lecture_threat_modeling.pptx
- Количество слайдов: 43
 Threat Modeling
Threat Modeling
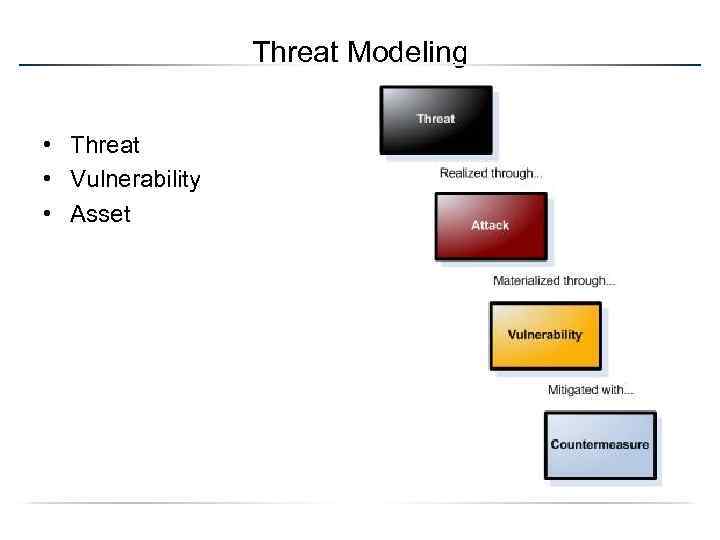 Threat Modeling • Threat • Vulnerability • Asset
Threat Modeling • Threat • Vulnerability • Asset
 Threat Modeling • A security control performed during the architecture and design phase of the SDLC to identify and reduce risk within software – Also called architectural risk analysis depending what camp you talk to – Sit down between security experts and architects & development leads – Performed through white boarding and thoughtful discussion
Threat Modeling • A security control performed during the architecture and design phase of the SDLC to identify and reduce risk within software – Also called architectural risk analysis depending what camp you talk to – Sit down between security experts and architects & development leads – Performed through white boarding and thoughtful discussion
 Who Benefits Threat Modeling • Threat modeling provides different benefits to the project stakeholders depending on their role and responsibility: – Architects – Developers – Security Testers – Project Managers – Business Managers – Information Risk Officers
Who Benefits Threat Modeling • Threat modeling provides different benefits to the project stakeholders depending on their role and responsibility: – Architects – Developers – Security Testers – Project Managers – Business Managers – Information Risk Officers
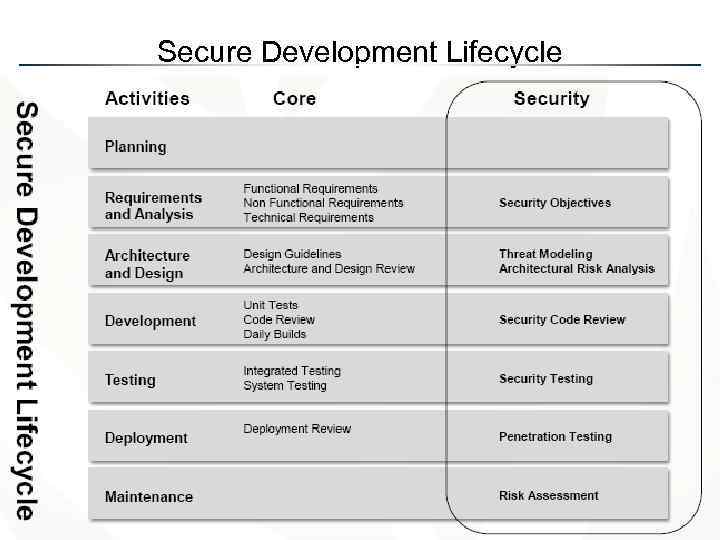 Secure Development Lifecycle
Secure Development Lifecycle
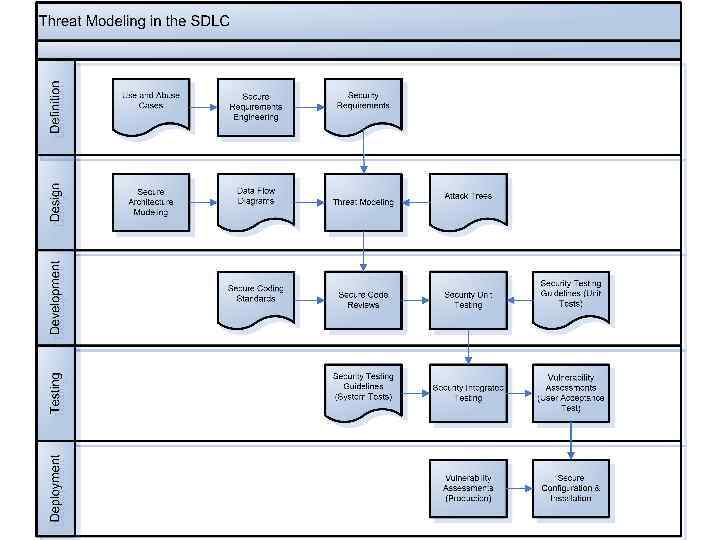
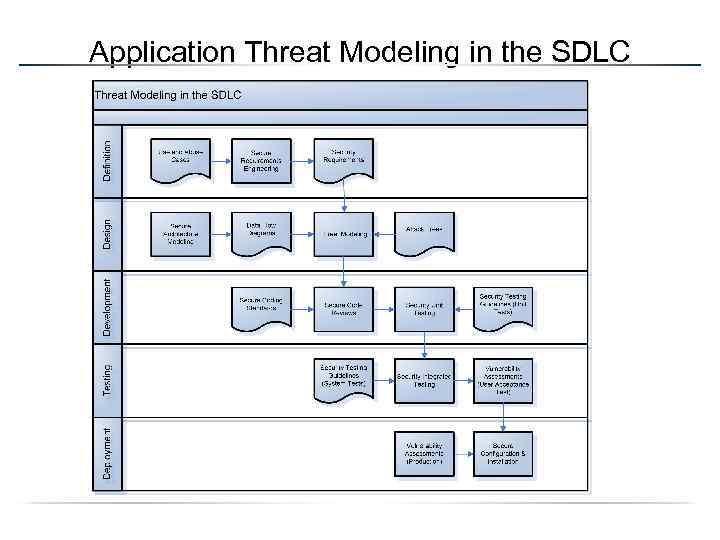 Application Threat Modeling in the SDLC
Application Threat Modeling in the SDLC
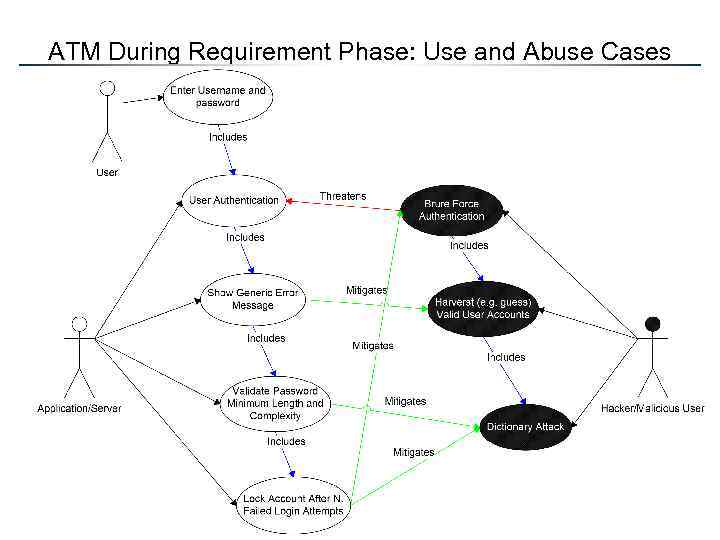 ATM During Requirement Phase: Use and Abuse Cases
ATM During Requirement Phase: Use and Abuse Cases
