270449683d24afdd689fea69802309ea.ppt
- Количество слайдов: 64

Total Discovery Log Analysis Training James T. Bennett, 9/17/07

RUNNING HEADER, 14 PT. , ALL CAPS, Line Spacing=1 line · TD Log Concepts 1. 2. Source, Destination, and Direction Rule Precedence · Rule Glossary 1. 2. 3. Rule purpose Rule trigger criteria Additional rule info · Threat Mitigation Policy 1. 2. F 4 Project Threat Mitigation Policies · TD Expert System 1. 2. 3. 4. 5. Getting Started Charts & Graphs Log Data & Pre-analysis Expert System CSV Future of the Expert System Trend Micro Incorporated – FOR INTERNAL USE ONLY Overview

RUNNING HEADER, 14 PT. , ALL CAPS, Line Spacing=1 line · Threat Log Analysis 1. 2. 3. 4. 5. 6. Start with the Spam VSAPI & NVP Pattern Matches Suspicious Packed Files Web Request from a Malware User-agent IRC Based Rules Discovering Gateways · Research 1. Research Resources · Putting the Report Together 1. Disclaimer Trend Micro Incorporated – FOR INTERNAL USE ONLY Overview

RUNNING HEADER, 14 PT. , ALL CAPS, Line Spacing=1 line TD Log Concepts Source, Destination, and Direction · · · Before describing the rules in Total Discovery, and before going into details on how to effectively analyze a site’s logs, the concepts of source, destination, and direction must be explained. Every log will have a source IP, port, and MAC and a destination IP, port, and MAC. The source is where the network packet originated and the destination is where the packet was sent to. When TDA is deployed at a site, the ranges of the network’s internal IP addresses must be specified in the console. This is critical for the accuracy and effectiveness of the rules and determines the direction of a log. If a log’s source IP address is within the internal IP ranges mentioned above, the direction is internal. This means that the packet originated from within the site’s network. Otherwise, the log’s direction is external, and the packet came from outside the network. Direction plays a major role in log analysis and should never be overlooked. More details will be given as the rules and log analysis are explained. Trend Micro Incorporated – FOR INTERNAL USE ONLY
RUNNING HEADER, 14 PT. , ALL CAPS, Line Spacing=1 line TD Log Concepts Rule Precedence · · Other than VSAPI and NVP (Network Virus Pattern) pattern matches, all rules in Total Discovery have a confidence level of either HIGH, MEDIUM, or LOW. There are some rules that overlap in some ways, and logically one packet could generate more than one log. However, rule precedence usually will only allow one log per packet, unless there are two rules triggered with the same confidence level. Here is the rule precedence hierarchy: VSAPI > NVP > HIGH > MEDIUM > LOW Example: one packet contains a VSAPI pattern match, and also has behavior that matches a HIGH confidence rule. In this case, the VSAPI pattern match would be logged and the HIGH confidence rule would be discarded. Trend Micro Incorporated – FOR INTERNAL USE ONLY
RUNNING HEADER, 14 PT. , ALL CAPS, Line Spacing=1 line Rule Glossary SMTP Open-Relay access attempt · An open mail relay is an SMTP server configured to allow anyone on the Internet to send email through it. This is commonly abused by spammers and it is recommended to disable it to avoid an email server being blacklisted. · This rule is triggered when an internal host sends an SMTP email where neither the domain of the sender nor the recipient exists in Total Discovery's registered domains. Email aliases are considered trusted for this rule. · It is important to note that this rule’s name can be misleading. It is more often triggered by spambots or false positives than actual open-relay attempts. Trend Micro Incorporated – FOR INTERNAL USE ONLY
RUNNING HEADER, 14 PT. , ALL CAPS, Line Spacing=1 line Rule Glossary Peer to Peer · Peer-to-peer networks are typically used for connecting hosts via largely ad hoc connections. Such networks are used commonly for sharing files, particularly media and software. Often, these files are copyright protected and illegal to be sharing in this manner. Also, files shared on P 2 P networks will sometimes contain viruses and/or malware. · This rule is triggered when one of the following P 2 P applications establishes a connection with another node: Bittorent, Blubster, Direct_Connect, e. Donkey 2000, e. Donkey_e. Mule, Gnucleus LAN, Limewire, Bearshare, Shareaza, i. Mesh, Kazaa, Kuro, MLDonkey, Morpheus, Open. Nap, Soul. Seek, Win. MX Trend Micro Incorporated – FOR INTERNAL USE ONLY
RUNNING HEADER, 14 PT. , ALL CAPS, Line Spacing=1 line Rule Glossary Pattern Matches · Total Discovery supports VSAPI and NVP (Network Virus Pattern) patterns. · When a log does not have a description, it is usually a pattern detection and you can find the pattern name in the “Detection. Name” field of the log. Trend Micro Incorporated – FOR INTERNAL USE ONLY
RUNNING HEADER, 14 PT. , ALL CAPS, Line Spacing=1 line Rule Glossary Malicious URL access attempt · This rule is triggered when a host attempts to access a URL whose URI matches one in our database of known malicious URIs. These URIs are commonly contacted by malicious downloader applications, adware, and malware that contacts scripts used to test HTTP proxies. · Example: http: //www. somesite. com/baddir/file. php? blah http: //www. anothersite. com/baddir/file. php? blah http: //www. onemoresite. com/baddir/file. php? blahblah In this example, we could create a bad URI of “/baddir/file. php” Trend Micro Incorporated – FOR INTERNAL USE ONLY
RUNNING HEADER, 14 PT. , ALL CAPS, Line Spacing=1 line Rule Glossary Suspicious file extension for an executable file · This rule is triggered when a host attempts to download a file that is determined to be an executable and has an extension of. com, . bat, . pif, or. cmd. These file extensions are commonly used to disguise malware. This rule can also be triggered when an executable file has more than one extension, such as "image. gif. exe". Trend Micro Incorporated – FOR INTERNAL USE ONLY
RUNNING HEADER, 14 PT. , ALL CAPS, Line Spacing=1 line Rule Glossary Suspicious archive file · This rule is triggered when a file contained in an archive attachment in an SMTP or POP 3 email has an extension of. com, . bat, . pif, or. cmd. These file extensions are commonly used to disguise malware. This rule can also be triggered when an executable file has more than one extension, such as "image. gif. exe". Trend Micro Incorporated – FOR INTERNAL USE ONLY
RUNNING HEADER, 14 PT. , ALL CAPS, Line Spacing=1 line Rule Glossary Suspicious packed file · Trend's Intelli. Trap detection technology heuristically identifies variants of known malware by detecting the use of the popular compression application that hackers use to create them. · This rule is most commonly triggered when a host attempts to download a file that is detected by Intellitrap. Trend Micro Incorporated – FOR INTERNAL USE ONLY
RUNNING HEADER, 14 PT. , ALL CAPS, Line Spacing=1 line Rule Glossary IRC protocol detected · The Internet Relay Chat (IRC) protocol is commonly used by malicious bots for communications. · This rule is triggered when the IRC protocol is detected on an incoming or outgoing connection. This does not necessarily signify the presence of a bot and could simply be legitimate chatting on the IRC protocol. Trend Micro Incorporated – FOR INTERNAL USE ONLY

