96508ae52cbbe17b3033eb5fd3ae6a3f.ppt
- Количество слайдов: 31

Tools for Grid/Campus Integration: Grid. Shib and My. Proxy Internet 2 Advanced Camp July 1, 2005 Von Welch vwelch@ncsa. uiuc. edu July 1, 2005 I 2 Advanced CAMP
Outline • Grid. Shib – Overview of Shibboleth and Globus – Our Motivation and Use Cases – Integration Approach – Status • My. Proxy – Overview – Local Authn Support July 1, 2005 I 2 Advanced CAMP 2
Shibboleth • http: //shibboleth. internet 2. edu/ • Internet 2 project • Allows for inter-institutional sharing of web resources (via browsers) – Provides attributes for authorization between institutions • Allows for pseudonymity via temporary, meaningless identifiers called ‘Handles’ • Standards-based (SAML) • Being extended to non-web resources July 1, 2005 I 2 Advanced CAMP 3
Shibboleth • Identity Provider composed of single sign-on (SSO) and attribute authority (AA) services • SSO: authenticates user locally and issues authentication assertion with Handle – Assertion is short-lived bearer assertion – Handle is also short-lived and non-identifying – Handle is registered with AA • Attribute Authority responds to queries regarding handle July 1, 2005 I 2 Advanced CAMP 4
Shibboleth • Service Provider composed of Assertion Consumer and Attribute Requestor • Assertion Consumer parses authentication assertion • Attribute Requestor: request attributes from AA – Attributes used for authorization • Where Are You From (WAYF) service determines user’s Identity Provider July 1, 2005 I 2 Advanced CAMP 5
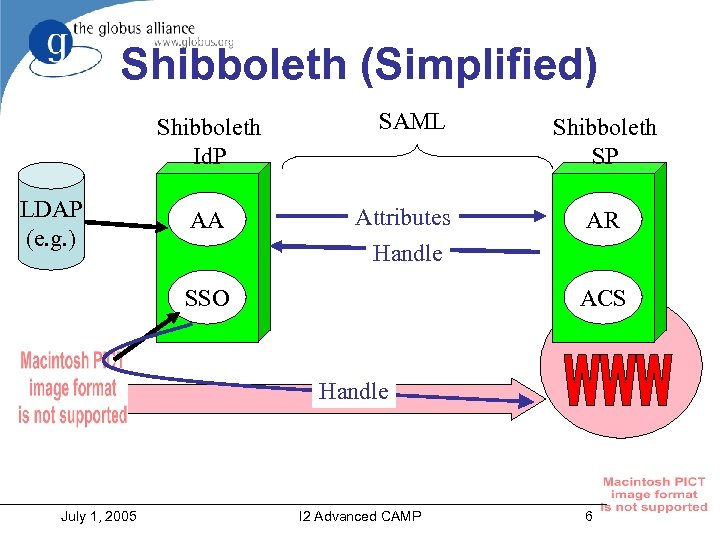
Shibboleth (Simplified) Shibboleth Id. P LDAP (e. g. ) AA SAML Attributes Handle SSO Shibboleth SP AR ACS Handle July 1, 2005 I 2 Advanced CAMP 6

Globus Toolkit • http: //www. globus. org • Toolkit for Grid computing – Job submission, data movement, data management, resource management • Based on Web Services and WSRF • Security based on X. 509 identity- and proxy -certificates – Maybe from conventional or on-line CAs • Some initial attribute-based authorization July 1, 2005 I 2 Advanced CAMP 7