 Threat Modeling Benefits • Improves Security – Uncovers logical/architectural vulnerabilities – Reduces risk and minimizes impact • Drives Testing – Validates design meets security requirements – Reduces scope of code inspection – Serves as a guide for verification testing • Reduces Cost – Identifies expensive mistakes early on – Improve understanding and structure of application
Threat Modeling Benefits • Improves Security – Uncovers logical/architectural vulnerabilities – Reduces risk and minimizes impact • Drives Testing – Validates design meets security requirements – Reduces scope of code inspection – Serves as a guide for verification testing • Reduces Cost – Identifies expensive mistakes early on – Improve understanding and structure of application
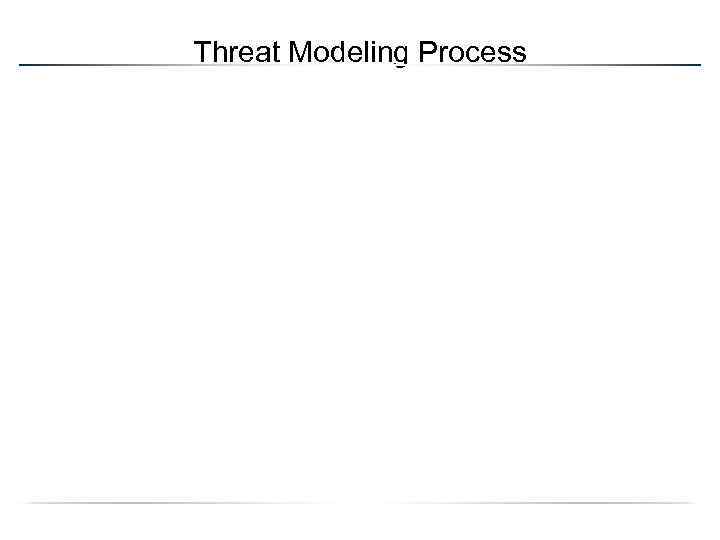 Threat Modeling Process
Threat Modeling Process
 Threat Modeling Approaches • Attack Centric – Evaluates from the point of view of an attacker • Defense Centric – Evaluates weakness in security controls • Asset Centric – Evaluates from asset classification and value • Hybrid – Evaluates application design using combination of methodologies to meet security objectives
Threat Modeling Approaches • Attack Centric – Evaluates from the point of view of an attacker • Defense Centric – Evaluates weakness in security controls • Asset Centric – Evaluates from asset classification and value • Hybrid – Evaluates application design using combination of methodologies to meet security objectives
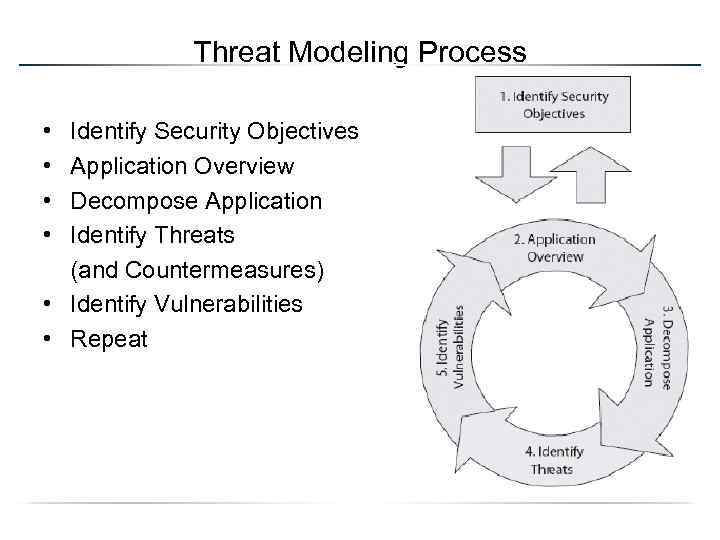 Threat Modeling Process • • Identify Security Objectives Application Overview Decompose Application Identify Threats (and Countermeasures) • Identify Vulnerabilities • Repeat
Threat Modeling Process • • Identify Security Objectives Application Overview Decompose Application Identify Threats (and Countermeasures) • Identify Vulnerabilities • Repeat
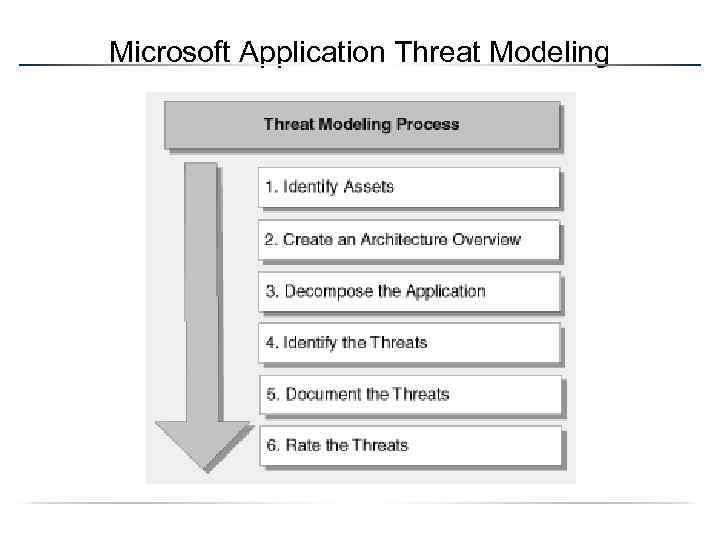 Microsoft Application Threat Modeling
Microsoft Application Threat Modeling
 Application Understanding
Application Understanding
