0a7fe0caef24e5f45ccf41aabbb4455a.ppt
- Количество слайдов: 57

Trusting Your Data to IBM Verse and IBM Connections Cloud David Kern – Resident Paranoid, STSM, and Global Security Architect for Enterprise Social Solutions, IBM Feb 2 2016

Please Note: • IBM’s statements regarding its plans, directions, and intent are subject to change or withdrawal without notice at IBM’s sole discretion. • Information regarding potential future products is intended to outline our general product direction and it should not be relied on in making a purchasing decision. • The information mentioned regarding potential future products is not a commitment, promise, or legal obligation to deliver any material, code or functionality. Information about potential future products may not be incorporated into any contract. • The development, release, and timing of any future features or functionality described for our products remains at our sole discretion. • Performance is based on measurements and projections using standard IBM benchmarks in a controlled environment. The actual throughput or performance that any user will experience will vary depending upon many factors, including considerations such as the amount of multiprogramming in the user’s job stream, the I/O configuration, the storage configuration, and the workload processed. Therefore, no assurance can be given that an individual user will achieve results similar to those stated here.

Agenda ●Platform and Process ●Transparent Authentication ●Encryption and Email Security ●Notes/Domino (NRPC) traffic ●Closing Thoughts 3

Platform and Process
Data Center Security IBM® has deployed IBM Connections Cloud services in data centers designed to promote high availability and enhanced network protection Redundancy Data centers are deployed in pairs Currently Active/Passive, Active/Active in plan Redundant power & backup generators Redundant network connectivity Monitoring Closed circuit TV 24 x 7 security officers Logging of staff activities Controls Slab-to-slab barriers Biometric cage controls (handprint) Fire prevention systems 5
Network and Infrastructure Defenses Designed to promote high availability for all servers Protection Layered firewall infrastructure Operational remote access via encrypted VPN Detection Active-active configuration of Domino ® replicas of customer mail data Daily restart of Domino servers Automated “auditor” checking for misconfigurations Health checking and “smart server kill” Real time anti-virus at application and server level Audit logs for logging and analysis of security related events Encryption For all HTTP, NRPC, IMAP, FTP, and ST traffic entering and leaving the data center Opportunistic TLS for SMTP traffic entering and leaving IBM Smart. Cloud Notes ® For all Smart. Cloud Notes mail files and attachments at rest For all Connections Files at rest 6

Process for People Security related processes cover all aspects of the IBM Connections Cloud life cycle Separation of duty matrix covers all Connections Cloud and IBM personnel Segregation of activities and personnel with change access to the Connections Cloud code base and change access to the operational configuration and data Processes and tools to ensure that support and debugging information shared across that boundary does not carry private and sensitive information Crash data is sanitized Daily system health and performance reports carry only information approved for developers Smart. Cloud Notes Code Controls Code updates are associated with an escalated problem report or an approved work item Code updates peer reviewed and approved by a development architect Full system build handed off to operations after internal system verification testing System verification testing performed on staging environment Regular manual and automated Ethical Hacking penetration testing Automated testing leverages the power of IBM Rational® App. Scan® 7
Compliance With Established Programs IBM compliance programs mandate periodic self-assessments and production scanning and reporting of compliance posture Business process-based reviews are conducted through the project cycles Privacy reviews align IBM Connections Cloud with IBM's comprehensive policies on privacy and client data protection Effectiveness of data center and operational controls tested via a SAS 70 Type II / SSAE 16 review Safe Harbor certified: http: //safeharbor. export. gov/companyinfo. aspx? id=16286 8

Transparent Authentication
Transparent Authentication Users have too many passwords Password prompts are annoying Many “different” passwords leads to lower security Users shouldn't know or care who provides their services or from where Password management is annoying – by using cryptographic mechanisms instead of passwords, we can help keep the problem from getting worse, and maybe even help improve the situation. IBM Connections Cloud uses Security Assertion Markup Language (SAML) Public standard from OASIS Based on the strength of PKI – SAML uses signed XML identity assertions Many implementations available from IBM and third party providers Including open source implementations Many organizations currently use SAML for web SSO Did I mention that SAML is a public standard yet? 10

