6ec2305248d10a9dcd13b46816323e65.ppt
- Количество слайдов: 42
 Trust Management: Access policy and deduction John Mitchell
Trust Management: Access policy and deduction John Mitchell
 Diffuse Computing Distributed Data Systems
Diffuse Computing Distributed Data Systems
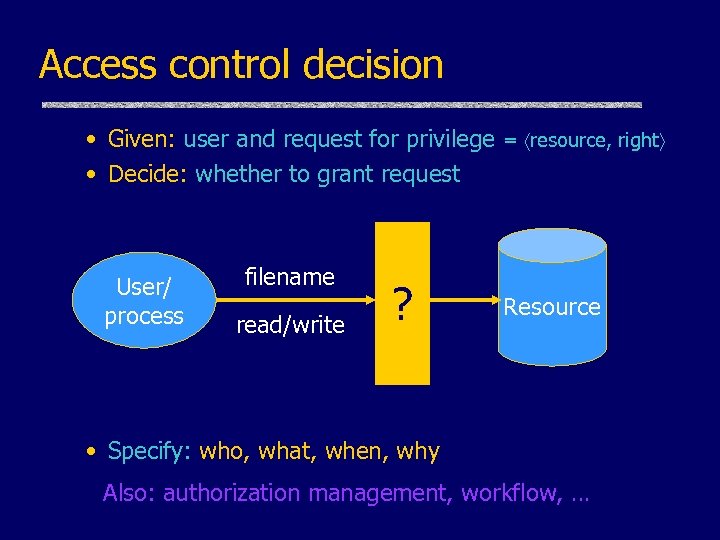 Access control decision • Given: user and request for privilege = resource, right • Decide: whether to grant request User/ process filename read/write ? Resource • Specify: who, what, when, why Also: authorization management, workflow, …
Access control decision • Given: user and request for privilege = resource, right • Decide: whether to grant request User/ process filename read/write ? Resource • Specify: who, what, when, why Also: authorization management, workflow, …
 Goals u. Flexible and scalable access control for largescale, open, decentralized systems • Resource sharing in decentralized systems – coalitions, multi-centric collaborative systems – grid computing • Electronic commerce • Health care systems • Authorization management
Goals u. Flexible and scalable access control for largescale, open, decentralized systems • Resource sharing in decentralized systems – coalitions, multi-centric collaborative systems – grid computing • Electronic commerce • Health care systems • Authorization management
 Core Issue Policy Language and Deduction u. Say what you want • Succinctly and directly • With confidence that you said what you meant u. Enforcement • Deduction, proof of compliance u. Policy development tools • Manage policy lifecycle • Safety analysis, availability
Core Issue Policy Language and Deduction u. Say what you want • Succinctly and directly • With confidence that you said what you meant u. Enforcement • Deduction, proof of compliance u. Policy development tools • Manage policy lifecycle • Safety analysis, availability
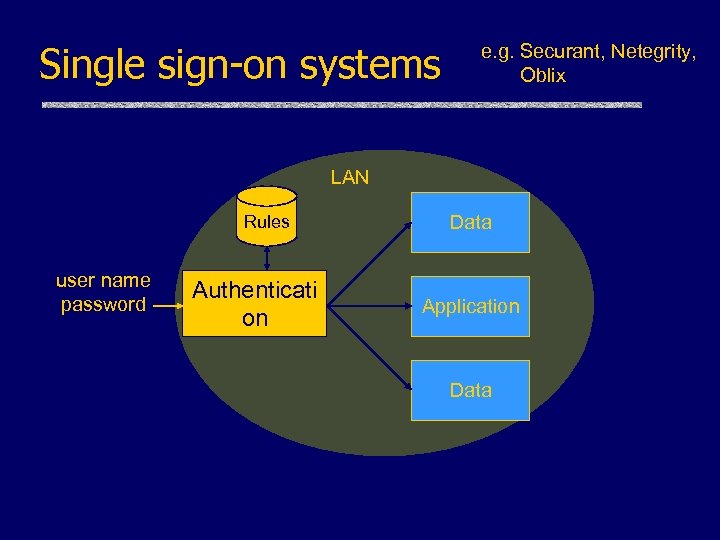 Single sign-on systems e. g. Securant, Netegrity, Oblix LAN Rules user name password Authenticati on Data Application Data
Single sign-on systems e. g. Securant, Netegrity, Oblix LAN Rules user name password Authenticati on Data Application Data
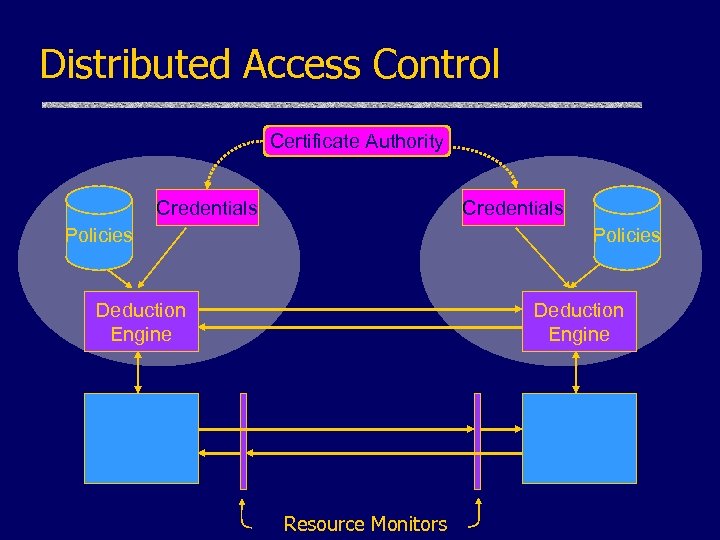 Distributed Access Control Certificate Authority Credentials Policies Deduction Engine Resource Monitors
Distributed Access Control Certificate Authority Credentials Policies Deduction Engine Resource Monitors
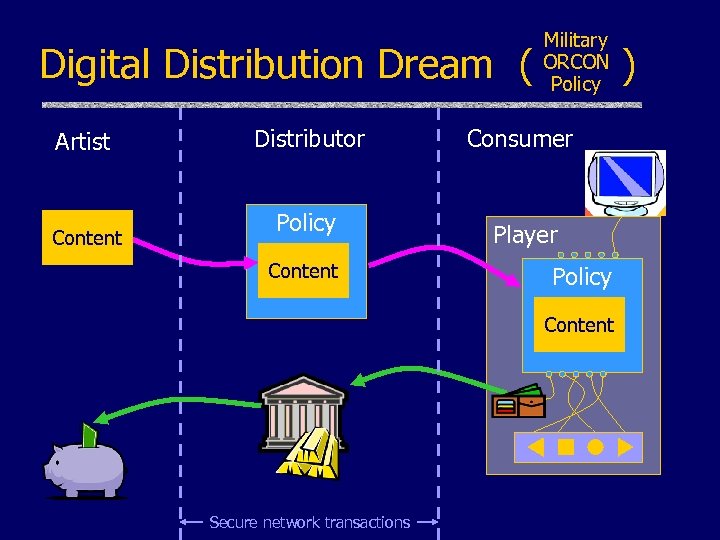 Digital Distribution Dream ( Artist Content Military ORCON Policy Distributor Consumer Policy Player Content Policy Content Secure network transactions )
Digital Distribution Dream ( Artist Content Military ORCON Policy Distributor Consumer Policy Player Content Policy Content Secure network transactions )
 Trust-Management (TM) u. Multicentric access control using delegation • access control decisions are based on distributed policy statements issued by multiple principals • policy statements contain – attributes of principals such as permissions, roles, qualifications, characteristics – trust relationships u. Common characteristics of TM systems: • treat public keys as principals to be authorized • use digitally signed credentials for non-local statements
Trust-Management (TM) u. Multicentric access control using delegation • access control decisions are based on distributed policy statements issued by multiple principals • policy statements contain – attributes of principals such as permissions, roles, qualifications, characteristics – trust relationships u. Common characteristics of TM systems: • treat public keys as principals to be authorized • use digitally signed credentials for non-local statements
