429dc66567db8505b95b8463941d1de0.ppt
- Количество слайдов: 16
Tutorial on "GRID Computing“ EMBnet Conference 2008 Authenticated Grid access with robot certificates Giuseppe LA ROCCA INFN Catania giuseppe. larocca@ct. infn. it Tutorial on “Grid Computing” EMBnet Conference 2008 CNR - ITB http: //www. libi. it

Private and Public keys • Grid security is based on the concept of public key encryption. Each user (or other entity like a server) has a private key, generated randomly. – The private key must therefore be kept totally secure; if someone can steal it they can impersonate the owner completely. • Each private key is mathematically related to another number called the public key. – As the name suggests this can be known to everyone. – Formally it’s possible to calculate the private key from the public key, but in practice such a calculation is expected to take an unfeasibly long time (the time grows exponentially with the size of the keys). Tutorial on "GRID Computing“, EMBnet Conference 2008, 17 September 2008
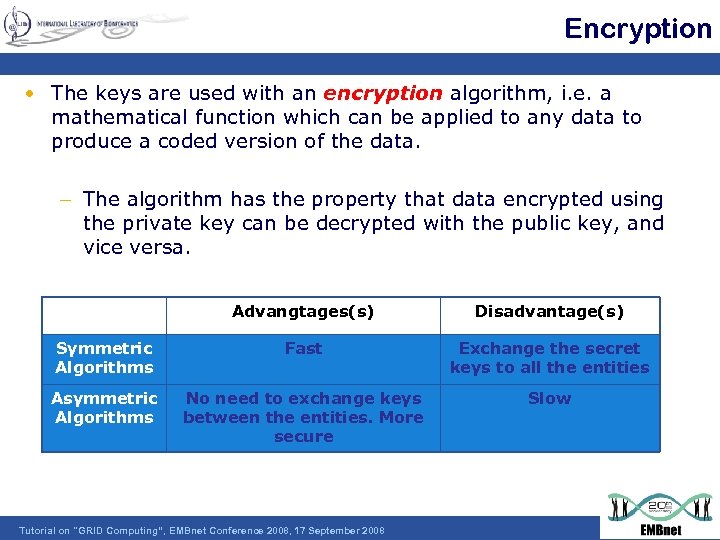
Encryption • The keys are used with an encryption algorithm, i. e. a mathematical function which can be applied to any data to produce a coded version of the data. – The algorithm has the property that data encrypted using the private key can be decrypted with the public key, and vice versa. Advangtages(s) Disadvantage(s) Symmetric Algorithms Fast Exchange the secret keys to all the entities Asymmetric Algorithms No need to exchange keys between the entities. More secure Slow Tutorial on "GRID Computing“, EMBnet Conference 2008, 17 September 2008
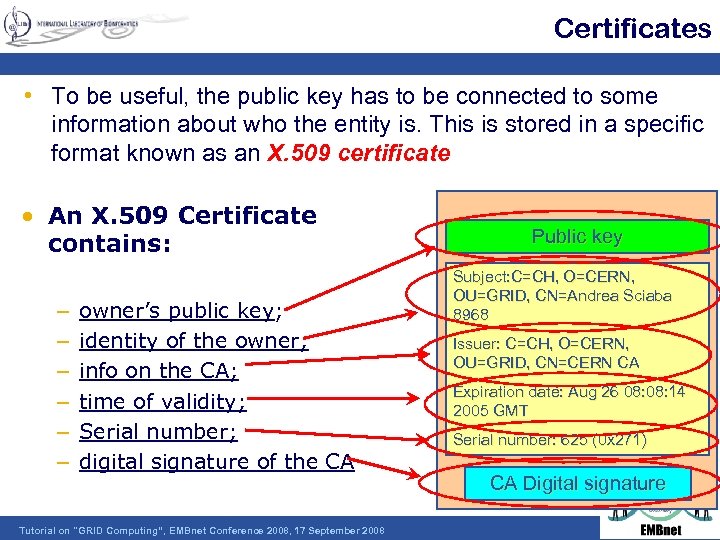
Certificates • To be useful, the public key has to be connected to some information about who the entity is. This is stored in a specific format known as an X. 509 certificate • An X. 509 Certificate contains: – – – owner’s public key; identity of the owner; info on the CA; time of validity; Serial number; digital signature of the CA Tutorial on "GRID Computing“, EMBnet Conference 2008, 17 September 2008 Public key Subject: C=CH, O=CERN, OU=GRID, CN=Andrea Sciaba 8968 Issuer: C=CH, O=CERN, OU=GRID, CN=CERN CA Expiration date: Aug 26 08: 14 2005 GMT Serial number: 625 (0 x 271) CA Digital signature

