45b358f6134bc6153fae1ac736100838.ppt
- Количество слайдов: 32

Topologies and behavioral properties of the network Yvon Kermarrec Based on http: //www. openp 2 p. com/pub/a/p 2 p/2001/12/14/topologies_one. html

Key player : the network ¢ The network plays a central role for communication and coordination ¢ How is it structured ? How does it behave ? What are its impacts on the applications ? Dpt/Auteur

Agenda ¢ Topologies and structural properties of the network ¢ Behavioral properties of the network Dpt/Auteur

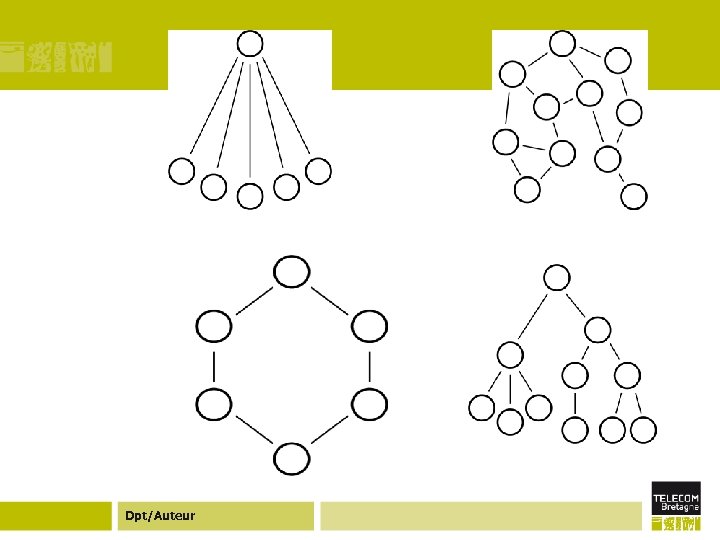
Topologies issues ¢ Centralized vs. decentralized systems ¢ How the nodes in the system are connected. ¢ Topology can be considered at many different levels: physical, logical, connection, or organizational. ¢ Topology is considered in terms of the information flow. • Nodes in the graph are individual computers or programs, • links between nodes indicate that those nodes are sharing information regularly in the system. Dpt/Auteur
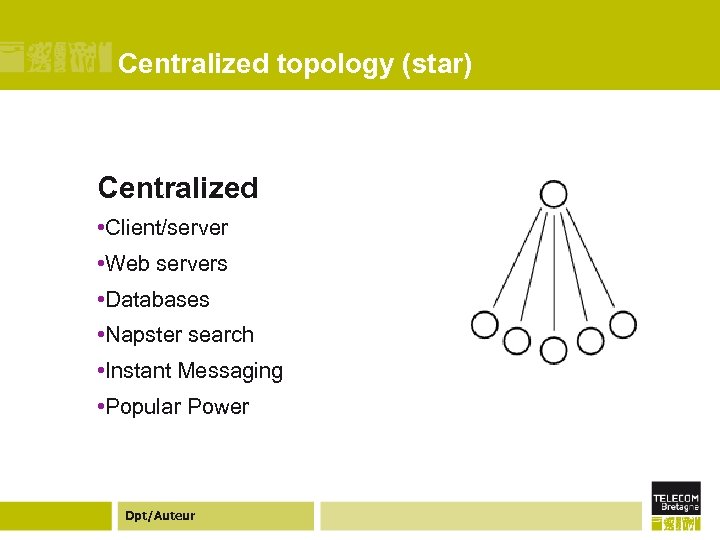
Centralized topology (star) Centralized • Client/server • Web servers • Databases • Napster search • Instant Messaging • Popular Power Dpt/Auteur
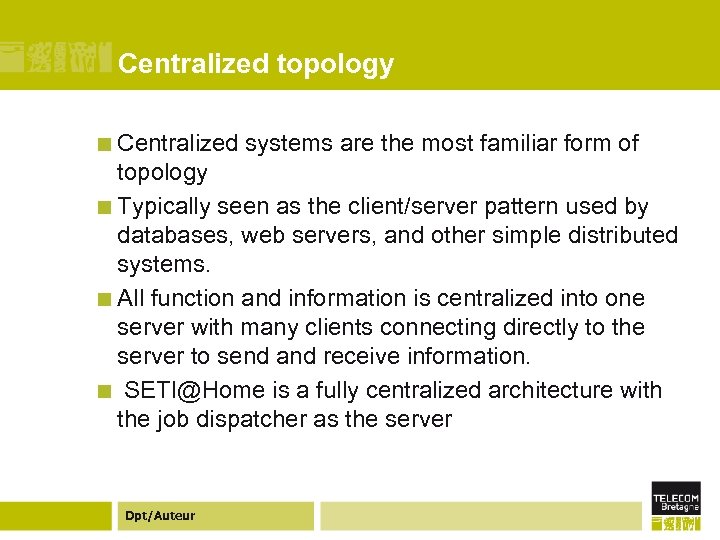
Centralized topology ¢ Centralized systems are the most familiar form of topology ¢ Typically seen as the client/server pattern used by databases, web servers, and other simple distributed systems. ¢ All function and information is centralized into one server with many clients connecting directly to the server to send and receive information. ¢ SETI@Home is a fully centralized architecture with the job dispatcher as the server Dpt/Auteur
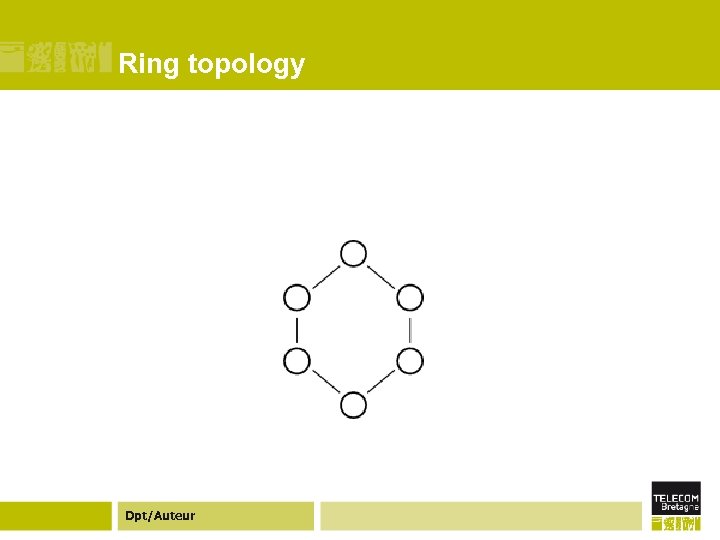
Ring topology Dpt/Auteur