 History u. Early TM languages • Policy. Maker, Key. Note [Blaze, Feigenbaum, et al. ] • SPKI/SDSI [Ellison, Rivest, Lampson, et al. ] u. Datalog-based TM languages • Delegation Logic • SD 3 • Binder [Li, Feigenbaum, and Grosof] [Jim] [De. Treville] u. Some other related work • ABLP logic • AF logic • QCM [Abadi, Burrows, Lampson, et al. ] [Appel and Felton] [Gunter and Jim]
History u. Early TM languages • Policy. Maker, Key. Note [Blaze, Feigenbaum, et al. ] • SPKI/SDSI [Ellison, Rivest, Lampson, et al. ] u. Datalog-based TM languages • Delegation Logic • SD 3 • Binder [Li, Feigenbaum, and Grosof] [Jim] [De. Treville] u. Some other related work • ABLP logic • AF logic • QCM [Abadi, Burrows, Lampson, et al. ] [Appel and Felton] [Gunter and Jim]
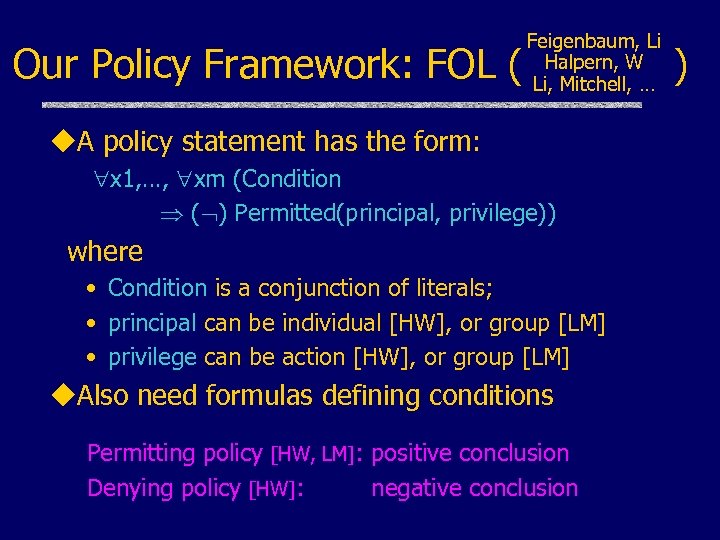 Our Policy Framework: FOL ( Feigenbaum, Li Halpern, W Li, Mitchell, … u. A policy statement has the form: x 1, …, xm (Condition ( ) Permitted(principal, privilege)) where • Condition is a conjunction of literals; • principal can be individual [HW], or group [LM] • privilege can be action [HW], or group [LM] u. Also need formulas defining conditions Permitting policy [HW, LM]: positive conclusion Denying policy [HW]: negative conclusion )
Our Policy Framework: FOL ( Feigenbaum, Li Halpern, W Li, Mitchell, … u. A policy statement has the form: x 1, …, xm (Condition ( ) Permitted(principal, privilege)) where • Condition is a conjunction of literals; • principal can be individual [HW], or group [LM] • privilege can be action [HW], or group [LM] u. Also need formulas defining conditions Permitting policy [HW, LM]: positive conclusion Denying policy [HW]: negative conclusion )
![What is RT? [Li, Mitchell, Winsborough] u. RT = Role-based Trust management u. Innovative What is RT? [Li, Mitchell, Winsborough] u. RT = Role-based Trust management u. Innovative](https://present5.com/presentation/6ec2305248d10a9dcd13b46816323e65/image-12.jpg) What is RT? [Li, Mitchell, Winsborough] u. RT = Role-based Trust management u. Innovative features of the RT family • • expressive delegation constructs permissions for structured resources tractable semantics based on Constraint Datalog strongly-typed credentials and vocabulary agreement • efficient deduction with millions of distributed policy statements • safety and availability analysis
What is RT? [Li, Mitchell, Winsborough] u. RT = Role-based Trust management u. Innovative features of the RT family • • expressive delegation constructs permissions for structured resources tractable semantics based on Constraint Datalog strongly-typed credentials and vocabulary agreement • efficient deduction with millions of distributed policy statements • safety and availability analysis
![[Li, Mitchell, Winsborough] Languages in RT Framework RT 0: Decentralized Roles RTT : for [Li, Mitchell, Winsborough] Languages in RT Framework RT 0: Decentralized Roles RTT : for](https://present5.com/presentation/6ec2305248d10a9dcd13b46816323e65/image-13.jpg) [Li, Mitchell, Winsborough] Languages in RT Framework RT 0: Decentralized Roles RTT : for Separation of Duties RTD: for RT 1: Parameterized Roles RT 2: Logical Objects Selective Use of Role memberships RT 1 C: structured resources RT 2 C: structured resources RTT and RTD can be used (either together or separately) with any of the five base languages: RT 0, RT 1, RT 2, RT 1 C, and RT 2 C
[Li, Mitchell, Winsborough] Languages in RT Framework RT 0: Decentralized Roles RTT : for Separation of Duties RTD: for RT 1: Parameterized Roles RT 2: Logical Objects Selective Use of Role memberships RT 1 C: structured resources RT 2 C: structured resources RTT and RTD can be used (either together or separately) with any of the five base languages: RT 0, RT 1, RT 2, RT 1 C, and RT 2 C
