1ca2ba5054bc1d3eca8a11139ece9c0c.ppt
- Количество слайдов: 43

The Web PKI In Theory and Malpractice Bruce Maggs Joint work with Frank Cangialosi, David Choffnes, Taejoong Chung, James Larisch, Dave Levin, Yabing Liu, Alan Mislove, Aaron Schulman, Will Tome, Christo Wilson, and Liang Zhang.
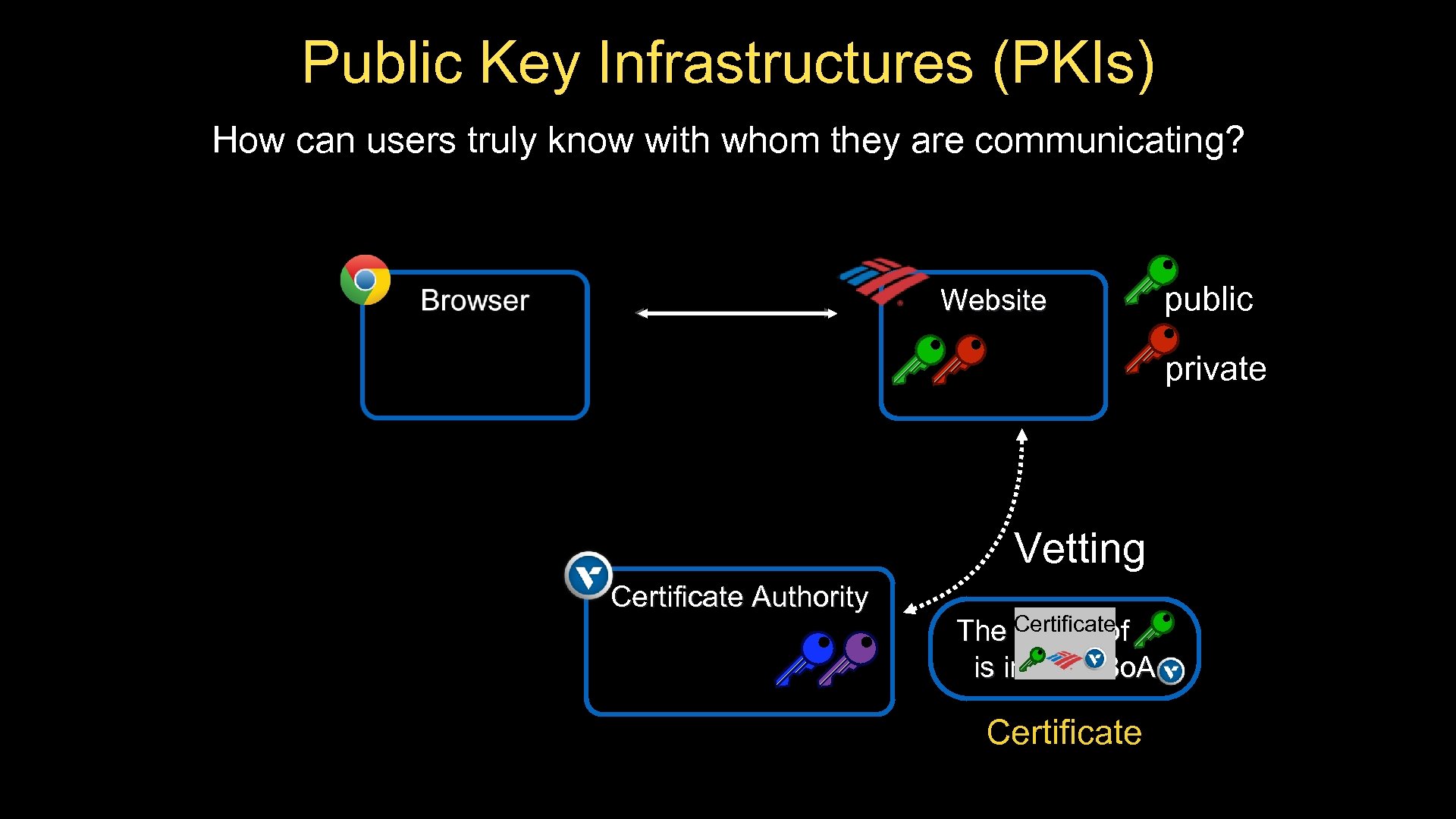
Public Key Infrastructures (PKIs) How can users truly know with whom they are communicating? Browser Website public private Vetting Certificate Authority Certificate The owner of is indeed Bo. A Certificate
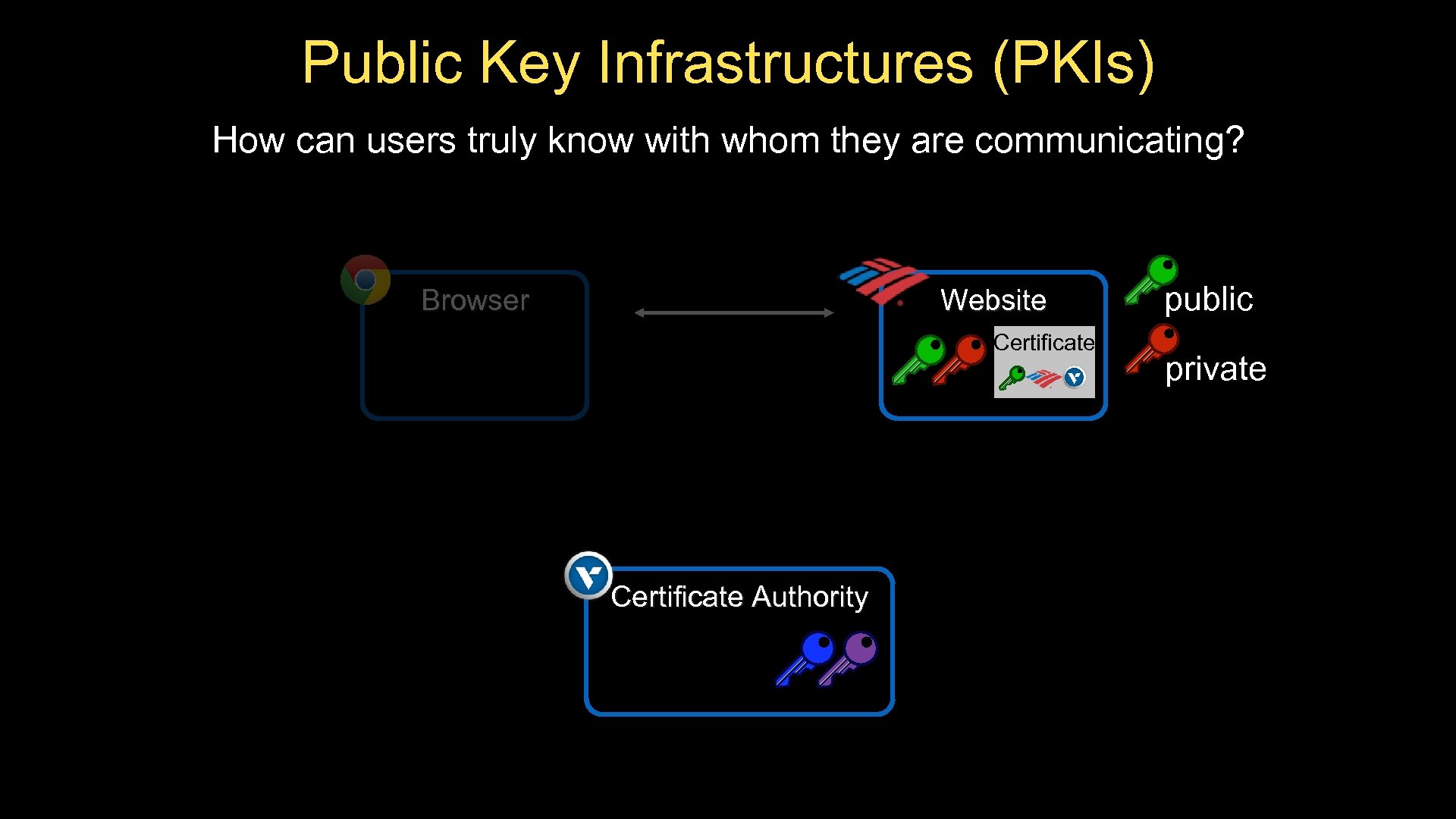
Public Key Infrastructures (PKIs) How can users truly know with whom they are communicating? Browser Website Certificate Authority public private
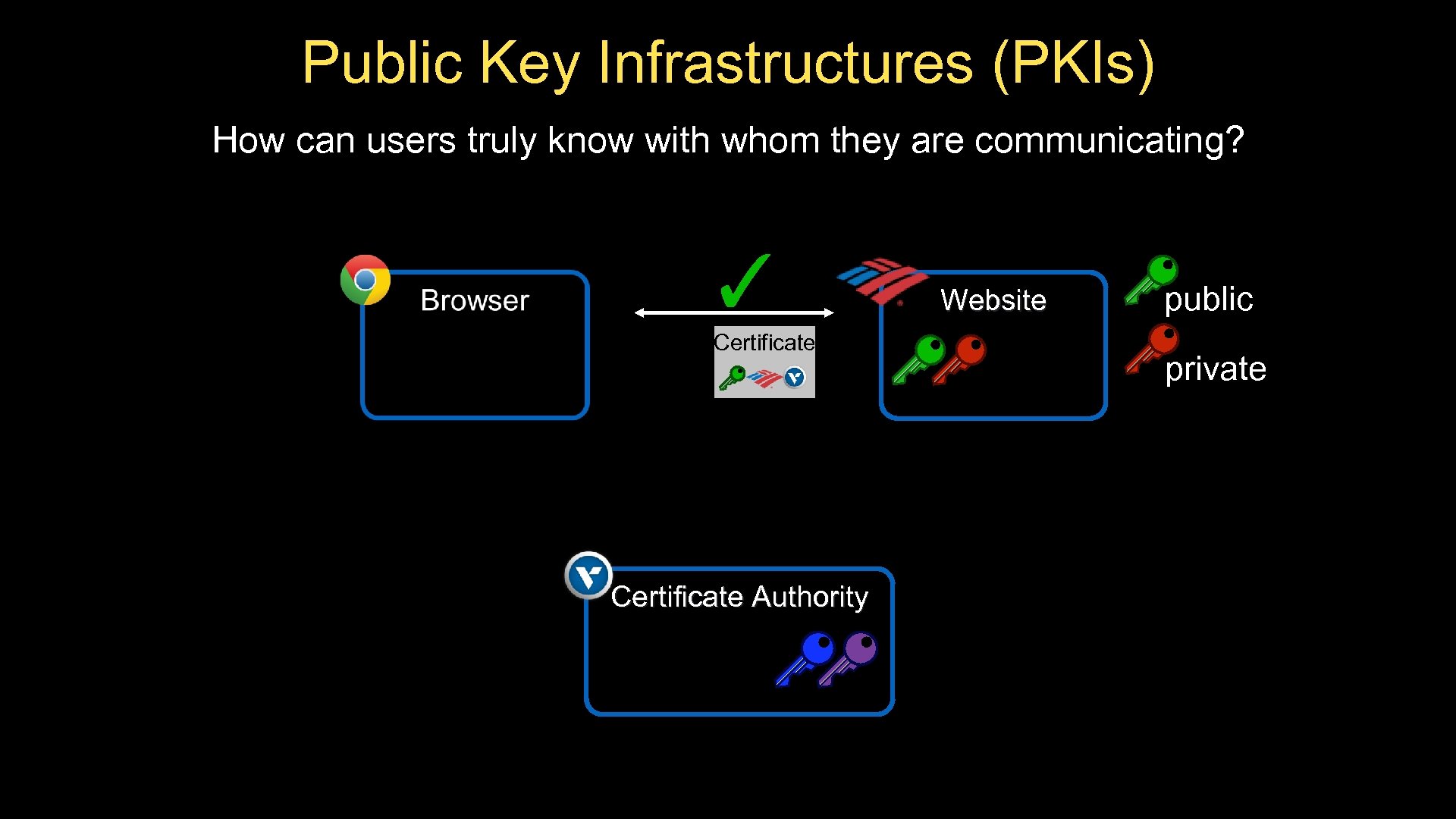
Public Key Infrastructures (PKIs) How can users truly know with whom they are communicating? ✓ Certificate Authority Website Certificate public private

EV Certificates More thorough vetting process of CAs and clients Normal Extended Validation
