d7f370b5b2a3221015341e2bfc73a78f.ppt
- Количество слайдов: 112
 Tools For Teaching Security+ Mark Ciampa Western Kentucky University mark. ciampa@wku. edu 1
Tools For Teaching Security+ Mark Ciampa Western Kentucky University mark. ciampa@wku. edu 1
 Cengage Feedback • Shorter sentences or just key words or phrases instead of longer, complete sentences • No more than 3 -5 points per slide • Have 20 slides for entire presentation 2
Cengage Feedback • Shorter sentences or just key words or phrases instead of longer, complete sentences • No more than 3 -5 points per slide • Have 20 slides for entire presentation 2
 Cengage Feedback 3
Cengage Feedback 3
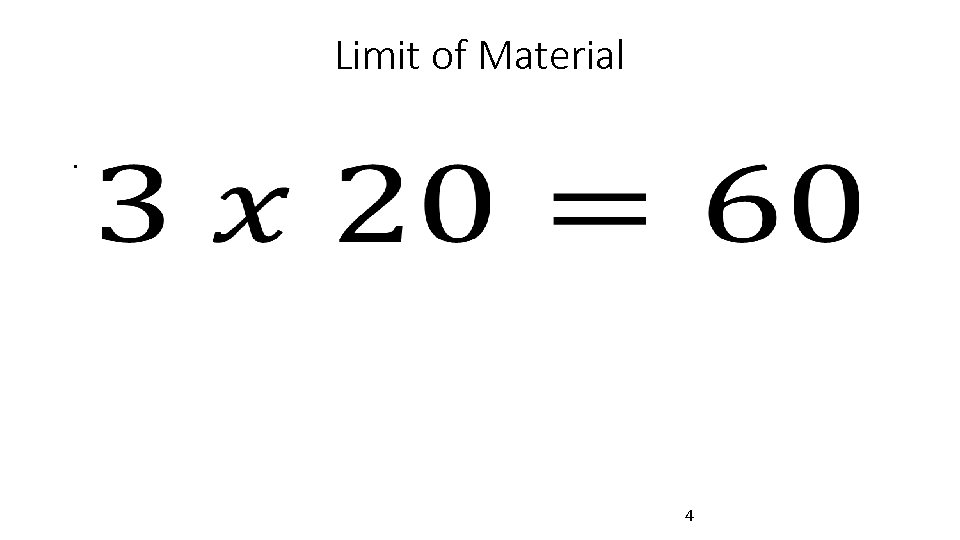 Limit of Material • 4
Limit of Material • 4
 Teaching, Tools & Presentation Philosophy Broad vs. Deep 5
Teaching, Tools & Presentation Philosophy Broad vs. Deep 5
 Teaching Security+ • Comp. TIA Security+ is more broad than deep • No single domain or topic is significantly in depth • When teaching Security+ very important to keep moving • Going too deep in a topic means you won’t be able to cover the material 6
Teaching Security+ • Comp. TIA Security+ is more broad than deep • No single domain or topic is significantly in depth • When teaching Security+ very important to keep moving • Going too deep in a topic means you won’t be able to cover the material 6
 Tools When Teaching Security+ • Tools for students likewise need be more broad than deep • Tempting to spend 4 weeks on configuring Server 2012 security • But very important to keep moving • Reflection of Hands-On Projects in Security+ Guide to Network Security Fundamentals 5 e 7
Tools When Teaching Security+ • Tools for students likewise need be more broad than deep • Tempting to spend 4 weeks on configuring Server 2012 security • But very important to keep moving • Reflection of Hands-On Projects in Security+ Guide to Network Security Fundamentals 5 e 7
 Presentation Security+ Tools • • This presentation of Tools for Teaching Security+ is more broad than deep Will not go into deep dive on any single tool; otherwise won’t be able to cover the material Few tools demonstrated while most introduced None of these in Security+ Guide to Network Security Fundamentals 5 e Hands-On Projects • Presented where fall in current chapter • Tools for student Hands-On Projects and demos 8
Presentation Security+ Tools • • This presentation of Tools for Teaching Security+ is more broad than deep Will not go into deep dive on any single tool; otherwise won’t be able to cover the material Few tools demonstrated while most introduced None of these in Security+ Guide to Network Security Fundamentals 5 e Hands-On Projects • Presented where fall in current chapter • Tools for student Hands-On Projects and demos 8
 Presentation Security+ Tools • • This presentation of Tools for Teaching Security+ is more broad than deep Will not go into deep dive on any single tool; otherwise won’t be able to cover the material Few tools demonstrated while most introduced None of these in Security+ Guide to Network Security Fundamentals 5 e Hands-On Projects • Presented where fall in current chapter • Tools for student Hands-On Projects and demos 9
Presentation Security+ Tools • • This presentation of Tools for Teaching Security+ is more broad than deep Will not go into deep dive on any single tool; otherwise won’t be able to cover the material Few tools demonstrated while most introduced None of these in Security+ Guide to Network Security Fundamentals 5 e Hands-On Projects • Presented where fall in current chapter • Tools for student Hands-On Projects and demos 9
 Security Employment • Tools for Teaching Security+ 10
Security Employment • Tools for Teaching Security+ 10
 How To Make Money In Security 11
How To Make Money In Security 11
 Carbanak • • • Most cybercrime targets consumers and businesses, stealing account information like passwords and other data that then lets thieves cash out hijacked bank accounts or create fake credit/debit cards Group now specializes in breaking into banks directly and then use ways to funnel cash from the financial institution itself Carbanak deployed malware via phishing scams to get inside of computers at 100+ banks and steal between $300 million to $1 billion 12
Carbanak • • • Most cybercrime targets consumers and businesses, stealing account information like passwords and other data that then lets thieves cash out hijacked bank accounts or create fake credit/debit cards Group now specializes in breaking into banks directly and then use ways to funnel cash from the financial institution itself Carbanak deployed malware via phishing scams to get inside of computers at 100+ banks and steal between $300 million to $1 billion 12
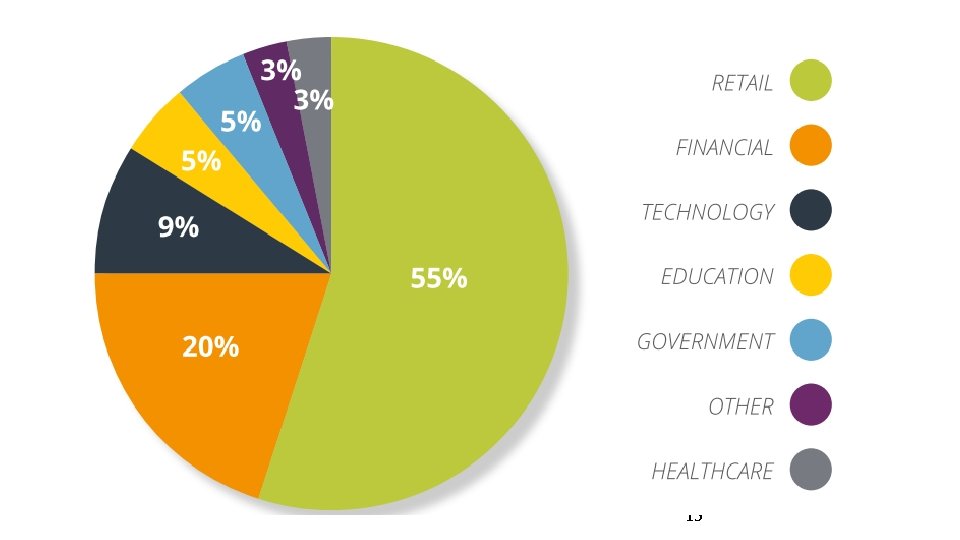
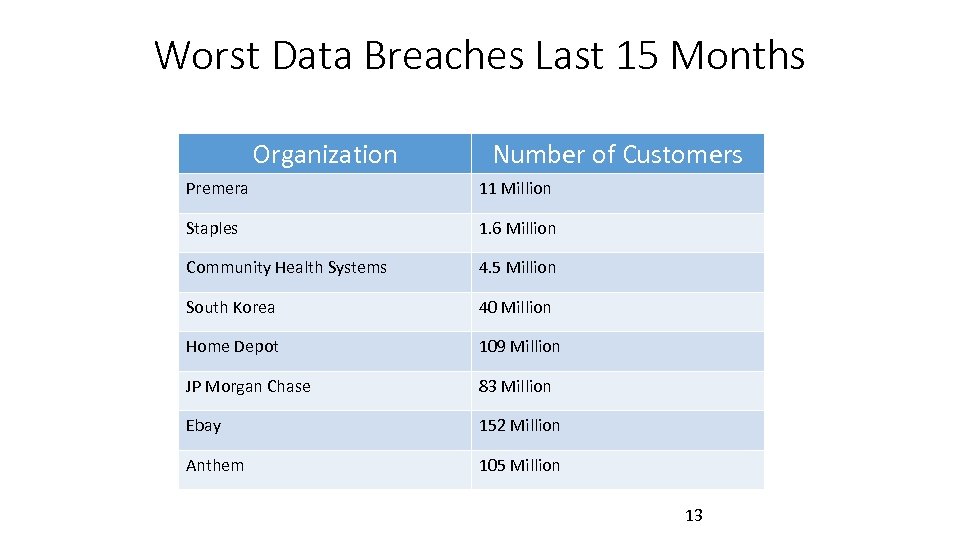 Worst Data Breaches Last 15 Months Organization Number of Customers Premera 11 Million Staples 1. 6 Million Community Health Systems 4. 5 Million South Korea 40 Million Home Depot 109 Million JP Morgan Chase 83 Million Ebay 152 Million Anthem 105 Million 13
Worst Data Breaches Last 15 Months Organization Number of Customers Premera 11 Million Staples 1. 6 Million Community Health Systems 4. 5 Million South Korea 40 Million Home Depot 109 Million JP Morgan Chase 83 Million Ebay 152 Million Anthem 105 Million 13
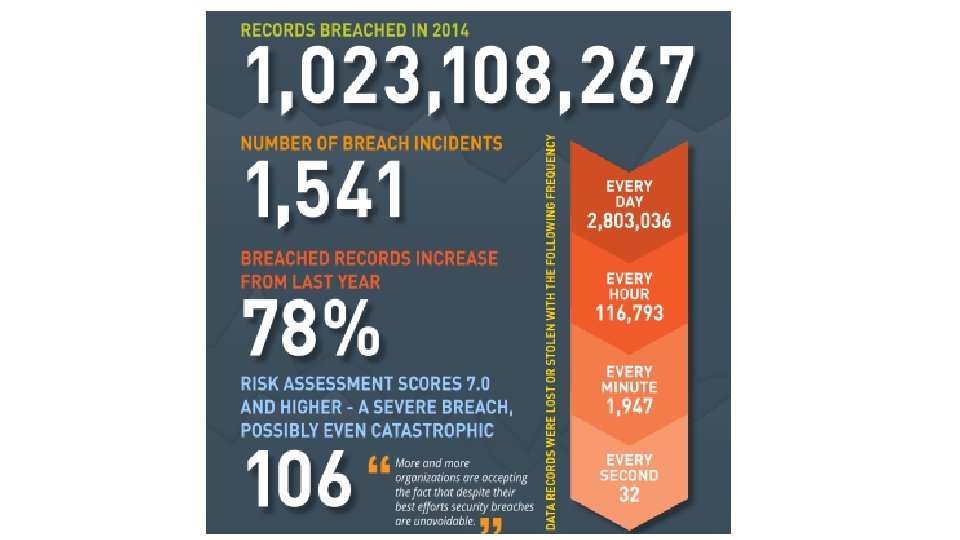 14
14
 15
15
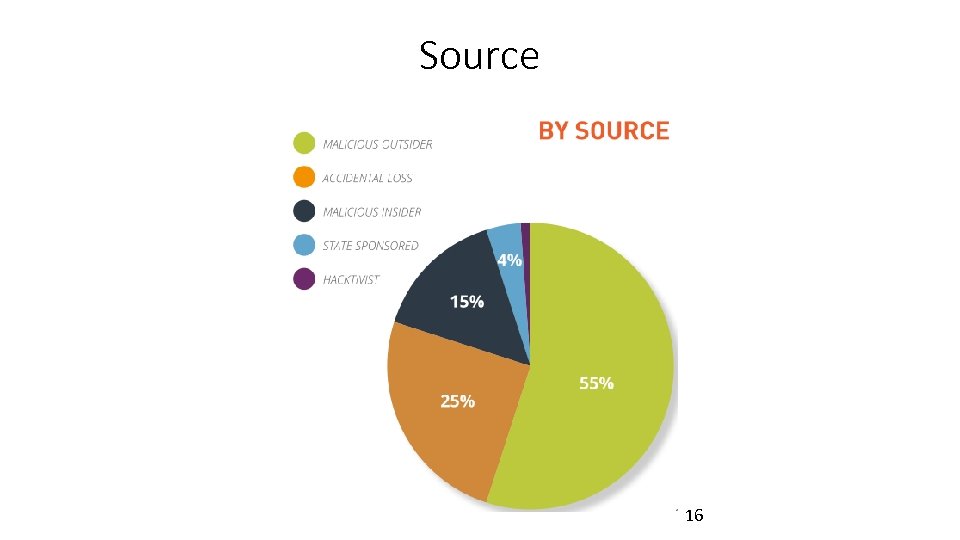 Source 16
Source 16
 Bug Bounties • • • Organizations pay for vulnerabilities that are reported by researchers In 2014 Google paid out $150, 000 to a researcher for uncovering a multi-vulnerability chain that exploited the Google Chrome OS Google set aside an astonishing $3. 14 million (yes, million) for paying for these "bug bounties. " In 2014 Facebook was able to patch 61 high-severity vulnerabilities, twice as many as the previous year Facebook pays a minimum of $500 per reported vulnerability with no upper limit for the high-value vulnerability (that's right, the sky's the 18 limit)
Bug Bounties • • • Organizations pay for vulnerabilities that are reported by researchers In 2014 Google paid out $150, 000 to a researcher for uncovering a multi-vulnerability chain that exploited the Google Chrome OS Google set aside an astonishing $3. 14 million (yes, million) for paying for these "bug bounties. " In 2014 Facebook was able to patch 61 high-severity vulnerabilities, twice as many as the previous year Facebook pays a minimum of $500 per reported vulnerability with no upper limit for the high-value vulnerability (that's right, the sky's the 18 limit)