RUNNING HEADER, 14 PT. , ALL CAPS, Line Spacing=1 line Rule Glossary IRC protocol uses non-standard port · The Internet Relay Chat (IRC) protocol typically uses a port in the range of 6665 -6669. It is common for malicious IRC bots to use non-standard ports for their communication. · This rule is triggered when an incoming or outgoing connection is detected using the IRC protocol on a port outside of this range. There is still a chance this is legitimate IRC traffic, but more likely it is a bot communication. Trend Micro Incorporated – FOR INTERNAL USE ONLY
RUNNING HEADER, 14 PT. , ALL CAPS, Line Spacing=1 line Rule Glossary Cross. Site Scripting (XSS) detected · · This rule covers a specific type of XSS vulnerability that allows a user to inject script code onto a web page. This vulnerability commonly exists in web forms or web applications which do not validate user input properly. This rule is triggered when the HTTP request contains a script tag “<script>” in the URL Example: http: //anysite. com/script. cgi? var=<script>alert(‘yo’)</script>&var 2=something This rule also checks for encoding, so the above example would also work if the characters were encoded. Trend Micro Incorporated – FOR INTERNAL USE ONLY
RUNNING HEADER, 14 PT. , ALL CAPS, Line Spacing=1 line Rule Glossary Default Account Usage · · Many services and applications come with a privileged default account which the user is expected to change the password for once installed. Not changing the default password for these default accounts poses a risk of unauthorized use. This rule is triggered when someone attempts to login to the default account for SQL or a Cisco switch present in the network. SQL using “sa” account with a blank password Cisco using “cisco” account with the password “cisco” Trend Micro Incorporated – FOR INTERNAL USE ONLY
RUNNING HEADER, 14 PT. , ALL CAPS, Line Spacing=1 line Rule Glossary DNS query of a known IRC C&C · · · The Internet Relay Chat (IRC) protocol is commonly used by malicious bots for communications. C&C stands for Command & Control. C&C servers are used by bot masters to control botnets. Typically, a bot will contact these servers to receive instructions and updates, in this case using the IRC protocol. This rule is triggered when a DNS query is made for a domain that is present in our database of known IRC C&C servers. This happens when a bot wishes to “phone home” for instructions from its master. Trend Micro Incorporated – FOR INTERNAL USE ONLY
RUNNING HEADER, 14 PT. , ALL CAPS, Line Spacing=1 line Rule Glossary Email contains a packed executable in an archive file attachment · · Trend's Intelli. Trap detection technology heuristically identifies variants of known malware by detecting the use of the popular compression application that hackers use to create them. This rule is triggered when an email attachment is an archive that contains a file detected by Intelli. Trap. Trend Micro Incorporated – FOR INTERNAL USE ONLY
RUNNING HEADER, 14 PT. , ALL CAPS, Line Spacing=1 line Rule Glossary Email contains a suspicious link to a possible phishing site · · It is common for a phishing email to contain a hard-coded IP address to the phishing site. Legitimate emails from your bank or ecommerce service would not contain such links. This rule is triggered when the domain of the sender’s email address matches our list of commonly phished domains (eg. Citibank, Pay. Pal, e. Bay, etc. ) and the message contains a hard-coded IP address. Trend Micro Incorporated – FOR INTERNAL USE ONLY
RUNNING HEADER, 14 PT. , ALL CAPS, Line Spacing=1 line Rule Glossary Email sent through a non-trusted SMTP server · This rule is triggered when an internal host sends SMTP email to an external SMTP server that is not present in Total Discovery's registered services. This could signify information leakage, but is also quite common in notification systems. It is recommended to investigate the legitimacy of the email being sent. Trend Micro Incorporated – FOR INTERNAL USE ONLY
RUNNING HEADER, 14 PT. , ALL CAPS, Line Spacing=1 line Rule Glossary Email subject matches malware-used subject and contains an executable file attachment · This rule is triggered when an SMTP or POP 3 email has a subject commonly used by email worms and contains an executable attachment. Trend Micro Incorporated – FOR INTERNAL USE ONLY

RUNNING HEADER, 14 PT. , ALL CAPS, Line Spacing=1 line Rule Glossary IRC session established with a known IRC C&C · · · The Internet Relay Chat (IRC) protocol is commonly used by malicious bots for communications. C&C stands for Command & Control. C&C servers are used by bot masters to control botnets. Typically, a bot will contact these servers to receive instructions and updates, in this case using the IRC protocol. This rule is triggered when a host connects with an IRC server present in our database of known IRC C&C servers. Trend Micro Incorporated – FOR INTERNAL USE ONLY
RUNNING HEADER, 14 PT. , ALL CAPS, Line Spacing=1 line Rule Glossary Host DNS IAXFR/IXFR request from a non-trusted source · · · The data contained in an entire DNS zone is sensitive. A hacker with this data could easily plan an attack on your network. This rule is triggered when any machine not listed in TDA’s trusted DNS services requests a DNS zone transfer (attempts to download all your DNS information). For this rule, the possible attacker is the destination IP address. Trend Micro Incorporated – FOR INTERNAL USE ONLY