Federated Identity Use your existing web passwords for IBM Connections Cloud web resources Keep your passwords behind your corporate firewall Manage your own password requirements Manage your own change intervals Manage your own re-use requirements Never send a password over the 'net to SCSB! Because SAML is a public standard, you can use any SAML 1. 1 or SAML 2. 0 compliant identity provider Also prevents crackers from guessing your passwords against SCSB Microsoft's ADFS 2. 0 for Active Directory integration IBM's own Tivoli Federated Identity Manager (TFIM) Open. SAML Id. P initiated SAML flows support a “web portal” user experience 11
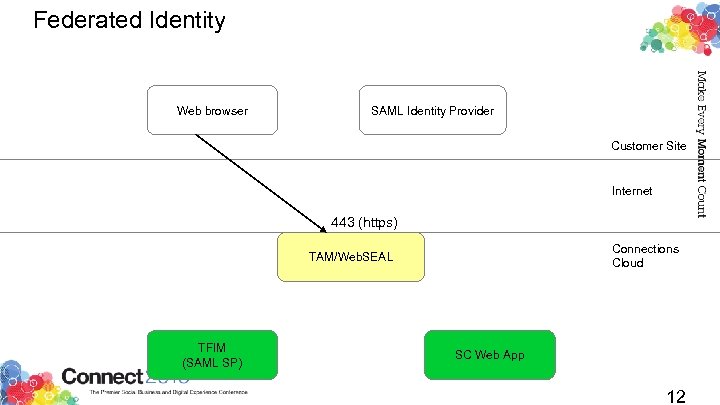
Federated Identity Web browser SAML Identity Provider Customer Site Internet 443 (https) Connections Cloud TAM/Web. SEAL TFIM (SAML SP) SC Web App 12
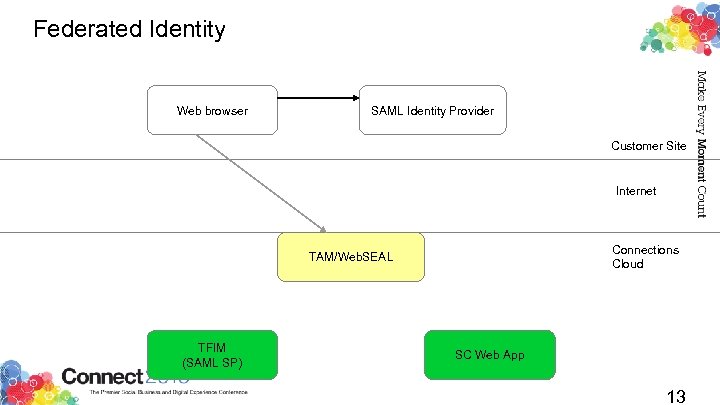
Federated Identity Web browser SAML Identity Provider Customer Site Internet Connections Cloud TAM/Web. SEAL TFIM (SAML SP) SC Web App 13
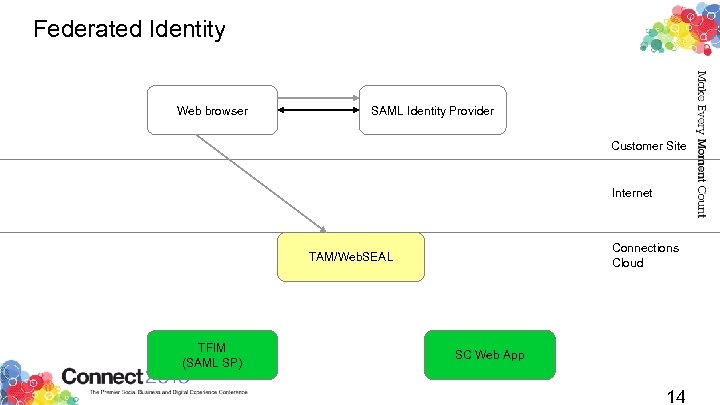
Federated Identity Web browser SAML Identity Provider Customer Site Internet Connections Cloud TAM/Web. SEAL TFIM (SAML SP) SC Web App 14
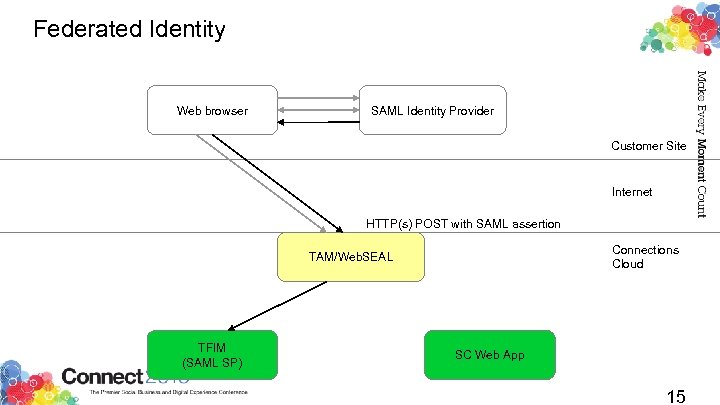
Federated Identity Web browser SAML Identity Provider Customer Site Internet HTTP(s) POST with SAML assertion Connections Cloud TAM/Web. SEAL TFIM (SAML SP) SC Web App 15
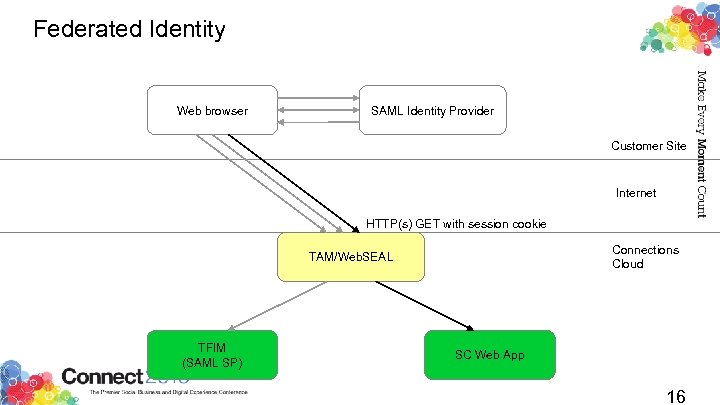
Federated Identity Web browser SAML Identity Provider Customer Site Internet HTTP(s) GET with session cookie Connections Cloud TAM/Web. SEAL TFIM (SAML SP) SC Web App 16
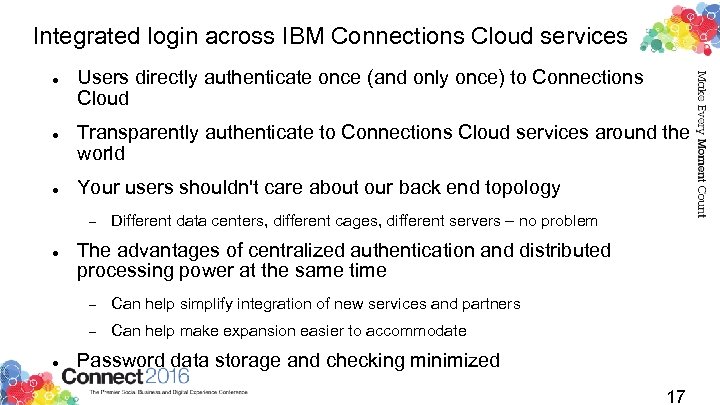
Integrated login across IBM Connections Cloud services Users directly authenticate once (and only once) to Connections Cloud Transparently authenticate to Connections Cloud services around the world Your users shouldn't care about our back end topology Different data centers, different cages, different servers – no problem The advantages of centralized authentication and distributed processing power at the same time Can help simplify integration of new services and partners Can help make expansion easier to accommodate Password data storage and checking minimized 17
