42624d1fbfb7f971f1795b86fb9cbfd1.ppt
- Количество слайдов: 72
 UCDavis, ecs 251 Fall 2007 Trust and Reputation System S. Felix Wu University of California, Davis wu@cs. ucdavis. edu http: //www. cs. ucdavis. edu/~wu/ 11/29/2007 Trust and Reputation System 1
UCDavis, ecs 251 Fall 2007 Trust and Reputation System S. Felix Wu University of California, Davis wu@cs. ucdavis. edu http: //www. cs. ucdavis. edu/~wu/ 11/29/2007 Trust and Reputation System 1
 UCDavis, ecs 251 Fall 2007 Computational Trust Attribute representing a trust relationship between two directly communicating entities 11/29/2007 Trust and Reputation System 2
UCDavis, ecs 251 Fall 2007 Computational Trust Attribute representing a trust relationship between two directly communicating entities 11/29/2007 Trust and Reputation System 2
 UCDavis, ecs 251 Fall 2007 Computational Trust • Trust Values – I “trust” him “ 50/50”. – I trust him “ 0. 715” • Partial Ordering Relationship – “I trust Alice more (than Bob)” – “I trust Alice more than the set threshold of my spam mail filter” 11/29/2007 Trust and Reputation System 3
UCDavis, ecs 251 Fall 2007 Computational Trust • Trust Values – I “trust” him “ 50/50”. – I trust him “ 0. 715” • Partial Ordering Relationship – “I trust Alice more (than Bob)” – “I trust Alice more than the set threshold of my spam mail filter” 11/29/2007 Trust and Reputation System 3
 UCDavis, ecs 251 Fall 2007 Trust Ordering • Trust Ordering – I trust you, otherwise, I don’t. • Information-based Ordering – I trust you, I don’t, or I don’t know based on the information I have currently. – Dynamics and Uncertainty 11/29/2007 Trust and Reputation System 4
UCDavis, ecs 251 Fall 2007 Trust Ordering • Trust Ordering – I trust you, otherwise, I don’t. • Information-based Ordering – I trust you, I don’t, or I don’t know based on the information I have currently. – Dynamics and Uncertainty 11/29/2007 Trust and Reputation System 4
 UCDavis, ecs 251 Fall 2007 Policy & Delegation • Policy: – If X trusts Y by Z, then A will trust B by C. – E. g. • If Bank American will lend you $1 M, then Washington Mutual will lend you $2 M. 11/29/2007 Trust and Reputation System 5
UCDavis, ecs 251 Fall 2007 Policy & Delegation • Policy: – If X trusts Y by Z, then A will trust B by C. – E. g. • If Bank American will lend you $1 M, then Washington Mutual will lend you $2 M. 11/29/2007 Trust and Reputation System 5
 UCDavis, ecs 251 Fall 2007 Policy & Delegation • Policy: – If X trusts Y by Z, then A will trust B by C. – E. g. • If Bank American will lend you $1 M, then Washington Mutual will lend you $2 M. – Trust means “Action and Risk” – Computational Trust needs to quantify the actions and their associated risks. – It might be “Mutual Recursive” though… 11/29/2007 Trust and Reputation System 6
UCDavis, ecs 251 Fall 2007 Policy & Delegation • Policy: – If X trusts Y by Z, then A will trust B by C. – E. g. • If Bank American will lend you $1 M, then Washington Mutual will lend you $2 M. – Trust means “Action and Risk” – Computational Trust needs to quantify the actions and their associated risks. – It might be “Mutual Recursive” though… 11/29/2007 Trust and Reputation System 6
 UCDavis, ecs 251 Fall 2007 Computational Trust • Direct DSL Link – Observing our direct neighbor’s behavior • Indirect Sources in Social Network – Trust delegation – About a peer, may or may not be your direct neighbor 11/29/2007 Trust and Reputation System 7
UCDavis, ecs 251 Fall 2007 Computational Trust • Direct DSL Link – Observing our direct neighbor’s behavior • Indirect Sources in Social Network – Trust delegation – About a peer, may or may not be your direct neighbor 11/29/2007 Trust and Reputation System 7
 UCDavis, ecs 251 Fall 2007 Trust in P 2 P • The Service Provider provides a management system for trust and reputation – – Google’s “Page. Rank” Antivirus system e. Bay’s seller reputation system PKI • P 2 P -- everything hopefully to be P 2 P – Decentralized model for trust 11/29/2007 Trust and Reputation System 8
UCDavis, ecs 251 Fall 2007 Trust in P 2 P • The Service Provider provides a management system for trust and reputation – – Google’s “Page. Rank” Antivirus system e. Bay’s seller reputation system PKI • P 2 P -- everything hopefully to be P 2 P – Decentralized model for trust 11/29/2007 Trust and Reputation System 8
 UCDavis, ecs 251 Fall 2007 Cheating & Incentives • Selfish users in Gnutella and Bittorrent • e. Bay flaw seller ranking • Google page rank • Selfishness or Reputation boost 11/29/2007 Trust and Reputation System 9
UCDavis, ecs 251 Fall 2007 Cheating & Incentives • Selfish users in Gnutella and Bittorrent • e. Bay flaw seller ranking • Google page rank • Selfishness or Reputation boost 11/29/2007 Trust and Reputation System 9
