2df29d5d68535e36a1506cd2fe748626.ppt
- Количество слайдов: 10

Threat Overview: The Italian Job / HTML_IFRAME. CU June 18, 2007 Presenter Name Presenter Title

Agenda • • • How It Works Status Messaging/Positioning Trend Micro Protection Best Practices Additional Information Classification Copyright 2007 - Trend Micro Inc. 2

How It Works “The Italian Job” is a Web threat that uses multiple components to surreptitiously infect a targeted group of users. ① First, URLs of legitimate websites are compromised by HTML_IFRAME. CU, a malware that takes advantage of an i. Frame vulnerability. Many of these sites are related to tourism and travel, entertainment, autos and adult content. ② When a user visits a compromised website, s/he is redirected to a second site, which contains a Javascript downloader, JS_DLOADER. NTJ. ③ DLOADER exploits browser vulnerabilities to download a Trojan, TROJ_SMALL. HCK, onto the target system. ④ Two additional Trojans are downloaded, TROJ_AGENT. UHL and TROJ_PAKES. NC. ⑤ The PAKES Trojan goes on to download an information stealer, a variant of the SINOWAL Trojan. The AGENT Trojan can act as a proxy server that allos a remote user to anonymously connect to the Internet via an infected PC. Classification Copyright 2007 - Trend Micro Inc. 3
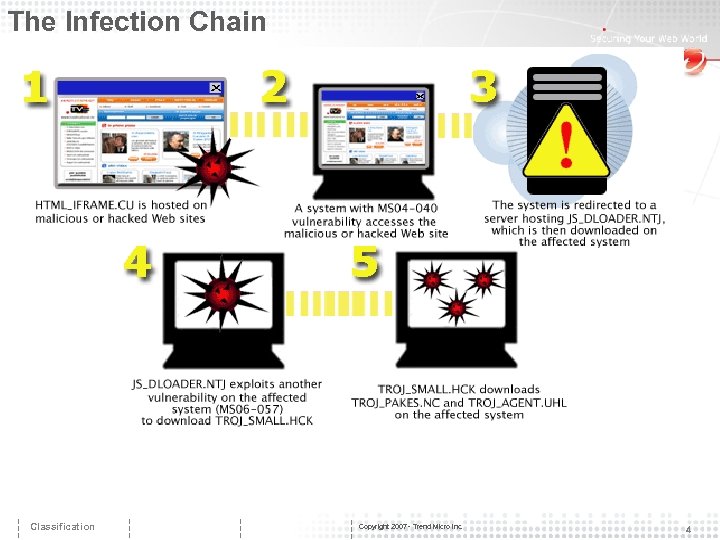
The Infection Chain Classification Copyright 2007 - Trend Micro Inc. 4
Status • The event began Friday, June 15 and began to subside Thursday, June 21 • Almost 6 K websites in Italy were compromised • Over 15 K visitors to these websites were infected – While the majority of infections were to Italian users, users in Spain and the US were affected and, to a lesser extent, users from other parts of the world as they accessed the infected sites. • One ISP hosted 90% of affected sites; a second hosted about 9% with 2 others hosting the remaining 1% • A malware toolkit, MPack v. 86, was used to create the initial downloader. Previous versions of this toolkit were available for purchase via a Russian website for ~$700. • Trend’s WRS and URL Filtering were updated to block the downloader and Trojan as of June 16 Classification Copyright 2007 - Trend Micro Inc. 5

Messaging/Positioning • The Italian Job represents a textbook example of today’s threat environment – Web-based, blended, sequential, targeted, profit-driven • It is highly likely that this type of attack will occur again, affecting users in another region – Javascript and the other types of technologies that enable the goodness of Web 2. 0 are highly susceptible to such attacks – Malware toolkits are available for sale on the Internet and frequently updated – Automated tools and technologies, such as bots, enable speedy proliferation of malware and crimeware • Trend Micro provides a variety of innovative products that protect both home users and businesses from this type of attack Classification Copyright 2007 - Trend Micro Inc. 6

Trend Micro Protection All products below provide protection against the Italian Job • Products that block the URLs from malicious websites: – – – Office. Scan 8. 0 Trend Micro Internet Security 2007 Inter. Scan Gateway Security Appliance 1. 0, 1. 1 and 1. 5 ISVW 6. 0 Inter. Scan Web Security Appliance (2500 v 2. 5)/Suite • Products that scan for malware and spyware downloads: – IMSS 7. 0 – IMSA 5000 v 7. 0 IGSA 1. 0, 1. 1 and 1. 5 – SMEX 7. 0 and 8. 0 – SMLN 3. 0 – IMHS – Trend Micro Internet Security 2007 • House. Call detects and cleans the malware associated with this threat Classification Copyright 2007 - Trend Micro Inc. 7

Best Practices -- Corporate Users • Deploy HTTP-scanning and make sure users cannot bypass. Force users to forward all web requests to the scanning device and deny them otherwise. • Do not allow unneeded protocols to enter the corporate network. The most dangerous of them are P 2 P communication protocols and IRC (chat). • Deploy vulnerability scanning software in the network and keep all applications patched. • Restrict user privileges for all network users. • Deploy corporate anti-spyware scanning. • Support User Awareness campaigns. Classification Copyright 2007 - Trend Micro Inc. 8
Best Practices – Home Users • Beware of pages that require software installation. Do not allow new software installation from your browser unless you absolutely trust both the Web page and the provider of the software. • Scan with an updated antivirus and anti-spyware software any program downloaded through the Internet. This includes any downloads from P 2 P networks, through the Web and any FTP server regardless of the source. • Beware of unexpected strange-looking emails, regardless of their sender. Never open attachments or click on links contained in these email messages. • Enable the “Automatic Update” feature in your Windows operating system and apply new updates as soon as they are available. • Always have an antivirus real-time scan service. Monitor regularly that it is being updated and that the service is running. Classification Copyright 2007 - Trend Micro Inc. 9
Additional Information • HTML_IFRAME. CU: http: //www. trendmicro. com/vinfo/virusencyclo/default 5. asp? VName= HTML_IFRAME. CU • JS_DLOADER. NTJ: http: //www. trendmicro. com/vinfo/virusencyclo/default 5. asp? VName= JS_DLOADER. NTJ • TROJ_SMALL. HCK: http: //www. trendmicro. com/vinfo/virusencyclo/default 5. asp? VName= TROJ%5 FSMALL%2 EHCK&VSect=P • TROJ_PAKES. NC: http: //www. trendmicro. com/vinfo/virusencyclo/default 5. asp? VName= TROJ%5 FPAKES%2 ENC&VSect=P • TROJ_AGENT. UHL: http: //www. trendmicro. com/vinfo/virusencyclo/default 5. asp? VName= TROJ_AGENT. UHL • TSPY_SINOWAL. BJ: http: //www. trendmicro. com/vinfo/grayware/ve_grayware. Details. asp? GNAME=TSPY%5 FSINOWAL%2 EBJ Classification Copyright 2007 - Trend Micro Inc. 10
2df29d5d68535e36a1506cd2fe748626.ppt