b2e2f21e41473ea810313d15a25ffeb5.ppt
- Количество слайдов: 18
 Tools for the Analysis and Design of Complex Multi-Scale Networks: Overview • • MURI Annual Review Berkeley, October 27, 2011 J. Walrand, PI SLIDES: http: //robotics. eecs. berkeley. edu/~wlr/ADCN. htm
Tools for the Analysis and Design of Complex Multi-Scale Networks: Overview • • MURI Annual Review Berkeley, October 27, 2011 J. Walrand, PI SLIDES: http: //robotics. eecs. berkeley. edu/~wlr/ADCN. htm
 1. Team • • • Venkat Anantharam, UCB John Doyle, Caltech Weibo Gong, UMASS Steven Low, Caltech R. Srikant, UIUC Don Towsley, UMASS Jean Walrand, UCB Avideh Zakhor, UCB 14 Ph. D Students, 7 Postdocs 12 Journal Papers, 21 Conference papers
1. Team • • • Venkat Anantharam, UCB John Doyle, Caltech Weibo Gong, UMASS Steven Low, Caltech R. Srikant, UIUC Don Towsley, UMASS Jean Walrand, UCB Avideh Zakhor, UCB 14 Ph. D Students, 7 Postdocs 12 Journal Papers, 21 Conference papers
 2. Scientific Objectives and Technical Approach
2. Scientific Objectives and Technical Approach
 2. Scientific Objectives and Technical Approach High Throughput Low Energy Low Delay Security Reliability GOALS of PROPOSED WORK: Improve Understanding of Multi-Scale Features of Networks Use that Understanding to Develop Better Protocols
2. Scientific Objectives and Technical Approach High Throughput Low Energy Low Delay Security Reliability GOALS of PROPOSED WORK: Improve Understanding of Multi-Scale Features of Networks Use that Understanding to Develop Better Protocols