 UCDavis, ecs 251 Fall 2007 P 2 P Trust Model • Less vulnerable? • Harder to implement? In a decentralized setting? 11/29/2007 Trust and Reputation System 10
UCDavis, ecs 251 Fall 2007 P 2 P Trust Model • Less vulnerable? • Harder to implement? In a decentralized setting? 11/29/2007 Trust and Reputation System 10
 UCDavis, ecs 251 Fall 2007 Problem • Problem: – Reduce inauthentic files distributed by malicious peers on a P 2 P network. • Motivation: “Major record labels have launched an aggressive new guerrilla assault on the underground music networks, flooding online swapping services with bogus copies of popular songs. ” -Silicon Valley Weekly 11/29/2007 Trust and Reputation System 11
UCDavis, ecs 251 Fall 2007 Problem • Problem: – Reduce inauthentic files distributed by malicious peers on a P 2 P network. • Motivation: “Major record labels have launched an aggressive new guerrilla assault on the underground music networks, flooding online swapping services with bogus copies of popular songs. ” -Silicon Valley Weekly 11/29/2007 Trust and Reputation System 11
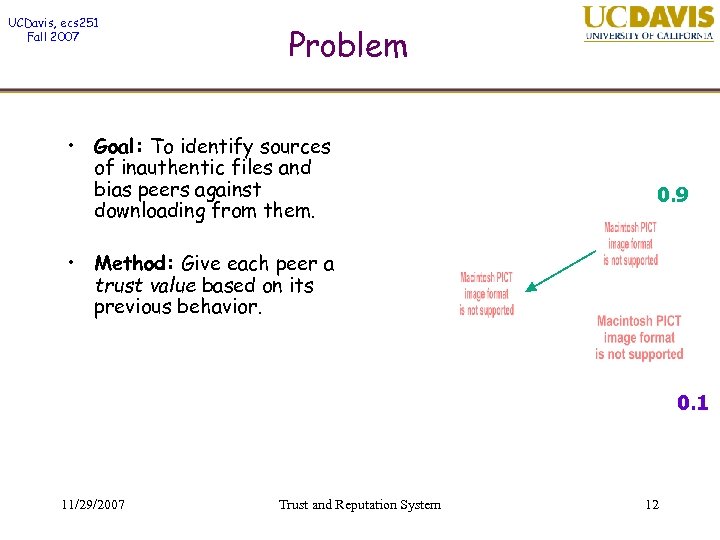 UCDavis, ecs 251 Fall 2007 Problem • Goal: To identify sources of inauthentic files and bias peers against downloading from them. 0. 9 • Method: Give each peer a trust value based on its previous behavior. 0. 1 11/29/2007 Trust and Reputation System 12
UCDavis, ecs 251 Fall 2007 Problem • Goal: To identify sources of inauthentic files and bias peers against downloading from them. 0. 9 • Method: Give each peer a trust value based on its previous behavior. 0. 1 11/29/2007 Trust and Reputation System 12
 UCDavis, ecs 251 Fall 2007 • • • Some approaches Past History Friends of Friends Eigen. Trust Peer. Trust. Davis 11/29/2007 Trust and Reputation System 13
UCDavis, ecs 251 Fall 2007 • • • Some approaches Past History Friends of Friends Eigen. Trust Peer. Trust. Davis 11/29/2007 Trust and Reputation System 13
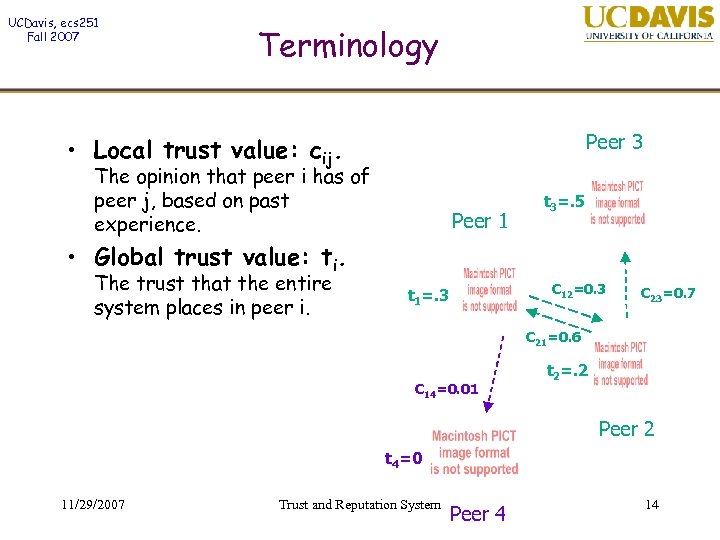 UCDavis, ecs 251 Fall 2007 Terminology Peer 3 • Local trust value: cij. The opinion that peer i has of peer j, based on past experience. Peer 1 t 3=. 5 • Global trust value: ti. The trust that the entire system places in peer i. C 12=0. 3 t 1=. 3 C 23=0. 7 C 21=0. 6 C 14=0. 01 t 2=. 2 Peer 2 t 4=0 11/29/2007 Trust and Reputation System Peer 4 14
UCDavis, ecs 251 Fall 2007 Terminology Peer 3 • Local trust value: cij. The opinion that peer i has of peer j, based on past experience. Peer 1 t 3=. 5 • Global trust value: ti. The trust that the entire system places in peer i. C 12=0. 3 t 1=. 3 C 23=0. 7 C 21=0. 6 C 14=0. 01 t 2=. 2 Peer 2 t 4=0 11/29/2007 Trust and Reputation System Peer 4 14
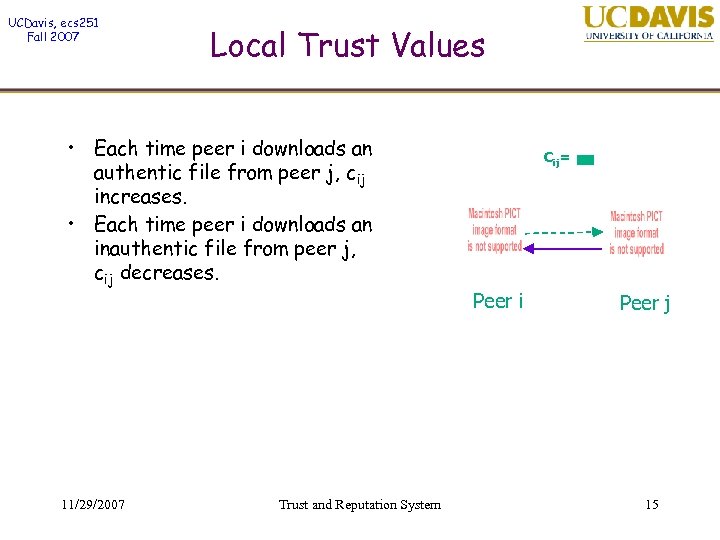 UCDavis, ecs 251 Fall 2007 Local Trust Values • Each time peer i downloads an authentic file from peer j, cij increases. • Each time peer i downloads an inauthentic file from peer j, cij decreases. 11/29/2007 Trust and Reputation System Cij= Peer i Peer j 15
UCDavis, ecs 251 Fall 2007 Local Trust Values • Each time peer i downloads an authentic file from peer j, cij increases. • Each time peer i downloads an inauthentic file from peer j, cij decreases. 11/29/2007 Trust and Reputation System Cij= Peer i Peer j 15
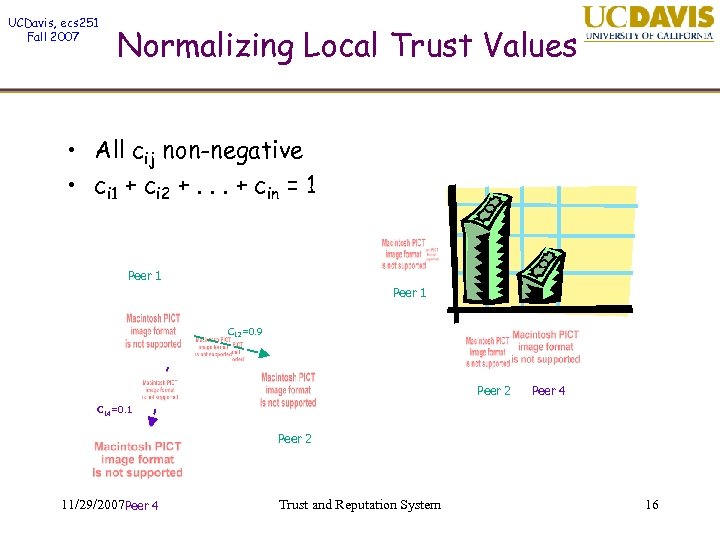 UCDavis, ecs 251 Fall 2007 Normalizing Local Trust Values • All cij non-negative • ci 1 + ci 2 +. . . + cin = 1 Peer 1 C 12=0. 9 Peer 2 Peer 4 C 14=0. 1 Peer 2 11/29/2007 Peer 4 Trust and Reputation System 16
UCDavis, ecs 251 Fall 2007 Normalizing Local Trust Values • All cij non-negative • ci 1 + ci 2 +. . . + cin = 1 Peer 1 C 12=0. 9 Peer 2 Peer 4 C 14=0. 1 Peer 2 11/29/2007 Peer 4 Trust and Reputation System 16
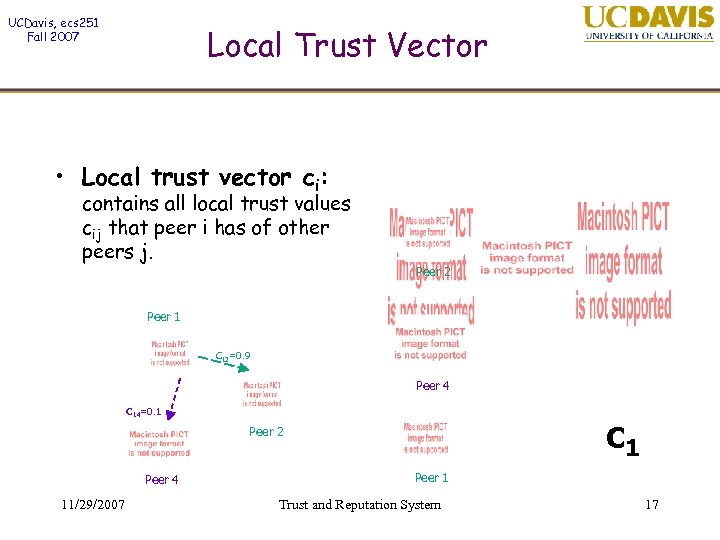 UCDavis, ecs 251 Fall 2007 Local Trust Vector • Local trust vector ci: contains all local trust values cij that peer i has of other peers j. Peer 2 Peer 1 C 12=0. 9 Peer 4 C 14=0. 1 c 1 Peer 2 Peer 4 11/29/2007 Peer 1 Trust and Reputation System 17
UCDavis, ecs 251 Fall 2007 Local Trust Vector • Local trust vector ci: contains all local trust values cij that peer i has of other peers j. Peer 2 Peer 1 C 12=0. 9 Peer 4 C 14=0. 1 c 1 Peer 2 Peer 4 11/29/2007 Peer 1 Trust and Reputation System 17
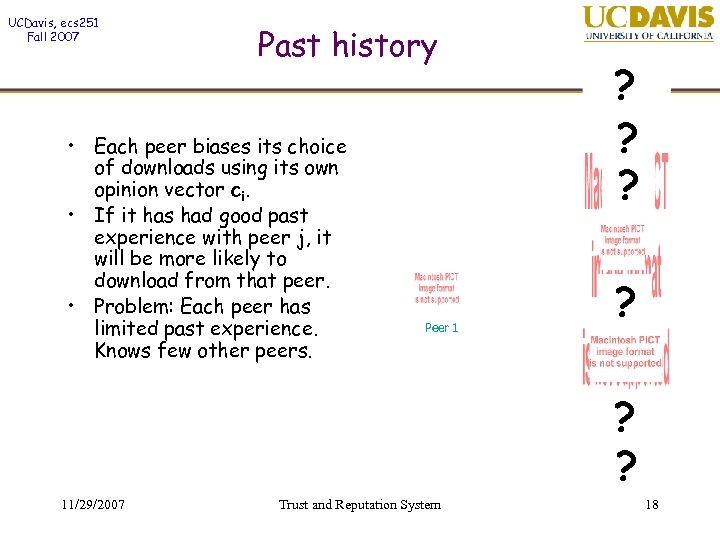 UCDavis, ecs 251 Fall 2007 Past history • Each peer biases its choice of downloads using its own opinion vector ci. • If it has had good past experience with peer j, it will be more likely to download from that peer. • Problem: Each peer has limited past experience. Knows few other peers. ? ? Peer 4 Peer 1 Peer 6 ? ? 11/29/2007 Trust and Reputation System 18