Certification Authorities • Certificates are issued by a Certification Authority (CA) How to obtain a certificate: The user wants to get a certificate The users meets the RA (Registration Authority) that will verify the user’s identity The RA will provide the user with a key to be used in the registration form to obtain a personal user’s Certificate. Tutorial on "GRID Computing“, EMBnet Conference 2008, 17 September 2008
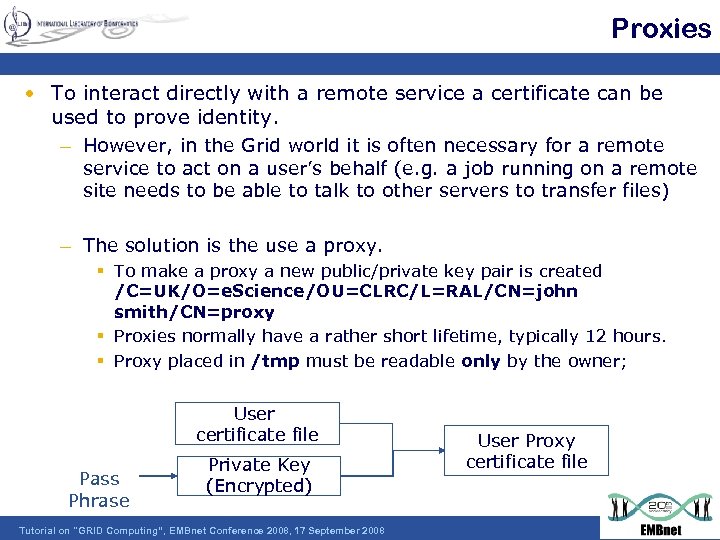
Proxies • To interact directly with a remote service a certificate can be used to prove identity. – However, in the Grid world it is often necessary for a remote service to act on a user’s behalf (e. g. a job running on a remote site needs to be able to talk to other servers to transfer files) – The solution is the use a proxy. § To make a proxy a new public/private key pair is created /C=UK/O=e. Science/OU=CLRC/L=RAL/CN=john smith/CN=proxy § Proxies normally have a rather short lifetime, typically 12 hours. § Proxy placed in /tmp must be readable only by the owner; User certificate file Pass Phrase Private Key (Encrypted) Tutorial on "GRID Computing“, EMBnet Conference 2008, 17 September 2008 User Proxy certificate file

VO & VOMS • Grid users MUST belong to Virtual Organization (VO) – Groups, Role and Capability • Virtual Organization Membership Service (VOMS) is a service responsible to maintain information about roles and privileges of users within a VO. • It grants users authorization to access the resource at VO level. • When the proxy is created one or more VOMS servers are contacted, and they return a mini certificate known as an Attribute Certificate (AC) which is signed by the VO and contains information about group membership and any associated roles within the VO Tutorial on "GRID Computing“, EMBnet Conference 2008, 17 September 2008
![voms-proxy-init [larocca@glite-tutor: ~]$ voms-proxy-init --voms gilda Your identity: /C=IT/O=GILDA/OU=Personal Certificate/L=INFN Catania/CN=Giuseppe La Rocca/Email=giuseppe. larocca@ct. voms-proxy-init [larocca@glite-tutor: ~]$ voms-proxy-init --voms gilda Your identity: /C=IT/O=GILDA/OU=Personal Certificate/L=INFN Catania/CN=Giuseppe La Rocca/Email=giuseppe. larocca@ct.](https://present5.com/presentation/429dc66567db8505b95b8463941d1de0/image-8.jpg)