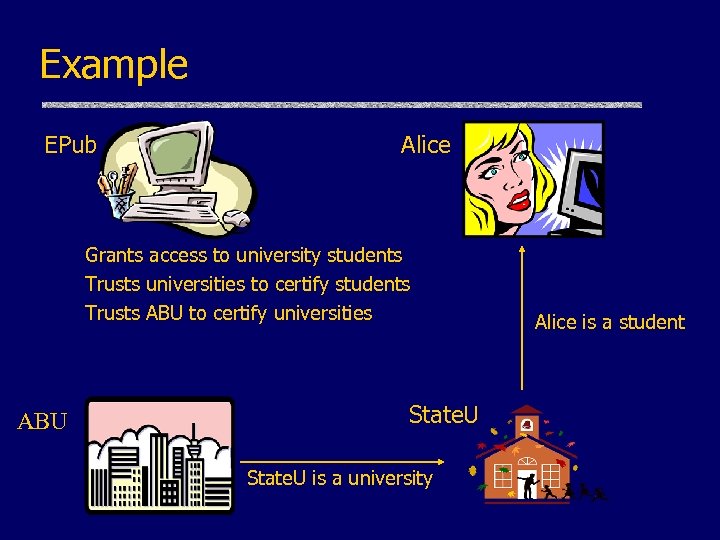 Example EPub Alice Grants access to university students Trusts universities to certify students Trusts ABU to certify universities ABU State. U is a university Alice is a student
Example EPub Alice Grants access to university students Trusts universities to certify students Trusts ABU to certify universities ABU State. U is a university Alice is a student
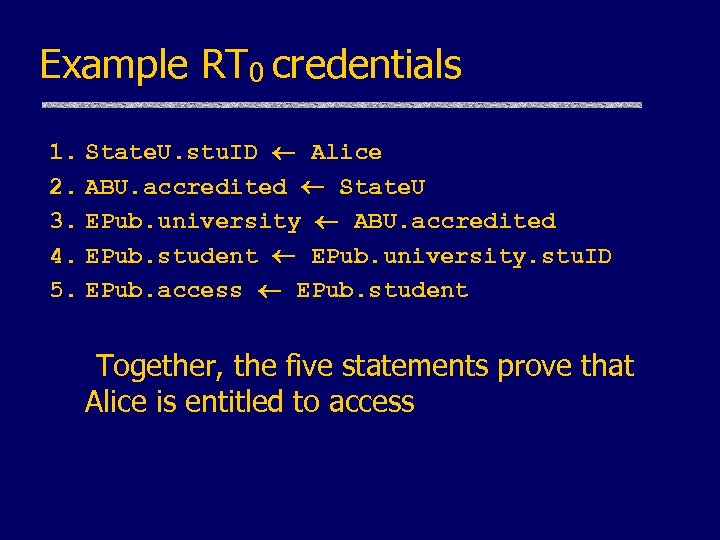 Example RT 0 credentials 1. State. U. stu. ID Alice 2. ABU. accredited State. U 3. EPub. university ABU. accredited 4. EPub. student EPub. university. stu. ID 5. EPub. access EPub. student Together, the five statements prove that Alice is entitled to access
Example RT 0 credentials 1. State. U. stu. ID Alice 2. ABU. accredited State. U 3. EPub. university ABU. accredited 4. EPub. student EPub. university. stu. ID 5. EPub. access EPub. student Together, the five statements prove that Alice is entitled to access
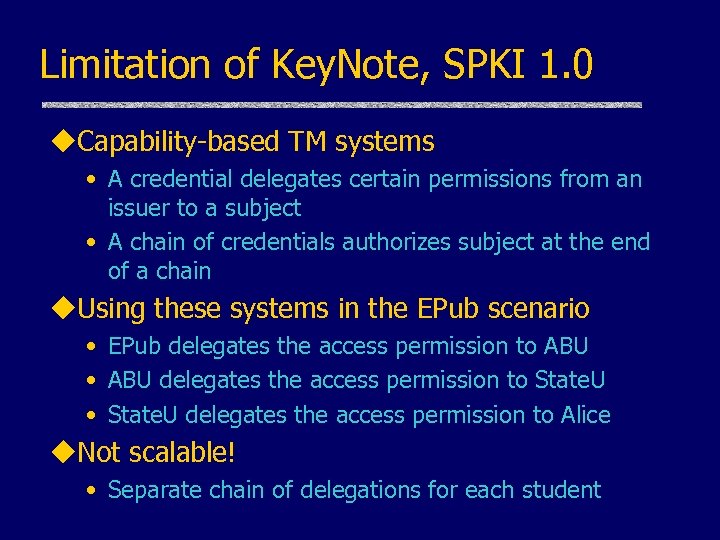 Limitation of Key. Note, SPKI 1. 0 u. Capability-based TM systems • A credential delegates certain permissions from an issuer to a subject • A chain of credentials authorizes subject at the end of a chain u. Using these systems in the EPub scenario • EPub delegates the access permission to ABU • ABU delegates the access permission to State. U • State. U delegates the access permission to Alice u. Not scalable! • Separate chain of delegations for each student
Limitation of Key. Note, SPKI 1. 0 u. Capability-based TM systems • A credential delegates certain permissions from an issuer to a subject • A chain of credentials authorizes subject at the end of a chain u. Using these systems in the EPub scenario • EPub delegates the access permission to ABU • ABU delegates the access permission to State. U • State. U delegates the access permission to Alice u. Not scalable! • Separate chain of delegations for each student
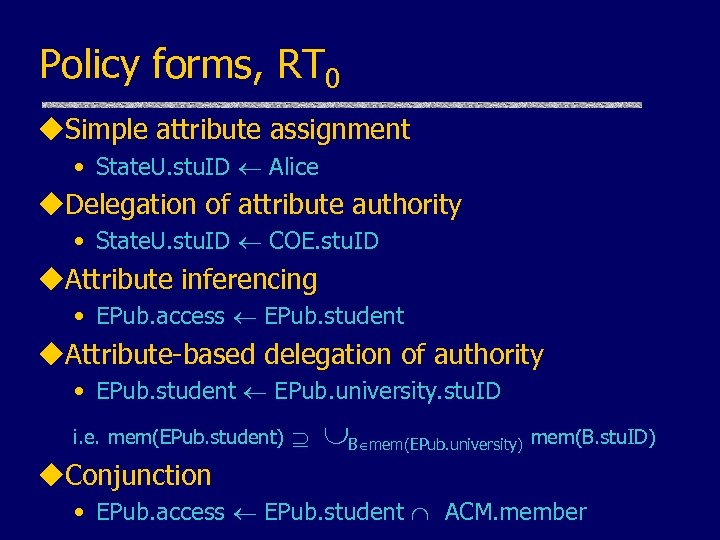 Policy forms, RT 0 u. Simple attribute assignment • State. U. stu. ID Alice u. Delegation of attribute authority • State. U. stu. ID COE. stu. ID u. Attribute inferencing • EPub. access EPub. student u. Attribute-based delegation of authority • EPub. student EPub. university. stu. ID i. e. mem(EPub. student) B mem(EPub. university) mem(B. stu. ID) u. Conjunction • EPub. access EPub. student ACM. member
Policy forms, RT 0 u. Simple attribute assignment • State. U. stu. ID Alice u. Delegation of attribute authority • State. U. stu. ID COE. stu. ID u. Attribute inferencing • EPub. access EPub. student u. Attribute-based delegation of authority • EPub. student EPub. university. stu. ID i. e. mem(EPub. student) B mem(EPub. university) mem(B. stu. ID) u. Conjunction • EPub. access EPub. student ACM. member
 Policy forms, RT 1 … u. Attributes with fields • State. U. stu. ID (name=. . , program=. . , …) Alice • EPub. access State. U. stu. ID(program=“graduate”) u. Permissions for structured resources • e. g. , allow connection to any host in a domain and at any port in a range
Policy forms, RT 1 … u. Attributes with fields • State. U. stu. ID (name=. . , program=. . , …) Alice • EPub. access State. U. stu. ID(program=“graduate”) u. Permissions for structured resources • e. g. , allow connection to any host in a domain and at any port in a range