RUNNING HEADER, 14 PT. , ALL CAPS, Line Spacing=1 line Rule Glossary IRC session on a non-standard port DCC sends an executable file · · · The Internet Relay Chat (IRC) protocol typically uses a port in the range of 6665 -6669. It is common for malicious IRC bots to use non-standard ports for their communication. DCC (Direct Client to Client) is used by IRC to transfer files. IRC based worms use social engineering tactics to send itself to other IRC users. This rule is triggered when a DCC request is made to send an executable file in an IRC session on a non-standard port. Trend Micro Incorporated – FOR INTERNAL USE ONLY

RUNNING HEADER, 14 PT. , ALL CAPS, Line Spacing=1 line Rule Glossary (Multiple/Too many) logon failed · · Numerous failed authentication attempts are a good indication of a malicious user or process trying to gain network access by performing password guessing. This is typically done using a so-called ‘dictionary attack’, where a list of words often used as passwords is simply tried on a given account. An alternative type of attack is the so called ‘brute-force’ attack. Here, a massive amount of passwords are automatically generated and tried. During a brute force attack, theoretically all combinations are tried, making it a very lengthy operation and thus, generating many more failed logins than the dictionary attack. This rule is triggered when a certain threshold of failed login attempts is reached. Below are the details of these thresholds per protocol. For the SMB protocol, the possible attacker is the destination IP address. Also for the SMB protocol, there are chances for false positives due to technical reason. You should consult the customer if you have suspicions. Trend Micro Incorporated – FOR INTERNAL USE ONLY
RUNNING HEADER, 14 PT. , ALL CAPS, Line Spacing=1 line Rule Glossary Oracle HTTP Exploit detected · This rule detects attempts to exploit Oracle web service vulnerabilities. Trend Micro Incorporated – FOR INTERNAL USE ONLY

RUNNING HEADER, 14 PT. , ALL CAPS, Line Spacing=1 line Rule Glossary Packed executable file dropped on an SMB administrative share · · Trend's Intelli. Trap detection technology heuristically identifies variants of known malware by detecting the use of the popular compression application that hackers use to create them. The Administrative Shares are the default network shares created by all Windows NTbased operating systems. These default shares share every hard drive partition in the system. These shares will allow anyone who can authenticate as any member of the local Administrators group access to the root directory of every hard drive on the system. Network worms commonly spread by copying themselves to network shares. Advanced network worms will use password attacks to take advantage of administrative network shares in order to propagate itself to other hosts joined to the network. This rule is triggered when an Intelli. Trap detected file is copied to an administrative share (C$, D$, Admin$). Trend Micro Incorporated – FOR INTERNAL USE ONLY

RUNNING HEADER, 14 PT. , ALL CAPS, Line Spacing=1 line Rule Glossary Possible Buffer-Overflow attempt detected · A buffer overflow is a condition where a process attempts to store data in a buffer that is more than what it the buffer is intended to hold. This causes valid data such as those used to store variables or program flow data to be overwritten which may cause a process to crash or produce undesirable results. · Buffer-Overflows can be triggered by malformed inputs that can be specifically crafted to execute arbitrary code; codes that can be used to download a malicious file from the internet, or open a port to execute remote commands. · This rule is triggered when an RPC (Remote Process Call) message is detected to contain a sequence of instructions generally found in buffer-overflow code. Trend Micro Incorporated – FOR INTERNAL USE ONLY
RUNNING HEADER, 14 PT. , ALL CAPS, Line Spacing=1 line Rule Glossary Possible NOP-sled detected · NOP (opcode 0 x 90) is an Intel x 86 instruction which stands for “no-operation”. When the CPU encounters such an instruction, it does nothing but move on to the next instruction. A sequence of NOP instructions (also known as NOP-sled) have been used in buffer overflow codes where the memory address to execute cannot be determined accurately. The padding of NOP’s help to slide the execution path to the malicious code. · This rule is triggered when an RPC (Remote Process Call) message is detected to contain a sequence of NOP (no-operation) instructions and thus could be an indication of a buffer overflow attack. Trend Micro Incorporated – FOR INTERNAL USE ONLY
RUNNING HEADER, 14 PT. , ALL CAPS, Line Spacing=1 line Rule Glossary Possible Downloader · This rule is triggered when the HTTP content downloaded was declared to be of another type in the response headers, like that of a Shockwave Flash, JPEG, GIF, or Office document type but is actually a Windows executable file. An executable file normally would be declared to be of “application” type. Trend Micro Incorporated – FOR INTERNAL USE ONLY
RUNNING HEADER, 14 PT. , ALL CAPS, Line Spacing=1 line Rule Glossary Rogue service detected · Rogue services are security risks in a corporate network as they are generally mismanaged, often lacking compliance with the existing security policies. · The lack of security patches of these services makes them vulnerable to compromise. The lack of proper configurations like authentication can be a cause of information leak. · In some cases, rogue services may be a result of a malware infection; malware infects a system and acts as an SMTP Open-relay allowing unsolicited emails such as spams to be relayed from one domain to another or act like an SMTP server or client to spam emails. · This rule detects SMTP and DNS services that are not registered in TDA’s registered services. It is usually best to confirm with the customer on these detections. Domain controllers, by default, have a DNS service active which needs to be registered in Total Discovery. Failure to do so will result in this rule being unnecessarily triggered. · Trend Micro Incorporated – FOR INTERNAL USE ONLY
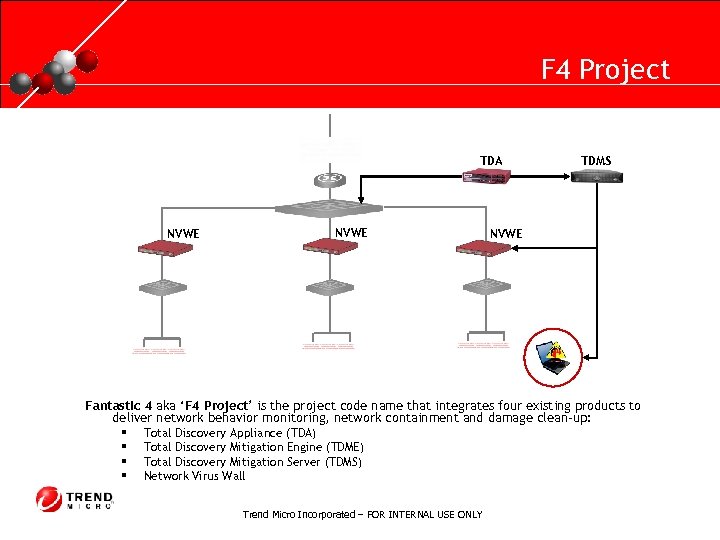
RUNNING HEADER, 14 PT. , ALL CAPS, Line Spacing=1 line F 4 Project TDA NVWE TDMS NVWE Fantastic 4 aka ‘F 4 Project’ is the project code name that integrates four existing products to deliver network behavior monitoring, network containment and damage clean-up: § Total Discovery Appliance (TDA) § Total Discovery Mitigation Engine (TDME) § Total Discovery Mitigation Server (TDMS) § Network Virus Wall Trend Micro Incorporated – FOR INTERNAL USE ONLY