voms-proxy-init [larocca@glite-tutor: ~]$ voms-proxy-init --voms gilda Your identity: /C=IT/O=GILDA/OU=Personal Certificate/L=INFN Catania/CN=Giuseppe La Rocca/Email=giuseppe. larocca@ct. infn. it Enter GRID pass phrase: Your proxy is valid until Sat Feb 4 01: 08: 28 2006 Creating temporary proxy. . . Done Contacting voms. ct. infn. it: 15001 [/C=IT/O=GILDA/OU=Host/L=INFN Catania/CN=voms. ct. infn. it/Email=emidio. giorgio@ct. infn. it] "gilda“ Done Creating proxy. . . . . Done Your proxy is valid until Sat Feb 4 01: 08: 38 2006 Tutorial on "GRID Computing“, EMBnet Conference 2008, 17 September 2008
![voms-proxy-init [larocca@glite-tutor: ~]$ voms-proxy-info --all subject : /C=IT/O=GILDA/OU=Personal Certificate/L=INFN Catania/CN=Giuseppe La Rocca/Email=giuseppe. larocca@ct. infn. voms-proxy-init [larocca@glite-tutor: ~]$ voms-proxy-info --all subject : /C=IT/O=GILDA/OU=Personal Certificate/L=INFN Catania/CN=Giuseppe La Rocca/Email=giuseppe. larocca@ct. infn.](https://present5.com/presentation/429dc66567db8505b95b8463941d1de0/image-9.jpg)
voms-proxy-init [larocca@glite-tutor: ~]$ voms-proxy-info --all subject : /C=IT/O=GILDA/OU=Personal Certificate/L=INFN Catania/CN=Giuseppe La Rocca/Email=giuseppe. larocca@ct. infn. it/CN=proxy issuer : /C=IT/O=GILDA/OU=Personal Certificate/L=INFN Catania/CN=Giuseppe La Rocca/Email=giuseppe. larocca@ct. infn. it identity : /C=IT/O=GILDA/OU=Personal Certificate/L=INFN Catania/CN=Giuseppe La Rocca/Email=giuseppe. larocca@ct. infn. it Standa type : proxy rd globus strength : 512 bits attrib path : /tmp/x 509 up_u 512 utte ues ib ate timeleft : 11: 55: 52 tr At ific === VO gilda extension information === rt Ce VO : gilda subject : /C=IT/O=GILDA/OU=Personal Certificate/L=INFN Catania/CN=Giuseppe La Rocca/Email=giuseppe. larocca@ct. infn. it issuer : /C=IT/O=GILDA/OU=Host/L=INFN Catania/CN=voms. ct. infn. it/Email=emidio. giorgio@ct. infn. it attribute : /gilda/Role=NULL/Capability=NULL timeleft : 11: 55: 41 Tutorial on "GRID Computing“, EMBnet Conference 2008, 17 September 2008
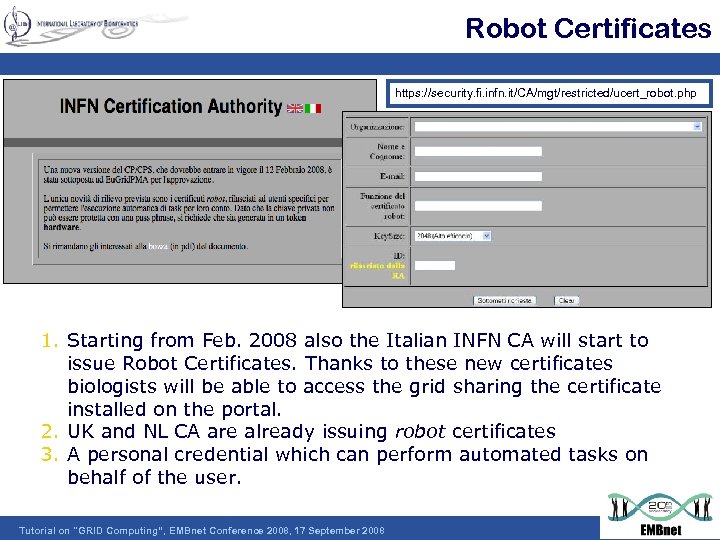
