83b078b1a98fdb0e246c39580af0ff81.ppt
- Количество слайдов: 11

Tolerating Intrusions Through Secure System Reconfiguration Dennis Heimbigner and Alexander Wolf University of Colorado at Boulder John Knight University of Virginia Prem Devanbu, Michael Gertz, and Karl Levitt University of California at Davis
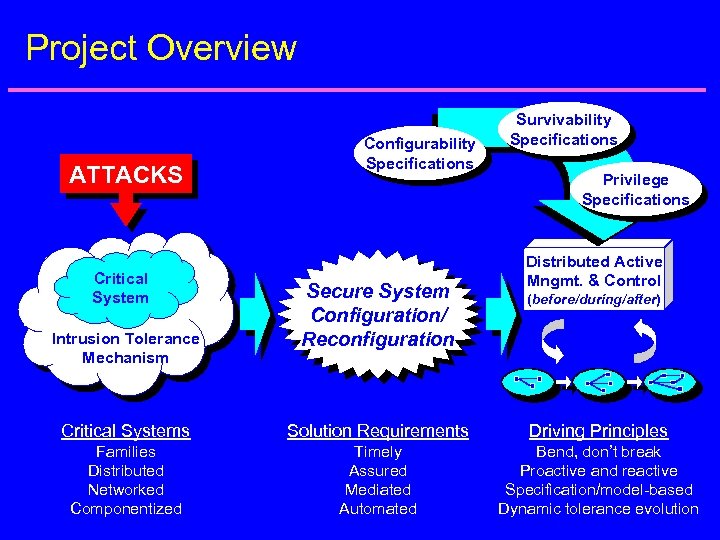
Project Overview ATTACKS Critical System Intrusion Tolerance Mechanism Configurability Specifications Secure System Configuration/ Reconfiguration Survivability Specifications Privilege Specifications Distributed Active Mngmt. & Control (before/during/after) Critical Systems Solution Requirements Driving Principles Families Distributed Networked Componentized Timely Assured Mediated Automated Bend, don’t break Proactive and reactive Specification/model-based Dynamic tolerance evolution
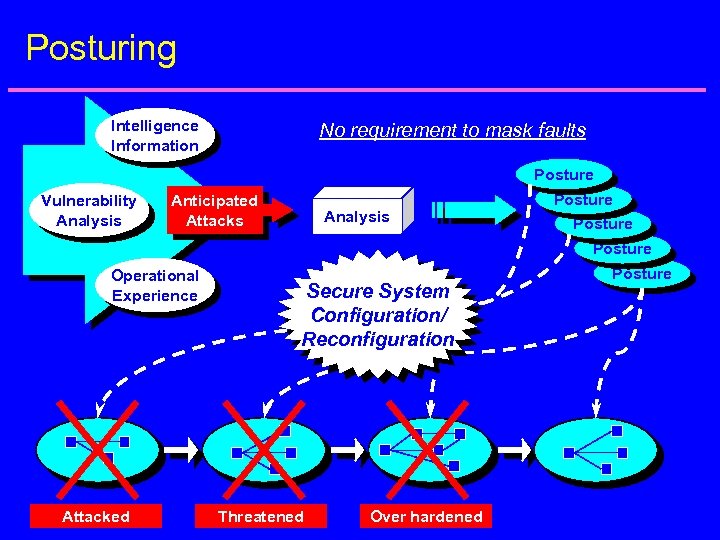
Posturing Intelligence Information No requirement to mask faults Posture Vulnerability Analysis Anticipated Attacks Analysis Posture Operational Experience Attacked Secure System Configuration/ Reconfiguration Threatened Over hardened Posture
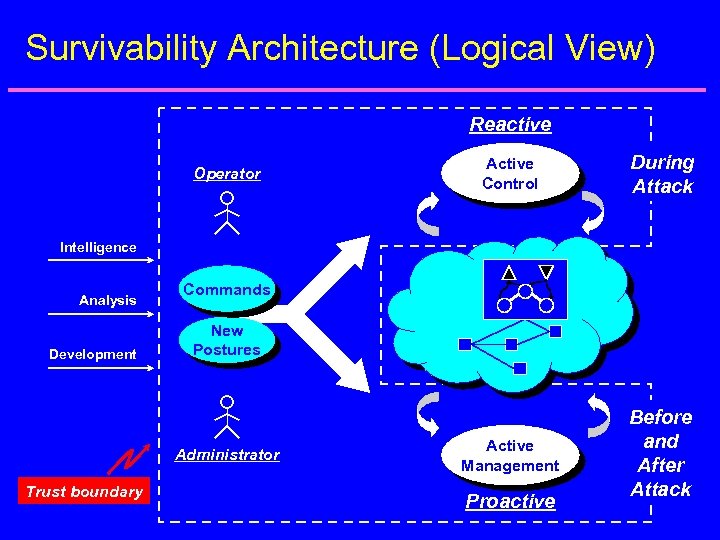
Survivability Architecture (Logical View) Reactive Operator Active Control During Attack Active Management Before and After Attack Intelligence Analysis Development Commands New Postures Administrator Trust boundary Proactive
