744385e079a14335d8e9019e9a947db3.ppt
- Количество слайдов: 15
 Todays’ Agenda Private vs. Personal Information Take out your notebook and copy the following information. • Private information – information that can be used for identity theft. • Personal information – information that cannot be used to identify you. • Identity Theft – when someone uses another persons information to pretend to be that person.
Todays’ Agenda Private vs. Personal Information Take out your notebook and copy the following information. • Private information – information that can be used for identity theft. • Personal information – information that cannot be used to identify you. • Identity Theft – when someone uses another persons information to pretend to be that person.
 What sites do you like to visit? What do you like to do online?
What sites do you like to visit? What do you like to do online?
 Private vs. Personal Information Many of the websites that you visit online request user information before you are allowed to participate in the online activity. • Can you name some examples? • What kind of information do you need to provide? • Why do you think they ask for this information?
Private vs. Personal Information Many of the websites that you visit online request user information before you are allowed to participate in the online activity. • Can you name some examples? • What kind of information do you need to provide? • Why do you think they ask for this information?
 Private and Personal Information Name the ways that information can be shared online. Online Games Social networking Online Shopping Video Sharing sites Are you giving out information that you should keep private?
Private and Personal Information Name the ways that information can be shared online. Online Games Social networking Online Shopping Video Sharing sites Are you giving out information that you should keep private?
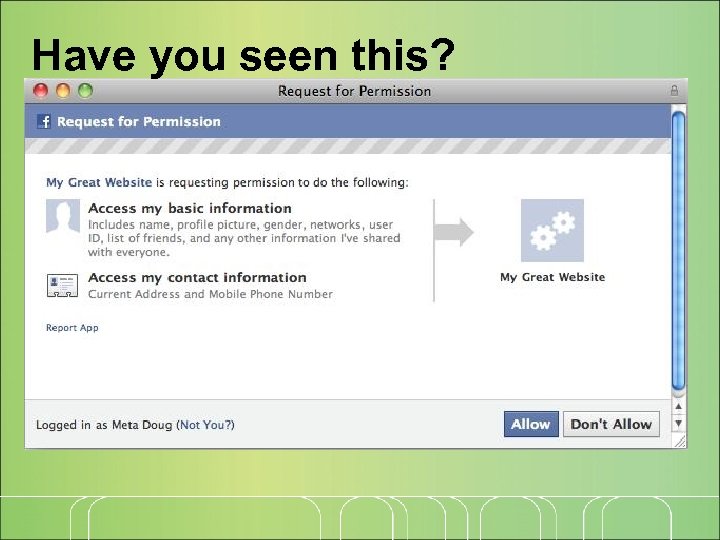 Have you seen this?
Have you seen this?
 FACEBOOK What kinds of information are you asked to provide? Do you stop to consider whether providing the information requested will reveal private identity information? Facebook “Places” may reveal too much http: //www. nbc 12. com/Global/story. asp? S=14054243
FACEBOOK What kinds of information are you asked to provide? Do you stop to consider whether providing the information requested will reveal private identity information? Facebook “Places” may reveal too much http: //www. nbc 12. com/Global/story. asp? S=14054243
 Identity Theft Kids, teens and adults, are targets for identity theft. An identity thief uses some else’s PRIVATE identity information to pretend to be that person Once that thief has a new identity, they can use it to get a driver’s license, or buy things or apply for a credit card in your name.
Identity Theft Kids, teens and adults, are targets for identity theft. An identity thief uses some else’s PRIVATE identity information to pretend to be that person Once that thief has a new identity, they can use it to get a driver’s license, or buy things or apply for a credit card in your name.
 What IS Private information? Full name Postal address E-mail address Phone numbers Passwords Credit card numbers Social Security number Mother’s maiden name
What IS Private information? Full name Postal address E-mail address Phone numbers Passwords Credit card numbers Social Security number Mother’s maiden name
 Personal Information Are you giving out information about yourself that should be kept private? Personal Information Your age Male or female How many brothers and sisters Favorite music Favorite food Name of your pet Opinion about an issue
Personal Information Are you giving out information about yourself that should be kept private? Personal Information Your age Male or female How many brothers and sisters Favorite music Favorite food Name of your pet Opinion about an issue
 Todays’ Agenda Smart, Safe, and Secure Online Take out your notebook and copy the following information. • Spam – commercial messages that you didn’t ask for • Malware – “malicious software” created to damage your files, your computer or steal your identity • Phishing – spammers who want to steal private identity information and send messages or links that look real. How computer viruses work
Todays’ Agenda Smart, Safe, and Secure Online Take out your notebook and copy the following information. • Spam – commercial messages that you didn’t ask for • Malware – “malicious software” created to damage your files, your computer or steal your identity • Phishing – spammers who want to steal private identity information and send messages or links that look real. How computer viruses work
 Smart, Safe, and Secure Online Firewall – a way to prevent outsiders getting into a computer or network. Antivirus software - software is used to prevent, detect, and remove malware and computer viruses
Smart, Safe, and Secure Online Firewall – a way to prevent outsiders getting into a computer or network. Antivirus software - software is used to prevent, detect, and remove malware and computer viruses
 Tips for fighting Spam or Malware 1. Always back up your computers 2. Update your operating system 3. Use and update antivirus and other security software 4. Be sure you know what new software does before you install it 5. Report spam or phishing to your ISP (Internet Service Provider)
Tips for fighting Spam or Malware 1. Always back up your computers 2. Update your operating system 3. Use and update antivirus and other security software 4. Be sure you know what new software does before you install it 5. Report spam or phishing to your ISP (Internet Service Provider)
 Strong Passwords How do people steal passwords? 1. Someone can look over your shoulder 2. Someone can get your password from a public computer (always log off and don’t save “remember password” option) 3. Be careful of “phishing” emails asking for private information
Strong Passwords How do people steal passwords? 1. Someone can look over your shoulder 2. Someone can get your password from a public computer (always log off and don’t save “remember password” option) 3. Be careful of “phishing” emails asking for private information
 Strong Passwords 1. Only your parents should know your password. 2. Don't use passwords that are easy to guess—like your nickname or your pet's name—because people who know you well can guess these kinds of passwords. 3. Never use any private identity information in your password 4. Don't use a word in the dictionary as a password because hackers use programs that will try every word in the dictionary to guess passwords. 5. Use a combination of numbers and letters 6. Don’t use obvious sequences like xyz, 123
Strong Passwords 1. Only your parents should know your password. 2. Don't use passwords that are easy to guess—like your nickname or your pet's name—because people who know you well can guess these kinds of passwords. 3. Never use any private identity information in your password 4. Don't use a word in the dictionary as a password because hackers use programs that will try every word in the dictionary to guess passwords. 5. Use a combination of numbers and letters 6. Don’t use obvious sequences like xyz, 123
 Do you “talk” too much? ? Protecting Yourself Online
Do you “talk” too much? ? Protecting Yourself Online