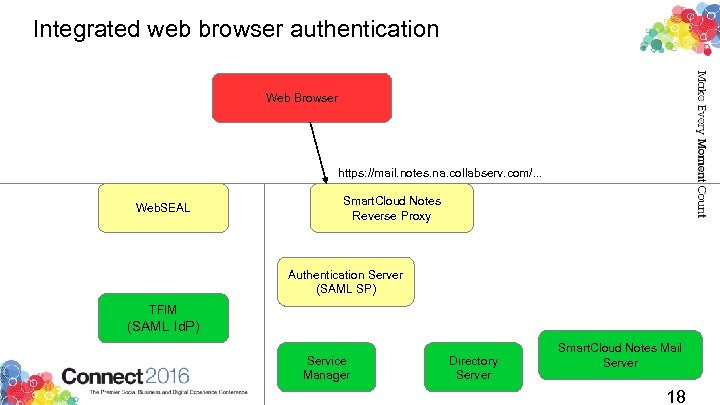
Integrated web browser authentication Web Browser https: //mail. notes. na. collabserv. com/. . . Web. SEAL Smart. Cloud Notes Reverse Proxy Authentication Server (SAML SP) TFIM (SAML Id. P) Service Manager Directory Server Smart. Cloud Notes Mail Server 18
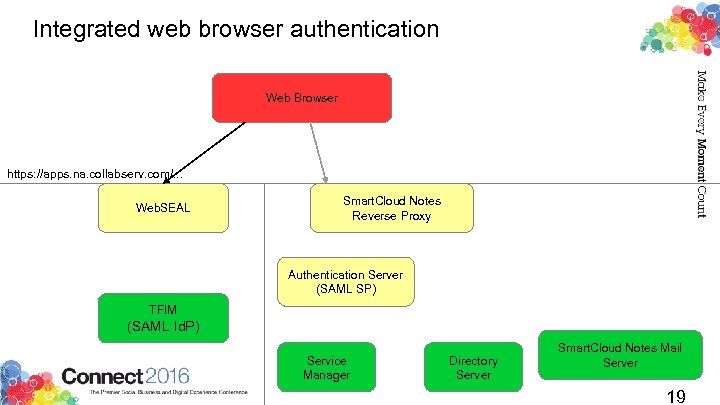
Integrated web browser authentication Web Browser https: //apps. na. collabserv. com/. . . Web. SEAL Smart. Cloud Notes Reverse Proxy Authentication Server (SAML SP) TFIM (SAML Id. P) Service Manager Directory Server Smart. Cloud Notes Mail Server 19
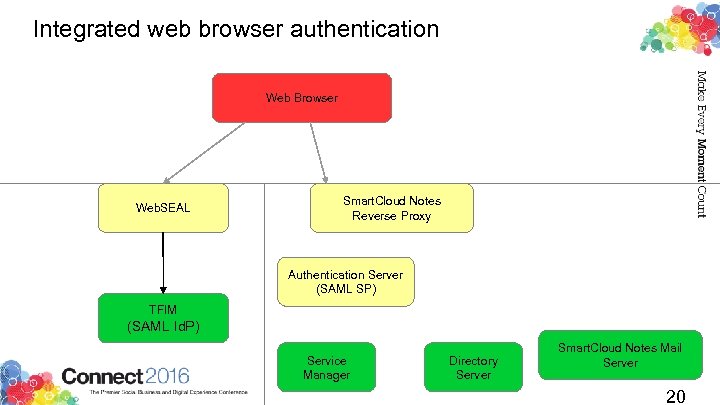
Integrated web browser authentication Web Browser Web. SEAL Smart. Cloud Notes Reverse Proxy Authentication Server (SAML SP) TFIM (SAML Id. P) Service Manager Directory Server Smart. Cloud Notes Mail Server 20
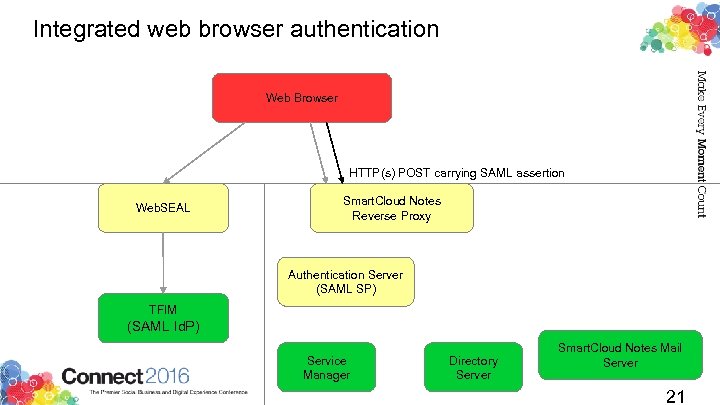
Integrated web browser authentication Web Browser HTTP(s) POST carrying SAML assertion Web. SEAL Smart. Cloud Notes Reverse Proxy Authentication Server (SAML SP) TFIM (SAML Id. P) Service Manager Directory Server Smart. Cloud Notes Mail Server 21
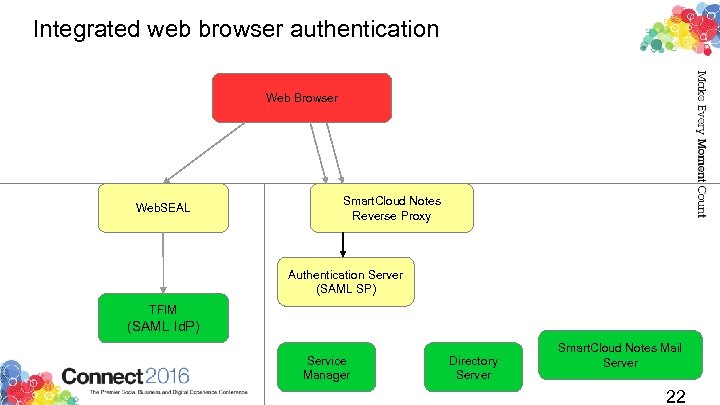
Integrated web browser authentication Web Browser Web. SEAL Smart. Cloud Notes Reverse Proxy Authentication Server (SAML SP) TFIM (SAML Id. P) Service Manager Directory Server Smart. Cloud Notes Mail Server 22
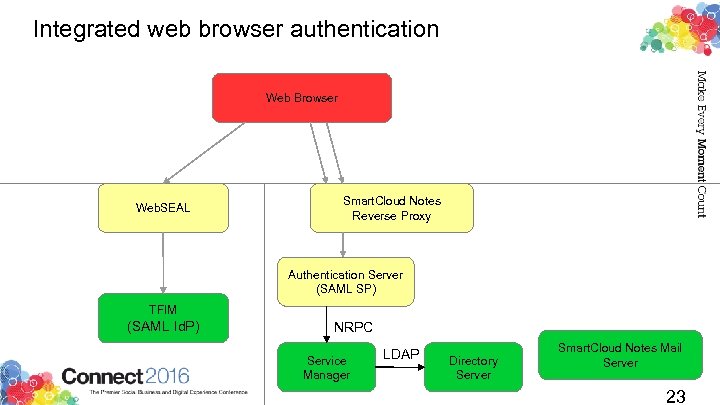
Integrated web browser authentication Web Browser Web. SEAL Smart. Cloud Notes Reverse Proxy Authentication Server (SAML SP) TFIM (SAML Id. P) NRPC Service Manager LDAP Directory Server Smart. Cloud Notes Mail Server 23
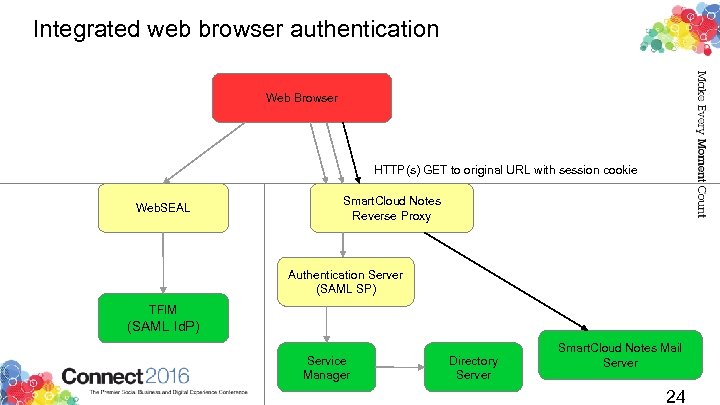
Integrated web browser authentication Web Browser HTTP(s) GET to original URL with session cookie Web. SEAL Smart. Cloud Notes Reverse Proxy Authentication Server (SAML SP) TFIM (SAML Id. P) Service Manager Directory Server Smart. Cloud Notes Mail Server 24