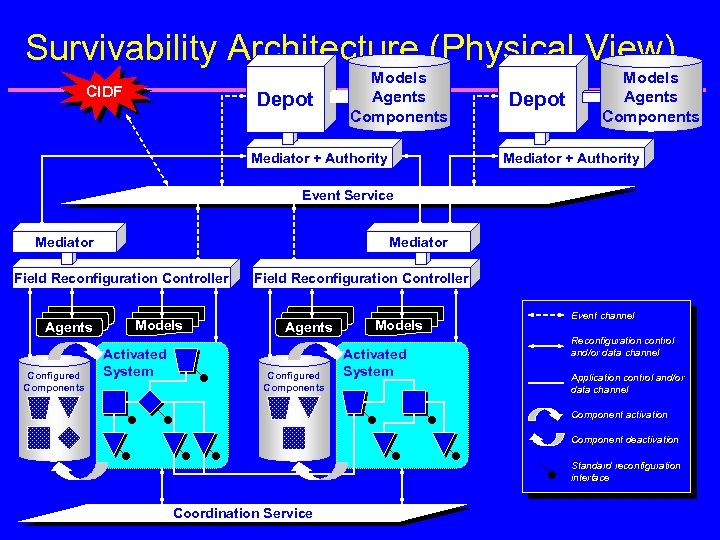
Survivability Architecture (Physical View) CIDF Depot Models Agents Components Mediator + Authority Event Service Mediator Field Reconfiguration Controller Agents Configured Components Models Activated System Event channel Reconfiguration control and/or data channel Application control and/or data channel Component activation Component deactivation Standard reconfiguration interface Coordination Service

Integrated Technology Strategy u Application reconfiguration for survivability – RAPTOR modeling system – Survivability specification u Agent-based software configuration and deployment – Software Dock software deployment system – Siena wide-area event notification service u Agent and information security – Secure, flexible information access – Trusted code on untrustworthy platforms
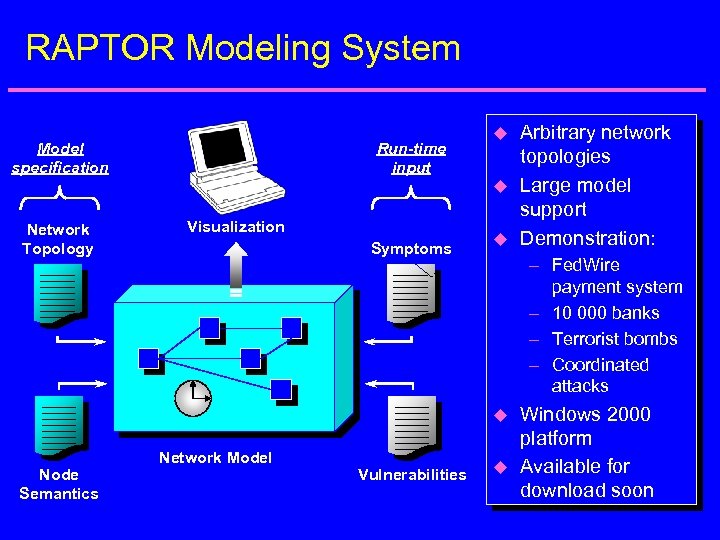
RAPTOR Modeling System Model specification Run-time input u u Network Topology Visualization Symptoms u – Fed. Wire payment system – 10 000 banks – Terrorist bombs – Coordinated attacks u Node Semantics Network Model Vulnerabilities Arbitrary network topologies Large model support Demonstration: u Windows 2000 platform Available for download soon
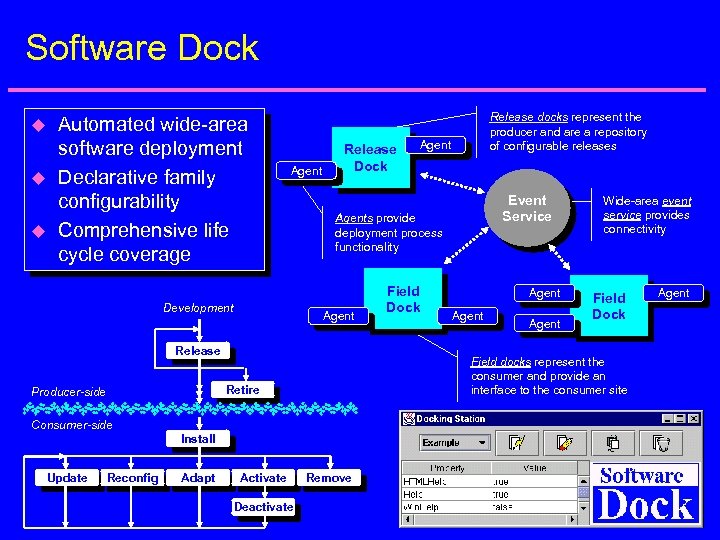
