13430865d8f6a1360c2484b298c5129b.ppt
- Количество слайдов: 74

Top Web App Attack Methods and How to Combat Them Dennis Hurst, SPI Dynamics Schedule: 9: 30~10: 00 Breakfast 10: 00~11: 30 Presentation 11: 30~12: 00 Break / Demo

Agenda § § § Who is SPI Dynamics The Evolution of Web Applications and Why They Need to Be Secured Web Application Vulnerabilities in Depth Managing Web Application Vulnerabilities Closing and Q&A SPI Dynamics Confidential
SPI Dynamics § The expert in web application security testing and enterprise security risk management § Established market and thought leader § Introduction of product line for application lifecycle and AMP § Multiple patent applications completed and pending § Co-creator of AVDL interoperability standard and other industry leading consortiums § Web. Inspect assesses the security of applications and web services throughout the application lifecycle § Development § QA § Production § Audit § SPI Labs § Research and development group § Recognized as leading authority on web application security SPI Dynamics Confidential
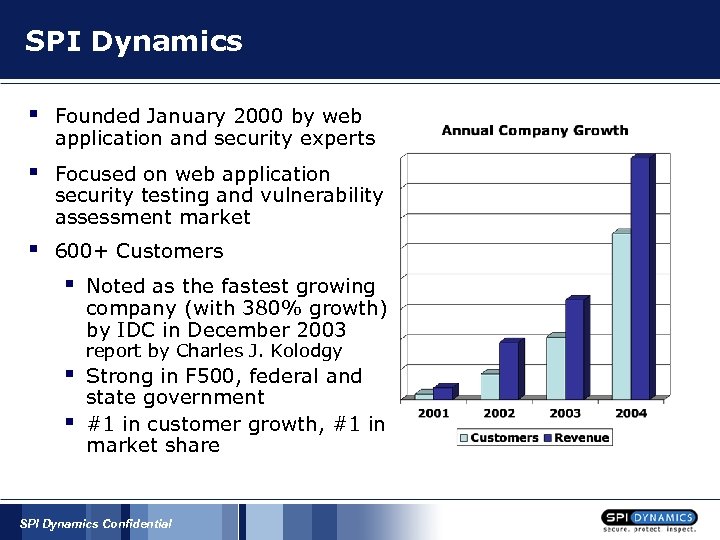
SPI Dynamics § Founded January 2000 by web application and security experts § Focused on web application security testing and vulnerability assessment market § 600+ Customers § § § Noted as the fastest growing company (with 380% growth) by IDC in December 2003 report by Charles J. Kolodgy Strong in F 500, federal and state government #1 in customer growth, #1 in market share SPI Dynamics Confidential

Selected Commercial Customers SPI Dynamics Confidential

Selected Government Customers SPI Dynamics Confidential
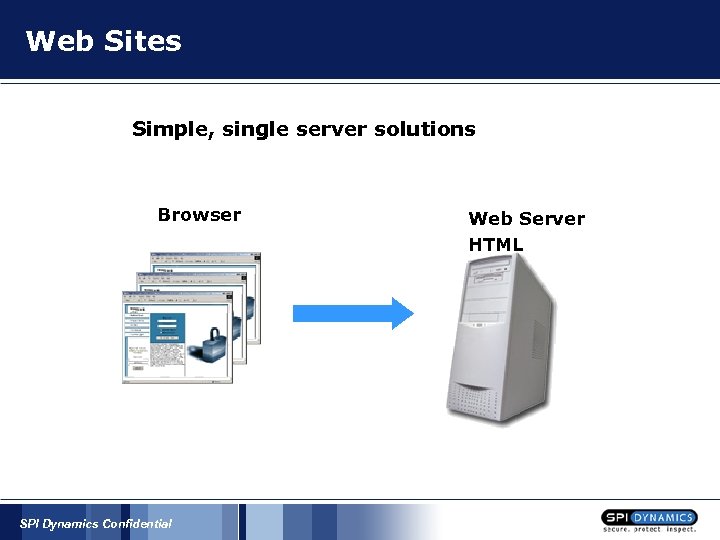
Web Sites Simple, single server solutions Browser SPI Dynamics Confidential Web Server HTML
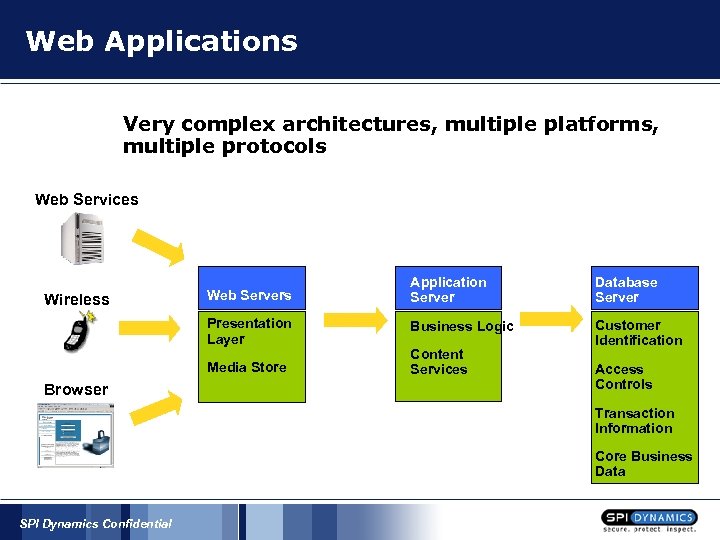
Web Applications Very complex architectures, multiple platforms, multiple protocols Web Services Application Server Database Server Presentation Layer Wireless Web Servers Business Logic Customer Identification Media Store Browser Content Services Access Controls Transaction Information Core Business Data SPI Dynamics Confidential
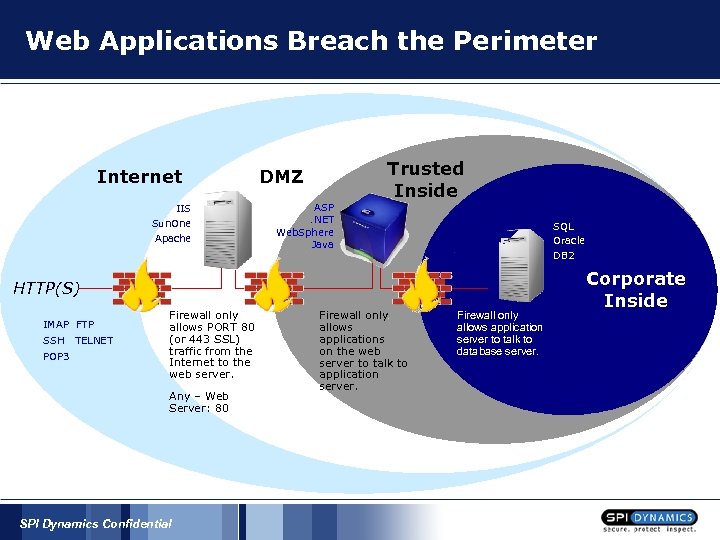
Web Applications Breach the Perimeter Internet IIS Sun. One Apache Trusted Inside DMZ ASP. NET Web. Sphere Java SQL Oracle DB 2 HTTP(S) IMAP FTP SSH POP 3 TELNET Firewall only allows PORT 80 (or 443 SSL) traffic from the Internet to the web server. Any – Web Server: 80 SPI Dynamics Confidential Firewall only allows applications on the web server to talk to application server. Firewall only allows application server to talk to database server. Corporate Inside

