ef2b3f576499dc3f8bedfd45e0171c4c.ppt
- Количество слайдов: 37
This Webcast Will Begin Shortly If you have any technical problems with the Webcast or the streaming audio, please contact us via email at: accwebcast@commpartners. com Thank You!

Panel Moderator Sonia G. Cudd, Associate Counsel and Assistant Secretary Mc. Cormick & Company, Incorporated Presenters Alice Lawrence, Principal Jordan Lawrence Daniel Cooperman, Senior Vice President, General Counsel and Secretary Oracle Corporation John Patzakis, Esq. , Vice Chairman and Chief Legal Officer Guidance Software

Infusing Records Policy into Technology April 18, 2007 Presented by Association of Corporate Counsel www. acc. com

About Jordan Lawrence • Twenty years experience helping companies solve real-world records and information management problems ASSESSING DEVELOPING ENFORCING • Objective - client-implemented best-practice standards and benchmarking data • ACC Alliance Partner

Legal and IT Objectives • Enforce your policy • Retain • Protect • Manage and Dispose • Make well-informed decisions • Have a verifiable legal hold process • Compliance with newly amended Federal Rules • Rule 26 “data map”

Better Information for Better Decisions • What record types you have • Who owns or controls them • Where records are held and on what applications or media • What is the value of information and record types • When should information and record types be disposed
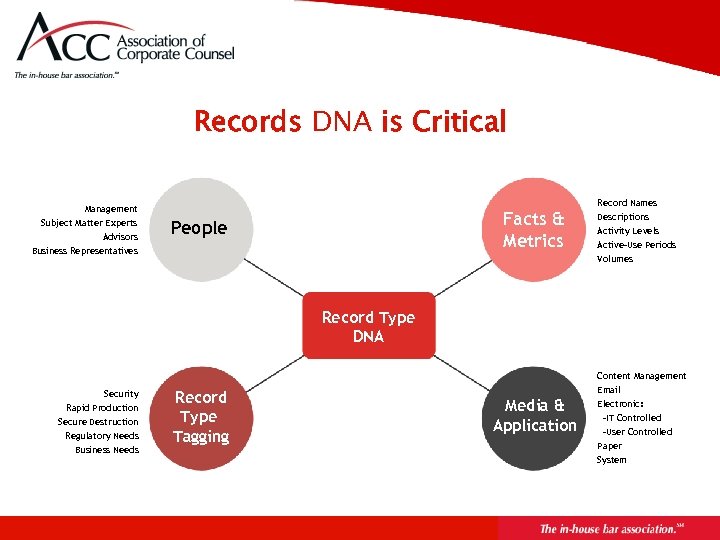
Records DNA is Critical Record Names Management Subject Matter Experts Advisors Facts & Metrics People Business Representatives Descriptions Activity Levels Active-Use Periods Volumes Record Type DNA Content Management Security Rapid Production Secure Destruction Regulatory Needs Business Needs Record Type Tagging Email Media & Application Electronic: -IT Controlled -User Controlled Paper System
Assessment Value for IT and Data Security • Map personally identifiable information • Identify redundancies • Locate where information is shared • Opportunities to reduce legacy records and information For more information, see www. jordanlawrence. com/benchmarking

Assessment Value for Legal • Rule 26 “data map” • Identify and prioritize risks • Bridge legal and IT objectives • Opportunities to reduce legacy records and information For more information, see www. jordanlawrence. com/benchmarking

Infusing Policy Into Technology Enforcement Solutions

Hold Management Enact immediate and verifiable legal holds Process must cover all users, all record types, all systems and media Dispose of obsolete records and information Keep policy and critical information up-to-date

Jordan Better information for better decisions Bridge legal and IT objectives Policy must be tied to process and technology Must have an effective “hold management” process alawrence 0407@jlgroup. com 636. 821. 2222