UCDavis, ecs 251 Fall 2007 Past history • Each peer biases its choice of downloads using its own opinion vector ci. • If it has had good past experience with peer j, it will be more likely to download from that peer. • Problem: Each peer has limited past experience. Knows few other peers. ? ? Peer 4 Peer 1 Peer 6 ? ? 11/29/2007 Trust and Reputation System 18
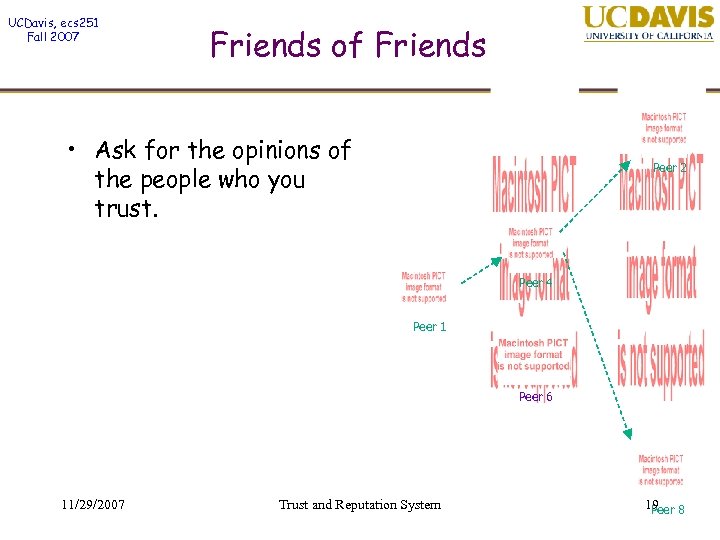 UCDavis, ecs 251 Fall 2007 Friends of Friends • Ask for the opinions of the people who you trust. Peer 2 Peer 4 Peer 1 Peer 6 11/29/2007 Trust and Reputation System 19 8 Peer
UCDavis, ecs 251 Fall 2007 Friends of Friends • Ask for the opinions of the people who you trust. Peer 2 Peer 4 Peer 1 Peer 6 11/29/2007 Trust and Reputation System 19 8 Peer
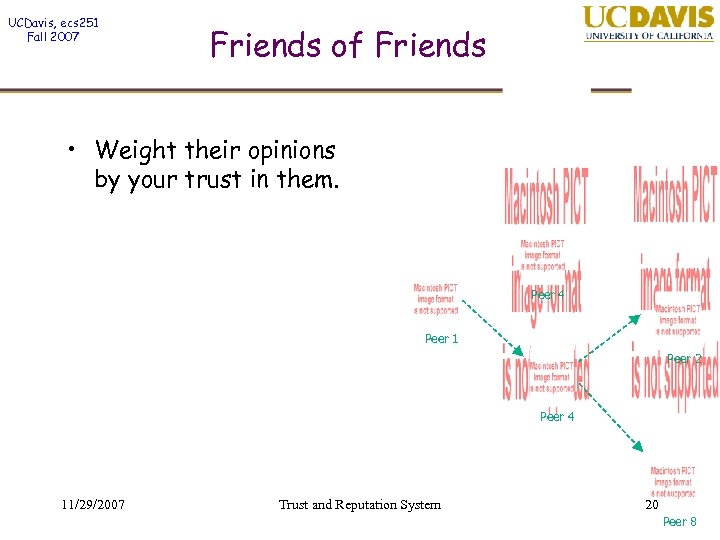 UCDavis, ecs 251 Fall 2007 Friends of Friends • Weight their opinions by your trust in them. Peer 4 Peer 1 Peer 2 Peer 4 11/29/2007 Trust and Reputation System 20 Peer 8
UCDavis, ecs 251 Fall 2007 Friends of Friends • Weight their opinions by your trust in them. Peer 4 Peer 1 Peer 2 Peer 4 11/29/2007 Trust and Reputation System 20 Peer 8
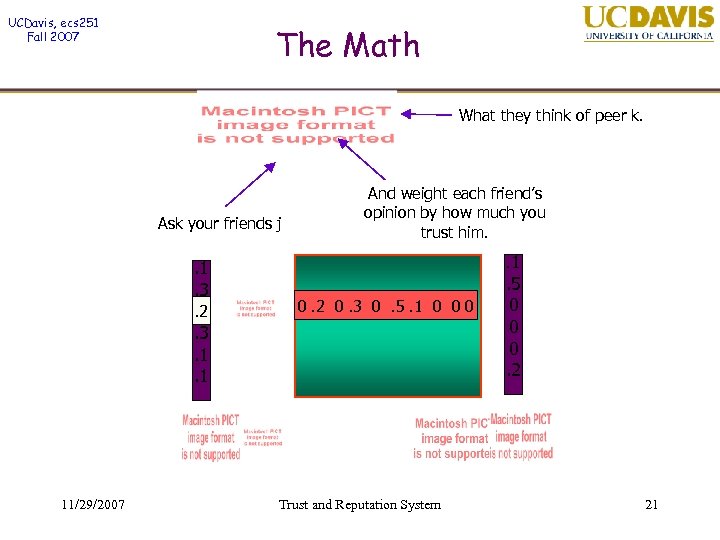 UCDavis, ecs 251 Fall 2007 The Math What they think of peer k. Ask your friends j . 1. 3. 2. 3. 1. 1 11/29/2007 And weight each friend’s opinion by how much you trust him. . 1 0. 2 0. 3 0. 5. 1 0 0 0 Trust and Reputation System . 5 0 0 0. 2 21
UCDavis, ecs 251 Fall 2007 The Math What they think of peer k. Ask your friends j . 1. 3. 2. 3. 1. 1 11/29/2007 And weight each friend’s opinion by how much you trust him. . 1 0. 2 0. 3 0. 5. 1 0 0 0 Trust and Reputation System . 5 0 0 0. 2 21
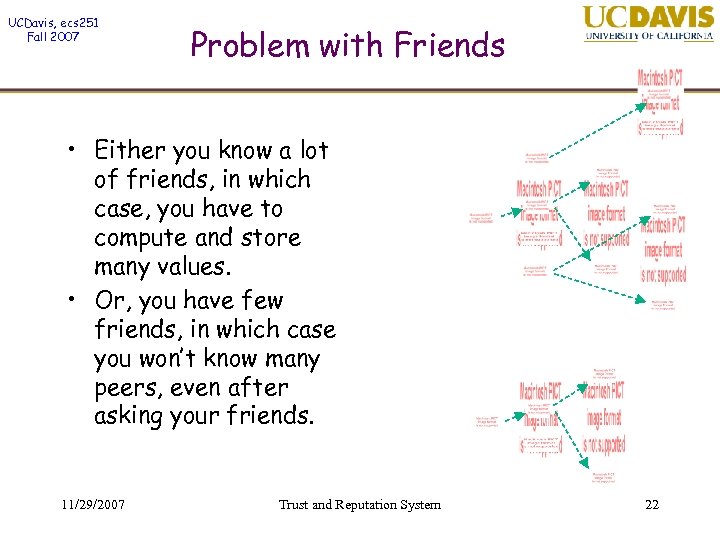 UCDavis, ecs 251 Fall 2007 Problem with Friends • Either you know a lot of friends, in which case, you have to compute and store many values. • Or, you have few friends, in which case you won’t know many peers, even after asking your friends. 11/29/2007 Trust and Reputation System 22
UCDavis, ecs 251 Fall 2007 Problem with Friends • Either you know a lot of friends, in which case, you have to compute and store many values. • Or, you have few friends, in which case you won’t know many peers, even after asking your friends. 11/29/2007 Trust and Reputation System 22
 UCDavis, ecs 251 Fall 2007 Dual Goal • We want each peer to: – Know all peers. – Perform minimal computation (and storage). 11/29/2007 Trust and Reputation System 23
UCDavis, ecs 251 Fall 2007 Dual Goal • We want each peer to: – Know all peers. – Perform minimal computation (and storage). 11/29/2007 Trust and Reputation System 23
 UCDavis, ecs 251 Fall 2007 Knowing All Peers • Ask your friends: t=CTci. • Ask their friends: t=(CT)2 ci. • Keep asking until the cows come home: t=(CT)nci. 11/29/2007 Trust and Reputation System 24
UCDavis, ecs 251 Fall 2007 Knowing All Peers • Ask your friends: t=CTci. • Ask their friends: t=(CT)2 ci. • Keep asking until the cows come home: t=(CT)nci. 11/29/2007 Trust and Reputation System 24
 UCDavis, ecs 251 Fall 2007 Minimal Computation • Luckily, the trust vector t, if computed in this manner, converges to the same thing for every peer! • Therefore, each peer doesn’t have to store and compute its own trust vector. The whole network can cooperate to store and compute t. 11/29/2007 Trust and Reputation System 25
UCDavis, ecs 251 Fall 2007 Minimal Computation • Luckily, the trust vector t, if computed in this manner, converges to the same thing for every peer! • Therefore, each peer doesn’t have to store and compute its own trust vector. The whole network can cooperate to store and compute t. 11/29/2007 Trust and Reputation System 25
 UCDavis, ecs 251 Fall 2007 Non-distributed Algorithm • Initialize: • Repeat until convergence: 11/29/2007 Trust and Reputation System 26
UCDavis, ecs 251 Fall 2007 Non-distributed Algorithm • Initialize: • Repeat until convergence: 11/29/2007 Trust and Reputation System 26
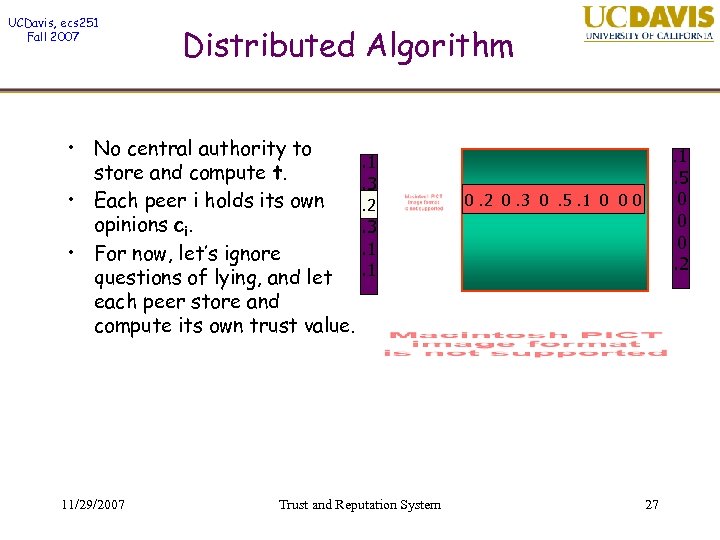 UCDavis, ecs 251 Fall 2007 Distributed Algorithm • No central authority to. 1 store and compute t. . 3 • Each peer i holds its own. 2 opinions ci. . 3. 1 • For now, let’s ignore questions of lying, and let. 1 each peer store and compute its own trust value. 11/29/2007 Trust and Reputation System . 1 . 5 0 0 0. 2 0. 3 0. 5. 1 0 0 0 27
UCDavis, ecs 251 Fall 2007 Distributed Algorithm • No central authority to. 1 store and compute t. . 3 • Each peer i holds its own. 2 opinions ci. . 3. 1 • For now, let’s ignore questions of lying, and let. 1 each peer store and compute its own trust value. 11/29/2007 Trust and Reputation System . 1 . 5 0 0 0. 2 0. 3 0. 5. 1 0 0 0 27