 Hacker Bounty Hunter • • Two U. S. government agencies are offering a $3 million reward for information leading to the arrest or conviction of Evgeniy Mikhailovich Bogachev who is suspected of having served as an administrator for the destructive Gameover Zeus botnet Over a two-year period Gameover Zeus targeted banking credentials resulted in financial losses exceeding $100 million. Bogachev is listed on the FBI's Cyber's Most Wanted list (did you know such a list even existed? ). The rewards for the other five members on this list are a mere $1 million each. 19
Hacker Bounty Hunter • • Two U. S. government agencies are offering a $3 million reward for information leading to the arrest or conviction of Evgeniy Mikhailovich Bogachev who is suspected of having served as an administrator for the destructive Gameover Zeus botnet Over a two-year period Gameover Zeus targeted banking credentials resulted in financial losses exceeding $100 million. Bogachev is listed on the FBI's Cyber's Most Wanted list (did you know such a list even existed? ). The rewards for the other five members on this list are a mere $1 million each. 19
 Finished! 20
Finished! 20
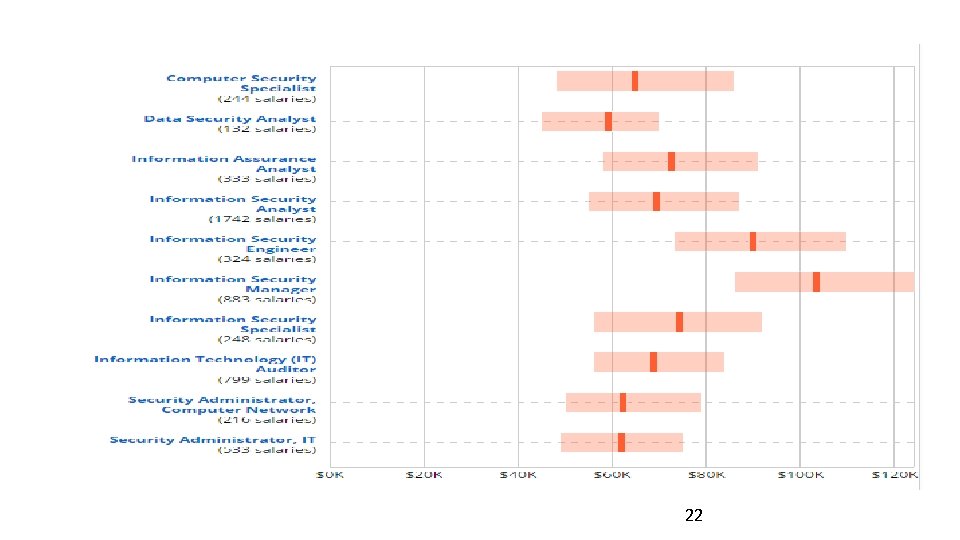
 Information Security Specialist • • • Mundane job in information security According to Bureau of Labor Statistics (BLS) Information Security Analysts with a bachelor's degree and less than five years' experience had median pay in 2013 of $86, 130 (the most recent data available) Over the next seven years these positions are expect to grow at a rate of 37%, or "much faster than average. " 21
Information Security Specialist • • • Mundane job in information security According to Bureau of Labor Statistics (BLS) Information Security Analysts with a bachelor's degree and less than five years' experience had median pay in 2013 of $86, 130 (the most recent data available) Over the next seven years these positions are expect to grow at a rate of 37%, or "much faster than average. " 21
 22
22
 2 3 Information Security Employment • In the past security was rarely outsourced – but that now changing • The increased use of cloud computing is particularly concerning • • By next year about 10% of overall IT security enterprise capabilities will be delivered as a cloud service Gartner says by 2018 over half of all organizations will have to rely on external security services firms that specialize in data protection, risk assessment, and infrastructure management
2 3 Information Security Employment • In the past security was rarely outsourced – but that now changing • The increased use of cloud computing is particularly concerning • • By next year about 10% of overall IT security enterprise capabilities will be delivered as a cloud service Gartner says by 2018 over half of all organizations will have to rely on external security services firms that specialize in data protection, risk assessment, and infrastructure management
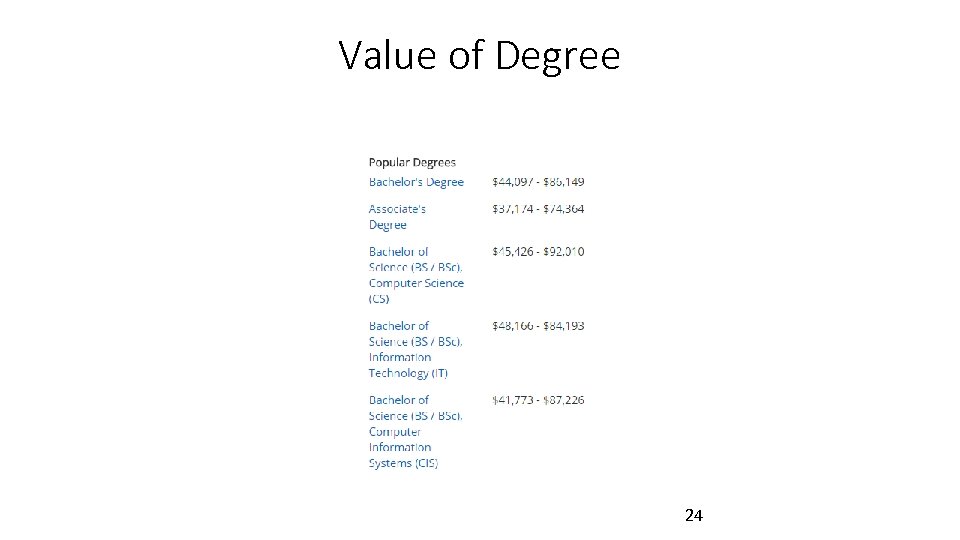 Value of Degree 24
Value of Degree 24
 Value of Certification • • 72% of employers use IT certifications as a requirement for specific job roles 66% of employers say that IT certifications are "very valuable" (increase from 30% in 2011) 60% of employers often use IT certifications to confirm a candidate's subject matter knowledge or expertise 65% of employers said if there are two otherwise equally qualified candidates for a job then will turn to IT certifications as the deciding factor 25
Value of Certification • • 72% of employers use IT certifications as a requirement for specific job roles 66% of employers say that IT certifications are "very valuable" (increase from 30% in 2011) 60% of employers often use IT certifications to confirm a candidate's subject matter knowledge or expertise 65% of employers said if there are two otherwise equally qualified candidates for a job then will turn to IT certifications as the deciding factor 25
 Value of Security+ Certification • • Foote Partners recently released its "IT Skills Demand Pay Trends Report“: Which certifications will carry the most weight throughout 2015 in terms of pay and demand? Charted pay growth over the last 3, 6 and 12 months for 337 different IT certifications and came up with the "historical pay premium performance. " Over last 3 months the market pay value of a Security+ certificate increased 30% (those with Security+ certification earned that much more than without) Over last 12 months the market pay value for the Security+ certificate 26
Value of Security+ Certification • • Foote Partners recently released its "IT Skills Demand Pay Trends Report“: Which certifications will carry the most weight throughout 2015 in terms of pay and demand? Charted pay growth over the last 3, 6 and 12 months for 337 different IT certifications and came up with the "historical pay premium performance. " Over last 3 months the market pay value of a Security+ certificate increased 30% (those with Security+ certification earned that much more than without) Over last 12 months the market pay value for the Security+ certificate 26
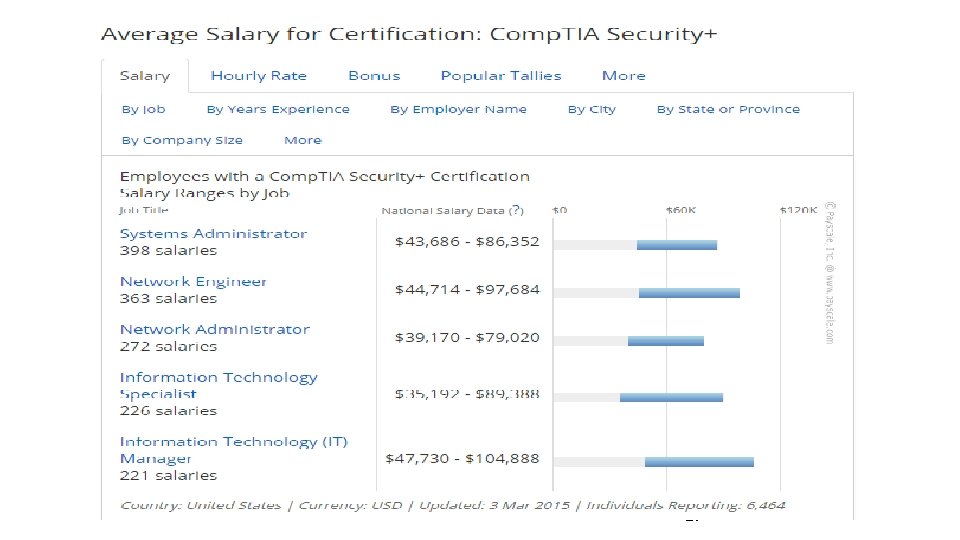 27
27
 Network+ • Tools for Teaching Security+ 28
Network+ • Tools for Teaching Security+ 28
 Network Security • • There are many different terms that are used when referring to security, like cybersecurity or information assurance Network security still common Network viewed as the protecting wall around which client computers could be kept safe: secure network keep attackers away from devices Not foolproof • Too many entry points that circumvent the network and allow malware to enter like infected USB flash drive 29
Network Security • • There are many different terms that are used when referring to security, like cybersecurity or information assurance Network security still common Network viewed as the protecting wall around which client computers could be kept safe: secure network keep attackers away from devices Not foolproof • Too many entry points that circumvent the network and allow malware to enter like infected USB flash drive 29
 Network Security • • • Network security still important Not all applications are designed and written with security and reliability in mind, so it falls on the network to provide protection Network-delivered services can scale better for larger environments and can complement server and application functionality Attacker who can successfully penetrate a computer network may have access to hundreds or even thousands of desktop systems, servers, and storage devices Organizations should make network defenses one of the first priorities in protecting information 30
