9475602b3d1f306065fd5bee090abbb9.ppt
- Количество слайдов: 20
 Transaction Flow end-end
Transaction Flow end-end
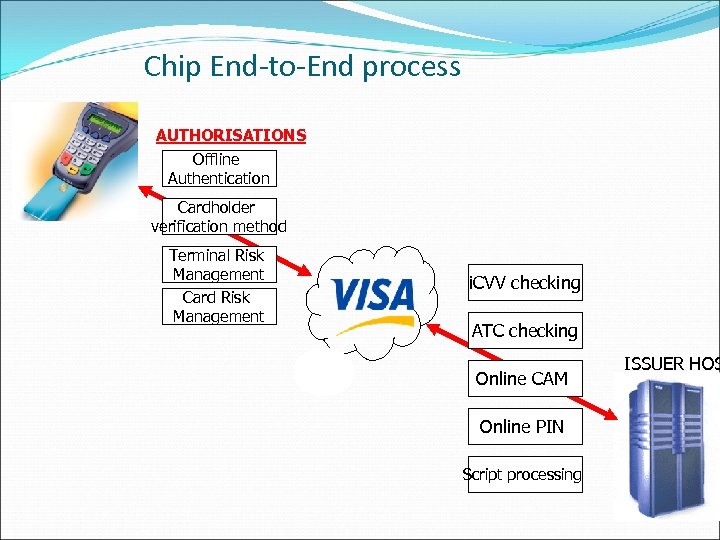 Chip End-to-End process AUTHORISATIONS Offline Authentication Cardholder verification method Terminal Risk Management Card Risk Management i. CVV checking ATC checking Online CAM Online PIN Script processing ISSUER HOS
Chip End-to-End process AUTHORISATIONS Offline Authentication Cardholder verification method Terminal Risk Management Card Risk Management i. CVV checking ATC checking Online CAM Online PIN Script processing ISSUER HOS
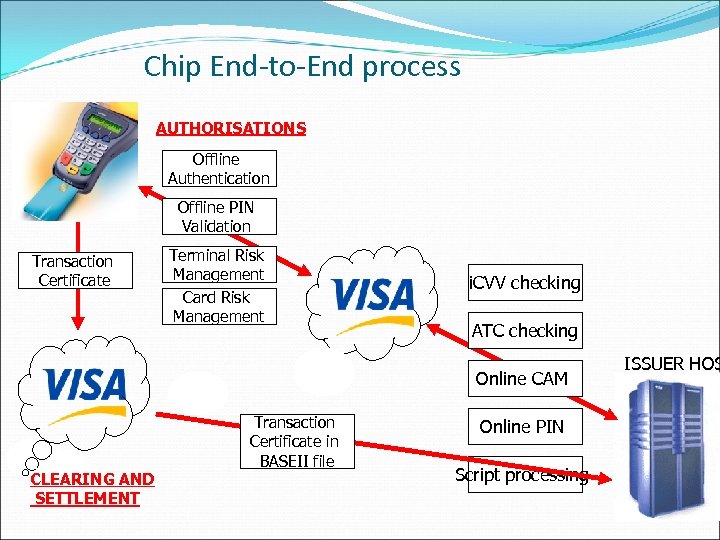 Chip End-to-End process AUTHORISATIONS Offline Authentication Offline PIN Validation Transaction Certificate Terminal Risk Management Card Risk Management i. CVV checking ATC checking Online CAM CLEARING AND SETTLEMENT Transaction Certificate in BASEII file Online PIN Script processing ISSUER HOS
Chip End-to-End process AUTHORISATIONS Offline Authentication Offline PIN Validation Transaction Certificate Terminal Risk Management Card Risk Management i. CVV checking ATC checking Online CAM CLEARING AND SETTLEMENT Transaction Certificate in BASEII file Online PIN Script processing ISSUER HOS
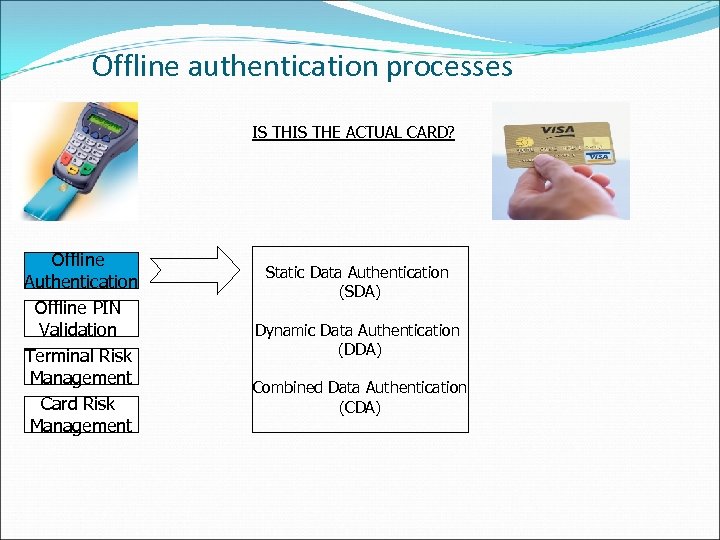 Offline authentication processes IS THE ACTUAL CARD? Offline Authentication Offline PIN Validation Terminal Risk Management Card Risk Management Static Data Authentication (SDA) Dynamic Data Authentication (DDA) Combined Data Authentication (CDA)
Offline authentication processes IS THE ACTUAL CARD? Offline Authentication Offline PIN Validation Terminal Risk Management Card Risk Management Static Data Authentication (SDA) Dynamic Data Authentication (DDA) Combined Data Authentication (CDA)
