38ea73dcbc2a84fd3e7ab21623b0ec08.ppt
- Количество слайдов: 57

UCCS Network/System Security Research C. Edward Chow Xiaobo Joe Zhou Yu Cai Ganesh Godavari Department of Computer Science University of Colorado at Colorado Springs Some of the research projects are sponsored by the Air Force Research Laboratory, under agreement number F 49620 -03 -1 -0207. It was sponsored by NISSC Summer/Fall 2003 grants. Part of these results are supported by a generous gift from Fujitsu for Internet research. Pfleeger Visit 4/13/2004 1 UCCS Network/System Security

Outline of the Talk Overview of Network/System Security Research Projects at Network/System Lab l Secure Collective Internet Defense (SCOLD): an Intrusion Tolerance System. l Autonomous Anti-DDo. S (A 2 D 2: )Integrated enhanced Snort IDS with multi-level adaptive rate limiting firewall l Secure Groupware for First Responders (SGFR): Integrated Group Rekeying (Keystone) with Instant Massaging (Jabber) on MANET l Secure Access Mobile Ad Hoc Network (SMANET): Implemented PEAP module on free. Radius server, compared PEAP with TTLS l First Responder Sensor Network (FRSN): Track Fire Fighters with Crossbow Mote-based Sensor Network. l Improving System Performance by Qo. S Regulations with Adaptive Resource Management under Cyber Threats l Intelligence/Information Fusion l Secure Information Sharing Pfleeger Visit 4/13/2004 2 UCCS Network/System Security

UCCS Network/System Research Lab n n n Director: Dr. C. Edward Chow (Network/Protocol) Assistant Professor: Dr. Xiaobo Zhou (Distributed Systems; Qo. S) Graduate students: l l l l John Bicknell/Steve Mc. Caughey/Anders Hansmat: Distributed Network Restoration/Network Survivability Hekki Julkunen: Dynamic Packet Filter Chandra Prakash: High Available Linux kernel-based Content Switch Ganesh Godavari: Linux based Secure Web Switch Angela Cearns: Autonomous Anti-DDo. S (A 2 D 2) Testbed Longhua Li: IXP-based Content Switch David Wikinson: Secure DNS (update/query) with multiple indirect routing entries Nirmala Bulusu: Secure Wireless Access; PEAP vs. TTLS; enhance free. Radius server with PEAP module (the above graduated) Yu Cai (Ph. D. research assistant): Proxy Server Based Multipath Routing; Secure Collective Internet Defense; Information Fusion; Ganesh Godavari: (Ph. D. research assistant): Content Switching Rule Conflict Detection; Secure Groupware; First Responder Sensor Network; Secure Information Sharing Frank Watson: enhanced TCP with multiple routes (User Mode Linux) Paul Fong: Wireless AODV Routing for sensor networks Murthy Andukuri/Jing Wu: i. SCSI/VPN/MPLS Secure Qo. S Storage Network. Patricia Ferrao/Merlin Vincent: Web-based Collaborative System Sarah Jelinek: Enterprise Intrusion Detection and Response System (A 2 D 2 V 2). UCCS Network/System Security Pfleeger Visit 4/13/2004 3
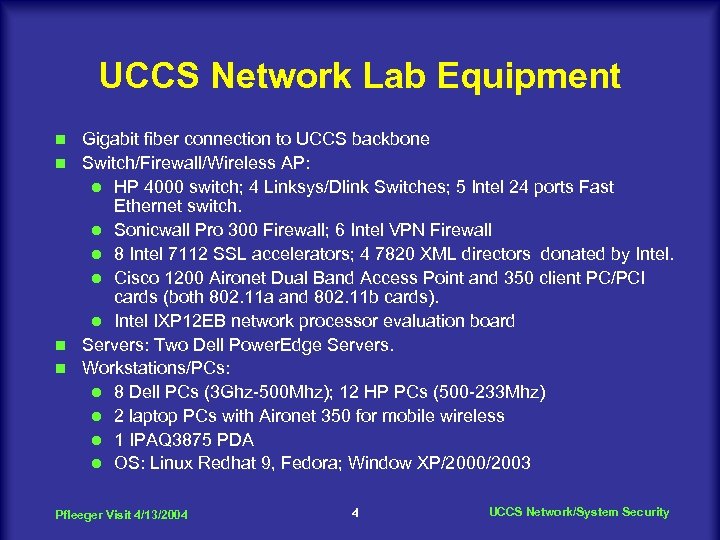
UCCS Network Lab Equipment Gigabit fiber connection to UCCS backbone n Switch/Firewall/Wireless AP: l HP 4000 switch; 4 Linksys/Dlink Switches; 5 Intel 24 ports Fast Ethernet switch. l Sonicwall Pro 300 Firewall; 6 Intel VPN Firewall l 8 Intel 7112 SSL accelerators; 4 7820 XML directors donated by Intel. l Cisco 1200 Aironet Dual Band Access Point and 350 client PC/PCI cards (both 802. 11 a and 802. 11 b cards). l Intel IXP 12 EB network processor evaluation board n Servers: Two Dell Power. Edge Servers. n Workstations/PCs: l 8 Dell PCs (3 Ghz-500 Mhz); 12 HP PCs (500 -233 Mhz) l 2 laptop PCs with Aironet 350 for mobile wireless l 1 IPAQ 3875 PDA l OS: Linux Redhat 9, Fedora; Window XP/2000/2003 n Pfleeger Visit 4/13/2004 4 UCCS Network/System Security