Motivation • Many Grid VOs are focused on science or business other than IT support – Don’t have expertise or resources to run security services • Allow for leveraging of Shibboleth code and deployments run by campuses July 1, 2005 I 2 Advanced CAMP 8
Use Cases • Project leveraging campus attributes – Simplest case • Project-operated Shib service – Project operates own service, conceptually easy, but not ideal • Campus-operated, project-administered Shib – Ideal mix, but need mechanisms for provisioning of attribute administration July 1, 2005 I 2 Advanced CAMP 9
Integration Approach • Conceptually, replace Shibboleth’s handle-based authentication with X 509 – Provides stronger security for non-web browser apps – Works with existing PKI install base • To allow leveraging of Shibboleth install base, require as few changes to Shibboleth AA as possible July 1, 2005 I 2 Advanced CAMP 10
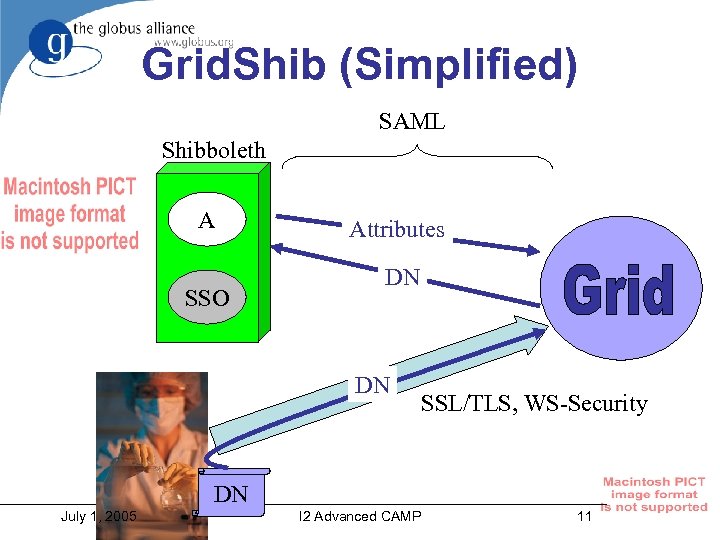
Grid. Shib (Simplified) SAML Shibboleth A SSO Attributes DN DN SSL/TLS, WS-Security DN July 1, 2005 I 2 Advanced CAMP 11
Integration Areas • • • Assertion Transmission Attribute Authority Discovery Distribute Attribute Administration User Registration Pseudonymous Interaction Authorization July 1, 2005 I 2 Advanced CAMP 12
Assertion Transmission • How to get SAML assertions from AA into Globus? • Initially: Pull mode with Globus acting as a Shibboleth Attribute Requestor • Will explore Pull modes to help with privacy and role combination • Implement Grid Name Mapper to map X 509 DNs to local identities used to obtain attributes July 1, 2005 I 2 Advanced CAMP 13

Attribute Authority Discovery • No interactive WAYF service in the Grid • Place identifier of Identity Provider in cert – Either in long-term EEC or short-term Proxy Cert • Will explore pushing attributes – Avoids the problem – Might also address combined attributes from multiple AAs July 1, 2005 I 2 Advanced CAMP 14