 Application Modeling • Flow Chart – Less commonly used – Difficult to overlay threats • Data Flow Diagrams (DFD) – Hierarchical in nature – Focused on data input – Representation used by Microsoft • Universal Modeling Language (UML) – Familiar to developers – OO and component diagramming
Application Modeling • Flow Chart – Less commonly used – Difficult to overlay threats • Data Flow Diagrams (DFD) – Hierarchical in nature – Focused on data input – Representation used by Microsoft • Universal Modeling Language (UML) – Familiar to developers – OO and component diagramming
 Open Web Application Security Project Threat Risk Modeling
Open Web Application Security Project Threat Risk Modeling
 Step 1: Identify Security Objectives • Tactical Security Assessments – Identification of Security Flaws, the Threats that can exploit them and the mitigations • Secure Architecture Reviews – Requirements, Decomposition, Threat Mapping, Threat Response & Mitigations – Threats and Countermeasures, Risk Mitigation Strategy • Application Risk Management – Technical Risk and Business Risk – Risk Mitigation Strategy • Mitigate, Transfer, Accept it
Step 1: Identify Security Objectives • Tactical Security Assessments – Identification of Security Flaws, the Threats that can exploit them and the mitigations • Secure Architecture Reviews – Requirements, Decomposition, Threat Mapping, Threat Response & Mitigations – Threats and Countermeasures, Risk Mitigation Strategy • Application Risk Management – Technical Risk and Business Risk – Risk Mitigation Strategy • Mitigate, Transfer, Accept it
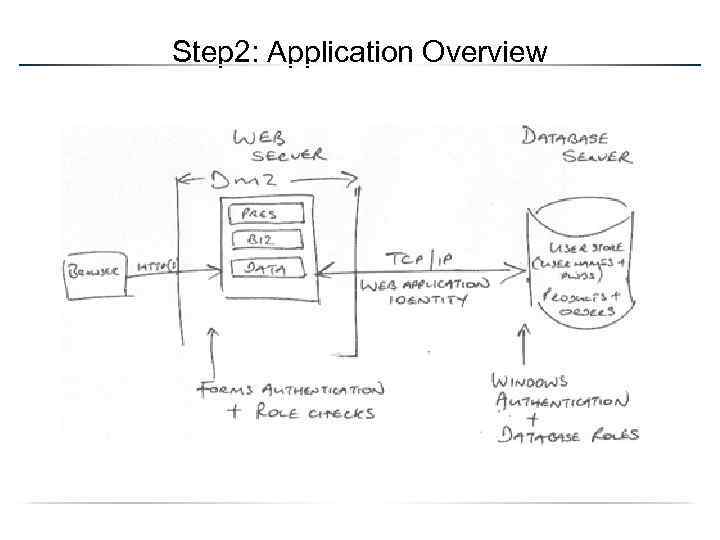 Step 2: Application Overview
Step 2: Application Overview
 Step 3: Decompose the Application • • Objective: understand the application and how it interacts with external entities. – Create Use Cases – Identify Entry Points – Identify Assets Outcome: Data flow diagrams (DFD) for the application show the different paths through the system highlighting the privilege boundaries.