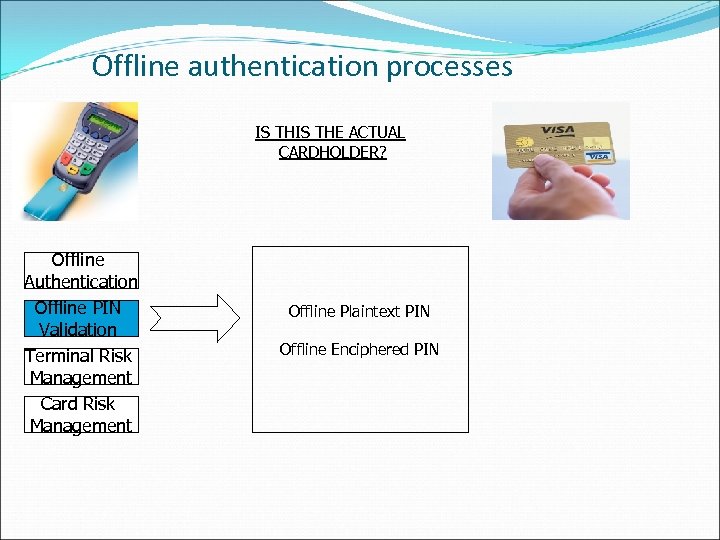 Offline authentication processes IS THE ACTUAL CARDHOLDER? Offline Authentication Offline PIN Validation Terminal Risk Management Card Risk Management Offline Plaintext PIN Offline Enciphered PIN
Offline authentication processes IS THE ACTUAL CARDHOLDER? Offline Authentication Offline PIN Validation Terminal Risk Management Card Risk Management Offline Plaintext PIN Offline Enciphered PIN
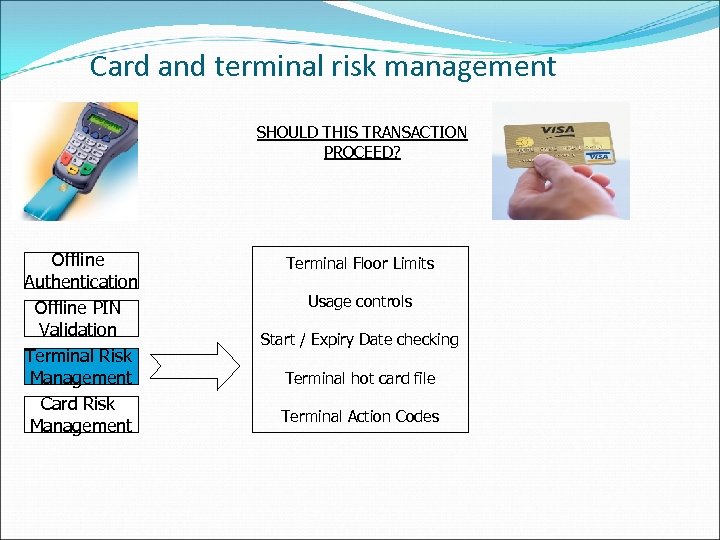 Card and terminal risk management SHOULD THIS TRANSACTION PROCEED? Offline Authentication Offline PIN Validation Terminal Risk Management Card Risk Management Terminal Floor Limits Usage controls Start / Expiry Date checking Terminal hot card file Terminal Action Codes
Card and terminal risk management SHOULD THIS TRANSACTION PROCEED? Offline Authentication Offline PIN Validation Terminal Risk Management Card Risk Management Terminal Floor Limits Usage controls Start / Expiry Date checking Terminal hot card file Terminal Action Codes
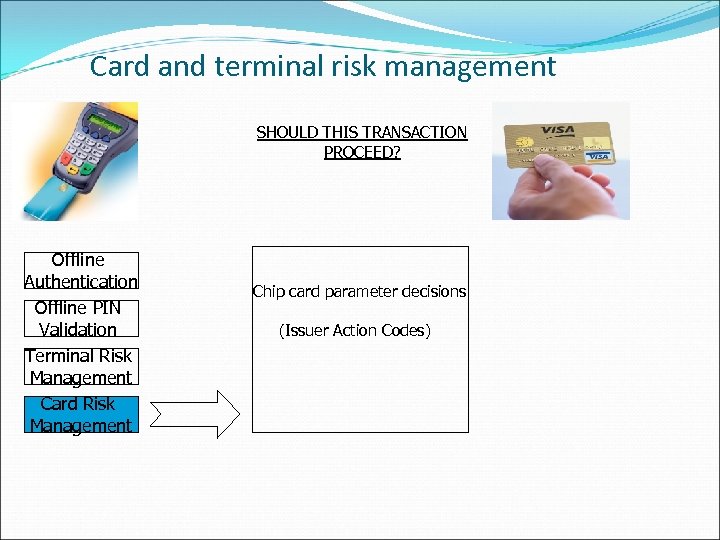 Card and terminal risk management SHOULD THIS TRANSACTION PROCEED? Offline Authentication Offline PIN Validation Terminal Risk Management Card Risk Management Chip card parameter decisions (Issuer Action Codes)
Card and terminal risk management SHOULD THIS TRANSACTION PROCEED? Offline Authentication Offline PIN Validation Terminal Risk Management Card Risk Management Chip card parameter decisions (Issuer Action Codes)
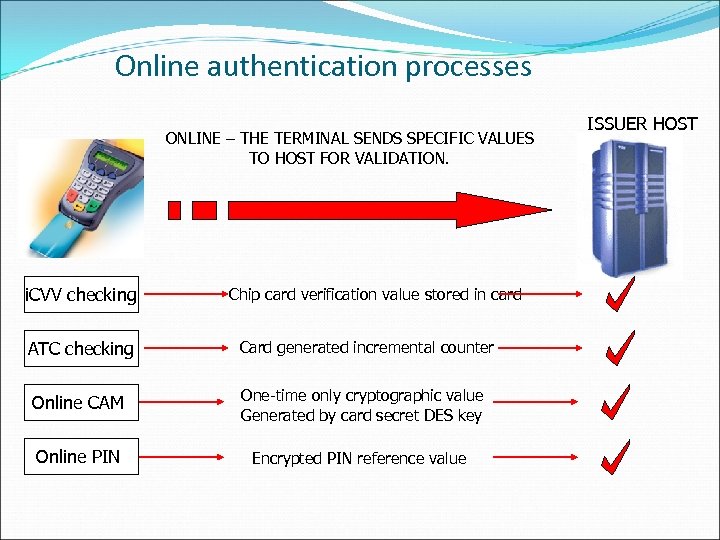 Online authentication processes ONLINE – THE TERMINAL SENDS SPECIFIC VALUES TO HOST FOR VALIDATION. i. CVV checking Chip card verification value stored in card ATC checking Card generated incremental counter Online CAM One-time only cryptographic value Generated by card secret DES key Online PIN Encrypted PIN reference value ISSUER HOST