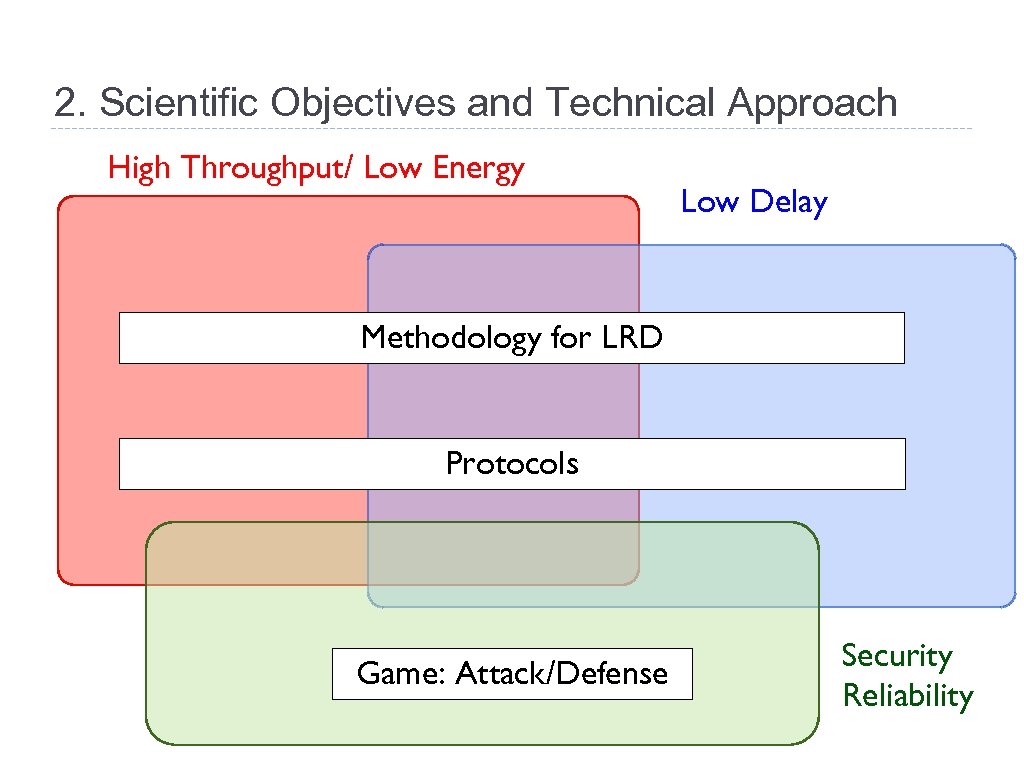 2. Scientific Objectives and Technical Approach High Throughput/ Low Energy Low Delay Methodology for LRD Protocols Game: Attack/Defense Security Reliability
2. Scientific Objectives and Technical Approach High Throughput/ Low Energy Low Delay Methodology for LRD Protocols Game: Attack/Defense Security Reliability
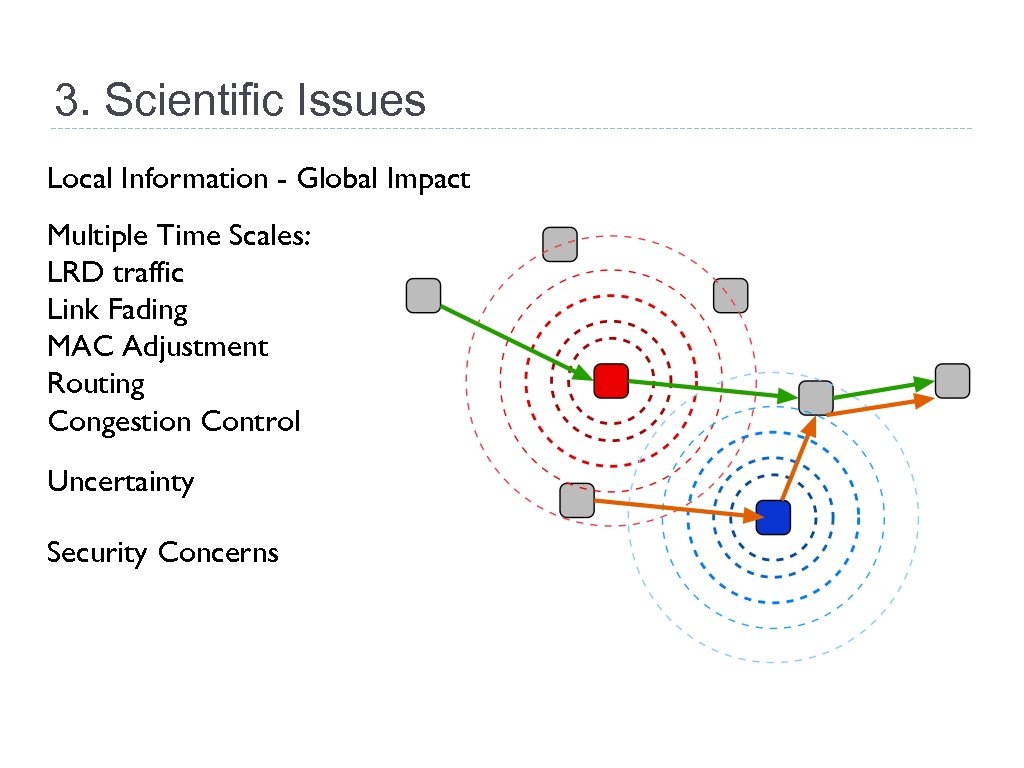 3. Scientific Issues Local Information - Global Impact Multiple Time Scales: LRD traffic Link Fading MAC Adjustment Routing Congestion Control Uncertainty Security Concerns
3. Scientific Issues Local Information - Global Impact Multiple Time Scales: LRD traffic Link Fading MAC Adjustment Routing Congestion Control Uncertainty Security Concerns
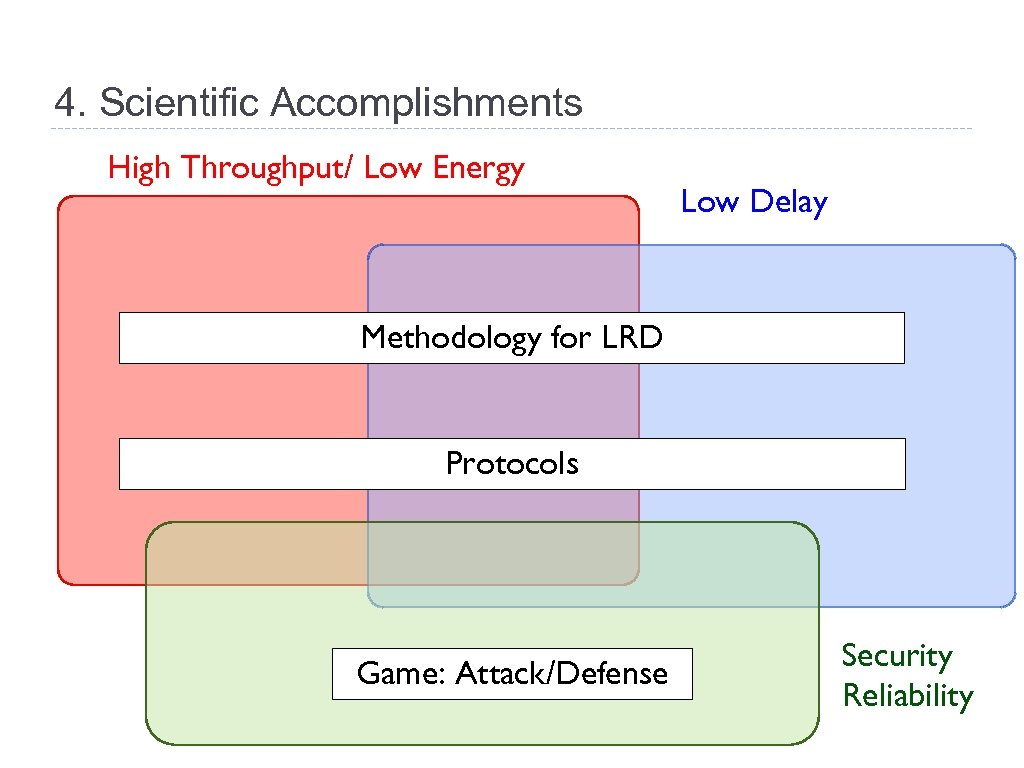 4. Scientific Accomplishments High Throughput/ Low Energy Low Delay Methodology for LRD Protocols Game: Attack/Defense Security Reliability
4. Scientific Accomplishments High Throughput/ Low Energy Low Delay Methodology for LRD Protocols Game: Attack/Defense Security Reliability
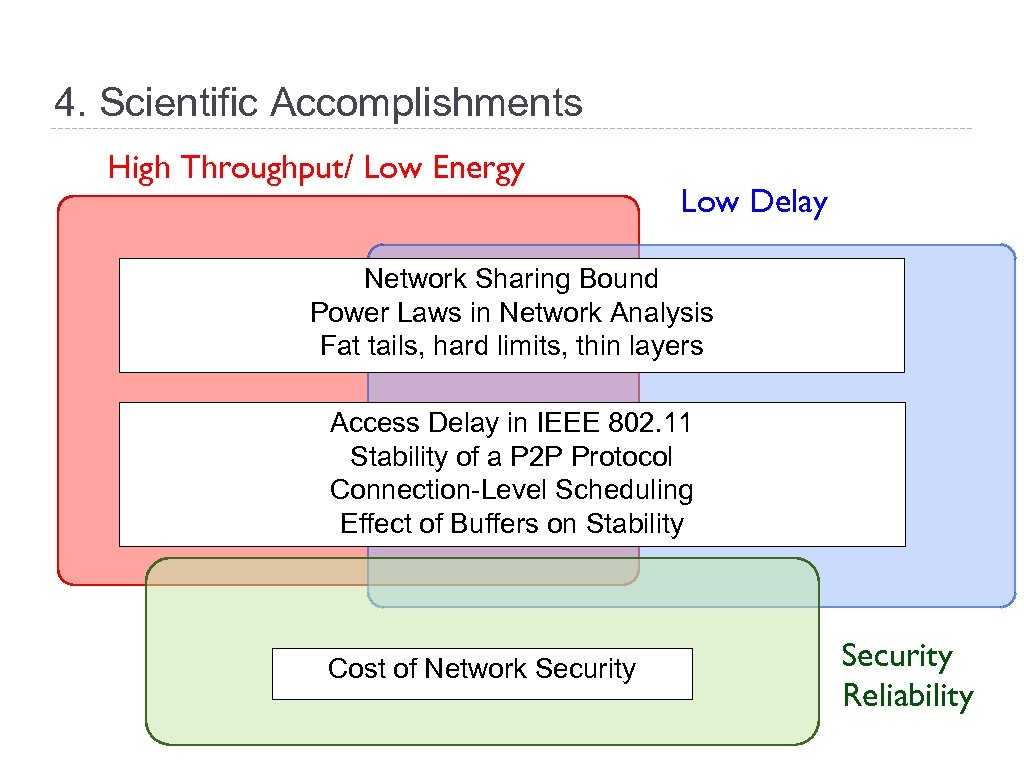 4. Scientific Accomplishments High Throughput/ Low Energy Low Delay Network Sharing Bound Power Laws in Network Analysis Fat tails, hard limits, thin layers Access Delay in IEEE 802. 11 Stability of a P 2 P Protocol Connection-Level Scheduling Effect of Buffers on Stability Cost of Network Security Reliability
4. Scientific Accomplishments High Throughput/ Low Energy Low Delay Network Sharing Bound Power Laws in Network Analysis Fat tails, hard limits, thin layers Access Delay in IEEE 802. 11 Stability of a P 2 P Protocol Connection-Level Scheduling Effect of Buffers on Stability Cost of Network Security Reliability