• Distributed Attribute Administration but may Campus is ideal for running services, not know all attributes of users • How does a campus issue attributes for which it is not authoritative? – E. g. IEEE Membership of staff – In Grid case, Project Membership • This may be the largest hurdle due to social, political and/or legal issues – Need accepted cookbook for process • Plan on exploring signet – http: //middleware. internet 2. edu/signet/ July 1, 2005 I 2 Advanced CAMP 15
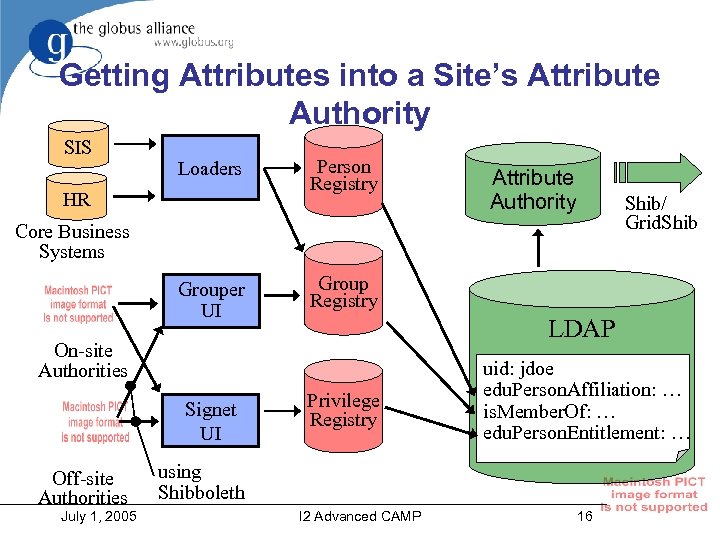
Getting Attributes into a Site’s Attribute Authority SIS Loaders HR Person Registry Attribute Authority Shib/ Grid. Shib Core Business Systems Grouper UI Group Registry LDAP On-site Authorities Signet UI Off-site Authorities July 1, 2005 Privilege Registry uid: jdoe edu. Person. Affiliation: … is. Member. Of: … edu. Person. Entitlement: … using Shibboleth I 2 Advanced CAMP 16

User Registration • How does the mapping from the User’s X 509 DN to local Campus identity get made in Name. Mapper configuration? • In initial version, this will be manual process • Yes, far from ideal • We envision – Something akin to a registration service that authenticates user’s X 509 and local credentials and puts mapping in automatically – Or a portal that hides all the X 509 from the user and also handles this mapping • E. g. PURSE, GAMA July 1, 2005 I 2 Advanced CAMP 17
Pseudonymous Interaction • How to maintain Shibboleth pseudonymous functionality with X 509? • Will develop online CA that issues certificates with non-identifying DNs – Register with AA just as SSO – Basically holder-of-key assertions July 1, 2005 I 2 Advanced CAMP 18
