017759453ae042c0baf2f50cbb1dc50c.ppt
- Количество слайдов: 23
 Trusted Hardware for Partitioned Multicore Alexandra Constantin James Cook Anindya De Computer Science, UC Berkeley
Trusted Hardware for Partitioned Multicore Alexandra Constantin James Cook Anindya De Computer Science, UC Berkeley
 What is a TPM? TPM – Trusted Platform Module Specs by Trusted Computing Group (TCG) Stores secret keys to be used for cryptographic protocols and authentication
What is a TPM? TPM – Trusted Platform Module Specs by Trusted Computing Group (TCG) Stores secret keys to be used for cryptographic protocols and authentication
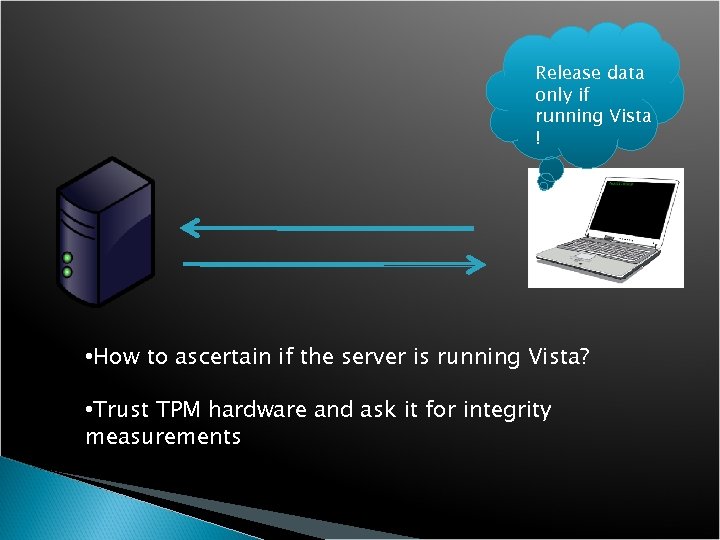 Release data only if running Vista ! • How to ascertain if the server is running Vista? • Trust TPM hardware and ask it for integrity measurements
Release data only if running Vista ! • How to ascertain if the server is running Vista? • Trust TPM hardware and ask it for integrity measurements
 Attestation TPM hardware is trusted AIK key pair AIK credential signed by trusted third party (privacy CA)
Attestation TPM hardware is trusted AIK key pair AIK credential signed by trusted third party (privacy CA)
 Boot Process BIOS boot block = Core Root of Trust Chain of trust ◦ Boot block ◦ rest of the bios ◦ OS, etc. Integrity measurements = hash of code to be loaded Signed hash of code used to establish trust
Boot Process BIOS boot block = Core Root of Trust Chain of trust ◦ Boot block ◦ rest of the bios ◦ OS, etc. Integrity measurements = hash of code to be loaded Signed hash of code used to establish trust
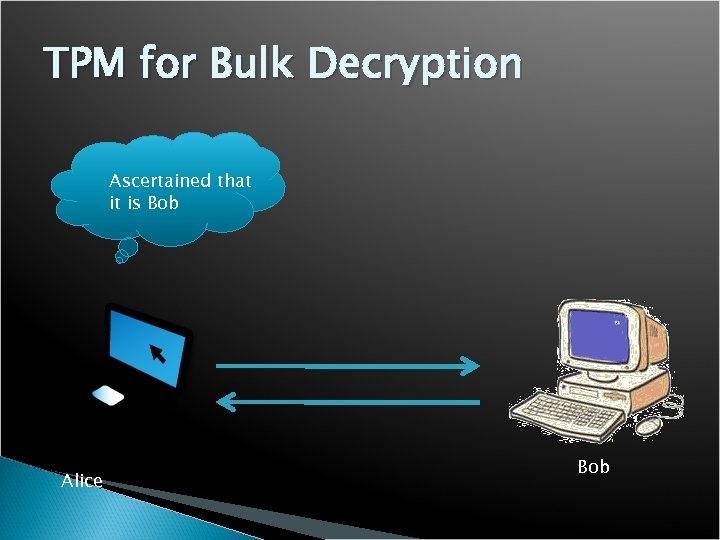 TPM for Bulk Decryption Ascertained that it is Bob Alice Bob
TPM for Bulk Decryption Ascertained that it is Bob Alice Bob
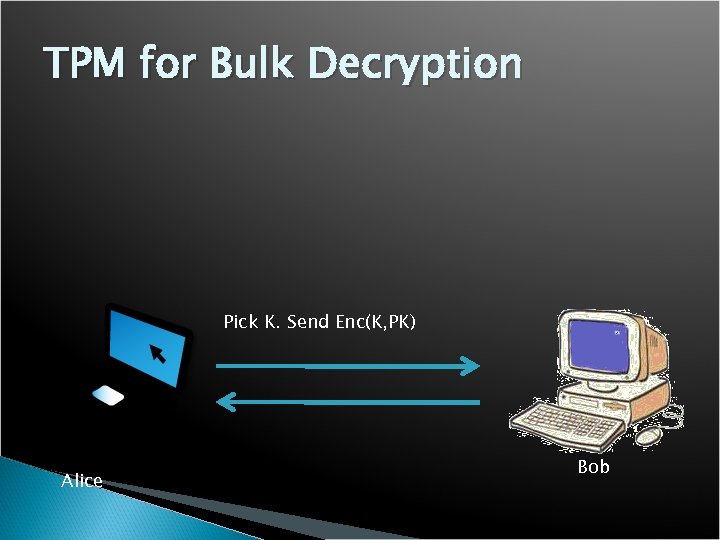 TPM for Bulk Decryption Pick K. Send Enc(K, PK) Alice Bob
TPM for Bulk Decryption Pick K. Send Enc(K, PK) Alice Bob
 TPM for Bulk Decryption Send Enc(K, Data) Alice Bob
TPM for Bulk Decryption Send Enc(K, Data) Alice Bob
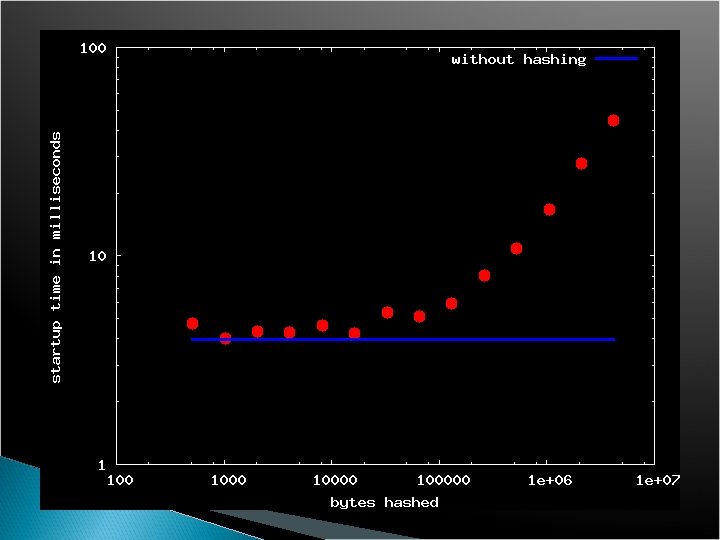
 Trade-offs in implementation u TPM hardware requirements to maintain efficiency for a system with many partitions? u When to hash? u Some simulation results
Trade-offs in implementation u TPM hardware requirements to maintain efficiency for a system with many partitions? u When to hash? u Some simulation results
 Issues with TPM protocols: u Privacy: Critical data to be hashed but source to remain undisclosed u Deflection attack: Server initially deflects communication to a TPM based server and later starts communication u Replay attacks : Continue to use certificate after switching OS u Snoopy attacks : Pry on the communication line for certificates and use them as your own