Transparent Authentication: Notes client Users already unlock their Notes clients – shouldn't that be enough? Leverage your existing Notes PKI to authenticate to Connections Cloud web resources Only available to users provisioned for Smart. Cloud Notes Requires 8. 5. 2+ Notes standard client Also works great with Notes Shared Login (NSLv 3) 25
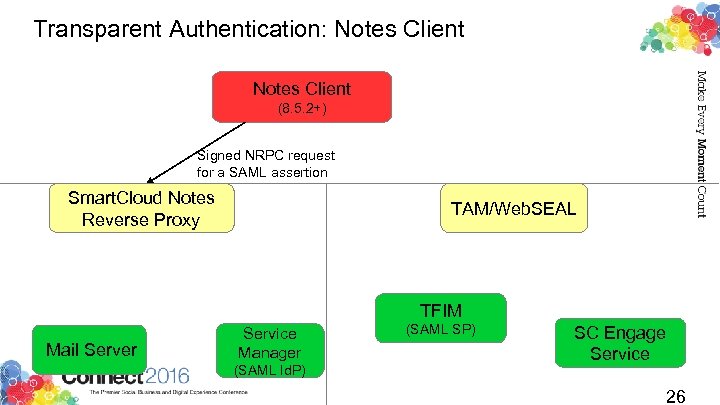
Transparent Authentication: Notes Client (8. 5. 2+) Signed NRPC request for a SAML assertion Smart. Cloud Notes Reverse Proxy TAM/Web. SEAL TFIM Mail Server Service Manager (SAML Id. P) (SAML SP) SC Engage Service 26
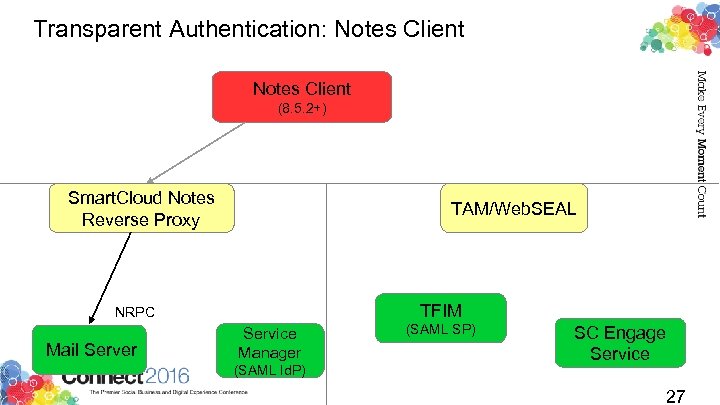
Transparent Authentication: Notes Client (8. 5. 2+) Smart. Cloud Notes Reverse Proxy TAM/Web. SEAL TFIM NRPC Mail Server Service Manager (SAML Id. P) (SAML SP) SC Engage Service 27
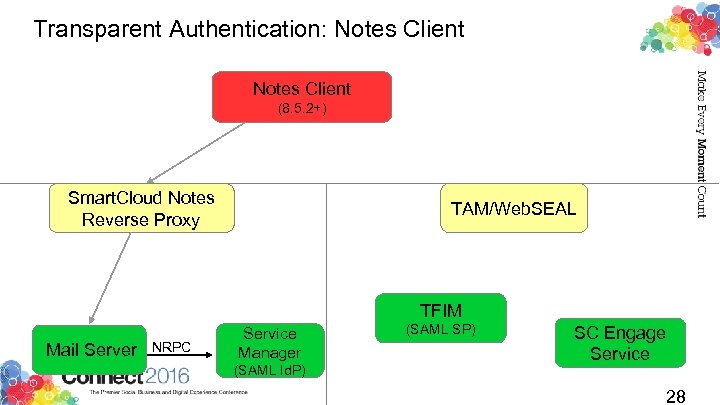
Transparent Authentication: Notes Client (8. 5. 2+) Smart. Cloud Notes Reverse Proxy TAM/Web. SEAL TFIM Mail Server NRPC Service Manager (SAML Id. P) (SAML SP) SC Engage Service 28
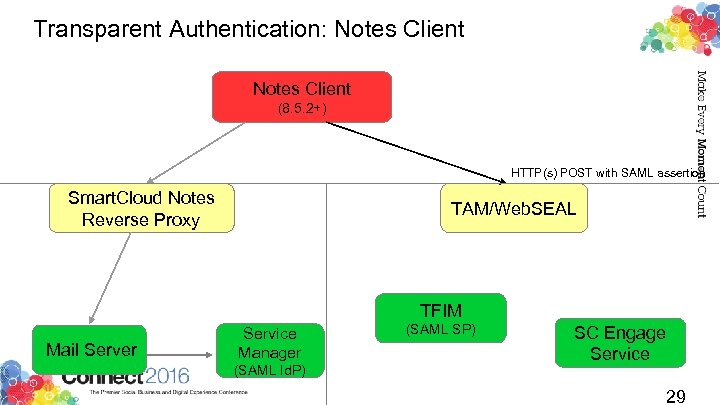
Transparent Authentication: Notes Client (8. 5. 2+) HTTP(s) POST with SAML assertion Smart. Cloud Notes Reverse Proxy TAM/Web. SEAL TFIM Mail Server Service Manager (SAML Id. P) (SAML SP) SC Engage Service 29
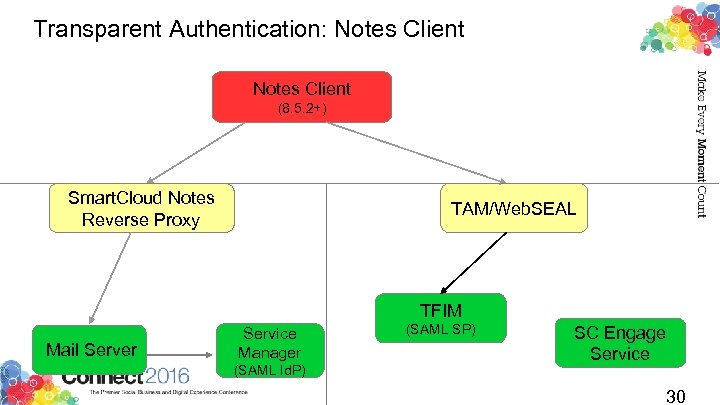
Transparent Authentication: Notes Client (8. 5. 2+) Smart. Cloud Notes Reverse Proxy TAM/Web. SEAL TFIM Mail Server Service Manager (SAML Id. P) (SAML SP) SC Engage Service 30
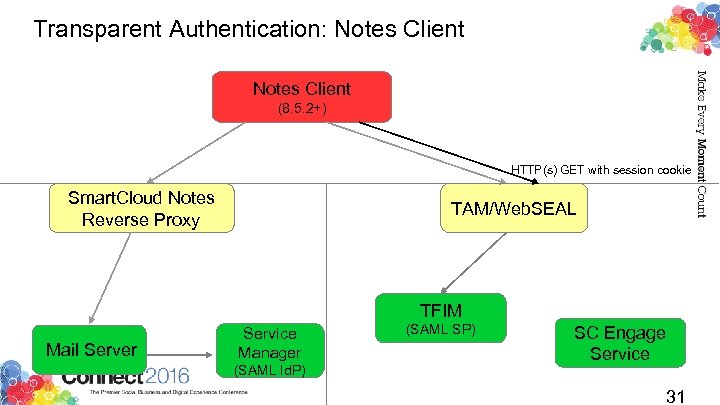
Transparent Authentication: Notes Client (8. 5. 2+) HTTP(s) GET with session cookie Smart. Cloud Notes Reverse Proxy TAM/Web. SEAL TFIM Mail Server Service Manager (SAML Id. P) (SAML SP) SC Engage Service 31
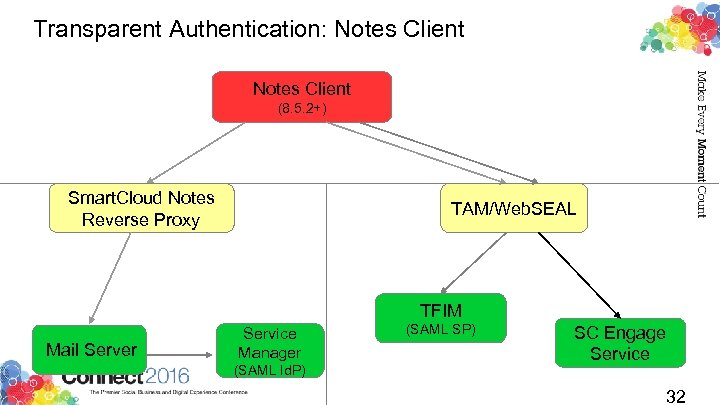
Transparent Authentication: Notes Client (8. 5. 2+) Smart. Cloud Notes Reverse Proxy TAM/Web. SEAL TFIM Mail Server Service Manager (SAML Id. P) (SAML SP) SC Engage Service 32
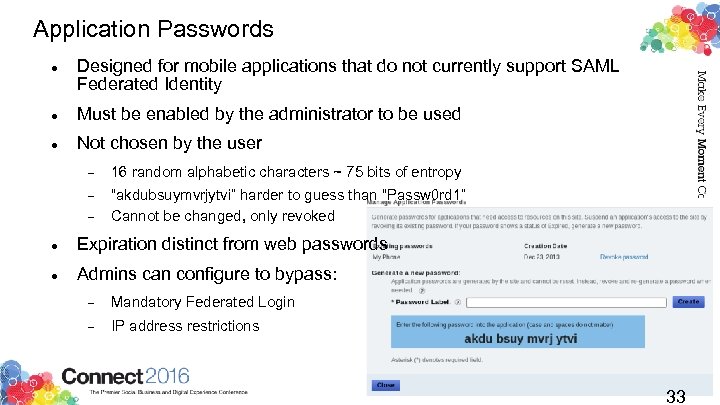
Application Passwords Designed for mobile applications that do not currently support SAML Federated Identity Must be enabled by the administrator to be used Not chosen by the user 16 random alphabetic characters ~ 75 bits of entropy “akdubsuymvrjytvi” harder to guess than “Passw 0 rd 1” Cannot be changed, only revoked Expiration distinct from web passwords Admins can configure to bypass: Mandatory Federated Login IP address restrictions 33