RUNNING HEADER, 14 PT. , ALL CAPS, Line Spacing=1 line F 4 Project F 4 Components: · · TDA (Total Discovery Appliance) § deployed offline at the core switch to monitor for suspicious network behavior § detect known threats by network content inspection technology (NCIT) along with all the major protocols scanned by VSAPI. detect unknown threats by network content correlation technology (NCCT). § TDME (Total Discovery Mitigation Engine) § branched from DCE § an engine to proactively eliminate malicious code from the infected system upon detection § incorporates “forensic cleanup” to clean up TDMS (Total Discovery Mitigation Server) § a server to receive the commands from TDA and then deploy agent to do forensic cleanup or damage § NVW § § § assessment. can also trigger NVW to quarantine the infected client. (Network Virus Wall) quarantine the infected client can quarantine or release the quarantine per TDMS instruction refers to NVWE 2500 and NVWE 1200 model. Trend Micro Incorporated – FOR INTERNAL USE ONLY

RUNNING HEADER, 14 PT. , ALL CAPS, Line Spacing=1 line Threat Mitigation Policy Important notes: · · · The term “mitigable” means a threat is both cleanable and blockable. Mitigation parameters are defined in the Network Content Correlation Pattern (NCCP). NCCP maps each rule with the mitigation parameters: § Cleanable (yes or no) § Direction to clean (inbound, outbound, both) § Protocol to clean (HTTP, IRC, SMTP, etc. ) § Clean priority (High, Medium-High, Medium-Low, Low) – clean task deployment priority is configurable in the TDMS console § Clean target (source ip, destination ip) § DCE pattern name to use if the target is the source (usually the attacker) § DCE pattern name to use if the target is the destination (usually the victim) Along with the mitigation task, TDA will also provide tips on: source ip/port, destination ip/port, filename, dcecrc, smb pid, dcs pattern name, etc. If threat is mitigable, mitigation task is sent and processed by TDMS has options to enable/disable policy and apply exceptions before deploying TDME. Trend Micro Incorporated – FOR INTERNAL USE ONLY
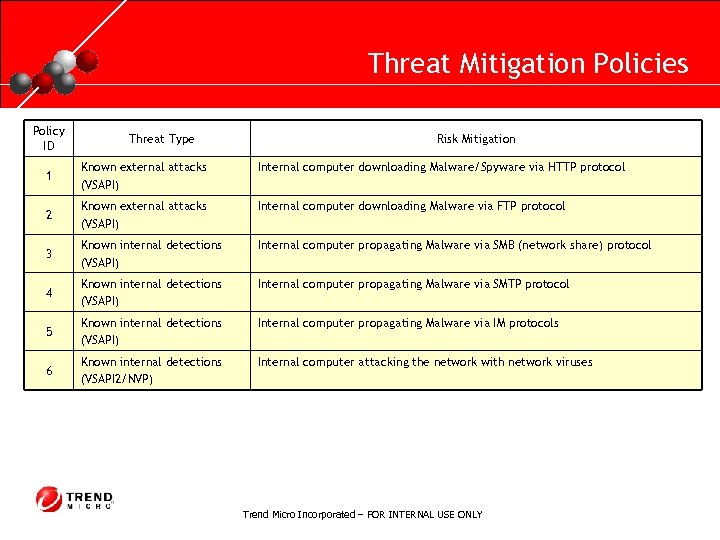
RUNNING HEADER, 14 PT. , ALL CAPS, Line Spacing=1 line Threat Mitigation Policies Policy ID Threat Type Risk Mitigation 1 Known external attacks (VSAPI) Internal computer downloading Malware/Spyware via HTTP protocol 2 Known external attacks (VSAPI) Internal computer downloading Malware via FTP protocol 3 Known internal detections (VSAPI) Internal computer propagating Malware via SMB (network share) protocol 4 Known internal detections (VSAPI) Internal computer propagating Malware via SMTP protocol 5 Known internal detections (VSAPI) Internal computer propagating Malware via IM protocols 6 Known internal detections (VSAPI 2/NVP) Internal computer attacking the network with network viruses Trend Micro Incorporated – FOR INTERNAL USE ONLY
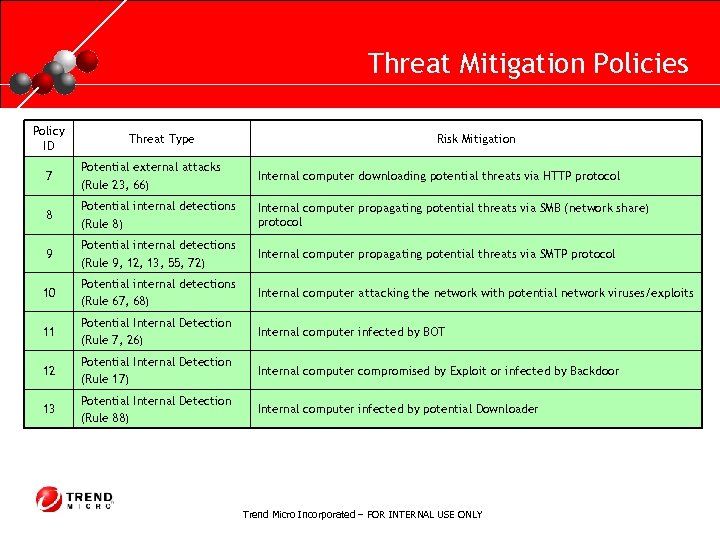
RUNNING HEADER, 14 PT. , ALL CAPS, Line Spacing=1 line Threat Mitigation Policies Policy ID Threat Type Risk Mitigation 7 Potential external attacks (Rule 23, 66) Internal computer downloading potential threats via HTTP protocol 8 Potential internal detections (Rule 8) Internal computer propagating potential threats via SMB (network share) protocol 9 Potential internal detections (Rule 9, 12, 13, 55, 72) Internal computer propagating potential threats via SMTP protocol 10 Potential internal detections (Rule 67, 68) Internal computer attacking the network with potential network viruses/exploits 11 Potential Internal Detection (Rule 7, 26) Internal computer infected by BOT 12 Potential Internal Detection (Rule 17) Internal computer compromised by Exploit or infected by Backdoor 13 Potential Internal Detection (Rule 88) Internal computer infected by potential Downloader Trend Micro Incorporated – FOR INTERNAL USE ONLY
RUNNING HEADER, 14 PT. , ALL CAPS, Line Spacing=1 line Total Discovery Expert System Getting Started – Generate the report data · The Expert System can be accessed at http: //10. 2. 168. 252/expertsystem/TD_Log_Analysis. php · First, choose which site you will be reporting on from the select box. · Then, use the dropdown menus to choose the date range of logs you will be reporting on and click the Submit button. · If you do not see the site you wish to report on in the select box, or if there any problems with the expert system or the data it generates, please contact james_bennett@trendmicro. com with the issue. Trend Micro Incorporated – FOR INTERNAL USE ONLY