Robot Certificates https: //security. fi. infn. it/CA/mgt/restricted/ucert_robot. php 1. Starting from Feb. 2008 also the Italian INFN CA will start to issue Robot Certificates. Thanks to these new certificates biologists will be able to access the grid sharing the certificate installed on the portal. 2. UK and NL CA are already issuing robot certificates 3. A personal credential which can perform automated tasks on behalf of the user. Tutorial on "GRID Computing“, EMBnet Conference 2008, 17 September 2008
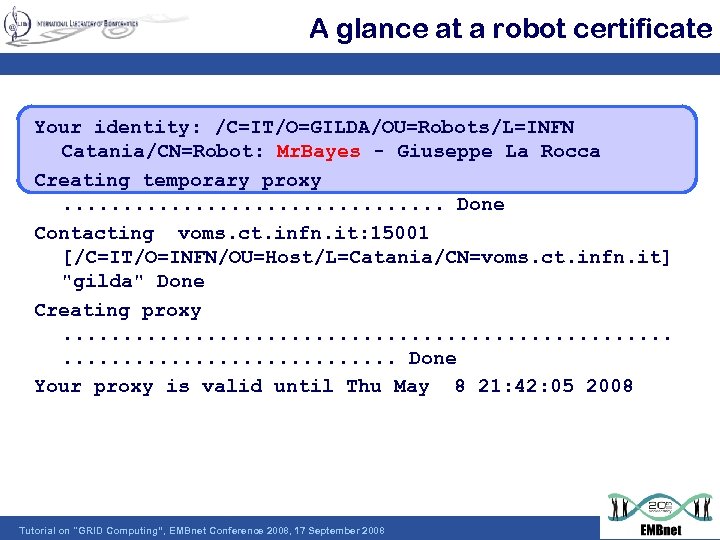
A glance at a robot certificate Your identity: /C=IT/O=GILDA/OU=Robots/L=INFN Catania/CN=Robot: Mr. Bayes - Giuseppe La Rocca Creating temporary proxy. . . . Done Contacting voms. ct. infn. it: 15001 [/C=IT/O=INFN/OU=Host/L=Catania/CN=voms. ct. infn. it] "gilda" Done Creating proxy. . . . . Done Your proxy is valid until Thu May 8 21: 42: 05 2008 Tutorial on "GRID Computing“, EMBnet Conference 2008, 17 September 2008

Robot Certificates • In order to strong reduce the risks of having the portal certificate compromised and improve the security, the INFN CA has decided to issue this new certificate on board of the Aladdin e. Token PRO 32 K smart card. • Each smart card can support several robot certificates: one for each application user wants to share with the other. – An user’s PIN is prompted every time user try to read the certificate on board of the smart card to generate a proxy. – A first prototype of Grid Portal using robot certificate on board of this hardware has been successfully designed. Tutorial on "GRID Computing“, EMBnet Conference 2008, 17 September 2008

Using the e. Token PRO to generate proxies • Once your grid certificate and private key are safely stored on your e. Token, you can generate grid proxies directly from the e. Token. • A shell script mkproxy script was written for this purpose. – This script requires quite a few special programs and libraries, which need to be installed before attempting to use the mkproxy script. • The mkproxy script has been tested on – Windows XP (using cygwin) – Linux Fedora Core 5 (fc 5) – Linux Cent. OS 4, Scientific Linux 4 (rhel 4) – Linux Open. Suse 10 (suse 10) – In the near future we hope to test it on Mac. OS X as well Tutorial on "GRID Computing“, EMBnet Conference 2008, 17 September 2008
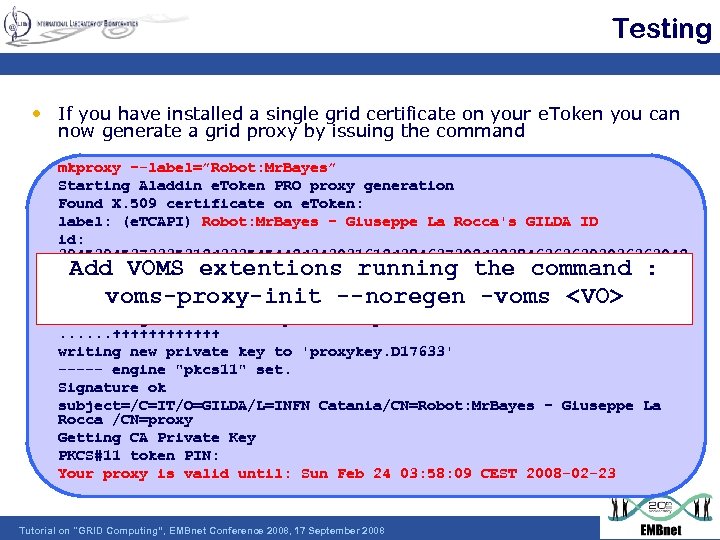