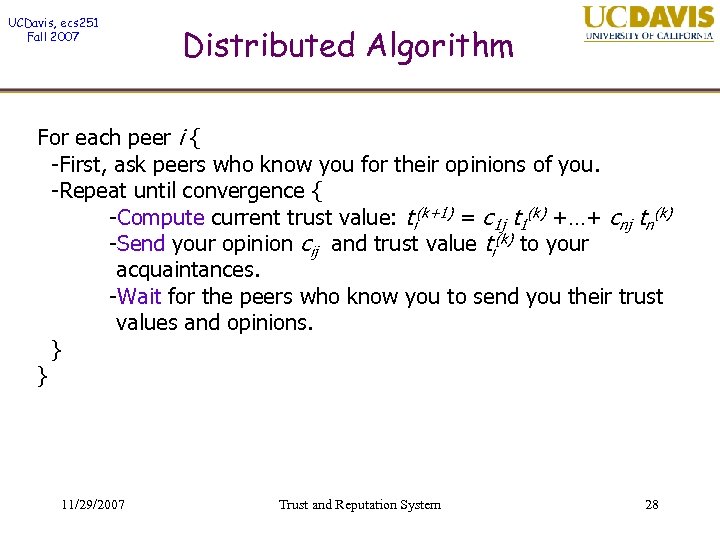 UCDavis, ecs 251 Fall 2007 Distributed Algorithm For each peer i { -First, ask peers who know you for their opinions of you. -Repeat until convergence { -Compute current trust value: ti(k+1) = c 1 j t 1(k) +…+ cnj tn(k) -Send your opinion cij and trust value ti(k) to your acquaintances. -Wait for the peers who know you to send you their trust values and opinions. } } 11/29/2007 Trust and Reputation System 28
UCDavis, ecs 251 Fall 2007 Distributed Algorithm For each peer i { -First, ask peers who know you for their opinions of you. -Repeat until convergence { -Compute current trust value: ti(k+1) = c 1 j t 1(k) +…+ cnj tn(k) -Send your opinion cij and trust value ti(k) to your acquaintances. -Wait for the peers who know you to send you their trust values and opinions. } } 11/29/2007 Trust and Reputation System 28
 UCDavis, ecs 251 Fall 2007 11/29/2007 Probabilistic Interpretation Trust and Reputation System 29
UCDavis, ecs 251 Fall 2007 11/29/2007 Probabilistic Interpretation Trust and Reputation System 29
 UCDavis, ecs 251 Fall 2007 11/29/2007 Malicious Collectives Trust and Reputation System 30
UCDavis, ecs 251 Fall 2007 11/29/2007 Malicious Collectives Trust and Reputation System 30
 UCDavis, ecs 251 Fall 2007 Pre-trusted Peers • Battling Malicious Collectives • Inactive Peers • Incorporating heuristic notions of trust • Convergence Rate 11/29/2007 Trust and Reputation System 31
UCDavis, ecs 251 Fall 2007 Pre-trusted Peers • Battling Malicious Collectives • Inactive Peers • Incorporating heuristic notions of trust • Convergence Rate 11/29/2007 Trust and Reputation System 31
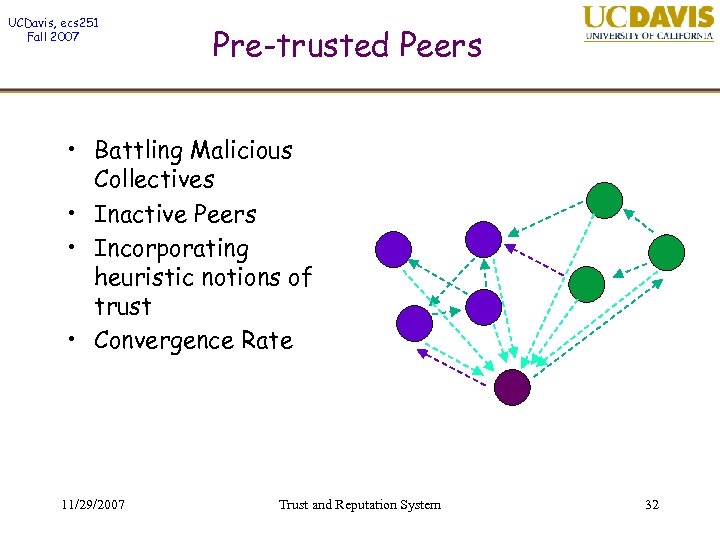 UCDavis, ecs 251 Fall 2007 Pre-trusted Peers • Battling Malicious Collectives • Inactive Peers • Incorporating heuristic notions of trust • Convergence Rate 11/29/2007 Trust and Reputation System 32
UCDavis, ecs 251 Fall 2007 Pre-trusted Peers • Battling Malicious Collectives • Inactive Peers • Incorporating heuristic notions of trust • Convergence Rate 11/29/2007 Trust and Reputation System 32
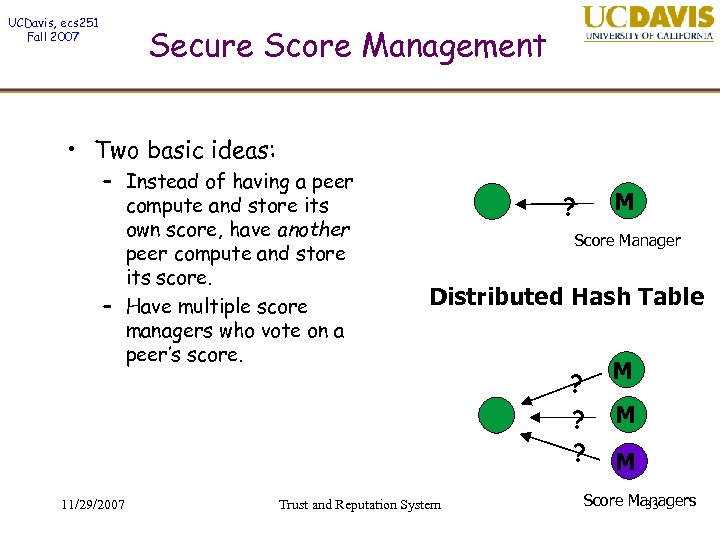 UCDavis, ecs 251 Fall 2007 Secure Score Management • Two basic ideas: – Instead of having a peer compute and store its own score, have another peer compute and store its score. – Have multiple score managers who vote on a peer’s score. M ? Score Manager Distributed Hash Table Trust and Reputation System M ? ? 11/29/2007 ? M M Score Managers 33
UCDavis, ecs 251 Fall 2007 Secure Score Management • Two basic ideas: – Instead of having a peer compute and store its own score, have another peer compute and store its score. – Have multiple score managers who vote on a peer’s score. M ? Score Manager Distributed Hash Table Trust and Reputation System M ? ? 11/29/2007 ? M M Score Managers 33
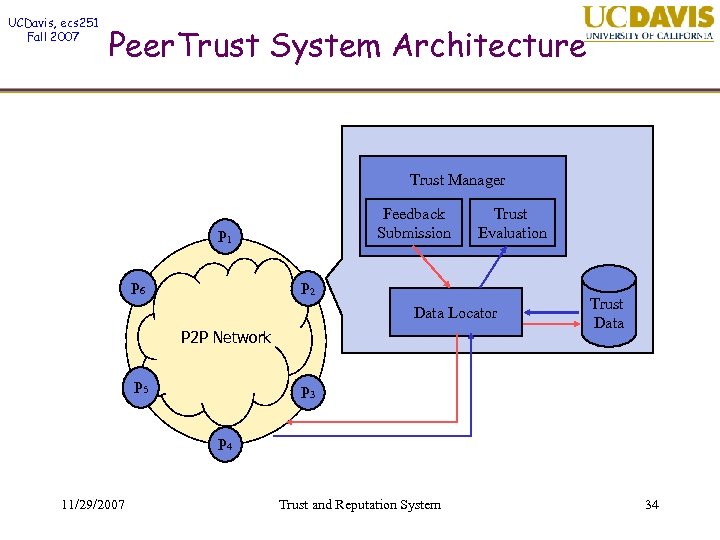 UCDavis, ecs 251 Fall 2007 Peer. Trust System Architecture Trust Manager Feedback Submission P 1 P 6 Trust Evaluation P 2 Data Locator P 2 P Network P 5 Trust Data P 3 P 4 11/29/2007 Trust and Reputation System 34
UCDavis, ecs 251 Fall 2007 Peer. Trust System Architecture Trust Manager Feedback Submission P 1 P 6 Trust Evaluation P 2 Data Locator P 2 P Network P 5 Trust Data P 3 P 4 11/29/2007 Trust and Reputation System 34
 UCDavis, ecs 251 Fall 2007 How to use the trust values ti • When you get responses from multiple peers: – Deterministic: Choose the one with highest trust value. – Probabilistic: Choose a peer with probability proportional to its trust value. 11/29/2007 Trust and Reputation System 35
UCDavis, ecs 251 Fall 2007 How to use the trust values ti • When you get responses from multiple peers: – Deterministic: Choose the one with highest trust value. – Probabilistic: Choose a peer with probability proportional to its trust value. 11/29/2007 Trust and Reputation System 35
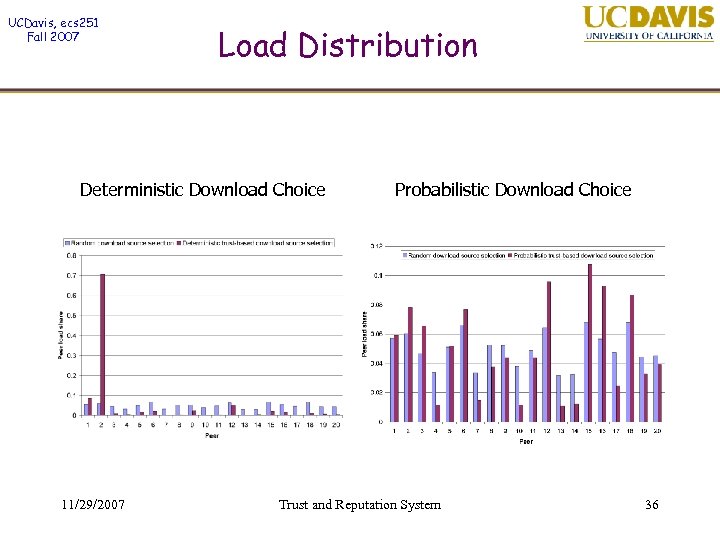 UCDavis, ecs 251 Fall 2007 Load Distribution Deterministic Download Choice 11/29/2007 Probabilistic Download Choice Trust and Reputation System 36
UCDavis, ecs 251 Fall 2007 Load Distribution Deterministic Download Choice 11/29/2007 Probabilistic Download Choice Trust and Reputation System 36
 UCDavis, ecs 251 Fall 2007 Threat Scenarios • Malicious Individuals – Always provide inauthentic files. • Malicious Collective – Always provide inauthentic files. – Know each other. Give each other good opinions, and give other peers bad opinions. 11/29/2007 Trust and Reputation System 37