Encryption and Email Security
Encryption of data in transit NRPC port encryption enforced on all Notes/Domino traffic Uses 128 bit data encryption keys SSL/TLS enforced on all web and IMAP All ciphers below 128 bits disabled Extended Validation (EV) certificates used for web browser traffic Opportunistic TLS used for inbound and outbound SMTP Of course, the remote server must support opportunistic TLS as well Uses the STARTTLS SMTP command 35

Encryption of data at rest All mail files in Smart. Cloud Notes are protected by Local Database Encryption Local database encryption uses 128 bit symmetric keys We've enhanced local database encryption for Smart. Cloud Notes: Designed to promote much faster creation of new replicas Uses shared 128 bit AES key (NEK) instead of the server's private RSA key AES secret key decryption is much faster than RSA private key decryption Connections Files encrypts all uploaded files at rest Optional “encrypt this file” adds a second layer of encryption 36
Secure email Yes, Notes and S/MIME signing and encryption still work with Smart. Cloud Notes AES encryption supported for both formats Provide end-to-end encryption of email messages “Encrypt Incoming Messages” supported for hybrid customers 37
Some Random Security Trivia Smart. Cloud Notes does not utilize the “Dual EC DRBG” pseudo-random number generator Nor does the on-premises Notes/Domino product family Replication of mail files between the primary and DR data centers is encrypted with NRPC port encryption Replication of BSS and Collaboration data between the primary and DR data centers is encrypted with SSL/TLS or an encrypted VPN IBM Connections Cloud has enforced SSL/TLS for all web traffic since day one including: TLSv 1. 2 support Extended Validation certs using 2048 bit RSA and SHA-256 DHE-RSA and ECDHE-RSA ciphers forward secrecy Was never vulnerable to the Open. SSL “Heartbleed” (CVE-2014 -0160) bug 38