 Datalog As A Foundation u. Natural • Security policy statements are if-then rules u. Precise • Declarative and widely-understood semantics u. Tractable • No function symbols tractability • Efficient goal-directed evaluation procedures u. Available technology • Extensive Datalog research in LP and DB
Datalog As A Foundation u. Natural • Security policy statements are if-then rules u. Precise • Declarative and widely-understood semantics u. Tractable • No function symbols tractability • Efficient goal-directed evaluation procedures u. Available technology • Extensive Datalog research in LP and DB
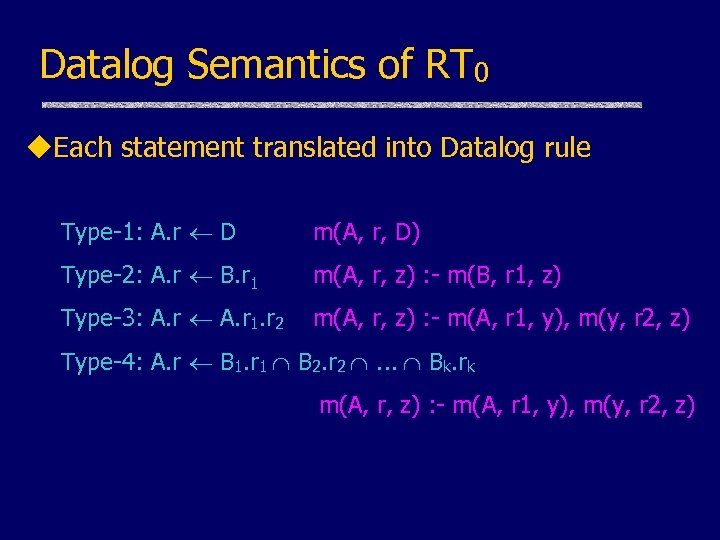 Datalog Semantics of RT 0 u. Each statement translated into Datalog rule Type-1: A. r D m(A, r, D) Type-2: A. r B. r 1 m(A, r, z) : - m(B, r 1, z) Type-3: A. r 1. r 2 m(A, r, z) : - m(A, r 1, y), m(y, r 2, z) Type-4: A. r B 1. r 1 B 2. r 2 . . . Bk. rk m(A, r, z) : - m(A, r 1, y), m(y, r 2, z)
Datalog Semantics of RT 0 u. Each statement translated into Datalog rule Type-1: A. r D m(A, r, D) Type-2: A. r B. r 1 m(A, r, z) : - m(B, r 1, z) Type-3: A. r 1. r 2 m(A, r, z) : - m(A, r 1, y), m(y, r 2, z) Type-4: A. r B 1. r 1 B 2. r 2 . . . Bk. rk m(A, r, z) : - m(A, r 1, y), m(y, r 2, z)
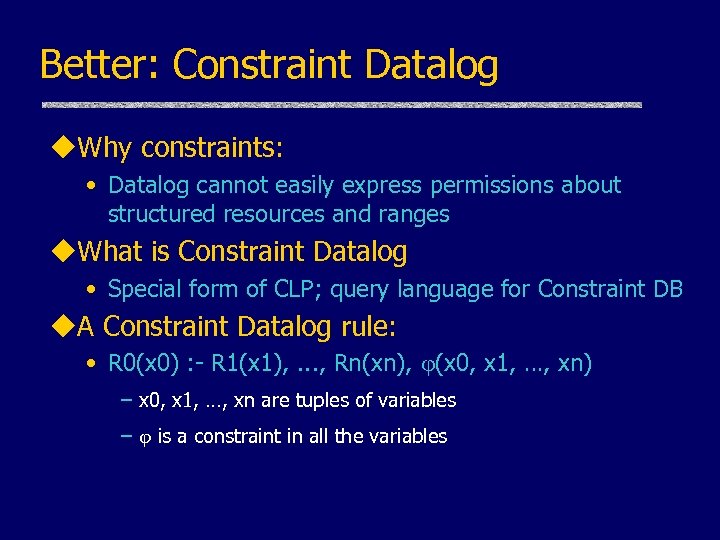 Better: Constraint Datalog u. Why constraints: • Datalog cannot easily express permissions about structured resources and ranges u. What is Constraint Datalog • Special form of CLP; query language for Constraint DB u. A Constraint Datalog rule: • R 0(x 0) : - R 1(x 1), . . . , Rn(xn), (x 0, x 1, …, xn) – x 0, x 1, …, xn are tuples of variables – is a constraint in all the variables
Better: Constraint Datalog u. Why constraints: • Datalog cannot easily express permissions about structured resources and ranges u. What is Constraint Datalog • Special form of CLP; query language for Constraint DB u. A Constraint Datalog rule: • R 0(x 0) : - R 1(x 1), . . . , Rn(xn), (x 0, x 1, …, xn) – x 0, x 1, …, xn are tuples of variables – is a constraint in all the variables
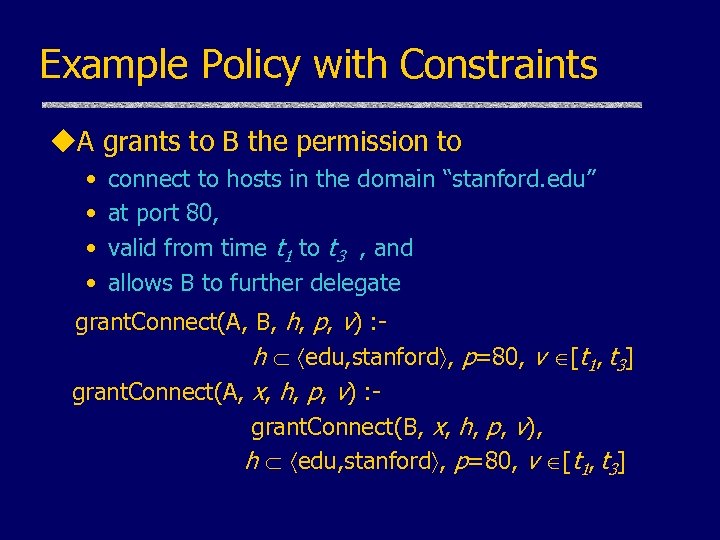 Example Policy with Constraints u. A grants to B the permission to • • connect to hosts in the domain “stanford. edu” at port 80, valid from time t 1 to t 3 , and allows B to further delegate grant. Connect(A, B, h, p, v) : h edu, stanford , p=80, v [t 1, t 3] grant. Connect(A, x, h, p, v) : grant. Connect(B, x, h, p, v), h edu, stanford , p=80, v [t 1, t 3]
Example Policy with Constraints u. A grants to B the permission to • • connect to hosts in the domain “stanford. edu” at port 80, valid from time t 1 to t 3 , and allows B to further delegate grant. Connect(A, B, h, p, v) : h edu, stanford , p=80, v [t 1, t 3] grant. Connect(A, x, h, p, v) : grant. Connect(B, x, h, p, v), h edu, stanford , p=80, v [t 1, t 3]
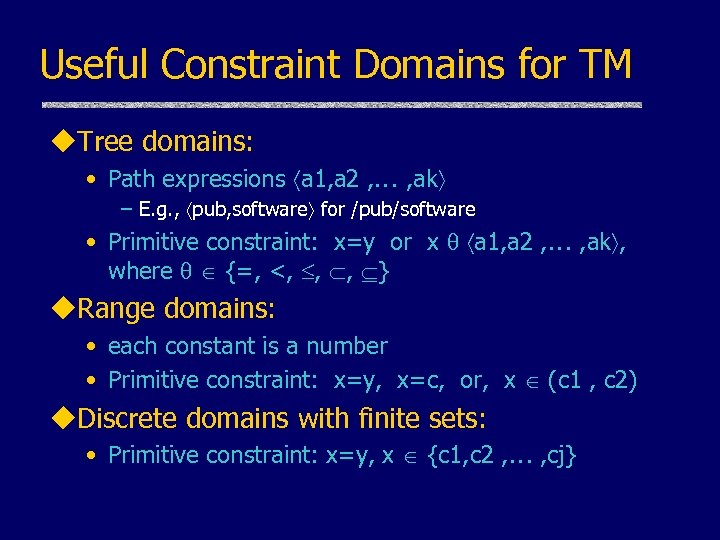 Useful Constraint Domains for TM u. Tree domains: • Path expressions a 1, a 2 , , ak – E. g. , pub, software for /pub/software • Primitive constraint: x=y or x a 1, a 2 , , ak , where {=, <, , , } u. Range domains: • each constant is a number • Primitive constraint: x=y, x=c, or, x (c 1 , c 2) u. Discrete domains with finite sets: • Primitive constraint: x=y, x {c 1, c 2 , , cj}
Useful Constraint Domains for TM u. Tree domains: • Path expressions a 1, a 2 , , ak – E. g. , pub, software for /pub/software • Primitive constraint: x=y or x a 1, a 2 , , ak , where {=, <, , , } u. Range domains: • each constant is a number • Primitive constraint: x=y, x=c, or, x (c 1 , c 2) u. Discrete domains with finite sets: • Primitive constraint: x=y, x {c 1, c 2 , , cj}