Authorization • Develop authorization framework in Globus Toolkit • Pluggable modules for processing authentication, gathering and processing attributes and rendering decisions • XACML used for expressing gathered identity, attribute and policy information – Convert Attributes into common format for policy evaluation – Allows for common evaluation of attributes expressed in SAML and X 509 (and others…) July 1, 2005 I 2 Advanced CAMP 19
Grid. Shib Status • Testing initial version internal to project • Will be a drop-in addition to GT 4. 0 and Shibboleth 1. 3 • Plan on releasing Beta version 2 -3 weeks after Shibboleth 1. 3 is released • Looking for interested testers • Project website: – http: //grid. ncsa. uiuc. edu/Grid. Shib/ July 1, 2005 I 2 Advanced CAMP 20
Acknowledgements and Details • NSF NMI project to allow the use of Shibboleth-issued attributes for authorization in NMI Grids built on the Globus Toolkit – Funded under NSF award SCI-0438424 • Grid. Shib team: NCSA, U. Chicago, ANL – Tom Barton, David Champion, Tim Freemon, Kate Keahey, Tom Scavo, Frank Siebenlist, Von Welch • Working in collaboration with Steven Carmody, Scott Cantor, Bob Morgan and the rest of the Internet 2 Shibboleth Design team July 1, 2005 I 2 Advanced CAMP 21
My. Proxy Enhancements for Local Integration Bill Baker, Jim Basney and Von Welch NCSA July 1, 2005 I 2 Advanced CAMP
What is My. Proxy? • Independent Globus Toolkit add-on since 2000 – To be included in Globus Toolkit 4. 0 • A service for securing private keys – Keys stored encrypted with user-chosen password – Keys never leave the My. Proxy server • A service for retrieving proxy credentials • A commonly-used service for grid portal security – Integrated with OGCE, Grid. Sphere, and Grid. Port, PURSE, GAMA July 1, 2005 I 2 Advanced CAMP 23
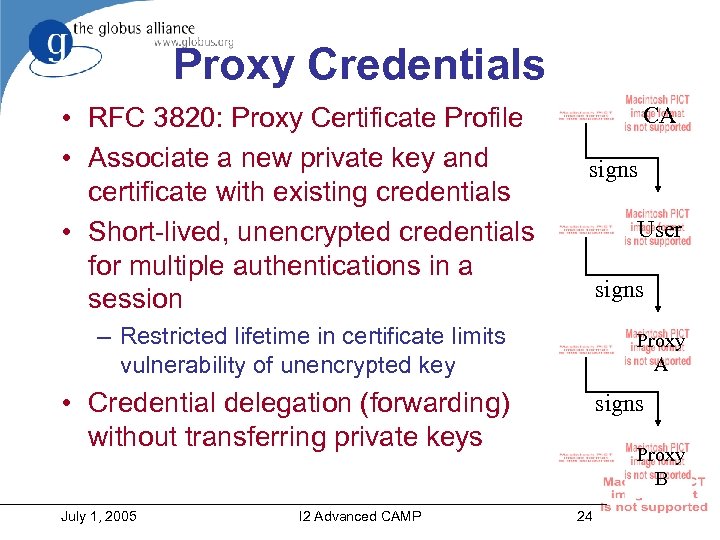
Proxy Credentials • RFC 3820: Proxy Certificate Profile • Associate a new private key and certificate with existing credentials • Short-lived, unencrypted credentials for multiple authentications in a session CA signs User signs – Restricted lifetime in certificate limits vulnerability of unencrypted key Proxy A • Credential delegation (forwarding) without transferring private keys July 1, 2005 I 2 Advanced CAMP signs Proxy B 24