Notes ID vault Smart. Cloud Notes creates a Notes ID vault for each customer Used for ID file backup and password reset capabilities Provides rename, key rollover, and Notes ID password expiration functionality Smart. Cloud Notes Web: On-premises “DWA” and Traveler users have always been prompted for their Notes ID file passwords to perform secure mail operations. We've integrated the vault with our mail servers to eliminate those prompts in SCNotes (You can use SAML to eliminate those prompts for on-premises “DWA” with Domino 9. 0. x) 39

Mail you don't want, and Mail you do! Lotus Protector for Anti-Virus and Anti-Spam SCNotes external SMTP traffic routed through Lotus Protector in the yellow zone Content analysis includes URL checker against URL database 9. 3 billion evaluated web pages and images 100 million URL filter entries Spam/Phishing database 80 million spam signatures 2 million new sigantures per day > 99% effective against spam < 0. 001% false-positives https: //www. icsalabs. com/technology-program/anti-spam/spam-data-center Independently evaluates anti-spam technologies against real-world data Archive Essentials provides email retention for legal discovery purposes Transparent authentication via SAML 40
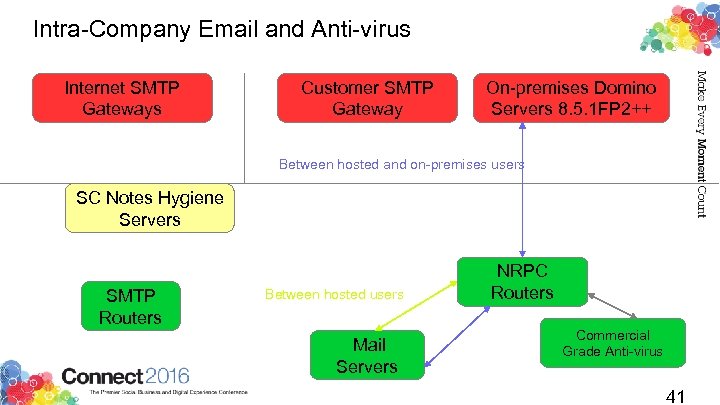
Intra-Company Email and Anti-virus Internet SMTP Gateways Customer SMTP Gateway On-premises Domino Servers 8. 5. 1 FP 2++ Between hosted and on-premises users SC Notes Hygiene Servers SMTP Routers Between hosted users Mail Servers NRPC Routers Commercial Grade Anti-virus 41
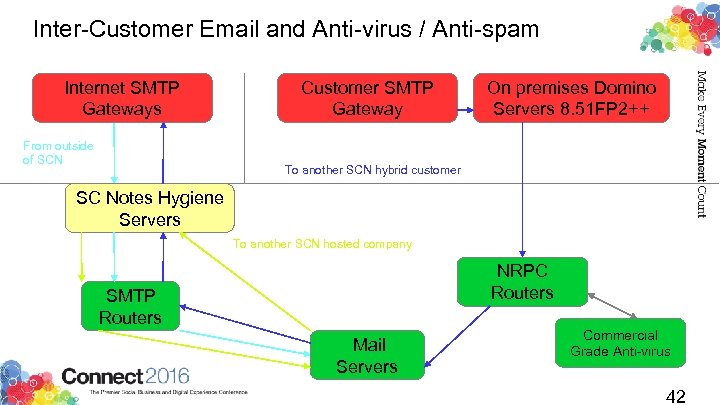
Inter-Customer Email and Anti-virus / Anti-spam Internet SMTP Gateways From outside of SCN Customer SMTP Gateway On premises Domino Servers 8. 51 FP 2++ To another SCN hybrid customer SC Notes Hygiene Servers To another SCN hosted company NRPC Routers SMTP Routers Mail Servers Commercial Grade Anti-virus 42
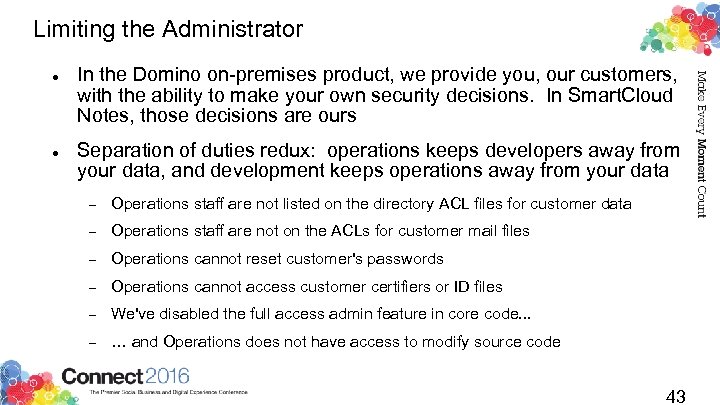
Limiting the Administrator In the Domino on-premises product, we provide you, our customers, with the ability to make your own security decisions. In Smart. Cloud Notes, those decisions are ours Separation of duties redux: operations keeps developers away from your data, and development keeps operations away from your data Operations staff are not listed on the directory ACL files for customer data Operations staff are not on the ACLs for customer mail files Operations cannot reset customer's passwords Operations cannot access customer certifiers or ID files We've disabled the full access admin feature in core code. . . … and Operations does not have access to modify source code 43