Ring topology ¢A single centralized server cannot handle high client load, so a common solution is to use a cluster of machines arranged in a ring to act as a distributed server. ¢ Communication between the nodes coordinates statesharing, producing a group of nodes that provide identical function but have failover and load-balancing capabilities. ¢ Unlike the other topologies here, ring systems are generally built assuming the machines are all nearby on the network and owned by a single organization. Dpt/Auteur
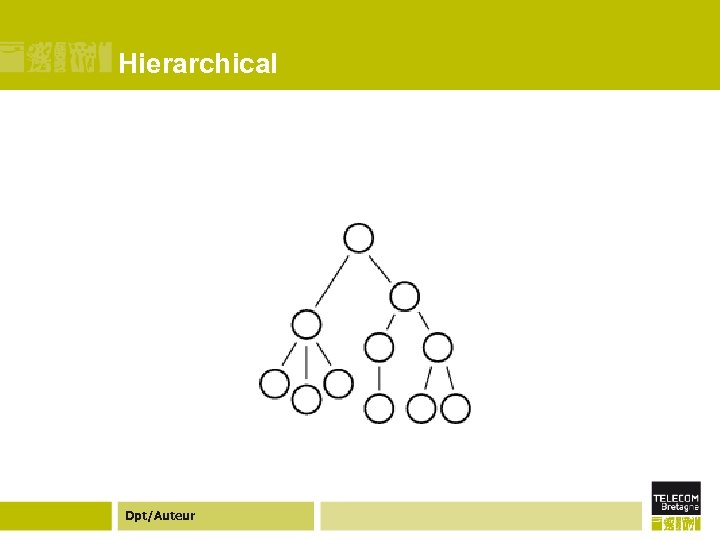
Hierarchical Dpt/Auteur