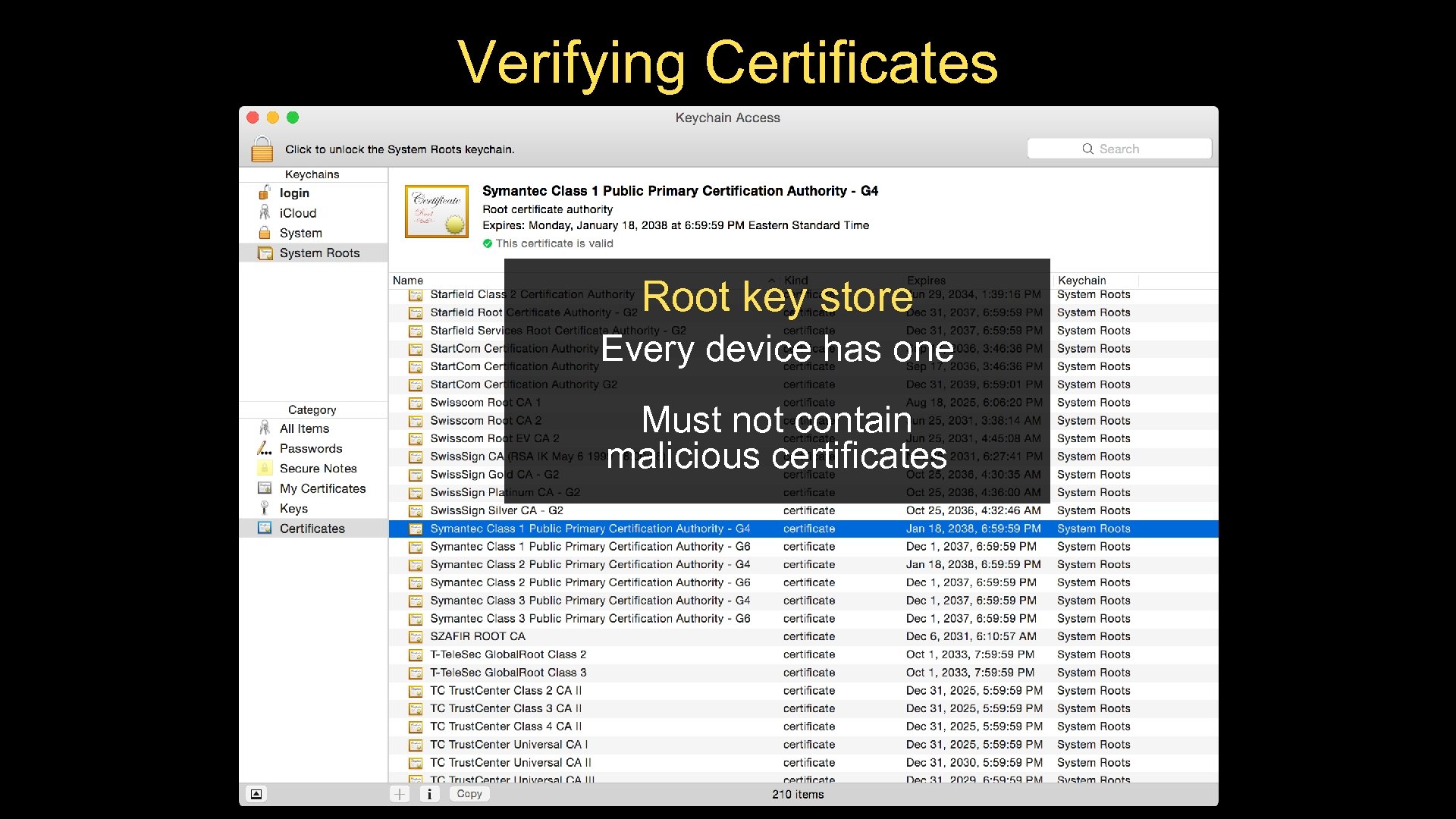
Verifying Certificates ✓ Certificate “I’m because I say so!” Root key store ✓ Every device has one Certificate Browser ✓ “I’m because says so” Must not contain malicious certificates Certificate
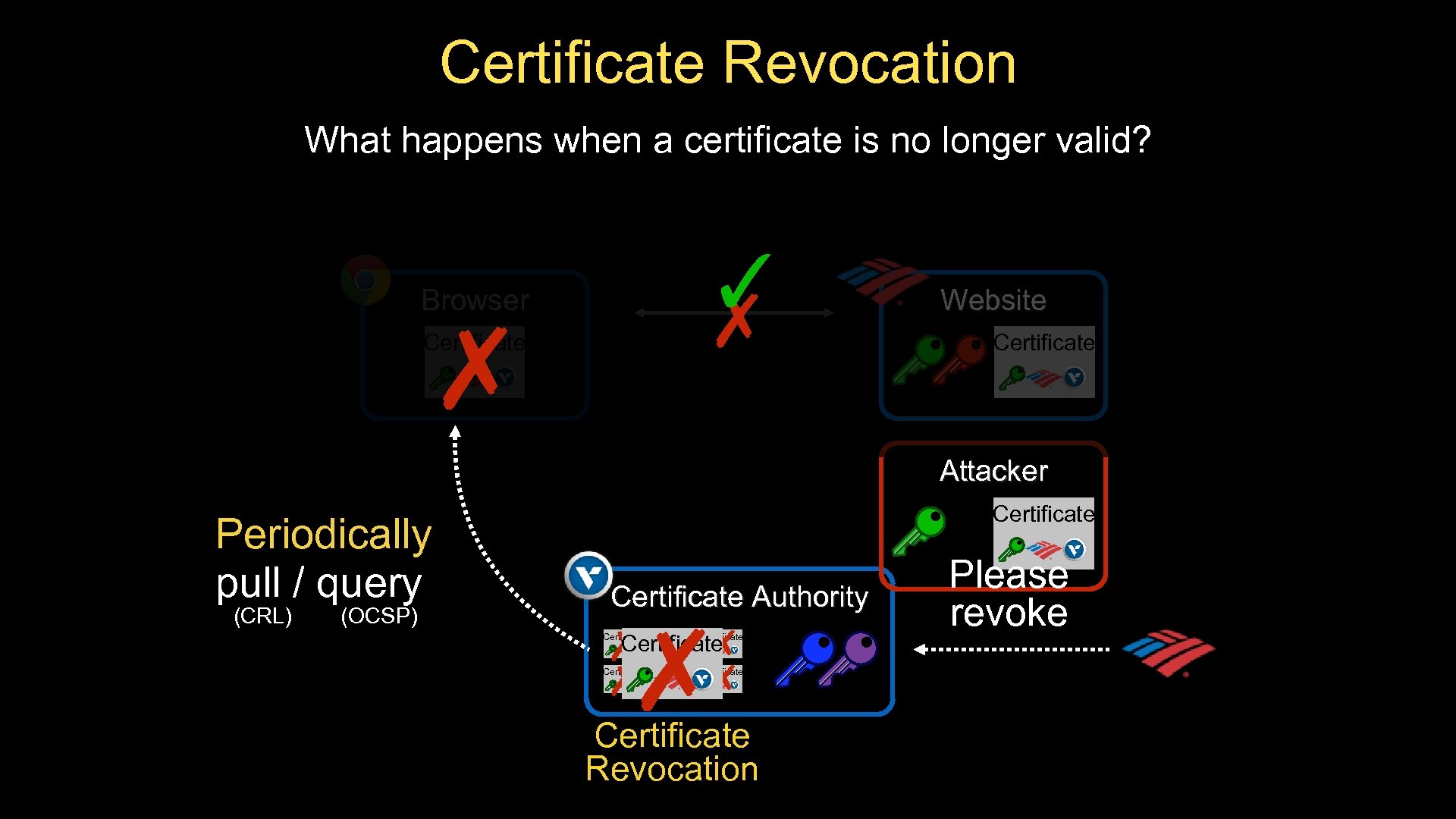
Certificate Revocation What happens when a certificate is no longer valid? Browser ✗ Certificate ✓ ✗ Website Certificate Attacker Periodically pull / query (CRL) (OCSP) Certificate Authority ✗ Certificate ✗✗✗ Certificate Certificate Revocation Please revoke
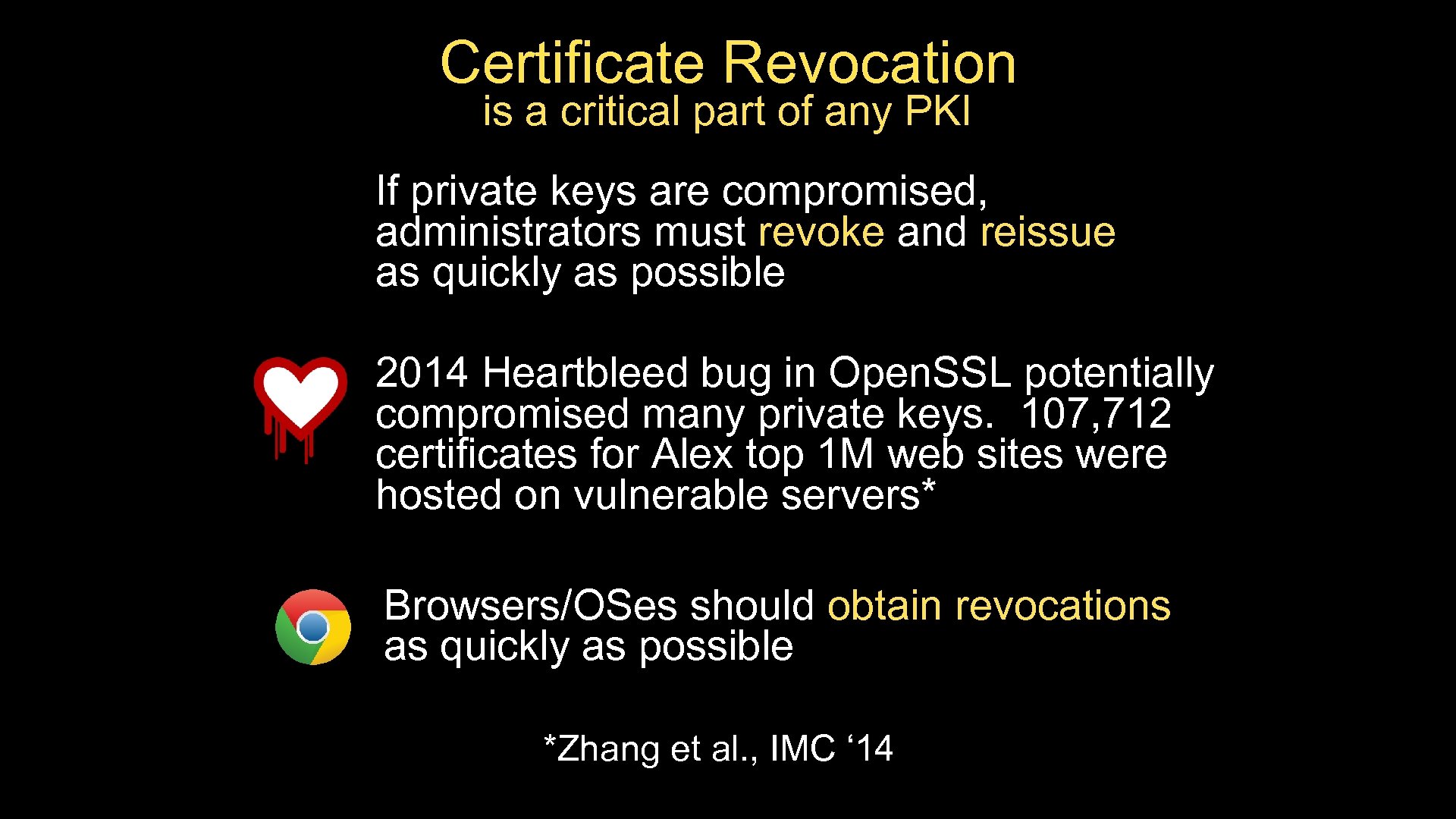
Certificate Revocation is a critical part of any PKI If private keys are compromised, administrators must revoke and reissue as quickly as possible 2014 Heartbleed bug in Open. SSL potentially compromised many private keys. 107, 712 certificates for Alex top 1 M web sites were hosted on vulnerable servers* Browsers/OSes should obtain revocations as quickly as possible *Zhang et al. , IMC ‘ 14