Issues with TPM protocols: u Privacy: Critical data to be hashed but source to remain undisclosed u Deflection attack: Server initially deflects communication to a TPM based server and later starts communication u Replay attacks : Continue to use certificate after switching OS u Snoopy attacks : Pry on the communication line for certificates and use them as your own
 Non-network attacks u Have to trust some part of the kernel u DRAM is unsafe – freeze the computation u Pry on the system bus u. Side Channel Attacks
Non-network attacks u Have to trust some part of the kernel u DRAM is unsafe – freeze the computation u Pry on the system bus u. Side Channel Attacks
 Trusted Hardware for Partitioned Multicore u Efficiency issues – Is the system reasonable when there are 20 cores and 120 partitions? u Some partitions trusted and some untrusted u Cannot even think of timestamping to prevent replay u More privacy issues : Should not be able to ascertain two partitions are physically on the same computer
Trusted Hardware for Partitioned Multicore u Efficiency issues – Is the system reasonable when there are 20 cores and 120 partitions? u Some partitions trusted and some untrusted u Cannot even think of timestamping to prevent replay u More privacy issues : Should not be able to ascertain two partitions are physically on the same computer
 Virtual TPMs for Partitioned Multicore Multiple partitions hosting operating systems Virtual operating systems reside in virtual machines Changing partitions Virtualize TPMs Create one VTPM per partition Each VTPM has its own keys and resources and can replicate the functions of a real TPM A VTPM manager connects the VTPM instance and the OS partitions VTPM manager collects integrity measurements of VTPM instances
Virtual TPMs for Partitioned Multicore Multiple partitions hosting operating systems Virtual operating systems reside in virtual machines Changing partitions Virtualize TPMs Create one VTPM per partition Each VTPM has its own keys and resources and can replicate the functions of a real TPM A VTPM manager connects the VTPM instance and the OS partitions VTPM manager collects integrity measurements of VTPM instances
 Virtualization of TPM u. Virtualizing the TPM takes care of privacy issues u Chain of trust now goes through the virtual TPM u VTPM manager can give different privileges to different partitions. u Assurance on Quality of Service (Qo. S) can be given : we have a novel priority algorithm u Compromise of one partition ≠ Compromising the entire system