UCDavis, ecs 251 Fall 2007 Threat Scenarios • Malicious Individuals – Always provide inauthentic files. • Malicious Collective – Always provide inauthentic files. – Know each other. Give each other good opinions, and give other peers bad opinions. 11/29/2007 Trust and Reputation System 37
 UCDavis, ecs 251 Fall 2007 More Threat Scenarios • Camouflaged Collective – Provide authentic files some of the time to trick good peers into giving them good opinions. • Malicious Spies – Some members of the collective good files all the time, but give good opinions to malicious peers. 11/29/2007 Trust and Reputation System 38
UCDavis, ecs 251 Fall 2007 More Threat Scenarios • Camouflaged Collective – Provide authentic files some of the time to trick good peers into giving them good opinions. • Malicious Spies – Some members of the collective good files all the time, but give good opinions to malicious peers. 11/29/2007 Trust and Reputation System 38
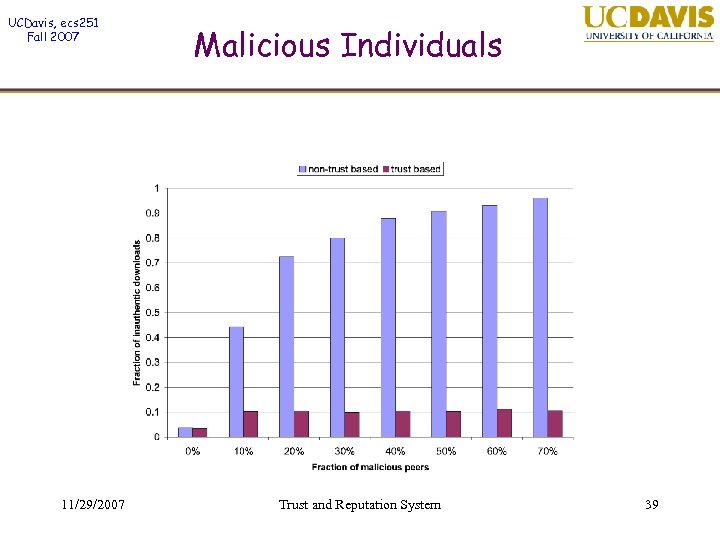 UCDavis, ecs 251 Fall 2007 11/29/2007 Malicious Individuals Trust and Reputation System 39
UCDavis, ecs 251 Fall 2007 11/29/2007 Malicious Individuals Trust and Reputation System 39
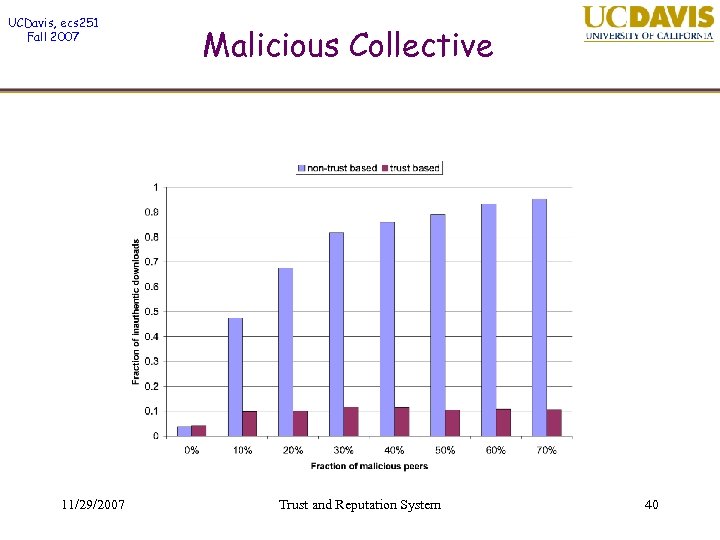 UCDavis, ecs 251 Fall 2007 11/29/2007 Malicious Collective Trust and Reputation System 40
UCDavis, ecs 251 Fall 2007 11/29/2007 Malicious Collective Trust and Reputation System 40
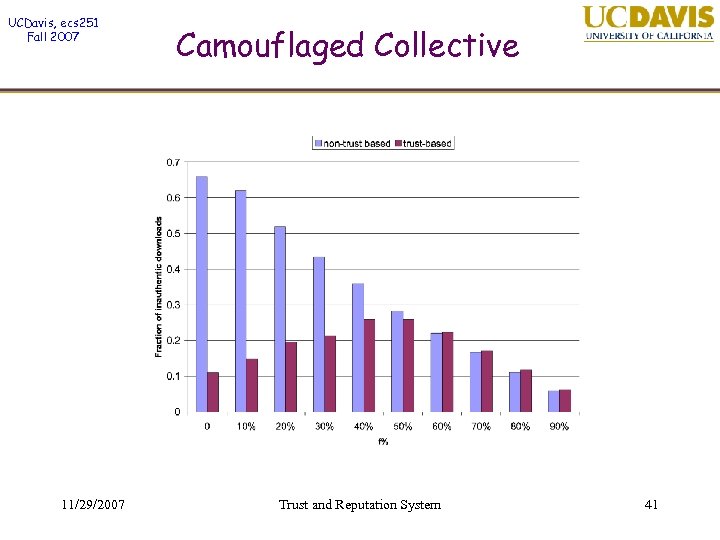 UCDavis, ecs 251 Fall 2007 11/29/2007 Camouflaged Collective Trust and Reputation System 41
UCDavis, ecs 251 Fall 2007 11/29/2007 Camouflaged Collective Trust and Reputation System 41
 UCDavis, ecs 251 Fall 2007 11/29/2007 P 2 P Electronic Communities Trust and Reputation System 42
UCDavis, ecs 251 Fall 2007 11/29/2007 P 2 P Electronic Communities Trust and Reputation System 42
 UCDavis, ecs 251 Fall 2007 11/29/2007 Motivation Trust and Reputation System 43
UCDavis, ecs 251 Fall 2007 11/29/2007 Motivation Trust and Reputation System 43
 UCDavis, ecs 251 Fall 2007 Motivation • Should we buy? • How do we decide? 11/29/2007 Trust and Reputation System 44
UCDavis, ecs 251 Fall 2007 Motivation • Should we buy? • How do we decide? 11/29/2007 Trust and Reputation System 44
 UCDavis, ecs 251 Fall 2007 11/29/2007 Motivation Trust and Reputation System 45
UCDavis, ecs 251 Fall 2007 11/29/2007 Motivation Trust and Reputation System 45
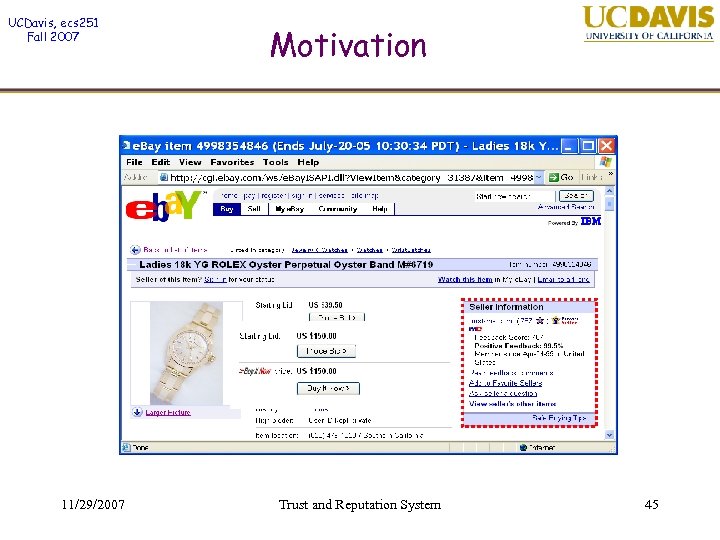
 UCDavis, ecs 251 Fall 2007 Motivation • Should we buy? • How do we decide? • What we want: – – accurately estimate risk of default minimize the risk of default minimize losses due to pseudonym change avoid trusting a centralized authority • How do we achieve these goals? 11/29/2007 Trust and Reputation System 46
UCDavis, ecs 251 Fall 2007 Motivation • Should we buy? • How do we decide? • What we want: – – accurately estimate risk of default minimize the risk of default minimize losses due to pseudonym change avoid trusting a centralized authority • How do we achieve these goals? 11/29/2007 Trust and Reputation System 46
 UCDavis, ecs 251 Fall 2007 Motivation • Trust. Davis is a reputation system that realizes these goals. • It recasts these goals as the following properties: 11/29/2007 Trust and Reputation System 47
UCDavis, ecs 251 Fall 2007 Motivation • Trust. Davis is a reputation system that realizes these goals. • It recasts these goals as the following properties: 11/29/2007 Trust and Reputation System 47
 UCDavis, ecs 251 Fall 2007 1. 2. 3. 4. Motivation – – Agents can accurately estimate risk Third parties provide accurate ratings Honest buyer/seller avoids risk (if possible) Insure transactions No advantage in obtaining multiple identities Agents can cope with pseudonym change No need to trust a centralized authority 11/29/2007 No centralized services needed Trust and Reputation System 48
UCDavis, ecs 251 Fall 2007 1. 2. 3. 4. Motivation – – Agents can accurately estimate risk Third parties provide accurate ratings Honest buyer/seller avoids risk (if possible) Insure transactions No advantage in obtaining multiple identities Agents can cope with pseudonym change No need to trust a centralized authority 11/29/2007 No centralized services needed Trust and Reputation System 48
 UCDavis, ecs 251 Fall 2007 Motivation Incentive Compatibility: Each player should have incentives to perform the actions that enable the system to achieve a desired global outcome. 11/29/2007 Trust and Reputation System 49
UCDavis, ecs 251 Fall 2007 Motivation Incentive Compatibility: Each player should have incentives to perform the actions that enable the system to achieve a desired global outcome. 11/29/2007 Trust and Reputation System 49