Intrusion Related Research Areas Intrusion Prevention l General Security Policy l Ingress/Egress Filtering n Intrusion Detection l Honey pot l Host-based IDS Tripwire l Anomaly Detection l Misuse Detection n Intrusion Response l Identification/Traceback/Pushback n l Intrusion Pfleeger Visit 4/13/2004 Tolerance 5 UCCS Network/System Security
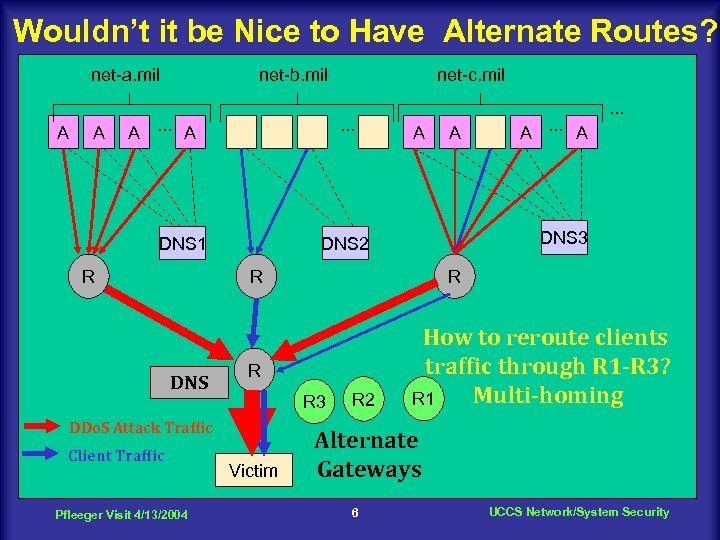
Wouldn’t it be Nice to Have Alternate Routes? net-a. mil A A net-b. mil A. . . A . . . DNS 1 R net-c. mil A Client Traffic Pfleeger Visit 4/13/2004 R R R 3 DDo. S Attack Traffic Victim A. . . A DNS 3 DNS 2 R DNS A . . . R 2 How to reroute clients traffic through R 1 -R 3? Multi-homing R 1 Alternate Gateways 6 UCCS Network/System Security
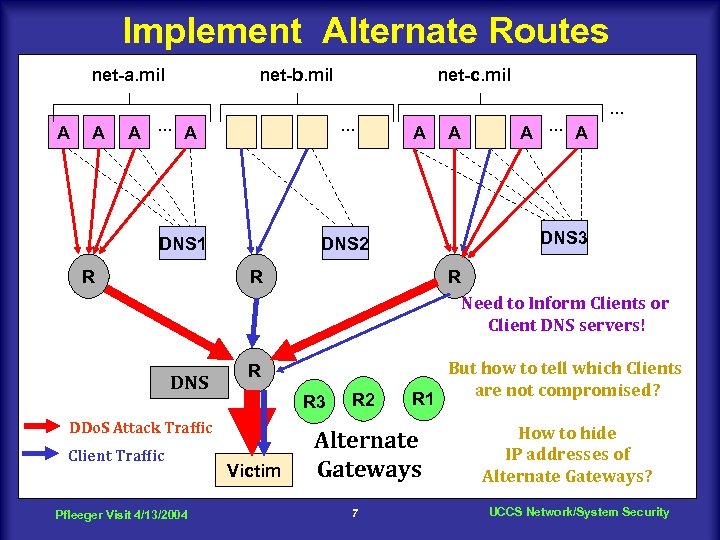
Implement Alternate Routes net-a. mil A A net-b. mil A. . . A . . . DNS 1 R net-c. mil A A A. . . A . . . DNS 3 DNS 2 R R Need to Inform Clients or Client DNS servers! DNS R R 3 DDo. S Attack Traffic Client Traffic Pfleeger Visit 4/13/2004 Victim R 2 R 1 Alternate Gateways 7 But how to tell which Clients are not compromised? How to hide IP addresses of Alternate Gateways? UCCS Network/System Security
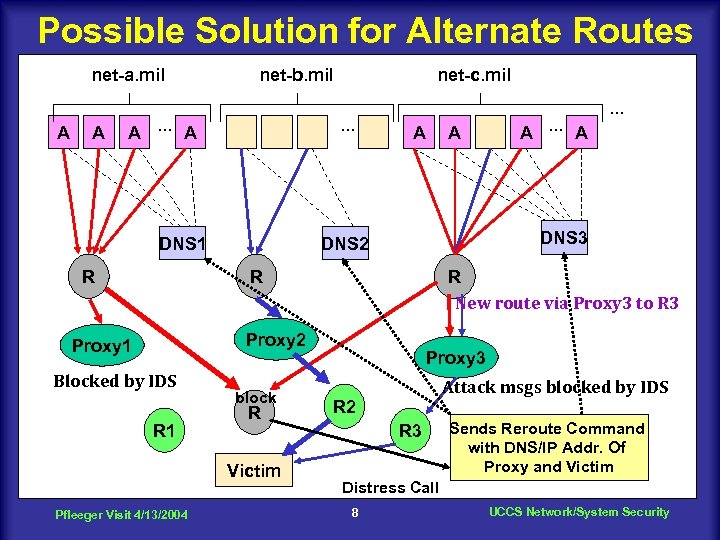
Possible Solution for Alternate Routes net-a. mil A A net-b. mil A. . . A . . . DNS 1 R net-c. mil A A DNS 3 DNS 2 R R New route via Proxy 3 to R 3 Proxy 2 Proxy 1 Blocked by IDS R 1 block R Victim Pfleeger Visit 4/13/2004 A. . . A . . . Proxy 3 Attack msgs blocked by IDS R 2 R 3 Sends Reroute Command with DNS/IP Addr. Of Proxy and Victim Distress Call 8 UCCS Network/System Security
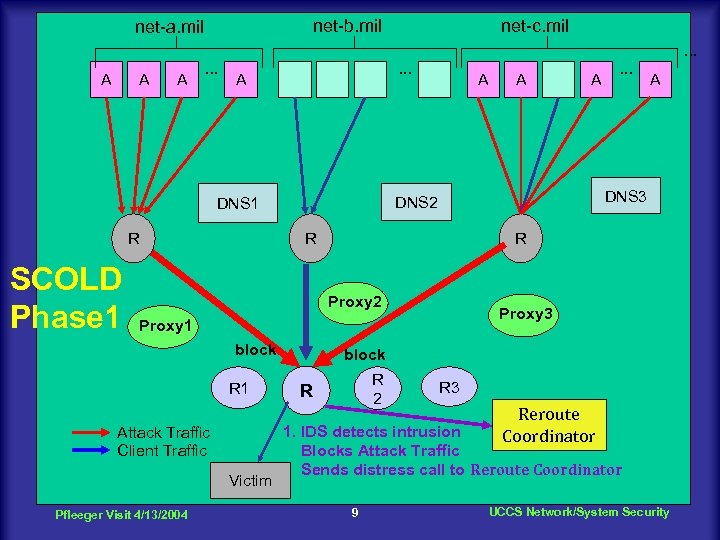
net-b. mil net-a. mil net-c. mil. . . A A A . . . A SCOLD Phase 1 Victim Pfleeger Visit 4/13/2004 A Proxy 3 Proxy 1 block . . . R Proxy 2 Attack Traffic Client Traffic A DNS 3 R R 1 A DNS 2 DNS 1 R A block R 2 R R 3 Reroute Coordinator 1. IDS detects intrusion Blocks Attack Traffic Sends distress call to Reroute Coordinator 9 UCCS Network/System Security
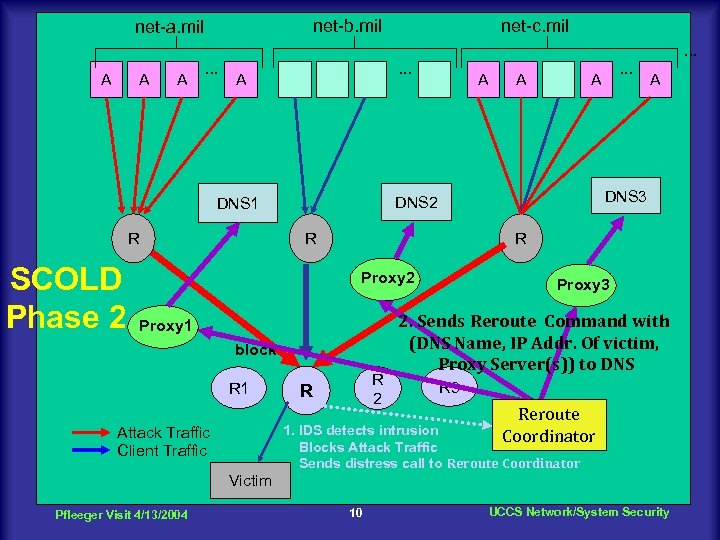
net-b. mil net-a. mil net-c. mil. . . A A A . . . A SCOLD Phase 2 . . . A A DNS 3 R R Proxy 2 Proxy 1 block R 1 A DNS 2 DNS 1 R A R 2 R Proxy 3 2. Sends Reroute Command with (DNS Name, IP Addr. Of victim, Proxy Server(s)) to DNS R 3 Reroute 1. IDS detects intrusion Coordinator Blocks Attack Traffic Sends distress call to Reroute Coordinator Attack Traffic Client Traffic Victim Pfleeger Visit 4/13/2004 10 UCCS Network/System Security
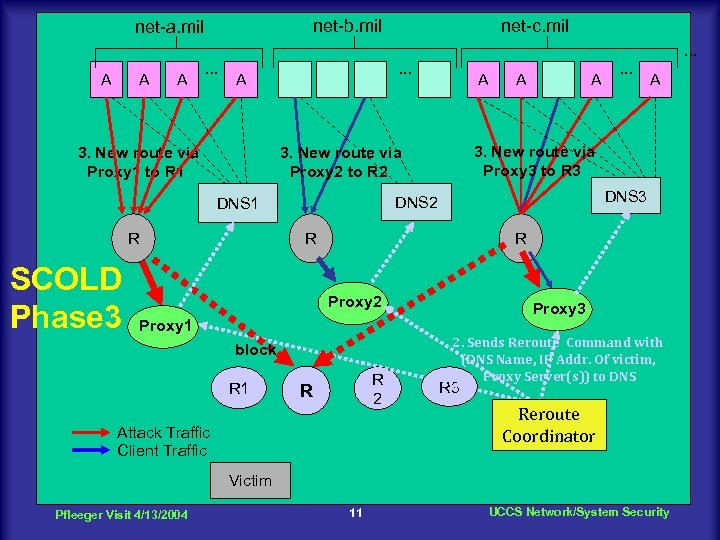
net-b. mil net-a. mil net-c. mil. . . A A A . . . A 3. New route via Proxy 1 to R 1 R A . . . A DNS 3 DNS 2 R R Proxy 2 Proxy 1 block R 1 A 3. New route via Proxy 3 to R 3 3. New route via Proxy 2 to R 2 DNS 1 SCOLD Phase 3 A R 2 R Attack Traffic Client Traffic Proxy 3 2. Sends Reroute Command with (DNS Name, IP Addr. Of victim, Proxy Server(s)) to DNS R 3 Reroute Coordinator Victim Pfleeger Visit 4/13/2004 11 UCCS Network/System Security
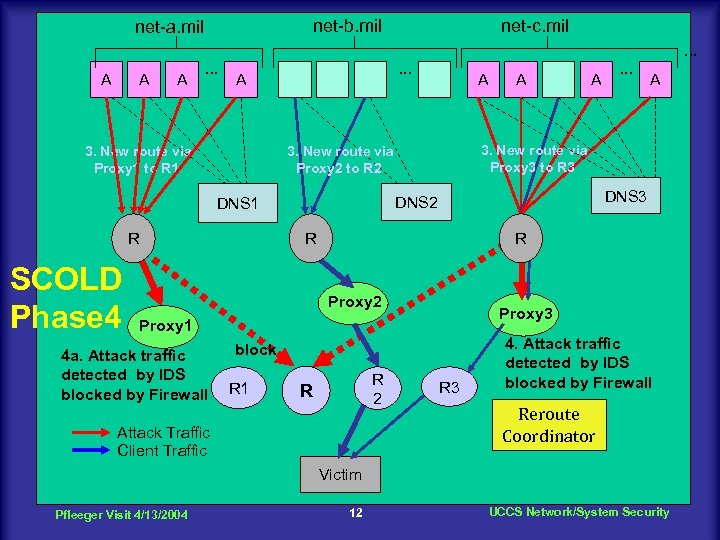
net-b. mil net-a. mil net-c. mil. . . A A A . . . A 3. New route via Proxy 1 to R 1 R . . . A DNS 3 R R Proxy 3 Proxy 1 block R 1 A DNS 2 Proxy 2 4 a. Attack traffic detected by IDS blocked by Firewall A 3. New route via Proxy 3 to R 3 3. New route via Proxy 2 to R 2 DNS 1 SCOLD Phase 4 A R 2 R Attack Traffic Client Traffic R 3 4. Attack traffic detected by IDS blocked by Firewall Reroute Coordinator Victim Pfleeger Visit 4/13/2004 12 UCCS Network/System Security
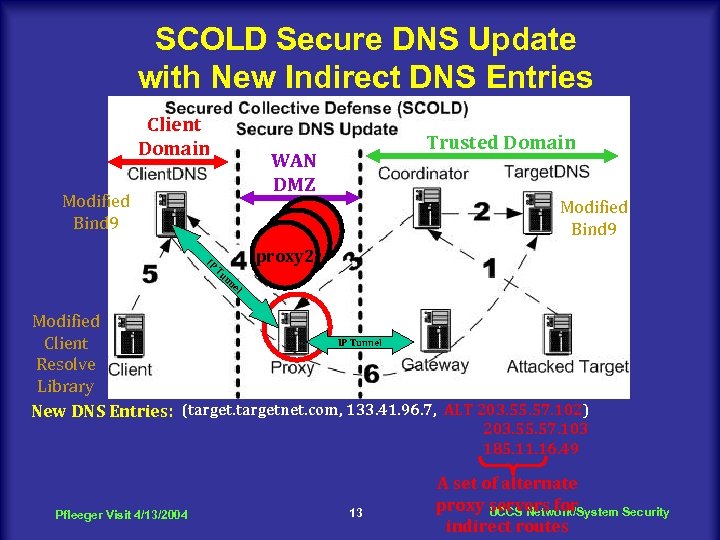
SCOLD Secure DNS Update with New Indirect DNS Entries Client Domain Trusted Domain WAN DMZ Modified Bind 9 IP proxy 2 Tu nn el Modified IP Tunnel Client Resolve Library New DNS Entries: (targetnet. com, 133. 41. 96. 7, ALT 203. 55. 57. 102) 203. 55. 57. 103 185. 11. 16. 49 Pfleeger Visit 4/13/2004 13 A set of alternate proxy UCCS Network/System Security servers for indirect routes
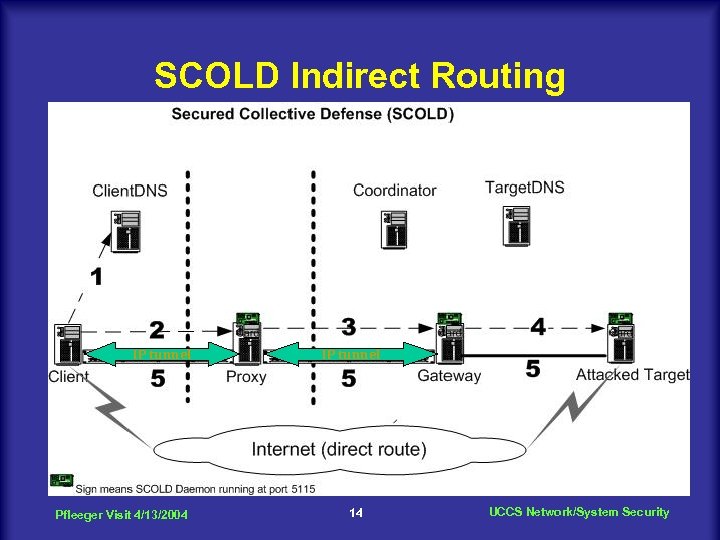
SCOLD Indirect Routing IP tunnel Pfleeger Visit 4/13/2004 IP tunnel 14 UCCS Network/System Security