Step 3: Decompose the Application • • Objective: understand the application and how it interacts with external entities. – Create Use Cases – Identify Entry Points – Identify Assets Outcome: Data flow diagrams (DFD) for the application show the different paths through the system highlighting the privilege boundaries.
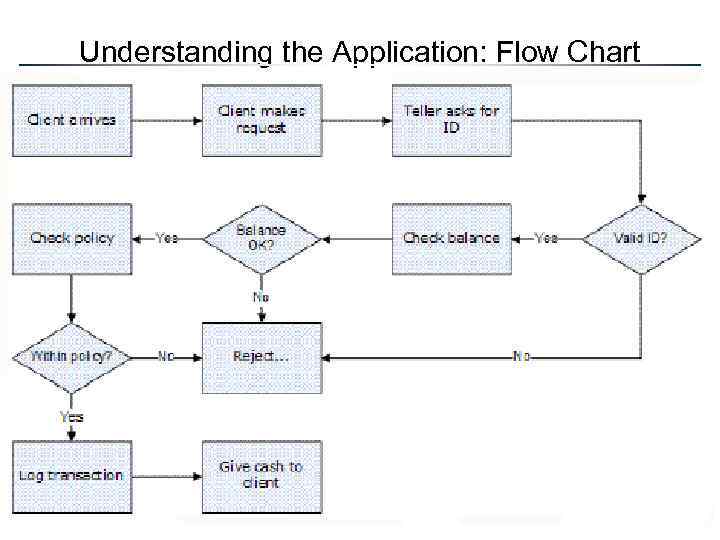 Understanding the Application: Flow Chart
Understanding the Application: Flow Chart
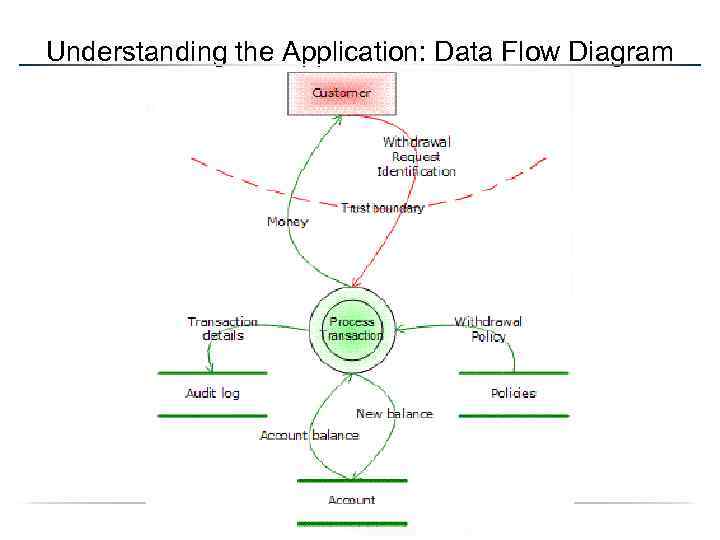 Understanding the Application: Data Flow Diagram
Understanding the Application: Data Flow Diagram
 Step 4: Threat Identification • • Objective: Use a systematic approach to identify the application exposure to threats – Threat Lists (STRIDE, ASF) – Use and Misuse cases – Attack Trees Outcome: List of threats relevant to the application environment, the hosts and the application tiers
Step 4: Threat Identification • • Objective: Use a systematic approach to identify the application exposure to threats – Threat Lists (STRIDE, ASF) – Use and Misuse cases – Attack Trees Outcome: List of threats relevant to the application environment, the hosts and the application tiers
