62cb51fd27f06df0889fb859cb5a5c5e.ppt
- Количество слайдов: 35
 Transmission Security Emission Security Tempest Raul Grajales
Transmission Security Emission Security Tempest Raul Grajales
 What Does It All Mean? w TRANSEC: Transmission Security – The component of communications security that results from the application of measures designed to protect transmissions from interception and exploitation by means other than cryptanalysis. w EMSEC: Emission Security – The protection resulting from all measures designed to deny unauthorized persons information of value that might be derived from intercept and analysis of compromising emanations from other than crypto-equipment and telecommunications systems. w TEMPEST: Transient Electromagnetic Pulse Emanation Standard – Is a U. S. government code word that identifies a classified set of standards for limiting electric or electromagnetic radiation emanations from electronic equipment. – It’s both a specification for equipment and a term used to describe the process for preventing compromising emanations.
What Does It All Mean? w TRANSEC: Transmission Security – The component of communications security that results from the application of measures designed to protect transmissions from interception and exploitation by means other than cryptanalysis. w EMSEC: Emission Security – The protection resulting from all measures designed to deny unauthorized persons information of value that might be derived from intercept and analysis of compromising emanations from other than crypto-equipment and telecommunications systems. w TEMPEST: Transient Electromagnetic Pulse Emanation Standard – Is a U. S. government code word that identifies a classified set of standards for limiting electric or electromagnetic radiation emanations from electronic equipment. – It’s both a specification for equipment and a term used to describe the process for preventing compromising emanations.
 TRANSEC w Refers To Not Only Obfuscating Data, But Hiding The Fact That It Even Exists w History: (In Ancient Times) – – – A messenger’s hair would be shaved Message would be tattooed onto the skull The hair would be allowed to grow back in Then the messenger was sent on his way The recipient would then shave the messenger again in order to retrieve the message
TRANSEC w Refers To Not Only Obfuscating Data, But Hiding The Fact That It Even Exists w History: (In Ancient Times) – – – A messenger’s hair would be shaved Message would be tattooed onto the skull The hair would be allowed to grow back in Then the messenger was sent on his way The recipient would then shave the messenger again in order to retrieve the message
 TRANSEC Transmission Security w TRANSEC does NOT involve Encryption – But How The Data Signal is Sent Out w Burst Sending Information – Use To Be Hard To Detect w Frequency – Frequency Modulation – Frequency Hopping – Spread Spectrum
TRANSEC Transmission Security w TRANSEC does NOT involve Encryption – But How The Data Signal is Sent Out w Burst Sending Information – Use To Be Hard To Detect w Frequency – Frequency Modulation – Frequency Hopping – Spread Spectrum
 Spread Spectrum History w Patented by – Hedy Lamaar – George Antheil • (1942) Scheme to control armed torpedoes over long distances without the enemy detecting them or jamming their transmissions w Spread Spectrum Used – 1962 – Secured communications during Cuban Missile Crisis – 1990’s – Used In Cellular Phones
Spread Spectrum History w Patented by – Hedy Lamaar – George Antheil • (1942) Scheme to control armed torpedoes over long distances without the enemy detecting them or jamming their transmissions w Spread Spectrum Used – 1962 – Secured communications during Cuban Missile Crisis – 1990’s – Used In Cellular Phones
 Low Observables w Low Probability of Detection (LPD) – Definition: there is a low probability that the opposition will be aware that there is any transmission • Examples: burst mode, frequency hopping, spread spectrum (when first introduced) w Low Probability of Interception (LPI) – Definition: there is a low probability that the opposition will be able to intercept (read) the data stream, even though they may be aware that there is a transmission • Examples: burst mode, frequency hopping, spread spectrum after better detection technologies were developed w Comments – Burst mode, frequency hopping, spread spectrum are all neither LPD or LPI in with today's technology – Multiple Input/Multiple Output (MIMO) is a current research area in LPD/LPI RF communications – LPD/LPI technology and detection technology is an ongoing "arms race"