Software Dock u u u Automated wide-area software deployment Declarative family configurability Comprehensive life cycle coverage Agent Development Release Dock Agent Retire Install Reconfig Adapt Activate Deactivate Event Service Field Dock Agent Wide-area event service provides connectivity Field Dock Field docks represent the consumer and provide an interface to the consumer site Consumer-side Update Agents provide deployment process functionality Release Producer-side Release docks represent the producer and are a repository of configurable releases Remove Agent
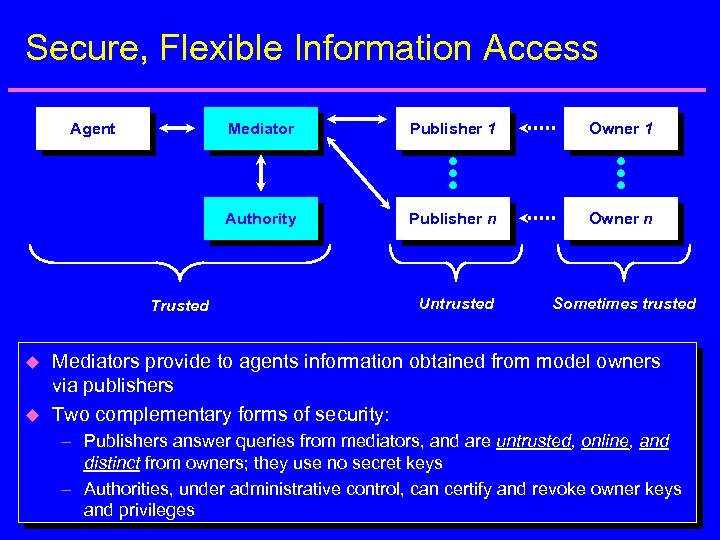
Secure, Flexible Information Access Agent Mediator u u Owner 1 Authority Trusted Publisher 1 Publisher n Owner n Untrusted Sometimes trusted Mediators provide to agents information obtained from model owners via publishers Two complementary forms of security: – Publishers answer queries from mediators, and are untrusted, online, and distinct from owners; they use no secret keys – Authorities, under administrative control, can certify and revoke owner keys and privileges
Evaluation u Continuous assessment – Increasingly sophisticated models – Increasingly capable prototypes u Scenario-based approach – Increasingly complex attacks – Informed by interaction with domain experts » banking and finance, power, transportation » security threats and vulnerabilities u Symptom and vulnerability injection u Metrics: speed, precision, and availability

83b078b1a98fdb0e246c39580af0ff81.ppt