Network Security • • • Network security still important Not all applications are designed and written with security and reliability in mind, so it falls on the network to provide protection Network-delivered services can scale better for larger environments and can complement server and application functionality Attacker who can successfully penetrate a computer network may have access to hundreds or even thousands of desktop systems, servers, and storage devices Organizations should make network defenses one of the first priorities in protecting information 30
 Comp. TIA Network+ N 10 -006 • Feb 28 2015 Comp. TIA released new Network+ exam (N 10 -006) • Increased emphasis on security • It has a separate domain just on security: "3. 0 Network Security" • • Although the percentage of the exam that covers network security is officially listed as 18%, according to Comp. TIA the overall coverage of security in the new Network+ exam is actually double that at 37% Exam also has extended coverage of wireless local area networks and security and covers about 30% of objectives found on Certified Wireless Network Administrator (CWNA) exam 31
Comp. TIA Network+ N 10 -006 • Feb 28 2015 Comp. TIA released new Network+ exam (N 10 -006) • Increased emphasis on security • It has a separate domain just on security: "3. 0 Network Security" • • Although the percentage of the exam that covers network security is officially listed as 18%, according to Comp. TIA the overall coverage of security in the new Network+ exam is actually double that at 37% Exam also has extended coverage of wireless local area networks and security and covers about 30% of objectives found on Certified Wireless Network Administrator (CWNA) exam 31
 Chapter 1 Introduction to Security • Tools for Teaching Security+ 32
Chapter 1 Introduction to Security • Tools for Teaching Security+ 32
 Chapter 1 Projects Security+ Guide 5 e • • Project 1 -1: Examine Data Breaches (The Privacy Rights Clearinghouse) Project 1 -2: Scan for Malware Using the Microsoft Safety Scanner Project 1 -3: Create a Virtual Machine of Windows 8. 1 for Security Testing—Part 1 Project 1 -4: Create a Virtual Machine of Windows 8. 1 for Security Testing—Part 2 (Virtual. Box) 33
Chapter 1 Projects Security+ Guide 5 e • • Project 1 -1: Examine Data Breaches (The Privacy Rights Clearinghouse) Project 1 -2: Scan for Malware Using the Microsoft Safety Scanner Project 1 -3: Create a Virtual Machine of Windows 8. 1 for Security Testing—Part 1 Project 1 -4: Create a Virtual Machine of Windows 8. 1 for Security Testing—Part 2 (Virtual. Box) 33
 Your Privacy • Google Location History • Immersion • You’ve Been Pwned! 34
Your Privacy • Google Location History • Immersion • You’ve Been Pwned! 34
 Real Time Attack Trackers • Fire. Eye Cyber Threat Map • Norse IPViking • Arbor Networks Digital Attack Map • Kaspersky Cyberthreat Real-time Map • Anubis Network Cyberfeed • F-Secure World Map • Trend Micro Global Botnet Threat Activity Map 35
Real Time Attack Trackers • Fire. Eye Cyber Threat Map • Norse IPViking • Arbor Networks Digital Attack Map • Kaspersky Cyberthreat Real-time Map • Anubis Network Cyberfeed • F-Secure World Map • Trend Micro Global Botnet Threat Activity Map 35
 Create & Run VM from USB Flash Drive • • • Fork of Virtual. Box called Portable Virtual. Box Run VM from USB flash drive as application running under Windows (like a virtualized version Windows 8 Enterprise Windows to Go option) Caveats • Requires administrator privileges to run • Consumes hard drive space, RAM (can adjust), processing power • Need licensed copy of OS • 36 Format USB drive as an NTFS file system (FAT 32 on some USB drives have file
Create & Run VM from USB Flash Drive • • • Fork of Virtual. Box called Portable Virtual. Box Run VM from USB flash drive as application running under Windows (like a virtualized version Windows 8 Enterprise Windows to Go option) Caveats • Requires administrator privileges to run • Consumes hard drive space, RAM (can adjust), processing power • Need licensed copy of OS • 36 Format USB drive as an NTFS file system (FAT 32 on some USB drives have file
 Create & Run VM from USB Flash Drive • Download Portable Virtual. Box (http: //www. vbox. me/) • Extract and launch Portable-Virtual. Box. exe • Click Download installation files of Virtual. Box • Click Extract files box for 32 -bit or 64 -bit operating systems • Check Start Portable-Virtual. Box after the extract and/or compress • IMPORTANT: Click OK button in bottom left corner (NOT Exit button) 37
Create & Run VM from USB Flash Drive • Download Portable Virtual. Box (http: //www. vbox. me/) • Extract and launch Portable-Virtual. Box. exe • Click Download installation files of Virtual. Box • Click Extract files box for 32 -bit or 64 -bit operating systems • Check Start Portable-Virtual. Box after the extract and/or compress • IMPORTANT: Click OK button in bottom left corner (NOT Exit button) 37
 Create & Run VM from USB Flash Drive • Launch Portable-Virtual. Box. exe to enter Virtual. Box • Network and USB support are disabled by default • • Can create VM of Windows, Linux Mint (http: //www. linuxmint. com/), Android (https: //code. google. com/p/android-x 86/downloads/list) Can also be used in Chapter 10 Mobile Device Security 38
Create & Run VM from USB Flash Drive • Launch Portable-Virtual. Box. exe to enter Virtual. Box • Network and USB support are disabled by default • • Can create VM of Windows, Linux Mint (http: //www. linuxmint. com/), Android (https: //code. google. com/p/android-x 86/downloads/list) Can also be used in Chapter 10 Mobile Device Security 38
 Chapter 2 Malware & Social Engineering Attacks • Tools for Teaching Security+ 39
Chapter 2 Malware & Social Engineering Attacks • Tools for Teaching Security+ 39
 Chapter 2 Projects Security+ Guide 5 e • Project 2 -1: Write-Protecting and Disabling a USB Flash Drive (Thumbscrew) • Project 2 -2: Scan for Rootkits Using a Basic Tool (TDSSKiller) • Project 2 -3: Scan for Rootkits Using an Advanced Tool (GMER) • Project 2 -4: Use a Software Keylogger (Spyrix) 40
Chapter 2 Projects Security+ Guide 5 e • Project 2 -1: Write-Protecting and Disabling a USB Flash Drive (Thumbscrew) • Project 2 -2: Scan for Rootkits Using a Basic Tool (TDSSKiller) • Project 2 -3: Scan for Rootkits Using an Advanced Tool (GMER) • Project 2 -4: Use a Software Keylogger (Spyrix) 40
