50c95d9d05f4026ae841cbd2d44f27e0.ppt
- Количество слайдов: 35

TRBAC: A Temporal Role-Based Access Control Model Elisa Bertino CERIAS and CS Department Purdue University
![What is TRBAC? RBAC Model [Sandhu 98] Temporal constraints on role activations/deactivations Elisa Bertino What is TRBAC? RBAC Model [Sandhu 98] Temporal constraints on role activations/deactivations Elisa Bertino](https://present5.com/presentation/50c95d9d05f4026ae841cbd2d44f27e0/image-2.jpg)
What is TRBAC? RBAC Model [Sandhu 98] Temporal constraints on role activations/deactivations Elisa Bertino 1
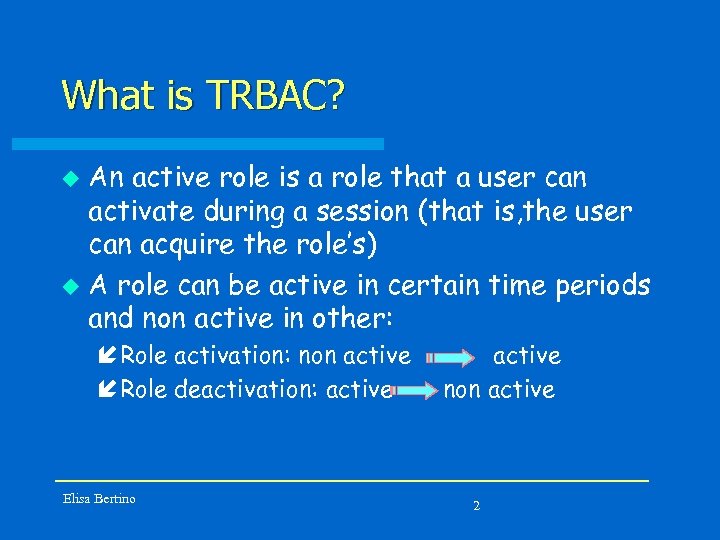
What is TRBAC? An active role is a role that a user can activate during a session (that is, the user can acquire the role’s) u A role can be active in certain time periods and non active in other: u í Role activation: non active í Role deactivation: active Elisa Bertino active non active 2
Why TRBAC? u Often roles are characterized by a temporal dimension : í Job functions may have limited or periodic time duration í There may be activation dependencies among roles Elisa Bertino 3
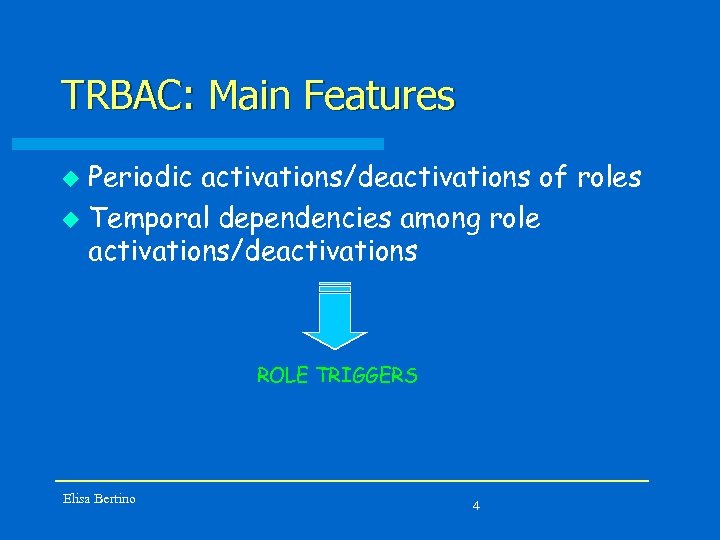
TRBAC: Main Features Periodic activations/deactivations of roles u Temporal dependencies among role activations/deactivations u ROLE TRIGGERS Elisa Bertino 4
TRBAC: Main Features u Role triggers may cause either: í Immediate activations/deactivations, or í Deferred activations/deactivations u Run-time requests to dynamically change the status of a role Elisa Bertino 5

TRBAC: Main Features u Priorities for: í Periodic activations/deactivations í Role triggers í Runt-time requests u Priorities are used for conflict resolution Elisa Bertino 6