Part Two Web Application Vulnerabilities in Depth § § Why Web Application Vulnerabilities Occur Web Application Attack Methodologies SPI Dynamics Confidential

Why Web Application Risks Occur Security Professionals Don’t Know The Applications “As a Network Security Professional, I don’t know how my companies web applications are supposed to work so I deploy a protective solution…but don’t know if it’s protecting what it’s supposed to. ” SPI Dynamics Confidential The Web Application Security Gap Application Developers and QA Professionals Don’t Know Security “As an Application Developer, I can build great features and functions while meeting deadlines, but I don’t know how to develop my web application with security as a feature. ”
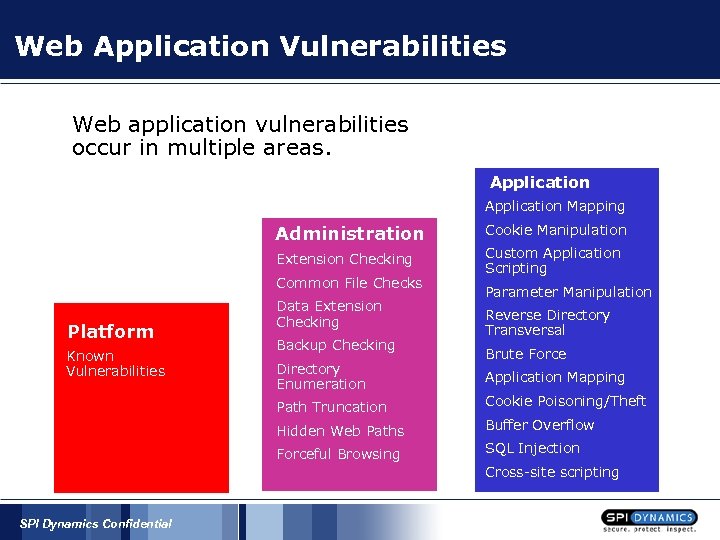
Web Application Vulnerabilities Web application vulnerabilities occur in multiple areas. Application Mapping Administration Extension Checking Common File Checks Platform Known Vulnerabilities Data Extension Checking Backup Checking Directory Enumeration Cookie Manipulation Custom Application Scripting Parameter Manipulation Reverse Directory Transversal Brute Force Application Mapping Path Truncation Cookie Poisoning/Theft Hidden Web Paths Buffer Overflow Forceful Browsing SQL Injection Cross-site scripting SPI Dynamics Confidential
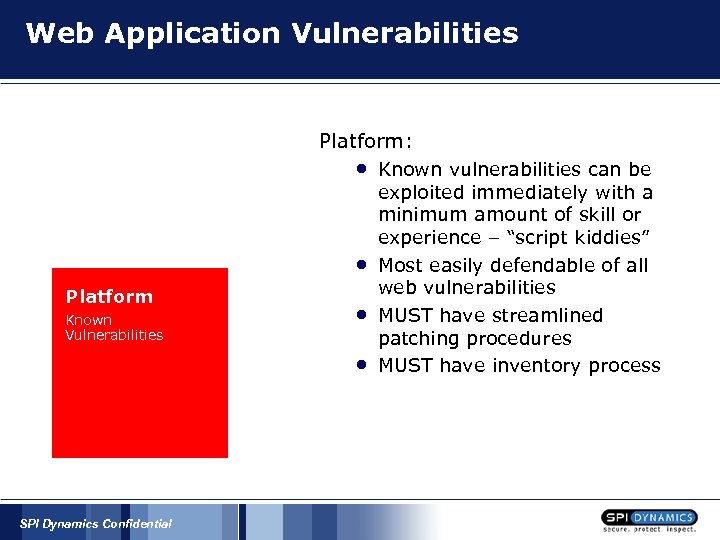
Web Application Vulnerabilities Platform: • • Platform Known Vulnerabilities • • SPI Dynamics Confidential Known vulnerabilities can be exploited immediately with a minimum amount of skill or experience – “script kiddies” Most easily defendable of all web vulnerabilities MUST have streamlined patching procedures MUST have inventory process
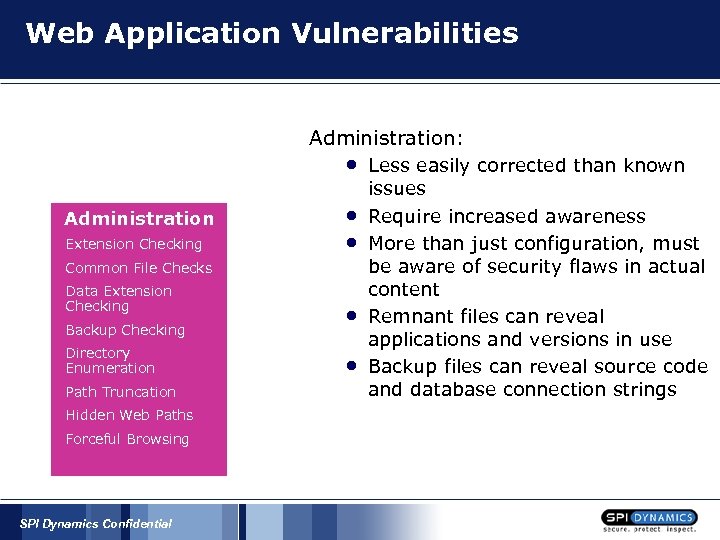
Web Application Vulnerabilities Administration: • Administration Extension Checking • • Common File Checks Data Extension Checking Backup Checking Directory Enumeration Path Truncation Hidden Web Paths Forceful Browsing SPI Dynamics Confidential • • Less easily corrected than known issues Require increased awareness More than just configuration, must be aware of security flaws in actual content Remnant files can reveal applications and versions in use Backup files can reveal source code and database connection strings