Hierarchical ¢ Hierarchical systems have a long history on the Internet, but in practice are often overlooked as a distinct distributed systems topology. ¢ The best-known hierarchical system on the Internet is the Domain Name Service, where authority flows from the root name-servers to the server for the registered name. ¢ NTP, the Network Time Protocol, creates another hierarchical system. Dpt/Auteur
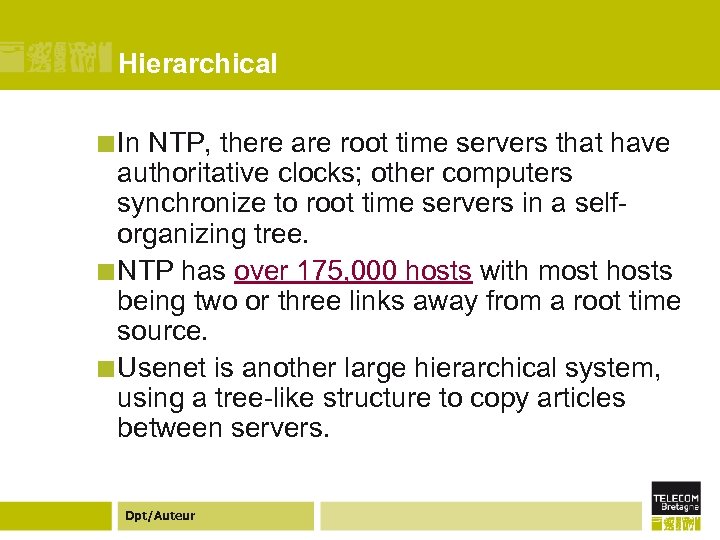
Hierarchical ¢ In NTP, there are root time servers that have authoritative clocks; other computers synchronize to root time servers in a selforganizing tree. ¢ NTP has over 175, 000 hosts with most hosts being two or three links away from a root time source. ¢ Usenet is another large hierarchical system, using a tree-like structure to copy articles between servers. Dpt/Auteur
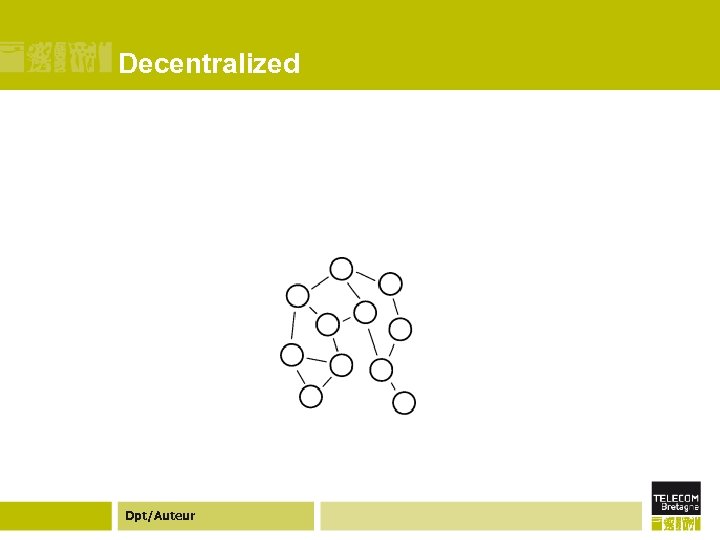
Decentralized Dpt/Auteur
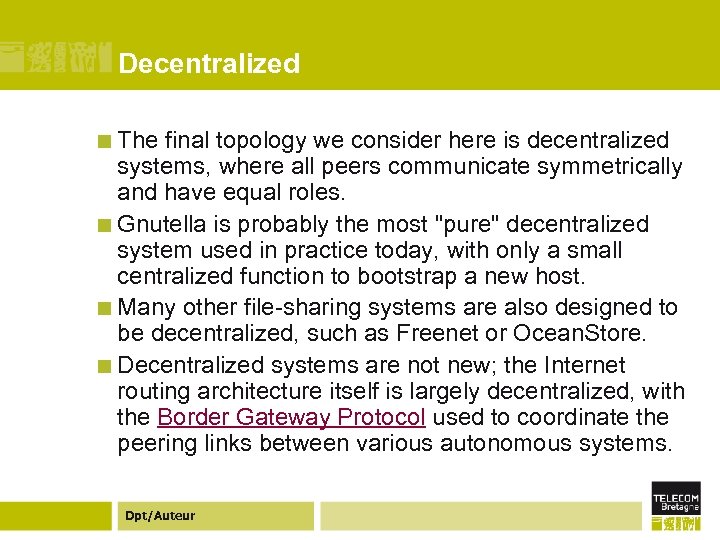