SCOLD Indirect Routing with Client running SCOLD client daemon IP tunnel Pfleeger Visit 4/13/2004 IP tunnel 15 UCCS Network/System Security
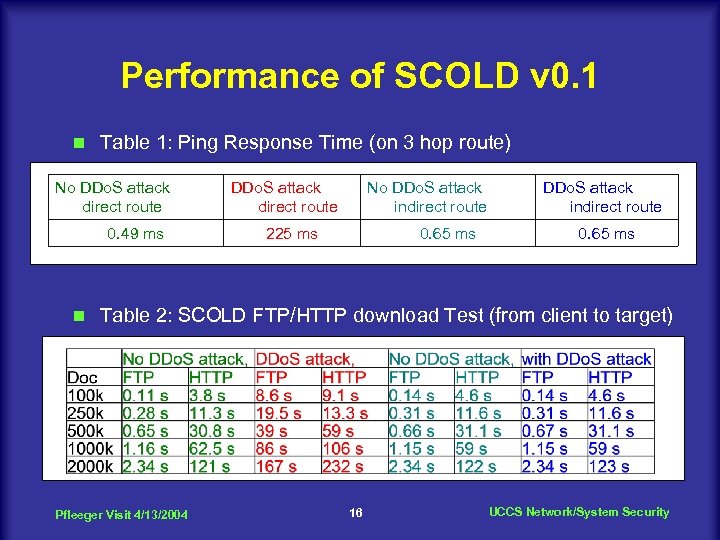
Performance of SCOLD v 0. 1 n Table 1: Ping Response Time (on 3 hop route) No DDo. S attack direct route 0. 49 ms n DDo. S attack direct route No DDo. S attack indirect route 225 ms 0. 65 ms DDo. S attack indirect route 0. 65 ms Table 2: SCOLD FTP/HTTP download Test (from client to target) Pfleeger Visit 4/13/2004 16 UCCS Network/System Security