Common file vulnerabilities § Robots. txt § shows files that the administrator does not want search engines to crawl § Don’t show confidential information in this file SPI Dynamics Confidential

Common file vulnerabilities § Web server logs & Stats folders § A web accessible web server log or Stats folder will show WAY to much information about your web site SPI Dynamics Confidential
Demonstration 1 Common file vulnerabilities
Configuration files § § Remnant files are any files that are left on a web server that are not in use or part of the web based application. § Remnant files can include backup files, documentation files, default files (like samples) or any other file that is not part of the production system. Remnant files solutions § Never leave unnecessary files on a web server (i. e. Web. config. old) § Assume all files on a web server will be seen by a hacker. § Encrypt secure information in configuration files SPI Dynamics Confidential
Demonstration 2 Configuration file vulnerabilities
Web Application Vulnerabilities Application Programming: Application Mapping Cookie Manipulation Custom Application Scripting Parameter Manipulation Reverse Directory Transversal Brute Force Application Mapping Cookie Poisoning/ Theft Buffer Overflow SQL Injection Cross-site scripting SPI Dynamics Confidential • Common coding techniques do not necessarily include security • Input is assumed to be valid, but not Administration tested • Inappropriate file calls can reveal source code and system files • Unexamined input from a browser can inject scripts into page for replay against later visitors • Unhandled error messages reveal application and database structures • Unchecked database calls can be ‘piggybacked’ with a hacker’s own database call, giving direct access to business data through a web browser

SQL Injection
SQL Injection § Cause: Using user provided data to build a SQL Statement w/o validating the data first § Goal: § Pass a SQL command to the web based application and have that command executed on the database server § Use the exploit to steal data or damage/alter the database. SPI Dynamics Confidential
SQL Injection § Demo § Browser based § HTTP Based § Automated SQL Injection § Blind SQL Injection SPI Dynamics Confidential

SQL Injection – Solution § Use parameterized queries cnn = new Sql. Connection(…database connection information here…); cmd = new Sql. Command("SELECT First. Name, Last. Name from Users “ + "WHERE User. Name = @uid AND password = @passwd", cnn); cmd. Parameters. Add("@uid", Sql. Db. Type. Var. Char, 100). Value=uid; cmd. Parameters. Add("@passwd", Sql. Db. Type. Var. Char, 100). Value = passwd; cnn. Open(); § § Trap your Errors!!! Don’t let the environment Use Stored Procedures Validate User Input Turn off default error messages SPI Dynamics Confidential

Federal Trade Commission investigates Guess Inc. § “Guess Settles with FTC over Cyber Security Snafu”, June 2003 by Kevin Poulson for Security. Focus § “ Guess. com was open to an "SQL injection attack, " permitting anyone able to construct a properly-crafted URL to pull down every name, credit card number and expiration date in the site's customer database -- over 200, 000 in all …The episode prompted a year-long FTC investigation into alleged deceptive trade practices by Guess “ § "Consumers have every right to expect that a business that says it's keeping personal information secure is doing exactly that, " said Howard Beales, Director of the FTC's consumer protection bureau, in a press release. "It's not just good business, it's the law. " SPI Dynamics Confidential