 41
41
 42
42
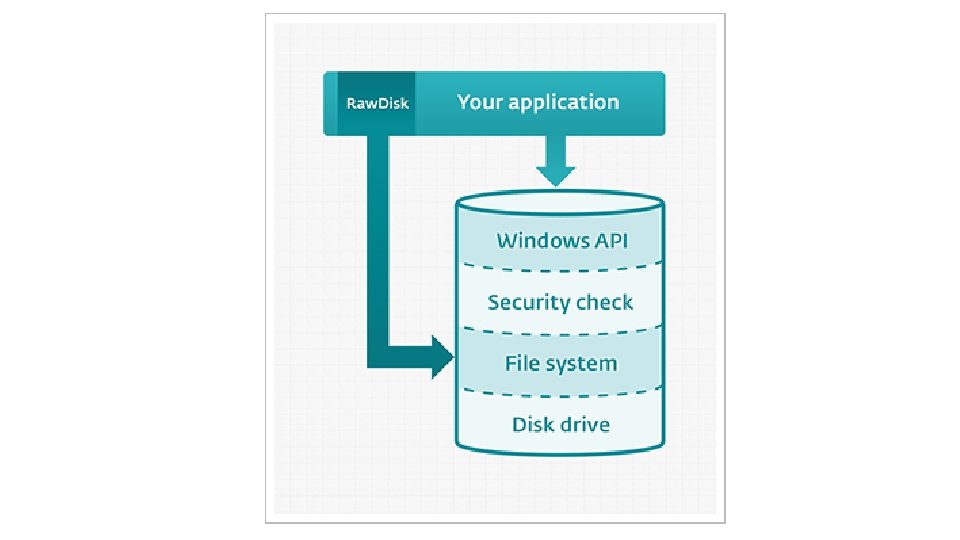
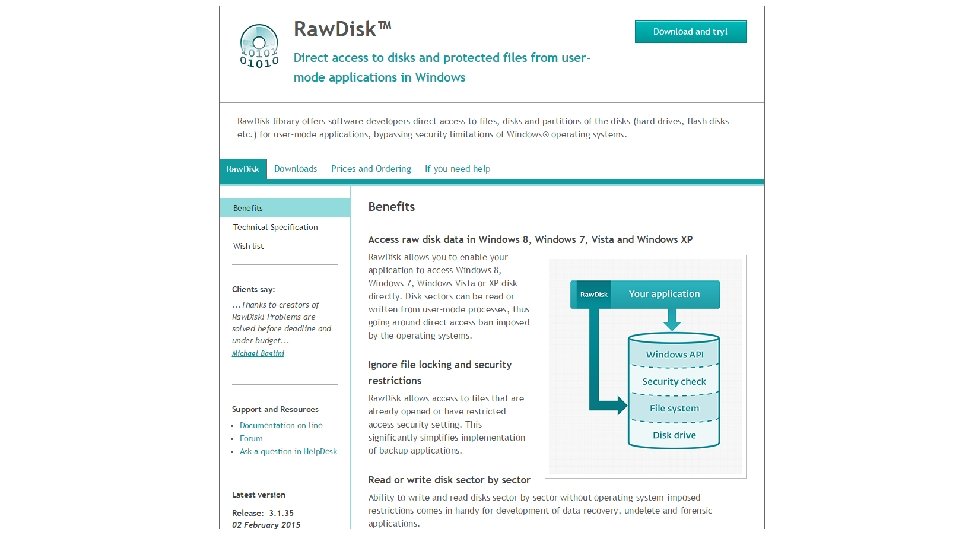
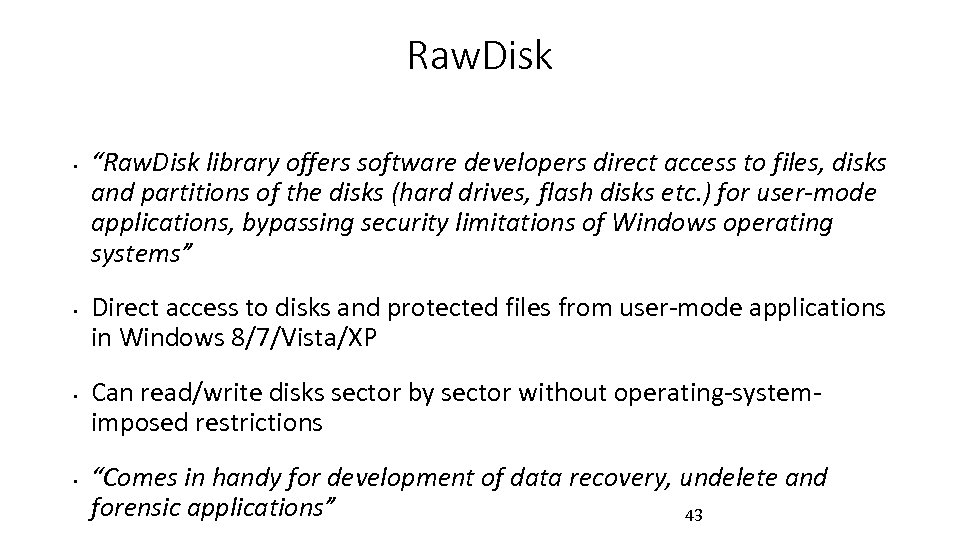 Raw. Disk • • “Raw. Disk library offers software developers direct access to files, disks and partitions of the disks (hard drives, flash disks etc. ) for user-mode applications, bypassing security limitations of Windows operating systems” Direct access to disks and protected files from user-mode applications in Windows 8/7/Vista/XP Can read/write disks sector by sector without operating-systemimposed restrictions “Comes in handy for development of data recovery, undelete and forensic applications” 43
Raw. Disk • • “Raw. Disk library offers software developers direct access to files, disks and partitions of the disks (hard drives, flash disks etc. ) for user-mode applications, bypassing security limitations of Windows operating systems” Direct access to disks and protected files from user-mode applications in Windows 8/7/Vista/XP Can read/write disks sector by sector without operating-systemimposed restrictions “Comes in handy for development of data recovery, undelete and forensic applications” 43
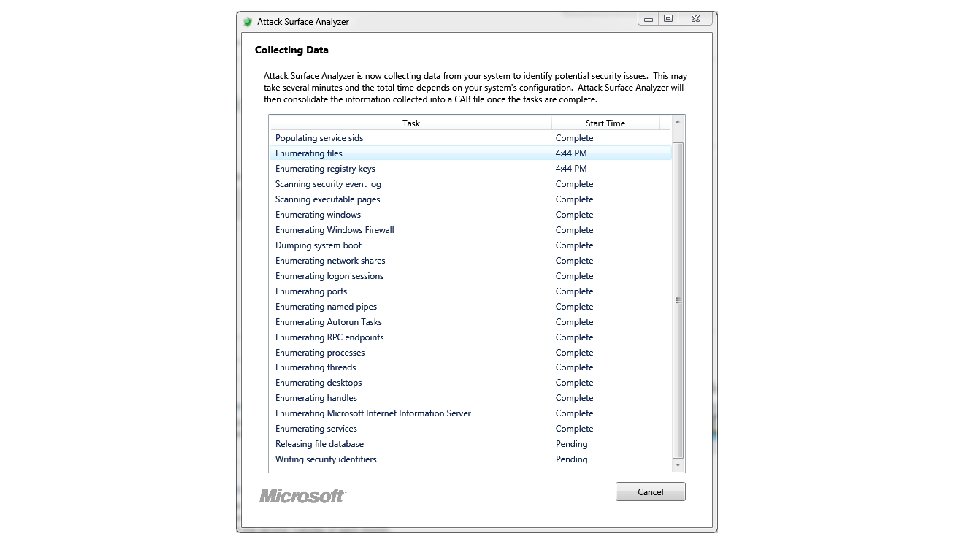
 Microsoft Attack Surface Analyzer • • “Understand how the attack surface of Windows systems change as a result of installing software” Can take snap shot of multiple security related information elements on a system, then after the system changes can take another snapshot Compares the before and after snapshots and show what changed in an HTML report http: //www. microsoft. com/en-us/download/details. aspx? id=24487 44
Microsoft Attack Surface Analyzer • • “Understand how the attack surface of Windows systems change as a result of installing software” Can take snap shot of multiple security related information elements on a system, then after the system changes can take another snapshot Compares the before and after snapshots and show what changed in an HTML report http: //www. microsoft. com/en-us/download/details. aspx? id=24487 44
 45
45
 DVWA • DVWA is PHP/My. SQL vulnerable web application • Install Apache Webserver • Install Mysql Server • Install PHP • Install and configure DVWA • Can perform XSS, SQL injection attacks • http: //www. dvwa. co. uk/ 46
DVWA • DVWA is PHP/My. SQL vulnerable web application • Install Apache Webserver • Install Mysql Server • Install PHP • Install and configure DVWA • Can perform XSS, SQL injection attacks • http: //www. dvwa. co. uk/ 46
 Web. Goat • • • Web. Goat - Deliberately insecure web application designed to teach web application security lessons Install and practice with Web. Goat in either J 2 EE or Web. Goat for . Net in ASP. NET. Users demonstrate their understanding of a security issue by exploiting a real vulnerability in the Web. Goat applications Example: User must use SQL injection to steal fake credit card numbers https: //www. owasp. org/index. php/Category: OWASP_Web. Goat_Proj 47
Web. Goat • • • Web. Goat - Deliberately insecure web application designed to teach web application security lessons Install and practice with Web. Goat in either J 2 EE or Web. Goat for . Net in ASP. NET. Users demonstrate their understanding of a security issue by exploiting a real vulnerability in the Web. Goat applications Example: User must use SQL injection to steal fake credit card numbers https: //www. owasp. org/index. php/Category: OWASP_Web. Goat_Proj 47
 Chapter 3 Application & Network-Based Attacks • Tools for Teaching Security+ 48
Chapter 3 Application & Network-Based Attacks • Tools for Teaching Security+ 48
 Chapter 3 Projects Security+ Guide 5 e • • Project 3 -1: Scan Web Browser Plug-ins (Qualys Browser Check) Project 3 -2: Configure Microsoft Windows Data Execution Prevention (DEP) • Project 3 -3: Set Web Browser Security • Project 3 -4: Hosts File Attack • Project 3 -5: ARP Poisoning • Project 3 -6: Create an HTTP Header • Project 3 -7: Manage Flash Cookies 49
Chapter 3 Projects Security+ Guide 5 e • • Project 3 -1: Scan Web Browser Plug-ins (Qualys Browser Check) Project 3 -2: Configure Microsoft Windows Data Execution Prevention (DEP) • Project 3 -3: Set Web Browser Security • Project 3 -4: Hosts File Attack • Project 3 -5: ARP Poisoning • Project 3 -6: Create an HTTP Header • Project 3 -7: Manage Flash Cookies 49
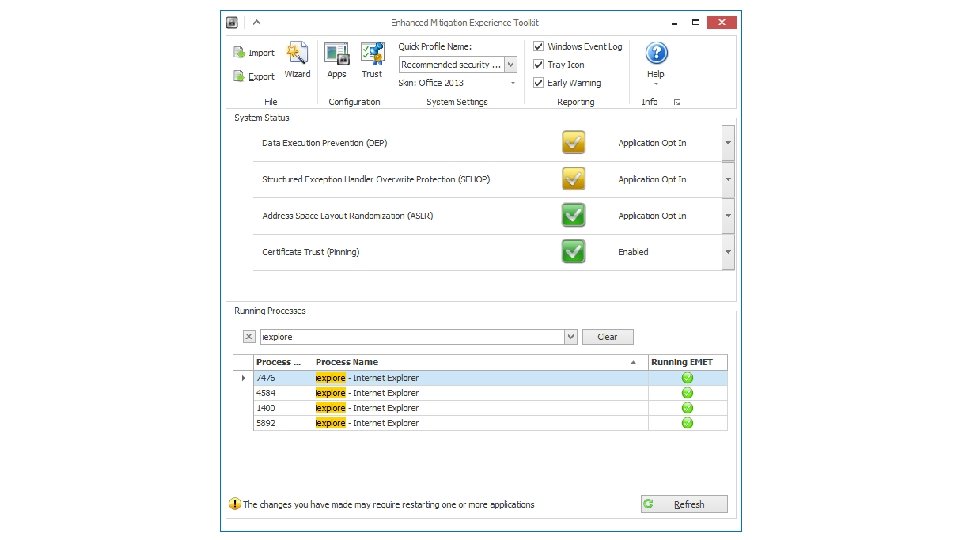
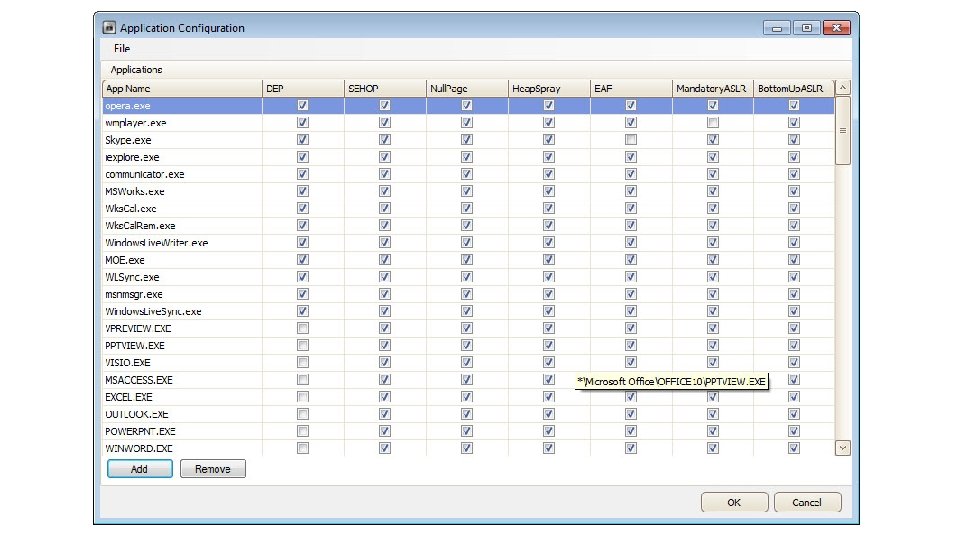
 Enhanced Mitigation Experience Toolkit (EMET) • • Strengthens the security of non-Microsoft applications by using defenses built within Windows Includes “Attack Surface Reduction” can block some of an application’s modules or plugins that might be abused EMET tell Internet Explorer to halt an SSL connection if an untrusted certificate is detected without sending session data http: //www. microsoft. com/en-us/download/details. aspx? id=43714 50
Enhanced Mitigation Experience Toolkit (EMET) • • Strengthens the security of non-Microsoft applications by using defenses built within Windows Includes “Attack Surface Reduction” can block some of an application’s modules or plugins that might be abused EMET tell Internet Explorer to halt an SSL connection if an untrusted certificate is detected without sending session data http: //www. microsoft. com/en-us/download/details. aspx? id=43714 50
 51
51
 52
52
 Chapter 4 Host, Application, and Data Security • Tools for Teaching Security+ 53
Chapter 4 Host, Application, and Data Security • Tools for Teaching Security+ 53
 Chapter 4 Projects Security+ Guide 5 e • Project 4 -1: Test Antivirus Software • Project 4 -2: Setting Windows Local Security Policy • Project 4 -3: Viewing Windows Firewall Settings • Project 4 -4: Analyze Files and URLs for Viruses Using Virus. Total 54
Chapter 4 Projects Security+ Guide 5 e • Project 4 -1: Test Antivirus Software • Project 4 -2: Setting Windows Local Security Policy • Project 4 -3: Viewing Windows Firewall Settings • Project 4 -4: Analyze Files and URLs for Viruses Using Virus. Total 54
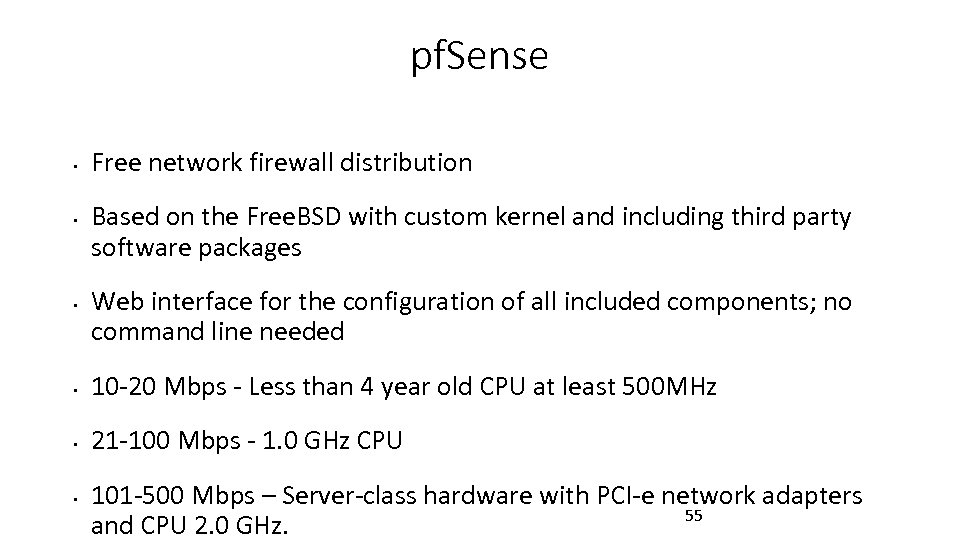 pf. Sense • • • Free network firewall distribution Based on the Free. BSD with custom kernel and including third party software packages Web interface for the configuration of all included components; no command line needed • 10 -20 Mbps - Less than 4 year old CPU at least 500 MHz • 21 -100 Mbps - 1. 0 GHz CPU • 101 -500 Mbps – Server-class hardware with PCI-e network adapters 55 and CPU 2. 0 GHz.