Low Observables w Low Probability of Detection (LPD) – Definition: there is a low probability that the opposition will be aware that there is any transmission • Examples: burst mode, frequency hopping, spread spectrum (when first introduced) w Low Probability of Interception (LPI) – Definition: there is a low probability that the opposition will be able to intercept (read) the data stream, even though they may be aware that there is a transmission • Examples: burst mode, frequency hopping, spread spectrum after better detection technologies were developed w Comments – Burst mode, frequency hopping, spread spectrum are all neither LPD or LPI in with today's technology – Multiple Input/Multiple Output (MIMO) is a current research area in LPD/LPI RF communications – LPD/LPI technology and detection technology is an ongoing "arms race"
 EMSEC Emissions Security w Refers To Preventing A System From Being Attacked Using Compromising Emanations – Conducted Electromagnetic Signals – Radiated Electromagnetic Signals – Compromising Vibrations • Speech (Confidential)
EMSEC Emissions Security w Refers To Preventing A System From Being Attacked Using Compromising Emanations – Conducted Electromagnetic Signals – Radiated Electromagnetic Signals – Compromising Vibrations • Speech (Confidential)
 How Important Is It w Government – Spent As Much On EMSEC As It Has On Cryptography w Commercial World – Smart Card Security Set Back
How Important Is It w Government – Spent As Much On EMSEC As It Has On Cryptography w Commercial World – Smart Card Security Set Back
 History EMSEC w Crosstalk on Telephone Wires (1914) – Field Telephone wires usingle core insulated cable • Earth Leakage caused crosstalk including messages from enemy side. – 100 yards for telephony, 300 yards for Morse Code. • Listening Posts & Protective Measures Introduced w Smart Cards (1996) – Attacked by inserting glitches in power & clock lines – Crypto keys found by appropriate processing of precise measurements of the current drawn by the card
History EMSEC w Crosstalk on Telephone Wires (1914) – Field Telephone wires usingle core insulated cable • Earth Leakage caused crosstalk including messages from enemy side. – 100 yards for telephony, 300 yards for Morse Code. • Listening Posts & Protective Measures Introduced w Smart Cards (1996) – Attacked by inserting glitches in power & clock lines – Crypto keys found by appropriate processing of precise measurements of the current drawn by the card
 Common EMSEC Attacks w Most attacks are not those that exploit some unintended design feature of innocuous equipment – But those in which a custom-designed device is introduced by the attacker w Data That Is Captured By A Device – Not Secure, No Matter How Well Its Protected • Encryption & Access Controls – Subsequent Protective Measures Are NOT Likely To Help
Common EMSEC Attacks w Most attacks are not those that exploit some unintended design feature of innocuous equipment – But those in which a custom-designed device is introduced by the attacker w Data That Is Captured By A Device – Not Secure, No Matter How Well Its Protected • Encryption & Access Controls – Subsequent Protective Measures Are NOT Likely To Help
 EMSEC Attack Devices w Off The Shelf Mobile Radio Technology – Simple Radio Microphone – Radio Transmitting TV Camera w Exotic Devices – 1946 Class of school children presented a US ambassador with a wooden replica of the Great Seal of the US, and he hung it on the wall of the office in his residence – 1952 Found to contain a resonant cavity • Acted as a microphone when illuminated by microwaves from outside the building, and retransmitted the conversations – Embassies in Moscow were regularly irradiated with microwaves
EMSEC Attack Devices w Off The Shelf Mobile Radio Technology – Simple Radio Microphone – Radio Transmitting TV Camera w Exotic Devices – 1946 Class of school children presented a US ambassador with a wooden replica of the Great Seal of the US, and he hung it on the wall of the office in his residence – 1952 Found to contain a resonant cavity • Acted as a microphone when illuminated by microwaves from outside the building, and retransmitted the conversations – Embassies in Moscow were regularly irradiated with microwaves
 EMSEC Attack Devices w Laser Microphones – Work by shining a laser at a reflective surface where the target conversation is taking place – The sound waves modulate the reflected light which can be picked up and decoded at a distance w High-End Devices – Low Probability Of Intercept Radio Techniques such as frequency hopping and burst transmission. They can be turned on & off remotely. Harder to Find.