Google Hacking

Google Hacking § § Find vulnerable sites using google (Old method – new life) Example Search Queries § “filetype: mdb inurl: admin” – 180 results § “Filetype: xls inurl: admin” – 14, 100 results § “ORA-00921: unexpected end of SQL command” – 3, 470 results § “allintitle: Netscape Enterprise Server Home Page” – 431 results SPI Dynamics Confidential
Google Hacking § § § Take this method a step further and use it to narrow your attack victims. “inurl: id= filetype: asp site: gov” – 572, 000 results “inurl: id= filetype: asp site: com” – 7, 150, 000 results “inurl: id= filetype: asp site: org” – 3, 240, 000 results Use this list as a baseline for identifying SQL injection vulnerabilities SPI Dynamics Confidential
Google Hacking § § § Take this method a step further and use it to narrow your attack victims. “inurl: id= filetype: asp site: gov” – 572, 000 results “inurl: id= filetype: asp site: com” – 7, 150, 000 results “inurl: id= filetype: asp site: org” – 3, 240, 000 results Use this list as a baseline for identifying SQL injection vulnerabilities SPI Dynamics Confidential
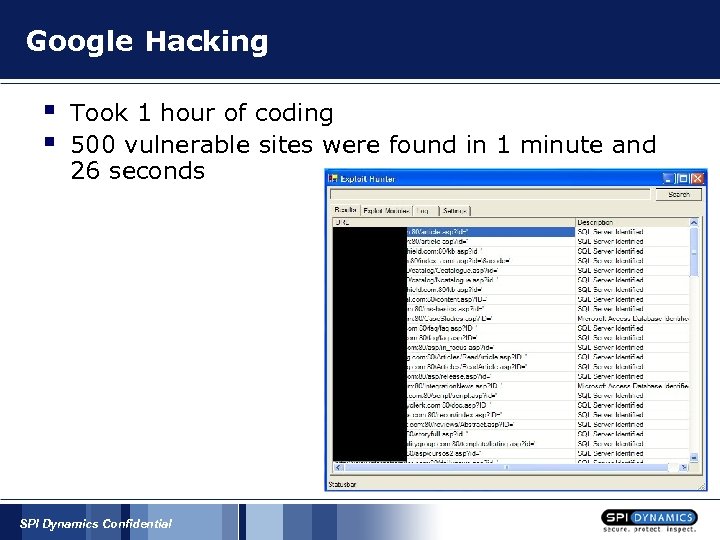
Google Hacking § § Took 1 hour of coding 500 vulnerable sites were found in 1 minute and 26 seconds SPI Dynamics Confidential
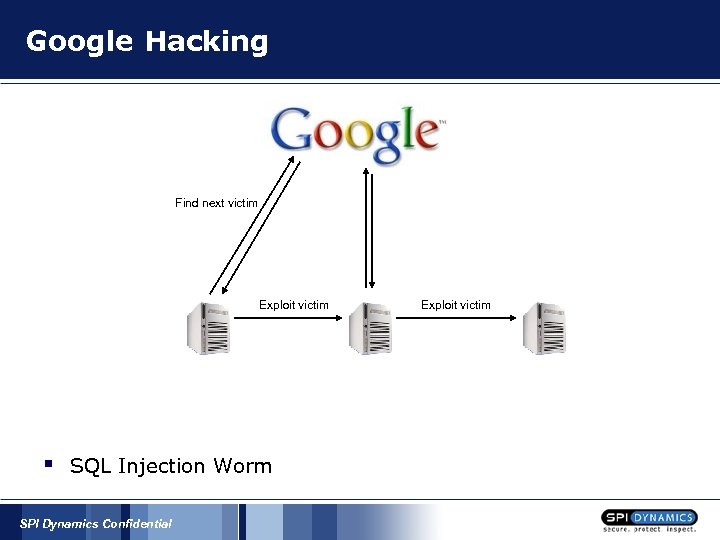
Google Hacking Find next victim Exploit victim § SQL Injection Worm SPI Dynamics Confidential Exploit victim

Session Hijacking
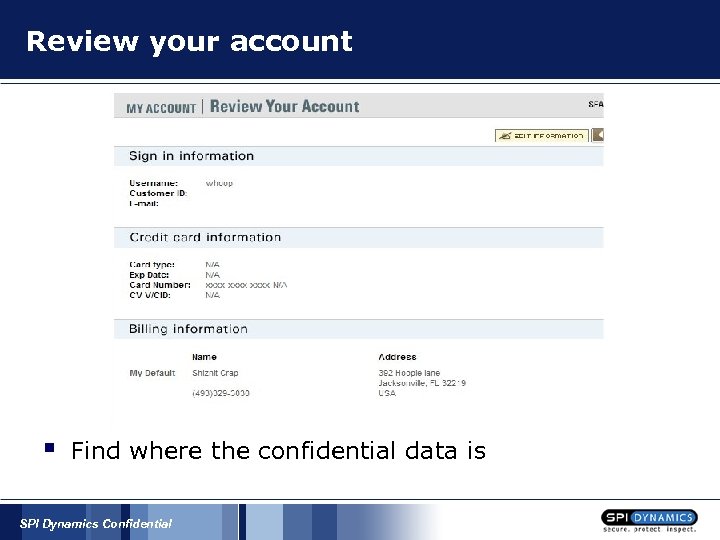
Review your account § Find where the confidential data is SPI Dynamics Confidential
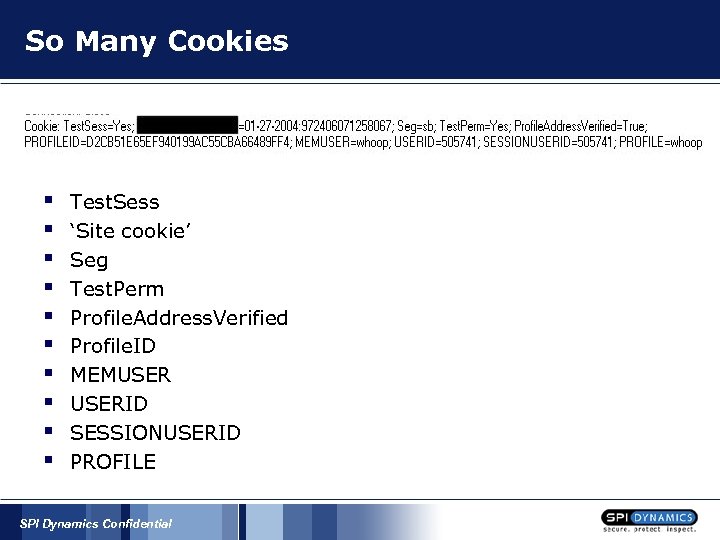
So Many Cookies § § § § § Test. Sess ‘Site cookie’ Seg Test. Perm Profile. Address. Verified Profile. ID MEMUSERID SESSIONUSERID PROFILE SPI Dynamics Confidential
§ Eliminate each one until the ones that matter are left § § § In this case ‘SESSIONUSERID=505741’ Is the number incremental? Keep everything the same except decrement the number – ‘SESSIONUSERID=505740’ SPI Dynamics Confidential