RUNNING HEADER, 14 PT. , ALL CAPS, Line Spacing=1 line Total Discovery Expert System The Charts and Graphs · The first series give overall detection statistics for the date range. Figure 1 -a is a pie chart that illustrates the percentage of internal and external detections. Chart 1 -b displays the counts for all of the rules triggered for both directions. · The second and third series give internal and external detection statistics for the date range respectively. Figures 2 -a and 3 -a are bar graphs that illustrate the counts of detections per protocol. Figures 2 -b and 3 -b are bar graphs that illustrate the counts of detections per confidence level. Confidence levels are assigned on a per rule basis. PATTERN is a VSAPI or NVW pattern detection. Charts 2 -c and 3 -c give detection statistics broken down by protocol, confidence level, and risk type ordered by their confidence level. Charts 2 -d and 3 -d give detection statistics broken down by protocol, confidence level, and rule description ordered by confidence level. Trend Micro Incorporated – FOR INTERNAL USE ONLY
RUNNING HEADER, 14 PT. , ALL CAPS, Line Spacing=1 line Total Discovery Expert System Log Data and Pre-Analysis · After the charts and graphs, the Expert System presents you with 2 items regarding preanalysis: Overview and Host Information. · The Overview section will group together internal IP addresses that have a similar preanalysis for your convenience. Each IP is a link that you can click on to display the all of the logs related to that IP. It is recommended that you right click on the link and choose to open in a new window so that you do not lose your place on the main page and have to scroll down again. · The Host Information section organizes and groups all of the logs by the internal IP address and displays any pre-analysis for each host if available. Just as in the Overview section, each IP is a link you can follow to view all of the logs for that particular host. NOTE: just because there is no pre-analysis for a host does not mean that there is no threat. Each host’s logs should be investigated. Trend Micro Incorporated – FOR INTERNAL USE ONLY

RUNNING HEADER, 14 PT. , ALL CAPS, Line Spacing=1 line Total Discovery Expert System Pre-analysis · · · applies log correlation involves adding pre-defined SQL queries on TDA events to provide automated analysis adds intelligence to recognize a series of patterned threat behavior or rule-out false positives Trend Micro Incorporated – FOR INTERNAL USE ONLY
RUNNING HEADER, 14 PT. , ALL CAPS, Line Spacing=1 line Total Discovery Expert System Pre-analysis Rules supported: · Threat Detection § Bot Infected § Possible Bot Activity § Possible IRC Bot § Bruteforce attack on FTP admin account; § Spamming Worm Infected Emails § SMTP Open Relay or Spam. Bot § Infected Internal Machine Performing Attacks § Spyware Infected § Possible Malware § Access to exploited site § Possible P 2 P § Possible Access to malicious URL § External Network Virus Attack Trend Micro Incorporated – FOR INTERNAL USE ONLY