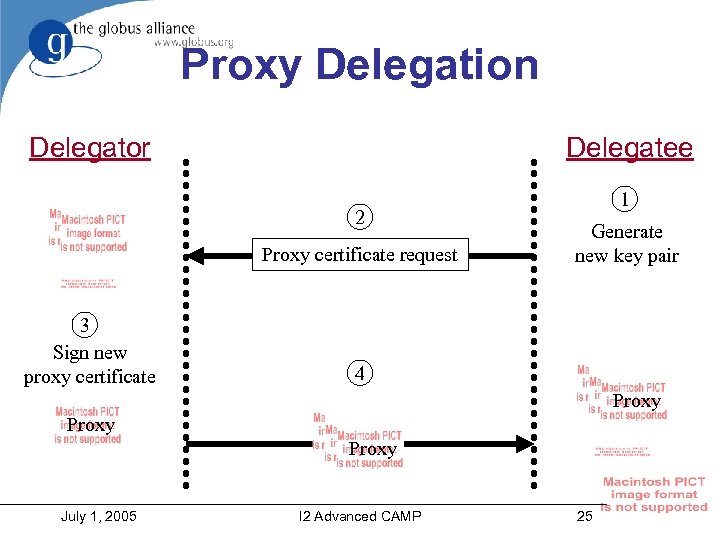
Proxy Delegation Delegator Delegatee 2 Proxy certificate request 3 Sign new proxy certificate 1 Generate new key pair 4 Proxy July 1, 2005 I 2 Advanced CAMP 25
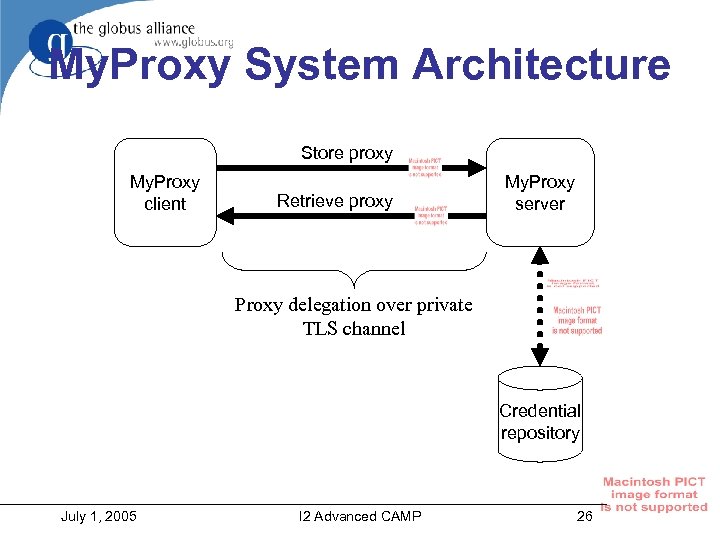
My. Proxy System Architecture Store proxy My. Proxy client Retrieve proxy My. Proxy server Proxy delegation over private TLS channel Credential repository July 1, 2005 I 2 Advanced CAMP 26
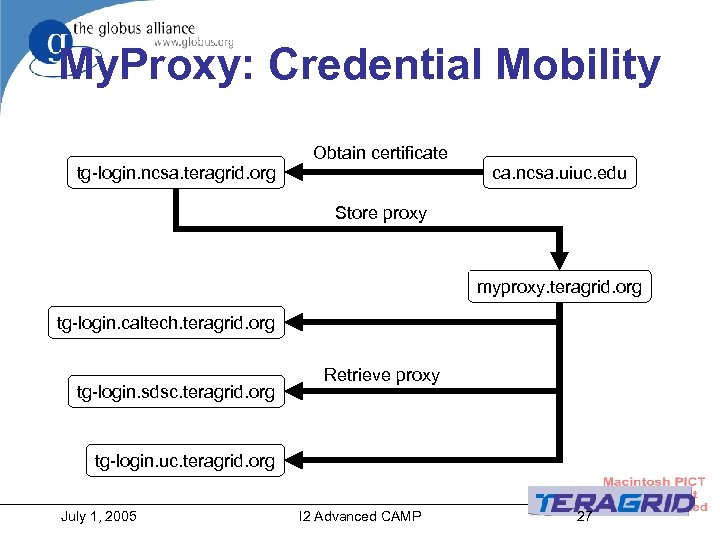
My. Proxy: Credential Mobility tg-login. ncsa. teragrid. org Obtain certificate ca. ncsa. uiuc. edu Store proxy myproxy. teragrid. org tg-login. caltech. teragrid. org tg-login. sdsc. teragrid. org Retrieve proxy tg-login. uc. teragrid. org July 1, 2005 I 2 Advanced CAMP 27
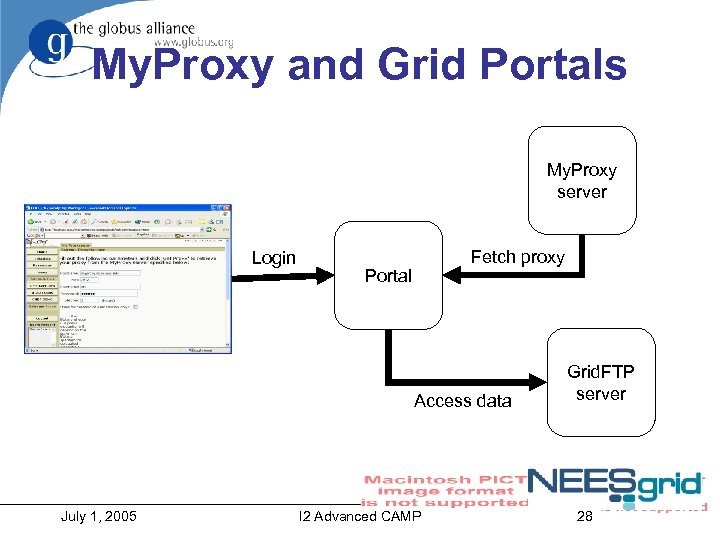
My. Proxy and Grid Portals My. Proxy server Login Fetch proxy Portal Access data July 1, 2005 I 2 Advanced CAMP Grid. FTP server 28
My. Proxy and PAM • My. Proxy now has ability to use PAM for authentication – As a replacement for locally-stored password • Users can use existing authentication mechanism to access Grid Credentials • Has been tested with PAM modules for LDAP, Kerberos, OTP (Crypto. Card) via RADIUS July 1, 2005 I 2 Advanced CAMP 29
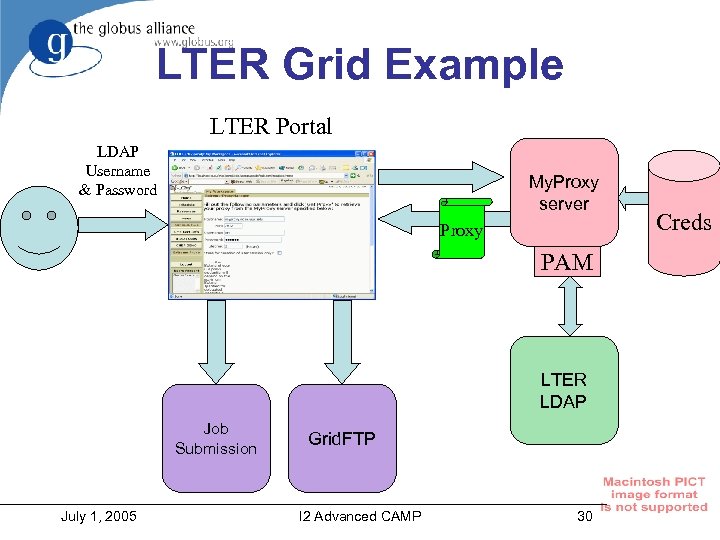
LTER Grid Example LTER Portal LDAP Username & Password My. Proxy server Proxy PAM LTER LDAP Job Submission July 1, 2005 Grid. FTP I 2 Advanced CAMP 30 Creds
Status • Support in My. Proxy v 2. 0 which is PAM released • Available at http: //myproxy. ncsa. uiuc. edu • Pam-specific documentation: – http: //grid. ncsa. uiuc. edu/myproxy/pam. html • PAM enhancements funded by NMI Grids Center July 1, 2005 I 2 Advanced CAMP 31
96508ae52cbbe17b3033eb5fd3ae6a3f.ppt