EMSEC Attack Devices w Laser Microphones – Work by shining a laser at a reflective surface where the target conversation is taking place – The sound waves modulate the reflected light which can be picked up and decoded at a distance w High-End Devices – Low Probability Of Intercept Radio Techniques such as frequency hopping and burst transmission. They can be turned on & off remotely. Harder to Find.
 Prevention Devices w Nonlinear Junction Detector – Device that can find hidden electronic equipment at close range w Surveillance Receivers – Sweep 10 k. Hz-3 GHz Look for signals that cant be explained as broadcast, police, air traffic control, etc. w Electromagnetic Shielding – Double Pane Windows To Prevent Laser Microphones
Prevention Devices w Nonlinear Junction Detector – Device that can find hidden electronic equipment at close range w Surveillance Receivers – Sweep 10 k. Hz-3 GHz Look for signals that cant be explained as broadcast, police, air traffic control, etc. w Electromagnetic Shielding – Double Pane Windows To Prevent Laser Microphones
 Prevention Devices Where Does It End? w Greater scope of attack as equipment begins to contains more features – Cordless phones are easy to eavesdrop – PBX can be reprogrammed to support surveillance – Laptops with microphones can record messages in a room and email them to the attacker
Prevention Devices Where Does It End? w Greater scope of attack as equipment begins to contains more features – Cordless phones are easy to eavesdrop – PBX can be reprogrammed to support surveillance – Laptops with microphones can record messages in a room and email them to the attacker
 *EMSEC ALERT ØFurby Remembers & Randomly Repeats Things Said In Its Presence
*EMSEC ALERT ØFurby Remembers & Randomly Repeats Things Said In Its Presence
 Type of EMSEC Attacks w Passive Attacks – Attacks in which the opponent makes use of whatever electromagnetic signals are presented to him without any effort to create • Hijack – conducted over a circuit – Power Line Or Phone Line • Tempest – radiated as a radio frequency energy – Electromagnetic Eavesdropping w Active Attacks – Disruptive Electromagnetic Attacks
Type of EMSEC Attacks w Passive Attacks – Attacks in which the opponent makes use of whatever electromagnetic signals are presented to him without any effort to create • Hijack – conducted over a circuit – Power Line Or Phone Line • Tempest – radiated as a radio frequency energy – Electromagnetic Eavesdropping w Active Attacks – Disruptive Electromagnetic Attacks
 Passive Attacks w Leakage through Power & Signal Cables – Red/Black Separation • Red equipment (carrying confidential data such as plaintext) has to be isolated by filters and shields from Black equipment (which can send signals directly to the outside world) • Red/Black Cipher Machines must meet standards for emission security (Tempest-Protected Systems) – NACISM 5100 A, NATO AMSG 720 B – Power Analysis, Rail Noise Analysis • Measure current drawn from power supply of Smart. Cards – Can Deduce Key If Knows The Smart. Card Design