Decentralized ¢ The final topology we consider here is decentralized systems, where all peers communicate symmetrically and have equal roles. ¢ Gnutella is probably the most "pure" decentralized system used in practice today, with only a small centralized function to bootstrap a new host. ¢ Many other file-sharing systems are also designed to be decentralized, such as Freenet or Ocean. Store. ¢ Decentralized systems are not new; the Internet routing architecture itself is largely decentralized, with the Border Gateway Protocol used to coordinate the peering links between various autonomous systems. Dpt/Auteur
Dpt/Auteur
Hybrid topologies ¢ Distributed systems often have a more complex organization than any one simple topology. ¢ Real-world systems often combine several topologies into one system, making a hybrid topology. ¢ Nodes typically play multiple roles in such a system. For example, a node might have a centralized interaction with one part of the system, while being part of a hierarchy in another part. Dpt/Auteur
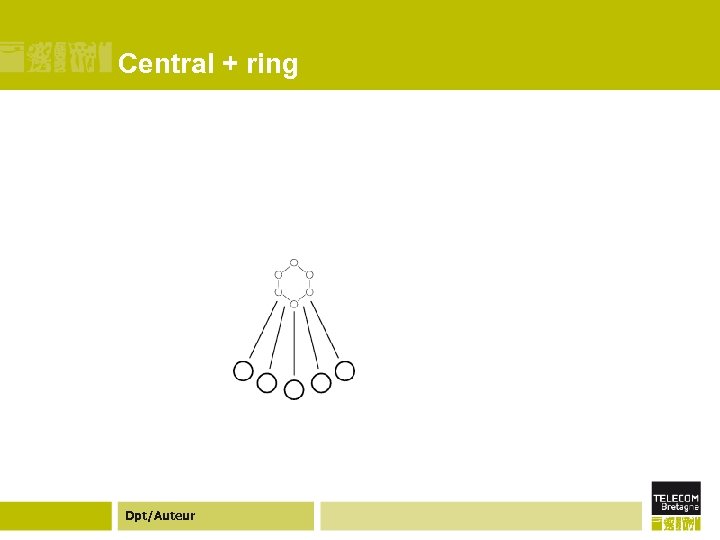
Central + ring Dpt/Auteur