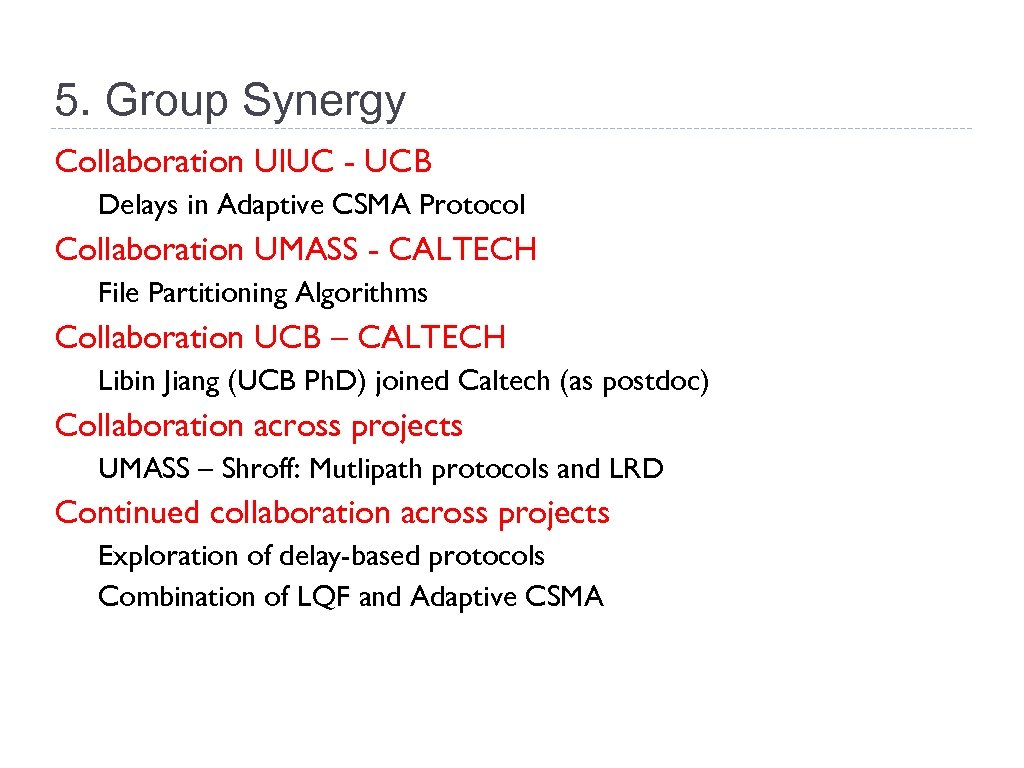 5. Group Synergy Collaboration UIUC - UCB Delays in Adaptive CSMA Protocol Collaboration UMASS - CALTECH File Partitioning Algorithms Collaboration UCB – CALTECH Libin Jiang (UCB Ph. D) joined Caltech (as postdoc) Collaboration across projects UMASS – Shroff: Mutlipath protocols and LRD Continued collaboration across projects Exploration of delay-based protocols Combination of LQF and Adaptive CSMA
5. Group Synergy Collaboration UIUC - UCB Delays in Adaptive CSMA Protocol Collaboration UMASS - CALTECH File Partitioning Algorithms Collaboration UCB – CALTECH Libin Jiang (UCB Ph. D) joined Caltech (as postdoc) Collaboration across projects UMASS – Shroff: Mutlipath protocols and LRD Continued collaboration across projects Exploration of delay-based protocols Combination of LQF and Adaptive CSMA
 6. Future Plans 1) Analysis of delays and likelihood of delivery in wireless networks; 2) Design of network topologies for reliability and resiliency to attacks; 3) Improvements of Wi. Fi protocols; 4) Study of LRD of functionals of Markov chains; 5) Development of secure wireless communication algorithms.
6. Future Plans 1) Analysis of delays and likelihood of delivery in wireless networks; 2) Design of network topologies for reliability and resiliency to attacks; 3) Improvements of Wi. Fi protocols; 4) Study of LRD of functionals of Markov chains; 5) Development of secure wireless communication algorithms.