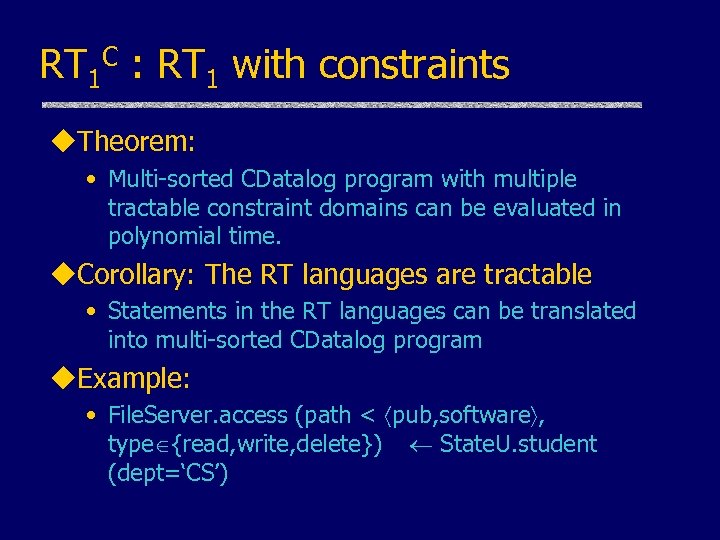 RT 1 C : RT 1 with constraints u. Theorem: • Multi-sorted CDatalog program with multiple tractable constraint domains can be evaluated in polynomial time. u. Corollary: The RT languages are tractable • Statements in the RT languages can be translated into multi-sorted CDatalog program u. Example: • File. Server. access (path < pub, software , type {read, write, delete}) State. U. student (dept=‘CS’)
RT 1 C : RT 1 with constraints u. Theorem: • Multi-sorted CDatalog program with multiple tractable constraint domains can be evaluated in polynomial time. u. Corollary: The RT languages are tractable • Statements in the RT languages can be translated into multi-sorted CDatalog program u. Example: • File. Server. access (path < pub, software , type {read, write, delete}) State. U. student (dept=‘CS’)
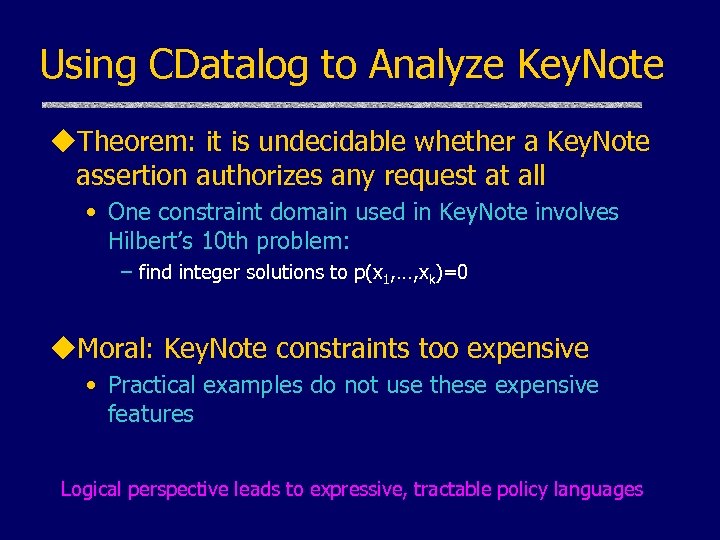 Using CDatalog to Analyze Key. Note u. Theorem: it is undecidable whether a Key. Note assertion authorizes any request at all • One constraint domain used in Key. Note involves Hilbert’s 10 th problem: – find integer solutions to p(x 1, …, xk)=0 u. Moral: Key. Note constraints too expensive • Practical examples do not use these expensive features Logical perspective leads to expressive, tractable policy languages
Using CDatalog to Analyze Key. Note u. Theorem: it is undecidable whether a Key. Note assertion authorizes any request at all • One constraint domain used in Key. Note involves Hilbert’s 10 th problem: – find integer solutions to p(x 1, …, xk)=0 u. Moral: Key. Note constraints too expensive • Practical examples do not use these expensive features Logical perspective leads to expressive, tractable policy languages
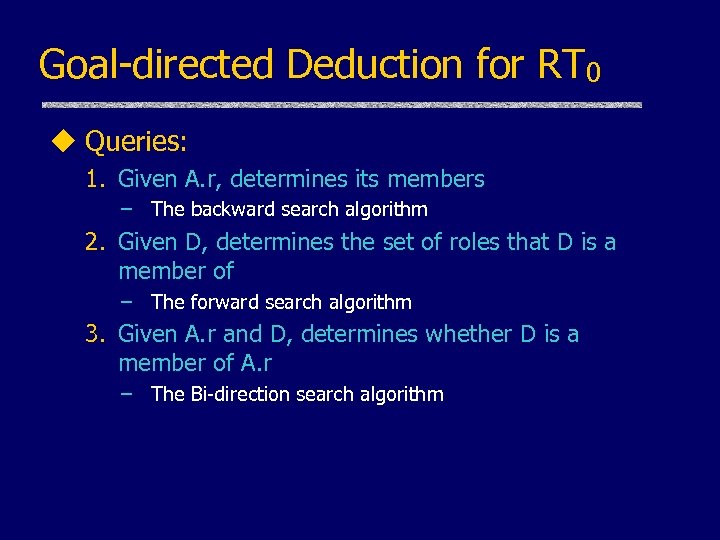 Goal-directed Deduction for RT 0 u Queries: 1. Given A. r, determines its members – The backward search algorithm 2. Given D, determines the set of roles that D is a member of – The forward search algorithm 3. Given A. r and D, determines whether D is a member of A. r – The Bi-direction search algorithm
Goal-directed Deduction for RT 0 u Queries: 1. Given A. r, determines its members – The backward search algorithm 2. Given D, determines the set of roles that D is a member of – The forward search algorithm 3. Given A. r and D, determines whether D is a member of A. r – The Bi-direction search algorithm
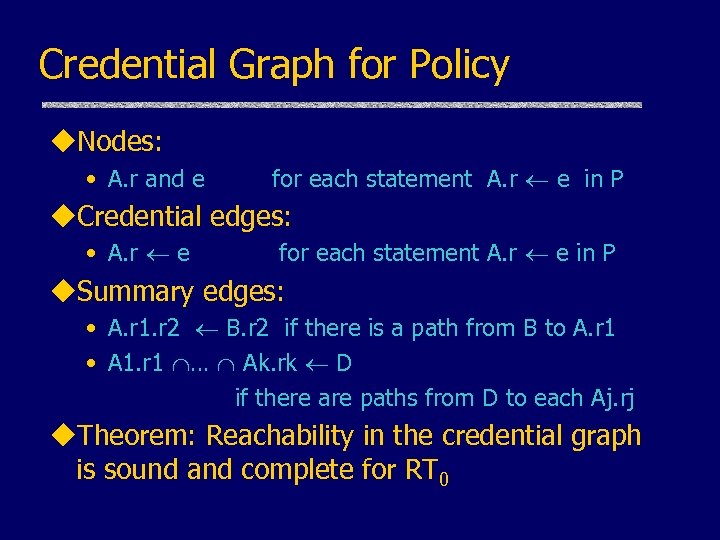 Credential Graph for Policy u. Nodes: • A. r and e for each statement A. r e in P u. Credential edges: • A. r e for each statement A. r e in P u. Summary edges: • A. r 1. r 2 B. r 2 if there is a path from B to A. r 1 • A 1. r 1 … Ak. rk D if there are paths from D to each Aj. rj u. Theorem: Reachability in the credential graph is sound and complete for RT 0
Credential Graph for Policy u. Nodes: • A. r and e for each statement A. r e in P u. Credential edges: • A. r e for each statement A. r e in P u. Summary edges: • A. r 1. r 2 B. r 2 if there is a path from B to A. r 1 • A 1. r 1 … Ak. rk D if there are paths from D to each Aj. rj u. Theorem: Reachability in the credential graph is sound and complete for RT 0
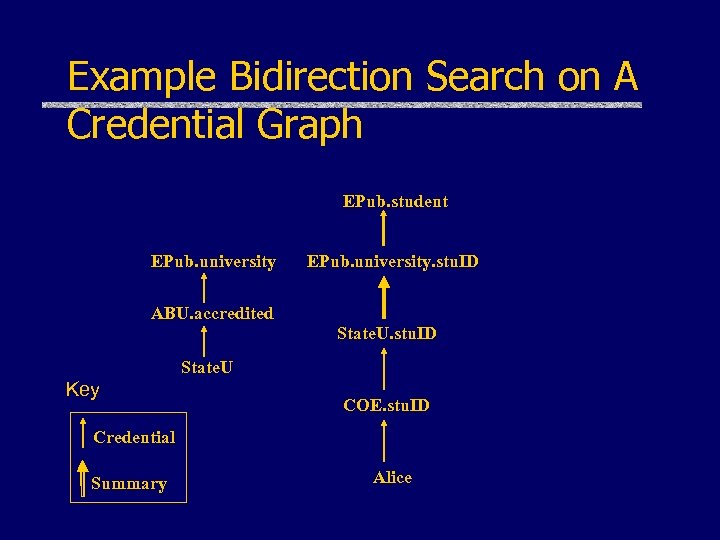 Example Bidirection Search on A Credential Graph EPub. student EPub. university. stu. ID ABU. accredited State. U. stu. ID State. U Key COE. stu. ID Credential Summary Alice
Example Bidirection Search on A Credential Graph EPub. student EPub. university. stu. ID ABU. accredited State. U. stu. ID State. U Key COE. stu. ID Credential Summary Alice
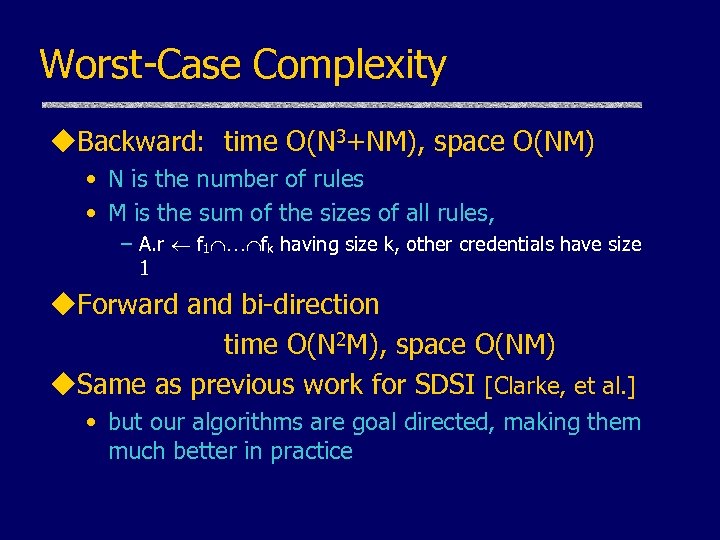 Worst-Case Complexity u. Backward: time O(N 3+NM), space O(NM) • N is the number of rules • M is the sum of the sizes of all rules, – A. r f 1 fk having size k, other credentials have size 1 u. Forward and bi-direction time O(N 2 M), space O(NM) u. Same as previous work for SDSI [Clarke, et al. ] • but our algorithms are goal directed, making them much better in practice