Testing • If you have installed a single grid certificate on your e. Token you can now generate a grid proxy by issuing the command mkproxy –-label=”Robot: Mr. Bayes” Starting Aladdin e. Token PRO proxy generation Found X. 509 certificate on e. Token: label: (e. TCAPI) Robot: Mr. Bayes – Giuseppe La Rocca's GILDA ID id: 3945373335312 d 333545442 d 343031612 d 384637302 d 3238463636393036363042 303 a 31 Your identity: /C=IT/O=GILDA/L=INFN Catania/CN=Robot: Genius – Giuseppe La Rocca Generating a 512 bit RSA private key. . ++++++. . . ++++++ writing new private key to 'proxykey. D 17633' ----- engine "pkcs 11" set. Signature ok subject=/C=IT/O=GILDA/L=INFN Catania/CN=Robot: Mr. Bayes – Giuseppe La Rocca /CN=proxy Getting CA Private Key PKCS#11 token PIN: Your proxy is valid until: Sun Feb 24 03: 58: 09 CEST 2008 -02 -23 Add VOMS extentions running the command : voms-proxy-init --noregen -voms <VO> Tutorial on "GRID Computing“, EMBnet Conference 2008, 17 September 2008
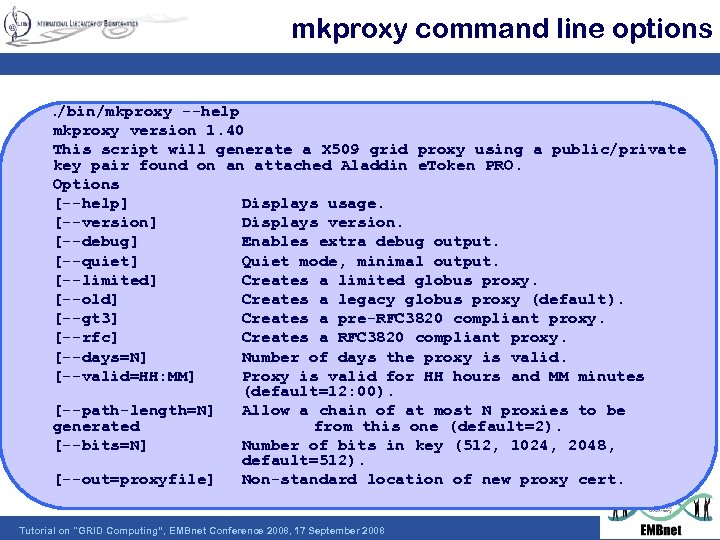
mkproxy command line options. /bin/mkproxy --help mkproxy version 1. 40 This script will generate a X 509 grid proxy using a public/private key pair found on an attached Aladdin e. Token PRO. Options [--help] Displays usage. [--version] Displays version. [--debug] Enables extra debug output. [--quiet] Quiet mode, minimal output. [--limited] Creates a limited globus proxy. [--old] Creates a legacy globus proxy (default). [--gt 3] Creates a pre-RFC 3820 compliant proxy. [--rfc] Creates a RFC 3820 compliant proxy. [--days=N] Number of days the proxy is valid. [--valid=HH: MM] Proxy is valid for HH hours and MM minutes (default=12: 00). [--path-length=N] Allow a chain of at most N proxies to be generated from this one (default=2). [--bits=N] Number of bits in key (512, 1024, 2048, default=512). [--out=proxyfile] Non-standard location of new proxy cert. Tutorial on "GRID Computing“, EMBnet Conference 2008, 17 September 2008
References & Questions • http: //www. nikhef. nl/gridwiki/index. php/Using_an_Aladdin _e. Token_PRO_to_generate_grid_proxies • [Jan Just Keijser] janjust@nikhef. nl • http: //security. fi. infn. it/CA/CPS-2. 3. pdf Tutorial on "GRID Computing“, EMBnet Conference 2008, 17 September 2008
429dc66567db8505b95b8463941d1de0.ppt