Virtualization of TPM u. Virtualizing the TPM takes care of privacy issues u Chain of trust now goes through the virtual TPM u VTPM manager can give different privileges to different partitions. u Assurance on Quality of Service (Qo. S) can be given : we have a novel priority algorithm u Compromise of one partition ≠ Compromising the entire system
 Hardware design for security TPM Secure DRAM Memory Encrypter Secure Box CPU
Hardware design for security TPM Secure DRAM Memory Encrypter Secure Box CPU
 More security measures u Security unusually dependent on correctness of kernel u Use the Hi-Star labeling mechanism u There are categories and labels – {0, 1, 2, 3} u Rules for information flow – function of category, label tuple u We have one Hi-star category for information flow from secure box to rest of the world
More security measures u Security unusually dependent on correctness of kernel u Use the Hi-Star labeling mechanism u There are categories and labels – {0, 1, 2, 3} u Rules for information flow – function of category, label tuple u We have one Hi-star category for information flow from secure box to rest of the world
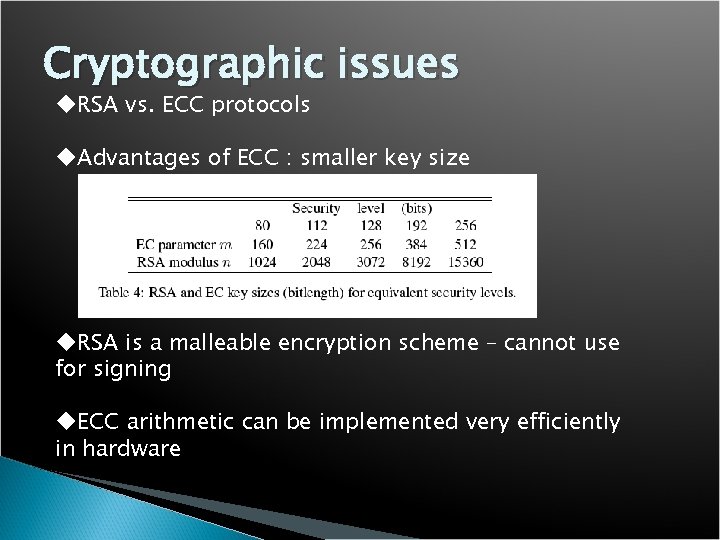 Cryptographic issues u. RSA vs. ECC protocols u. Advantages of ECC : smaller key size u. RSA is a malleable encryption scheme – cannot use for signing u. ECC arithmetic can be implemented very efficiently in hardware
Cryptographic issues u. RSA vs. ECC protocols u. Advantages of ECC : smaller key size u. RSA is a malleable encryption scheme – cannot use for signing u. ECC arithmetic can be implemented very efficiently in hardware
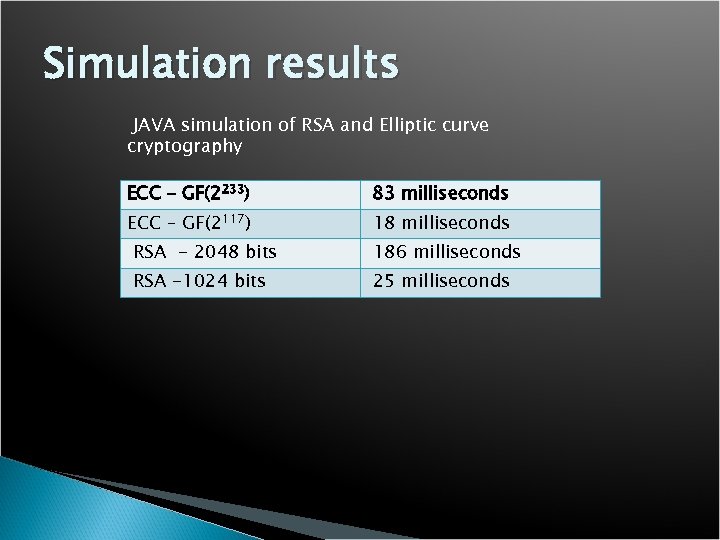 Simulation results JAVA simulation of RSA and Elliptic curve cryptography ECC – GF(2233) 83 milliseconds ECC – GF(2117) 18 milliseconds RSA - 2048 bits 186 milliseconds RSA -1024 bits 25 milliseconds
Simulation results JAVA simulation of RSA and Elliptic curve cryptography ECC – GF(2233) 83 milliseconds ECC – GF(2117) 18 milliseconds RSA - 2048 bits 186 milliseconds RSA -1024 bits 25 milliseconds
![ECC FPGA Coprocessors for Improved Performance [Rebeiro and Mukhopadhyay] 3 main modules: ALU, register ECC FPGA Coprocessors for Improved Performance [Rebeiro and Mukhopadhyay] 3 main modules: ALU, register](https://present5.com/presentation/017759453ae042c0baf2f50cbb1dc50c/image-20.jpg) ECC FPGA Coprocessors for Improved Performance [Rebeiro and Mukhopadhyay] 3 main modules: ALU, register bank, control unit ALU components ◦ ◦ 14 cascaded circuits quad circuits, used for inversion Multiplier N x Squarer N x Adder Register Bank: 233 bit dual port registers; input to the registers = base point or output of ALU Control unit: Finite State Machine for 32 control signals Replicate coprocessor components according to partitioned multicore performance requirements
