d5d671db48b8075a4c2883a5ca4aadb4.ppt
- Количество слайдов: 39
 Tunneling into Tor client proxy and “hidden services” Rick Troth rogue programmer
Tunneling into Tor client proxy and “hidden services” Rick Troth rogue programmer
 Disclaimer The content of this presentation is informational only. The reader or attendee is responsible for his/her own use of the concepts and examples presented herein. In other words: Your mileage may vary. “It Depends. ” Results not typical. Actual mileage will probably be less. Use only as directed. Do not fold, spindle, or mutilate. Not to be taken on an empty stomach. Refrigerate after opening. 2
Disclaimer The content of this presentation is informational only. The reader or attendee is responsible for his/her own use of the concepts and examples presented herein. In other words: Your mileage may vary. “It Depends. ” Results not typical. Actual mileage will probably be less. Use only as directed. Do not fold, spindle, or mutilate. Not to be taken on an empty stomach. Refrigerate after opening. 2
 Tunneling into Tor Agenda (for varying values of “Agenda”) Tor history and tech, what little I know Get the Tor source, build it, now what? Using Tor as a proxy (e. g. , for web browser) Security tips, leakage and profiling Hidden Service example Exit nodes and Relay nodes Using TAILS 3
Tunneling into Tor Agenda (for varying values of “Agenda”) Tor history and tech, what little I know Get the Tor source, build it, now what? Using Tor as a proxy (e. g. , for web browser) Security tips, leakage and profiling Hidden Service example Exit nodes and Relay nodes Using TAILS 3
 about: rick Unix for 30+ years Linux since 0. 99 (circa 1993) VM/SP (and following) since 1981 Obsessed with source-based systems Previous jobs: SSL stack, z/VM, Linux Day job is data sec … it's all about trust 4
about: rick Unix for 30+ years Linux since 0. 99 (circa 1993) VM/SP (and following) since 1981 Obsessed with source-based systems Previous jobs: SSL stack, z/VM, Linux Day job is data sec … it's all about trust 4
 Tunneling into Tor This is a personal odyssey I have … technical interest, and privacy/security interest, and no underworld interest, but I want to arm the good guys (including me) 5
Tunneling into Tor This is a personal odyssey I have … technical interest, and privacy/security interest, and no underworld interest, but I want to arm the good guys (including me) 5
 about: tor The Onion Router http: //www. torproject. org/ ●Originally a US Navy project ●Other sponsors (e. g. : EFF), now 501(c)(3) ● “making the web safe for whistleblowers” 6
about: tor The Onion Router http: //www. torproject. org/ ●Originally a US Navy project ●Other sponsors (e. g. : EFF), now 501(c)(3) ● “making the web safe for whistleblowers” 6
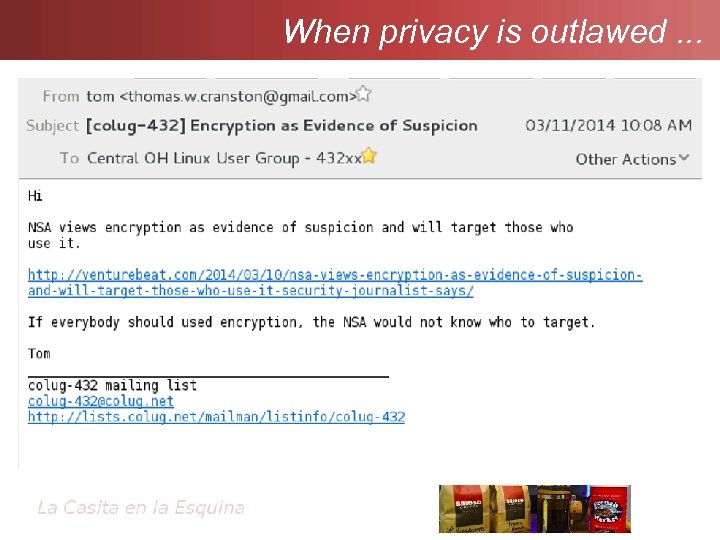 When privacy is outlawed. . .
When privacy is outlawed. . .