Phishing

Phishing Attacks In computing, phishing is the fraudulent acquisition, through deception, of sensitive personal information such as passwords and credit card details, by masquerading as someone trustworthy with a real need for such information. The term was coined in the mid 1990's by crackers attempting to steal AOL accounts. An attacker would pose as an AOL staff member and send an instant message to a potential victim. The message would ask the victim to reveal his or her password, for instance to "verify your account" or to "confirm billing information". Once the victim gave over the password, the attacker could access the victim's account and use it for criminal purposes, such as spamming. SPI Dynamics Confidential Source: www. wikipedia. org

Phishing Defined § § The word "phishing" comes from the analogy that Internet scammers are using email lures to "fish" for passwords and financial data from the sea of Internet users. The term was coined in the 1996 timeframe by hackers who were stealing America On-Line accounts. The first mention on the Internet of phishing is on the alt. 2600 hacker newsgroup in January 1996. Over the years, phishing attacks grew from simply stealing AOL dialup accounts into a more sinister criminal enterprise. (source: www. antiphishing. org) SPI Dynamics Confidential

Phishing Stats § § Number of active phishing sites reported in January: 2560 Average monthly growth rate in phishing sites July through January: 28% SPI Dynamics Confidential (source: http: //antiphishing. org/APWG_Phishing_Activity_Report-January 2005. pdf )
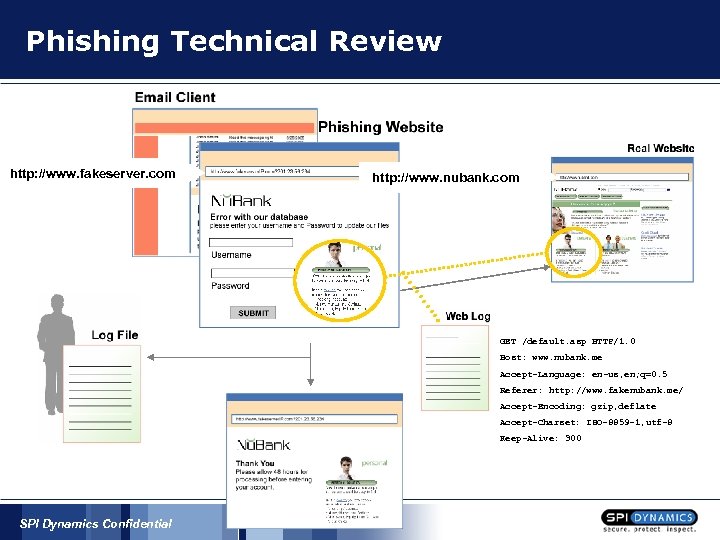
Phishing Technical Review http: //www. fakeserver. com http: //www. nubank. com GET /default. asp HTTP/1. 0 Host: www. nubank. me Accept-Language: en-us, en; q=0. 5 Referer: http: //www. fakenubank. me/ Accept-Encoding: gzip, deflate Accept-Charset: ISO-8859 -1, utf-8 Keep-Alive: 300 SPI Dynamics Confidential

Avoiding Phishing Attacks § § Companies should NEVER send an email that asks users to log in and change their passwords via an embedded link. This policy MUST be communicated to end users. When critical account changes are made send a verification email and lock the account until the change is verified. Send a notification email to users when significant transactions are made. SPI Dynamics Confidential
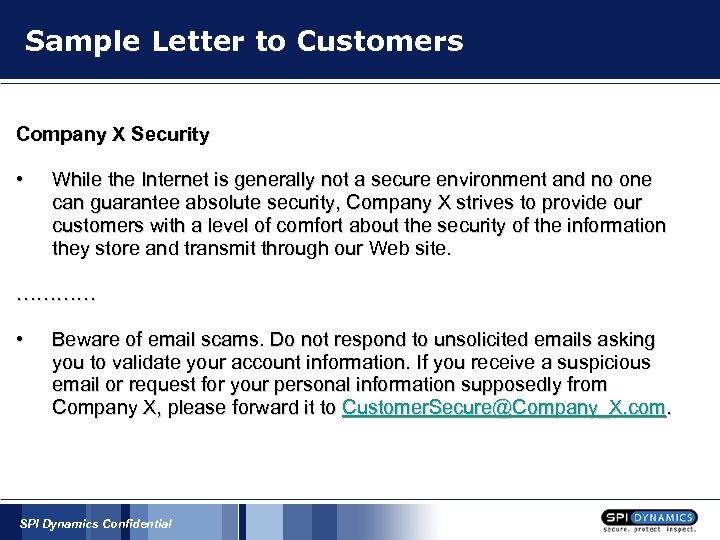
Sample Letter to Customers Company X Security • While the Internet is generally not a secure environment and no one can guarantee absolute security, Company X strives to provide our customers with a level of comfort about the security of the information they store and transmit through our Web site. ………… • Beware of email scams. Do not respond to unsolicited emails asking you to validate your account information. If you receive a suspicious email or request for your personal information supposedly from Company X, please forward it to Customer. Secure@Company_X. com. SPI Dynamics Confidential

Identifying Phishing attacks § § § Bounced emails, LOTS of bounces § Phishers will send “phishing spam” Notification from customers Referer headers being sent from unknown or malicious Web sites § Referer: http: //www. fakenubank. me/ § Applications can track referer headers sent by users‘ browsers, detect Phishing attacks and notify the user of the possible attack SPI Dynamics Confidential

Responding to Phishing attacks 1. Attempt to determine who has been compromised by the attack and take appropriate action 2. Find out who is hosting the phishing Web site § Use: http: //www. samspade. org 3. Send a “cease and desist” letter to the ISP that is hosting the phishing site 4. Contact Federal officials (FBI) SPI Dynamics Confidential

Session Summary § § § Session Hijacking and Phishing attacks are both ways that criminals attempt to steal users’ credentials and possibly money Minimizing the risk of these attacks requires understanding how your application works and recognizing the signs of a potential attack Responding to an ongoing attack is possible but will require some amount of up-front work to be prepared SPI Dynamics Confidential