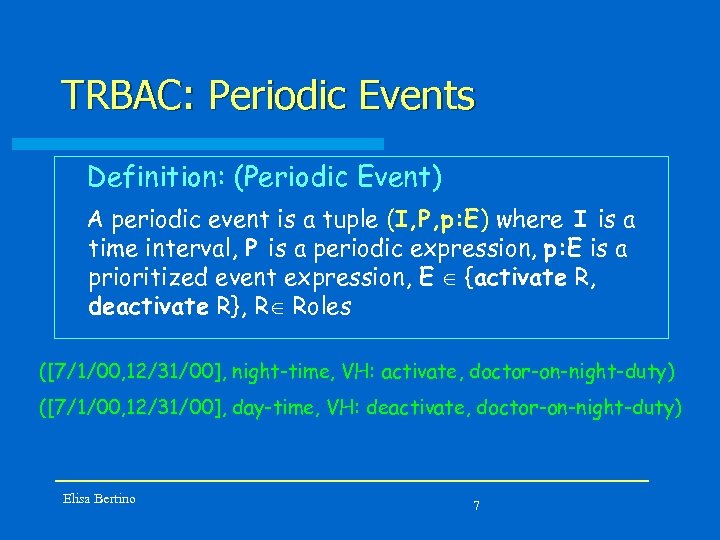
TRBAC: Periodic Events Definition: (Periodic Event) A periodic event is a tuple (I, P, p: E) where I is a time interval, P is a periodic expression, p: E is a prioritized event expression, E Î {activate R, deactivate R}, RÎ Roles ([7/1/00, 12/31/00], night-time, VH: activate, doctor-on-night-duty) ([7/1/00, 12/31/00], day-time, VH: deactivate, doctor-on-night-duty) Elisa Bertino 7
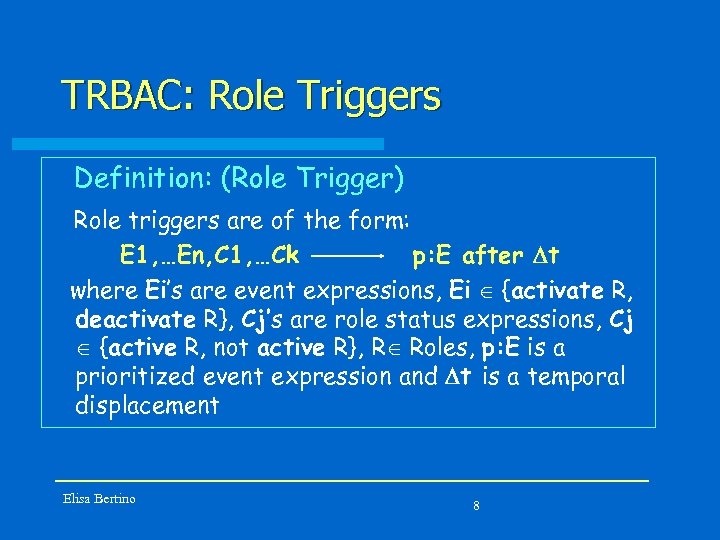
TRBAC: Role Triggers Definition: (Role Trigger) Role triggers are of the form: E 1, …En, C 1, …Ck p: E after Dt where Ei’s are event expressions, Ei Î {activate R, deactivate R}, Cj’s are role status expressions, Cj Î {active R, not active R}, RÎ Roles, p: E is a prioritized event expression and Dt is a temporal displacement Elisa Bertino 8

Role Triggers: Example activate doctor-on-night-duty activate nurse-on-day-duty Elisa Bertino VH: activate nurse-on-nigth-duty H: activate nurse-on-training after 2 Hours 9
![Role Activation Base ([1/1/00, 12/31/00], night-time, VH: activate doctor-on-night-duty) RAB = Periodic Events + Role Activation Base ([1/1/00, 12/31/00], night-time, VH: activate doctor-on-night-duty) RAB = Periodic Events +](https://present5.com/presentation/50c95d9d05f4026ae841cbd2d44f27e0/image-11.jpg)
Role Activation Base ([1/1/00, 12/31/00], night-time, VH: activate doctor-on-night-duty) RAB = Periodic Events + doctor-on-night-duty) ([1/1/00, 12/31/00], day-time, VH: deactivate. Role Triggers ([1/1/00, 12/31/00], day-time, VH: activate doctor-on-day-duty) ([1/1/00, 12/31/00], night-time, VH: deactivate doctor-on-day-duty) activate doctor-on-night-duty H: activate nurse-on-nigth-duty deactivate doctor-on-night-duty activate doctor-on-day-duty deactivate doctor-on-day-duty activate nurse-on-day-duty deactivate nurse-on-day-duty Elisa Bertino H: deactivate nurse-on-nigth-duty H: activate nurse-on-day-duty H: deactivate nurse-on-day-duty H: activate nurse-on-training after 2 Hours VH: deactivate nurse-on-training 10

TRBAC: Runtime Request Expressions Definition: (Runtime Request Expression) A runtime request expression has the form: p: E after Dt where p: E is a prioritized event expression and Dt is a temporal displacement deactivate nurse-on-training after 2 Hours activate emergency-doctor Elisa Bertino 11

TRBAC: Formal Aspects u The Execution Model of a RAB specifies, for each istant t, the set of events that should occur at time t according to: í periodic events & triggers in the RAB í runtime request expressions í priorities Elisa Bertino 12
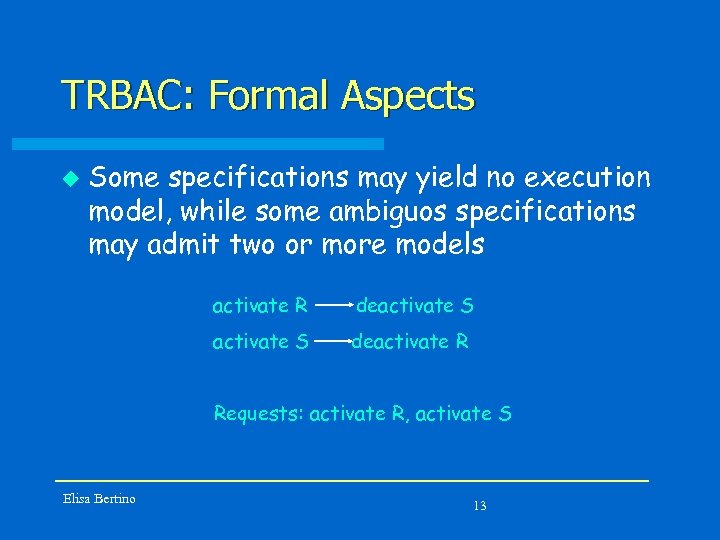
TRBAC: Formal Aspects u Some specifications may yield no execution model, while some ambiguos specifications may admit two or more models activate R deactivate S deactivate R Requests: activate R, activate S Elisa Bertino 13
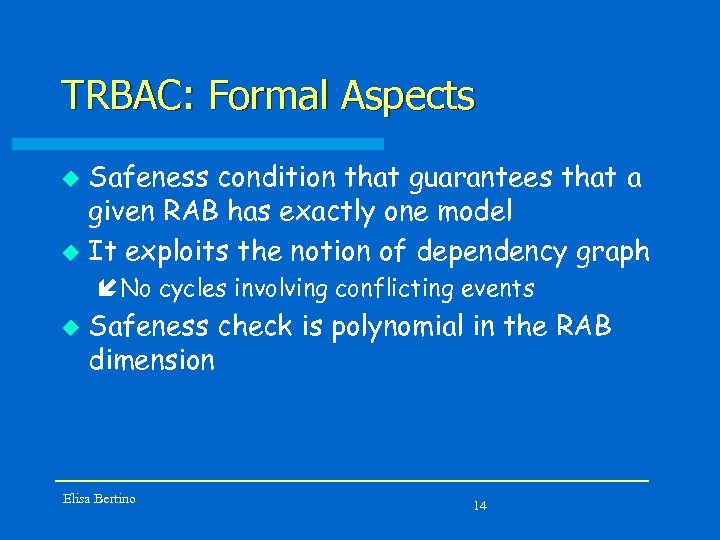
TRBAC: Formal Aspects Safeness condition that guarantees that a given RAB has exactly one model u It exploits the notion of dependency graph u í No cycles involving conflicting events u Safeness check is polynomial in the RAB dimension Elisa Bertino 14

TRBAC: Architectural Aspects At each time it is necessary to know which are the active roles, on the basis of the RAB and runtime requests u A request by a user to activate a role is authorized if: u í The user has the authorization to play that role í The role is active at the time of the request Elisa Bertino 15