 UCDavis, ecs 251 Fall 2007 1. 2. 3. 4. Motivation – – Agents can accurately estimate risk Third parties provide accurate ratings Honest buyer/seller avoids risk (if possible) Insure transactions No advantage in obtaining multiple identities Agents can cope with pseudonym change No need to trust a centralized authority No centralized services needed Incentive Compatibility! 11/29/2007 Trust and Reputation System 50
UCDavis, ecs 251 Fall 2007 1. 2. 3. 4. Motivation – – Agents can accurately estimate risk Third parties provide accurate ratings Honest buyer/seller avoids risk (if possible) Insure transactions No advantage in obtaining multiple identities Agents can cope with pseudonym change No need to trust a centralized authority No centralized services needed Incentive Compatibility! 11/29/2007 Trust and Reputation System 50
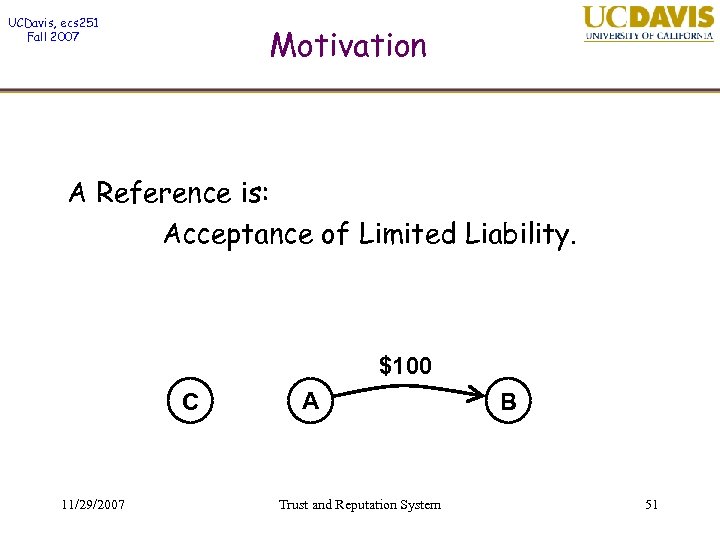 UCDavis, ecs 251 Fall 2007 Motivation A Reference is: Acceptance of Limited Liability. $100 C 11/29/2007 A Trust and Reputation System B 51
UCDavis, ecs 251 Fall 2007 Motivation A Reference is: Acceptance of Limited Liability. $100 C 11/29/2007 A Trust and Reputation System B 51
 UCDavis, ecs 251 Fall 2007 1. 2. 3. 4. Motivation – – – – Agents can accurately estimate risk Third parties provide accurate ratings Parties are liable for the references they provide Honest buyer/seller avoids risk (if possible) Insure transactions Buyers/sellers pay for references to insure their transactions No advantage in obtaining multiple identities Agents can cope with pseudonym change References are issued only to trusted identities No need to trust a centralized authority 11/29/2007 No centralized services needed Anyone can issue a reference Use References! Trust and Reputation System 52
UCDavis, ecs 251 Fall 2007 1. 2. 3. 4. Motivation – – – – Agents can accurately estimate risk Third parties provide accurate ratings Parties are liable for the references they provide Honest buyer/seller avoids risk (if possible) Insure transactions Buyers/sellers pay for references to insure their transactions No advantage in obtaining multiple identities Agents can cope with pseudonym change References are issued only to trusted identities No need to trust a centralized authority 11/29/2007 No centralized services needed Anyone can issue a reference Use References! Trust and Reputation System 52
 UCDavis, ecs 251 Fall 2007 Outline • Trust. Davis leverages social networks • For now, examples assume No False Claims (NFC) • The use of Trust. Davis does NOT preclude trade outside the system. 11/29/2007 Trust and Reputation System 53
UCDavis, ecs 251 Fall 2007 Outline • Trust. Davis leverages social networks • For now, examples assume No False Claims (NFC) • The use of Trust. Davis does NOT preclude trade outside the system. 11/29/2007 Trust and Reputation System 53
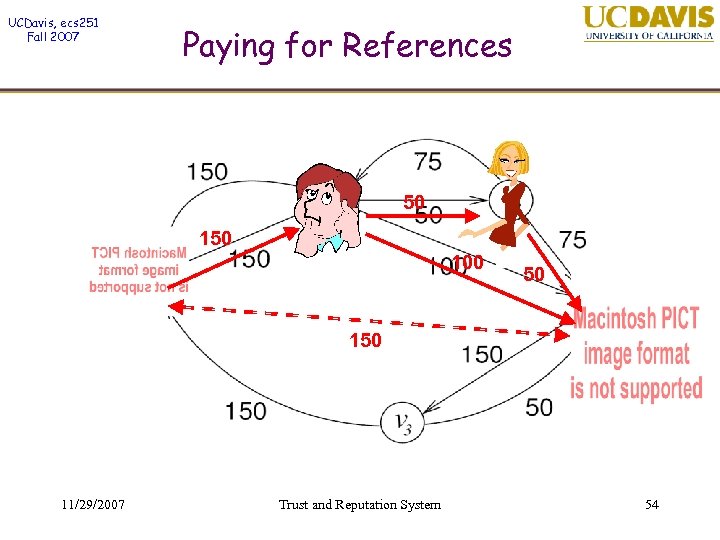 UCDavis, ecs 251 Fall 2007 Paying for References 50 100 50 11/29/2007 Trust and Reputation System 54
UCDavis, ecs 251 Fall 2007 Paying for References 50 100 50 11/29/2007 Trust and Reputation System 54
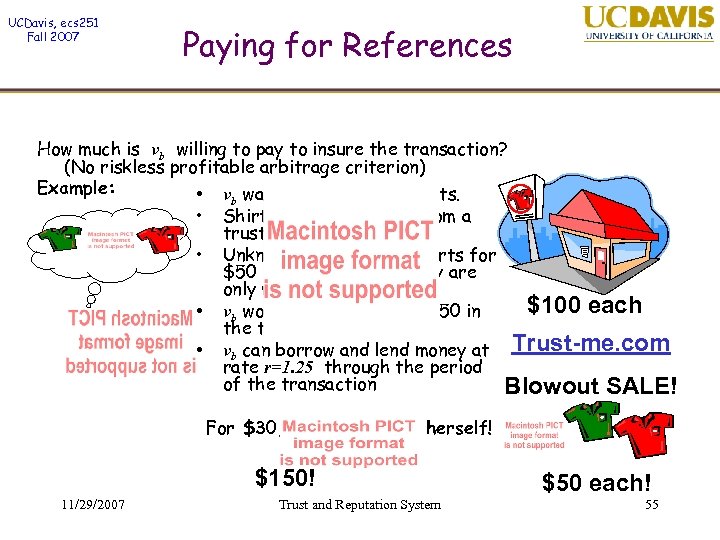 UCDavis, ecs 251 Fall 2007 Paying for References How much is vb willing to pay to insure the transaction? (No riskless profitable arbitrage criterion) Example: • v wants to buy three shirts. • • b Shirts cost $100 each from a trustworthy seller Unknown seller offers shirts for $50 each (but maybe they are only worth $25). vb would risk 3 x $50 = $150 in the transaction vb can borrow and lend money at rate r=1. 25 through the period of the transaction $100 each Trust-me. com Blowout SALE! For $30, vb can insure herself! $150! 11/29/2007 Trust and Reputation System $50 each! 55
UCDavis, ecs 251 Fall 2007 Paying for References How much is vb willing to pay to insure the transaction? (No riskless profitable arbitrage criterion) Example: • v wants to buy three shirts. • • b Shirts cost $100 each from a trustworthy seller Unknown seller offers shirts for $50 each (but maybe they are only worth $25). vb would risk 3 x $50 = $150 in the transaction vb can borrow and lend money at rate r=1. 25 through the period of the transaction $100 each Trust-me. com Blowout SALE! For $30, vb can insure herself! $150! 11/29/2007 Trust and Reputation System $50 each! 55
 UCDavis, ecs 251 Fall 2007 Paying for References To insure herself vb buys the shirts and a hedging portfolio as follows: 1. Instead of buying 3 shirts for $50 each she buys only 2, saving $50. 2. The buyer, vb , adds $30 of her own money and lends the resulting $80 at rate r = 1. 25. 11/29/2007 Trust and Reputation System 56
UCDavis, ecs 251 Fall 2007 Paying for References To insure herself vb buys the shirts and a hedging portfolio as follows: 1. Instead of buying 3 shirts for $50 each she buys only 2, saving $50. 2. The buyer, vb , adds $30 of her own money and lends the resulting $80 at rate r = 1. 25. 11/29/2007 Trust and Reputation System 56