Online authentication processes ONLINE – THE TERMINAL SENDS SPECIFIC VALUES TO HOST FOR VALIDATION. i. CVV checking Chip card verification value stored in card ATC checking Card generated incremental counter Online CAM One-time only cryptographic value Generated by card secret DES key Online PIN Encrypted PIN reference value ISSUER HOST
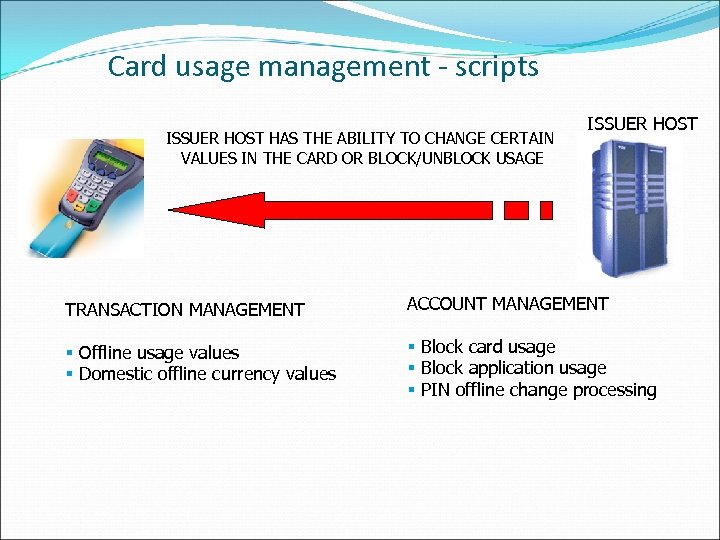 Card usage management - scripts ISSUER HOST HAS THE ABILITY TO CHANGE CERTAIN VALUES IN THE CARD OR BLOCK/UNBLOCK USAGE ISSUER HOST TRANSACTION MANAGEMENT ACCOUNT MANAGEMENT § Offline usage values § Domestic offline currency values § Block card usage § Block application usage § PIN offline change processing
Card usage management - scripts ISSUER HOST HAS THE ABILITY TO CHANGE CERTAIN VALUES IN THE CARD OR BLOCK/UNBLOCK USAGE ISSUER HOST TRANSACTION MANAGEMENT ACCOUNT MANAGEMENT § Offline usage values § Domestic offline currency values § Block card usage § Block application usage § PIN offline change processing
 Guidelines to PKI cryptography § EMV Offline Authentication uses Public Key Infrastructure (PKI) based on Rivest Shamir and Alderman (RSA) cryptography § Made up of Key pairs. Private and Public § Private must be kept secret to the owner (Visa, Issuer, Card) § Public is available to anybody § Sign and verify concept – Secretly sign something with your private key which can be verified with your public key § One way conversation only § Used for SDA, DDA and CDA Offline Authentication
Guidelines to PKI cryptography § EMV Offline Authentication uses Public Key Infrastructure (PKI) based on Rivest Shamir and Alderman (RSA) cryptography § Made up of Key pairs. Private and Public § Private must be kept secret to the owner (Visa, Issuer, Card) § Public is available to anybody § Sign and verify concept – Secretly sign something with your private key which can be verified with your public key § One way conversation only § Used for SDA, DDA and CDA Offline Authentication