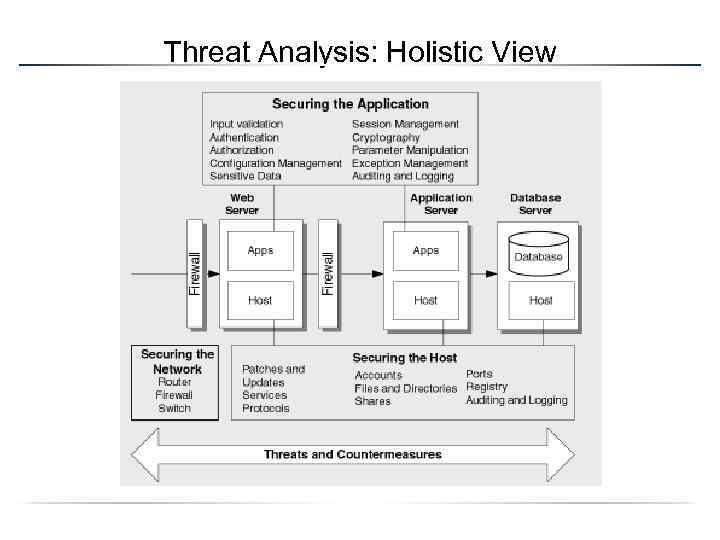 Threat Analysis: Holistic View
Threat Analysis: Holistic View
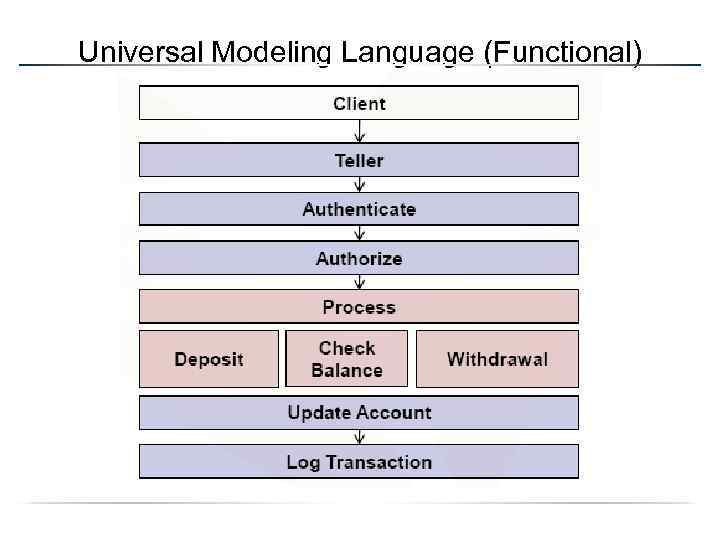 Universal Modeling Language (Functional)
Universal Modeling Language (Functional)
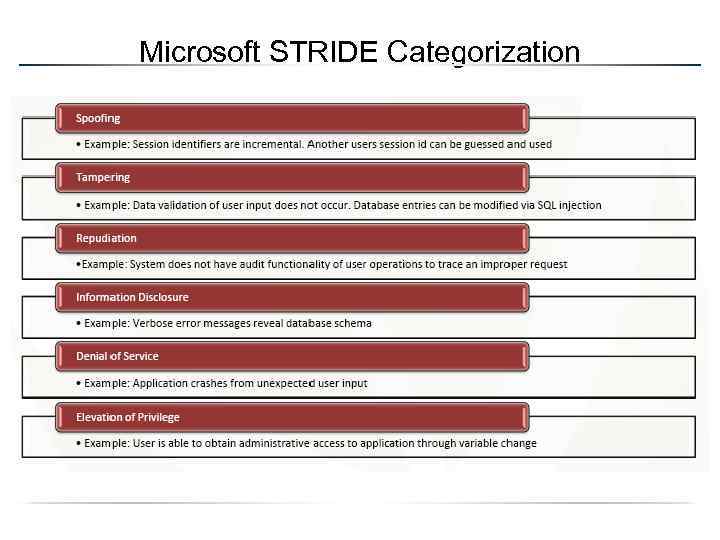 Microsoft STRIDE Categorization
Microsoft STRIDE Categorization
 Step 5: Vulnerability Identification • • Objective: Identify un-mitigated threats (e. g. threats with no countermeasures) – Use and Misuse cases – Threat Tree – Threat-Countermeasure Lists (STRIDE, ASF) Outcome: threat profile describing each security application flaw in terms of the threat impacting it, the host, tier, component impacted the vulnerability being exposed and the suggested mitigation control/countermeasure.
Step 5: Vulnerability Identification • • Objective: Identify un-mitigated threats (e. g. threats with no countermeasures) – Use and Misuse cases – Threat Tree – Threat-Countermeasure Lists (STRIDE, ASF) Outcome: threat profile describing each security application flaw in terms of the threat impacting it, the host, tier, component impacted the vulnerability being exposed and the suggested mitigation control/countermeasure.