Secure Collective Defense n Main Idea Explore secure alternate paths for clients to come in; Utilize geographically separated proxy servers. n Goal: l l n Provide secure alternate routes Hide IP addresses of alternate gateways Techniques: l Multiple Path (Indirect) Routing l Enhanced Secure DNS extension: how to inform client DNS servers to add new DNS entries with alternate routes (Not your normal DNS name/IP address mapping entry). l Utilize a consortium of Proxy servers with IDS that hides the IP address of alternate gateways. l Partition clients to come in at different proxy servers. can help identify the origin of spoofed attacks! l How clients use the new multiple path indirect DNS entries and route traffic through proxy servers? Use Sock protocol, modify resolver library Pfleeger Visit 4/13/2004 17 UCCS Network/System Security
Current SCOLD Project Results Proposed new DNS entries for intrusion tolerance, containing multiple proxy servers info for establishing indirect routes. n Modified Bind 9 DNS server to accept secure DNS updates and to serve queries with new indirect DNS entries. n Developed new secure DNS update utility to securely update target zone file in the new enhanced Bind 9 DNS server. n Implemented new secure indirect routing protocol l to allow client DNS to query target DNS during DDo. S attack. l to allow client to communicate with target server through proxy server and alternate gateway. n Pfleeger Visit 4/13/2004 18 UCCS Network/System Security
Benefits of Secure Collective Defense Security l When attacked, users switch to different routes dynamically l Urgent/critical packets sent over multiple routes simultaneously l Encrypted content sent over multiple routes l Information on DDo. S attacks used to isolate source of attacks n Reliability: l Users can choose most reliable route dynamically l Packet content spread over multiple routes l Use redundant transmission or error correction to reduce PLR n Performance: l Multiple indirect routes provide additional bandwidth l Can be used for dynamic bandwidth provisioning n Pfleeger Visit 4/13/2004 19 UCCS Network/System Security
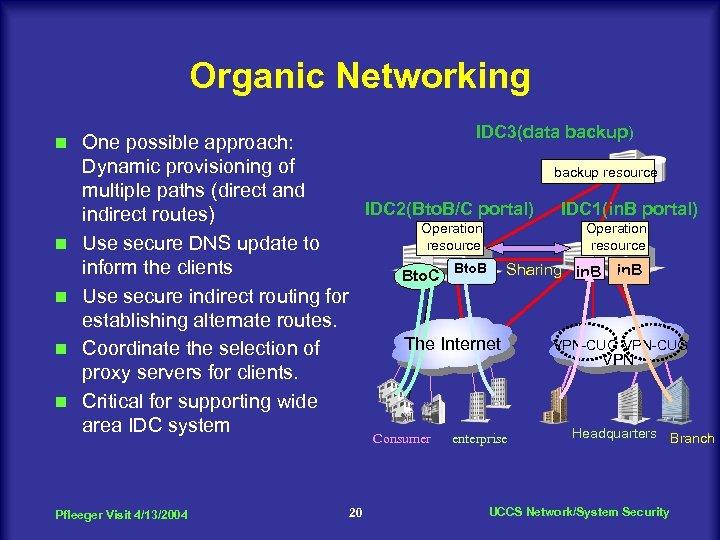
Organic Networking n n n IDC 3(data backup) One possible approach: Dynamic provisioning of backup resource multiple paths (direct and IDC 2(Bto. B/C portal) IDC 1(in. B portal) indirect routes) Operation Use secure DNS update to resource inform the clients Bto. C Bto. B Sharing in. B Use secure indirect routing for establishing alternate routes. VPN-CUG The Internet Coordinate the selection of VPN proxy servers for clients. Critical for supporting wide area IDC system Headquarters Consumer Pfleeger Visit 4/13/2004 20 enterprise UCCS Network/System Security Branch