Revocation in the Wild 74 full IPv 4 scans of port 443 (October 2013 to March 2015) 5, 067, 476 distinct valid certificates discovered (90% of certificates discovered were invalid!) 8% were revoked at some point 1% of those still served in March 2015 had been revoked
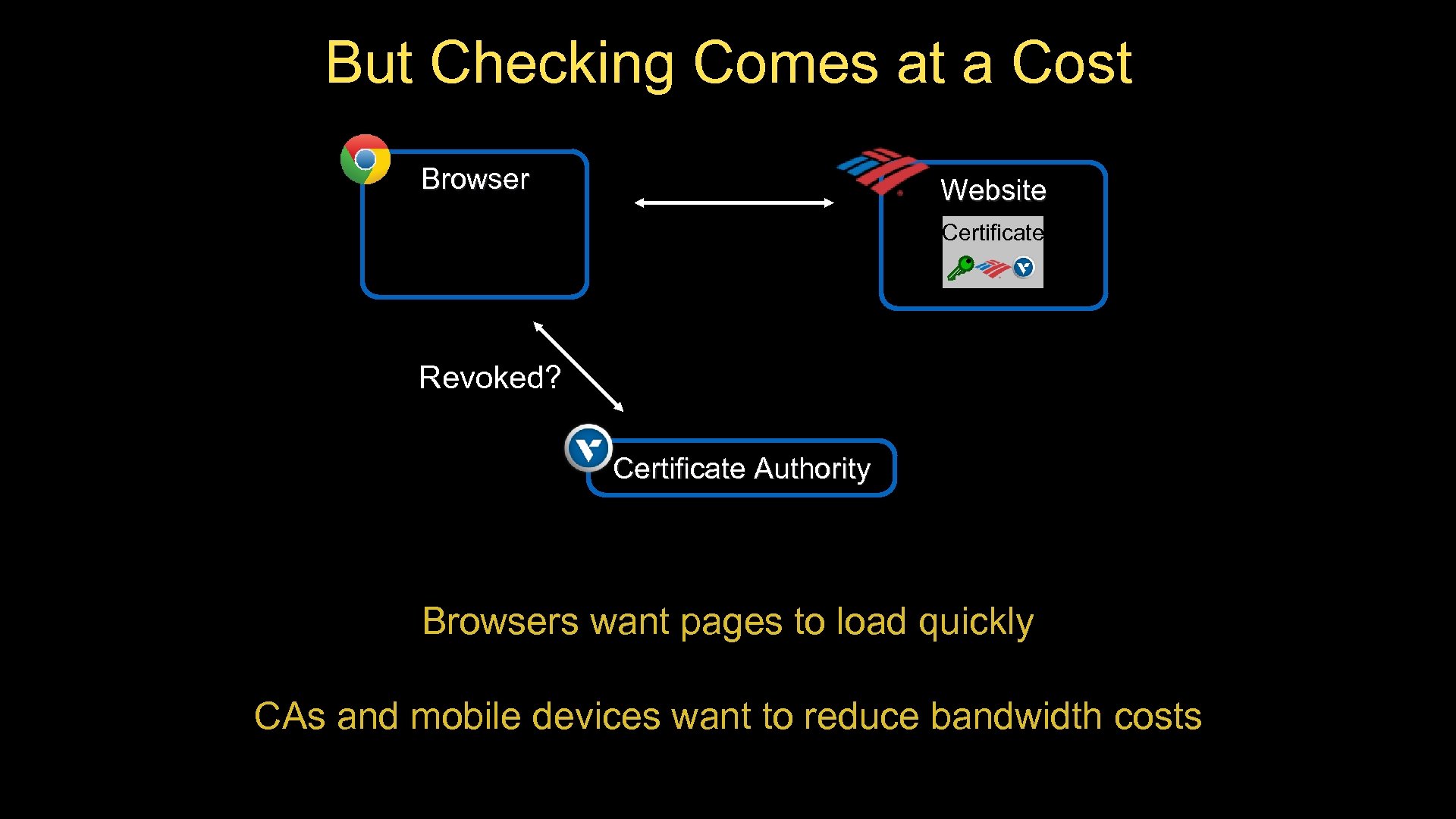
But Checking Comes at a Cost Browser Website Certificate Revoked? Certificate Authority Browsers want pages to load quickly CAs and mobile devices want to reduce bandwidth costs
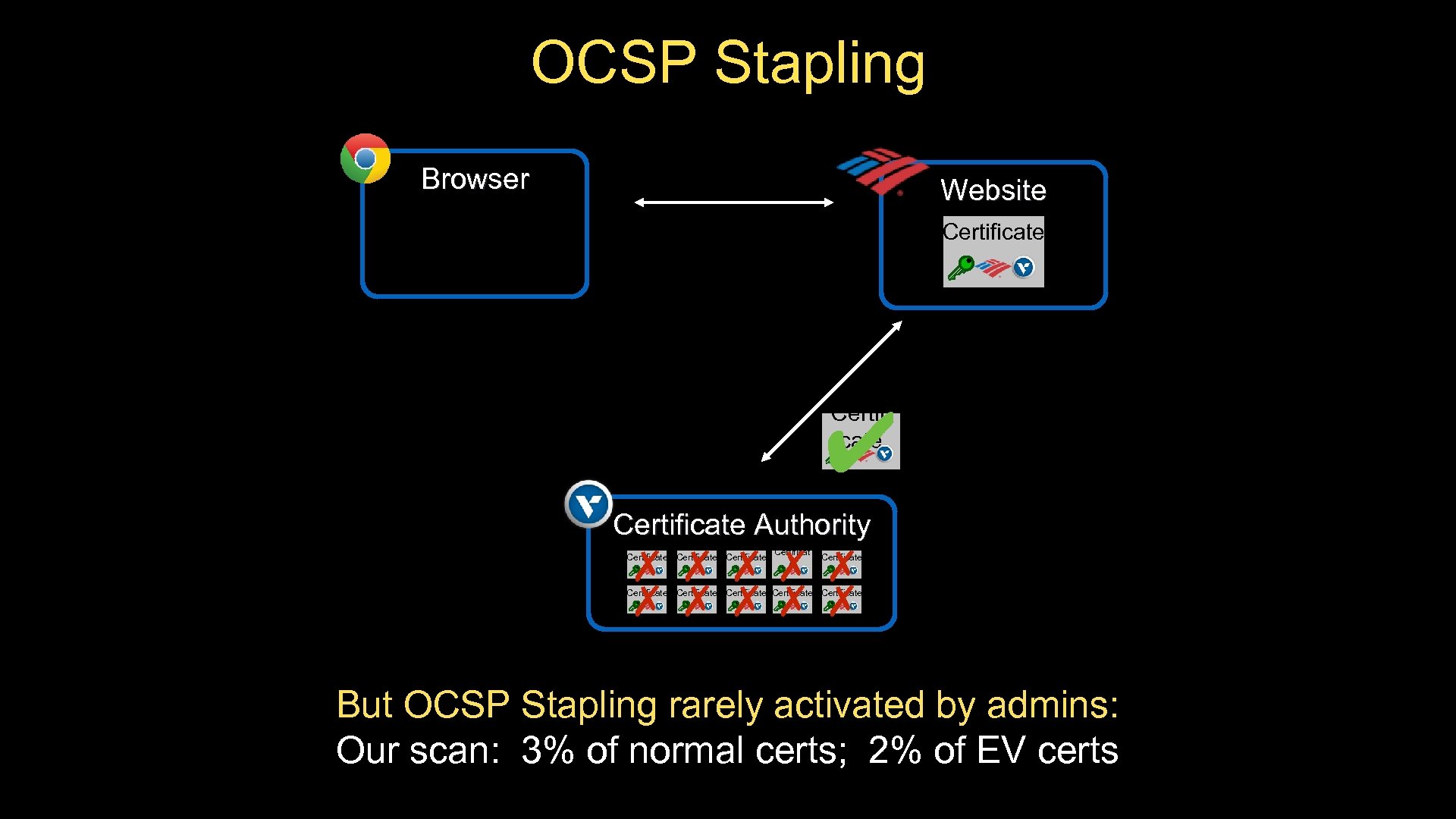
OCSP Stapling Browser Website Certificate ✔ Certifi cate Certificate Authority ✗ ✗ ✗✗ ✗ Certificate Certificat e Certificate Certificate But OCSP Stapling rarely activated by admins: Our scan: 3% of normal certs; 2% of EV certs
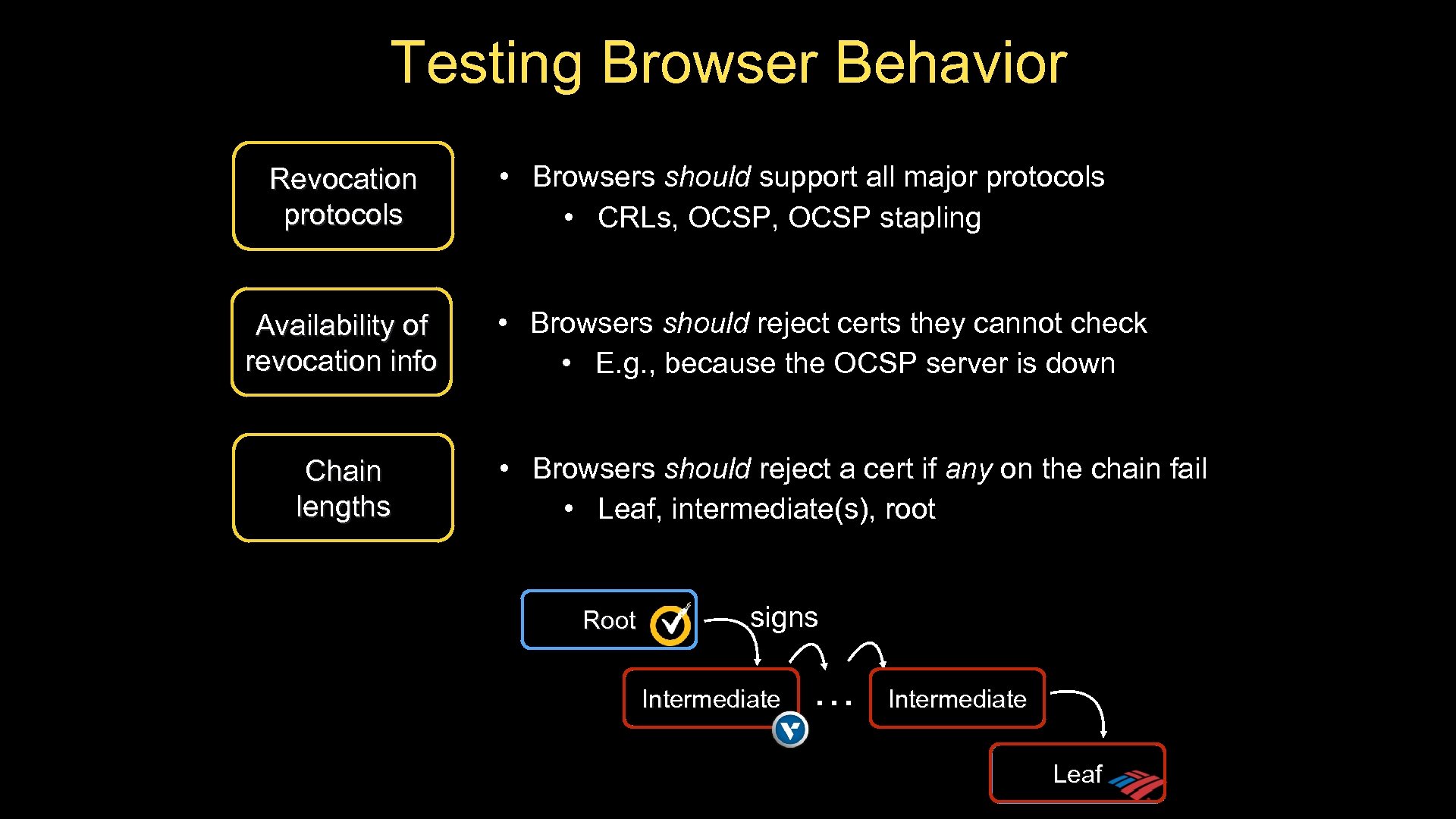
Testing Browser Behavior Revocation protocols Availability of revocation info Chain lengths • Browsers should support all major protocols • CRLs, OCSP stapling • Browsers should reject certs they cannot check • E. g. , because the OCSP server is down • Browsers should reject a cert if any on the chain fail • Leaf, intermediate(s), root Root signs Intermediate … Intermediate Leaf
