e8827f6693da1bbe759d4cd1ec072bf2.ppt
- Количество слайдов: 20

Topics X. 509 PGP S/MIME Kerberos

Directory Authentication Framework • X. 509 is part of the ISO X. 500 directory standard. • used by S/MIME, SSL, IPSec, and others Important Components of X. 509 1) a standard certificate format 2) a standard scheme for implementing certificate authorities 3) standard authentication protocols 4) a digital signature “standard” • no particular cipher is dictated, but RSA is recommended • no particular hash is dictated.
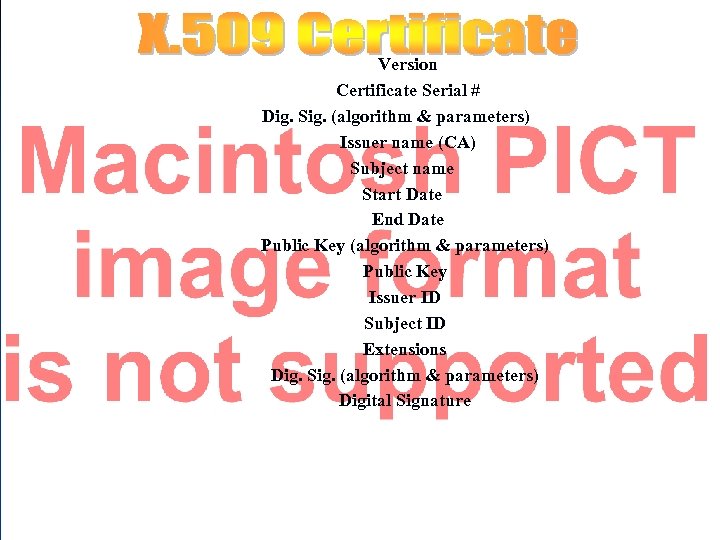
Version Certificate Serial # Dig. Sig. (algorithm & parameters) Issuer name (CA) Subject name Start Date End Date Public Key (algorithm & parameters) Public Key Issuer ID Subject ID Extensions Dig. Sig. (algorithm & parameters) Digital Signature
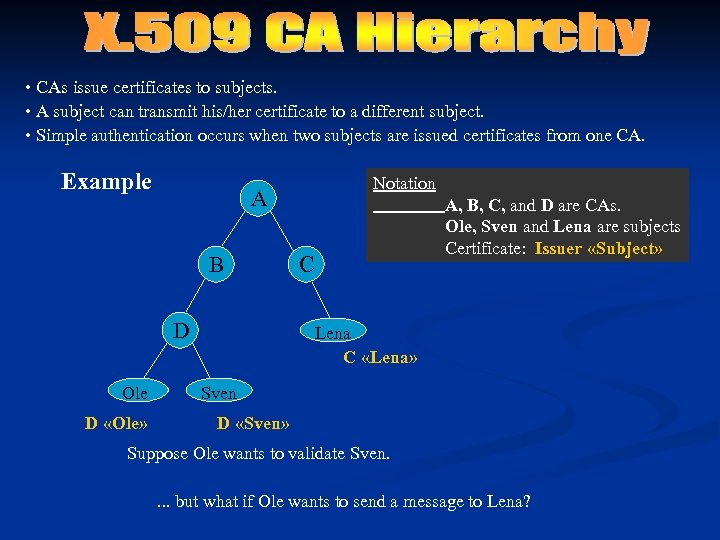
• CAs issue certificates to subjects. • A subject can transmit his/her certificate to a different subject. • Simple authentication occurs when two subjects are issued certificates from one CA. Example A B D Ole D «Ole» Notation A, B, C, and D are CAs. Ole, Sven and Lena are subjects Certificate: Issuer «Subject» C Lena C «Lena» Sven D «Sven» Suppose Ole wants to validate Sven. . but what if Ole wants to send a message to Lena?