Passive Attacks w Leakage through Power & Signal Cables – Red/Black Separation • Red equipment (carrying confidential data such as plaintext) has to be isolated by filters and shields from Black equipment (which can send signals directly to the outside world) • Red/Black Cipher Machines must meet standards for emission security (Tempest-Protected Systems) – NACISM 5100 A, NATO AMSG 720 B – Power Analysis, Rail Noise Analysis • Measure current drawn from power supply of Smart. Cards – Can Deduce Key If Knows The Smart. Card Design
 Passive Attacks w Leakage through RF Signals – IBM machine with a 1. 5 MHz clock & Radio Tuned to this frequency creates a loud whistle – Video Display Units emit a weak TV signal • A VHF/UHF radio signal modulated with a distorted version of the image currently being displayed • Contrary to popular belief, LCD displays are also generally easy for an eavesdropper
Passive Attacks w Leakage through RF Signals – IBM machine with a 1. 5 MHz clock & Radio Tuned to this frequency creates a loud whistle – Video Display Units emit a weak TV signal • A VHF/UHF radio signal modulated with a distorted version of the image currently being displayed • Contrary to popular belief, LCD displays are also generally easy for an eavesdropper
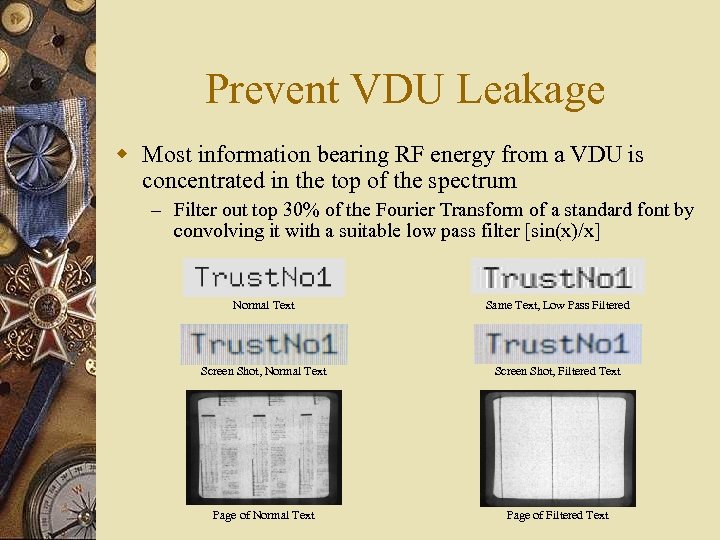 Prevent VDU Leakage w Most information bearing RF energy from a VDU is concentrated in the top of the spectrum – Filter out top 30% of the Fourier Transform of a standard font by convolving it with a suitable low pass filter [sin(x)/x] Normal Text Same Text, Low Pass Filtered Screen Shot, Normal Text Screen Shot, Filtered Text Page of Normal Text Page of Filtered Text
Prevent VDU Leakage w Most information bearing RF energy from a VDU is concentrated in the top of the spectrum – Filter out top 30% of the Fourier Transform of a standard font by convolving it with a suitable low pass filter [sin(x)/x] Normal Text Same Text, Low Pass Filtered Screen Shot, Normal Text Screen Shot, Filtered Text Page of Normal Text Page of Filtered Text
 Active Attacks w Tempest Viruses w Nonstop w Glitching w Differential Fault Analysis w Combination Attacks w Commercial Exploitation
Active Attacks w Tempest Viruses w Nonstop w Glitching w Differential Fault Analysis w Combination Attacks w Commercial Exploitation
 Active Attacks w Tempest Viruses – Software-Based RF exploits • Virus infects a computer and makes it transmit secret data to a radio receiver hidden nearby. w Nonstop – Exploitation of RF emanations that are accidentally induced by nearby radio transmitters & other RF sources • Phone’s transmitter may induce currents that get modulated with sensitive data by the nonlinear junction effect and reradiated • Mobile Phones banned within 5 meters of classified equipment
Active Attacks w Tempest Viruses – Software-Based RF exploits • Virus infects a computer and makes it transmit secret data to a radio receiver hidden nearby. w Nonstop – Exploitation of RF emanations that are accidentally induced by nearby radio transmitters & other RF sources • Phone’s transmitter may induce currents that get modulated with sensitive data by the nonlinear junction effect and reradiated • Mobile Phones banned within 5 meters of classified equipment