A 2 D 2: Autonomous Anti DDo. S n Main Idea Integrate enhanced IDS with adaptive firewall for autonomous intrusion defense. n Goal: l l n Automate adaptive intrusion handling triggered by enhanced intrusion detection Investigate the impact of various intrusion types on Qo. S Techniques: l Enhanced Snort Plug-in with subnet spoofing detection l Adaptive rate limiting firewall with user defined threshold and intrusion history. Pfleeger Visit 4/13/2004 21 UCCS Network/System Security
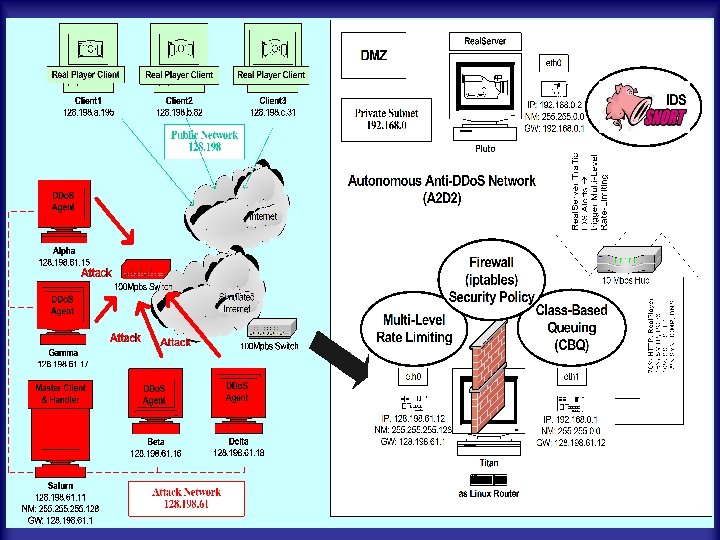
Pfleeger Visit 4/13/2004 22 UCCS Network/System Security
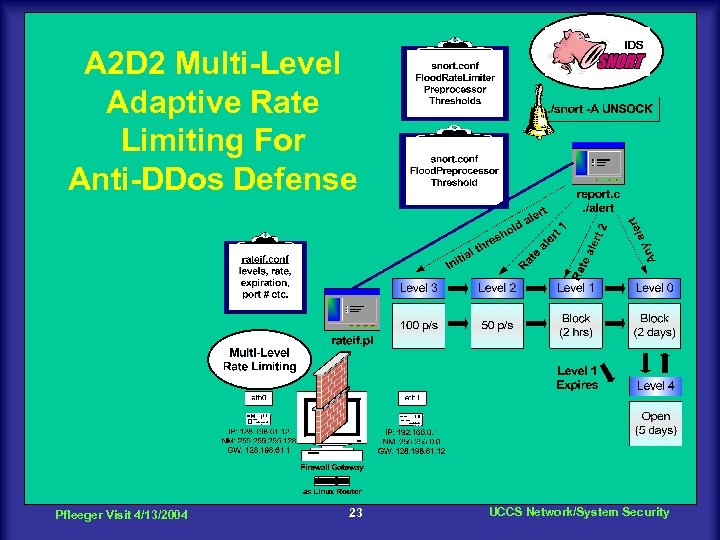
A 2 D 2 Multi-Level Adaptive Rate Limiting For Anti-DDos Defense Pfleeger Visit 4/13/2004 23 UCCS Network/System Security
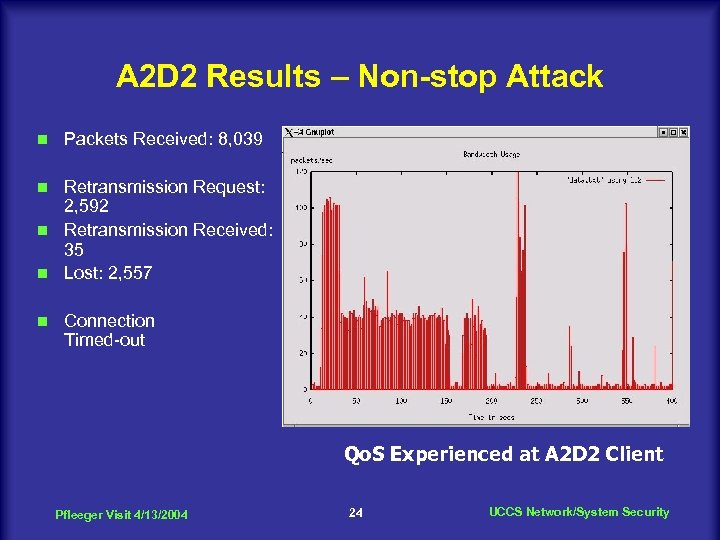
A 2 D 2 Results – Non-stop Attack n Packets Received: 8, 039 Retransmission Request: 2, 592 n Retransmission Received: 35 n Lost: 2, 557 n n Connection Timed-out Qo. S Experienced at A 2 D 2 Client Pfleeger Visit 4/13/2004 24 UCCS Network/System Security
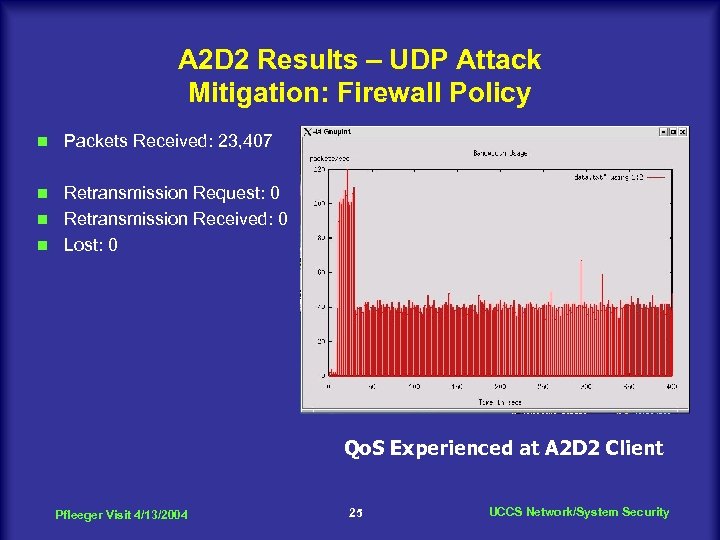
A 2 D 2 Results – UDP Attack Mitigation: Firewall Policy n Packets Received: 23, 407 Retransmission Request: 0 n Retransmission Received: 0 n Lost: 0 n Qo. S Experienced at A 2 D 2 Client Pfleeger Visit 4/13/2004 25 UCCS Network/System Security
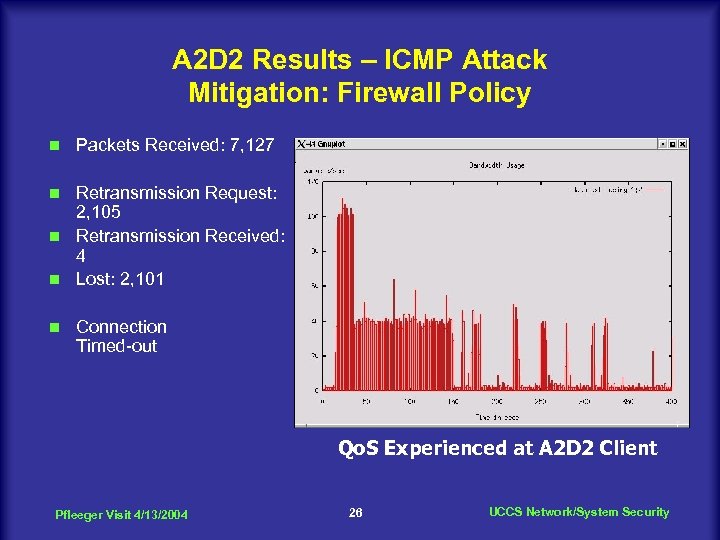
A 2 D 2 Results – ICMP Attack Mitigation: Firewall Policy n Packets Received: 7, 127 Retransmission Request: 2, 105 n Retransmission Received: 4 n Lost: 2, 101 n n Connection Timed-out Qo. S Experienced at A 2 D 2 Client Pfleeger Visit 4/13/2004 26 UCCS Network/System Security
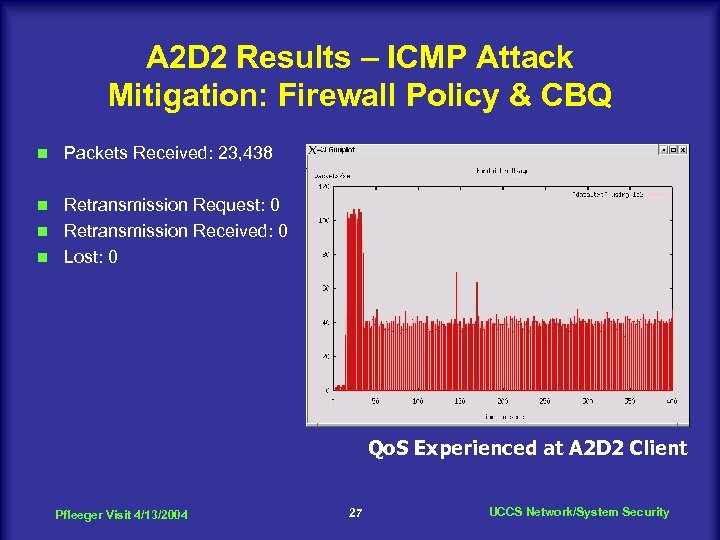
A 2 D 2 Results – ICMP Attack Mitigation: Firewall Policy & CBQ n Packets Received: 23, 438 Retransmission Request: 0 n Retransmission Received: 0 n Lost: 0 n Qo. S Experienced at A 2 D 2 Client Pfleeger Visit 4/13/2004 27 UCCS Network/System Security
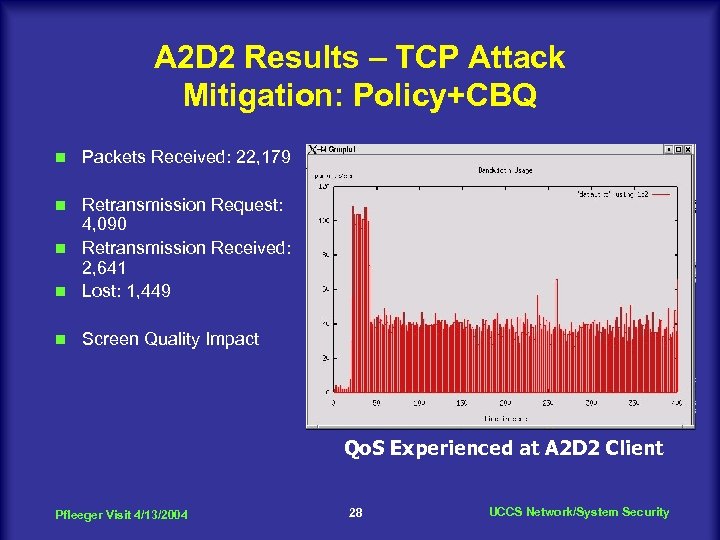
A 2 D 2 Results – TCP Attack Mitigation: Policy+CBQ n Packets Received: 22, 179 Retransmission Request: 4, 090 n Retransmission Received: 2, 641 n Lost: 1, 449 n n Screen Quality Impact Qo. S Experienced at A 2 D 2 Client Pfleeger Visit 4/13/2004 28 UCCS Network/System Security
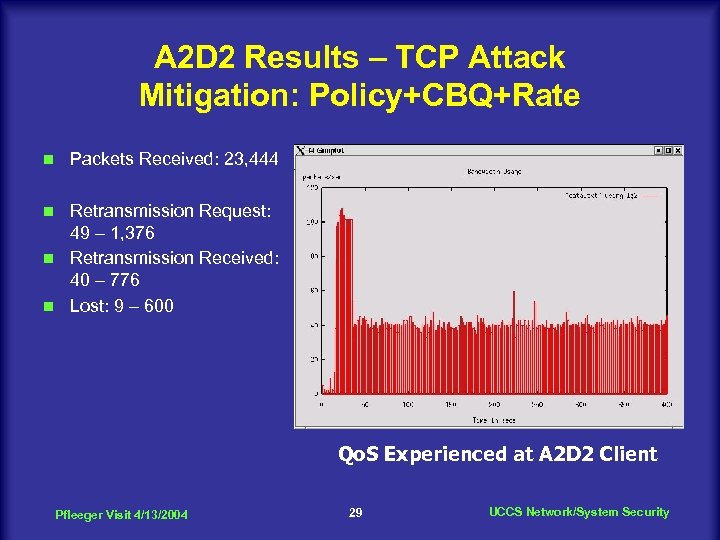
A 2 D 2 Results – TCP Attack Mitigation: Policy+CBQ+Rate n Packets Received: 23, 444 Retransmission Request: 49 – 1, 376 n Retransmission Received: 40 – 776 n Lost: 9 – 600 n Qo. S Experienced at A 2 D 2 Client Pfleeger Visit 4/13/2004 29 UCCS Network/System Security
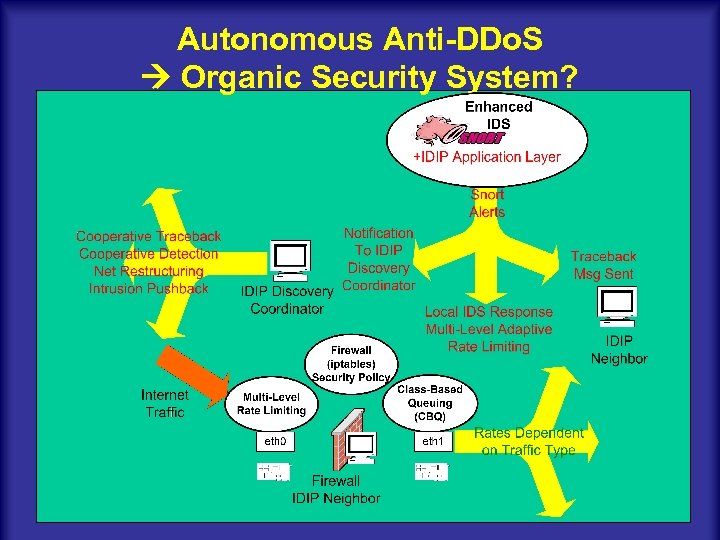
Autonomous Anti-DDo. S Organic Security System? Pfleeger Visit 4/13/2004 30 UCCS Network/System Security

SGFR: Secure Groupware for First Responder n Main Idea design a framework for enhancing security of groupware packages such as instant messenger and video monitoring/conferencing tool. Goal: l Investigate proper interface between group rekeying system and groupware. l Develop secure instant messaging system with remote group file download and remote display. l Experiment the prototype software on PDA with mobile ad hoc network. l Integrate with stress level and tool usage effectiveness evaluation n This is a joint project with Dr. Chip Benight of psychology department at UCCS. n n Techniques: l Scalable group key management (Keystone from UT Austin) l Efficient groupware (Jabber Instant Messaging System) l Mobile Ad Hoc Network (NIST) Pfleeger Visit 4/13/2004 31 UCCS Network/System Security