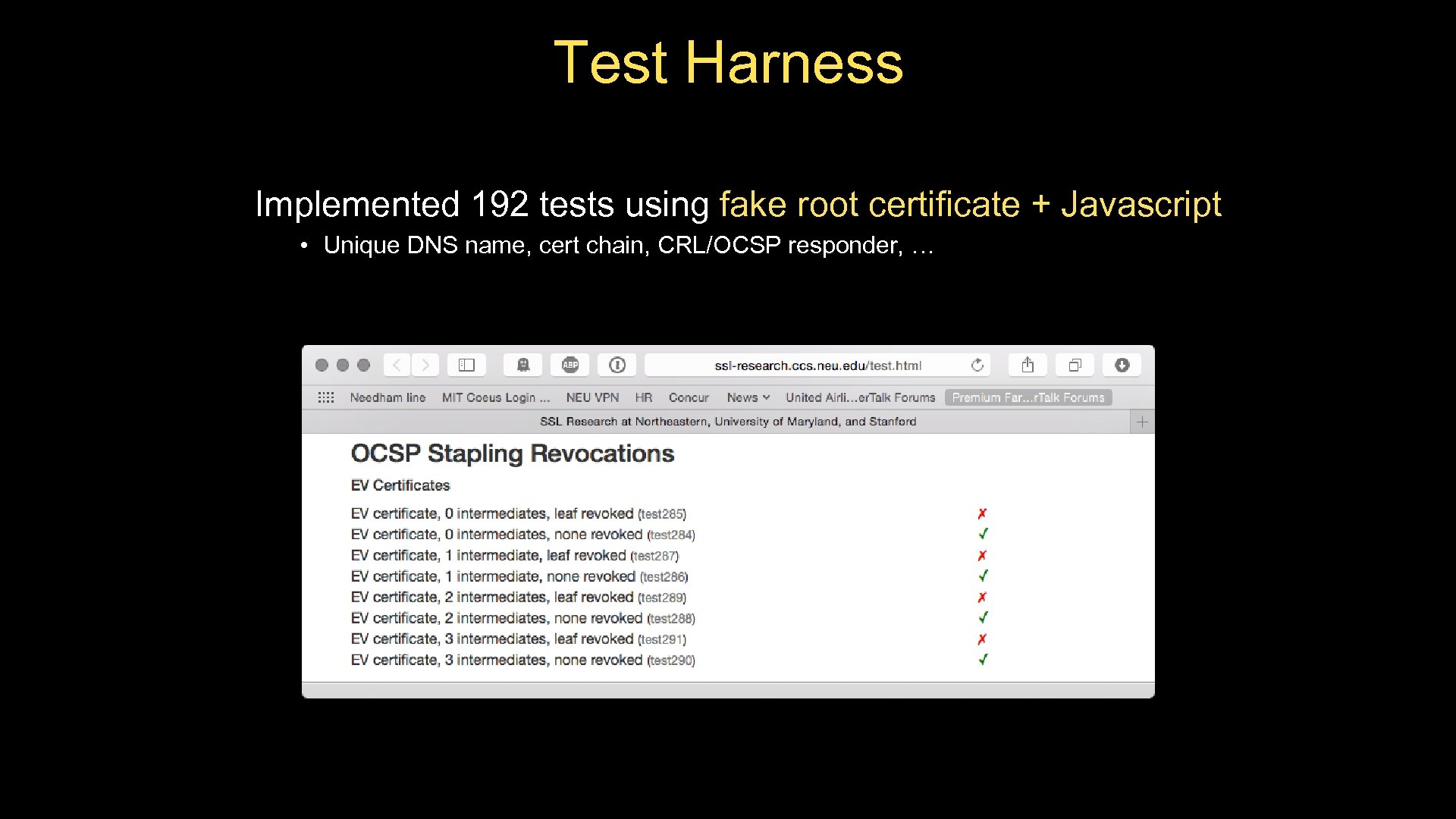
Test Harness Implemented 192 tests using fake root certificate + Javascript • Unique DNS name, cert chain, CRL/OCSP responder, …
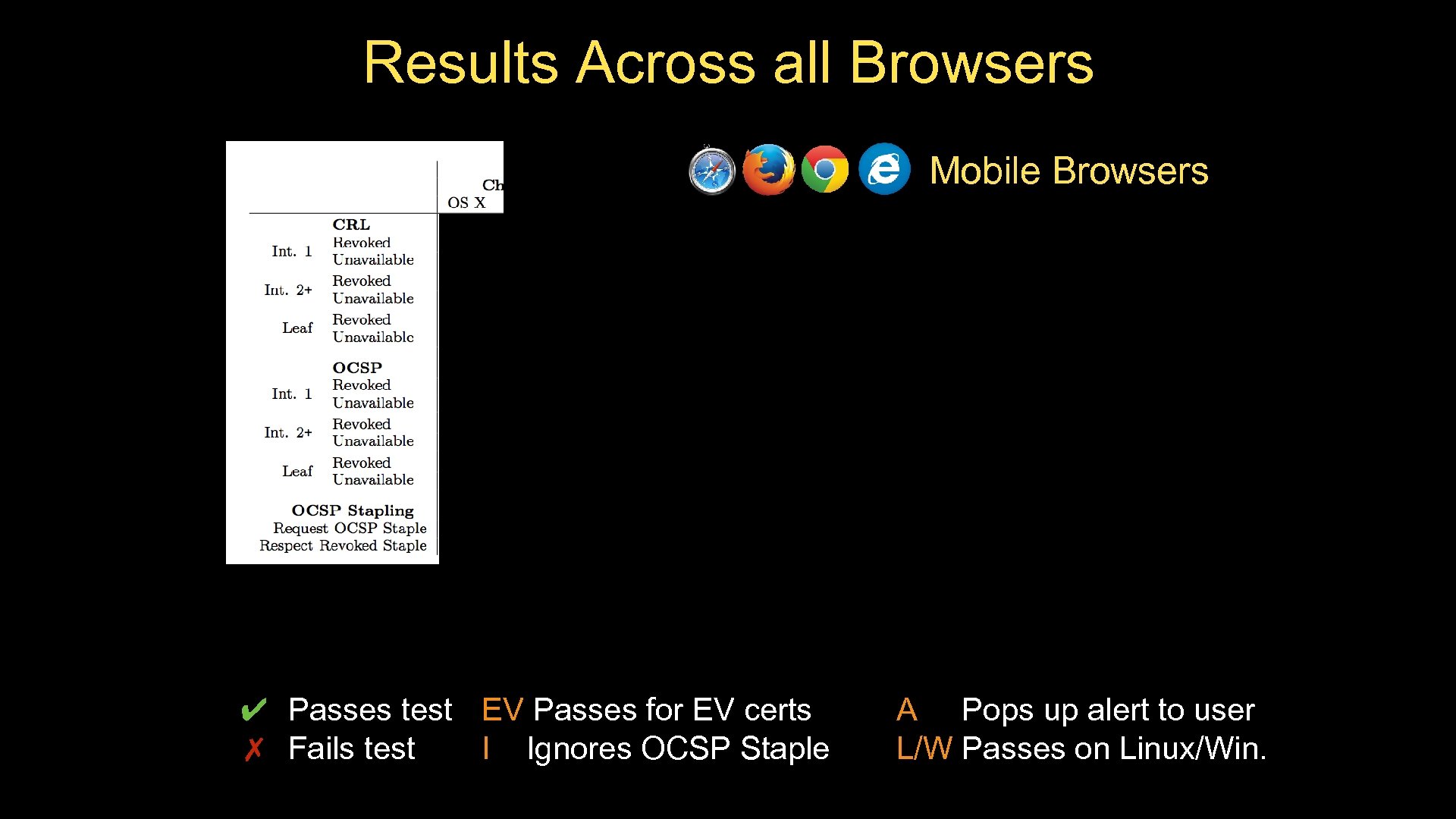
Results Across all Browsers Mobile Browsers Internet Explorer Firefox Safari Chrome Uniformly never check Never checks CRLs OCSP Checks CRLs and OCSP Generally, only checks for EV certs Only checks intermediates for EV certs ~3% of all certs Often rejects if revocation info unavailable Allows if revocation info unavailable Pops up alert for leaf in IE 10+ Except for first intermediate, for CRLs Allows if revocation info unavailable Android browsers request Staple Supports OCSP stapling …and promptly ignore it Supports OCSP stapling Does not support OCSP stapling ✔ Passes test EV Passes for EV certs ✗ Fails test I Ignores OCSP Staple A Pops up alert to user L/W Passes on Linux/Win.