 UCDavis, ecs 251 Fall 2007 Paying for References On Success: – vb obtains $100 from the loan and buys the 3 rd shirt On failure: – vb sells the two shirts for $25 each – gets $100 from the loan. – She obtains a total of $150 Thus, vb can insure herself for $30. 11/29/2007 Trust and Reputation System 57
UCDavis, ecs 251 Fall 2007 Paying for References On Success: – vb obtains $100 from the loan and buys the 3 rd shirt On failure: – vb sells the two shirts for $25 each – gets $100 from the loan. – She obtains a total of $150 Thus, vb can insure herself for $30. 11/29/2007 Trust and Reputation System 57
 UCDavis, ecs 251 Fall 2007 11/29/2007 Selling References Trust and Reputation System 58
UCDavis, ecs 251 Fall 2007 11/29/2007 Selling References Trust and Reputation System 58
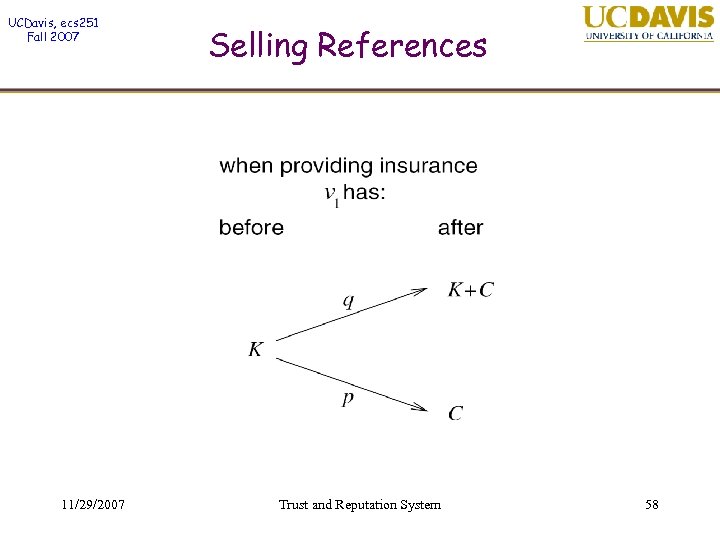
 UCDavis, ecs 251 Fall 2007 Selling References Seen as an investment… On Success the ROI is: On failure the ROI is: If repeated many times the insurer may go bankrupt. Assume the insurer has W dollars available to insure this transaction. 11/29/2007 Trust and Reputation System 59
UCDavis, ecs 251 Fall 2007 Selling References Seen as an investment… On Success the ROI is: On failure the ROI is: If repeated many times the insurer may go bankrupt. Assume the insurer has W dollars available to insure this transaction. 11/29/2007 Trust and Reputation System 59
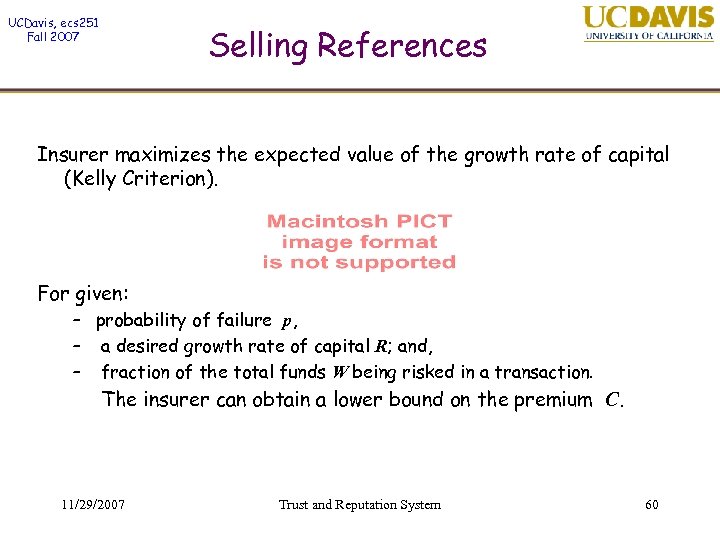 UCDavis, ecs 251 Fall 2007 Selling References Insurer maximizes the expected value of the growth rate of capital (Kelly Criterion). For given: – probability of failure p, – a desired growth rate of capital R; and, – fraction of the total funds W being risked in a transaction. The insurer can obtain a lower bound on the premium C. 11/29/2007 Trust and Reputation System 60
UCDavis, ecs 251 Fall 2007 Selling References Insurer maximizes the expected value of the growth rate of capital (Kelly Criterion). For given: – probability of failure p, – a desired growth rate of capital R; and, – fraction of the total funds W being risked in a transaction. The insurer can obtain a lower bound on the premium C. 11/29/2007 Trust and Reputation System 60
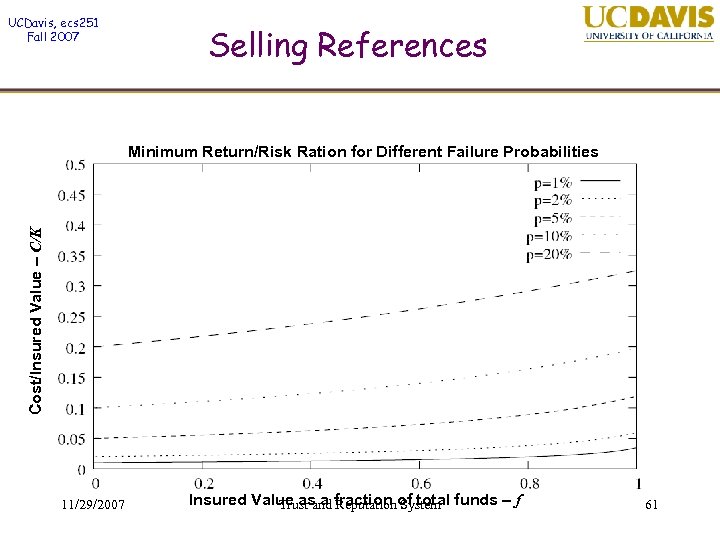 UCDavis, ecs 251 Fall 2007 Selling References Cost/Insured Value – C/K Minimum Return/Risk Ration for Different Failure Probabilities 11/29/2007 Insured Value as a fraction of total funds – f Trust and Reputation System 61
UCDavis, ecs 251 Fall 2007 Selling References Cost/Insured Value – C/K Minimum Return/Risk Ration for Different Failure Probabilities 11/29/2007 Insured Value as a fraction of total funds – f Trust and Reputation System 61
 UCDavis, ecs 251 Fall 2007 A Non-Exploitable Strategy Two Scenarios: • No False Claims - NFC • With False Claims - FC False claims only change the probability p. We can incorporate the cost of verification. Key Idea: Save part of the money obtained in successful transactions in excess of the opportunity cost. 11/29/2007 Trust and Reputation System 62
UCDavis, ecs 251 Fall 2007 A Non-Exploitable Strategy Two Scenarios: • No False Claims - NFC • With False Claims - FC False claims only change the probability p. We can incorporate the cost of verification. Key Idea: Save part of the money obtained in successful transactions in excess of the opportunity cost. 11/29/2007 Trust and Reputation System 62
 UCDavis, ecs 251 Fall 2007 A Non-Exploitable Strategy Example. The buyer, vb, has $190 to spend on 1 of 3 options: 1. Buying 3 shirts from an unknown seller for $50 each and insuring the transaction for $40. She values each shirt at $100. 2. Buying 2 pairs of shoes from a reliable retailer for $70 each. She thinks each pair is worth $90. 3. Buying 1 game console for $150, from a reliable online shop. She values the console at $240. 11/29/2007 Trust and Reputation System 63
UCDavis, ecs 251 Fall 2007 A Non-Exploitable Strategy Example. The buyer, vb, has $190 to spend on 1 of 3 options: 1. Buying 3 shirts from an unknown seller for $50 each and insuring the transaction for $40. She values each shirt at $100. 2. Buying 2 pairs of shoes from a reliable retailer for $70 each. She thinks each pair is worth $90. 3. Buying 1 game console for $150, from a reliable online shop. She values the console at $240. 11/29/2007 Trust and Reputation System 63