ECC FPGA Coprocessors for Improved Performance [Rebeiro and Mukhopadhyay] 3 main modules: ALU, register bank, control unit ALU components ◦ ◦ 14 cascaded circuits quad circuits, used for inversion Multiplier N x Squarer N x Adder Register Bank: 233 bit dual port registers; input to the registers = base point or output of ALU Control unit: Finite State Machine for 32 control signals Replicate coprocessor components according to partitioned multicore performance requirements
 Use specialized hardware! Results from Software Simulation Operations Time Product – GF(2233) 0. 239 milliseconds Addition – GF(2233) 0. 001 milliseconds Inverse – GF(2233) 61. 722 millseconds Results from Hardware simulation Operations Time Clock Cycles Product – GF(2233) 0. 2178 μs 33 Inverse – GF(2233) 68 μs 10306
Use specialized hardware! Results from Software Simulation Operations Time Product – GF(2233) 0. 239 milliseconds Addition – GF(2233) 0. 001 milliseconds Inverse – GF(2233) 61. 722 millseconds Results from Hardware simulation Operations Time Clock Cycles Product – GF(2233) 0. 2178 μs 33 Inverse – GF(2233) 68 μs 10306
 Efficient implementation of primitives u Efficient implementation of finite field primitives is of central importance u Doubling a point on Elliptic curve: Can be done in 3 clock cycles (9 field multiplications) u Adding two points on elliptic curve: Can be done in 8 clock cycles (13 field multiplications)
Efficient implementation of primitives u Efficient implementation of finite field primitives is of central importance u Doubling a point on Elliptic curve: Can be done in 3 clock cycles (9 field multiplications) u Adding two points on elliptic curve: Can be done in 8 clock cycles (13 field multiplications)
 Even more decisions? u Tradeoffs: chip area, time complexity, power u Even for basic multiplication (finite field or Zn), one can have the hardware scale as n(log 3)/(log 2) and time as log n or have the hardware scale as n and time n(log 3)/(log 2) u Circuits have been implemented in Verilog showing tradeoff
Even more decisions? u Tradeoffs: chip area, time complexity, power u Even for basic multiplication (finite field or Zn), one can have the hardware scale as n(log 3)/(log 2) and time as log n or have the hardware scale as n and time n(log 3)/(log 2) u Circuits have been implemented in Verilog showing tradeoff