Results Across all Browsers ✔ Passes test Browser developers are not EV Passes for EV certs A Pops up alert to user ✗ Fails test I Ignores OCSP Staple L/W Passes on Linux/Win. doing what the PKI needs them to do
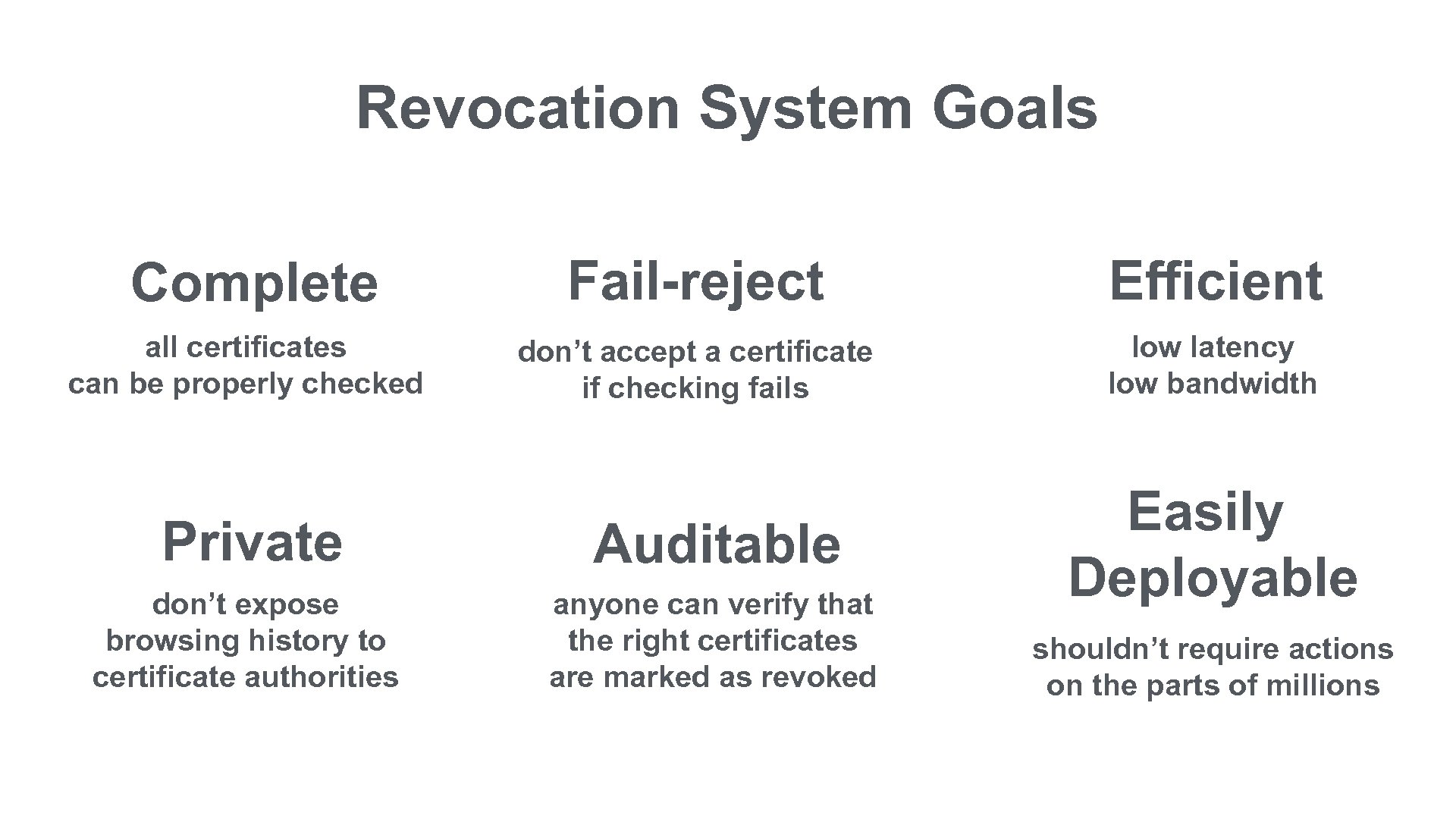
Revocation System Goals Complete Fail-reject Efficient all certificates can be properly checked don’t accept a certificate if checking fails low latency low bandwidth Private Auditable don’t expose browsing history to certificate authorities anyone can verify that the right