 If a human can touch the key. . . 8
If a human can touch the key. . . 8
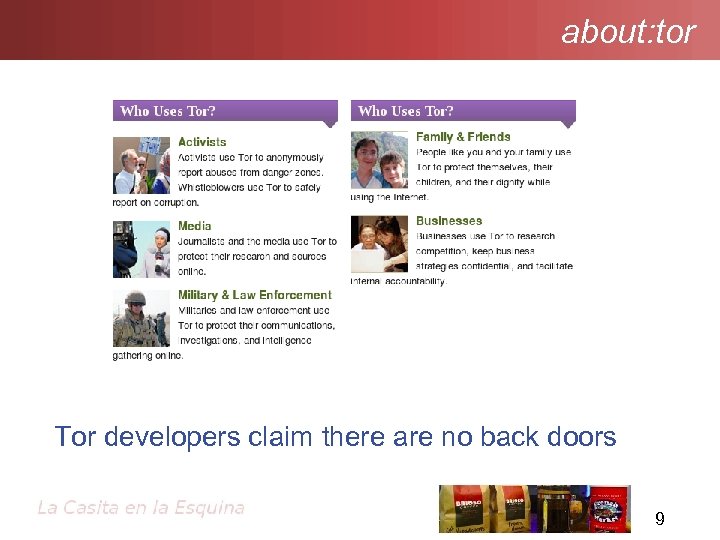 about: tor Tor developers claim there are no back doors 9
about: tor Tor developers claim there are no back doors 9
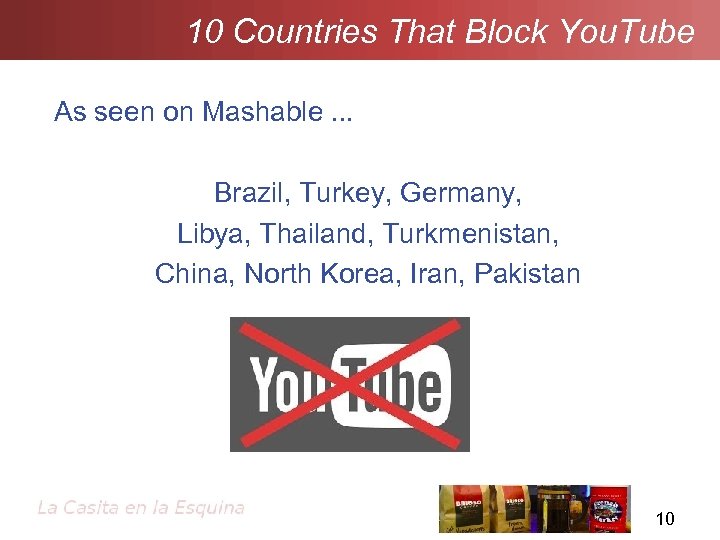 10 Countries That Block You. Tube As seen on Mashable. . . Brazil, Turkey, Germany, Libya, Thailand, Turkmenistan, China, North Korea, Iran, Pakistan 10
10 Countries That Block You. Tube As seen on Mashable. . . Brazil, Turkey, Germany, Libya, Thailand, Turkmenistan, China, North Korea, Iran, Pakistan 10
 Getting Tor – Building Tor https: //www. torproject. org/dist/ tor-0. 3. 0. 8. tar. gz. asc Download the signature too, and check it. 11
Getting Tor – Building Tor https: //www. torproject. org/dist/ tor-0. 3. 0. 8. tar. gz. asc Download the signature too, and check it. 11
 Tor Browser Bundle TBB Easiest/Quickest method https: //www. torproject. org/dist/torbrowser/ 7. 0. 1/torbrowser-install-7. 0. 1_en-US. exe. asc Download the signature too, and check it. 12
Tor Browser Bundle TBB Easiest/Quickest method https: //www. torproject. org/dist/torbrowser/ 7. 0. 1/torbrowser-install-7. 0. 1_en-US. exe. asc Download the signature too, and check it. 12
 Using Tor Just run it Don't run it as root RC file, perhaps /etc/torrc “not present, using reasonable defaults” State directory $HOME/. tor 13
Using Tor Just run it Don't run it as root RC file, perhaps /etc/torrc “not present, using reasonable defaults” State directory $HOME/. tor 13
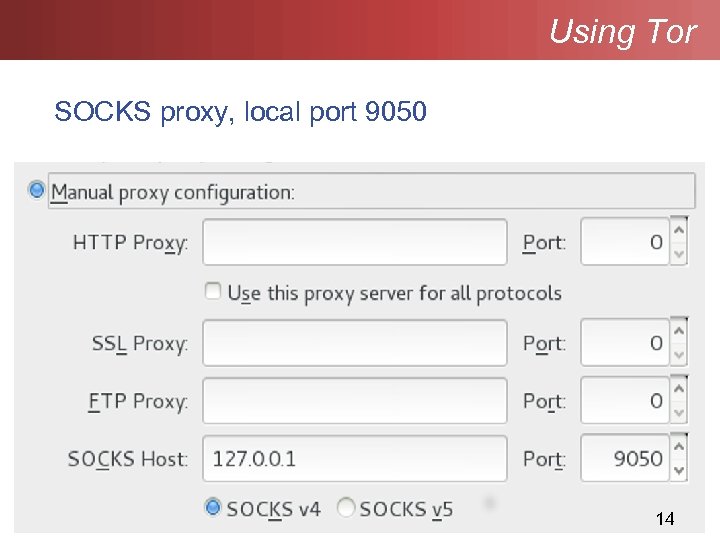 Using Tor SOCKS proxy, local port 9050 14
Using Tor SOCKS proxy, local port 9050 14
 demo 15
demo 15
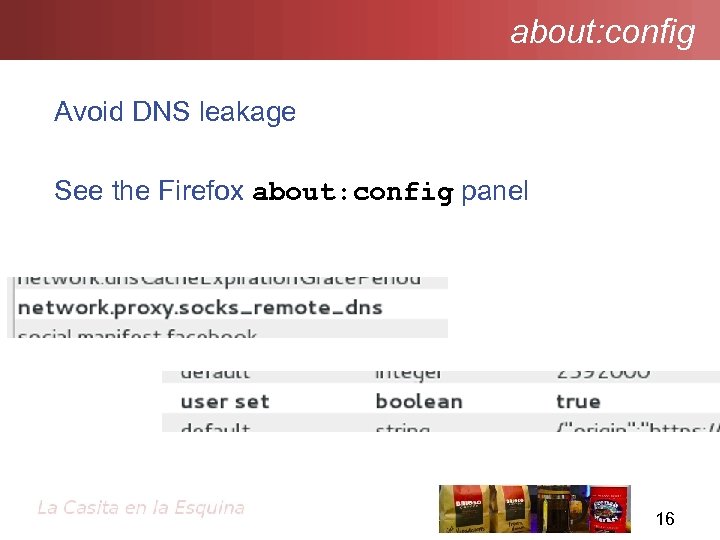 about: config Avoid DNS leakage See the Firefox about: config panel 16