 Guidelines to PKI cryptography § Within EMV, certificates are produced by signing data with Private Keys § Validation and retrieval of data is performed in public with the corresponding Public Key § Complex algorithm based on prime number calculations § Current key lengths are 1920 and 2048 bits Offline Authentication
Guidelines to PKI cryptography § Within EMV, certificates are produced by signing data with Private Keys § Validation and retrieval of data is performed in public with the corresponding Public Key § Complex algorithm based on prime number calculations § Current key lengths are 1920 and 2048 bits Offline Authentication
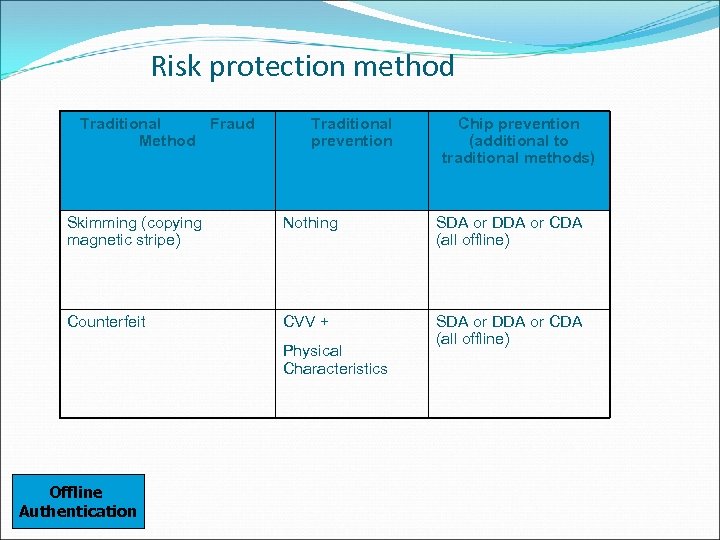 Risk protection method Traditional Fraud Method Traditional prevention Chip prevention (additional to traditional methods) Skimming (copying magnetic stripe) Nothing SDA or DDA or CDA (all offline) Counterfeit CVV + SDA or DDA or CDA (all offline) Physical Characteristics Offline Authentication
Risk protection method Traditional Fraud Method Traditional prevention Chip prevention (additional to traditional methods) Skimming (copying magnetic stripe) Nothing SDA or DDA or CDA (all offline) Counterfeit CVV + SDA or DDA or CDA (all offline) Physical Characteristics Offline Authentication
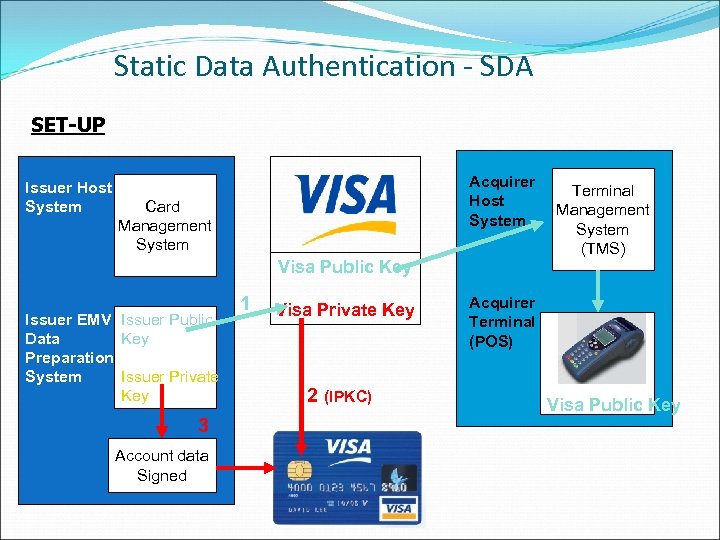 Static Data Authentication - SDA SET-UP Issuer Host System Acquirer Host System Card Management System Visa Public Key Issuer EMV Issuer Public Key Data Preparation Issuer Private System Key 3 Account data Signed 1 Visa Private Key 2 (IPKC) Terminal Management System (TMS) Acquirer Terminal (POS) Visa Public Key
Static Data Authentication - SDA SET-UP Issuer Host System Acquirer Host System Card Management System Visa Public Key Issuer EMV Issuer Public Key Data Preparation Issuer Private System Key 3 Account data Signed 1 Visa Private Key 2 (IPKC) Terminal Management System (TMS) Acquirer Terminal (POS) Visa Public Key