Central + ring ¢ As mentioned above, serious web server applications often have a ring of servers for load balancing and failover. ¢ The server system itself is a ring, but the system as a whole (including the clients) is a hybrid: a centralized system where the server is itself a ring. The result is the simplicity of a centralized system (from the client's point of view) with the robustness of a ring. Dpt/Auteur
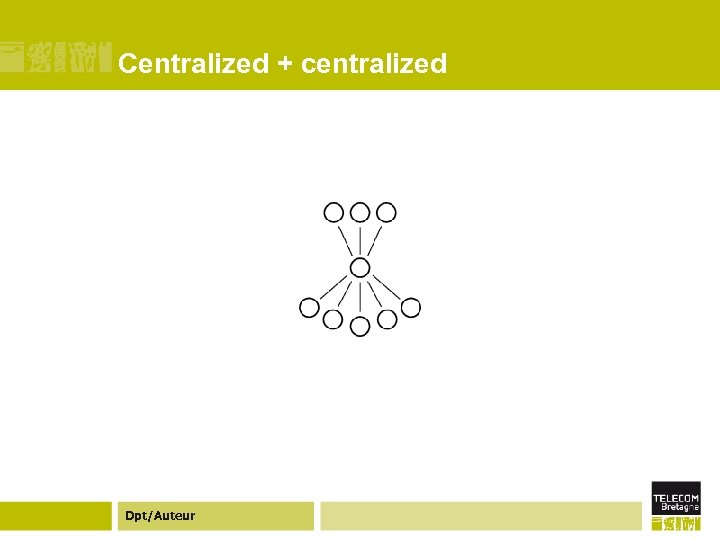
Centralized + centralized Dpt/Auteur
Centralized + centralized ¢ The server in a centralized system is itself often a client of one or more other servers. Stacking multiple centralized systems is the core of n-tier application frameworks. ¢ For example, when a web browser contacts a server, the software on that server may just be formatting results into HTML for presentation and itself calling to servers hosting business logic or data. ¢ Web services intermediaries such as Grand Central Networks also create several layers of centralized system. Centralized systems are often stacked as a way to compose function. Dpt/Auteur
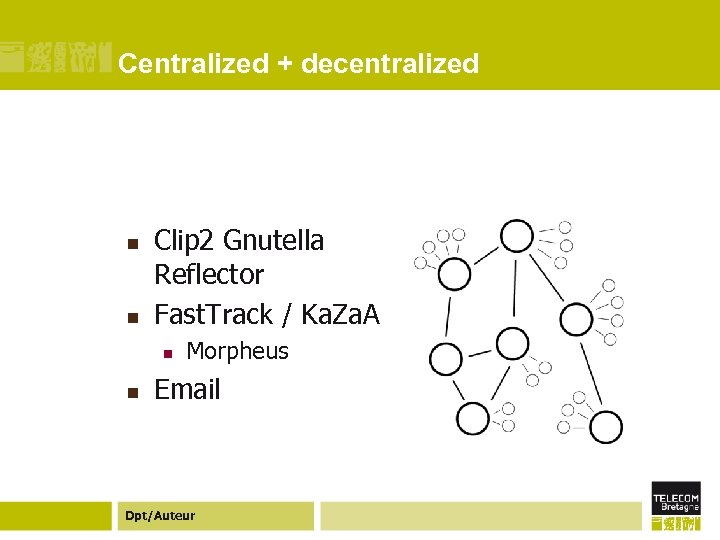
Centralized + decentralized n n Clip 2 Gnutella Reflector Fast. Track / Ka. Za. A n n Morpheus Email Dpt/Auteur