certificates are marked as revoked Easily Deployable shouldn’t require actions on the parts of millions
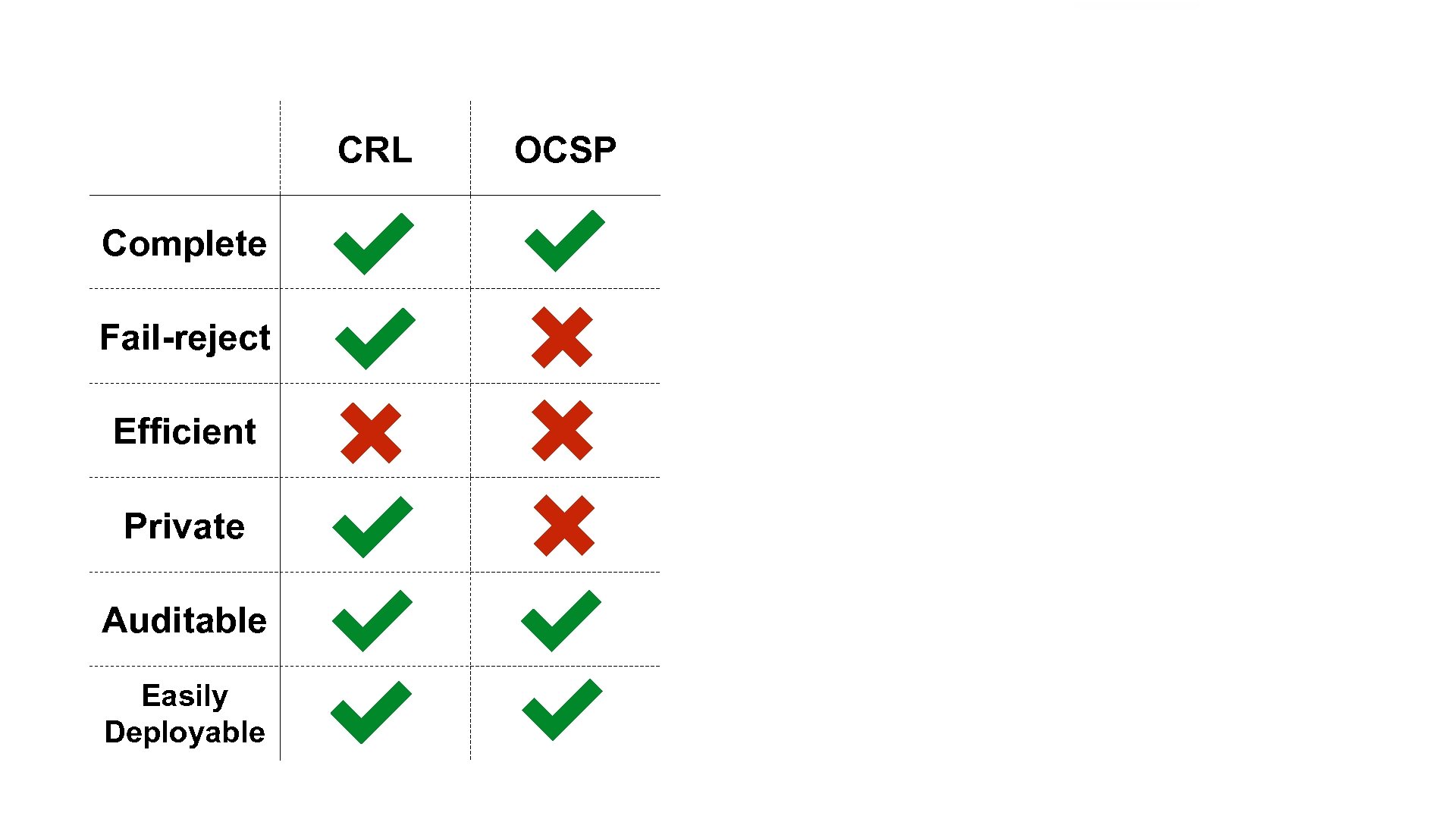
CRL Complete OCSP One. CRLSet 400 15 K Fail-reject Efficient Private Auditable Easily Deployable Revocation Transparency Rev. Cast
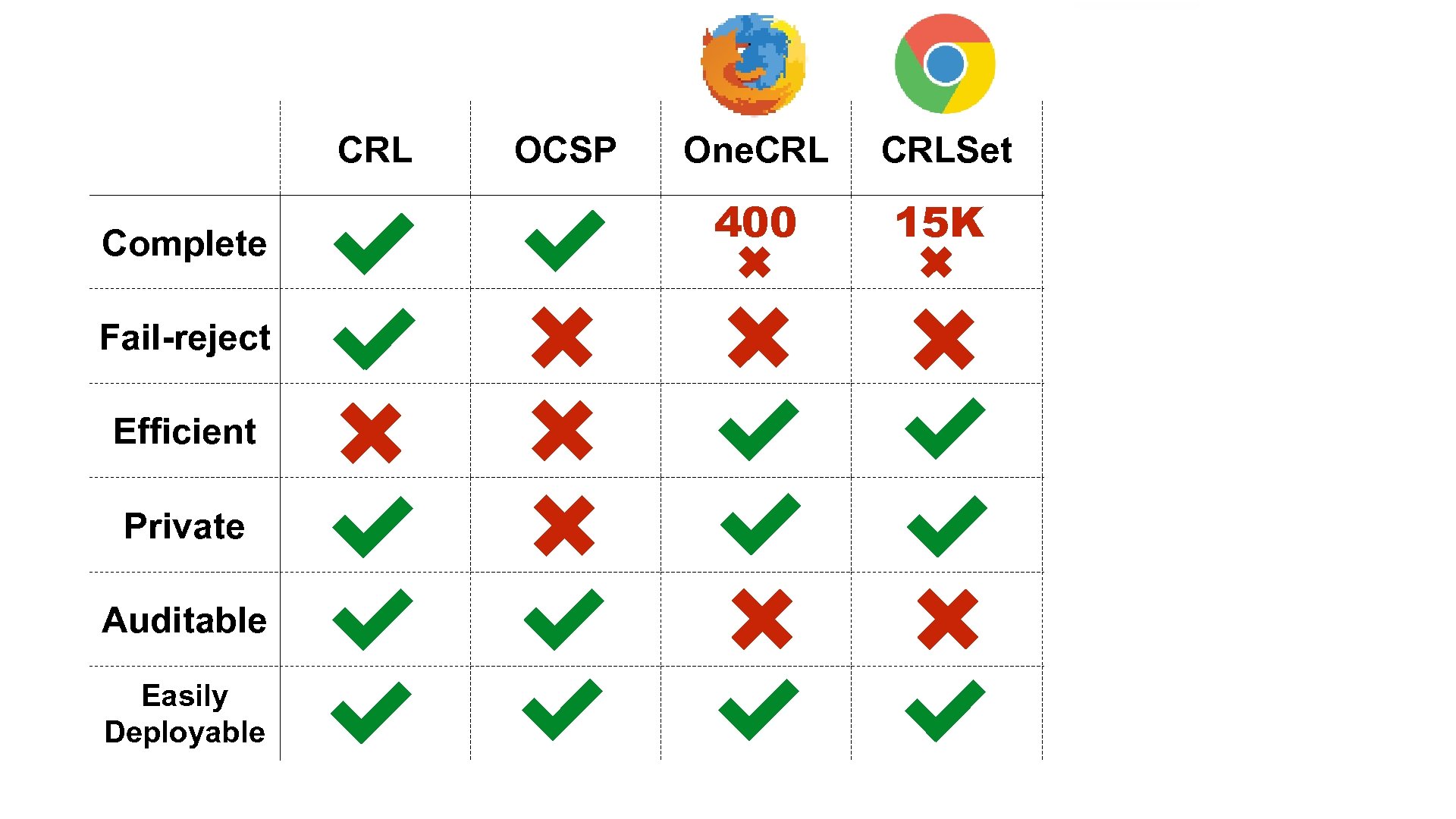
CRL Complete Fail-reject Efficient Private Auditable Easily Deployable OCSP One. CRLSet 400 15 K Revocation Transparency Rev. Cast
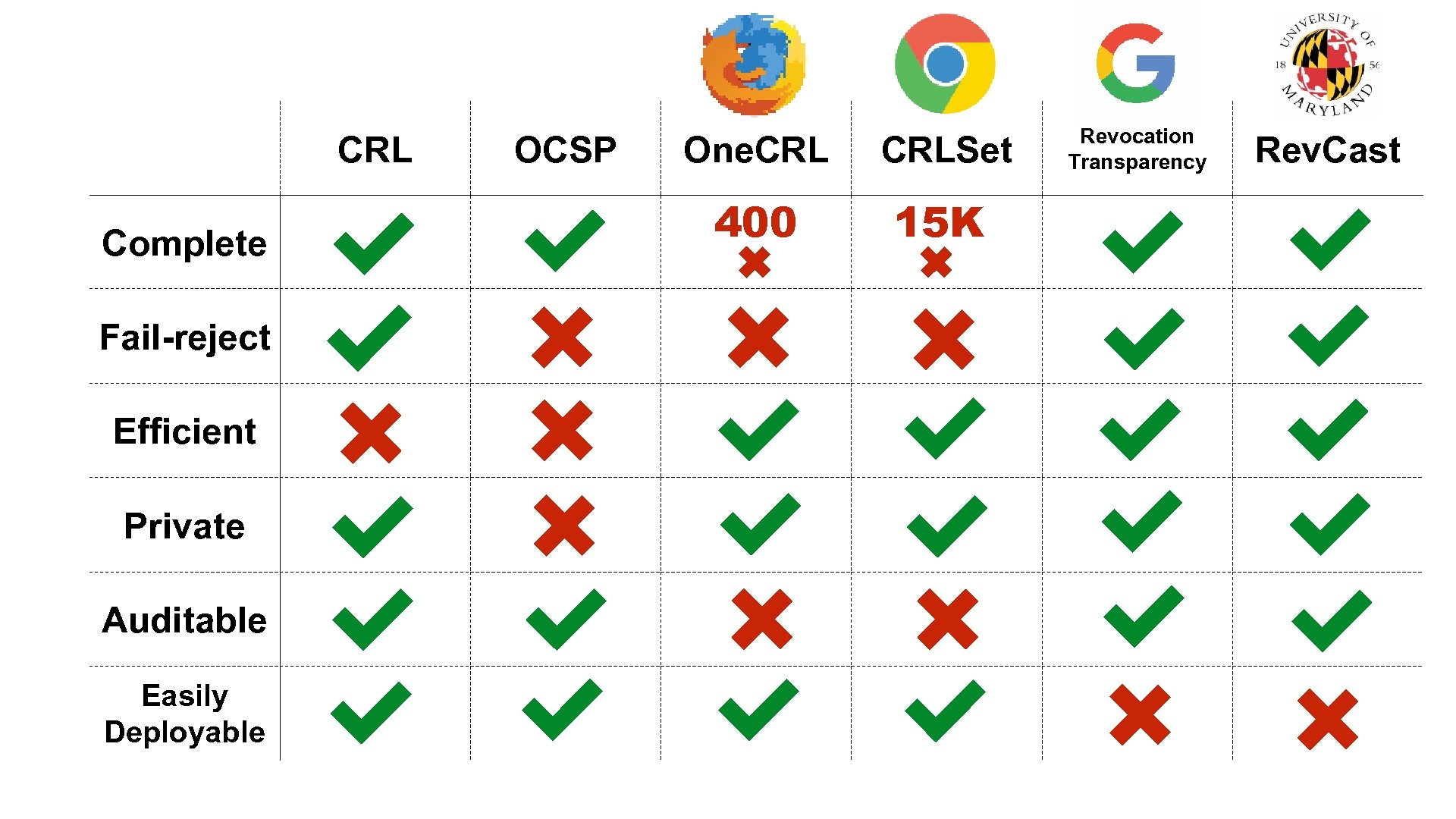