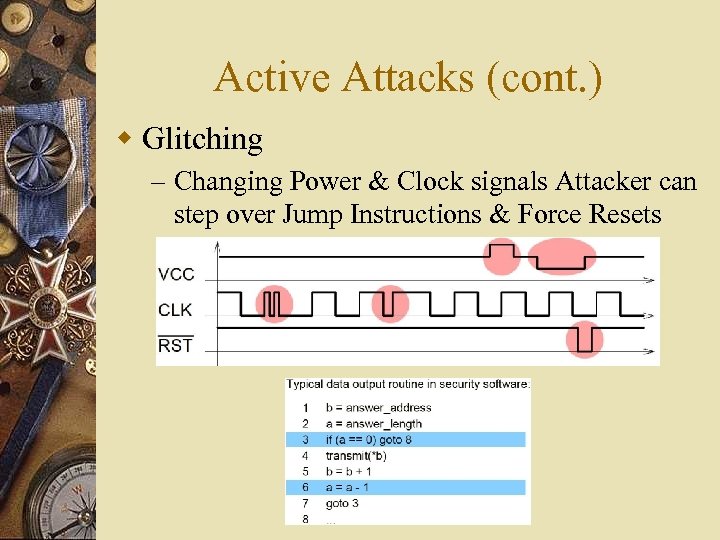 Active Attacks (cont. ) w Glitching – Changing Power & Clock signals Attacker can step over Jump Instructions & Force Resets
Active Attacks (cont. ) w Glitching – Changing Power & Clock signals Attacker can step over Jump Instructions & Force Resets
 Active Attacks (cont. ) w Differential Fault Analysis – RSA Cards that aren’t protected against glitches – S = h(m)d (mod pq) carried out mod p then mod q • If card returns defective signature (Sp) which is correct modulo p but incorrect modulo q then we have: Ø p = gcd(pq, Spe – h(m)) Breaks System w Combination Attacks – Active & Passive attacks • If PIN incorrect decrements counter which writes to EEPROM • Current consumed by card rises measurably w Commercial Exploitation – SFX Entertainment monitors what customers are playing on their car radios
Active Attacks (cont. ) w Differential Fault Analysis – RSA Cards that aren’t protected against glitches – S = h(m)d (mod pq) carried out mod p then mod q • If card returns defective signature (Sp) which is correct modulo p but incorrect modulo q then we have: Ø p = gcd(pq, Spe – h(m)) Breaks System w Combination Attacks – Active & Passive attacks • If PIN incorrect decrements counter which writes to EEPROM • Current consumed by card rises measurably w Commercial Exploitation – SFX Entertainment monitors what customers are playing on their car radios
 TEMPEST Transient Electromagnetic Pulse Emanation Standard w During the 1950's, the government became concerned that emanations could be captured and then reconstructed – What Are Important Emanations • Blender Vs. Electric Encryption Device – Emanations can be recorded, interpreted, and then played back on a similar device • Reveal the contents of an encrypted message (Smart Card) – Research showed it was possible to capture emanations from a distance • The TEMPEST program was started
TEMPEST Transient Electromagnetic Pulse Emanation Standard w During the 1950's, the government became concerned that emanations could be captured and then reconstructed – What Are Important Emanations • Blender Vs. Electric Encryption Device – Emanations can be recorded, interpreted, and then played back on a similar device • Reveal the contents of an encrypted message (Smart Card) – Research showed it was possible to capture emanations from a distance • The TEMPEST program was started
 Tempest Purpose w Introduce standards that would reduce the chances of “leakage” on devices used to: – Process, Transmit, or Store Sensitive Information • TEMPEST computers and peripherals (printers, scanners, tape drives, mice, etc. ) are used by government agencies and contractors to protect data from emanations monitoring. • Shielding the device (or sometimes a room or entire building) with copper or other conductive materials. • Active measures for “Jamming” electromagnetic signals.