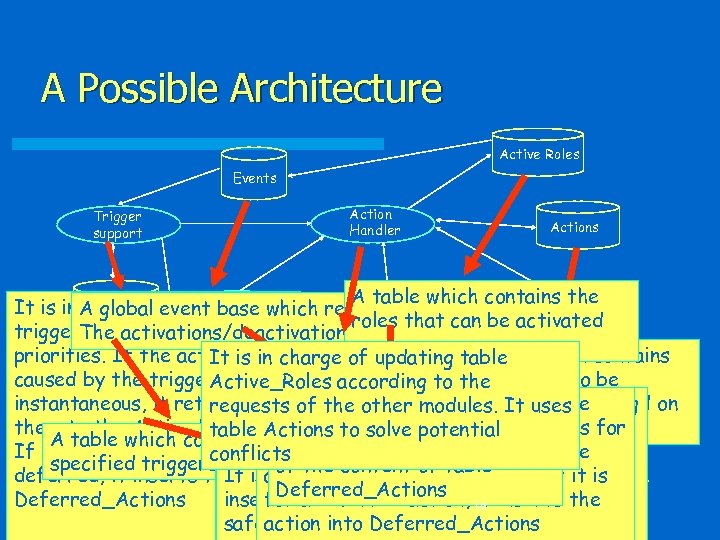
A Possible Architecture Active Roles Events Trigger support Action Handler Actions PE DA A table which contains the It is records Handler roles that can be activated triggers according to their The activations/deactivations of roles priorities. If the action(s)in charge of updating table which contains A table It is caused by the trigger(s) are Active_Roles according to the actions to be Deferred Safeness instantaneous, it returns It is activated each time a runtime potentially executed requests of the other is in charge of managing on Actions It modules. It uses Checker It is in charge of executing them to the Action Handler. request is solve potential Periodic events periodic events and Active_Roles table Actions to issued. If the request is for runtime requests deferred actions on the basis A table which contains the If the actions have to be an immediate inserting/deletingthe action, it returns the conflicts specified triggers of the content of table deferred, it inserts themisaction to the corresponding actionsis It into activated each time a trigger if it Action_Handler, is Deferred_Actions Elisa Bertino Deferred_Actions A a deferred action, 16 an entry for inserted/modified to verify table fortable which contains whether the into/from inserts it each preserved safeness isdeferred action into Deferred_Actions RTR Triggers in A globalof firing charge event base which Handler