Worst-Case Complexity u. Backward: time O(N 3+NM), space O(NM) • N is the number of rules • M is the sum of the sizes of all rules, – A. r f 1 fk having size k, other credentials have size 1 u. Forward and bi-direction time O(N 2 M), space O(NM) u. Same as previous work for SDSI [Clarke, et al. ] • but our algorithms are goal directed, making them much better in practice
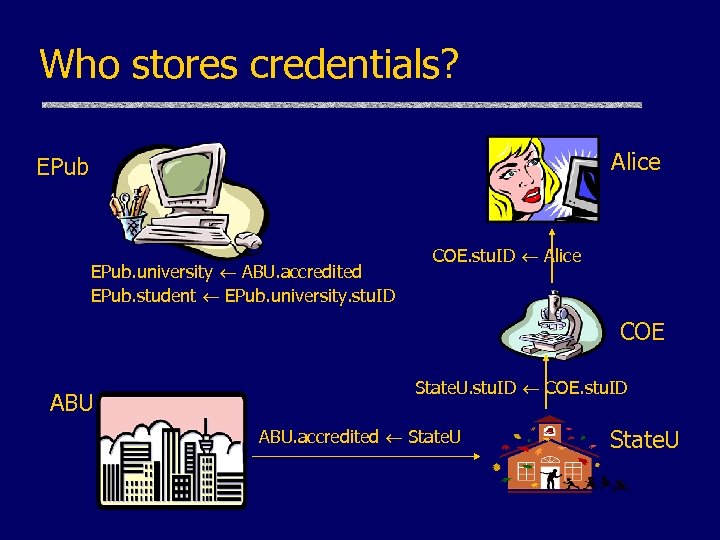 Who stores credentials? Alice EPub. university ABU. accredited EPub. student EPub. university. stu. ID COE. stu. ID Alice COE ABU State. U. stu. ID COE. stu. ID ABU. accredited State. U
Who stores credentials? Alice EPub. university ABU. accredited EPub. student EPub. university. stu. ID COE. stu. ID Alice COE ABU State. U. stu. ID COE. stu. ID ABU. accredited State. U
 Automated Trust Negotiation u. Credentials may contain sensitive information • need protection just as other resources • deduction must be interactive u. The Trust Target Graph (TTG) protocol • supports RT 0, which has delegation • supports distributed discovery of statements • supports Ack policies, which also protects against unauthorized leakage of attribute information u. Cryptographic protocols for ATN • Oblivious Signature-Based Envelope (OSBE)
Automated Trust Negotiation u. Credentials may contain sensitive information • need protection just as other resources • deduction must be interactive u. The Trust Target Graph (TTG) protocol • supports RT 0, which has delegation • supports distributed discovery of statements • supports Ack policies, which also protects against unauthorized leakage of attribute information u. Cryptographic protocols for ATN • Oblivious Signature-Based Envelope (OSBE)
 Safety and Availability Analysis u. Organizations delegate partial control • What happens if other organizations change policy in the future without my knowledge? u. Given policy P and restriction R on changes • Simple safety: Is A. r {D} possible? PTIME • Simple availability: Is A. r {D} necessary? PTIME • Bounded safety: Is {D 1, …, Dn} A. r necessary? PTIME
Safety and Availability Analysis u. Organizations delegate partial control • What happens if other organizations change policy in the future without my knowledge? u. Given policy P and restriction R on changes • Simple safety: Is A. r {D} possible? PTIME • Simple availability: Is A. r {D} necessary? PTIME • Bounded safety: Is {D 1, …, Dn} A. r necessary? PTIME
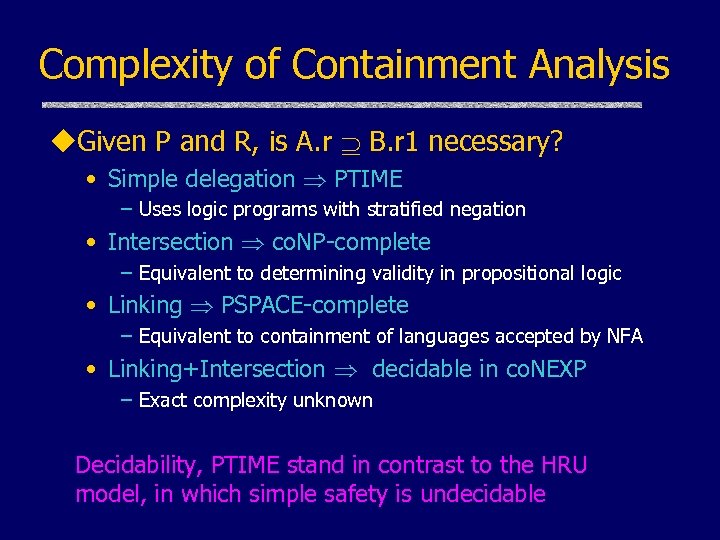 Complexity of Containment Analysis u. Given P and R, is A. r B. r 1 necessary? • Simple delegation PTIME – Uses logic programs with stratified negation • Intersection co. NP-complete – Equivalent to determining validity in propositional logic • Linking PSPACE-complete – Equivalent to containment of languages accepted by NFA • Linking+Intersection decidable in co. NEXP – Exact complexity unknown Decidability, PTIME stand in contrast to the HRU model, in which simple safety is undecidable
Complexity of Containment Analysis u. Given P and R, is A. r B. r 1 necessary? • Simple delegation PTIME – Uses logic programs with stratified negation • Intersection co. NP-complete – Equivalent to determining validity in propositional logic • Linking PSPACE-complete – Equivalent to containment of languages accepted by NFA • Linking+Intersection decidable in co. NEXP – Exact complexity unknown Decidability, PTIME stand in contrast to the HRU model, in which simple safety is undecidable