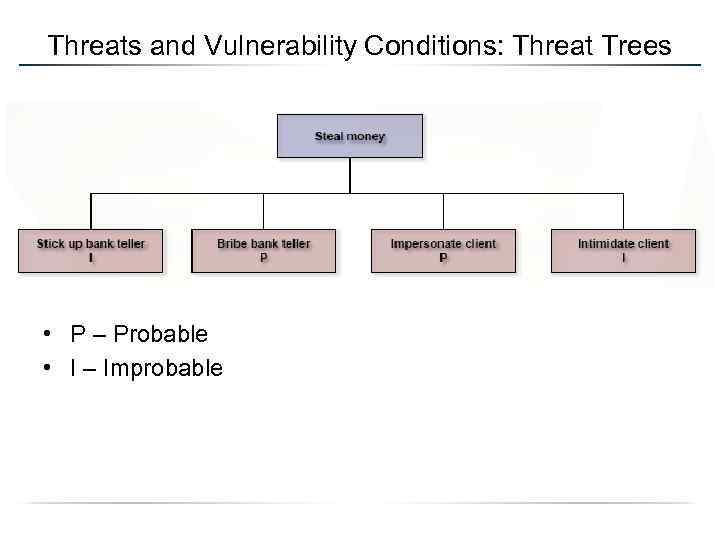 Threats and Vulnerability Conditions: Threat Trees • P – Probable • I – Improbable
Threats and Vulnerability Conditions: Threat Trees • P – Probable • I – Improbable
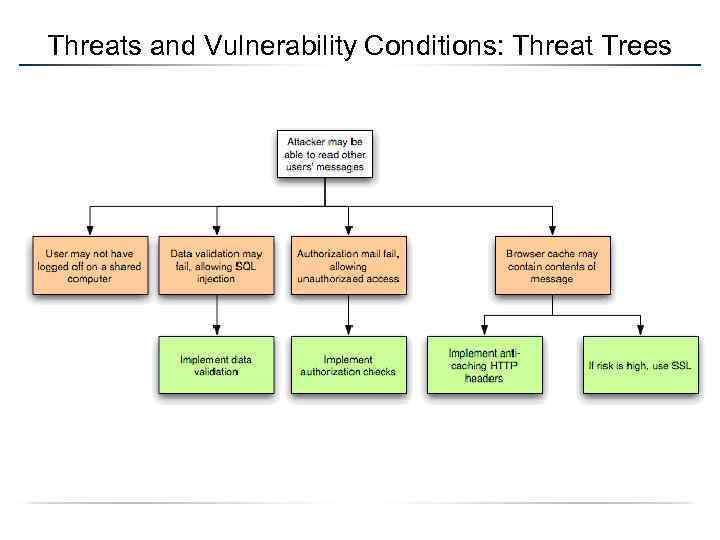 Threats and Vulnerability Conditions: Threat Trees
Threats and Vulnerability Conditions: Threat Trees
 Vulnerability Prioritization
Vulnerability Prioritization
 General Risk Approach • Risk = Threat * Vulnerability * Cost • Threat – An action intended to do damage or harm • Vulnerability – Likelihood of success of a threat • Cost – Total impact or cost of the incident
General Risk Approach • Risk = Threat * Vulnerability * Cost • Threat – An action intended to do damage or harm • Vulnerability – Likelihood of success of a threat • Cost – Total impact or cost of the incident
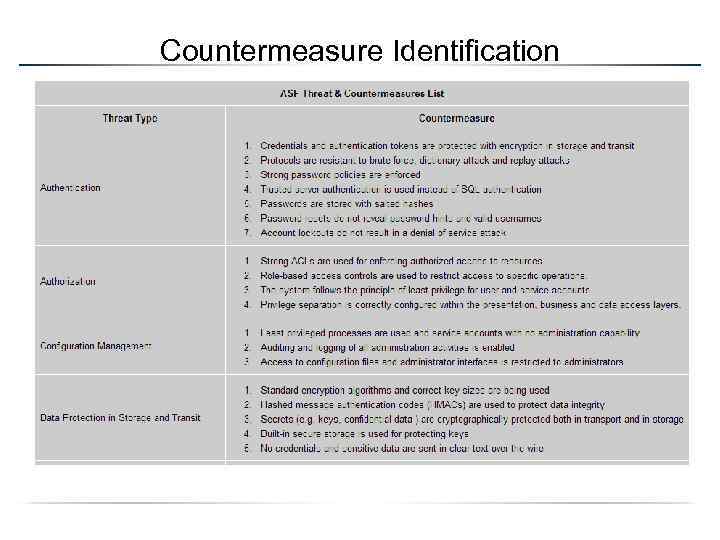 Countermeasure Identification
Countermeasure Identification
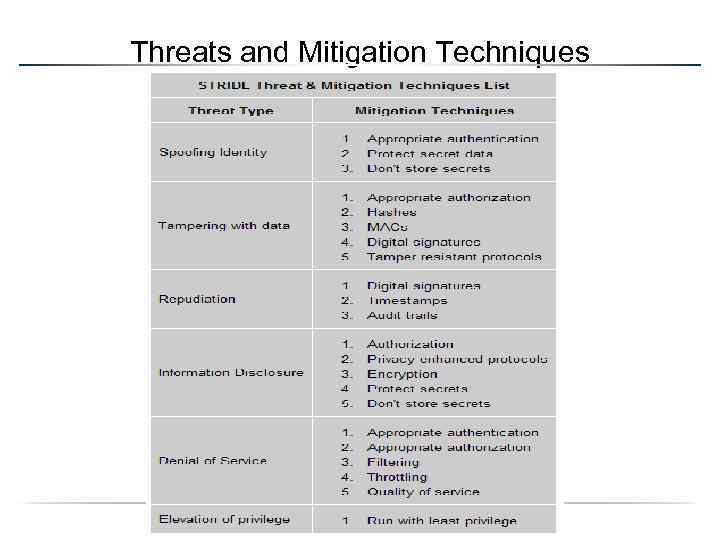 Threats and Mitigation Techniques
Threats and Mitigation Techniques
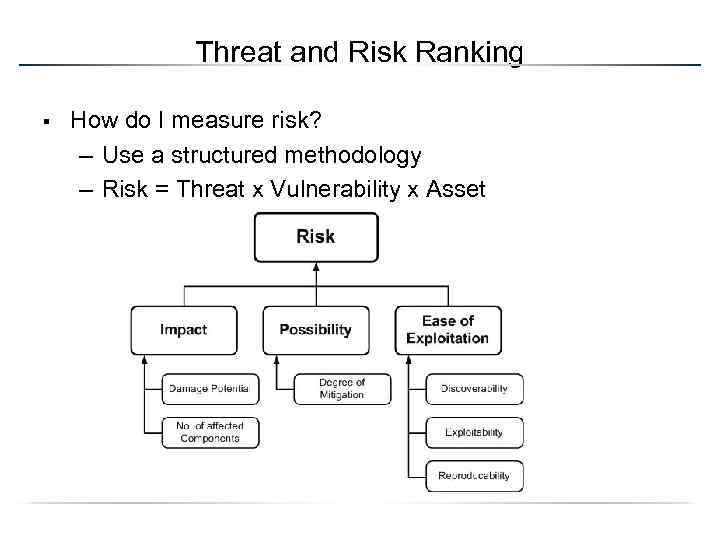 Threat and Risk Ranking § How do I measure risk? – Use a structured methodology – Risk = Threat x Vulnerability x Asset
Threat and Risk Ranking § How do I measure risk? – Use a structured methodology – Risk = Threat x Vulnerability x Asset
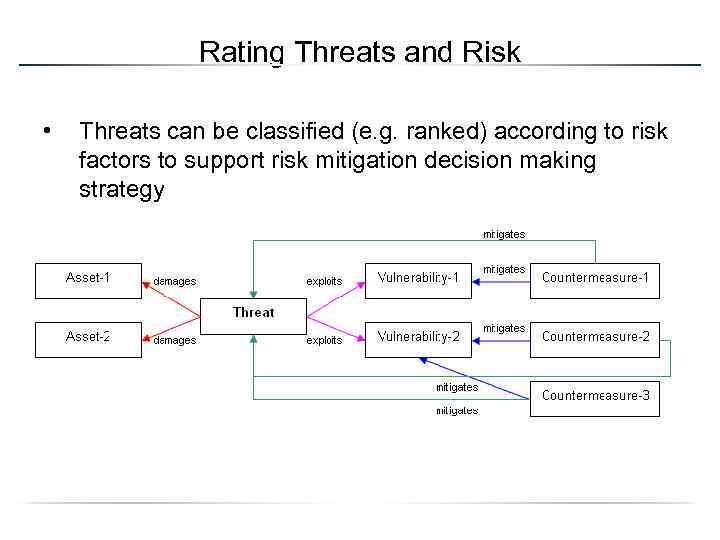 Rating Threats and Risk • Threats can be classified (e. g. ranked) according to risk factors to support risk mitigation decision making strategy
Rating Threats and Risk • Threats can be classified (e. g. ranked) according to risk factors to support risk mitigation decision making strategy
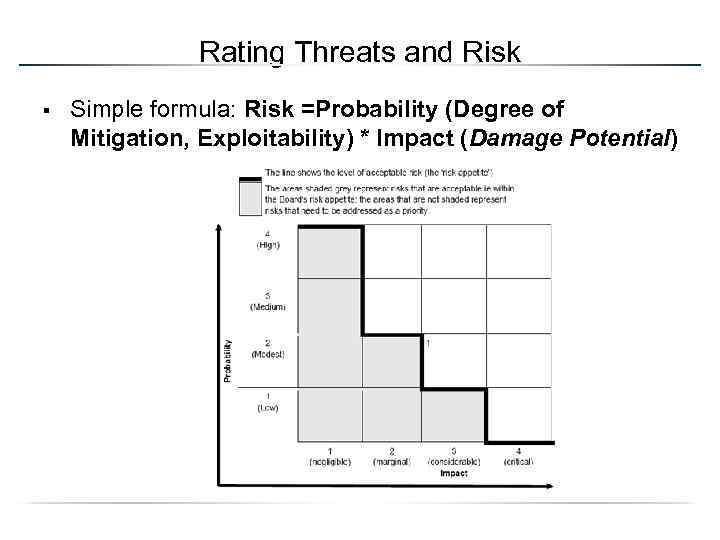 Rating Threats and Risk § Simple formula: Risk =Probability (Degree of Mitigation, Exploitability) * Impact (Damage Potential)
Rating Threats and Risk § Simple formula: Risk =Probability (Degree of Mitigation, Exploitability) * Impact (Damage Potential)