RUNNING HEADER, 14 PT. , ALL CAPS, Line Spacing=1 line Total Discovery Expert System Pre-analysis Rules supported: · False Positive Detection § False Positive (Email through Non-Trusted SMTP) § False Positive (Open-relay) Trend Micro Incorporated – FOR INTERNAL USE ONLY
RUNNING HEADER, 14 PT. , ALL CAPS, Line Spacing=1 line Total Discovery Expert System Bot infected machine · rule 26 (session established with known IRC C&C server) Bot activity · rule 7 (Bot command detected) Note: · dstip is the infected host · srcip is the IRC C&C server recommended to be blocked Possible IRC Bot · · rule 18 (DNS query of known C&C) direction is internal Trend Micro Incorporated – FOR INTERNAL USE ONLY

RUNNING HEADER, 14 PT. , ALL CAPS, Line Spacing=1 line Total Discovery Expert System Brute-force attack on FTP admin account. · { rule 21 (multiple logon failed) protocol is FTP event count >= 5 or rule 15 (too many logon failed) · } username ‘Administrator’ Spamming worm infected emails · · direction is internal protocol is SMTP description is ‘Pattern Detection’ event count >=5 Trend Micro Incorporated – FOR INTERNAL USE ONLY
RUNNING HEADER, 14 PT. , ALL CAPS, Line Spacing=1 line Total Discovery Expert System SMTP Open-Relay Server or Spambot · · · rule 29 (SMTP open-relay) average event count/day > 20 unique sender count > 5 unique recipient count > 5 Infected Internal Machine Performing Attacks · · protocol is ‘virus_pattern_udp’ or ‘virus_pattern_tcp’ srcip is internal Trend Micro Incorporated – FOR INTERNAL USE ONLY
RUNNING HEADER, 14 PT. , ALL CAPS, Line Spacing=1 line Total Discovery Expert System Spyware infected Machine · · rule 70 (web request from spyware user-agent) direction is internal Possible malware · · · protocol is http external attack { rule 32 (suspicious file extension "com" for exe) or rule 47 (suspicious packed) } Note: dstip is possible infected machine Trend Micro Incorporated – FOR INTERNAL USE ONLY

RUNNING HEADER, 14 PT. , ALL CAPS, Line Spacing=1 line Total Discovery Expert System Access to exploited site · rule 75 (ANI exploit) · protocol is http · external attack Note: · High Confidence Level if domaintools. com returns a reverse ip of more than x sites hosted and/or blacklist status says "currently listed" Possible P 2 P · · protocolgroup is P 2 P internal detection Trend Micro Incorporated – FOR INTERNAL USE ONLY

RUNNING HEADER, 14 PT. , ALL CAPS, Line Spacing=1 line Total Discovery Expert System Possible Access to malicious URL · · rule 56 (web request to malware user-agent) direction is internal External Network Virus Attack · · protocol is ‘virus_pattern_udp’ or ‘virus_pattern_tcp’ srcip is external Trend Micro Incorporated – FOR INTERNAL USE ONLY
RUNNING HEADER, 14 PT. , ALL CAPS, Line Spacing=1 line Total Discovery Expert System False Positive (Email sent through a non-trusted SMTP server) · rule 52 (Email sent through a non-trusted SMTP server) · unique sender <= 2 False Positive (SMTP Open-Relay) · rule 29 (SMTP Open-Relay) · unique sender <= 2 Trend Micro Incorporated – FOR INTERNAL USE ONLY

RUNNING HEADER, 14 PT. , ALL CAPS, Line Spacing=1 line Total Discovery Expert System The Expert System CSV File · · · Right click and choose ‘Save Target As’ to save the csv file to your computer, then open it in Excel to view. One of the Expert System’s most useful features is how it organizes and presents TD log data to you. It organizes the logs by internal IP address, and shows you only the data you want to see for each log, ordering the logs by log time. What you see is a timeline of events for each host on the customer’s network, making it much easier to recognize when a threat is present. Each row in the csv contains the following data: the name of the site, the log time, the rule id# (for debugging purposes), the direction, the protocol, the source IP address, the source port, the destination IP address, the destination port, the rule description, and a series of “special” fields. A row of asterisks (*) is used to separate each internal host for easier reading. The special fields are for rule specific data. For example, an email based rule would have the sender, recipient, subject, and possibly URL data while an IRC based rule would possibly have the chat room name, nickname, and bot command issued. For pattern detections, there will be no rule description and instead you will see the detection name in the special field. These fields were all previously explained in the Rule Glossary section per each rule. Trend Micro Incorporated – FOR INTERNAL USE ONLY

RUNNING HEADER, 14 PT. , ALL CAPS, Line Spacing=1 line Total Discovery Expert System Future of the Expert System · · · Generate more of the report automatically, and perhaps generate a complete preliminary report. Automated research. Determine suspiciousness of IP address/URL/file. Web based reports and reporting functions. Trend Micro Incorporated – FOR INTERNAL USE ONLY
RUNNING HEADER, 14 PT. , ALL CAPS, Line Spacing=1 line Threat Log Analysis Start with the spam. . · · · For most sites you will encounter, SMTP based rules will be the most popular. Scroll through the csv file and look at the SMTP rules for each host. First look at the number of emails for each host. Most spam comes in large numbers, so look more closely at the hosts which have a lot of SMTP logs. Look at the subject and URL. These can tell a lot about the nature of an email. First think about the name of the site you are analyzing and the nature of its business. Do the subjects of the emails fit with the environment? Of course, there always personal emails at every site you will analyze. You need to become familiar with typical spamming and social engineering tactics. These become easy to spot with some practice. Unfortunately, TD only holds the first 32 characters of an email subject. But, this is usually enough to make a good judgement. Trend Micro Incorporated – FOR INTERNAL USE ONLY