Daniel Cooperman SVP, General Counsel and Secretary Oracle Corporation
Oracle Corporation Key Facts Applications Middleware Founded in 1977. Headquarters in Redwood Shores, CA • $14 billion revenue FY 06 (46% from outside US) • 275, 000 customers • 17, 700 partners • 68, 000 employees (59% outside US) • 14, 000 developers • Operations in 145 countries • 87 operating subsidiaries Database
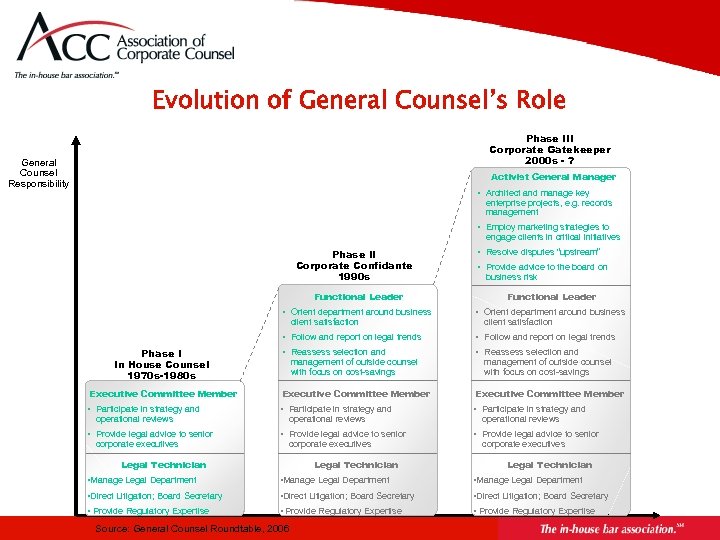
Evolution of General Counsel’s Role Phase III Corporate Gatekeeper 2000 s - ? General Counsel Responsibility Activist General Manager • Architect and manage key enterprise projects, e. g. records management • Employ marketing strategies to engage clients in critical initiatives Phase II Corporate Confidante 1990 s • Resolve disputes “upstream” • Provide advice to the board on business risk Functional Leader • Orient department around business • Follow and report on legal trends • Reassess selection and Executive Committee Member • Participate in strategy and • Provide legal advice to senior client satisfaction Phase I In House Counsel 1970 s-1980 s operational reviews corporate executives management of outside counsel with focus on cost-savings operational reviews corporate executives Legal Technician client satisfaction management of outside counsel with focus on cost-savings operational reviews corporate executives Legal Technician • Manage Legal Department • Direct Litigation; Board Secretary • Provide Regulatory Expertise Source: General Counsel Roundtable, 2006
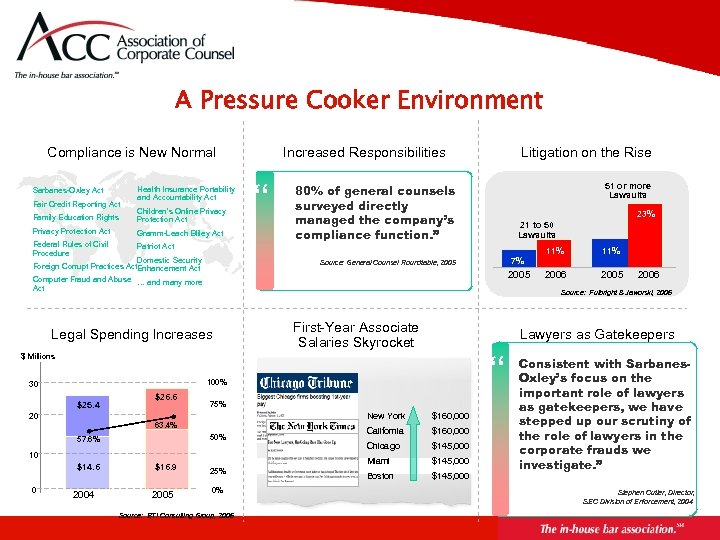
A Pressure Cooker Environment Compliance is New Normal Sarbanes-Oxley Act Fair Credit Reporting Act Health Insurance Portability and Accountability Act Family Education Rights Children’s Online Privacy Protection Act Gramm-Leach Bliley Act Federal Rules of Civil Procedure Patriot Act Domestic Security Foreign Corrupt Practices Act. Enhancement Act Computer Fraud and Abuse … and many more Act Increased Responsibilities “ First-Year Associate Salaries Skyrocket “ New York 50% 10 0 2004 $16. 9 2005 25% 0% Source: BTI Consulting Group, 2006 $160, 000 California $160, 000 Chicago $145, 000 Miami 63. 4% $14. 6 11% 2006 2005 2006 Lawyers as Gatekeepers 75% 20 57. 6% 7% Source: Fulbright & Jaworski, 2006 100% $26. 6 23% 21 to 50 Lawsuits 2005 $ Millions $25. 4 51 or more Lawsuits 80% of general counsels surveyed directly managed the company’s compliance function. ” Source: General Counsel Roundtable, 2005 Legal Spending Increases 30 Litigation on the Rise $145, 000 Boston $145, 000 Consistent with Sarbanes. Oxley’s focus on the important role of lawyers as gatekeepers, we have stepped up our scrutiny of the role of lawyers in the corporate frauds we investigate. ” Stephen Cutler, Director, SEC Division of Enforcement, 2004
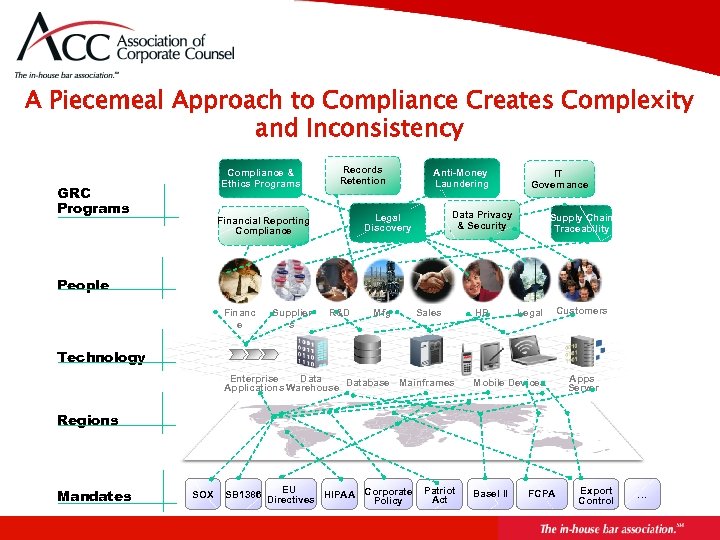
A Piecemeal Approach to Compliance Creates Complexity and Inconsistency Compliance & Ethics Programs GRC Programs Records Retention Anti-Money Laundering Data Privacy & Security Legal Discovery Financial Reporting Compliance IT Governance Supply Chain Traceability People Financ e Supplier s R&D Mfg Sales HR Legal Customers Technology Enterprise Database Mainframes Applications Warehouse Mobile Devices EU SB 1386 Directives HIPAA Corporate Policy Basel II Apps Server Regions Mandates SOX Patriot Act FCPA Export Control …
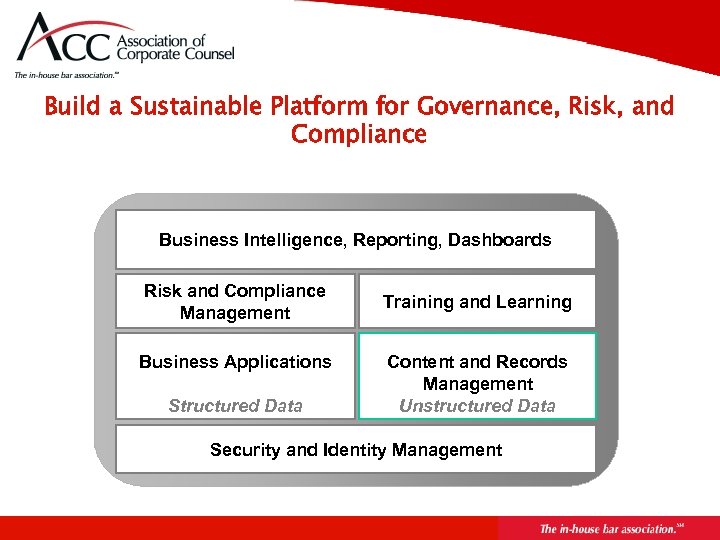
Build a Sustainable Platform for Governance, Risk, and Compliance Business Intelligence, Reporting, Dashboards Risk and Compliance Management Business Applications Structured Data Training and Learning Content and Records Management Unstructured Data Security and Identity Management
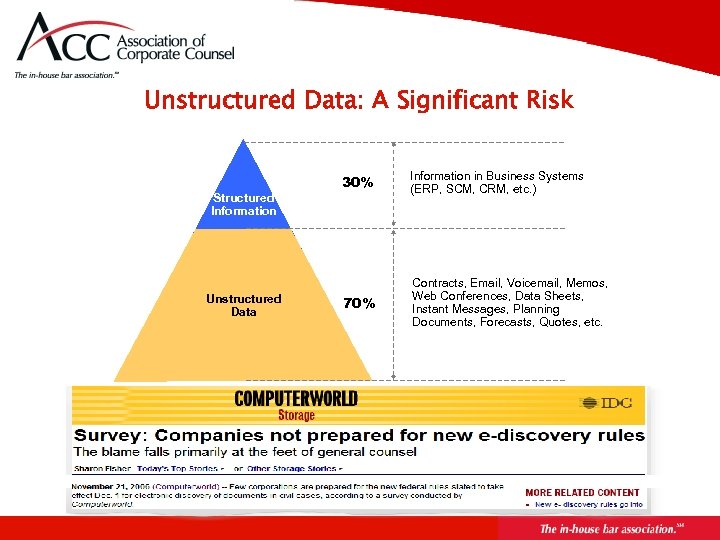
Unstructured Data: A Significant Risk Structured Information Unstructured Data 30% Information in Business Systems (ERP, SCM, CRM, etc. ) 70% Contracts, Email, Voicemail, Memos, Web Conferences, Data Sheets, Instant Messages, Planning Documents, Forecasts, Quotes, etc.