 7. Original Goals Improve Understanding of Multi-Scale Features of Networks Control protocols that capture the effect of buffers; Analysis of interaction of speed scaling and load balancing; Optimization of consensus algorithm; PCSDE models of heavy tails. Using that Understanding to Develop Improved Protocols Reduced-delay protocols for wireless networks; Stable distributed peer-to-peer algorithms; Stable multipath rate control algorithms; Wi. Fi protocols with carriers sense and packet length adaptation; Geographical load balancing algorithms for renewables; Design of robust scheduling algorithms for heavy-tails; Algorithms for identifying important nodes in large networks; Algorithms for maintaining secure wireless communications.
7. Original Goals Improve Understanding of Multi-Scale Features of Networks Control protocols that capture the effect of buffers; Analysis of interaction of speed scaling and load balancing; Optimization of consensus algorithm; PCSDE models of heavy tails. Using that Understanding to Develop Improved Protocols Reduced-delay protocols for wireless networks; Stable distributed peer-to-peer algorithms; Stable multipath rate control algorithms; Wi. Fi protocols with carriers sense and packet length adaptation; Geographical load balancing algorithms for renewables; Design of robust scheduling algorithms for heavy-tails; Algorithms for identifying important nodes in large networks; Algorithms for maintaining secure wireless communications.