about: config Avoid DNS leakage See the Firefox about: config panel 16
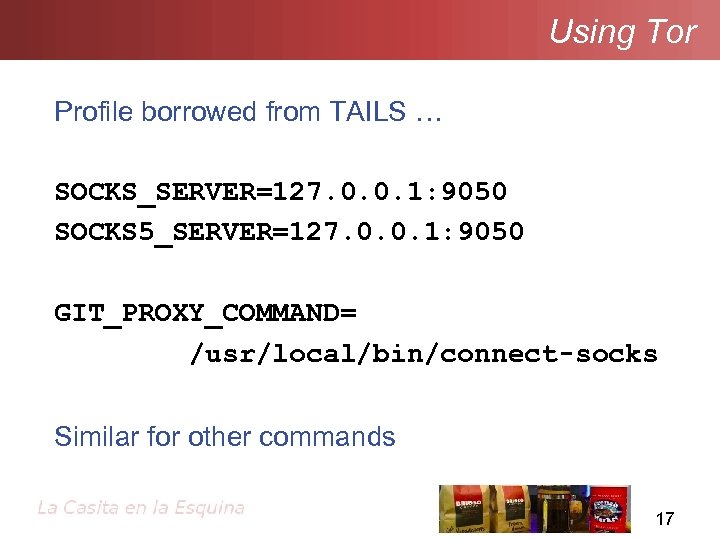 Using Tor Profile borrowed from TAILS … SOCKS_SERVER=127. 0. 0. 1: 9050 SOCKS 5_SERVER=127. 0. 0. 1: 9050 GIT_PROXY_COMMAND= /usr/local/bin/connect-socks Similar for other commands 17
Using Tor Profile borrowed from TAILS … SOCKS_SERVER=127. 0. 0. 1: 9050 SOCKS 5_SERVER=127. 0. 0. 1: 9050 GIT_PROXY_COMMAND= /usr/local/bin/connect-socks Similar for other commands 17
 Multiple Anonymity Methods ●Multiple Configuration Tricks ●Debian based ●Boots and runs from CD or USB/flash ● https: //tails. boum. org/ 18
Multiple Anonymity Methods ●Multiple Configuration Tricks ●Debian based ●Boots and runs from CD or USB/flash ● https: //tails. boum. org/ 18
 Freedombone https: //github. com/bashrc/freedombone 19
Freedombone https: //github. com/bashrc/freedombone 19
 Freedombone ● ● ● ● An email server with GPG encryption Cloud-like sync and share files Social networking: Hubzilla and GNU Social Media services like DLNA to play devices Host your blog and wiki Encrypted IRC, XMPP, Tox and Vo. IP services Github-like project hosting A wireless mesh network 20
Freedombone ● ● ● ● An email server with GPG encryption Cloud-like sync and share files Social networking: Hubzilla and GNU Social Media services like DLNA to play devices Host your blog and wiki Encrypted IRC, XMPP, Tox and Vo. IP services Github-like project hosting A wireless mesh network 20
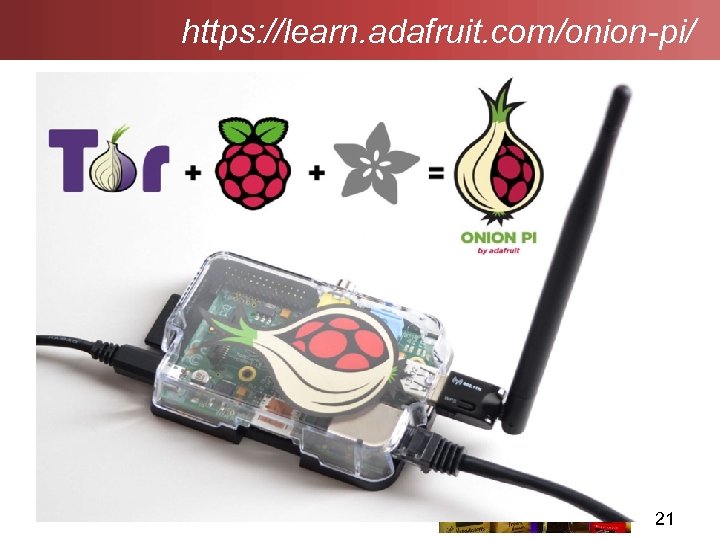 https: //learn. adafruit. com/onion-pi/ 21
https: //learn. adafruit. com/onion-pi/ 21
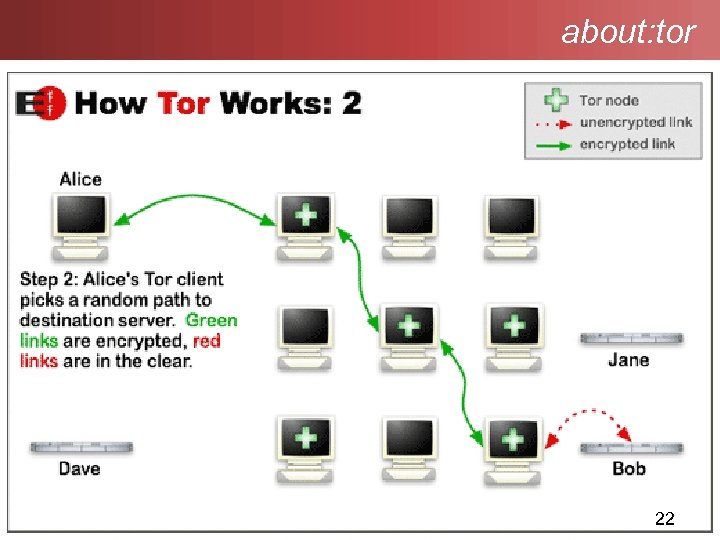 about: tor 22
about: tor 22
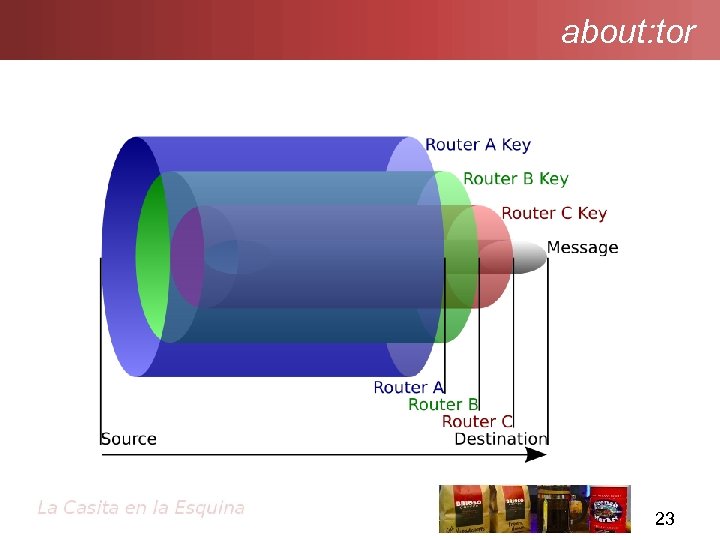 about: tor 23