Phishing Resources Individuals www. ic 3. gov – Internet Crime Complaint Center § Established as a partnership between the FBI and the National White Collar Crime Center to provide a way to receive Internet-related criminal complaints and to research, develop and refer the criminal complaints to law enforcement agencies for any investigation they deem to be appropriate. SPI Dynamics Confidential

Phishing Resources Companies § § § www. fbi. gov – Federal Bureau of Investigation § Ask for the “Cyber Crime Officer” § Contact the FBI to report a Phishing attack www. antiphishing. org – Anti-Phishing Working Group § The Anti-Phishing Working Group (APWG) is the global pan-industrial and law enforcement association focused on eliminating the fraud and identity theft that result from phishing, pharming and email spoofing of all types § Excellent resource for Phishing information www. digitalphishnet. org – Digital Phish. Net § The Digital Phish. Net is a joint enforcement initiative between industry and law enforcement designed to ensnare those who perpetrate phishing attacks § Requires specific resources within a company SPI Dynamics Confidential
Cross Site Scripting (XSS)

Cross Site Scripting - XSS § § § Cross-site scripting (also know as XSS or CSS) occurs when dynamically generated web pages display input that is not property validated. A user passes input in the form of a parameter to the web server. The web server returns the user provided input back to the user without proper encoding. SPI Dynamics Confidential
Demonstration 4 Cross site scripting (XSS) example (login. aspx)
XSS solutions § Fix § Use the validate. Request=false cautiously § Server. HTMLEncode SPI Dynamics Confidential
Part Three Managing and Detecting Web Application Vulnerabilities § § Changing the application development process Assess in depth to defend in depth! Manual vs. automated approach Web. Inspect’s approach SPI Dynamics Confidential
How the Industry Has Changed 1990’s § Zero Liability 2004 § § § SPI Dynamics Confidential Federal Trade Commission Regulatory requirements § GLB § HIPAA § SOX § CA 1386 Legal precedents

Testing and verifying § § Web Application attacks come from many vectors Application development is by nature an error (bug) prone process. Some bugs will have a security aspect. Testing for security bugs is critical. SPI Dynamics Confidential
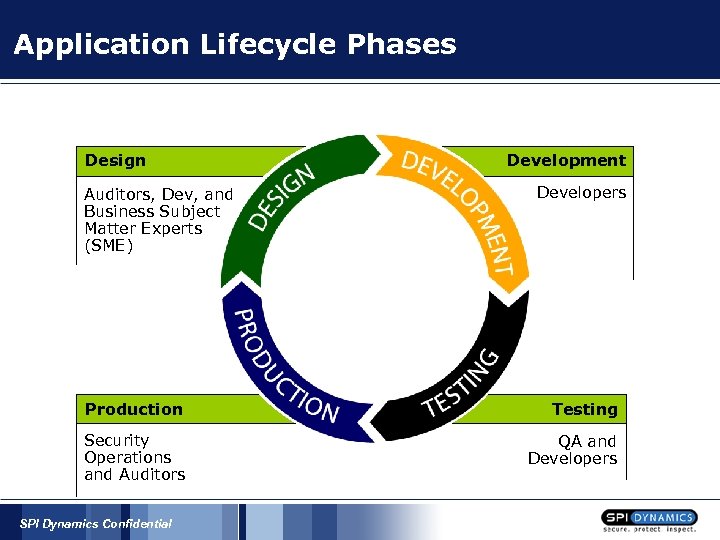
Application Lifecycle Phases Design Auditors, Dev, and Business Subject Matter Experts (SME) Development Developers Production Testing Security Operations and Auditors QA and Developers SPI Dynamics Confidential
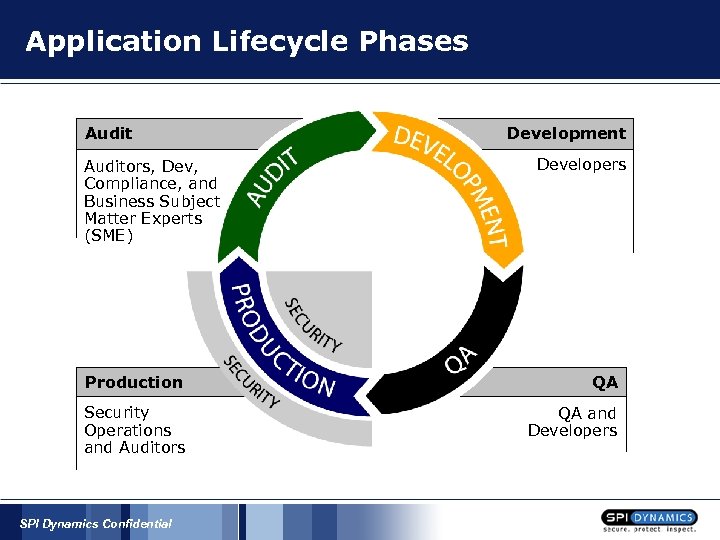
Application Lifecycle Phases Auditors, Dev, Compliance, and Business Subject Matter Experts (SME) Development Developers Production QA Security Operations and Auditors QA and Developers SPI Dynamics Confidential
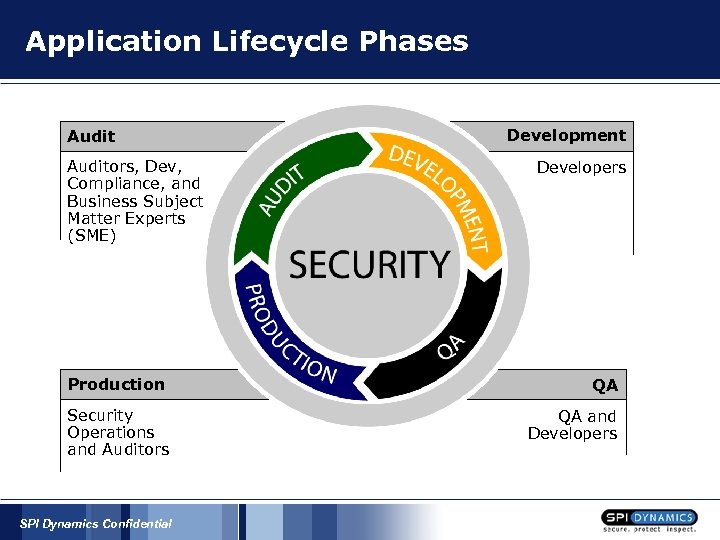
Application Lifecycle Phases Auditors, Dev, Compliance, and Business Subject Matter Experts (SME) Development Developers Production QA Security Operations and Auditors QA and Developers SPI Dynamics Confidential