Strength and weakness ¢ Plenty of topologies to choose from ¢ What is each kind good for? ¢ Need a set of properties to measure Dpt/Auteur

Issues to be considered ¢ ¢ ¢ ¢ Manageability • How hard is it to keep working? Information coherence • How authoritative is info? (Auditing, non-repudiation) Extensibility • How easy is it to grow? Fault tolerance • How well can it handle failures? Security • How hard is it to subvert? Resistance to legal or political intervention • How hard is it to shut down? (Can be good or bad) Scalability • How big can it grow? Dpt/Auteur
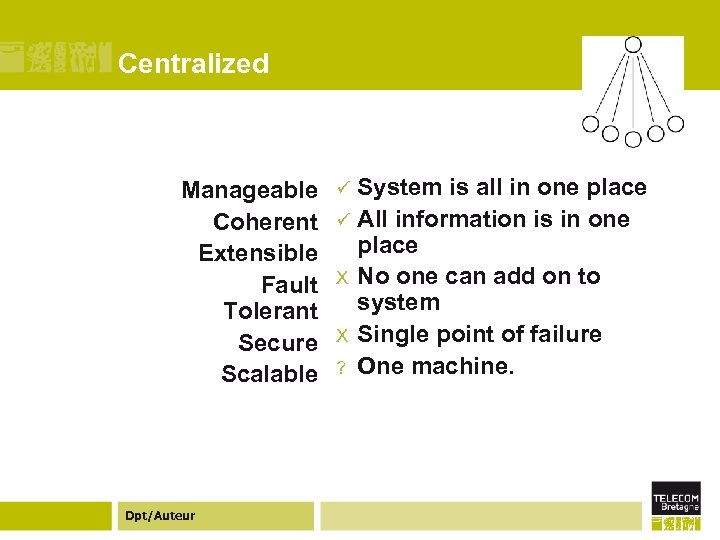
Centralized Manageable Coherent Extensible Fault Tolerant Secure Scalable Dpt/Auteur System is all in one place ü All information is in one place X No one can add on to system X Single point of failure ? One machine. ü
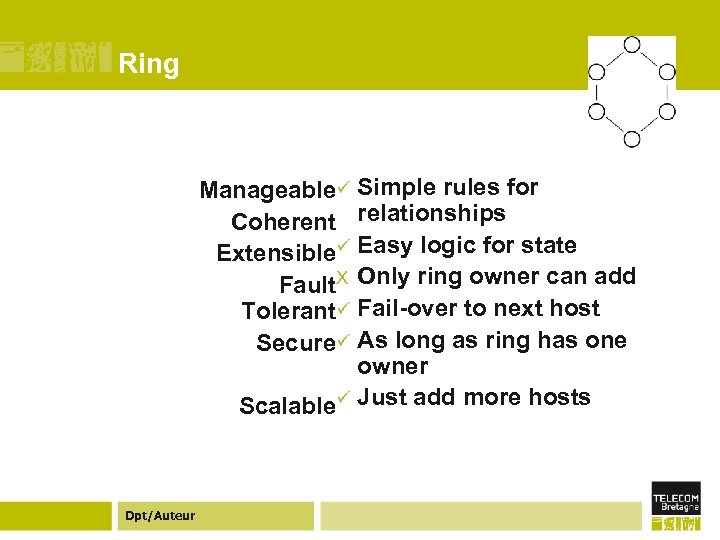
Ring Manageableü Simple rules for Coherent relationships Extensibleü Easy logic for state Fault. X Only ring owner can add Tolerantü Fail-over to next host Secureü As long as ring has one owner Scalableü Just add more hosts Dpt/Auteur

Hierarchical Manageable ½ Chain of authority Coherent ½ Cache consistency Extensible ½ Add more leaves, rebalance Fault ½ Root is vulnerable Tolerant X Too easy to spoof links Secure Scalable ü Hugely scalable – DNS Dpt/Auteur

Decentralized Manageable X Very difficult, many owners Coherent X Difficult, unreliable peers Extensible ü Anyone can join in! Fault Tolerant ü Redundancy Secure X Difficult, open research Scalable ? Theory – yes : Practice – no Dpt/Auteur

Centralized + Ring Manageable ü Just manage the ring Coherent ü As coherent as ring Extensible X No more than ring Fault ü Ring is a huge win Tolerant ü As secure as ring Secure ü Ring is a huge win Scalable Dpt/Auteur

Centralized + Decentralized Manageable X Same as decentralized Coherent ½ Better than decentralized Extensible ü Anyone can still join! Fault ü Plenty of redundancy Tolerant X Same as decentralized Secure ? Looking very hopeful Scalable Dpt/Auteur

Centralized vs. Decentralized ¢ Centralized is pretty good! • Manageable • Coherent • Security ¢ Decentralized is exciting • Extensible • Massive fault tolerance • Lawsuit-proof ¢ Scalability Dpt/Auteur is the big question
Conclusions ¢ Importance of regularity ¢ Impacts of the topology on the application code : • To communicate with other machines: routing • To broadcast • To deal with failure ¢ The application and the underlying topology are closely related ¢ The application can benefit of the topology and can rely on multiple ‘logical’ topologies Dpt/Auteur

Conclusions ¢ Centralized is easy to deal with • Major architecture for distributed systems • Combines well with rings ¢ Decentralized research is good, needs • Coherence, Manageability, Security • Scalability ¢ Hierarchical is overlooked ¢ Combining architectures is powerful Dpt/Auteur

Behavioral properties of the network ¢ Ideal nertwork does not : • Loose a message • Duplicate message • Alter the message content • Desequence messages • Provide bound for communication times ¢ But we have to deal with non perfect networks ! Dpt/Auteur
45b358f6134bc6153fae1ac736100838.ppt