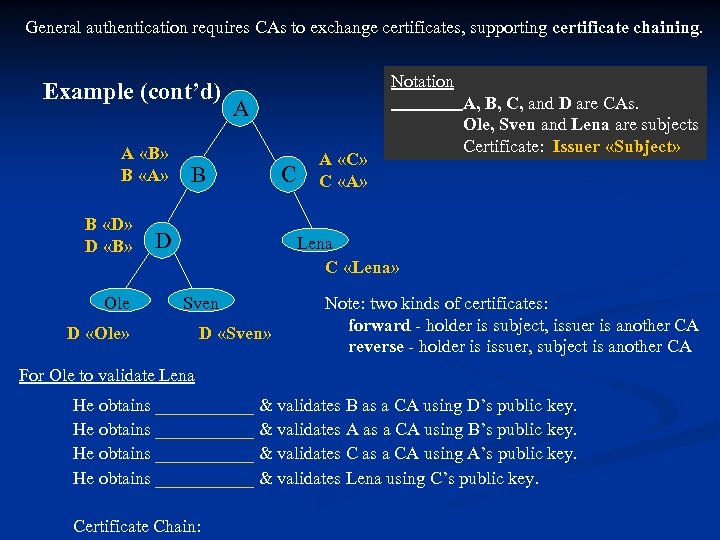
General authentication requires CAs to exchange certificates, supporting certificate chaining. Example (cont’d) A «B» B «A» B «D» D «B» Ole Notation A B D C A «C» C «A» A, B, C, and D are CAs. Ole, Sven and Lena are subjects Certificate: Issuer «Subject» Lena C «Lena» Sven D «Ole» D «Sven» Note: two kinds of certificates: forward - holder is subject, issuer is another CA reverse - holder is issuer, subject is another CA For Ole to validate Lena He obtains ______ & validates B as a CA using D’s public key. He obtains ______ & validates A as a CA using B’s public key. He obtains ______ & validates C as a CA using A’s public key. He obtains ______ & validates Lena using C’s public key. Certificate Chain:
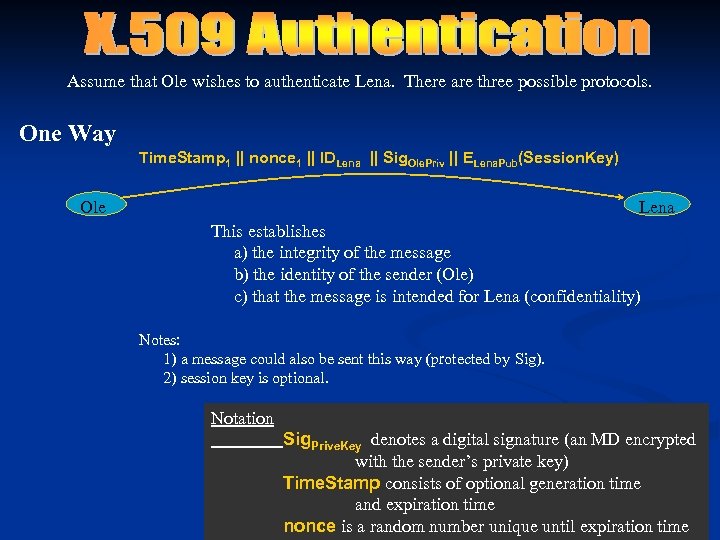
Assume that Ole wishes to authenticate Lena. There are three possible protocols. One Way Time. Stamp 1 || nonce 1 || IDLena || Sig. Ole. Priv || ELena. Pub(Session. Key) Ole Lena This establishes a) the integrity of the message b) the identity of the sender (Ole) c) that the message is intended for Lena (confidentiality) Notes: 1) a message could also be sent this way (protected by Sig). 2) session key is optional. Notation Sig. Prive. Key denotes a digital signature (an MD encrypted with the sender’s private key) Time. Stamp consists of optional generation time and expiration time nonce is a random number unique until expiration time
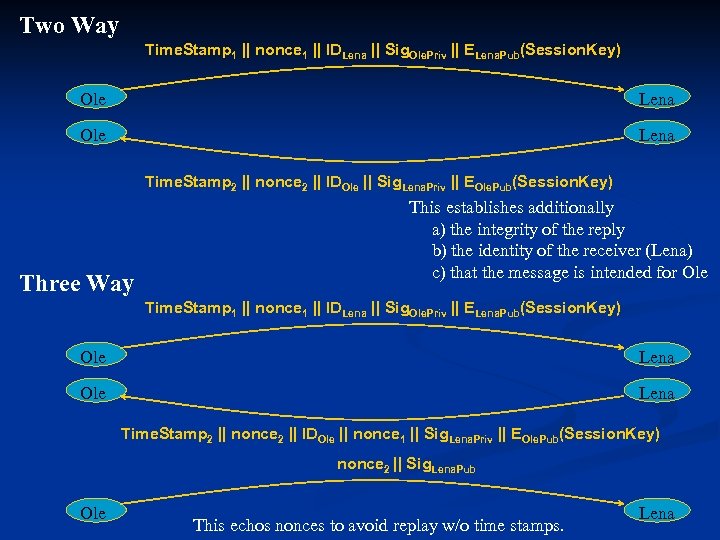
Two Way Time. Stamp 1 || nonce 1 || IDLena || Sig. Ole. Priv || ELena. Pub(Session. Key) Ole Lena Time. Stamp 2 || nonce 2 || IDOle || Sig. Lena. Priv || EOle. Pub(Session. Key) Three Way This establishes additionally a) the integrity of the reply b) the identity of the receiver (Lena) c) that the message is intended for Ole Time. Stamp 1 || nonce 1 || IDLena || Sig. Ole. Priv || ELena. Pub(Session. Key) Ole Lena Time. Stamp 2 || nonce 2 || IDOle || nonce 1 || Sig. Lena. Priv || EOle. Pub(Session. Key) nonce 2 || Sig. Lena. Pub Ole This echos nonces to avoid replay w/o time stamps. Lena

Brief History • 1991 - PGP created by Phil Zimmerman • widely-used secure email standard • 1996 purchased by Network Associates Ring of Trust • Each user maintains a trusted keyring (public keys) and an owned keyring (private keys). • Keys may be retrieved from a server or included at the end of a message. • Keys can be revoked by the owner. • Each key is signed by owner (and possibly others). • Trust is based on who signed the key. • Subject discretion ultimately determines who to trust.

Potential PGP Operations • create a random session key (for symmetric cipher) • encrypt/decrypt session key using public key (RSA or Diffie-Hellman) • encrypt/decrypt message using session key (IDEA, 3 DES or CAST-128) • generate & encrypt (or decrypt) MD (SHA-1) using private key • attach encrypted session key (as a digital signature) to a message • transmit message
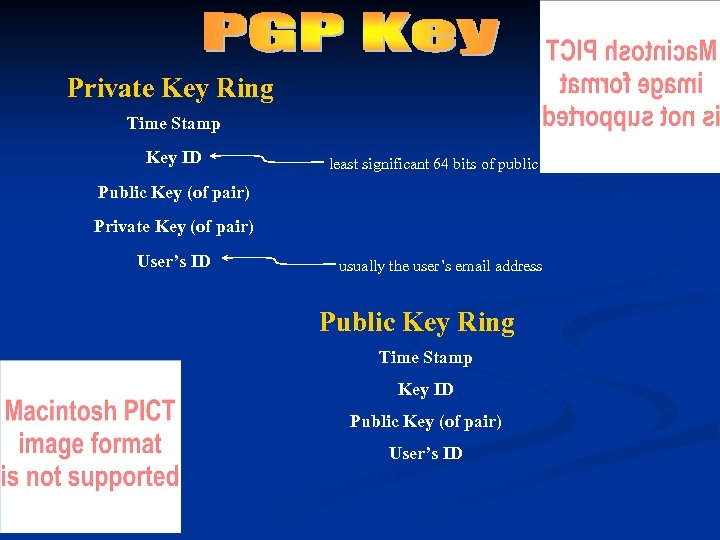
Private Key Ring Time Stamp Key ID least significant 64 bits of public key Public Key (of pair) Private Key (of pair) User’s ID usually the user’s email address Public Key Ring Time Stamp Key ID Public Key (of pair) User’s ID
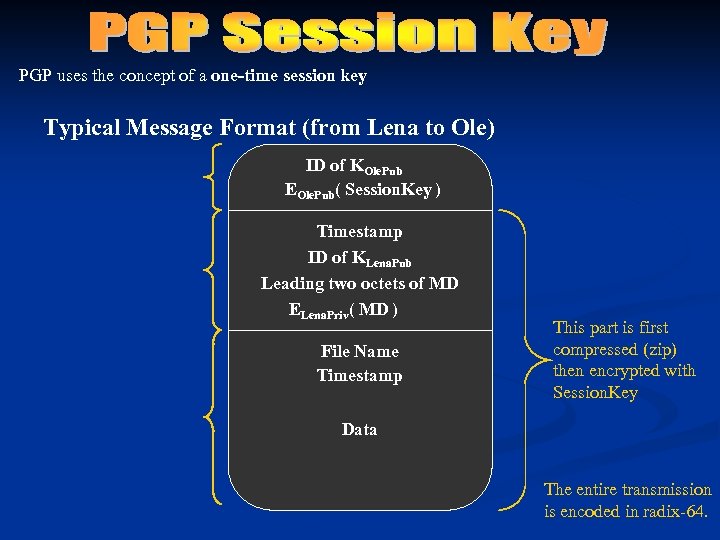
PGP uses the concept of a one-time session key Typical Message Format (from Lena to Ole) ID of KOle. Pub EOle. Pub( Session. Key ) Timestamp ID of KLena. Pub Leading two octets of MD ELena. Priv( MD ) File Name Timestamp This part is first compressed (zip) then encrypted with Session. Key Data The entire transmission is encoded in radix-64.