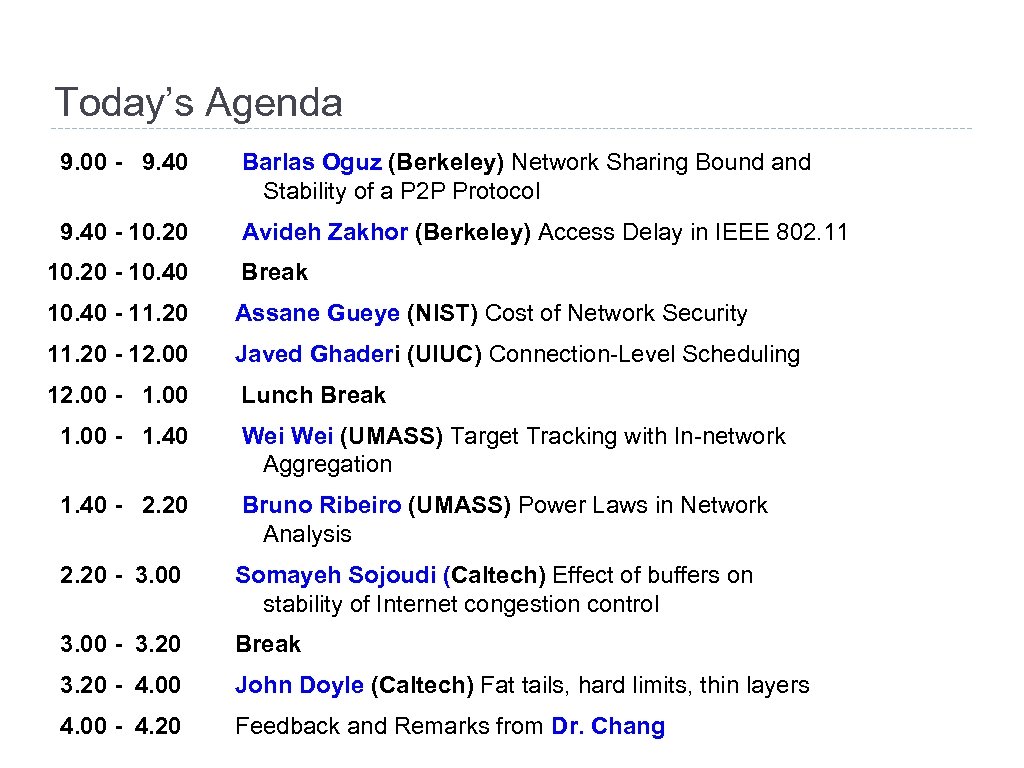 Today’s Agenda 9. 00 - 9. 40 Barlas Oguz (Berkeley) Network Sharing Bound and Stability of a P 2 P Protocol 9. 40 - 10. 20 Avideh Zakhor (Berkeley) Access Delay in IEEE 802. 11 10. 20 - 10. 40 Break 10. 40 - 11. 20 Assane Gueye (NIST) Cost of Network Security 11. 20 - 12. 00 Javed Ghaderi (UIUC) Connection-Level Scheduling 12. 00 - 1. 00 Lunch Break 1. 00 - 1. 40 Wei (UMASS) Target Tracking with In-network Aggregation 1. 40 - 2. 20 Bruno Ribeiro (UMASS) Power Laws in Network Analysis 2. 20 - 3. 00 Somayeh Sojoudi (Caltech) Effect of buffers on stability of Internet congestion control 3. 00 - 3. 20 Break 3. 20 - 4. 00 John Doyle (Caltech) Fat tails, hard limits, thin layers 4. 00 - 4. 20 Feedback and Remarks from Dr. Chang
Today’s Agenda 9. 00 - 9. 40 Barlas Oguz (Berkeley) Network Sharing Bound and Stability of a P 2 P Protocol 9. 40 - 10. 20 Avideh Zakhor (Berkeley) Access Delay in IEEE 802. 11 10. 20 - 10. 40 Break 10. 40 - 11. 20 Assane Gueye (NIST) Cost of Network Security 11. 20 - 12. 00 Javed Ghaderi (UIUC) Connection-Level Scheduling 12. 00 - 1. 00 Lunch Break 1. 00 - 1. 40 Wei (UMASS) Target Tracking with In-network Aggregation 1. 40 - 2. 20 Bruno Ribeiro (UMASS) Power Laws in Network Analysis 2. 20 - 3. 00 Somayeh Sojoudi (Caltech) Effect of buffers on stability of Internet congestion control 3. 00 - 3. 20 Break 3. 20 - 4. 00 John Doyle (Caltech) Fat tails, hard limits, thin layers 4. 00 - 4. 20 Feedback and Remarks from Dr. Chang
 Publications JOURNALS Libin Jiang, Venkat Anantharam and Jean Walrand, ``How Bad are Selfish Investments in Network Security? ", IEEE/ACM Transactions on Networking, Vol. 19, No. 2, pp. 549 -560, April 2011. Aminzadeh Gohari and Venkat Anantharam, “Evaluation of Marton's Inner Bound for the General Broadcast Channel”. To appear in IEEE Transactions on Information Theory. Venkat Anantharam and Takis Konstantopoulos, ”Integral representation of Skorokhod reflection, ” To appear in Proceedings of the American Mathematical Society. Lijun Chen, Na Li, Steven H. Low and John C. Doyle. “Two Market Models for Demand Response in Power Networks, ” IEEE Smart. Grid. Comm, 2010. J. J. Jaramillo, R. Srikant and L. Ying, Scheduling for Optimal Rate Allocation in Ad Hoc Networks with Hetergeneous Delay Constraints, IEEE Journal on Selected Areas in Communications, May 2011. J. J. Jaramillo and R. Srikant, Optimal scheduling for fair resource allocation in ad hoc networks with elastic and inelastic traffic, IEEE/ACM Transactions on Networking, 2011.