Secure Software Development Lifecycle A Microsoft case study
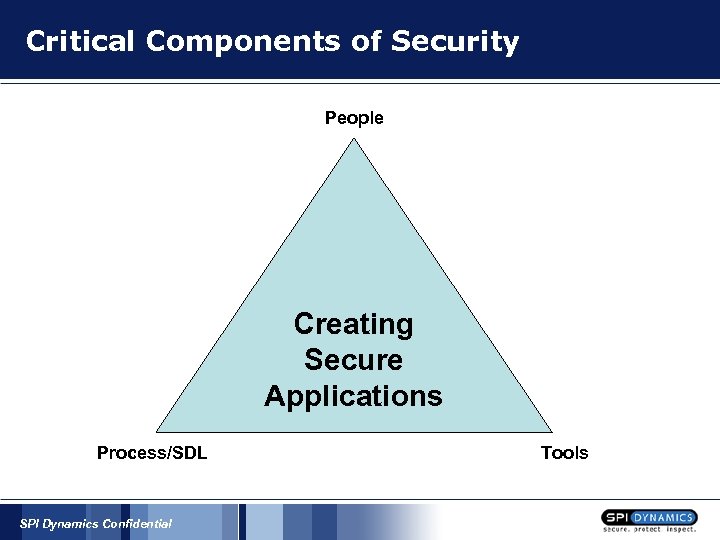
Critical Components of Security People Creating Secure Applications Process/SDL SPI Dynamics Confidential Tools

People Providing Developers with the Guidance to Create Secure Applications SPI Dynamics Confidential
MSDN Developer Security Center http: //msdn. microsoft. com/security/ SPI Dynamics Confidential

Process/SDL Security Cannot be an Afterthought SPI Dynamics Confidential

Security Development Lifecycle (SDL) A PROCESS by which Microsoft develops software and defines security requirements and milestones § Mandatory for products that are exposed to meaningful security risk § Evolving and new factors, such as privacy, are being added *Steve Lipner, Director of Security Engineering Strategy, Microsoft SPI Dynamics Confidential
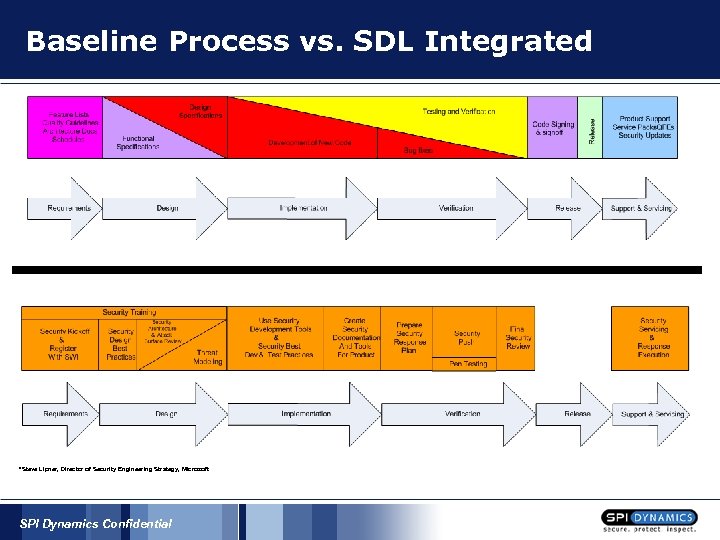
Baseline Process vs. SDL Integrated *Steve Lipner, Director of Security Engineering Strategy, Microsoft SPI Dynamics Confidential
Accountability and Incentives § Almost 40 percent of developers say that their companies do not think it is “very important” to write secure applications § CIOs, CTOs, CSOs, and ITDMs say it is very important § Current incentives on performance and ship dates § Must be driven top-down SPI Dynamics Confidential
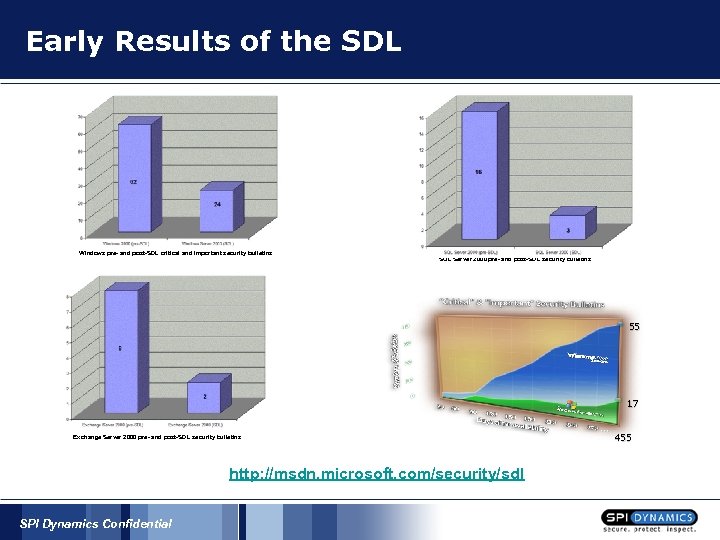
Early Results of the SDL Windows pre- and post-SDL critical and important security bulletins SQL Server 2000 pre- and post-SDL security bulletins 55 17 Exchange Server 2000 pre- and post-SDL security bulletins http: //msdn. microsoft. com/security/sdl SPI Dynamics Confidential 455
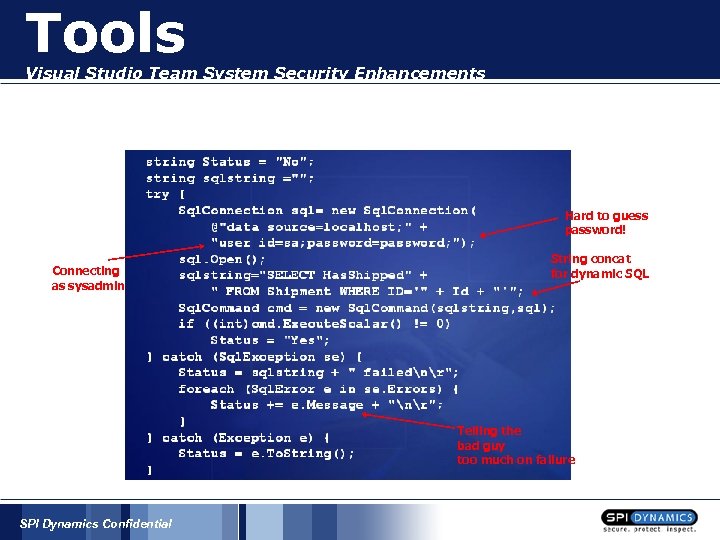
Tools Visual Studio Team System Security Enhancements Hard to guess password! Connecting as sysadmin String concat for dynamic SQL Telling the bad guy too much on failure SPI Dynamics Confidential

