6d23fd60cfcb2af7a3347f6e1b357680.ppt
- Количество слайдов: 13

Trojan Horse Implementation and Prevention By Pallavi Dharmadhikari Sirisha Bollineni Vijaya. Lakshmi Jothiram Vasanthi Madala

Trojan Horse n Agenda q q q q Introduction of Trojan Horse Objectives of Trojan Horse Types of Trojan Horses Trojan Horse Techniques Implementation with an example Prevention Methods Q&A
Trojan Horse : Introduction n. A Trojan Horse program is a unique form of computer attack that allows a remote user a means of gaining access to a victim's machine without their knowledge. n. Trojan Horse initially appears to be harmless, but later proves to be extremely destructive. n. Trojan Horse is not a Virus.
Objectives of Trojan Horse Programs Trojan horses can exploit your system in various and creative ways including: n Creating a "backdoor" that allows remote access to control your machine n Recording keystrokes to steal credit card or password information n Commandeering your system to distribute malware or spam to other computers n Spying on your activities by sending screenshots of your monitor to a remote location n Uploading or downloading files n Erasing or overwriting data

Types of Trojan Horses The EC Council groups Trojan horses into seven main types n Remote Access Trojans q Subseven n Data Sending Trojans q Eblaster n Destructive Trojans q Hard Disk Killer n Proxy Trojans q Troj/Proxy-GG n FTP Trojans q Trojan. Win 32. FTP Attack n security software disabler Trojans q Trojan. Win 32. Disabler. b n denial-of-service attack (Do. S) Trojans q PC Cyborg Trojan
Trojan Horse Techniques n Alter name of malicious code on system. n Create a file name to obscure the file's type. q just_text. txt. exe n abcd. shs where by default the shs file will not be displayed in the system"
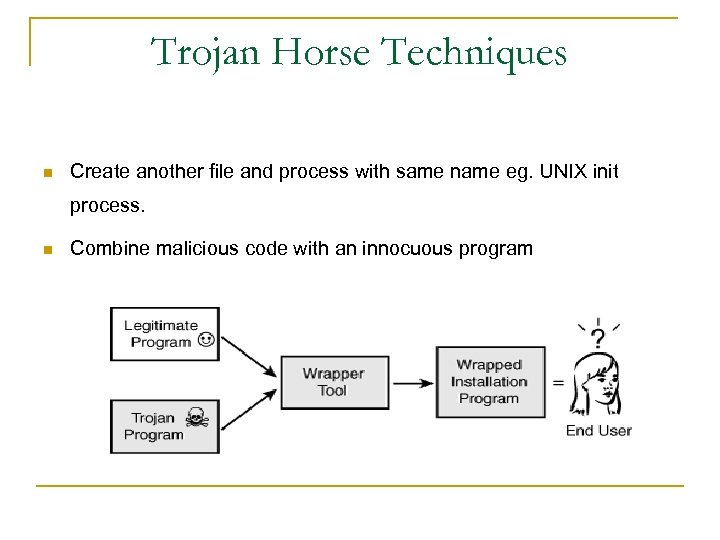
Trojan Horse Techniques n Create another file and process with same name eg. UNIX init process. n Combine malicious code with an innocuous program
Implementation of a Trojan Horse Program Trojan. Gletta. A is a Trojan horse program that steals Internet banking passwords. It logs keystrokes of a victim computer when the user visits certain Web pages and then emails the log to the attacker. 1) Trojan. Gletta. A executable locates the System folder copies itself to the system folder and the Windows installation folder. q q q %System%Wmiprvse. exe %System%Ntsvc. exe %Windir%Userlogon. exe 2) Creates %System%Rsasec. dll, which is a key logger and %System%rsacb. dll, which is actually a text file key logger file. 3) Adds a registry key value "wmiprvse. exe"="%system%wmiprvse. exe" , to the registry key: HKEY_LOCAL_MACHINESoftwareMicrosoftWindowsCurrent. VersionRun, so that the Trojan runs when you start Windows.
Implementation of a Trojan Horse Program 4) On Windows NT/2000/XP, it adds the value: "Run" = "%Windir%userlogon. exe" to the registry key: HKEY_LOCAL_MACHINESoftwareMicrosoftWindows. NTCurrent. VersionWindows, so that the Trojan runs when you start the operating systems. The program watches for Internet Explorer windows that have any of the following titles: n National Internet Banking n Welcome to Citibank n Bank of China n HSBC in Hong Kong or one of the following URLs: n https: / /olb. westpac. com. au/ib/asp/ n https: / /olb. westpac. com. au/ib/ 5) It also captures all the keystrokes entered into any windows that match those listed above, and writes them into a log file. 6) Later it uses its own SMTP engine to send the log file to an external mail account of the intruder. The mail has the following characteristics: q Both the FROM and TO addresses have the domain "mail. ru" q The subject starts with "Business News from"

Prevention of Trojan Horse Programs n Install latest security patches for the operating system. n Install Anti-Trojan software. q q Trojan Hunter A- Squared n Install anti-virus software and update it regularly n Install a secure firewall n Do not give strangers access (remote as well as physical) to your computer. n Do not run any unknown or suspicious executable program just to "check it out". n Scan all email attachments with an antivirus program before opening it.

Prevention of Trojan Horse Programs n Do regular backup of your system. n Do not use the features in programs that can automatically get or preview files. n Do not type commands that others tell you to type, or go to web addresses mentioned by strangers. n Never open instant message (IM) attachments from unknown people. n Do not use peer-to-peer or P 2 P sharing networks, such as Kazaa, Limewire, Gnutella, etc. as they do not filter out malicious programs hidden in shared files. n Educate your coworkers, employees, and family members about the effects of Trojan Horse. n Finally, protection from Trojans involves simple common sense
![References n [1] Trojan horse, http: //www. webopedia. com/TERM/R/Remote_Access_Trojan. html n [2] The corporate References n [1] Trojan horse, http: //www. webopedia. com/TERM/R/Remote_Access_Trojan. html n [2] The corporate](https://present5.com/presentation/6d23fd60cfcb2af7a3347f6e1b357680/image-12.jpg)
References n [1] Trojan horse, http: //www. webopedia. com/TERM/R/Remote_Access_Trojan. html n [2] The corporate threat posed by email Trojans, http: //www. gfi. com/whitepapers/network-protection-against-trojans. pdf n [3] Trojan. Gletta. A, June 09, 2004 http: //www. sarc. com/avcenter/venc/data/trojan. gletta. a. html n [4] What You Click May Not Always Be What You Get!, Robert B. Fried, http: //www. crime-scene-investigator. net/Trojan. Horse. pdf n [5] Trojan Programs, http: //www. viruslist. com/en/virusesdescribed? chapter=152540521 n [6]. Lo, Joseph, "Trojan Horse or Virus? ", Feb 5, 2006 http: //www. irchelp. org/irchelp/security/trojanterms. html n [7]. Delio, Michelle, "Viruses? Feh! Fear the Trojan". May 24, 2001. http: //www. wired. com/news/infostructure/0, 1377, 43981, 00. html n [8] Trojan horse, http: //www. cybertraveler. org/trojan_horse. html n [9]Microsoft CRM Implementation Guide - Planning the Security of your Microsoft CRM System, http: //www. microsoft. com/technet/prodtechnol/mscrm 1/plan/13_secur. mspx n [10] Trojan horse, http: //en. wikipedia. org/wiki/Trojan_horse_(computing) n [11] Safari Online, Pro. Quest Information and Learning, http: //proquest. safaribooksonline. com.
Q & A?
6d23fd60cfcb2af7a3347f6e1b357680.ppt