Stamp – Tx fills this field when the segment is sent Dr. Clincy Lecture 26
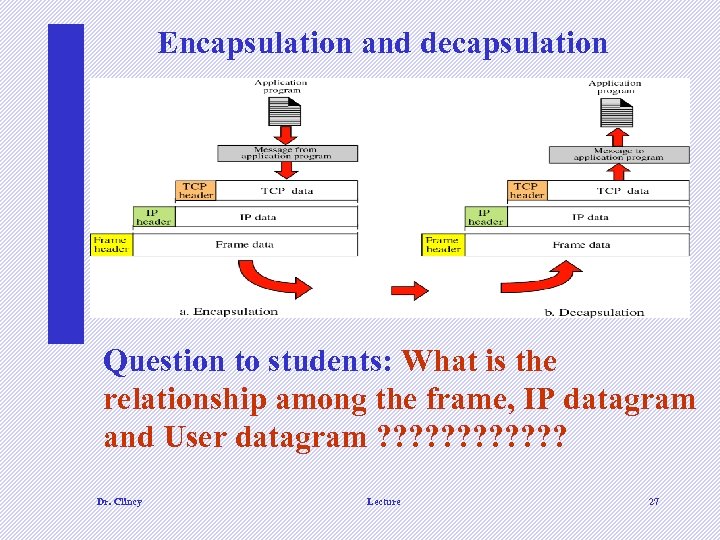 Encapsulation and decapsulation Question to students: What is the relationship among the frame, IP datagram and User datagram ? ? ? Dr. Clincy Lecture 27
Encapsulation and decapsulation Question to students: What is the relationship among the frame, IP datagram and User datagram ? ? ? Dr. Clincy Lecture 27
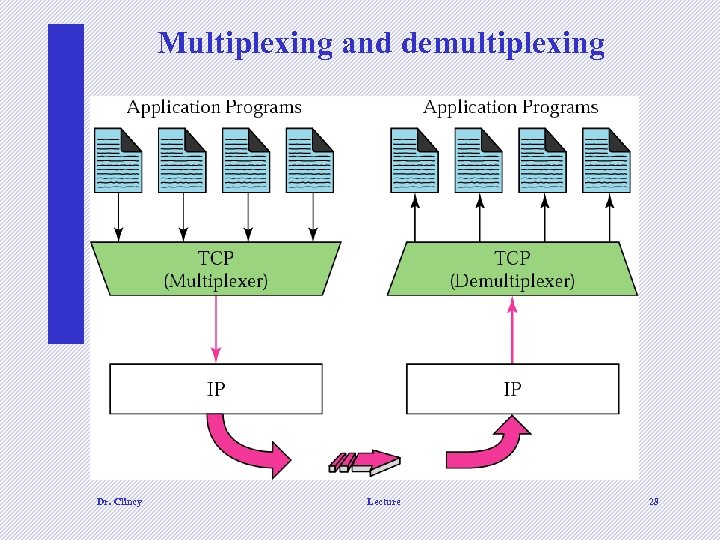 Multiplexing and demultiplexing Dr. Clincy Lecture 28
Multiplexing and demultiplexing Dr. Clincy Lecture 28
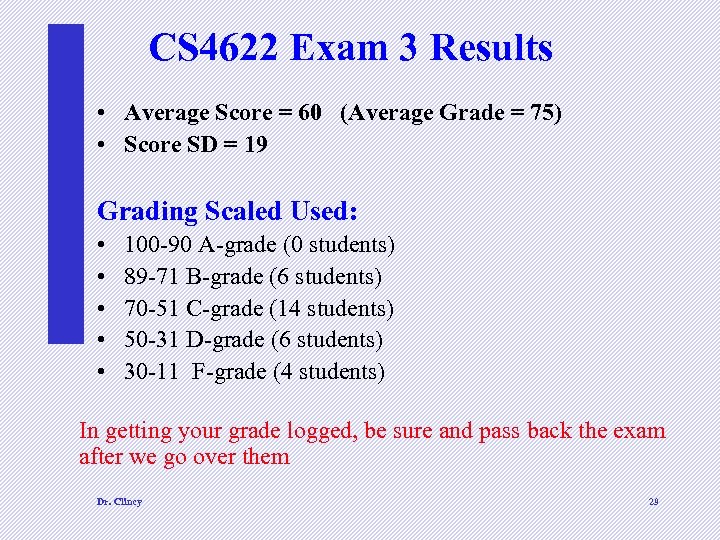 CS 4622 Exam 3 Results • Average Score = 60 (Average Grade = 75) • Score SD = 19 Grading Scaled Used: • • • 100 -90 A-grade (0 students) 89 -71 B-grade (6 students) 70 -51 C-grade (14 students) 50 -31 D-grade (6 students) 30 -11 F-grade (4 students) In getting your grade logged, be sure and pass back the exam after we go over them Dr. Clincy 29
CS 4622 Exam 3 Results • Average Score = 60 (Average Grade = 75) • Score SD = 19 Grading Scaled Used: • • • 100 -90 A-grade (0 students) 89 -71 B-grade (6 students) 70 -51 C-grade (14 students) 50 -31 D-grade (6 students) 30 -11 F-grade (4 students) In getting your grade logged, be sure and pass back the exam after we go over them Dr. Clincy 29