SGFR Features Psychology Evaluation Stress Level Tracking Effectiveness of Tool Usage (Keyboard/Mouse Event Tracking, History of Commands, Mistakes, Popup Quiz? ) Security Enhanced Groupware Instant messenger (Jabber. X) Group Key Managment Secure Group Rekeying system (Keystone) Pfleeger Visit 4/13/2004 Group Communication Server Instant Messaging Server (Jabber) 32 UCCS Network/System Security
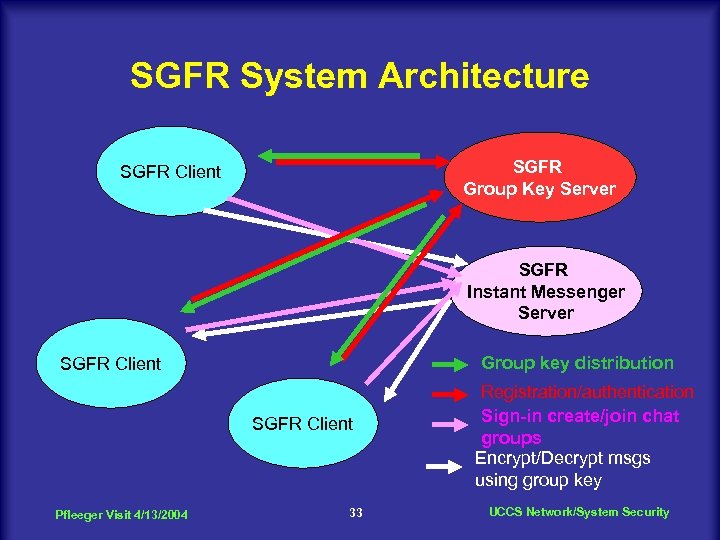
SGFR System Architecture SGFR Group Key Server SGFR Client SGFR Instant Messenger Server Group key distribution SGFR Client Pfleeger Visit 4/13/2004 33 Registration/authentication Sign-in create/join chat groups Encrypt/Decrypt msgs using group key UCCS Network/System Security
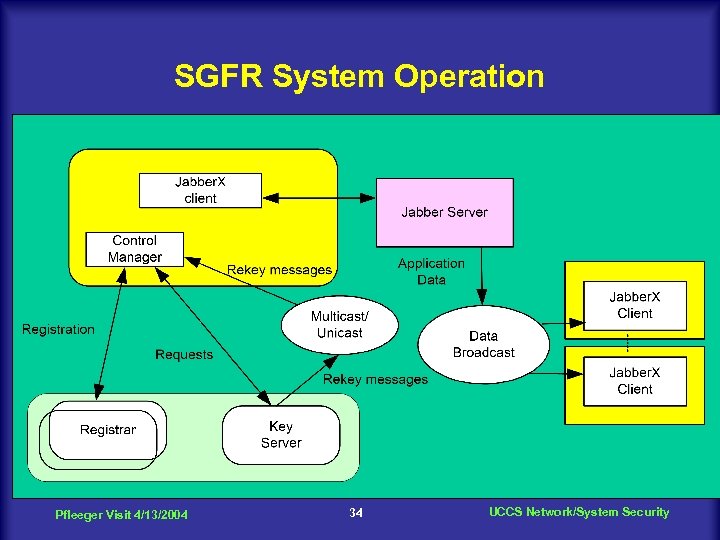
SGFR System Operation Pfleeger Visit 4/13/2004 34 UCCS Network/System Security

Associate Jabber. X client with Keyserver and Jabber server n n n Users login to the Jabber server If login successful, the client registers with the Keyserver by presenting digital certificate. When a user creates/joins a group, the Keyserver issues a group key to the client. When a user leaves the group, the Keyserver generates a new group key for the remaining members of the group. Group key can be refreshed periodically. Group key are used to encrypt data and authenticate the group. Pfleeger Visit 4/13/2004 35 UCCS Network/System Security
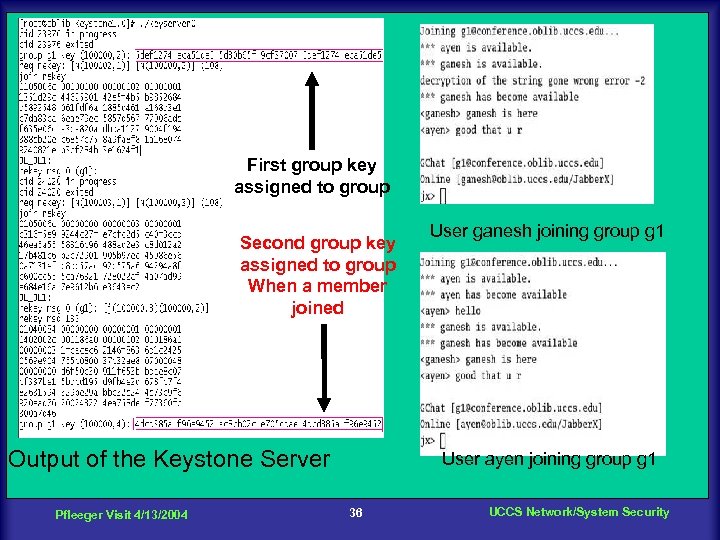
First group key assigned to group Second group key assigned to group When a member joined Output of the Keystone Server Pfleeger Visit 4/13/2004 User ganesh joining group g 1 User ayen joining group g 1 36 UCCS Network/System Security
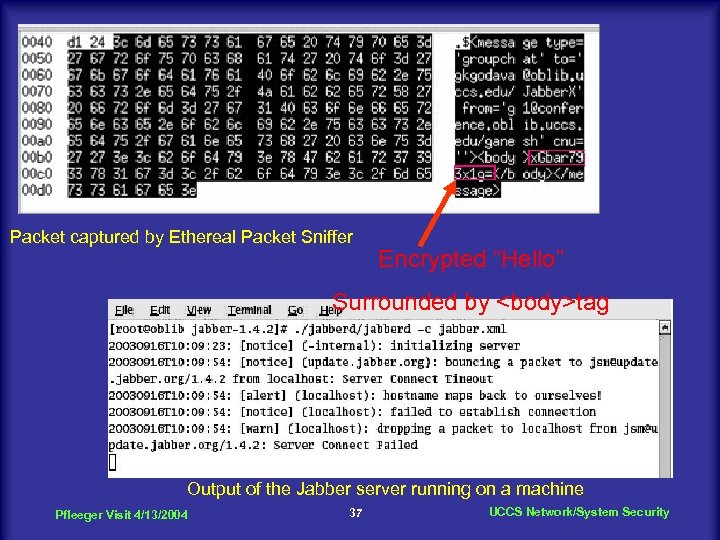
Packet captured by Ethereal Packet Sniffer Encrypted “Hello” Surrounded by <body>tag Output of the Jabber server running on a machine Pfleeger Visit 4/13/2004 37 UCCS Network/System Security
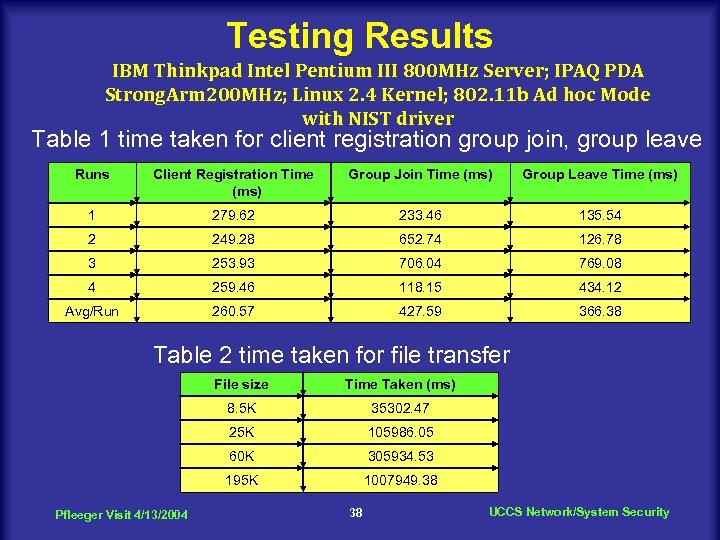
Testing Results IBM Thinkpad Intel Pentium III 800 MHz Server; IPAQ PDA Strong. Arm 200 MHz; Linux 2. 4 Kernel; 802. 11 b Ad hoc Mode with NIST driver Table 1 time taken for client registration group join, group leave Runs Client Registration Time (ms) Group Join Time (ms) Group Leave Time (ms) 1 279. 62 233. 46 135. 54 2 249. 28 652. 74 126. 78 3 253. 93 706. 04 769. 08 4 259. 46 118. 15 434. 12 Avg/Run 260. 57 427. 59 366. 38 Table 2 time taken for file transfer File size 8. 5 K 35302. 47 25 K 105986. 05 60 K 305934. 53 195 K Pfleeger Visit 4/13/2004 Time Taken (ms) 1007949. 38 38 UCCS Network/System Security