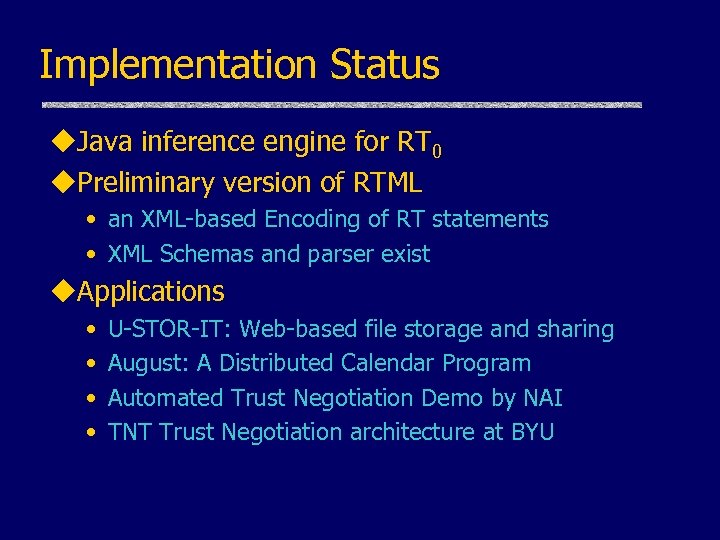 Implementation Status u. Java inference engine for RT 0 u. Preliminary version of RTML • an XML-based Encoding of RT statements • XML Schemas and parser exist u. Applications • • U-STOR-IT: Web-based file storage and sharing August: A Distributed Calendar Program Automated Trust Negotiation Demo by NAI TNT Trust Negotiation architecture at BYU
Implementation Status u. Java inference engine for RT 0 u. Preliminary version of RTML • an XML-based Encoding of RT statements • XML Schemas and parser exist u. Applications • • U-STOR-IT: Web-based file storage and sharing August: A Distributed Calendar Program Automated Trust Negotiation Demo by NAI TNT Trust Negotiation architecture at BYU
![Publications on RT u. Language specification, distributed deduction [ACM CCS’ 01] [JCS] [IEEE S&P’ Publications on RT u. Language specification, distributed deduction [ACM CCS’ 01] [JCS] [IEEE S&P’](https://present5.com/presentation/6ec2305248d10a9dcd13b46816323e65/image-35.jpg) Publications on RT u. Language specification, distributed deduction [ACM CCS’ 01] [JCS] [IEEE S&P’ 02] u. Constraint Datalog [PADL’ 03] [CSFW’ 03] u. Summary of RT [DISCEX’ 03] u. Interactive deduction, protecting sensitive credentials [IEEE Policy’ 02] [ACM WPES’ 02] u. Safety and availability analysis of RT policies [IEEE S&P’ 03]
Publications on RT u. Language specification, distributed deduction [ACM CCS’ 01] [JCS] [IEEE S&P’ 02] u. Constraint Datalog [PADL’ 03] [CSFW’ 03] u. Summary of RT [DISCEX’ 03] u. Interactive deduction, protecting sensitive credentials [IEEE Policy’ 02] [ACM WPES’ 02] u. Safety and availability analysis of RT policies [IEEE S&P’ 03]
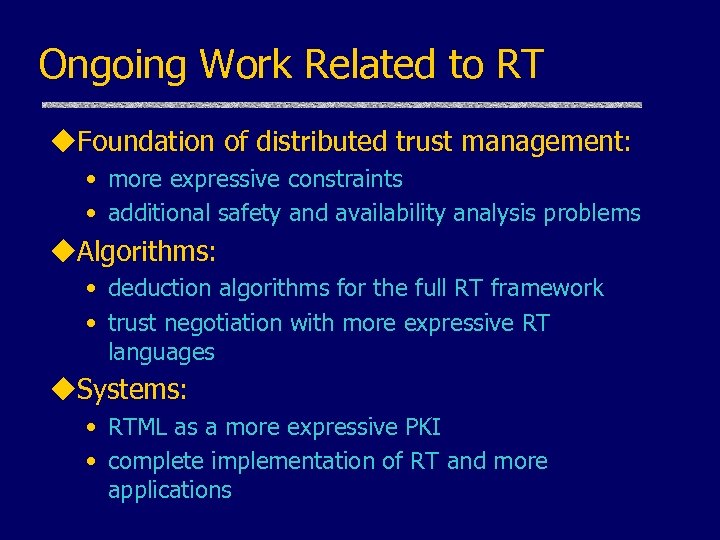 Ongoing Work Related to RT u. Foundation of distributed trust management: • more expressive constraints • additional safety and availability analysis problems u. Algorithms: • deduction algorithms for the full RT framework • trust negotiation with more expressive RT languages u. Systems: • RTML as a more expressive PKI • complete implementation of RT and more applications
Ongoing Work Related to RT u. Foundation of distributed trust management: • more expressive constraints • additional safety and availability analysis problems u. Algorithms: • deduction algorithms for the full RT framework • trust negotiation with more expressive RT languages u. Systems: • RTML as a more expressive PKI • complete implementation of RT and more applications
![[Halpern, Lagoze, Weissman] Policy with negation, functions u. Many applications explicitly forbid actions. • [Halpern, Lagoze, Weissman] Policy with negation, functions u. Many applications explicitly forbid actions. •](https://present5.com/presentation/6ec2305248d10a9dcd13b46816323e65/image-37.jpg) [Halpern, Lagoze, Weissman] Policy with negation, functions u. Many applications explicitly forbid actions. • `Smoking is prohibited in the dining areas of all restaurants seating more than 35 people’ is part of the NYC Smoke-Free Air Act. • `The tickets may not be refunded’ is a policy of many theaters, special airline fares, … u. Functions may be useful • x 1, x 2 (On. Site(x 1) Permitted(x 2, copy(x 1))) u. These policies cannot be written directly in Datalog, Constraint Datalog
[Halpern, Lagoze, Weissman] Policy with negation, functions u. Many applications explicitly forbid actions. • `Smoking is prohibited in the dining areas of all restaurants seating more than 35 people’ is part of the NYC Smoke-Free Air Act. • `The tickets may not be refunded’ is a policy of many theaters, special airline fares, … u. Functions may be useful • x 1, x 2 (On. Site(x 1) Permitted(x 2, copy(x 1))) u. These policies cannot be written directly in Datalog, Constraint Datalog