Why use a one-time (session) key?

S/MIME -- Secure / Multipurpose Internet Mail Extensions Originally developed by RSA Certificate Processing • Uses X. 509 v 3 certificates • Responsibility for maintaining certificates is local. • Certificates are signed by a Certificate Authority • CAs - Veri. Sign, GTE, Nortel, U. S. Postal Service Typical Functions • The client must generate keys. • A pair of generated keys are registered with a CA. • The CA supplies certificates in X. 509 format. • The client can maintain a list of trusted certificates.

Veri. Sign Certificates Class 1 Veri. Sign required unambiguous name and email address, PIN is emailed to user Web browsers, email Class 2 Veri. Sign does online database search and sends digital ID & PIN to postal address online subscriptions, secure email Client must prove identity via notary public or appear in person banking, secure database, membership-based services, e-commerce Class 3 Algorithms • must support SHA-1 (should support MD 5 for backward compatibility) • must support DSS (should support RSA-512 and RSA-1024 for digital signatures) • must support RC 2/40 with one-time key and should support 3 DES • session key encryption with Diffie-Hellman is preferred (RSA is possible)

• Kerberos is an authentication system - authenticating users and services. • It was originally developed as part of Project Athena - MIT. • Kerberos relies upon a centralized Kerberos server per realm. • Multi-realm communication is also possible. • A kerberos server must contain a database of user IDs and hashed passwords. • A kerberos server must share a secret key with registered servers. • The client can maintain a list of trusted certificates.