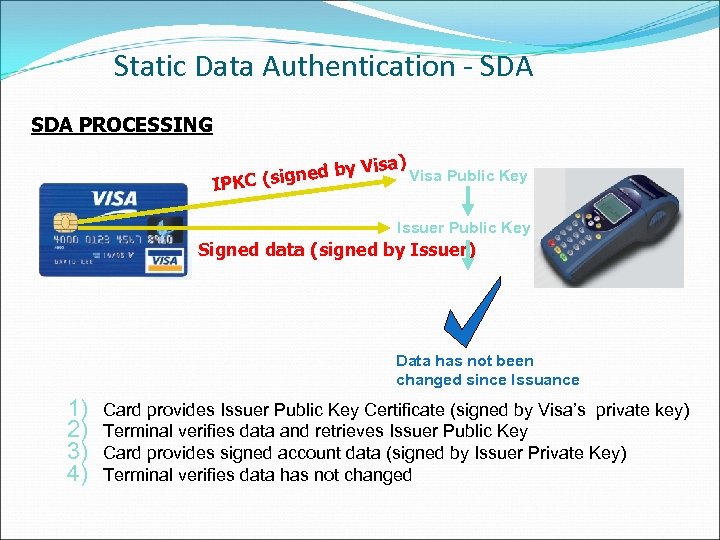 Static Data Authentication - SDA PROCESSING by C (signed IPK Visa) Visa Public Key Issuer Public Key Signed data (signed by Issuer) Data has not been changed since Issuance 1) 2) 3) 4) Card provides Issuer Public Key Certificate (signed by Visa’s private key) Terminal verifies data and retrieves Issuer Public Key Card provides signed account data (signed by Issuer Private Key) Terminal verifies data has not changed
Static Data Authentication - SDA PROCESSING by C (signed IPK Visa) Visa Public Key Issuer Public Key Signed data (signed by Issuer) Data has not been changed since Issuance 1) 2) 3) 4) Card provides Issuer Public Key Certificate (signed by Visa’s private key) Terminal verifies data and retrieves Issuer Public Key Card provides signed account data (signed by Issuer Private Key) Terminal verifies data has not changed
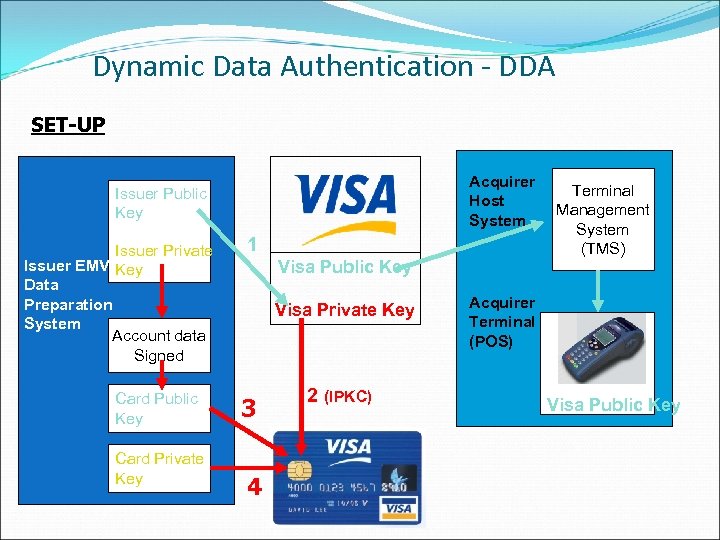 Dynamic Data Authentication - DDA SET-UP Acquirer Host System Issuer Public Key Issuer Private Issuer EMV Key Data Preparation System Account data Signed Card Public Key Card Private Key 1 Visa Public Key Visa Private Key 3 4 2 (IPKC) Terminal Management System (TMS) Acquirer Terminal (POS) Visa Public Key
Dynamic Data Authentication - DDA SET-UP Acquirer Host System Issuer Public Key Issuer Private Issuer EMV Key Data Preparation System Account data Signed Card Public Key Card Private Key 1 Visa Public Key Visa Private Key 3 4 2 (IPKC) Terminal Management System (TMS) Acquirer Terminal (POS) Visa Public Key