 DREAD Model § § Another method for determining risk is the DREAD model: – Damage potential – How great is the damage if the vulnerability is exploited? – Reproducibility – How easy is it to reproduce the attack? – Exploitability – How easy is it to launch an attack? – Affected users – As a rough percentage, how many users are affected? – Discoverability – How easy is it to find the vulnerability? Risk = Min(D, (D+R+E+A+D) / 5)
DREAD Model § § Another method for determining risk is the DREAD model: – Damage potential – How great is the damage if the vulnerability is exploited? – Reproducibility – How easy is it to reproduce the attack? – Exploitability – How easy is it to launch an attack? – Affected users – As a rough percentage, how many users are affected? – Discoverability – How easy is it to find the vulnerability? Risk = Min(D, (D+R+E+A+D) / 5)
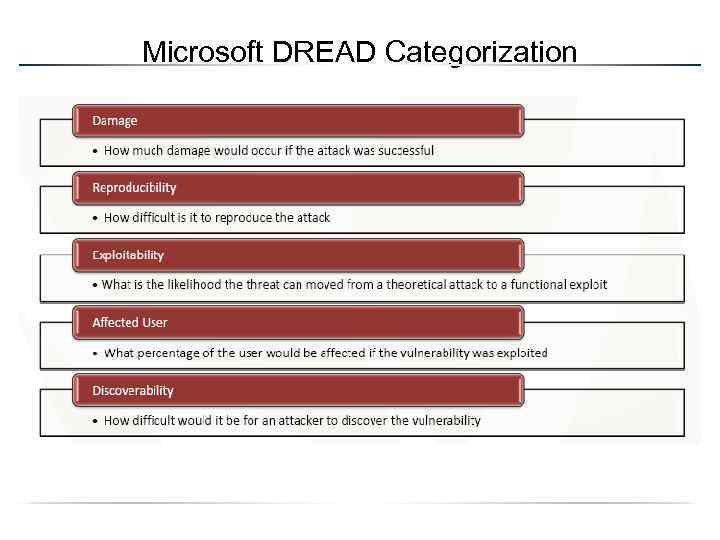 Microsoft DREAD Categorization
Microsoft DREAD Categorization
 Threat Modelling and Risk Decision Making § § Threats can be resolved by: – Risk Acceptance - doing nothing – Risk Transference - pass risk to an externality – Risk Avoidance - removing the feature/component that causes the risk – Risk Mitigation - decrease the risk Mitigation strategies should be examined for each threat Mitigations should be chosen according to the appropriate technology Resolution should be decided according to risk level and cost of mitigations
Threat Modelling and Risk Decision Making § § Threats can be resolved by: – Risk Acceptance - doing nothing – Risk Transference - pass risk to an externality – Risk Avoidance - removing the feature/component that causes the risk – Risk Mitigation - decrease the risk Mitigation strategies should be examined for each threat Mitigations should be chosen according to the appropriate technology Resolution should be decided according to risk level and cost of mitigations