about: tor 23
 Hidden Services In your “torrc” file. . . Hidden. Service. Dir /var/lib/tor/hidden_service/ Hidden. Service. Port 80 127. 0. 0. 1: 80 Hidden. Service. Port 22 127. 0. 0. 1: 22 Can have multiple HS Services can be remote (from Tor server) Hostnames “xxxxxxxx. onion” 24
Hidden Services In your “torrc” file. . . Hidden. Service. Dir /var/lib/tor/hidden_service/ Hidden. Service. Port 80 127. 0. 0. 1: 80 Hidden. Service. Port 22 127. 0. 0. 1: 22 Can have multiple HS Services can be remote (from Tor server) Hostnames “xxxxxxxx. onion” 24
 Avoid Leaking Metadata Avoid profiling/correlation. . . Hidden. Service. Dir /var/lib/tor/hidden_service/ Hidden. Service. Port 80 127. 0. 0. 1: 8888 Hidden. Service. Port 22 127. 0. 0. 1: 2222 Alternates answer only locally Alternates have different keys, data, “profile” 25
Avoid Leaking Metadata Avoid profiling/correlation. . . Hidden. Service. Dir /var/lib/tor/hidden_service/ Hidden. Service. Port 80 127. 0. 0. 1: 8888 Hidden. Service. Port 22 127. 0. 0. 1: 2222 Alternates answer only locally Alternates have different keys, data, “profile” 25
 Android Access Not always on home LAN Tried IPv 6 via 'aiccu' included with Debian, but no TUN driver included with Android Built Tor anyway … tried hidden service … worked! Tor → poor man's VPN 26
Android Access Not always on home LAN Tried IPv 6 via 'aiccu' included with Debian, but no TUN driver included with Android Built Tor anyway … tried hidden service … worked! Tor → poor man's VPN 26
 Hidden Service: Facebook via Tor … https: //facebookcorewwwi. onion/ http: //www. bbc. com/news/technology-29879851 27
Hidden Service: Facebook via Tor … https: //facebookcorewwwi. onion/ http: //www. bbc. com/news/technology-29879851 27