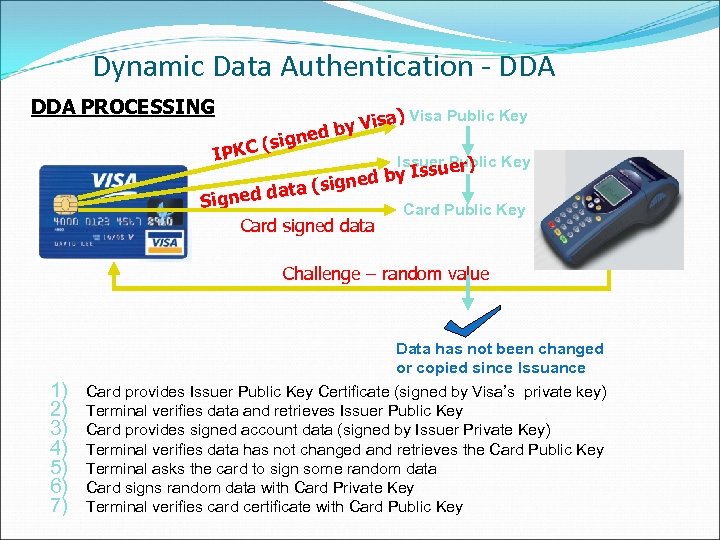 Dynamic Data Authentication - DDA PROCESSING sig ( IPKC sa) Visa Public Key Vi d by ne Issuer Public Key uer) ed by ta (sign a d Signed Card signed data Iss Card Public Key Challenge – random value 1) 2) 3) 4) 5) 6) 7) Data has not been changed or copied since Issuance Card provides Issuer Public Key Certificate (signed by Visa’s private key) Terminal verifies data and retrieves Issuer Public Key Card provides signed account data (signed by Issuer Private Key) Terminal verifies data has not changed and retrieves the Card Public Key Terminal asks the card to sign some random data Card signs random data with Card Private Key Terminal verifies card certificate with Card Public Key
Dynamic Data Authentication - DDA PROCESSING sig ( IPKC sa) Visa Public Key Vi d by ne Issuer Public Key uer) ed by ta (sign a d Signed Card signed data Iss Card Public Key Challenge – random value 1) 2) 3) 4) 5) 6) 7) Data has not been changed or copied since Issuance Card provides Issuer Public Key Certificate (signed by Visa’s private key) Terminal verifies data and retrieves Issuer Public Key Card provides signed account data (signed by Issuer Private Key) Terminal verifies data has not changed and retrieves the Card Public Key Terminal asks the card to sign some random data Card signs random data with Card Private Key Terminal verifies card certificate with Card Public Key
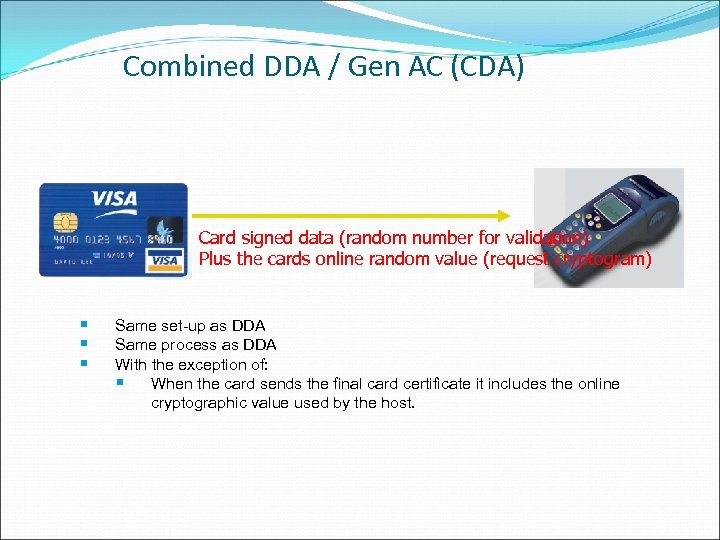 Combined DDA / Gen AC (CDA) Card signed data (random number for validation) Plus the cards online random value (request cryptogram) § § § Same set-up as DDA Same process as DDA With the exception of: § When the card sends the final card certificate it includes the online cryptographic value used by the host.
Combined DDA / Gen AC (CDA) Card signed data (random number for validation) Plus the cards online random value (request cryptogram) § § § Same set-up as DDA Same process as DDA With the exception of: § When the card sends the final card certificate it includes the online cryptographic value used by the host.