Critical Success Factor Connecting Record Policies to Technology Establish Retention Policies for Information and Records Create the technology infrastructure to support Records and Retention Management Platform across the Enterprise
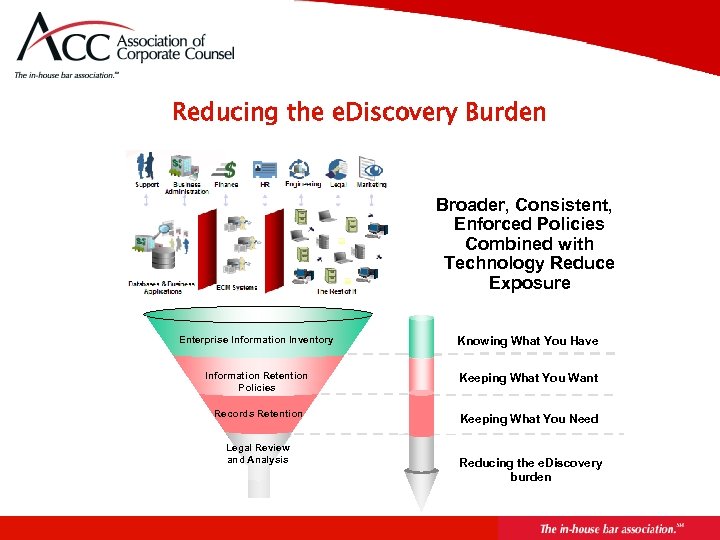
Reducing the e. Discovery Burden Broader, Consistent, Enforced Policies Combined with Technology Reduce Exposure Enterprise Information Inventory Knowing What You Have Information Retention Policies Keeping What You Want Records Retention Keeping What You Need Legal Review and Analysis Reducing the e. Discovery burden