pf. Sense • • • Free network firewall distribution Based on the Free. BSD with custom kernel and including third party software packages Web interface for the configuration of all included components; no command line needed • 10 -20 Mbps - Less than 4 year old CPU at least 500 MHz • 21 -100 Mbps - 1. 0 GHz CPU • 101 -500 Mbps – Server-class hardware with PCI-e network adapters 55 and CPU 2. 0 GHz.
 Chapter 5 Basic Cryptography • Tools for Teaching Security+ 56
Chapter 5 Basic Cryptography • Tools for Teaching Security+ 56
 Chapter 5 Projects Security+ Guide 5 e • Project 5 -1: Using Open. Puff Steganography • Project 5 -2: Running an RSA Cipher Demonstration • Project 5 -3: Installing Command-Line Hash Generators and Comparing Hashes • Project 5 -4: Installing GUI Hash Generators and Comparing Digests • Project 5 -5: Using Microsoft’s Encrypting File System (EFS) • Project 5 -6: Using True. Crypt 57
Chapter 5 Projects Security+ Guide 5 e • Project 5 -1: Using Open. Puff Steganography • Project 5 -2: Running an RSA Cipher Demonstration • Project 5 -3: Installing Command-Line Hash Generators and Comparing Hashes • Project 5 -4: Installing GUI Hash Generators and Comparing Digests • Project 5 -5: Using Microsoft’s Encrypting File System (EFS) • Project 5 -6: Using True. Crypt 57
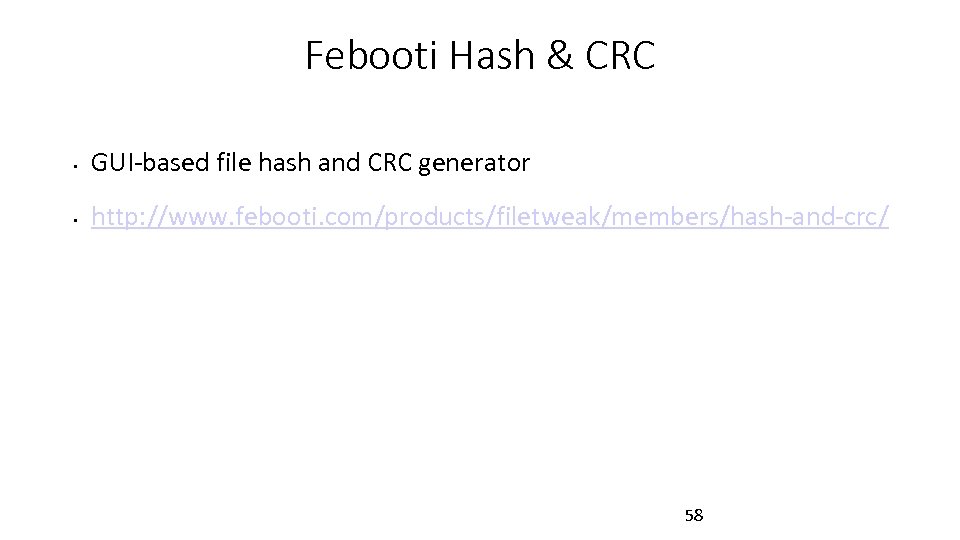 Febooti Hash & CRC • GUI-based file hash and CRC generator • http: //www. febooti. com/products/filetweak/members/hash-and-crc/ 58
Febooti Hash & CRC • GUI-based file hash and CRC generator • http: //www. febooti. com/products/filetweak/members/hash-and-crc/ 58
 True. Crypt Alternatives • • True. Crypt suddenly ceased operations 2014 True. Crypt v 7. 1 a still available (https: //www. grc. com/misc/truecrypt. htm) • Vera. Crypt (https: //veracrypt. codeplex. com/) • Disk. Cryptor (https: //diskcryptor. net/wiki/Main_Page) • Cipher. Shed (https: //ciphershed. org/) • Best. Crypt (http: //www. jetico. com/) 59
True. Crypt Alternatives • • True. Crypt suddenly ceased operations 2014 True. Crypt v 7. 1 a still available (https: //www. grc. com/misc/truecrypt. htm) • Vera. Crypt (https: //veracrypt. codeplex. com/) • Disk. Cryptor (https: //diskcryptor. net/wiki/Main_Page) • Cipher. Shed (https: //ciphershed. org/) • Best. Crypt (http: //www. jetico. com/) 59
 Chapter 6 Advanced Cryptography • Tools for Teaching Security+ 60
Chapter 6 Advanced Cryptography • Tools for Teaching Security+ 60
 Chapter 6 Projects Security+ Guide 5 e • Project 6 -1: SSL Server and Client Tests • Project 6 -2: Viewing Digital Certificates • Project 6 -3: Viewing Digital Certificate Revocation Lists (CRL) and Untrusted Certificates • Project 6 -4: Downloading and Installing a Digital Certificate • Project 6 -5: Using a Digital Certificate for Signing Documents 61
Chapter 6 Projects Security+ Guide 5 e • Project 6 -1: SSL Server and Client Tests • Project 6 -2: Viewing Digital Certificates • Project 6 -3: Viewing Digital Certificate Revocation Lists (CRL) and Untrusted Certificates • Project 6 -4: Downloading and Installing a Digital Certificate • Project 6 -5: Using a Digital Certificate for Signing Documents 61
 Virtru • • • End-to-end email and attachment encryption using existing email (Chrome, Firefox, Outlook, Mac Mail, i. OS and Android) Install Virtru in browser, mobile device, or email application using Trusted Data Format (TDF) When composing “flip the Virtru switch” to encrypt message and attachments Recipients can read your message without installing software after verify identity Sender can revoke messages at any time, see and control forwarding, 62
Virtru • • • End-to-end email and attachment encryption using existing email (Chrome, Firefox, Outlook, Mac Mail, i. OS and Android) Install Virtru in browser, mobile device, or email application using Trusted Data Format (TDF) When composing “flip the Virtru switch” to encrypt message and attachments Recipients can read your message without installing software after verify identity Sender can revoke messages at any time, see and control forwarding, 62
 End-To-End • • End-To-End is Chrome extension to encrypt, decrypt, digital sign, and verify signed messages within the browser using Open. PGP Built on Java. Script-based crypto library Enables key generation, encryption, decryption, digital signature, and signature verification https: //github. com/google/end-to-end 63
End-To-End • • End-To-End is Chrome extension to encrypt, decrypt, digital sign, and verify signed messages within the browser using Open. PGP Built on Java. Script-based crypto library Enables key generation, encryption, decryption, digital signature, and signature verification https: //github. com/google/end-to-end 63
 Fiddler • • Web Debugging - Debug traffic to ensure the proper cookies, headers and cache directives are transferred between the client and server (supports. NET, Java, Ruby, etc. framework) Performance Testing – View HTTP caching and compression HTTP/HTTPS Traffic Recording - Web debugging proxy that logs all HTTP(s) traffic between computer and Internet Web Session Manipulation - Edit web sessions by setting breakpoint to pause the processing of the session and permit alteration of the 64 request/response; can also compose own HTTP requests to run
Fiddler • • Web Debugging - Debug traffic to ensure the proper cookies, headers and cache directives are transferred between the client and server (supports. NET, Java, Ruby, etc. framework) Performance Testing – View HTTP caching and compression HTTP/HTTPS Traffic Recording - Web debugging proxy that logs all HTTP(s) traffic between computer and Internet Web Session Manipulation - Edit web sessions by setting breakpoint to pause the processing of the session and permit alteration of the 64 request/response; can also compose own HTTP requests to run
 Chapter 7 Network Security Fundamentals • Tools for Teaching Security+ 65
Chapter 7 Network Security Fundamentals • Tools for Teaching Security+ 65
 Chapter 7 Projects Security+ Guide 5 e • Project 7 -1: Configuring the Windows Firewall • Project 7 -2: Using Behavior-Based Monitoring Tools • Project 7 -3: Using an Internet Content Filter • Project 7 -4: Configure a Windows Client for Network Access Protection 66
Chapter 7 Projects Security+ Guide 5 e • Project 7 -1: Configuring the Windows Firewall • Project 7 -2: Using Behavior-Based Monitoring Tools • Project 7 -3: Using an Internet Content Filter • Project 7 -4: Configure a Windows Client for Network Access Protection 66
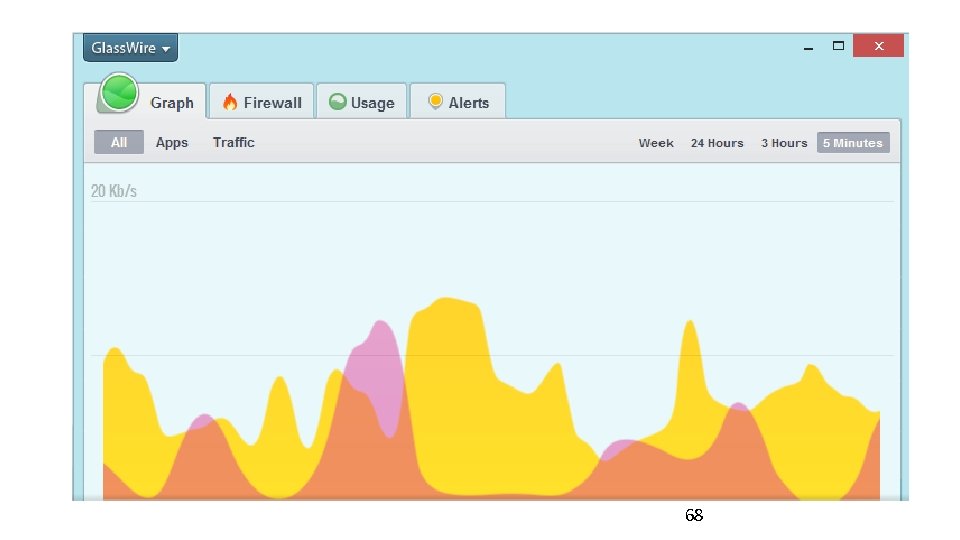
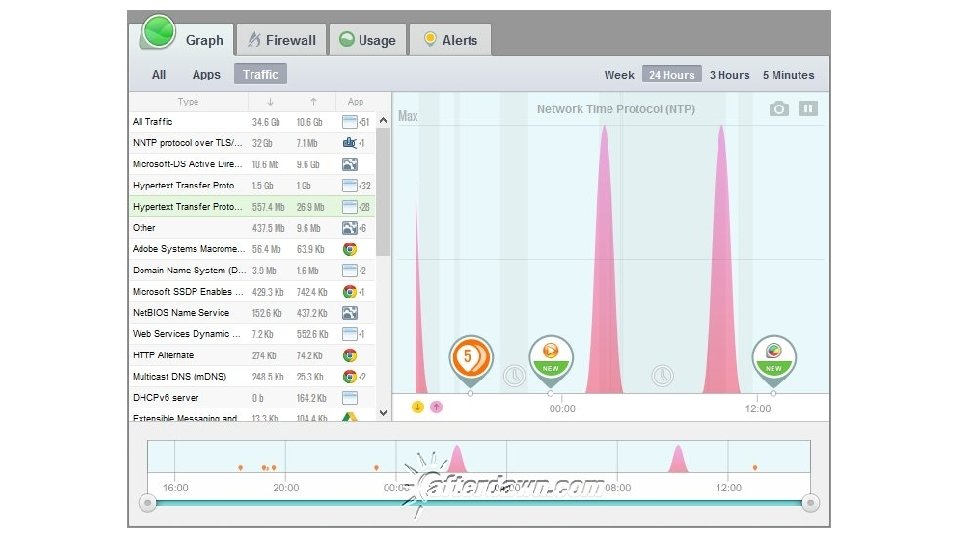
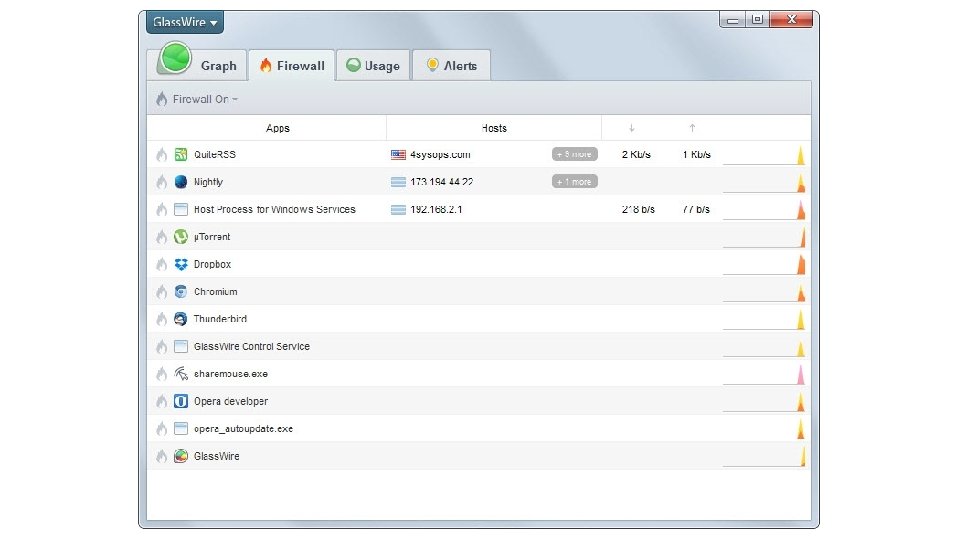
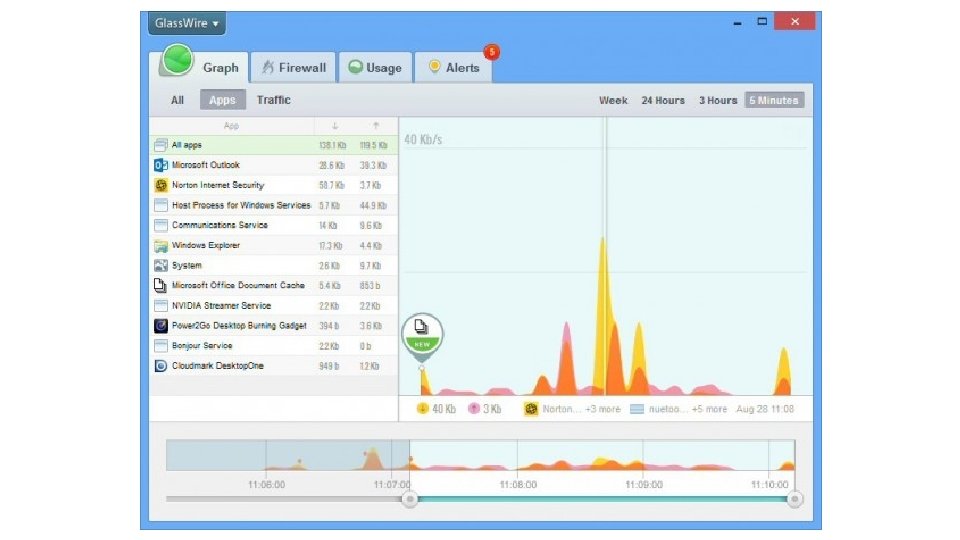
 Glass. Wire • • Network monitor - Visualizes current and past network activity by traffic type, application, geographic location; can go back in time up to 30 days Threat monitoring - Reveals hosts that are known threats, unexpected network system file changes, unusual application changes, ARP spoofing, DNS changes; can remotely monitor servers or other computers and block activity Firewall – Shows new application or service accessing the Internet for the first time Detailed log - Shows current and past servers communicating with 67
Glass. Wire • • Network monitor - Visualizes current and past network activity by traffic type, application, geographic location; can go back in time up to 30 days Threat monitoring - Reveals hosts that are known threats, unexpected network system file changes, unusual application changes, ARP spoofing, DNS changes; can remotely monitor servers or other computers and block activity Firewall – Shows new application or service accessing the Internet for the first time Detailed log - Shows current and past servers communicating with 67