Summary § People § Guidance § Training § Accountability § Process § Security is an evolving challenge § SDL process has proven effective at improving software security § As operating system security improves, attackers will move “up the stack” § Be ready to meet the challenge § § http: //msdn. microsoft. com/security/sdl Tools § People cannot find all the defects SPI Dynamics Confidential
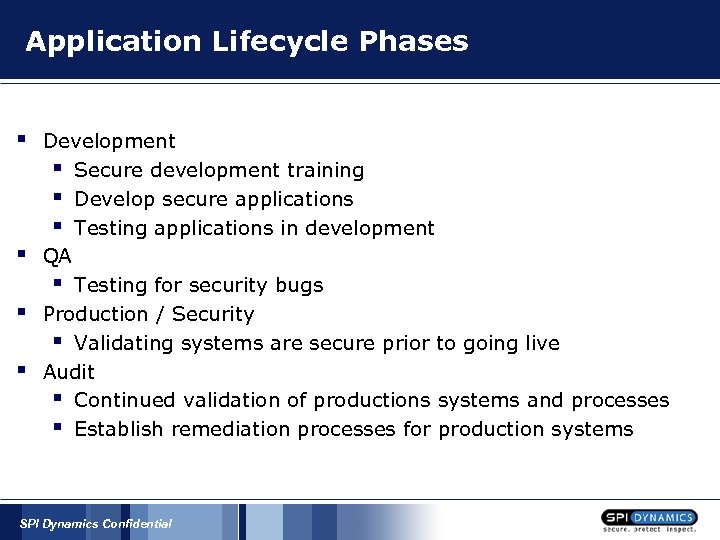
Application Lifecycle Phases § § Development § Secure development training § Develop secure applications § Testing applications in development QA § Testing for security bugs Production / Security § Validating systems are secure prior to going live Audit § Continued validation of productions systems and processes § Establish remediation processes for production systems SPI Dynamics Confidential

Session Summary § § § Anything sent by a user to a web server, including parameters, headers, cookies, etc can be modified. Always validate input before using it or returning it to a user. Application development is by it’s nature prone to bugs. It is critical that applications be tested to verify the absence of parameter based vulnerabilities. SPI Dynamics Confidential
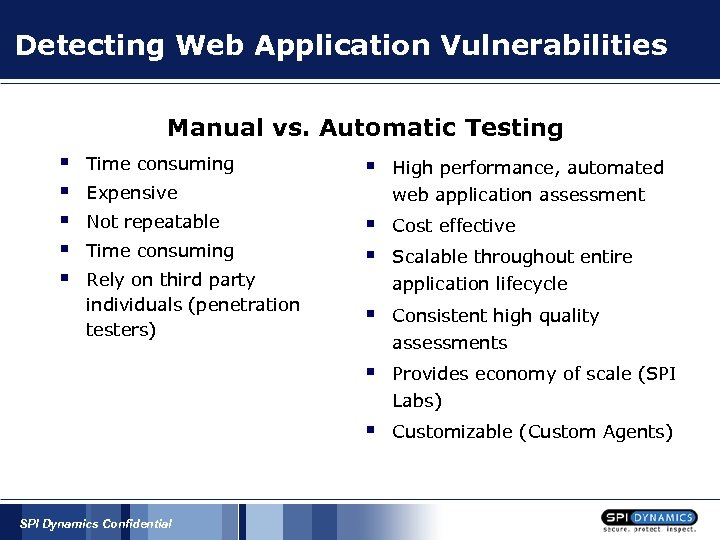
Detecting Web Application Vulnerabilities Manual vs. Automatic Testing § § § Time consuming § High performance, automated web application assessment § § Cost effective § Consistent high quality assessments § Provides economy of scale (SPI Labs) § Customizable (Custom Agents) Expensive Not repeatable Time consuming Rely on third party individuals (penetration testers) SPI Dynamics Confidential Scalable throughout entire application lifecycle

SPI Dynamics Security Throughout the Application Development Lifecycle SPI Dynamics Confidential
Start Secure. Stay Secure. SPI Dynamics Confidential
Part Four Closing and Q&A § § SPI Dynamics Confidential Q&A Break Web. Inspect Demo For a free 15 day trial of Web. Inspect please visit http: //www. spidynamics. com
13430865d8f6a1360c2484b298c5129b.ppt