Base Your Records Retention Policies on “Best Practices” Capture information from the right people to design policies that support business and regulatory requirements Apply retention policies to all content across multiple repositories, not only records Don’t retain more content than is necessary Apply policies consistently and universally Centralize policy administration and disposition processing Apply legal holds promptly and universally to minimize user disruption
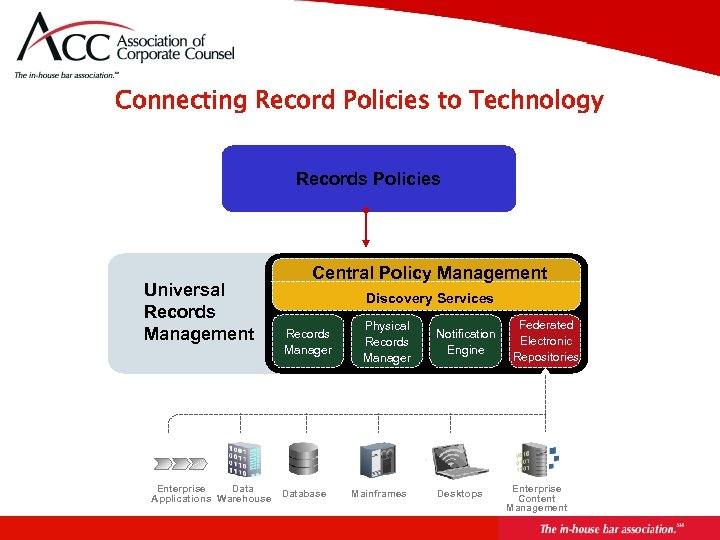
Connecting Record Policies to Technology Records Policies Universal Records Management Enterprise Data Applications Warehouse Central Policy Management Discovery Services Records Manager Database Physical Records Manager Mainframes Notification Engine Desktops Federated Electronic Repositories Enterprise Content Management
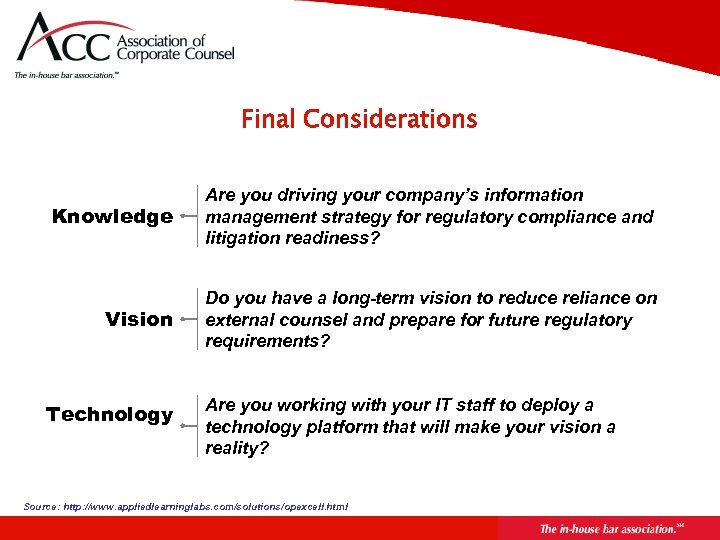
Final Considerations Knowledge Are you driving your company’s information management strategy for regulatory compliance and litigation readiness? Vision Do you have a long-term vision to reduce reliance on external counsel and prepare for future regulatory requirements? Technology Are you working with your IT staff to deploy a technology platform that will make your vision a reality? Source: http: //www. appliedlearninglabs. com/solutions/opexcell. html