 68
68
 69
69
 70
70
 71
71
 Chapter 8 Administering a Secure Network • Tools for Teaching Security+ 72
Chapter 8 Administering a Secure Network • Tools for Teaching Security+ 72
 Chapter 8 Projects Security+ Guide 5 e • Project 8 -1: Using an Application Sandbox • Project 8 -2: Create a Virtual Machine from a Physical Computer • Project 8 -3: Load the Virtual Machine • • • Project 8 -4: View SNMP Management Information Base (MIB) Elements Project 8 -5: Viewing Logs Using the Microsoft Windows Event Viewer Project 8 -6: Creating a Custom View in Microsoft Windows Event Viewer 73
Chapter 8 Projects Security+ Guide 5 e • Project 8 -1: Using an Application Sandbox • Project 8 -2: Create a Virtual Machine from a Physical Computer • Project 8 -3: Load the Virtual Machine • • • Project 8 -4: View SNMP Management Information Base (MIB) Elements Project 8 -5: Viewing Logs Using the Microsoft Windows Event Viewer Project 8 -6: Creating a Custom View in Microsoft Windows Event Viewer 73
 DNS Services • • Recursive (not authoritative) DNS services are “middlemen” between browser and website content with offer additional functionality for both users and network administrators Content filtering - Block adult sites and other unwanted content, while requiring no software on the computers and devices Malware and phishing blocking - Block sites containing malware, scams and other dangerous content Protection against botnets - Blocks communication with known botnet servers 74
DNS Services • • Recursive (not authoritative) DNS services are “middlemen” between browser and website content with offer additional functionality for both users and network administrators Content filtering - Block adult sites and other unwanted content, while requiring no software on the computers and devices Malware and phishing blocking - Block sites containing malware, scams and other dangerous content Protection against botnets - Blocks communication with known botnet servers 74
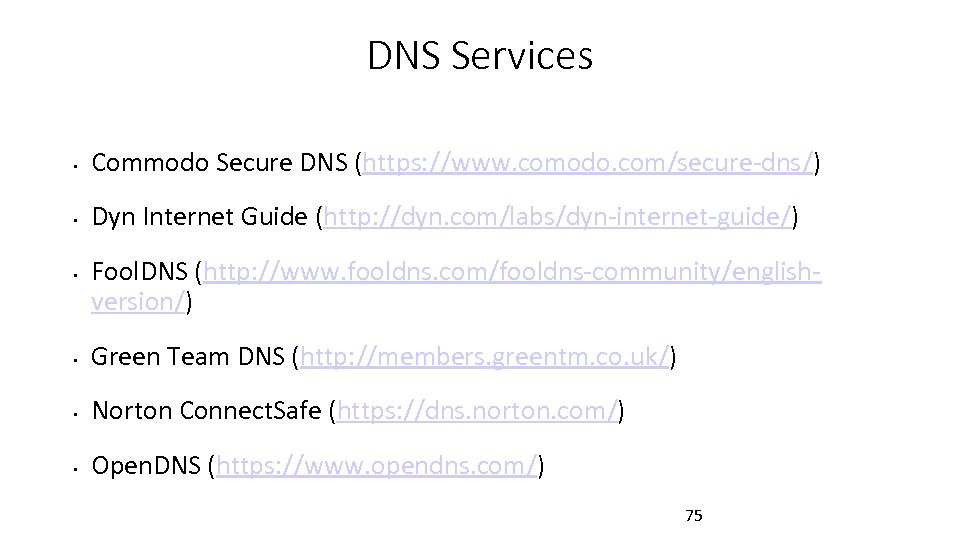 DNS Services • Commodo Secure DNS (https: //www. comodo. com/secure-dns/) • Dyn Internet Guide (http: //dyn. com/labs/dyn-internet-guide/) • Fool. DNS (http: //www. fooldns. com/fooldns-community/englishversion/) • Green Team DNS (http: //members. greentm. co. uk/) • Norton Connect. Safe (https: //dns. norton. com/) • Open. DNS (https: //www. opendns. com/) 75
DNS Services • Commodo Secure DNS (https: //www. comodo. com/secure-dns/) • Dyn Internet Guide (http: //dyn. com/labs/dyn-internet-guide/) • Fool. DNS (http: //www. fooldns. com/fooldns-community/englishversion/) • Green Team DNS (http: //members. greentm. co. uk/) • Norton Connect. Safe (https: //dns. norton. com/) • Open. DNS (https: //www. opendns. com/) 75
 Chapter 9 Wireless Network Security • Tools for Teaching Security+ 76
Chapter 9 Wireless Network Security • Tools for Teaching Security+ 76
 Chapter 9 Projects Security+ Guide 5 e • Project 9 -1: Viewing WLAN Security Information with Vistumbler • Project 9 -2: Substitute a MAC Address Using SMAC • Project 9 -3: Use Microsoft Windows 7 Netsh Commands • Project 9 -4: Configuring Access Points—WPA 2 and WPS 77
Chapter 9 Projects Security+ Guide 5 e • Project 9 -1: Viewing WLAN Security Information with Vistumbler • Project 9 -2: Substitute a MAC Address Using SMAC • Project 9 -3: Use Microsoft Windows 7 Netsh Commands • Project 9 -4: Configuring Access Points—WPA 2 and WPS 77
 Kali Linux • www. kali. com • Formerly “Backtrack” • Open source Debian Linux distribution • Designed for penetration testing: has 300 built-in pen testing tools • Regularly updated and customizable • Different options • Bootable ISO (Live Distro) • Virtual machine 78
Kali Linux • www. kali. com • Formerly “Backtrack” • Open source Debian Linux distribution • Designed for penetration testing: has 300 built-in pen testing tools • Regularly updated and customizable • Different options • Bootable ISO (Live Distro) • Virtual machine 78
 Kali Linux Wireless Tools • • • Kismet – Display wireless networks Airmon-ng – Capture wireless packets, inject packets into wireless network Ifconfig/iwconfig – Part of Linux for configuration of wireless interfaces • Wireshark – Protocol analyzer • Nmap – Network scanner (Zen. Map GUI) • Kali Linux menu 79
Kali Linux Wireless Tools • • • Kismet – Display wireless networks Airmon-ng – Capture wireless packets, inject packets into wireless network Ifconfig/iwconfig – Part of Linux for configuration of wireless interfaces • Wireshark – Protocol analyzer • Nmap – Network scanner (Zen. Map GUI) • Kali Linux menu 79
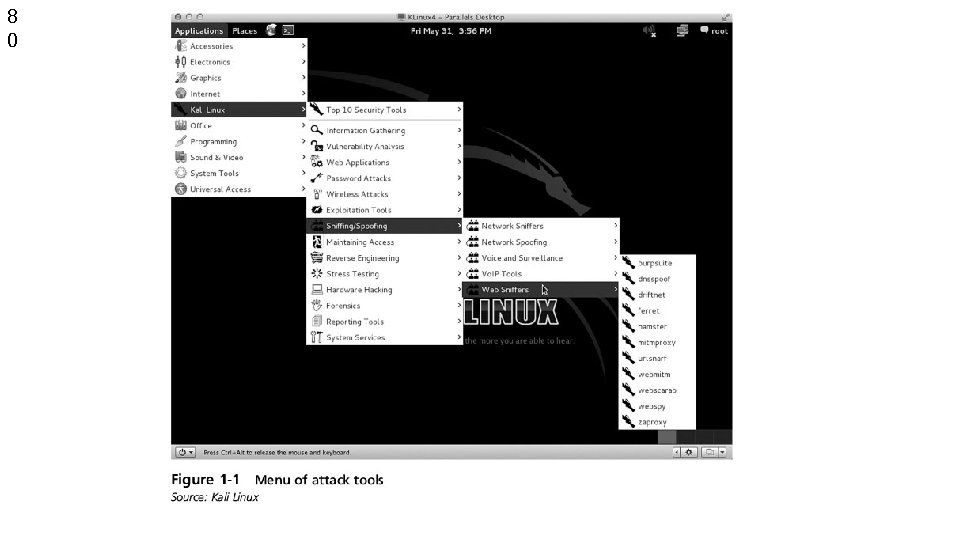 8 0
8 0
 Wireless Adapters for Kali Linux • Wireless USB adapter • Hawking HD 45 U 3 x 3 x 3 USB 3. 0 • Uses Ralink chipset • $40 • 802. 11 n only • Edimax AC-1200 • Edimax EW-7822 UAC 81
Wireless Adapters for Kali Linux • Wireless USB adapter • Hawking HD 45 U 3 x 3 x 3 USB 3. 0 • Uses Ralink chipset • $40 • 802. 11 n only • Edimax AC-1200 • Edimax EW-7822 UAC 81
 • Organizational Systems Wireless Auditor (OSWA-Assistant) Associated certifications • Wi-Fi, Bluetooth, and RFID penetration testing tools • Supports web interface • http: //securitystartshere. org/page-training-oswa-assistant. htm 82
• Organizational Systems Wireless Auditor (OSWA-Assistant) Associated certifications • Wi-Fi, Bluetooth, and RFID penetration testing tools • Supports web interface • http: //securitystartshere. org/page-training-oswa-assistant. htm 82
 OSWA-Assistant: Wi-Fi • Afrag; Aircrack-ng; Airfart; Airpwn; Airsnort; Airsnarf; Airtraf; APHopper; AP-Radar; AP-Utils; Asleap; Chop; Co. WPAtty; Eap. MD 5 pass; Fake. AP; Freeradius Pwnage Edition; Host. APD; Hotspotter; Karma; Kismet; Leapcracker; MDK 3; Moocher. Hunter; Probemapper; Pyrawcovert; Rcovert; Ska; SSIDsniff; SSLstrip; Wardrive; Wavemon; WEPlab; WEP 0 ff; Wi-Find; Wi-Spy Tools; Wifi. Tap; Wifi. Zoo; WPA-attack; WPA Buddy; WPA Supplicant; Wireless Extensions & Wireless Tools package (iwconfig/iwpriv, etc); Zulu 83
OSWA-Assistant: Wi-Fi • Afrag; Aircrack-ng; Airfart; Airpwn; Airsnort; Airsnarf; Airtraf; APHopper; AP-Radar; AP-Utils; Asleap; Chop; Co. WPAtty; Eap. MD 5 pass; Fake. AP; Freeradius Pwnage Edition; Host. APD; Hotspotter; Karma; Kismet; Leapcracker; MDK 3; Moocher. Hunter; Probemapper; Pyrawcovert; Rcovert; Ska; SSIDsniff; SSLstrip; Wardrive; Wavemon; WEPlab; WEP 0 ff; Wi-Find; Wi-Spy Tools; Wifi. Tap; Wifi. Zoo; WPA-attack; WPA Buddy; WPA Supplicant; Wireless Extensions & Wireless Tools package (iwconfig/iwpriv, etc); Zulu 83
 OSWA-Assistant: Bluetooth • Bluebugger; Bluediving Suite; Bluemaho Suite (lite); Blueper; Blueprint; Bluescanner; Bluesmash; Bluesnarfer; Bluesquirrel Suite; BT-Audit; Btfs; Btscanner; Carwhisperer; Ghettotooth; Obexpush-dos; HIDattack; Redfang; Spooftooph; T-Bear; Ussp-push; Vcardblaster; Bluez Bluetooth package with hcitool/hciconfig 84
OSWA-Assistant: Bluetooth • Bluebugger; Bluediving Suite; Bluemaho Suite (lite); Blueper; Blueprint; Bluescanner; Bluesmash; Bluesnarfer; Bluesquirrel Suite; BT-Audit; Btfs; Btscanner; Carwhisperer; Ghettotooth; Obexpush-dos; HIDattack; Redfang; Spooftooph; T-Bear; Ussp-push; Vcardblaster; Bluez Bluetooth package with hcitool/hciconfig 84
 OSWA-Assistant: RFID & Other • • RFID Tools: Rfdump; RFIDiot; Rfidtool Miscellaneous: Macchanger; Metasploit Framework; SET; Wireshar 85
OSWA-Assistant: RFID & Other • • RFID Tools: Rfdump; RFIDiot; Rfidtool Miscellaneous: Macchanger; Metasploit Framework; SET; Wireshar 85
 Reaver • • Reaver implements a brute force attack against Wi-Fi Protected Setup (WPS) registrar PINs in order to recover WPA/WPA 2 passphrases On average Reaver can recover the target AP's plain text WPA/WPA 2 passphrase in 4 -10 hours May only take half this time to guess the correct WPS pin and recover the passphrase https: //code. google. com/p/reaver-wps/ 86