Generalized TRBAC (GTRBAC) u Motivations: í TRBAC does not distinguish between a role being enabled and a role being active í A role is enabled if the temporal conditions associated with it are satisfied í A role is active if a user has logged in the role í Only enabled roles can be activated í Because of such limitations, TRBAC cannot support some forms of constraints, such as the maximum number of activations of a role by a user in a given time interval Elisa Bertino 17
GTRBAC u GTRBAC extends TRBAC by introducing temporal conditions on: í User-role assignments í Role-permission assignments u A large number of constraints can thus be supported Elisa Bertino 18
GTRBAC – Examples of Constraints u Constraints on the number of concurrent activations í “there can be at most 10 users activating the role Day. Doctor at a time” u Constraints on the number of total activations in a given period í “the role Head. Nurse can be activated at most 2 times per day” Elisa Bertino 19
X-GTRBAC - Motivations u Role Based Access Control Model í Many benefits over traditional access control models when applied to emerging applications u XML is a uniform platform for information interchange Our Goal XML + RBAC extension To provide access control framework for Web. Services environments Elisa Bertino 20
X-GTRBAC - why XML? XML - main benefits: u u Uniform, vendor-neutral representation of enterprise data Mechanism for interchange of information across heterogeneous systems Extensible syntax and semantics Widespread support from main platforms and tool vendors Elisa Bertino 21
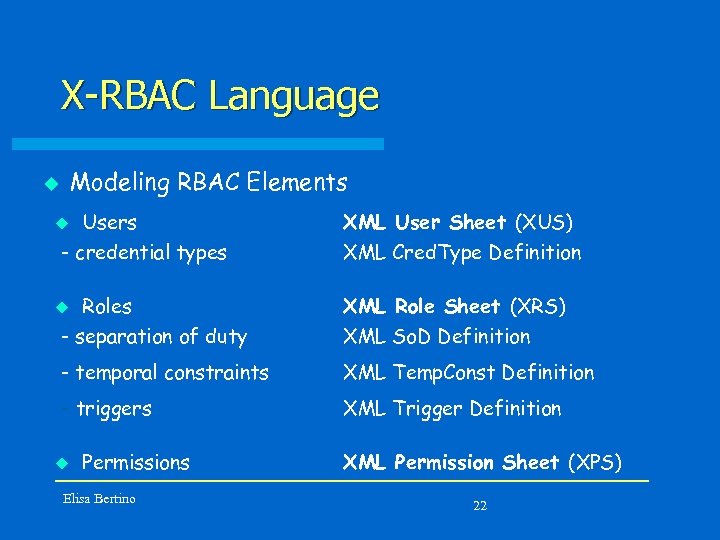
X-RBAC Language Modeling RBAC Elements u Users - credential types XML User Sheet (XUS) XML Cred. Type Definition Roles - separation of duty XML Role Sheet (XRS) XML So. D Definition - temporal constraints XML Temp. Const Definition - triggers XML Trigger Definition u u u Permissions Elisa Bertino XML Permission Sheet (XPS) 22