John Patzakis, Esq. Vice Chairman and Chief Legal Officer Guidance Software

3 Key Legal Requirements Related to Records Management 1. Need to Actively Enforce Existing Policies 2. Need to Execute Timely and Effective Litigation Holds to Override Retention Procedures 3. Need for Documentation and Transparency of e. Records Enforcement Efforts and Litigation Holds

E-Records Retention Enforcement and The Law 1. Enforcement Using a Systemized and Objective Process -Samsung Electronics v. Rambus, 439 F. Supp. 2 d 524 (E. D. Va. 2006), (Court finds records management policy applied in bad faith and in a non-systemic manner) -Active Enforcement is Key To Establishing Routine Operation and Process Defensibility 2. Must Document and Report e. Records Enforcement Activity -Samsung Electronics v. Rambus, (Rambus kept no records of the kinds of documents that were destroyed, ” or the parameters for such destruction) 3. Purging of Records Pursuant to Established Policy Must Be Overriden in Face of Duty to Preserve -Broccoli v. Echostar Communications, 229 F. R. D. 506 (D. Md. 2005)

Safe Harbor: Only Possible with a Process Rule 37(f): No Penalties for Deleting ESI due to Routine Operation of IT Systems, and if Reasonable Preservation Steps Taken Must be Due to Routine Operation in Good Faith and • Procedures Must be: Established, Documented and Operational • Systemized Framework For Early Attention (Litigation Hold) Must be in Place • Caveat --- Committee Note: “A party is not permitted to exploit the routine operation of an information system to thwart discovery obligations by allowing that operation to continue in order to destroy (relevant ESI). ”

Court Scrutiny of E-Discovery Collection Process • • • In re NTL, Inc. Securities Litigation, 2007 WL 241344 (S. D. N. Y. Jan. 30 2007) • “Although NTL sent out hold memos in March and June 2002. . . those hold memos were not sufficient, since they subsequently were ignored. . . The evidence, in fact, is that no adequate litigation hold existed. ” Samsung Electronics v. Rambus, 439 F. Supp. 2 d 524 (E. D. Va. 2006) • "It is not sufficient, however, for a company merely to tell employees to 'save relevant documents, '. . . this sort of token effort will hardly ever suffice. " • court faults “the lack of specificity in defining what documents would be relevant to litigation” Wachtel v. Health. Net, 2006 WL 3538935 (D. N. J. ); Court criticizes Health. Net’s “utterly inadequate” e. Discovery process where paralegal merely emails preservation notifications