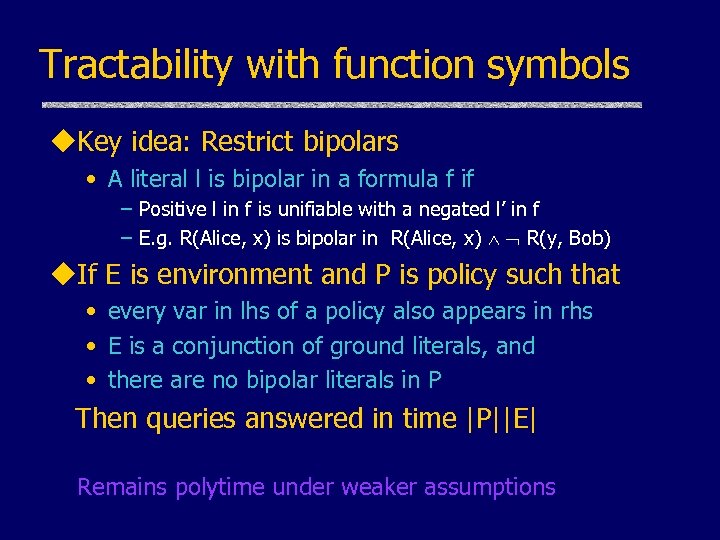 Tractability with function symbols u. Key idea: Restrict bipolars • A literal l is bipolar in a formula f if – Positive l in f is unifiable with a negated l’ in f – E. g. R(Alice, x) is bipolar in R(Alice, x) R(y, Bob) u. If E is environment and P is policy such that • every var in lhs of a policy also appears in rhs • E is a conjunction of ground literals, and • there are no bipolar literals in P Then queries answered in time |P||E| Remains polytime under weaker assumptions
Tractability with function symbols u. Key idea: Restrict bipolars • A literal l is bipolar in a formula f if – Positive l in f is unifiable with a negated l’ in f – E. g. R(Alice, x) is bipolar in R(Alice, x) R(y, Bob) u. If E is environment and P is policy such that • every var in lhs of a policy also appears in rhs • E is a conjunction of ground literals, and • there are no bipolar literals in P Then queries answered in time |P||E| Remains polytime under weaker assumptions
 Explanation of restrictions u. Every variable on the lhs also on the rhs • Permissions (prohibitions) depend only on attributes of individual and action being regulated u. Environment E a conjunction of ground literals • Reasonable if the environment is a database, and/or set of certificates u. No bipolar literals in policy P • Reasonable if – permitted is not in any policy’s premise – All policies are permitting (or all denying)
Explanation of restrictions u. Every variable on the lhs also on the rhs • Permissions (prohibitions) depend only on attributes of individual and action being regulated u. Environment E a conjunction of ground literals • Reasonable if the environment is a database, and/or set of certificates u. No bipolar literals in policy P • Reasonable if – permitted is not in any policy’s premise – All policies are permitting (or all denying)
 Mixed policy sets u Thm: For any env E, policy P, can reformulate as
Mixed policy sets u Thm: For any env E, policy P, can reformulate as
 Future SPYCE Directions u. Accomplishments • Framework and logic for policy definition • Algorithms for policy enforcement • Some experience with capturing practical policy requirements from a variety of applications u. Challenges • Continue implementation and deployment efforts • Policy development algorithms and tools – Debugging and testing, safety and availability analysis • Additional challenges – Policy privacy, Automated trust negotiation, Revocation
Future SPYCE Directions u. Accomplishments • Framework and logic for policy definition • Algorithms for policy enforcement • Some experience with capturing practical policy requirements from a variety of applications u. Challenges • Continue implementation and deployment efforts • Policy development algorithms and tools – Debugging and testing, safety and availability analysis • Additional challenges – Policy privacy, Automated trust negotiation, Revocation
 Sample Applications u. August Distributed Calendar u. USTORIT u. Social security database • policy to qualify for social security • Also: tax law database u. Library policy • Have to administer copyright • Who is allowed to access course notes? u. Xr. ML • Commercial license and rights framework
Sample Applications u. August Distributed Calendar u. USTORIT u. Social security database • policy to qualify for social security • Also: tax law database u. Library policy • Have to administer copyright • Who is allowed to access course notes? u. Xr. ML • Commercial license and rights framework