Reaver • • Reaver implements a brute force attack against Wi-Fi Protected Setup (WPS) registrar PINs in order to recover WPA/WPA 2 passphrases On average Reaver can recover the target AP's plain text WPA/WPA 2 passphrase in 4 -10 hours May only take half this time to guess the correct WPS pin and recover the passphrase https: //code. google. com/p/reaver-wps/ 86
 Wifiphisher • • Social engineering attack that as easy way for obtaining credentials from captive portals and third party login pages or WPA/WPA 2 secret passphrases. Attack in three phases: Victim deauthenticated from AP: Wifiphisher continuously jams all target AP devices by sending deauth packets to the client from the AP, to AP from client, and to broadcast address Victim joins a rogue access point: Wifiphisher copies target AP settings to creates rogue AP; sets up a NAT/DHCP server and forwards the right ports so clients start connecting to the rogue AP 87
Wifiphisher • • Social engineering attack that as easy way for obtaining credentials from captive portals and third party login pages or WPA/WPA 2 secret passphrases. Attack in three phases: Victim deauthenticated from AP: Wifiphisher continuously jams all target AP devices by sending deauth packets to the client from the AP, to AP from client, and to broadcast address Victim joins a rogue access point: Wifiphisher copies target AP settings to creates rogue AP; sets up a NAT/DHCP server and forwards the right ports so clients start connecting to the rogue AP 87
 Chapter 10 Mobile Device Security • Tools for Teaching Security+ 88
Chapter 10 Mobile Device Security • Tools for Teaching Security+ 88
 Chapter 10 Projects Security+ Guide 5 e • Project 10 -1: Creating and Using QR Codes • Project 10 -2: Software to Locate a Missing Laptop • Project 10 -3: Installing Bluestacks Android Emulator • Project 10 -4: Installing Security Apps Using Bluestacks Android Emulator 89
Chapter 10 Projects Security+ Guide 5 e • Project 10 -1: Creating and Using QR Codes • Project 10 -2: Software to Locate a Missing Laptop • Project 10 -3: Installing Bluestacks Android Emulator • Project 10 -4: Installing Security Apps Using Bluestacks Android Emulator 89
 Mobile Tracking Software • Monitoring Software • m. Spy (www. mspy. com) • Mobile. Spy (http: //www. mobile-spy. com/) • Mobistealth (http: //www. mobistealth. com/) • MBL Stealth (http: //www. mblstealth. com/main/) 90
Mobile Tracking Software • Monitoring Software • m. Spy (www. mspy. com) • Mobile. Spy (http: //www. mobile-spy. com/) • Mobistealth (http: //www. mobistealth. com/) • MBL Stealth (http: //www. mblstealth. com/main/) 90
 Prey • Lock down devices • Delete stored passwords • https: //preyproject. com/ 91
Prey • Lock down devices • Delete stored passwords • https: //preyproject. com/ 91
 Confide • • • Free i. OS & Android app Can send email along with an attached document/photo (Word, Excel, Power. Point and PDF files stored on Dropbox, Box, Google Drive, One. Drive and other document-storage services) that gets encrypted When the recipient opens it the content is blurry and unreadable Can only be read by touching the screen, and only the line under the finger is readable If someone snaps a picture of the screen only the one exposed line is 92
Confide • • • Free i. OS & Android app Can send email along with an attached document/photo (Word, Excel, Power. Point and PDF files stored on Dropbox, Box, Google Drive, One. Drive and other document-storage services) that gets encrypted When the recipient opens it the content is blurry and unreadable Can only be read by touching the screen, and only the line under the finger is readable If someone snaps a picture of the screen only the one exposed line is 92
 Confide • • If recipient not have Confide app installed a button on the message opens the Apple App Store or Google Play Store on the Confide page so can download Both the recipient and the sender have the ability to delete a message Sender can change the amount of time a message will last before it self-destructs (set message to be viewable for week but change mind after sending it you can adjust life span remotely or instantly delete it Confide for Business will have address book integration, distribution lists and other features and desktop version coming 93
Confide • • If recipient not have Confide app installed a button on the message opens the Apple App Store or Google Play Store on the Confide page so can download Both the recipient and the sender have the ability to delete a message Sender can change the amount of time a message will last before it self-destructs (set message to be viewable for week but change mind after sending it you can adjust life span remotely or instantly delete it Confide for Business will have address book integration, distribution lists and other features and desktop version coming 93
 Dstrux • • Dstrux similar to Confide to send messages & documents encrypted and self-destructing It enables sharing over Facebook or Twitter, but only a link to the secure content in the cloud is shared Can apply controls to a message before you send it (how long before it self-destructs, whether it's blurry upon opening, if recipient can forward) Message can be viewed, but not printed, copied, saved or captured with a screen capture 94
Dstrux • • Dstrux similar to Confide to send messages & documents encrypted and self-destructing It enables sharing over Facebook or Twitter, but only a link to the secure content in the cloud is shared Can apply controls to a message before you send it (how long before it self-destructs, whether it's blurry upon opening, if recipient can forward) Message can be viewed, but not printed, copied, saved or captured with a screen capture 94
 Dstrux • • Before sending decide how long the message will last before it selfdestructs (days, hours or minutes), to blur content, allow/disallow forwarding To see a full image have to rapidly swipe all over the screen, then look fast before it vanishes • Confide more polished, Dstrux more options • https: //dstrux. com/ 95
Dstrux • • Before sending decide how long the message will last before it selfdestructs (days, hours or minutes), to blur content, allow/disallow forwarding To see a full image have to rapidly swipe all over the screen, then look fast before it vanishes • Confide more polished, Dstrux more options • https: //dstrux. com/ 95
 Disconnect • Blocks malicious tracking and malvertising threats disguised as legitimate ads • Privacy icons - See how websites collect and use data • Disconnect - Visualize & block invisible websites that track • https: //disconnect. me/disconnect 96
Disconnect • Blocks malicious tracking and malvertising threats disguised as legitimate ads • Privacy icons - See how websites collect and use data • Disconnect - Visualize & block invisible websites that track • https: //disconnect. me/disconnect 96
 Other Android Apps • • • VT View Source – View HTML, CSS, Java. Script, XML sources of webpages and remotely located files (https: //play. google. com/store/apps/details? id=com. tozalakyan. view source) k. WS Android Web Server - https: //play. google. com/store/apps/details? id=org. xeustechnologies. android. kws Hacker’s Keyboard – Full keyboard (https: //play. google. com/store/apps/details? id=org. pocketworkstatio n. pckeyboard&feature=search_result) 97