Notes/Domino (NRPC) Traffic
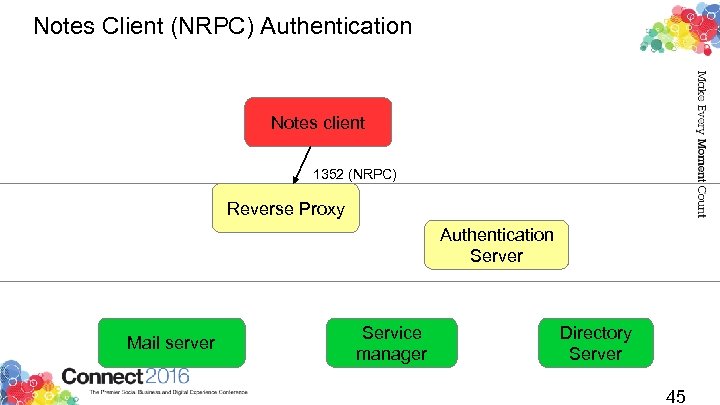
Notes Client (NRPC) Authentication Notes client 1352 (NRPC) Reverse Proxy Authentication Server Mail server Service manager Directory Server 45
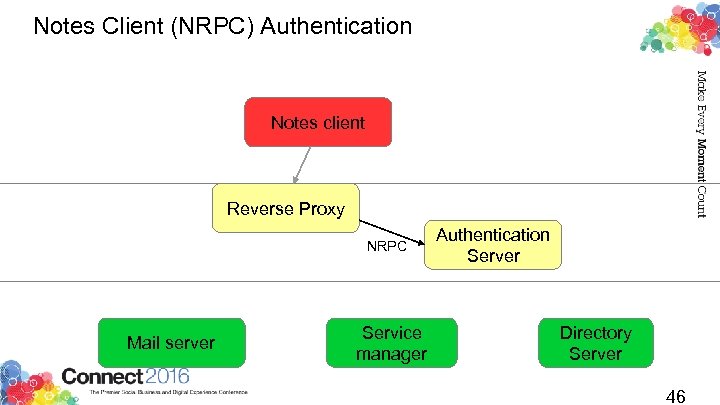
Notes Client (NRPC) Authentication Notes client Reverse Proxy NRPC Mail server Service manager Authentication Server Directory Server 46
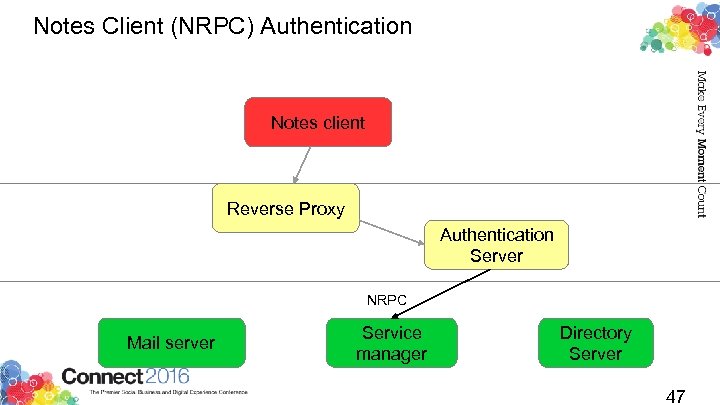
Notes Client (NRPC) Authentication Notes client Reverse Proxy Authentication Server NRPC Mail server Service manager Directory Server 47
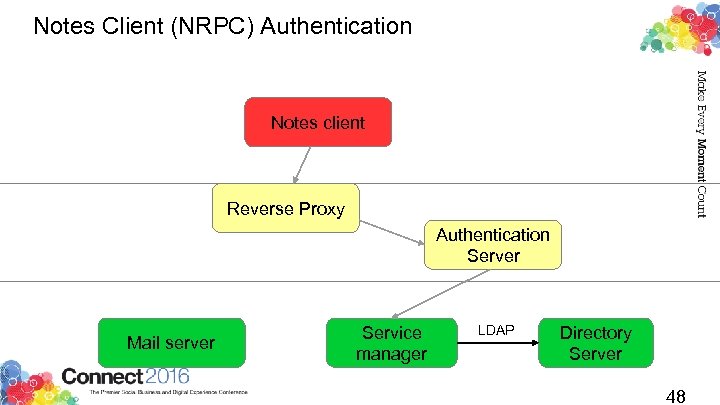
Notes Client (NRPC) Authentication Notes client Reverse Proxy Authentication Server Mail server Service manager LDAP Directory Server 48
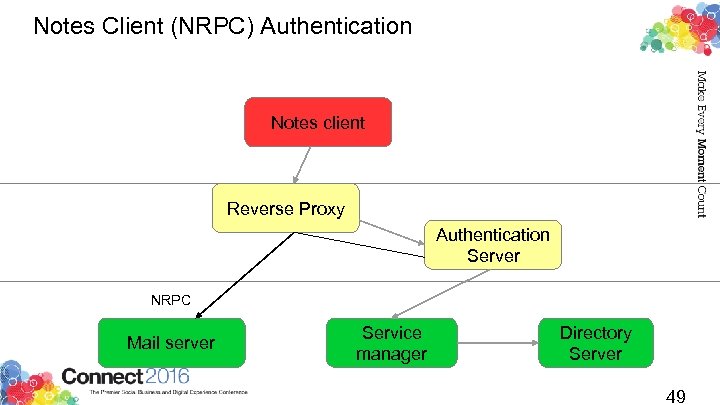
Notes Client (NRPC) Authentication Notes client Reverse Proxy Authentication Server NRPC Mail server Service manager Directory Server 49
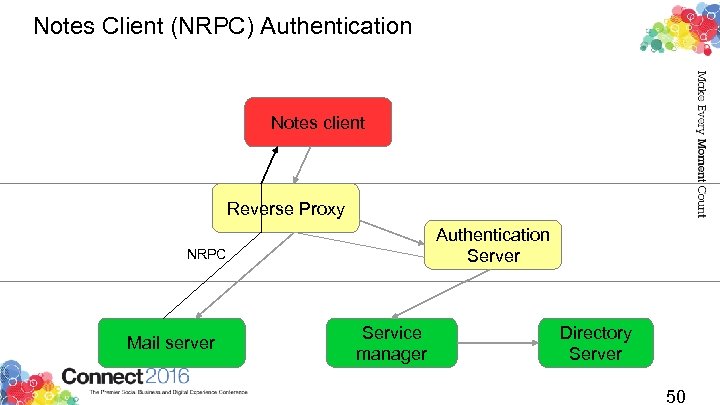
Notes Client (NRPC) Authentication Notes client Reverse Proxy Authentication Server NRPC Mail server Service manager Directory Server 50
Virtual Servers Leverage your existing PKI for authentication Familiar org (/Iris, /Renovations, etc. ) for user peace of mind No cross certificates to manage Create and upload a new OU cert off your root certifier to SCN during account setup We'll use that OU to create our virtual servers Users can use existing ID files to contact DBs on-premises and in the cloud transparently Core principle of the Smart. Cloud Notes multi-tenant environment Our servers assume a virtual identity for your organization when communicating with your users A small number of authentication servers are authenticating all customers Each mail server is hosting mail files for multiple customers Requires at least Domino 8. 5. 1 FP 2 / Notes 8. 5. 1 FP 5 … although I would have to highly recommend 9. 0. x over 8. 5. x 51