Publications JOURNALS Libin Jiang, Venkat Anantharam and Jean Walrand, ``How Bad are Selfish Investments in Network Security? ", IEEE/ACM Transactions on Networking, Vol. 19, No. 2, pp. 549 -560, April 2011. Aminzadeh Gohari and Venkat Anantharam, “Evaluation of Marton's Inner Bound for the General Broadcast Channel”. To appear in IEEE Transactions on Information Theory. Venkat Anantharam and Takis Konstantopoulos, ”Integral representation of Skorokhod reflection, ” To appear in Proceedings of the American Mathematical Society. Lijun Chen, Na Li, Steven H. Low and John C. Doyle. “Two Market Models for Demand Response in Power Networks, ” IEEE Smart. Grid. Comm, 2010. J. J. Jaramillo, R. Srikant and L. Ying, Scheduling for Optimal Rate Allocation in Ad Hoc Networks with Hetergeneous Delay Constraints, IEEE Journal on Selected Areas in Communications, May 2011. J. J. Jaramillo and R. Srikant, Optimal scheduling for fair resource allocation in ad hoc networks with elastic and inelastic traffic, IEEE/ACM Transactions on Networking, 2011.
 Publications JOURNALS J. Ni, R. Srikant and X. Wu. Coloring Spatial Point Processes with Applications to Peer Discovery in Large Wireless Networks, IEEE/ACM Transactions on Networking, April 2011. M. Leconte, J. Ni and R. Srikant, Improved Bounds on the Throughput Efficiency of Greedy Maximal Scheduling in Wireless Networks, IEEE/ACM Transactions on Networking, June 2011. Y. Cai, Patrick P. C. Lee, W. Gong, D. Towsley. “Analysis of Traffic Correlation Attacks on Router Queues, ” J. Computer Networks, 55(3), 734— 747, February 2011. B. Jiang, Y. Cai, D. Towsley. “On the Resource Utilization and Traffic Distribution of Multipath. Transmission Control”, to appear in Performance L. Ying, R. Srikant D. Towsley, “Cluster-Based Back-Pressure Routing Algorithm, ” IEEE/ACM Trans. on Networking, to appear. (Collaborative effort. ) B. Jiang, R. Brockett, W. Gong, D. Towsley. “Stochastic differential equations for power law behaviors”, submitted to J. Applied Probability.
Publications JOURNALS J. Ni, R. Srikant and X. Wu. Coloring Spatial Point Processes with Applications to Peer Discovery in Large Wireless Networks, IEEE/ACM Transactions on Networking, April 2011. M. Leconte, J. Ni and R. Srikant, Improved Bounds on the Throughput Efficiency of Greedy Maximal Scheduling in Wireless Networks, IEEE/ACM Transactions on Networking, June 2011. Y. Cai, Patrick P. C. Lee, W. Gong, D. Towsley. “Analysis of Traffic Correlation Attacks on Router Queues, ” J. Computer Networks, 55(3), 734— 747, February 2011. B. Jiang, Y. Cai, D. Towsley. “On the Resource Utilization and Traffic Distribution of Multipath. Transmission Control”, to appear in Performance L. Ying, R. Srikant D. Towsley, “Cluster-Based Back-Pressure Routing Algorithm, ” IEEE/ACM Trans. on Networking, to appear. (Collaborative effort. ) B. Jiang, R. Brockett, W. Gong, D. Towsley. “Stochastic differential equations for power law behaviors”, submitted to J. Applied Probability.