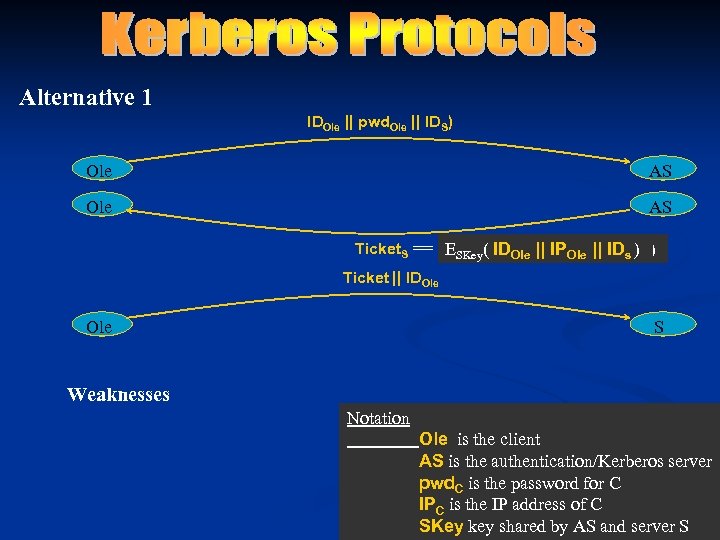
Alternative 1 IDOle || pwd. Ole || IDS) Ole AS Ticket. S == E( ID|| IPOle || IDs, IDs )S ) ESKey Ole || IPOle || key Ticket || IDOle S Weaknesses Notation Ole is the client AS is the authentication/Kerberos server pwd. C is the password for C IPC is the IP address of C SKey key shared by AS and server key. S key shared by AS and server SS
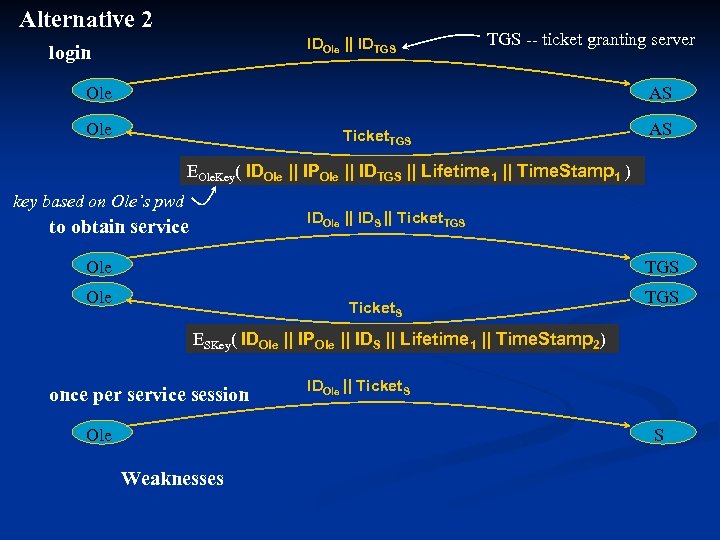
Alternative 2 IDOle || IDTGS login TGS -- ticket granting server Ole AS Ole Ticket. TGS AS EOle. Key( IDOle || IPOle || IDTGS || Lifetime 1 || Time. Stamp 1 ) key based on Ole’s pwd IDOle || IDS || Ticket. TGS to obtain service Ole TGS Ole Ticket. S TGS ESKey( IDOle || IPOle || IDS || Lifetime 1 || Time. Stamp 2) once per service session Ole IDOle || Ticket. S S Weaknesses
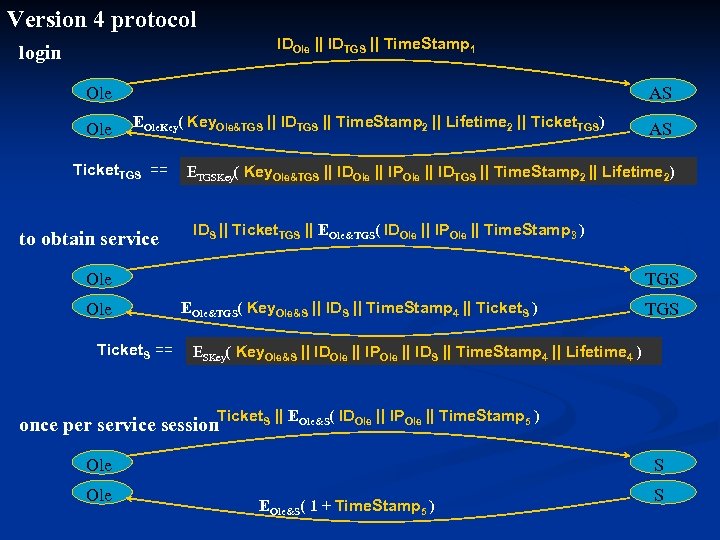
Version 4 protocol IDOle || IDTGS || Time. Stamp 1 login Ole AS EOle. Key( Key. Ole&TGS || IDTGS || Time. Stamp 2 || Lifetime 2 || Ticket. TGS) Ticket. TGS == to obtain service ETGSKey( Key. Ole&TGS || IDOle || IPOle || IDTGS || Time. Stamp 2 || Lifetime 2) IDS || Ticket. TGS || EOle&TGS( IDOle || IPOle || Time. Stamp 3 ) Ole Ticket. S == AS TGS EOle&TGS( Key. Ole&S || IDS || Time. Stamp 4 || Ticket. S ) TGS ESKey( Key. Ole&S || IDOle || IPOle || IDS || Time. Stamp 4 || Lifetime 4 ) once per service session. Ticket. S || EOle&S( IDOle || IPOle || Time. Stamp 5 ) Ole S EOle&S( 1 + Time. Stamp 5 ) S