Closing Thoughts

Closing Thoughts Security Rich by Design Standards Matter Your Data Belongs to You Enterprise-grade Controls 53
Your Feedback Is Important! Based upon your session attendance, a customized list of surveys will be built for you. Please complete your surveys via the conference kiosks or any web enabled device at https: //www. connectsurveys. com or through IBM Event Connect.

Notices and Disclaimers Copyright © 2015 by International Business Machines Corporation (IBM). No part of this document may be reproduced or transmitted in any form without written permission from IBM. U. S. Government Users Restricted Rights - Use, duplication or disclosure restricted by GSA ADP Schedule Contract with IBM. Information in these presentations (including information relating to products that have not yet been announced by IBM) has been reviewed for accuracy as of the date of initial publication and could include unintentional technical or typographical errors. IBM shall have no responsibility to update this information. THIS DOCUMENT IS DISTRIBUTED "AS IS" WITHOUT ANY WARRANTY, EITHER EXPRESS OR IMPLIED. IN NO EVENT SHALL IBM BE LIABLE FOR ANY DAMAGE ARISING FROM THE USE OF THIS INFORMATION, INCLUDING BUT NOT LIMITED TO, LOSS OF DATA, BUSINESS INTERRUPTION, LOSS OF PROFIT OR LOSS OF OPPORTUNITY. IBM products and services are warranted according to the terms and conditions of the agreements under which they are provided. Any statements regarding IBM's future direction, intent or product plans are subject to change or withdrawal without notice. Performance data contained herein was generally obtained in a controlled, isolated environments. Customer examples are presented as illustrations of how those customers have used IBM products and the results they may have achieved. Actual performance, cost, savings or other results in other operating environments may vary. References in this document to IBM products, programs, or services does not imply that IBM intends to make such products, programs or services available in all countries in which IBM operates or does business. Workshops, sessions and associated materials may have been prepared by independent session speakers, and do not necessarily reflect the views of IBM. All materials and discussions are provided for informational purposes only, and are neither intended to, nor shall constitute legal or other guidance or advice to any individual participant or their specific situation. It is the customer’s responsibility to insure its own compliance with legal requirements and to obtain advice of competent legal counsel as to the identification and interpretation of any relevant laws and regulatory requirements that may affect the customer’s business and any actions the customer may need to take to comply with such laws. IBM does not provide legal advice or represent or warrant that its services or products will ensure that the customer is in compliance with any law

Notices and Disclaimers cont. Information concerning non-IBM products was obtained from the suppliers of those products, their published announcements or other publicly available sources. IBM has not tested those products in connection with this publication and cannot confirm the accuracy of performance, compatibility or any other claims related to non-IBM products. Questions on the capabilities of non-IBM products should be addressed to the suppliers of those products. IBM does not warrant the quality of any third-party products, or the ability of any such third-party products to interoperate with IBM’s products. IBM EXPRESSLY DISCLAIMS ALL WARRANTIES, EXPRESSED OR IMPLIED, INCLUDING BUT NOT LIMITED TO, THE IMPLIED WARRANTIES OF MERCHANTABILITY AND FITNESS FOR A PARTICULAR PURPOSE. The provision of the information contained herein is not intended to, and does not, grant any right or license under any IBM patents, copyrights, trademarks or other intellectual property right. • IBM, the IBM logo, ibm. com, Aspera®, Bluemix, Blueworks Live, CICS, Clearcase, Cognos®, DOORS®, Emptoris®, Enterprise Document Management System™, FASP®, File. Net®, Global Business Services ®, Global Technology Services ®, IBM Experience. One™, IBM Smart. Cloud®, IBM Social Business®, Information on Demand, ILOG, Maximo®, MQIntegrator®, MQSeries®, Netcool®, OMEGAMON, Open. Power, Pure. Analytics™, Pure. Application®, pure. Cluster™, Pure. Coverage®, Pure. Data®, Pure. Experience®, Pure. Flex®, pure. Query®, pure. Scale®, Pure. Systems®, QRadar®, Rational®, Rhapsody®, Smarter Commerce®, So. DA, SPSS, Sterling Commerce®, Stored. IQ, Tealeaf®, Tivoli®, Trusteer®, Unica®, urban{code}®, Watson, Web. Sphere®, Worklight®, X-Force® and System z® Z/OS, are trademarks of International Business Machines Corporation, registered in many jurisdictions worldwide. Other product and service names might be trademarks of IBM or other companies. A current list of IBM trademarks is available on the Web at "Copyright and trademark information" at: www. ibm. com/legal/copytrade. shtml.

Thank you
0a7fe0caef24e5f45ccf41aabbb4455a.ppt