 Risk Mitigation Strategy Best Practices • General Objectives: – Translate the identified technical risk issues into business risk issues – Determine whether standards compliance is violated – Determine whether other compensating security controls and mitigation factors are present – Determine which protective measure (e. g. security control, policy measures) should be in place to mitigate threat, how should be implemented and when – Determine short term and long term solutions
Risk Mitigation Strategy Best Practices • General Objectives: – Translate the identified technical risk issues into business risk issues – Determine whether standards compliance is violated – Determine whether other compensating security controls and mitigation factors are present – Determine which protective measure (e. g. security control, policy measures) should be in place to mitigate threat, how should be implemented and when – Determine short term and long term solutions
 Application Risk Management Best Practices • Eliminate vulnerabilities before they become liabilities • Manage the risks of serious financial loss, negative publicity, legal liability, loss of contracts, erosion of market share, degraded performance or other serious business impact as a result of a failure in security • Set, enforce and report that software assurance thresholds are maintained • Measurable reports prove progress internally and for compliance
Application Risk Management Best Practices • Eliminate vulnerabilities before they become liabilities • Manage the risks of serious financial loss, negative publicity, legal liability, loss of contracts, erosion of market share, degraded performance or other serious business impact as a result of a failure in security • Set, enforce and report that software assurance thresholds are maintained • Measurable reports prove progress internally and for compliance
 Structured Lists • • Round table discussion Prioritization based on consensus Utilize Praetorian Risk Approach Numbered list generated
Structured Lists • • Round table discussion Prioritization based on consensus Utilize Praetorian Risk Approach Numbered list generated
 Q&A Questions ?
Q&A Questions ?
 End
End