 Hidden Service: Keybase. io via Tor … http: //fncuwbiisyh 6 ak 3 i. onion/ https: //keybase. io/docs/command_line/tor 28
Hidden Service: Keybase. io via Tor … http: //fncuwbiisyh 6 ak 3 i. onion/ https: //keybase. io/docs/command_line/tor 28
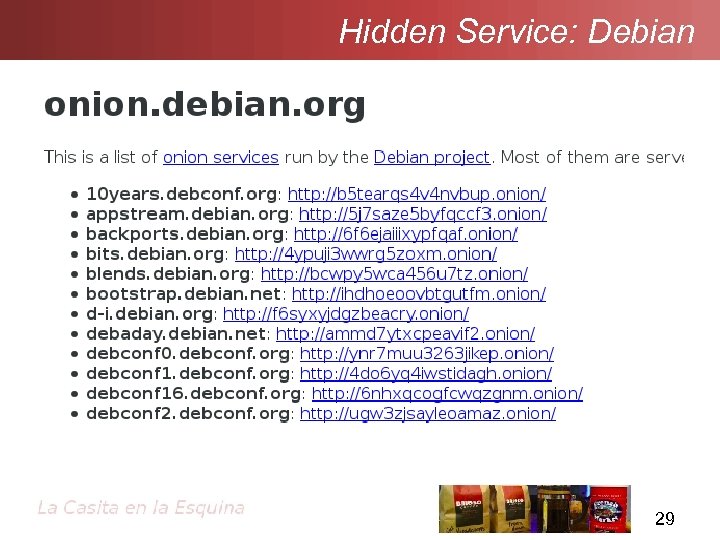 Hidden Service: Debian 29
Hidden Service: Debian 29
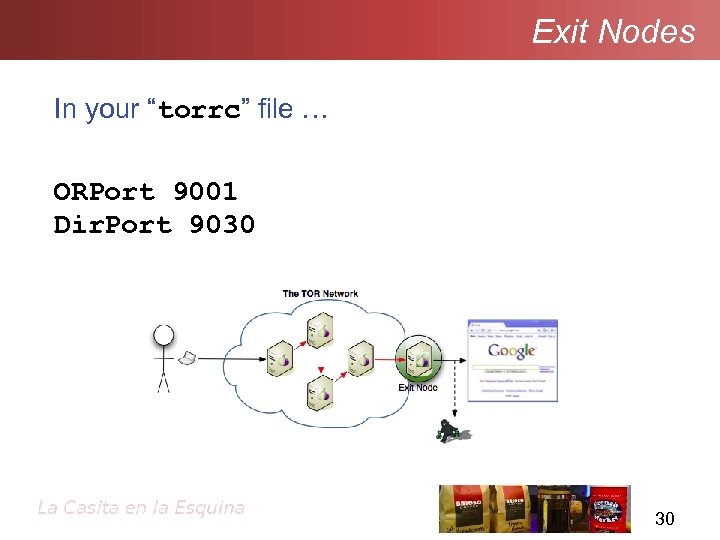 Exit Nodes In your “torrc” file … ORPort 9001 Dir. Port 9030 30
Exit Nodes In your “torrc” file … ORPort 9001 Dir. Port 9030 30
 Relay Nodes Set the policy of your relay Exit Node (default) ●Relay Node (non-exit) ●Bridge Node (unlisted) ● 31
Relay Nodes Set the policy of your relay Exit Node (default) ●Relay Node (non-exit) ●Bridge Node (unlisted) ● 31
 Chicory (Portable Apps) Rick's Rules for /usr/opt wrapper make source make verify make config make install make distclean. /setup 32
Chicory (Portable Apps) Rick's Rules for /usr/opt wrapper make source make verify make config make install make distclean. /setup 32
 Tor Weaknesses ● ● ● DNS leakage Traffic Analysis Correlation Attacks (end point leakage) DOS attacks (voluntary) blockage
Tor Weaknesses ● ● ● DNS leakage Traffic Analysis Correlation Attacks (end point leakage) DOS attacks (voluntary) blockage
 Tor is. . . ● ● ● ● slow IPv 4 only TCP only Easy to use Hard to use right Not the only anonymizer Not the strongest anonymizer Avoid leakage
Tor is. . . ● ● ● ● slow IPv 4 only TCP only Easy to use Hard to use right Not the only anonymizer Not the strongest anonymizer Avoid leakage
 Tor is. . . ● ➢ ● ● ● Attacked by bad guys To stop the good guys Attacked by good guys To stop the bad guys Controversial Not well understood slow
Tor is. . . ● ➢ ● ● ● Attacked by bad guys To stop the good guys Attacked by good guys To stop the bad guys Controversial Not well understood slow