 Publications CONFERENCES Krishnan, E. Haghani, A. Zakhor, “Local Estimation of Collision Probabilities in 802. 11 WLANs: An Experimental Study, " IEEE WCNC 2011, Cancun. Krishnan, and A. Zakhor, “Adaptive Carrier-Sensing for Throughput Improvement in IEEE 802. 11 Networks, " IEEE GLOBECOM 2010, Miami, FL. A. Zakhor, "A Method for Estimating Access Delay Distribution in IEEE 802. 11 Networks, " accepted for publication at IEEE GLOBECOM 2011, Houston, TX, December 2011. M. Krishnan, E. Haghani, A. Zakhor, “"Packet Length Adaptation in WLANs with Hidden Nodes and Time. Varying Channels, " accepted for publication at IEEE GLOBECOM 2011, Houston, Texas. Somayeh Sojoudi, Steven H. Low and John C. Doyle, "Effects of Buffers on Stability of Internet Congestion Controllers", IEEE International Conference on Computer Communications (INFOCOM), mini conference, China, 2011. Zhenhua Liu, Minghong Lin, Adam Wierman, Steven H. Low and Lachlan L. H. Andrew, "Greening geographic load balancing", Proc. ACM Sigmetrics, 2011
Publications CONFERENCES Krishnan, E. Haghani, A. Zakhor, “Local Estimation of Collision Probabilities in 802. 11 WLANs: An Experimental Study, " IEEE WCNC 2011, Cancun. Krishnan, and A. Zakhor, “Adaptive Carrier-Sensing for Throughput Improvement in IEEE 802. 11 Networks, " IEEE GLOBECOM 2010, Miami, FL. A. Zakhor, "A Method for Estimating Access Delay Distribution in IEEE 802. 11 Networks, " accepted for publication at IEEE GLOBECOM 2011, Houston, TX, December 2011. M. Krishnan, E. Haghani, A. Zakhor, “"Packet Length Adaptation in WLANs with Hidden Nodes and Time. Varying Channels, " accepted for publication at IEEE GLOBECOM 2011, Houston, Texas. Somayeh Sojoudi, Steven H. Low and John C. Doyle, "Effects of Buffers on Stability of Internet Congestion Controllers", IEEE International Conference on Computer Communications (INFOCOM), mini conference, China, 2011. Zhenhua Liu, Minghong Lin, Adam Wierman, Steven H. Low and Lachlan L. H. Andrew, "Greening geographic load balancing", Proc. ACM Sigmetrics, 2011
 Publications CONFERENCES J. Nair, A. Wierman, B. Zwart. “Scheduling for the tail: robustness versus optimality”, Proceedings of Allerton, 2010 (Invited paper) V. Borkar, J. Nair and N. Sanketh. “Manufacturing consent, ” Proceedings of Allerton, 2010 (Invited paper) Sudeep Kamath and Venkat Anantharam, ``A new dual to the Gacs-Korner common information defined via the Gray-Wyner system", Proceedings of the 48 th Annual Allerton Conference on Communications, Control and Computing, Urbana, Illinois, September 29 -October 1, 2010. Naryana Santhanam and Venkat Anantharam, ``What risks lead to ruin", Proceedings of the 48 th Annual Allerton Conference on Communications, Control and Computing, Urbana, Illinois, September 29 -October 1, 2010. Assane Gueye, Jean C. Walrand Venkat Anantharam. ``Design of Network Topology in an Adversarial Environment", Game. Sec 2010, Conference on Decision and Game Theory for Security, 22 -23 November 2010, Berlin, Germany. Assane Gueye, Jean C. Walrand, and Venkat Anantharam, “A Network Topology Design Game: How to Choose Communication Links in an Adversarial Environment? ”, Game. Nets 2011, 2 nd International ICST Conference on Game Theory for Networks, April 16 -18, 2011, Shanghai, China.
Publications CONFERENCES J. Nair, A. Wierman, B. Zwart. “Scheduling for the tail: robustness versus optimality”, Proceedings of Allerton, 2010 (Invited paper) V. Borkar, J. Nair and N. Sanketh. “Manufacturing consent, ” Proceedings of Allerton, 2010 (Invited paper) Sudeep Kamath and Venkat Anantharam, ``A new dual to the Gacs-Korner common information defined via the Gray-Wyner system", Proceedings of the 48 th Annual Allerton Conference on Communications, Control and Computing, Urbana, Illinois, September 29 -October 1, 2010. Naryana Santhanam and Venkat Anantharam, ``What risks lead to ruin", Proceedings of the 48 th Annual Allerton Conference on Communications, Control and Computing, Urbana, Illinois, September 29 -October 1, 2010. Assane Gueye, Jean C. Walrand Venkat Anantharam. ``Design of Network Topology in an Adversarial Environment", Game. Sec 2010, Conference on Decision and Game Theory for Security, 22 -23 November 2010, Berlin, Germany. Assane Gueye, Jean C. Walrand, and Venkat Anantharam, “A Network Topology Design Game: How to Choose Communication Links in an Adversarial Environment? ”, Game. Nets 2011, 2 nd International ICST Conference on Game Theory for Networks, April 16 -18, 2011, Shanghai, China.