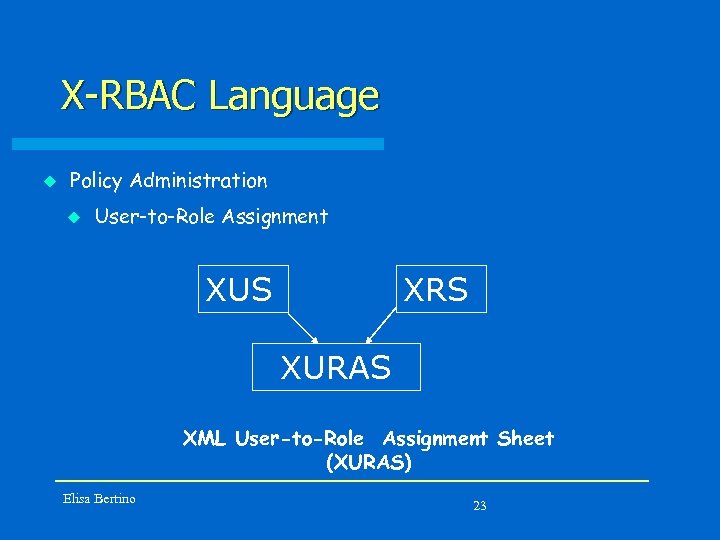
X-RBAC Language u Policy Administration u User-to-Role Assignment XUS XRS XURAS XML User-to-Role Assignment Sheet (XURAS) Elisa Bertino 23
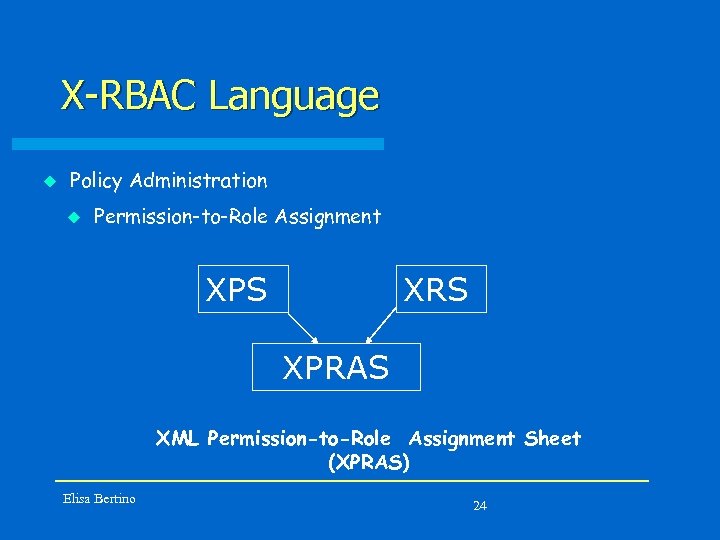
X-RBAC Language u Policy Administration u Permission-to-Role Assignment XPS XRS XPRAS XML Permission-to-Role Assignment Sheet (XPRAS) Elisa Bertino 24
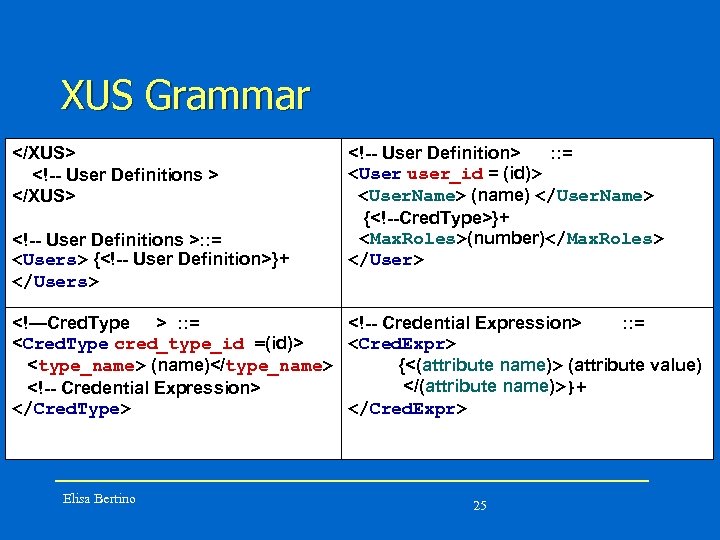
XUS Grammar </XUS> <!-- User Definitions >: : = <Users> {<!-- User Definition>}+ </Users> <!-- User Definition> : : = <User user_id = (id)> <User. Name> (name) </User. Name> {<!--Cred. Type>}+ <Max. Roles>(number)</Max. Roles> </User> <!—Cred. Type > : : = <!-- Credential Expression> : : = <Cred. Type cred_type_id =(id)> <Cred. Expr> <type_name> (name)</type_name> {<(attribute name)> (attribute value) </(attribute name)>}+ <!-- Credential Expression> </Cred. Expr> </Cred. Type> Elisa Bertino 25
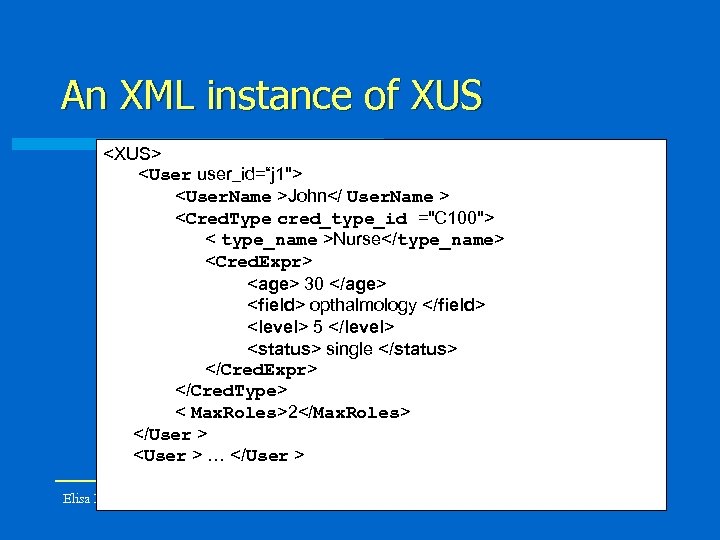
An XML instance of XUS <XUS> <User user_id=“j 1"> <User. Name >John</ User. Name > <Cred. Type cred_type_id ="C 100"> < type_name >Nurse</type_name> <Cred. Expr> <age> 30 </age> <field> opthalmology </field> <level> 5 </level> <status> single </status> </Cred. Expr> </Cred. Type> < Max. Roles>2</Max. Roles> </User > <User > … </User > …. Elisa Bertino </XUS> 26
![XRS Grammar <!-- XML Role Sheet> : : = <XRS [xrs_id = (id) ]> XRS Grammar <!-- XML Role Sheet> : : = <XRS [xrs_id = (id) ]>](https://present5.com/presentation/50c95d9d05f4026ae841cbd2d44f27e0/image-28.jpg)