Other Android Apps • • • VT View Source – View HTML, CSS, Java. Script, XML sources of webpages and remotely located files (https: //play. google. com/store/apps/details? id=com. tozalakyan. view source) k. WS Android Web Server - https: //play. google. com/store/apps/details? id=org. xeustechnologies. android. kws Hacker’s Keyboard – Full keyboard (https: //play. google. com/store/apps/details? id=org. pocketworkstatio n. pckeyboard&feature=search_result) 97
 Chapter 11 Access Control Fundamentals • Tools for Teaching Security+ 98
Chapter 11 Access Control Fundamentals • Tools for Teaching Security+ 98
 Chapter 11 Projects Security+ Guide 5 e • • Project 11 -1: Using Windows Local Group Policy Editor Project 11 -2: Using Discretionary Access Control to Share Files in Windows • Project 11 -3: Enabling IEEE 802. 1 x • Project 11 -4: Explore User Account Control (UAC) 99
Chapter 11 Projects Security+ Guide 5 e • • Project 11 -1: Using Windows Local Group Policy Editor Project 11 -2: Using Discretionary Access Control to Share Files in Windows • Project 11 -3: Enabling IEEE 802. 1 x • Project 11 -4: Explore User Account Control (UAC) 99
 Chapter 12 Authentication and Account Management • Tools for Teaching Security+ 100
Chapter 12 Authentication and Account Management • Tools for Teaching Security+ 100
 Chapter 12 Projects Security+ Guide 5 e • Project 12 -1: Use an Online Rainbow Table Cracker • Project 12 -2: Keystroke Dynamics • Project 12 -3: Download and Install a Password Management Program • Project 12 -4: Use Cognitive Biometrics • Project 12 -5: Create an Open. ID Account • Project 12 -6: Use an Open. ID Account 101
Chapter 12 Projects Security+ Guide 5 e • Project 12 -1: Use an Online Rainbow Table Cracker • Project 12 -2: Keystroke Dynamics • Project 12 -3: Download and Install a Password Management Program • Project 12 -4: Use Cognitive Biometrics • Project 12 -5: Create an Open. ID Account • Project 12 -6: Use an Open. ID Account 101
 Useless User Tricks - 1 • • Even when users attempt to create stronger passwords, they generally follow predictable patterns Appending - Typically only add a number after letters (caitlin 1 or cheer 99); if they add all more it in sequence letters+punctuation+number (amanda. 7 or chris#6). Replacing – A zero is used instead of the letter o (passw 0 rd), the digit 1 for the letter i (denn 1 s), or a dollar sign for an s (be$tfriend). Attackers are aware of these patterns in passwords and can search for them, dramatically weakening passwords and make it easier for attackers to crack them. 102
Useless User Tricks - 1 • • Even when users attempt to create stronger passwords, they generally follow predictable patterns Appending - Typically only add a number after letters (caitlin 1 or cheer 99); if they add all more it in sequence letters+punctuation+number (amanda. 7 or chris#6). Replacing – A zero is used instead of the letter o (passw 0 rd), the digit 1 for the letter i (denn 1 s), or a dollar sign for an s (be$tfriend). Attackers are aware of these patterns in passwords and can search for them, dramatically weakening passwords and make it easier for attackers to crack them. 102
 Useless User Tricks - 2 1. 2. 3. 4. Take the first letter of the site’s name in lower case (Gmail. com -> g) Add the last two digits of your birth year but reverse them (1993 -> 39) Add a + Add the next four letters of the site’s name in upper case ("gmail. com" -> MAIL) 5. Add a - 6. 103 Add the last four digits of your phone number backwards (877 -555 -
Useless User Tricks - 2 1. 2. 3. 4. Take the first letter of the site’s name in lower case (Gmail. com -> g) Add the last two digits of your birth year but reverse them (1993 -> 39) Add a + Add the next four letters of the site’s name in upper case ("gmail. com" -> MAIL) 5. Add a - 6. 103 Add the last four digits of your phone number backwards (877 -555 -
 Useless User Tricks - 3 • • • The Qwerty Card is a simple plastic card laid out like a Qwerty keyboard and also has a unique code like sh(/J 3 Hq. You add your own secret password (shine) to the code and then append the encoded version of the site’s name using the character map on the card Amazon becomes. u. rqf which is added to the previous strings to generate the complete password sh(/J 3 Hqshine. u. rqf 104
Useless User Tricks - 3 • • • The Qwerty Card is a simple plastic card laid out like a Qwerty keyboard and also has a unique code like sh(/J 3 Hq. You add your own secret password (shine) to the code and then append the encoded version of the site’s name using the character map on the card Amazon becomes. u. rqf which is added to the previous strings to generate the complete password sh(/J 3 Hqshine. u. rqf 104
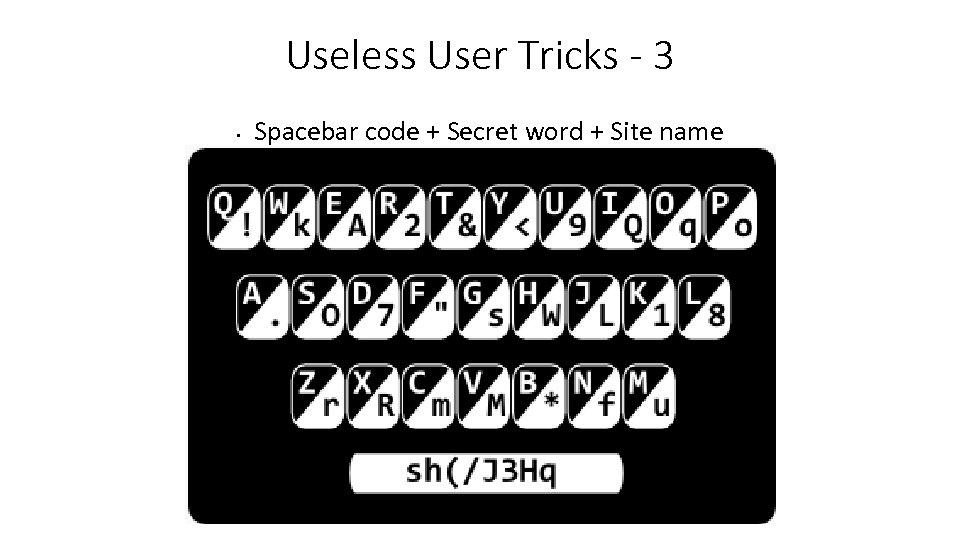 Useless User Tricks - 3 • Spacebar code + Secret word + Site name 105
Useless User Tricks - 3 • Spacebar code + Secret word + Site name 105
 Password Principles 1. 2. 3. Any password that can be memorized is a weak password Any password that is repeated is a weak password Use technology instead of brain 106
Password Principles 1. 2. 3. Any password that can be memorized is a weak password Any password that is repeated is a weak password Use technology instead of brain 106
 Length Over Complexity • How Secure Is My Password • Password Strength Calculator • Haystack • Password Meter 107
Length Over Complexity • How Secure Is My Password • Password Strength Calculator • Haystack • Password Meter 107
 Password Management Applications • Dashlane • Last. Pass • Kee. Pass • 1 Password • Blur • Password. Box • Robo. Form 108
Password Management Applications • Dashlane • Last. Pass • Kee. Pass • 1 Password • Blur • Password. Box • Robo. Form 108
 Hash. Cat • • Optimum password cracking program Brute-Force attack, combinator attack, dictionary attack, fingerprint attack, hybrid attack, mask attack, permutation attack, rule-based attack • Multi-GPU (up to 128 gpus) • Multi-Hash (up to 100 million hashes) • Multi-OS (Linux & Windows native binaries) • http: //hashcat. net/oclhashcat/ 109
Hash. Cat • • Optimum password cracking program Brute-Force attack, combinator attack, dictionary attack, fingerprint attack, hybrid attack, mask attack, permutation attack, rule-based attack • Multi-GPU (up to 128 gpus) • Multi-Hash (up to 100 million hashes) • Multi-OS (Linux & Windows native binaries) • http: //hashcat. net/oclhashcat/ 109
 Security+ 5 e • Security+ Guide to Network Security Fundaments, 5 e from Cengage Learning (9781305093911) • Published August, 2014 • Maps completely to new SY 0 -401 exam objectives • Retains popular format • Increased from 14 to 15 chapters (new chapter on Mobile Device Security) • Increased chapter length by 2 -3 pages 110
Security+ 5 e • Security+ Guide to Network Security Fundaments, 5 e from Cengage Learning (9781305093911) • Published August, 2014 • Maps completely to new SY 0 -401 exam objectives • Retains popular format • Increased from 14 to 15 chapters (new chapter on Mobile Device Security) • Increased chapter length by 2 -3 pages 110
 Security+ 5 e • Cryptography moved up to Chapters 5 -6 • New “Today’s Attacks & Defenses” openers • New sectional units • New and updated Review Questions, Hands-On Projects, Case Projects • New lecture videos • New material on companion web site to be updated regularly • Cengage Mind. Tap for Security+ 5 e released Mar 18 2015 111
Security+ 5 e • Cryptography moved up to Chapters 5 -6 • New “Today’s Attacks & Defenses” openers • New sectional units • New and updated Review Questions, Hands-On Projects, Case Projects • New lecture videos • New material on companion web site to be updated regularly • Cengage Mind. Tap for Security+ 5 e released Mar 18 2015 111
 Mind. Tap 112
Mind. Tap 112
 Tools For Teaching Security+ Mark Ciampa Western Kentucky University mark. ciampa@wku. edu 113
Tools For Teaching Security+ Mark Ciampa Western Kentucky University mark. ciampa@wku. edu 113