Conclusion A secure group communication software package SGFR v. 0 was developed. l Use Digital Certificate to authenticate client access. l Group keys are distributed when members join/leave or based on some time period. l Group key is used to encrypted the messages. l Enhanced Jabber-based text chat with remote file download and remote display. l Lesson 1: Fire fighters do not like stylus input and they carry heavy load!! l Lesson 2: Fire fighter don’t care security; Police do!! n Ported the SGFR v. 0 to run on handheld devices include i. PAQ PDA running Linux and Sony Palm. Top with 802. 11 b mobile ad hoc network. n Pfleeger Visit 4/13/2004 39 UCCS Network/System Security
Secure Wireless Access Control n Goal: l Compare performance of two proposed wireless authentication protocols, PEAP vs. TTLS. l Develop a PEAP module for free. Radius server on Linux. n Techniques/Tools used: l Xsupplicant, Window XP l free. Radius, Win 2003 server l Open. SSL Pfleeger Visit 4/13/2004 40 UCCS Network/System Security
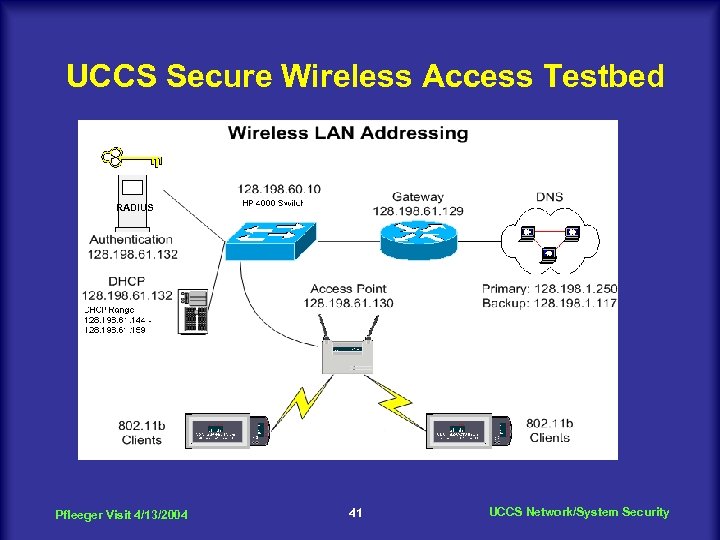
UCCS Secure Wireless Access Testbed RADIUS Client Pfleeger Visit 4/13/2004 41 UCCS Network/System Security
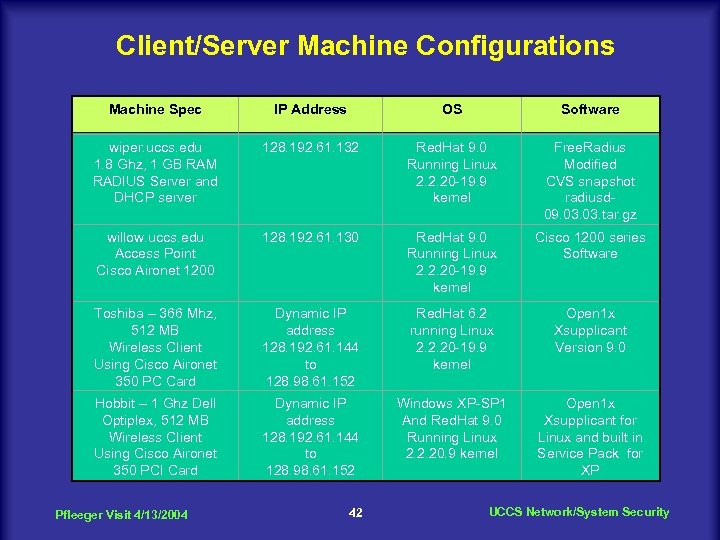
Client/Server Machine Configurations Machine Spec IP Address OS Software wiper. uccs. edu 1. 8 Ghz, 1 GB RAM RADIUS Server and DHCP server 128. 192. 61. 132 Red. Hat 9. 0 Running Linux 2. 2. 20 -19. 9 kernel Free. Radius Modified CVS snapshot radiusd 09. 03. tar. gz willow. uccs. edu Access Point Cisco Aironet 1200 128. 192. 61. 130 Red. Hat 9. 0 Running Linux 2. 2. 20 -19. 9 kernel Cisco 1200 series Software Toshiba – 366 Mhz, 512 MB Wireless Client Using Cisco Aironet 350 PC Card Dynamic IP address 128. 192. 61. 144 to 128. 98. 61. 152 Red. Hat 6. 2 running Linux 2. 2. 20 -19. 9 kernel Open 1 x Xsupplicant Version 9. 0 Hobbit – 1 Ghz Dell Optiplex, 512 MB Wireless Client Using Cisco Aironet 350 PCI Card Dynamic IP address 128. 192. 61. 144 to 128. 98. 61. 152 Windows XP-SP 1 And Red. Hat 9. 0 Running Linux 2. 2. 20. 9 kernel Open 1 x Xsupplicant for Linux and built in Service Pack for XP Pfleeger Visit 4/13/2004 42 UCCS Network/System Security
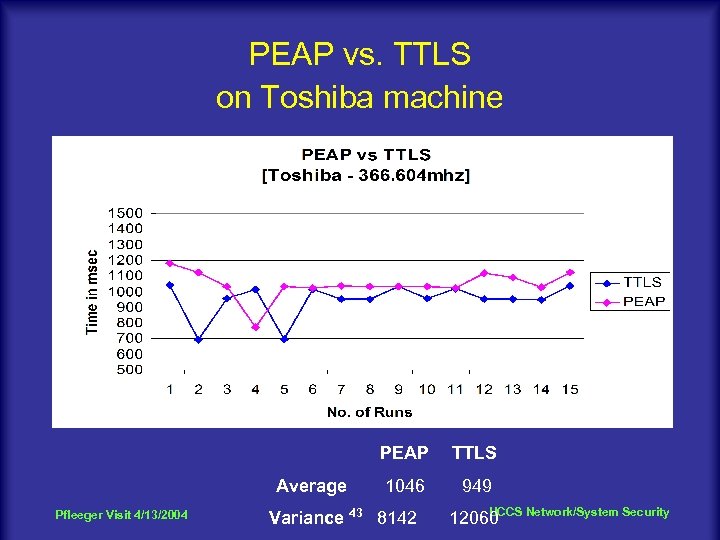
PEAP vs. TTLS on Toshiba machine PEAP Average Pfleeger Visit 4/13/2004 TTLS 1046 949 Variance 43 8142 UCCS 12060 Network/System Security
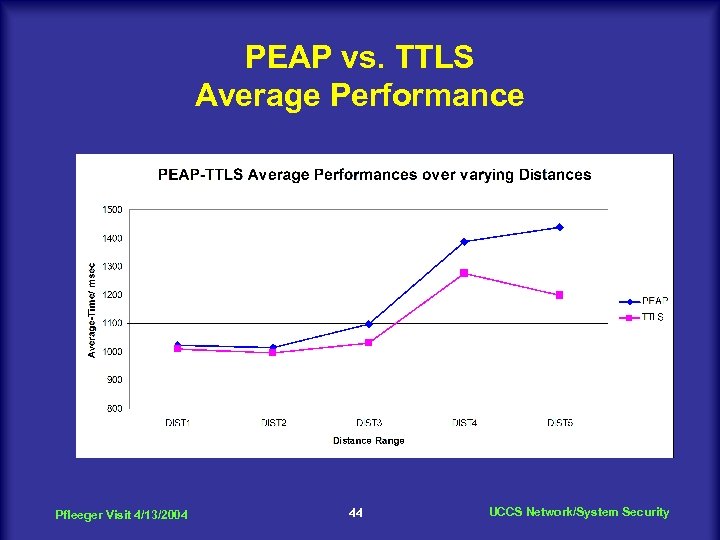
PEAP vs. TTLS Average Performance Pfleeger Visit 4/13/2004 44 UCCS Network/System Security
Conclusion l Developed a Radius Server on Linux that supports both PEAP and TTLS. l PEAP is relatively more influenced by Client’s processor speeds, distance range and network transient nature as compared to TTLS. l Although the higher performance shown by TTLS over PEAP is negligible, it is worth noting that TTLS was outperforming PEAP on an average by 10% in all the tests. l The enhanced Radius Server can serve both Windows and Linux clients. Pfleeger Visit 4/13/2004 45 UCCS Network/System Security