XRS Grammar <!-- XML Role Sheet> : : = <XRS [xrs_id = (id) ]> {<!-- Role Definitions>}+ </XRS> Elisa Bertino <!-- Role Definitions> : : = <Roles> <Role role_id = (id) <Role. Name> (role name)> <Role. Name> [<!--{En|Dis}abling Constraint>] [<!--[De]Activation Constraint>] {<SSDRole. Set. ID> (id) </SSDRole. Set. ID>}* {<DSDRole. Set. ID> (id) </DSDRole. Set. ID>}* {<Junior> (name) </Junior>}* {<Senior> (name) </Senior>}* [<Cardinality>(number)</Cardinality>] </Role> <Role>. . </Role>. . <Roles> 27

An XML instance of XRS <XRS> <Roles > <Role role_id = "R 100"> <Role. Name> Nurse </ Role. Name > <Senior> Eye_Doctor </ Senior> <Cardinality> 8 </ Cardinality > </Role> <Role role_id = "R 200"> <Role. Name> Eye_Doctor </Role. Name> < DSDRole. Set. ID>DSD 1</ DSDRole. Set. ID > < Junior>Nurse</ Junior> <Senior> Eye_Surgeon </Senior> <Cardinality> 6 </Cardinality> </Roles> </XRS > Elisa Bertino 28
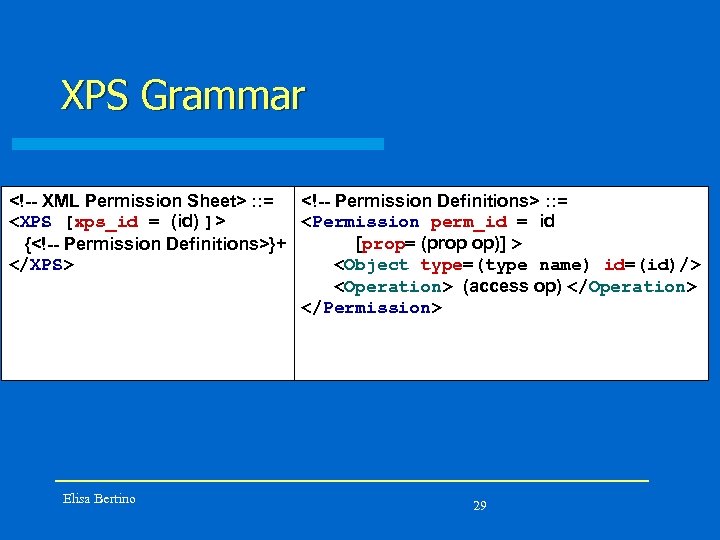
XPS Grammar <!-- XML Permission Sheet> : : = <!-- Permission Definitions> : : = <XPS [xps_id = (id) ]> <Permission perm_id = id [prop= (prop op)] > {<!-- Permission Definitions>}+ <Object type=(type name) id=(id)/> </XPS> <Operation> (access op) </Operation> </Permission> Elisa Bertino 29

An XML instance of XPS <XPS> <Permission perm_id ="P 1"> <Object type = “Schema” id = “XS 101” /> <Operation> all</operation> </Permission > <Permission perm_id ="P 2"> <Object type = “Instance” id = “XI 100” /> <Operation> all</operation> </Permission > <Permission perm_id ="P 3"> <Object type = “Element” id = “XE 100” /> <Operation> navigate </operation> </Permission > </XPS> Elisa Bertino 30