 Considerations § Q - Is there an effective offline authentication process within magnetic stripe processing ? § A - No § Q -Is SDA more secure than magnetic stripe? § A - Yes § Q – Is DDA more secure than SDA? § A - Yes § Q – Is CDA more secure than DDA? § A – Yes § HOWEVER, CDA may not be the best solution for your market just because it is the most secure. We have to consider where we are and where we are going!
Considerations § Q - Is there an effective offline authentication process within magnetic stripe processing ? § A - No § Q -Is SDA more secure than magnetic stripe? § A - Yes § Q – Is DDA more secure than SDA? § A - Yes § Q – Is CDA more secure than DDA? § A – Yes § HOWEVER, CDA may not be the best solution for your market just because it is the most secure. We have to consider where we are and where we are going!
 Summary § All processes (SDA, DDA, CDA) are skimming and counterfeit protection measures § SDA is the cheapest (no need for a card crypto-processor) § DDA and CDA require a card that can perform RSA cryptography § Visa mandates SDA on all cards § When choosing a method you should consider all functions of the card and likelyhood of a full compromise that can not be detected. Such as (Offline PIN, Online cryptography, Acquirer market floor limits, card terminal risk management)
Summary § All processes (SDA, DDA, CDA) are skimming and counterfeit protection measures § SDA is the cheapest (no need for a card crypto-processor) § DDA and CDA require a card that can perform RSA cryptography § Visa mandates SDA on all cards § When choosing a method you should consider all functions of the card and likelyhood of a full compromise that can not be detected. Such as (Offline PIN, Online cryptography, Acquirer market floor limits, card terminal risk management)
 Areas that Combat Fraud ATC Checking CVM Usage DDA or CDA Scripts
Areas that Combat Fraud ATC Checking CVM Usage DDA or CDA Scripts