First Responder Sensor Network Goal: How wireless sensor network can assist first responders. Status: Created a wireless sensor testbed with Crossbow Professional Mote Kits and Intel stargateway devices. Current Tasks: n Investigate how to deploy sensor networks (preplanned/dynamically deployed). n Develop algorithms for tracking first responders using wireless sensors. n Security in SMANET+FRSN. Pfleeger Visit 4/13/2004 46 UCCS Network/System Security
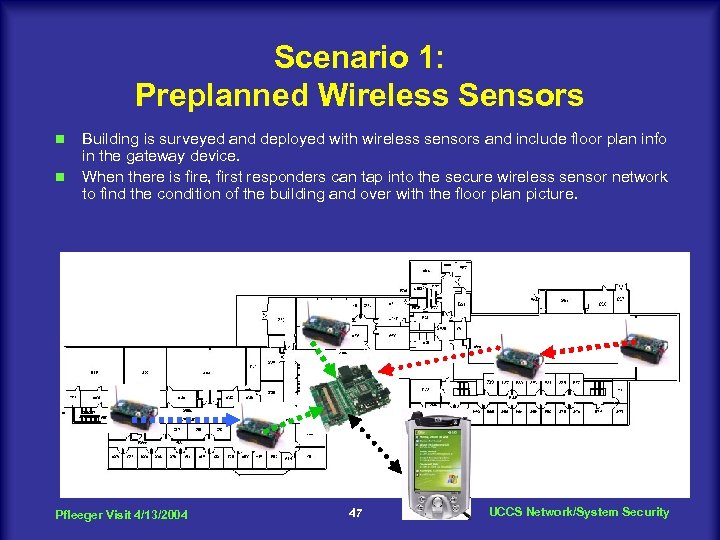
Scenario 1: Preplanned Wireless Sensors n n Building is surveyed and deployed with wireless sensors and include floor plan info in the gateway device. When there is fire, first responders can tap into the secure wireless sensor network to find the condition of the building and over with the floor plan picture. Pfleeger Visit 4/13/2004 47 UCCS Network/System Security
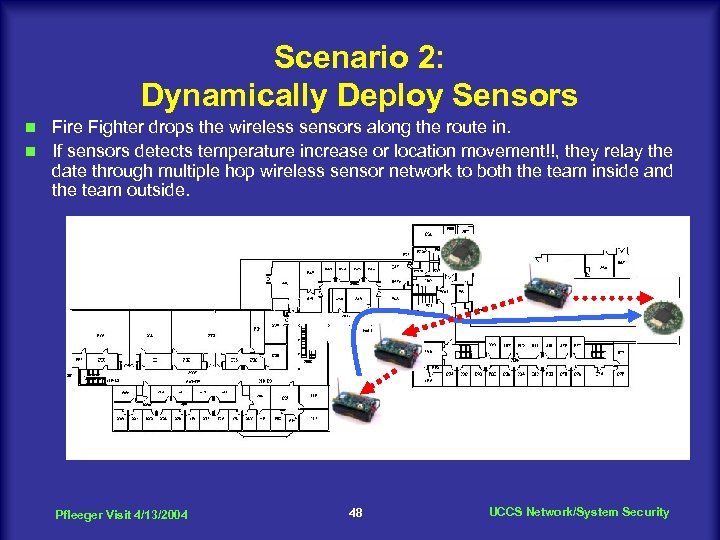
Scenario 2: Dynamically Deploy Sensors Fire Fighter drops the wireless sensors along the route in. n If sensors detects temperature increase or location movement!!, they relay the date through multiple hop wireless sensor network to both the team inside and the team outside. n Pfleeger Visit 4/13/2004 48 UCCS Network/System Security

Secure Access to Sensor Network Terrorist may access the sensors and information on the gateway. n Need authentication for secure access. n Need encryption for avoid sniffing by terrorist. n Need redundancy for fault tolerance and verifying the sensor results. n Pfleeger Visit 4/13/2004 49 UCCS Network/System Security

Improving System Performance by Qo. S Regulations with Adaptive Resource Management under Cyber Threats Xiaobo Joe Zhou Pfleeger Visit 4/13/2004 50 UCCS Network/System Security

Information Fusion n Project Goal: l Intelligence/information fusion among multiple agencies. Starting with federal/state/city agencies extend it to including those from Canada, the United States, and Mexico. l How to exchange, verify, correlate intelligence information for decision support, l How to allocate resources and coordinate sensors in different agencies for a set of tasks with different priority Pfleeger Visit 4/13/2004 51 UCCS Network/System Security

Related Works Multilayered Video l Deliver Multimedia Streams with Flexible Qo. S via a Multicast DAG, Jiong Yang, UIUC, ICDCS 03 l Source-adaptive multilayered multicast algorithms for realtime video distribution, Brett Vickers, IEEE/ACM Transactions on Networking 2000 l An End-to-End Adaptation Protocol for Layered Video Multicast Using Optimal Rate Allocation, Ya-Qin Zhang, IEEE Transaction on Multimedia 2004 n Qo. S and multipath l Admission Control and Dynamic Adaptation for a Proportional-Delay Diff. Serv-Enabled Web Server, Sam C. M. Lee, John C. S. Lui, David K. Y. Yau, SIGMETRICS 2002 l Parallel Access For Mirror Sites in the Internet, Pablo Rodriguez, et al. , Infocom 1999 n Pfleeger Visit 4/13/2004 52 UCCS Network/System Security

Research Direction Data Fusion Operations l Artificial Neural Network for merging results from multiple classifiers l Negotiation/Coordination Protocol [Idian, CIDF, IDMEF, IDIP] l Specific test cases: distributed intrusion detection, compromised node detection, tracking with sensors. n Data transmission in data fusion l Techniques for guaranteeing the quality of service for the prioritized sensor information fusion/delivery l Multilayered video encoding and distribution multilayered information data classification and transportation l Feedback control mechanism n Comment? Other important research topics/directions? n Pfleeger Visit 4/13/2004 53 UCCS Network/System Security

Secure Information Sharing n Project Goal: l Secure Intelligence/information sharing among multiple agencies/organizations l How to exchange, verify information and provide security and non repudiation l How to share information between different agencies and protect against misuse of authority during information sharing Pfleeger Visit 4/13/2004 54 UCCS Network/System Security

Related Works n n n NIST standard on Role Based Access Control An Internet Attribute Certificate Profile for Authorization – RFC 3281 IETF Working Group on Public Key Infrastructure (X. 509) Privilege and Role Management Infrastructure Standards Validation http: //www. permis. org/ Akenti Distributed Access Control http: //www-itg. lbl. gov/ Pfleeger Visit 4/13/2004 55 UCCS Network/System Security

Research Direction Data Sharing Operations l Access control mechanism for sharing information l Mandatory, Discretionary, and Role Based Access Control Mechanisms l Specific test cases: File Distribution, Directory Access Control, secure instant messaging for group communications n Attribute Certificate profile for Authorization l Provide non repudiation and Role Based Access Control l Easy to Manage than certificates -- Short life span than certificates l Provide resource access for short duration; tighter control, misuse avoidance, and increased responsibility n Comment? Other important research topics/directions? n Pfleeger Visit 4/13/2004 56 UCCS Network/System Security

Summary We have innovated ideas on intrusion tolerance We have developed expertise in l Secure DNS system Organic Networking? l Secure multiple path indirect routing Organic Networking? l Autonomous security system with Enhanced IDS+Firewall Organic Security? l Secure wireless access and MANET l Group key management l Secure groupware l Wireless sensor network for first responders l Content switching l Network restoration l Qo. S (proportional differential services) n Developing expertise in information fusion/sharing. n n Pfleeger Visit 4/13/2004 57 UCCS Network/System Security
38ea73dcbc2a84fd3e7ab21623b0ec08.ppt