 Publications CONFERENCES Sudeep U. Kamath, David N. C. Tse, and Venkat Anantharam, “Generalized Network Sharing Bound and the Two-Unicast Problem". Net. Cod 2011, The 2011 International Symposium on Network Coding, Beijing, China, 25 - 27 July, 2011. T. H. Kim. J. Ni, R. Srikant and N. Vaidya. On the Achievable Throughput of CSMA Under Imperfect Carrier Sensing. Proc. IEEE INFOCOM 2011. L. Jiang, M. Leconte, J. Ni, R. Srikant and J. Walrand. Fast Mixing of Parallel Glauber Dynamics and Low. Delay CSMA Scheduling, Proc. IEEE INFOCOM Mini-Conference 2011. (Collaborative Effort) T. Ji and R. Srikant. Scheduling in Wireless Networks with Connection Arrivals and Departures. Proc. ITA 2011. S Xiao, W Gong, D Towsley. Secure Wireless Communication with Dynamic Secrets. INFOCOM 2010. (runnerup for best paper award) S Xiao, W Gong. Mobility Can Help: Protect User Identity with Dynamic Credentials. 11 th International Conference on Mobile Data Management (MDM 2010)
Publications CONFERENCES Sudeep U. Kamath, David N. C. Tse, and Venkat Anantharam, “Generalized Network Sharing Bound and the Two-Unicast Problem". Net. Cod 2011, The 2011 International Symposium on Network Coding, Beijing, China, 25 - 27 July, 2011. T. H. Kim. J. Ni, R. Srikant and N. Vaidya. On the Achievable Throughput of CSMA Under Imperfect Carrier Sensing. Proc. IEEE INFOCOM 2011. L. Jiang, M. Leconte, J. Ni, R. Srikant and J. Walrand. Fast Mixing of Parallel Glauber Dynamics and Low. Delay CSMA Scheduling, Proc. IEEE INFOCOM Mini-Conference 2011. (Collaborative Effort) T. Ji and R. Srikant. Scheduling in Wireless Networks with Connection Arrivals and Departures. Proc. ITA 2011. S Xiao, W Gong, D Towsley. Secure Wireless Communication with Dynamic Secrets. INFOCOM 2010. (runnerup for best paper award) S Xiao, W Gong. Mobility Can Help: Protect User Identity with Dynamic Credentials. 11 th International Conference on Mobile Data Management (MDM 2010)
 Publications CONFERENCES J. Tan, W. Wei, B. Jiang, N. Shroff, D. Towsley. “Can Multipath Routing Mitigate Power Law Delays? – Effects of Parallelism on Tail Performance, ITC 2010, September 2010. (collaborative effort) B. Ribeiro and D. Towsley. "Estimating and Sampling Graphs with Multidimensional Random Walks", ACM SIGCOMM Internet Measurement Conference, Nov, 2010. W Zeng, X Chen, A Russell, S Vasudevan, B Wang and W Wei, "Neighbor Discovery in Wireless Networks with Multipacket Reception", Proceedings of Mobi. Hoc, Paris, France, May 2011. Y. -s. Lim, B. Ribeiro, D. S. Menasche, P. Basu, D. Towsley. “Online Estimating The Top k Nodes of a Network”, Proc. NSW 2011.
Publications CONFERENCES J. Tan, W. Wei, B. Jiang, N. Shroff, D. Towsley. “Can Multipath Routing Mitigate Power Law Delays? – Effects of Parallelism on Tail Performance, ITC 2010, September 2010. (collaborative effort) B. Ribeiro and D. Towsley. "Estimating and Sampling Graphs with Multidimensional Random Walks", ACM SIGCOMM Internet Measurement Conference, Nov, 2010. W Zeng, X Chen, A Russell, S Vasudevan, B Wang and W Wei, "Neighbor Discovery in Wireless Networks with Multipacket Reception", Proceedings of Mobi. Hoc, Paris, France, May 2011. Y. -s. Lim, B. Ribeiro, D. S. Menasche, P. Basu, D. Towsley. “Online Estimating The Top k Nodes of a Network”, Proc. NSW 2011.