 When Encryption is Outlawed. . . “For us, anonymity will be the first line of defense. ” -- Professor X
When Encryption is Outlawed. . . “For us, anonymity will be the first line of defense. ” -- Professor X
 Miranda Rights You have the right to encrypt your data. If you data is found un-encrypted, anything it says can and will be used against you in a court of law or court of public opinion. You have a right to use of a private network. If you cannot afford a private network, any one of several pro-bono private networks may be appointed for your use.
Miranda Rights You have the right to encrypt your data. If you data is found un-encrypted, anything it says can and will be used against you in a court of law or court of public opinion. You have a right to use of a private network. If you cannot afford a private network, any one of several pro-bono private networks may be appointed for your use.
 NORD Project – please help Not trying to start a distro … http: //2 hiyjpes 6 xu 5 ds 7 l. onion/nord http: //2 hiyjpes 6 xu 5 ds 7 l. onion/chicory … just change the world.
NORD Project – please help Not trying to start a distro … http: //2 hiyjpes 6 xu 5 ds 7 l. onion/nord http: //2 hiyjpes 6 xu 5 ds 7 l. onion/chicory … just change the world.
 Thank You http: //2 hiyjpes 6 xu 5 ds 7 l. onion/vmworkshop/2017/ presentations/troth-vmworkshop-tor-2017. odp http: //2 hiyjpes 6 xu 5 ds 7 l. onion/vmworkshop/2017/ presentations/troth-vmworkshop-tor-2017. ppt
Thank You http: //2 hiyjpes 6 xu 5 ds 7 l. onion/vmworkshop/2017/ presentations/troth-vmworkshop-tor-2017. odp http: //2 hiyjpes 6 xu 5 ds 7 l. onion/vmworkshop/2017/ presentations/troth-vmworkshop-tor-2017. ppt