RUNNING HEADER, 14 PT. , ALL CAPS, Line Spacing=1 line Threat Log Analysis Start with the spam. . (continued) · To familiarize yourself with some common spam subjects, review the following “in the wild” subjects. Worm (attempts to lure victim to run attachment or click link that leads to exploit): ecards (lures victim with promise of an ecard or egreeting): funny postcard holiday e-card movie-quality card funny ecard greeting card musical card birthday ecard animated postcard love e-card interesting pics/videos (lures victim with promise of scandalous pictures or video): Hey man, check out these pics I My friend took these pics of me, Oh man this girl is a freak, lol Don't tell my husband I gave you Honey, i miss you. let me show y Oh man I found these pictures of I bet your wife wont do this for My EX-boyfriend took these of me OMG, what are you thinking LMAO, your crazy man current events (lures victim using upcoming holiday, event, or current news): The Big Labor Day Weekend A Labor Day E-Card A Labor Day Greeting Your Friend Sends A Labor Day Gr Trend Micro Incorporated – FOR INTERNAL USE ONLY
RUNNING HEADER, 14 PT. , ALL CAPS, Line Spacing=1 line Threat Log Analysis Start with the spam. . (continued) Anti-malware: Worm Detected! Trojan Detected! Virus Activity Detected! Most recently noted NFL related subjects: Do you have your NFL Game List? Free NFL Game Tracker Are you ready for some football? Currently, worm emails are using links to hardcoded IP addresses (often home users’ compromised PCs). The URLs will either link to the root directory of the IP (http: //x. x/), or to some script (http: //x. x/folder/in. php). Worms will otherwise include the binary as an attachment cleverly named to fool the recipient into thinking it is something else. If VSAPI has a pattern for the file, it will show up in the logs as a pattern match. Phishing(attempts to trick user into sending login info for banking and ecommerce sites): Pay. Pal : Please confirm your Pay IMPORTANT: Alert from e. Bay This is your official notificati North. Fork Bank: Secure Confirmat North. Fork Bank: Secure Update Pr North. Fork e. Cash Management Servi http: //82. 241. 245. 37/chaseonline. chase. com/index. htm http: //70. 88. 210. 45: 81/ebay. com/index. html http: //nfbconnect. northforkbank. com. pid 24 adhsadu. FZGZBBB. com/confirm/cashman/banking/Confirm. asp http: //0 xce. 0 x 4 a. 0 x 2 e. 0 xcd/Members. Login/index. htm http: //0 x 574 a 115 a/bancoposte http: //3664571179/a. php There are many different banking and online payment services that are spoofed for phishing scams. The key is recognizing a “phishy” subject and even more importantly, a “phishy” URL. You can see the name of the banking institution or website in the URL, but it is not actually ever in the domain. The Northfork Bank comes close and could fool some, but notice how it is actually a subdomain? Also notice the notation of some of the IP addresses, they use decimal and hexadecimal in various formats. Trend Micro Incorporated – FOR INTERNAL USE ONLY

RUNNING HEADER, 14 PT. , ALL CAPS, Line Spacing=1 line Threat Log Analysis Start with the spam. . (continued) · · · There are many other types and varieties of spam and they will continue to evolve. Other things to pay attention to besides the subject and URL in an email is the sender/recipient. For internal detections, look at the senders. Are there multiple senders coming from one IP address? Do the domains of the senders belong to the site? For external detections, are you seeing similar subjects being sent to many different recipients? The direction is important because it can hint to us that a machine in the network may actually be infected with a spamming bot. If the direction is internal, the threat is more severe because this means that the source IP for these logs is infected and actively spamming. Trend Micro Incorporated – FOR INTERNAL USE ONLY

RUNNING HEADER, 14 PT. , ALL CAPS, Line Spacing=1 line Threat Log Analysis Reporting on Spam · · The most important spam related events to report on are internal detections. The customer is always concerned with spam originating from their network. This can cause their servers to be put on spam block lists. (refer to TD_report_SILGAN_20070822. doc) Every network receives spam, and most will already have spam protection in place. This makes reporting on external spam detections less of a priority, though it is a good practice to inform the customer of the possible threat, including the nature of the spam, the risks involved, and how to educate the end users on the network. If you are to include this analysis in your report, it should be towards the end after any higher priority events. (refer to TD_Report_Colo. State_08012007. doc) Trend Micro Incorporated – FOR INTERNAL USE ONLY

RUNNING HEADER, 14 PT. , ALL CAPS, Line Spacing=1 line Threat Log Analysis VSAPI & NVP Pattern Matches · · · Perhaps the easiest events to report on, the highest confidence detections of course are pattern detections. TD uses VSAPI and NVP patterns to detect malicious files and attacks on the network. It is common for multiple hosts on the network to be affected by the same pattern or group of patterns around the same time span, so look for all the hosts affected by the pattern(s) and group them together into one item on the report. The item should contain the IP addresses of the hosts affected, the log time of the detections (for multiple detections, use the latest date), the pattern names, and if the patterns are for NVP, the source IP addresses from where the attacks came. You should try to find a Trend Virus Encyclopedia entry for each pattern name and link to the entry from the pattern name in the report: http: //www. trendmicro. com/vinfo/virusencyclo/default. asp It is also common to see the ‘Suspicious Packed File’ rule detection surrounding VSAPI pattern detections over HTTP. These files are other components of the malware or other malware in a payload and can be referred to as suspicious when reporting the incident. Much like with the spam related rules, the NVP detections that are internal are a higher priority than the external detections. Internal NVP detections tell us that an internal host is attacking other machines on the internet and is probably infected. You can determine if the pattern is an NVP pattern by looking at the protocol or risk type of the log. (refer to TD_report_SILGAN_20070808. doc & TD_report_JSUN_20070822. doc) Trend Micro Incorporated – FOR INTERNAL USE ONLY