Tempest Purpose w Introduce standards that would reduce the chances of “leakage” on devices used to: – Process, Transmit, or Store Sensitive Information • TEMPEST computers and peripherals (printers, scanners, tape drives, mice, etc. ) are used by government agencies and contractors to protect data from emanations monitoring. • Shielding the device (or sometimes a room or entire building) with copper or other conductive materials. • Active measures for “Jamming” electromagnetic signals.
 Tempest History w The original 1950 s emanations standard was called NAG 1 A. w During the 1960 s it was revised and reissued as FS 222 and later FS 222 A. w In 1970 the standard was significantly revised and published as National Communications Security Information Memorandum 5100 (Directive on TEMPEST Security) – Also known as NACSIM 5100 – This was again revised in 1974
Tempest History w The original 1950 s emanations standard was called NAG 1 A. w During the 1960 s it was revised and reissued as FS 222 and later FS 222 A. w In 1970 the standard was significantly revised and published as National Communications Security Information Memorandum 5100 (Directive on TEMPEST Security) – Also known as NACSIM 5100 – This was again revised in 1974
 Tempest History (cont. ) w Current national TEMPEST policy is set in National Communications Security Committee Directive 4, dated January 16, 1981 – Instructs federal agencies to protect classified information against compromising emanations – This document is known as NACSIM 5100 A and is classified w The National Communications Security Instruction (NACSI) 5004 (classified Secret) – Published in January 1984 – Provides procedures for departments and agencies to use in determining the safeguards needed for equipment and facilities which process national security information in the United States
Tempest History (cont. ) w Current national TEMPEST policy is set in National Communications Security Committee Directive 4, dated January 16, 1981 – Instructs federal agencies to protect classified information against compromising emanations – This document is known as NACSIM 5100 A and is classified w The National Communications Security Instruction (NACSI) 5004 (classified Secret) – Published in January 1984 – Provides procedures for departments and agencies to use in determining the safeguards needed for equipment and facilities which process national security information in the United States
 Tempest History (cont. ) w National Security Decision Directive 145, dated September 17, 1984, designates the National Security Agency (NSA) as the focal point and national manager for the security of government telecommunications and Automated Information Systems (AISs). w NSA is authorized to review and approve all standards, techniques, systems and equipment for AIS security, including TEMPEST. – In this role, NSA makes recommendations to the National Telecommunications and Information Systems Security Committee for changes in TEMPEST polices and guidance.
Tempest History (cont. ) w National Security Decision Directive 145, dated September 17, 1984, designates the National Security Agency (NSA) as the focal point and national manager for the security of government telecommunications and Automated Information Systems (AISs). w NSA is authorized to review and approve all standards, techniques, systems and equipment for AIS security, including TEMPEST. – In this role, NSA makes recommendations to the National Telecommunications and Information Systems Security Committee for changes in TEMPEST polices and guidance.
 Product Cycle TEMPEST Certified w Information Systems need to meet certain specifications as required by national TEMPEST policies and procedures w Objective is to minimize the risk of Hostile Intelligence Services (HOIS) exploiting unintentional emanations from intelligence systems CONCEPTS DEVELOPMENT PHASE NO DESIGN PHASE YES DEVELOPMENT PHASE YES DEPLOYMENT PHASE YES OPERATIONS PHASE YES RECERTIFICATION PHASE YES DISPOSAL PHASE YES
Product Cycle TEMPEST Certified w Information Systems need to meet certain specifications as required by national TEMPEST policies and procedures w Objective is to minimize the risk of Hostile Intelligence Services (HOIS) exploiting unintentional emanations from intelligence systems CONCEPTS DEVELOPMENT PHASE NO DESIGN PHASE YES DEVELOPMENT PHASE YES DEPLOYMENT PHASE YES OPERATIONS PHASE YES RECERTIFICATION PHASE YES DISPOSAL PHASE YES
 Certified TEMPEST Technical Authority (CTTA) w An experienced, technically qualified U. S. Government employee who has met established certification requirements in accordance with: – National Security Telecommunications Information Systems Security Committee (NSTISSC) approved criteria • Appointed by a U. S. Government Department or Agency to fulfill CTTA responsibilities.