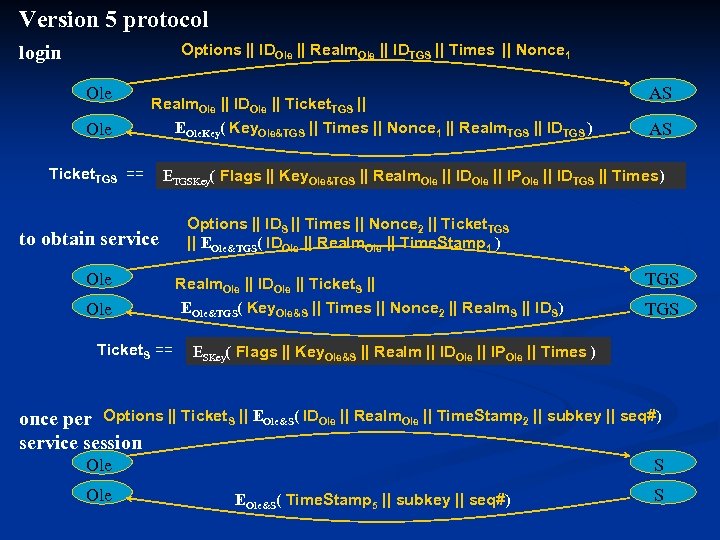
Version 5 protocol Options || IDOle || Realm. Ole || IDTGS || Times || Nonce 1 login Ole Realm. Ole || IDOle || Ticket. TGS || EOle. Key( Key. Ole&TGS || Times || Nonce 1 || Realm. TGS || IDTGS ) Ticket. TGS == AS AS ETGSKey( Flags || Key. Ole&TGS || Realm. Ole || IDOle || IPOle || IDTGS || Times) to obtain service Ole Ticket. S == Options || IDS || Times || Nonce 2 || Ticket. TGS || EOle&TGS( IDOle || Realm. Ole || Time. Stamp 1 ) Realm. Ole || IDOle || Ticket. S || EOle&TGS( Key. Ole&S || Times || Nonce 2 || Realm. S || IDS) TGS ESKey( Flags || Key. Ole&S || Realm || IDOle || IPOle || Times ) once per Options || Ticket. S || EOle&S( IDOle || Realm. Ole || Time. Stamp 2 || subkey || seq#) service session Ole S EOle&S( Time. Stamp 5 || subkey || seq#) S
• Version 4 required the use of DES - Version 5 supports the use of algorithm tags • Version 4 used an 8 -bit lifetime - restricted to approx. 21 hrs. - Version 5 more flexible. • Version 5 also adds realms • Both versions are somewhat vulnerable to password attacks, because keys are based on passwords.
e8827f6693da1bbe759d4cd1ec072bf2.ppt