RUNNING HEADER, 14 PT. , ALL CAPS, Line Spacing=1 line Threat Log Analysis Suspicious Packed Files · · · A “Suspicious packed file” detection is an Intellitrap Generic_PAK detection. It is a generic detection of a file which has been packed by an application popularly used by malware authors. These detections can possibly be false positives, and alone are not enough to report on. However, these detections are great hints and with a little more research you can have enough confidence to report on an infection that otherwise would have been missed. Are there any other rules triggered around the same time on this host? As mentioned in the previous slide, it is common to see this rule alongside with pattern detections. This is an obvious infection taking place and should be reported. Other possibilities include seeing this rule after a “Malicious URL access attempt” detection, or “IRC protocol uses non-standard port”. Or maybe following the rule, you see “Web request from a malware user-agent”. All of these hint towards the file being malicious, and together, the combination of these rules gives you enough confidence to report that an infection has occurred. Another way to investigate if the file is malicious or not is by researching the source IP address where the file came from. More information on researching will be covered in the upcoming Research section. Trend Micro Incorporated – FOR INTERNAL USE ONLY
RUNNING HEADER, 14 PT. , ALL CAPS, Line Spacing=1 line Threat Log Analysis Web request from a malware user-agent · · The chance for false positives on this rule are small, but possible. When analyzing these logs, research the URL and IP it is contacting to determine that it is indeed malicious. Often times the files will be. txt, . ini, or some kind of script like. php, . cgi, . pl. Try to investigate what kind of data is being sent and/or received to help raise or lower your suspicions. Please report possible false positives to ed_malibiran@premium. trendmicro. com and james_bennett@trendmicro. com The direction of these detections should mostly always be internal. If you find an external detection of this rule, there is a slight chance that some host on the network has been compromised and is hosting malicious files. Otherwise, this is likely a false positive. (refer to TD_report_JSUN_20070808. doc) Trend Micro Incorporated – FOR INTERNAL USE ONLY

RUNNING HEADER, 14 PT. , ALL CAPS, Line Spacing=1 line Threat Log Analysis IRC Based Rules · · There a collection of different rules for the IRC protocol with varying confidence levels. Pay attention to the frequency of IRC logs for a host. If you see many IRC logs that are only seconds apart, this is a good indication of malware activity. Try using an IRC client or telnet to connect to the IRC server yourself. See if it looks like a legitimate chat server or possibly a C&C server. If the rule states it is on a non-standard port, be sure to use the proper port when connecting. Usually this will be src port for external and dst port for internal, unless the IRC server is actually the internal host. Also, perform research of the external IP address to help make a better determination of possible suspicious activity. More information on research will be provided in the next section. Trend Micro Incorporated – FOR INTERNAL USE ONLY
RUNNING HEADER, 14 PT. , ALL CAPS, Line Spacing=1 line Threat Log Analysis Gateway Discovery · · Some customers may have gateway devices installed in their network for various reasons, including security and this can cause confusion when analyzing the logs. If you see large amounts of logs for many different rules and pattern detections on one host, there is a chance it may be a gateway device. You should consult the customer to confirm this. If you see a log from an external address to an internal address, then see a similar log from that internal address to another internal address, this is also a good sign of a gateway device. The reverse of this is true as well, a log from an internal address to another internal address, then another log from that internal address to an external address. Example: a VSAPI pattern match was detected from an external address to an internal address. Another detection for that same VSAPI pattern match was detected with the same timestamp (or maybe 1 or 2 seconds later) from that internal address to another internal address. Trend Micro Incorporated – FOR INTERNAL USE ONLY
RUNNING HEADER, 14 PT. , ALL CAPS, Line Spacing=1 line Research Resources · · A good way to better confirm the suspicious activities indicated by many types of logs is to do some research of the external IP address. There are many tools on the internet, and Trend’s intranet to help aid in your research Google: Other search engines will work as well, though Google’s extensive database, search features, and security risk warnings returned with your search results make it the most useful for log analysis. Simply perform a search of the IP address, domain name, or URL in question and look at the results returned. Look for antivirus, tech support, or other security sites in the results. Also look for words like “block this”, “blacklist”, etc. Click on some of these links and read to find more information about what the IP may have been involved with in the past. Domaintools. com: This is a great site for finding domain and whois info based on an IP address or domain name. It will also tell you if the domain/IP is on any popular blacklists. Watch out for the following names in the whois info: Russian Business Network, Intercage, ESTDOMAINS http: //reclassify. wrs. trendmicro. com/submit-files/wrsonlinequery. asp Trend Micro Incorporated – FOR INTERNAL USE ONLY
RUNNING HEADER, 14 PT. , ALL CAPS, Line Spacing=1 line Research Resources · Another way to better confirm the suspicious activities indicated by some types of logs is to do some analysis of the questionable files involved. · To learn how to extract a file from the TDA console, read the slides from Beta_Training_TDA_CAV. ppt · · Zip the file and password protect it with the password ‘virus’, then email it to vtest@av. trendmicro. com. In a few minutes, you will receive an email response with the PAFI scan results of our scanners and our top competitor’s scanners. Send the file to CWSandbox for automatic behavior logging: https: //168. 61. 10. 39/submit. php User: trend Pw: 6 otn 3 tdat 4 Trend Micro Incorporated – FOR INTERNAL USE ONLY

RUNNING HEADER, 14 PT. , ALL CAPS, Line Spacing=1 line Putting the Report Together DISCLAIMERS: · This report format is subject to change and can be considered a “work in progress”. · I do not possess the greatest ability with Microsoft Office products =) · · · Open the Word doc, TD_report_template. doc Copy the charts and graphs from the Expert System results and paste them into their corresponding locations in the report template. Review the charts, graphs, and the logs. Then add some brief commentary about the logs for the most popular protocol for each direction. In section 4, replace the 3 dots (…) with your commentary on the logs for the most popular protocol for internal detections. In section 5, do the same for external detections. Use some of the previous reports as a guideline if needed. If you have reported on this site previously, include your last report’s analysis in section 6 as a reference for the customer. Using the tips given in the Threat Log Analysis slides, and using the previous reports for examples, fill in section 2 with your host level analysis. Change the page numbers in the table of contents to accurately reflect the report. Trend Micro Incorporated – FOR INTERNAL USE ONLY
270449683d24afdd689fea69802309ea.ppt