Certified TEMPEST Technical Authority (CTTA) w An experienced, technically qualified U. S. Government employee who has met established certification requirements in accordance with: – National Security Telecommunications Information Systems Security Committee (NSTISSC) approved criteria • Appointed by a U. S. Government Department or Agency to fulfill CTTA responsibilities.
 INSTALLATION REQUIREMENTS w All computer equipment and peripherals must meet the requirements of National Security Telecommunications Information Systems Security Advisory Memorandum (NSTISSAM) TEMPEST/1 -92 and be installed IAW NSTISSAM TEMPEST/2 -95, – RED/BLACK separation criteria or as determined by a CTTA. The local TEMPEST Manager will oversee all such installations and coordinate on all accreditation documents resulting from the installation. w Use All Equipment As Intended. – All TEMPEST access doors, covers, and plates must be closed and fastened. Unauthorized modifications, even for testing purposes, are strictly forbidden.
INSTALLATION REQUIREMENTS w All computer equipment and peripherals must meet the requirements of National Security Telecommunications Information Systems Security Advisory Memorandum (NSTISSAM) TEMPEST/1 -92 and be installed IAW NSTISSAM TEMPEST/2 -95, – RED/BLACK separation criteria or as determined by a CTTA. The local TEMPEST Manager will oversee all such installations and coordinate on all accreditation documents resulting from the installation. w Use All Equipment As Intended. – All TEMPEST access doors, covers, and plates must be closed and fastened. Unauthorized modifications, even for testing purposes, are strictly forbidden.
 INSTALLATION REQUIREMENTS (cont. ) w Additional TEMPEST requirements may exist if the equipment is not TEMPEST approved – In such a case, your local TEMPEST Manager should be contacted for further guidance. w The local TEMPEST Manager must inspect all equipment installations.
INSTALLATION REQUIREMENTS (cont. ) w Additional TEMPEST requirements may exist if the equipment is not TEMPEST approved – In such a case, your local TEMPEST Manager should be contacted for further guidance. w The local TEMPEST Manager must inspect all equipment installations.
 INSTALLATION REQUIREMENTS (cont. ) w Special prohibitions and installation requirements exist for all transmitters, modems, and other networking and communications devices or equipment. – Because of the broad range of this category, coordinate all requests for these devices with your local TEMPEST Manager. w Do not consider a RED IS for any network which has any direct connection to a BLACK IS or other communications medium such as administrative telephone lines except through an approved cryptographic device.
INSTALLATION REQUIREMENTS (cont. ) w Special prohibitions and installation requirements exist for all transmitters, modems, and other networking and communications devices or equipment. – Because of the broad range of this category, coordinate all requests for these devices with your local TEMPEST Manager. w Do not consider a RED IS for any network which has any direct connection to a BLACK IS or other communications medium such as administrative telephone lines except through an approved cryptographic device.
 INSTALLATION REQUIREMENTS (cont. ) w Do not use acoustically coupled modems and transmitters or locate them in any secure area without specific written approval from your Designated Approving Authority (DAA). w You may use non-acoustic wire line modems with stand-alone, dedicated BLACK ISs providing that all appropriate telephone security requirements are met, consult with your local TEMPEST Manager.
INSTALLATION REQUIREMENTS (cont. ) w Do not use acoustically coupled modems and transmitters or locate them in any secure area without specific written approval from your Designated Approving Authority (DAA). w You may use non-acoustic wire line modems with stand-alone, dedicated BLACK ISs providing that all appropriate telephone security requirements are met, consult with your local TEMPEST Manager.
 Conclusion w Questions? ? ?
Conclusion w Questions? ? ?