Example of XURAS <XURAS> <URA_id="URA 1"> <Role. Name> Eye_Doctor</ Role. Name> <Users> <User user_id=“s 1“ /> <User user_id=“s 2“ /> </Users > <Cred. Conditions> <Cred. Condition> <Cred. Type> Doctor </Cred. Type> <Logical. Expr op="AND"> <Predicate> <operator>eq</operator> <name_param>field</name_param> <value_param> Eye </value_param> </Predicate> <Logical. Expr op="OR"> Elisa Bertino <Predicate> <operator> lt </operator> <name_param> age </name_param> <value_param> 60 </value_param> </Predicate> <operator> gt </operator> <name_param> level </name_param> <value_param> 7 </value_param> </Predicate> </Logical. Expr > </Cred. Conditions > </URA> </XURAS> 31
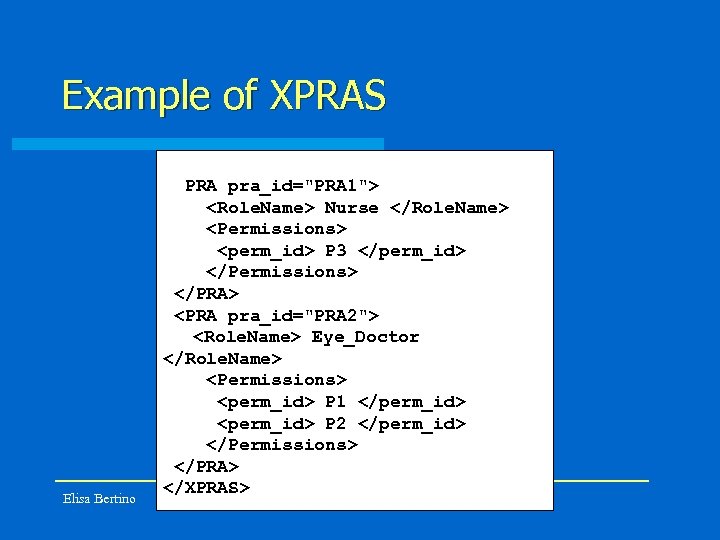
Example of XPRAS Elisa Bertino <XPRAS> <PRA pra_id="PRA 1"> <Role. Name> Nurse </Role. Name> <Permissions> <perm_id> P 3 </perm_id> </Permissions> </PRA> <PRA pra_id="PRA 2"> <Role. Name> Eye_Doctor </Role. Name> <Permissions> <perm_id> P 1 </perm_id> <perm_id> P 2 </perm_id> </Permissions> </PRA> </XPRAS> 32
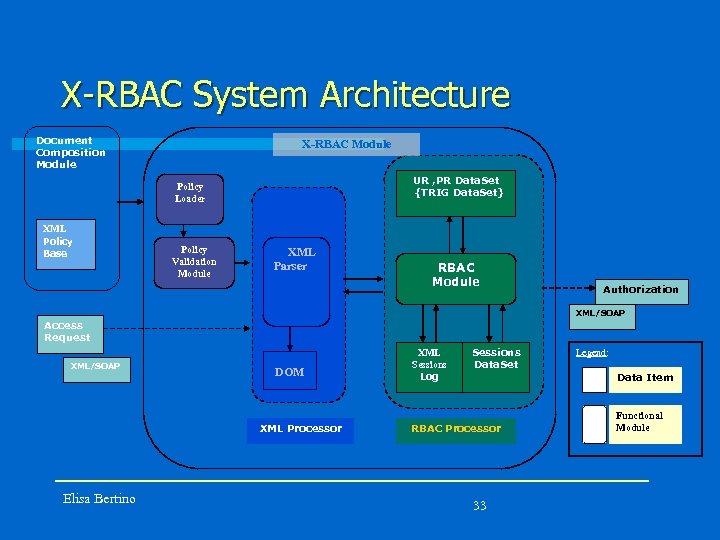
X-RBAC System Architecture Document Composition Module X-RBAC Module UR , PR Data. Set {TRIG Data. Set} Policy Loader XML Policy Base Policy Validation Module XML Parser RBAC Module Authorization XML/SOAP Access Request XML/SOAP DOM XML Processor Elisa Bertino XML Sessions Log Sessions Data. Set Legend: Data Item RBAC Processor 33 Functional Module

On-going Work u Extension of the constraint language í Constraints on the set of roles a user can activate Obbligations & Duties u Development of graphical tools for TRBAC administration u Testing on an Healthcare information system u Elisa Bertino 34
50c95d9d05f4026ae841cbd2d44f27e0.ppt