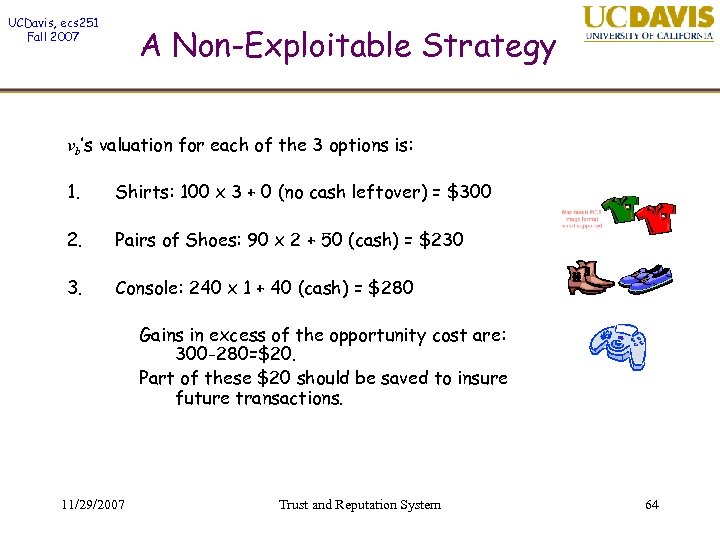 UCDavis, ecs 251 Fall 2007 A Non-Exploitable Strategy vb’s valuation for each of the 3 options is: 1. Shirts: 100 x 3 + 0 (no cash leftover) = $300 2. Pairs of Shoes: 90 x 2 + 50 (cash) = $230 3. Console: 240 x 1 + 40 (cash) = $280 Gains in excess of the opportunity cost are: 300 -280=$20. Part of these $20 should be saved to insure future transactions. 11/29/2007 Trust and Reputation System 64
UCDavis, ecs 251 Fall 2007 A Non-Exploitable Strategy vb’s valuation for each of the 3 options is: 1. Shirts: 100 x 3 + 0 (no cash leftover) = $300 2. Pairs of Shoes: 90 x 2 + 50 (cash) = $230 3. Console: 240 x 1 + 40 (cash) = $280 Gains in excess of the opportunity cost are: 300 -280=$20. Part of these $20 should be saved to insure future transactions. 11/29/2007 Trust and Reputation System 64
 UCDavis, ecs 251 Fall 2007 A Non-Exploitable Strategy The Strategy: 1. 2. 3. 4. Initially only provide references to known agents or those that leave a security deposit. Insure all trade through references provided by trusted agents. Do not provide more insurance than you can recover. Charge at least the lower bound for providing a reference. Save part of the money received “in excess of the opportunity cost”. 11/29/2007 Trust and Reputation System 65
UCDavis, ecs 251 Fall 2007 A Non-Exploitable Strategy The Strategy: 1. 2. 3. 4. Initially only provide references to known agents or those that leave a security deposit. Insure all trade through references provided by trusted agents. Do not provide more insurance than you can recover. Charge at least the lower bound for providing a reference. Save part of the money received “in excess of the opportunity cost”. 11/29/2007 Trust and Reputation System 65
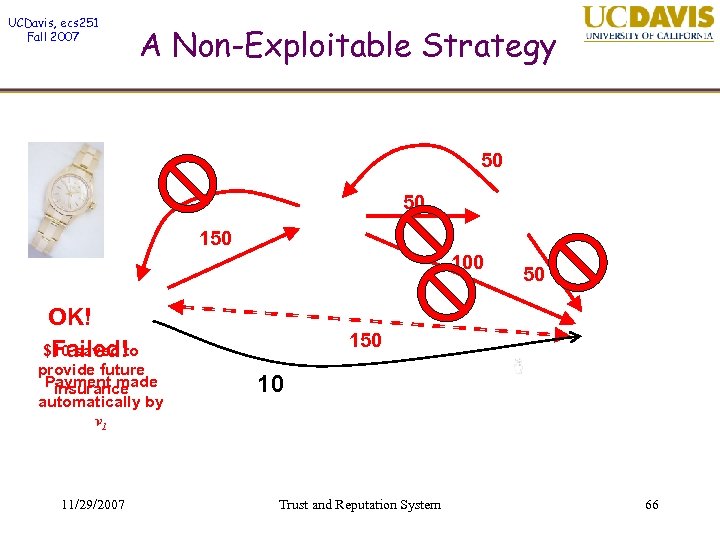 UCDavis, ecs 251 Fall 2007 A Non-Exploitable Strategy 50 50 100 OK! $10 saved to Failed! provide future Payment made insurance automatically by v 1 11/29/2007 50 10 Trust and Reputation System 66
UCDavis, ecs 251 Fall 2007 A Non-Exploitable Strategy 50 50 100 OK! $10 saved to Failed! provide future Payment made insurance automatically by v 1 11/29/2007 50 10 Trust and Reputation System 66
 UCDavis, ecs 251 Fall 2007 Outline • Motivation • The Model – Buying references – Selling references • A Non-Exploitable Strategy • Future Work • Conclusion – Key ideas 11/29/2007 Trust and Reputation System 67
UCDavis, ecs 251 Fall 2007 Outline • Motivation • The Model – Buying references – Selling references • A Non-Exploitable Strategy • Future Work • Conclusion – Key ideas 11/29/2007 Trust and Reputation System 67
 UCDavis, ecs 251 Fall 2007 Future Work • Simulation – sensitivity to estimates of p – growth rate of capital – dynamic behavior • Price Negotiation – should avoid “double spending” problem – fair distribution among insurers of the premium paid 11/29/2007 Trust and Reputation System 68
UCDavis, ecs 251 Fall 2007 Future Work • Simulation – sensitivity to estimates of p – growth rate of capital – dynamic behavior • Price Negotiation – should avoid “double spending” problem – fair distribution among insurers of the premium paid 11/29/2007 Trust and Reputation System 68
 UCDavis, ecs 251 Fall 2007 Outline • Motivation • The Model – Buying references – Selling references • A Non-Exploitable Strategy • Future Work • Conclusion – Key ideas 11/29/2007 Trust and Reputation System 69
UCDavis, ecs 251 Fall 2007 Outline • Motivation • The Model – Buying references – Selling references • A Non-Exploitable Strategy • Future Work • Conclusion – Key ideas 11/29/2007 Trust and Reputation System 69
 UCDavis, ecs 251 Fall 2007 Conclusion Trust. Davis provides: • Accurate Ratings • Non-exploitable strategy for honest agents • Pseudonym change tolerance • Decentralized infrastructure Through the use of References. 11/29/2007 Trust and Reputation System 70
UCDavis, ecs 251 Fall 2007 Conclusion Trust. Davis provides: • Accurate Ratings • Non-exploitable strategy for honest agents • Pseudonym change tolerance • Decentralized infrastructure Through the use of References. 11/29/2007 Trust and Reputation System 70
 UCDavis, ecs 251 Fall 2007 Conclusion Key Ideas: • Incentive Compatibility – Incentive to accurately rate – Incentive to insure – No incentive to change pseudonym • Saving gains in excess of the opportunity cost to insure future transactions. 11/29/2007 Trust and Reputation System 71
UCDavis, ecs 251 Fall 2007 Conclusion Key Ideas: • Incentive Compatibility – Incentive to accurately rate – Incentive to insure – No incentive to change pseudonym • Saving gains in excess of the opportunity cost to insure future transactions. 11/29/2007 Trust and Reputation System 71
 UCDavis, ecs 251 Fall 2007 11/29/2007 The End Trust and Reputation System 72
UCDavis, ecs 251 Fall 2007 11/29/2007 The End Trust and Reputation System 72