Would Your Organization’s e. Discovery Search and Collection Efforts Withstand This Scrutiny? • Peskoff v. Ferber --- F. R. D. ----, 2007 WL 530096 (Feb. 21, 2007 D. D. C. ) "Once the search is completed. . . Defendant must also file a statement under oath by the person who conducts the search, explaining how the search was conducted, of which electronic depositories, and how it was designed to produce and did in fact produce all of the emails I have just described. I must insist that the person performing the search have the competence and skill to do so comprehensively. An evidentiary hearing will then be held, at which I expect the person who made the attestation to testify and explain how he or she conducted the search, his or her qualifications to conduct the search, and why I should find the search was adequate. “
Preservation Only Required For Relevant Data “Clearly” no duty to “preserve every shred of paper, every e-mail or electronic document, and every backup tape…Such a rule would cripple large corporations. ” Zubulake v. UBS Warburg LLC, 220 F. R. D. 212, 217 (S. D. N. Y. 2004) This concept is reflected in the New Federal Rules (FRCP). Committee Notes endorse “narrowly tailored” preservation and the need to “balance between the competing needs to preserve relevant evidence and to continue routine operations critical to ongoing activities” (Note to Rule 26(f). ) Rule 26(f) also invokes the Manual for Complex Litigation (4 th) § 40. 25(2); Which Provides for Targeted Collection Based Upon Keywords, Date Ranges, File Types and Specified Custodians

Recent Cases Support Targeted ESI Search and Collection Flexys Americas v. Kumho Tire: 2006 WL 3526794 (N. D. Ohio); • Court limits Search to Specific Custodians, Time Frames and Keywords Treppel v. Biovail Corporation, 233 F. R. D. 363 (S. D. N. Y. 2006). • Court: defined search strategies are appropriate in cases involving ESI. If meet and confer efforts are refused, producing party should proceed with reasonable search criteria with a clear record of opponent’s refusal. Caveat: Without an Established Process with the Right Technology, Collection Efforts Will Be Overly Broad, Resulting in Substantial “Back End” Costs (processing, excess data hosting and review).

About Guidance Software Founded 1997. (NASD: GUID) Largest provider of computer investigation software, training and services • Over 24, 000 users of En. Case® computer forensic software worldwide • More than 3, 800 trained annually • Over 350 of Global 2000, including over 100 of the Fortune 500, use En. Case® Enterprise software Headquartered in Pasadena, CA Offices in SF, DC, NY, Houston, Chicago (opening Q 1 2007) and the UK

Key Cases That Address “Process Defensibility” and En. Case: • • Sanders v. State (Texas), 191 S. W. 3 rd 272 (Tex. App. , 2006); Cert. Denied, --- S. Ct. ---, 2007 WL 91482 (U. S. ), (Court takes Judicial Notice of the reliability of En. Case, finding “En. Case is a ‘field standard’ forensic computer examination; treatises about En. Case have been published. ”) Krumwiede v. Brighton Assocs. , L. L. C. , 2006 WL 1308629 (N. D. Ill. May 8, 2006) [Court finds that e. Discovery Consultant “created a forensically valid copy of the laptop's hard drive using En. Case software. ” This allowed the consultant “to examine the metadata and the content of the files on the computer. . . ”] Williford v. State (Texas), 127 S. W. 3 d 309 (Tex. App. 2004). State (Ohio) v. Cook, 777 N. E. 2 d 882 (Ohio App. 2002) Used by the SEC, FBI, Secret Service, FTC, foreign governments, state and local law enforcement, etc. See, e. g. , United States v. Shirazi, 2006 WL 1155945 (N. D. Ill. , May 1, 2006)
Key Benefits of The En. Case Enterprise Process Order of magnitude cost savings. En. Case e. Discovery enables an inhouse process that is highly efficient due to its scalability, ability to cull at the point of collection, and integrated processing capabilities. Consistent and systemic enterprise-wide processes. Enables implementation of repeatable enterprise-wide e. Discovery process. This facilitates compliance with the new Federal Rules. Judicial acceptance of En. Case technology. Company can count on judicial approval of their defensible process for collection and preservation of ESI. En. Case Enterprise is also the Industry Standard for Internal Investigations involving ESI. Ability to Enforce e. Records Retention Polices at the Desktop Level on a Global Basis

Further Resources Request new white paper on e. Discovery Collection Best Practices: Legal@En. Case. com e. Discovery Resources: www. kenwithers. com www. thesedonaconference. org “Digital Discovery & e-Evidence” Pike & Fisher http: //ddee. pf. com

Infusing Records Policy into Technology April 18, 2007 Presented by www. jordanlawrence. com 636. 821. 2222
ef2b3f576499dc3f8bedfd45e0171c4c.ppt