CRL Complete Fail-reject Efficient Private Auditable Easily Deployable OCSP One. CRLSet 400 15 K Revocation Transparency Rev. Cast
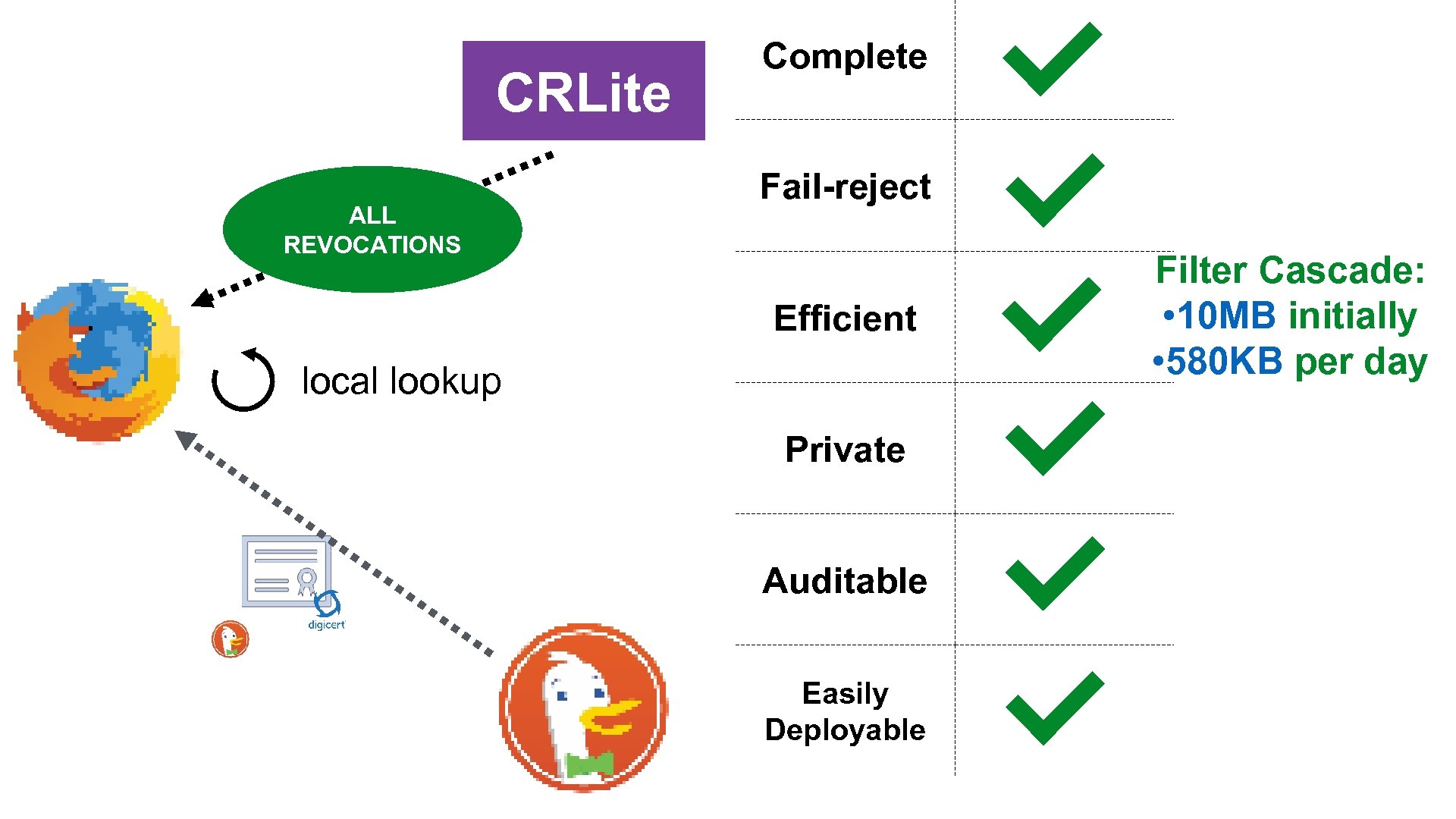
CRLite ALL REVOCATIONS Complete Fail-reject Efficient local lookup Private Auditable Easily Deployable Filter Cascade: • 10 MB initially • 580 KB per day
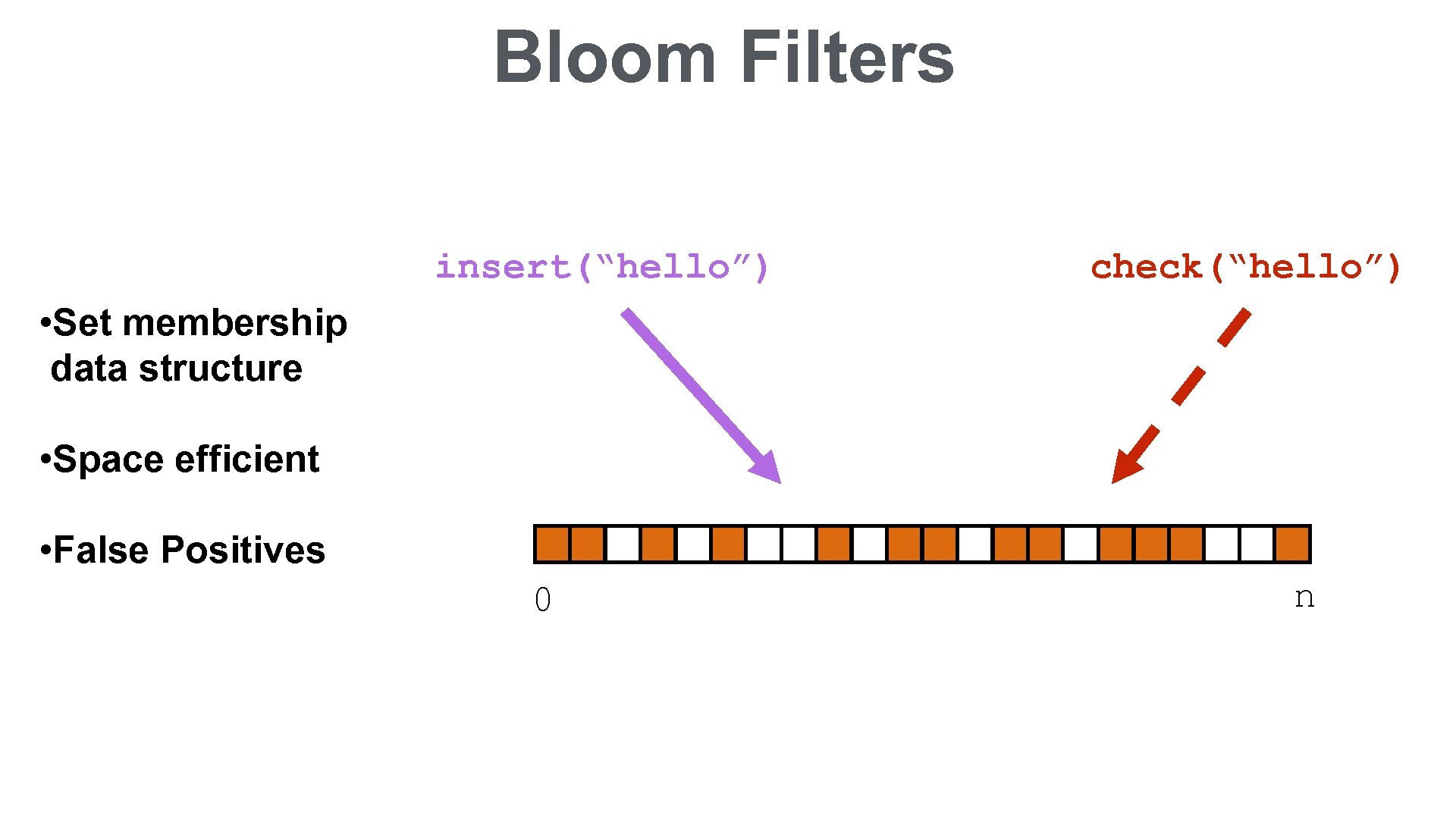
Bloom Filters insert(“hello”) check(“hello”) • Set membership data structure • Space efficient • False Positives 0 n
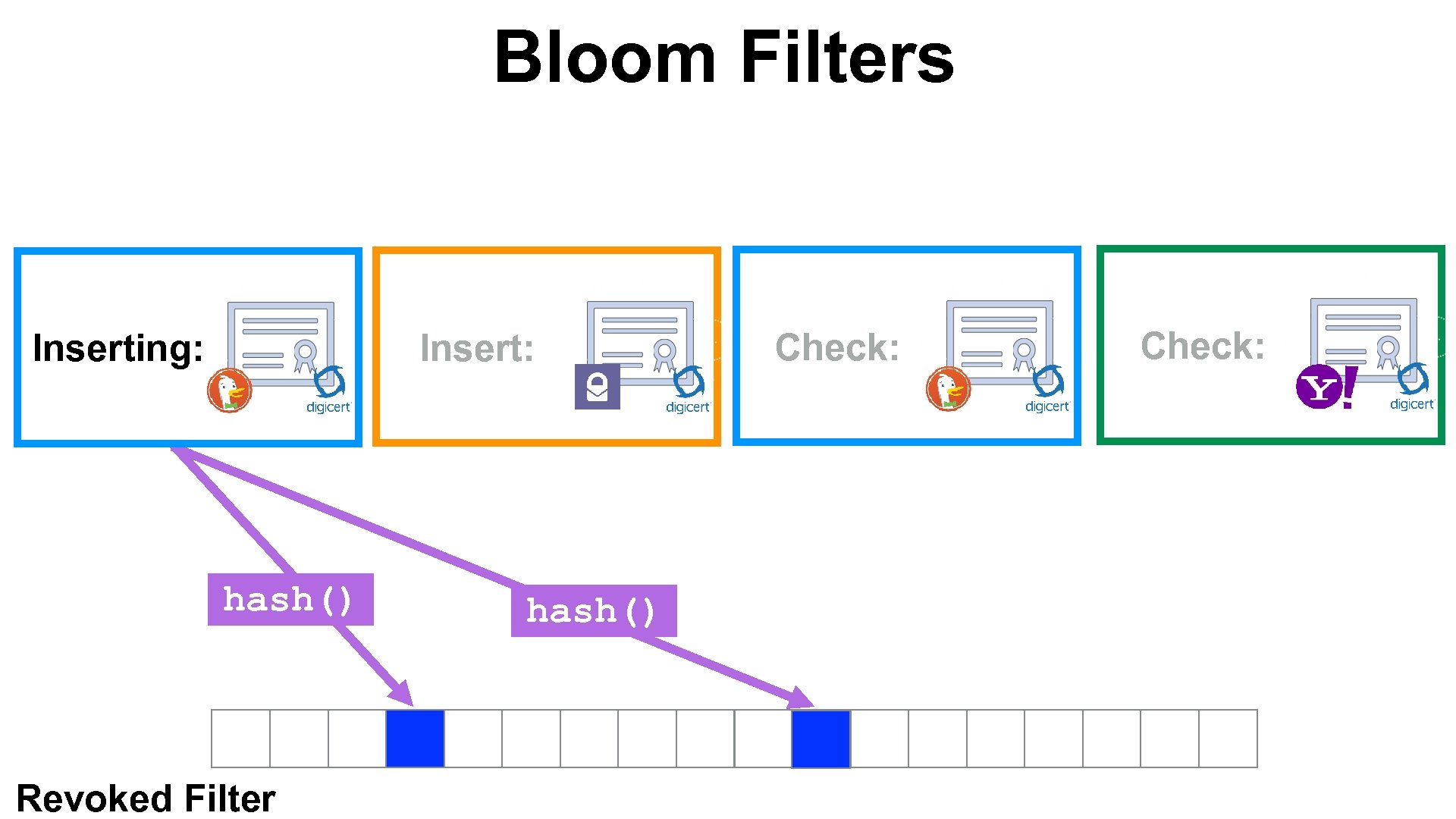
Bloom Filters Insert: Inserting: hash() Revoked Filter hash() Check:
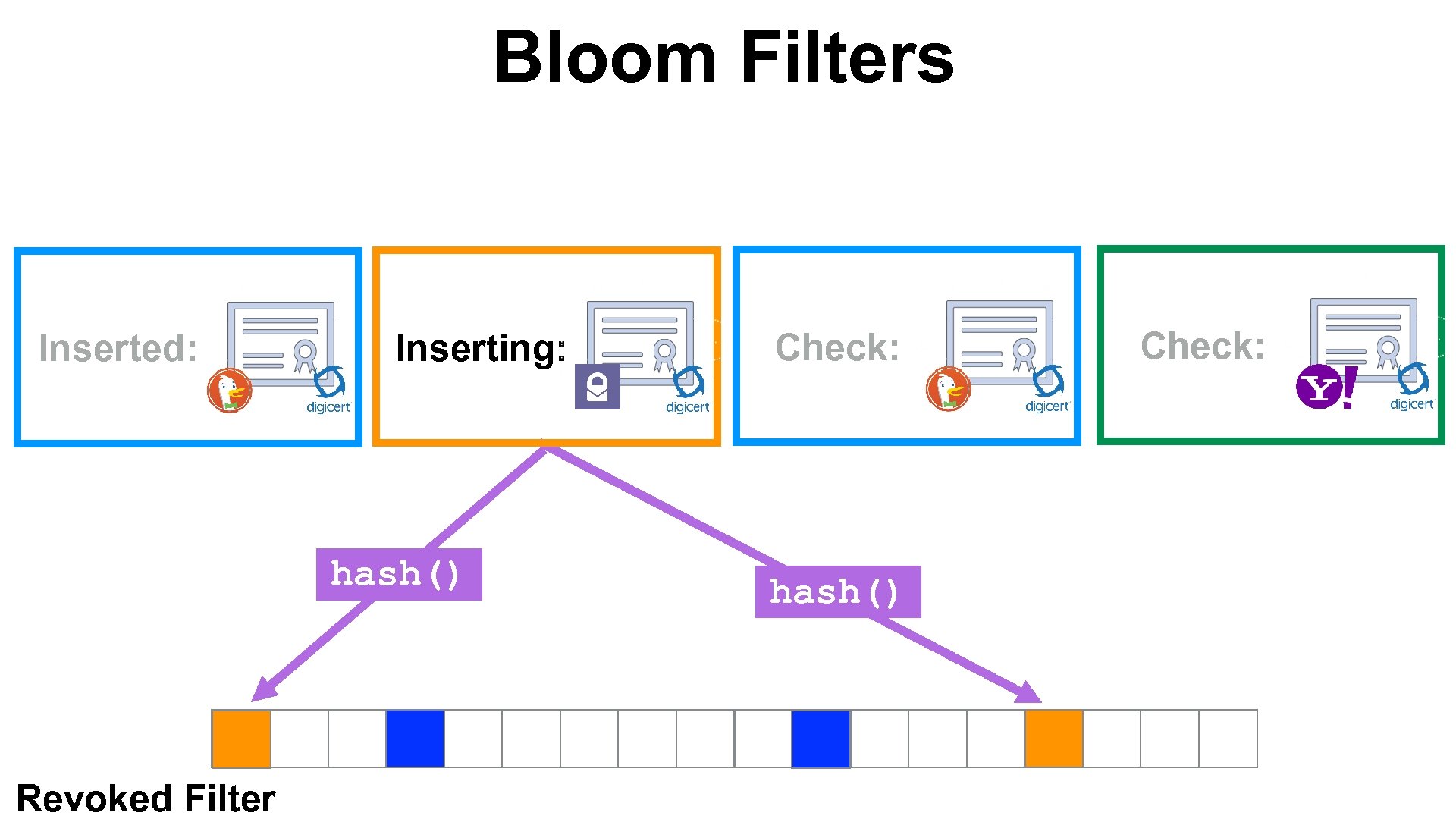
Bloom Filters Inserted: Inserting: hash() Revoked Filter Check: hash() Check:
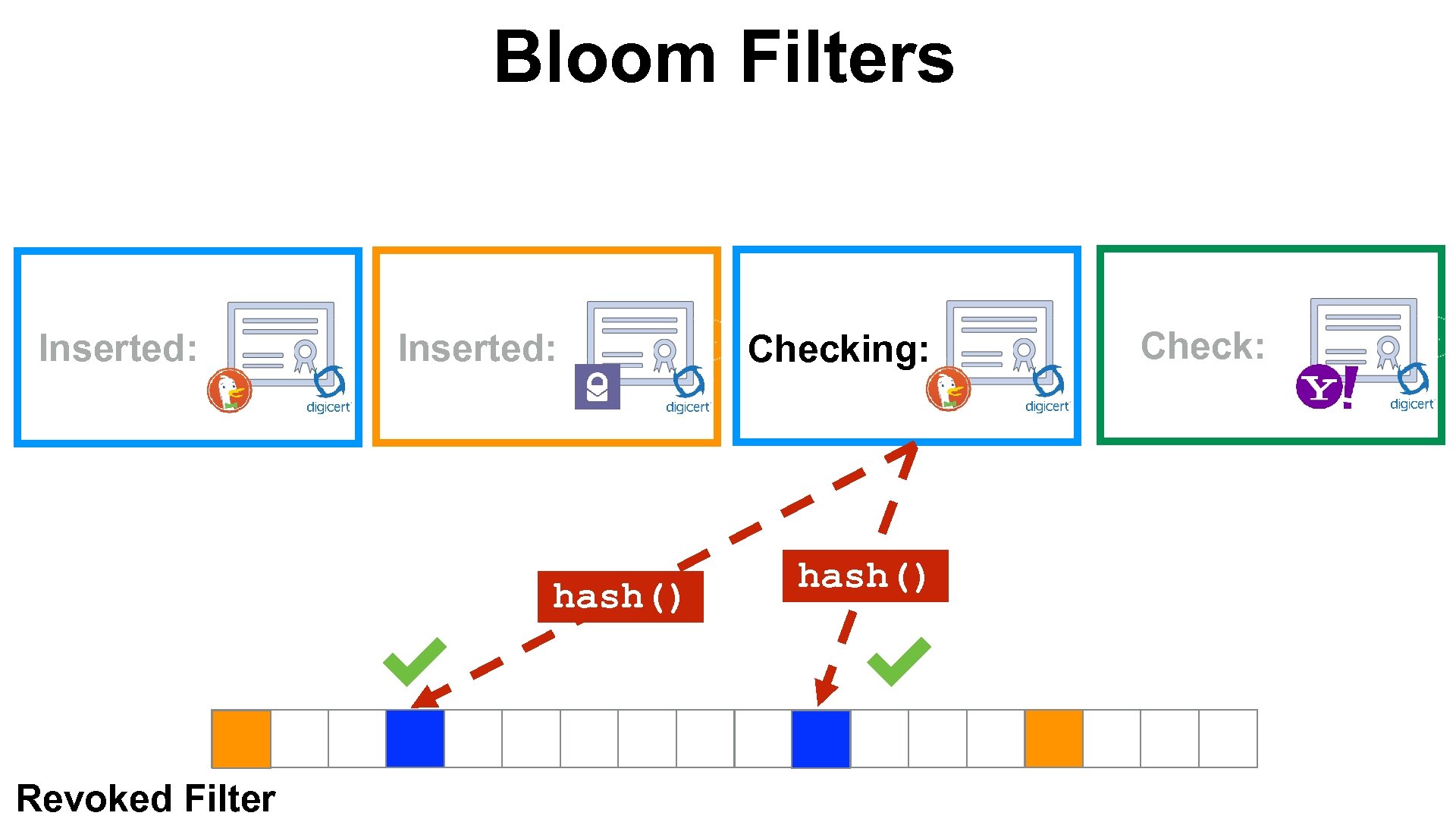
Bloom Filters Inserted: hash() Revoked Filter Checking: hash() Check:
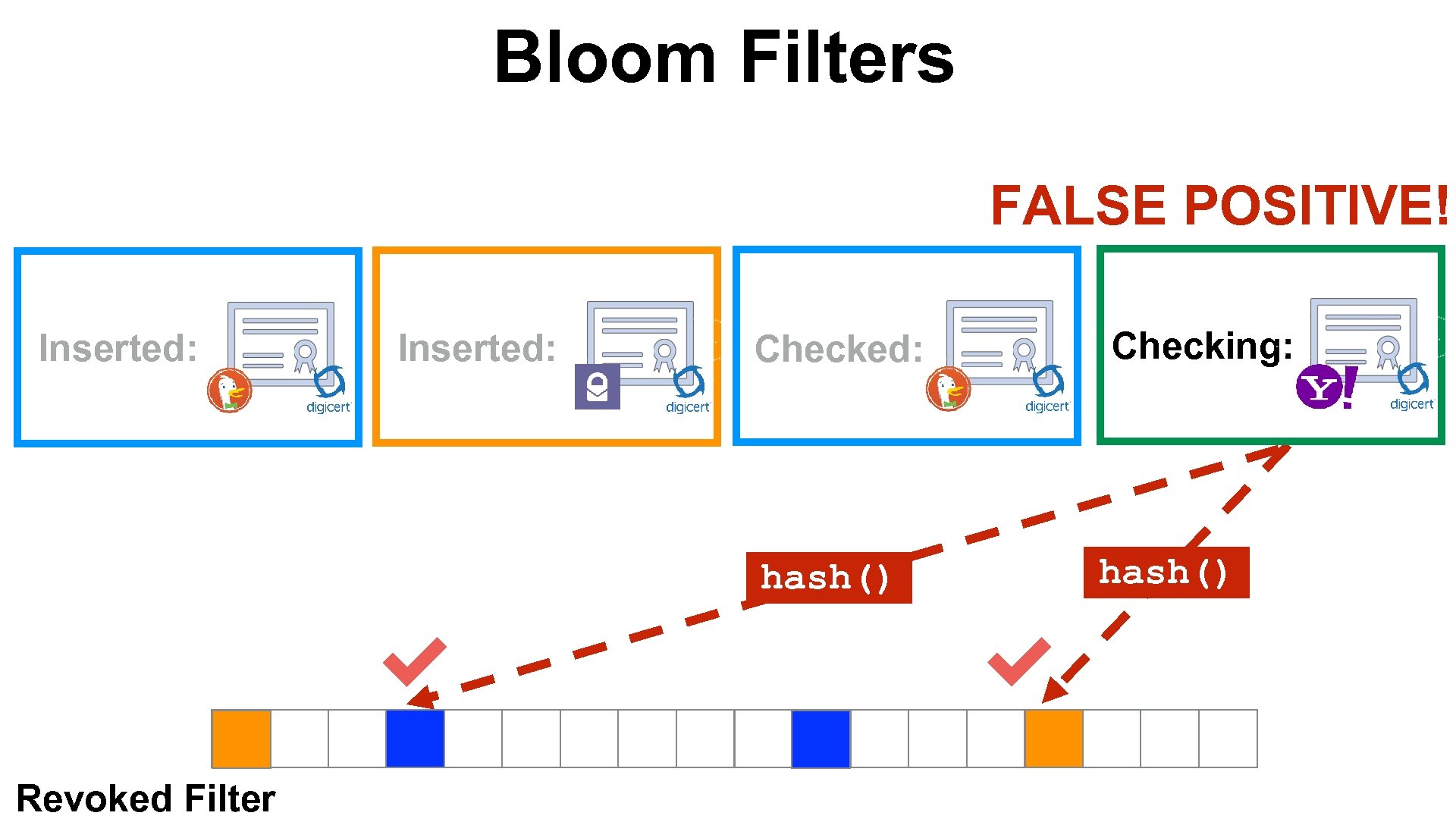
Bloom Filters FALSE POSITIVE! Inserted: Checked: hash() Revoked Filter Checking: hash()

Opportunity: new databases now include all valid certificates Towards a complete view of the certificate ecosystem - Vandersloot et al. 2016
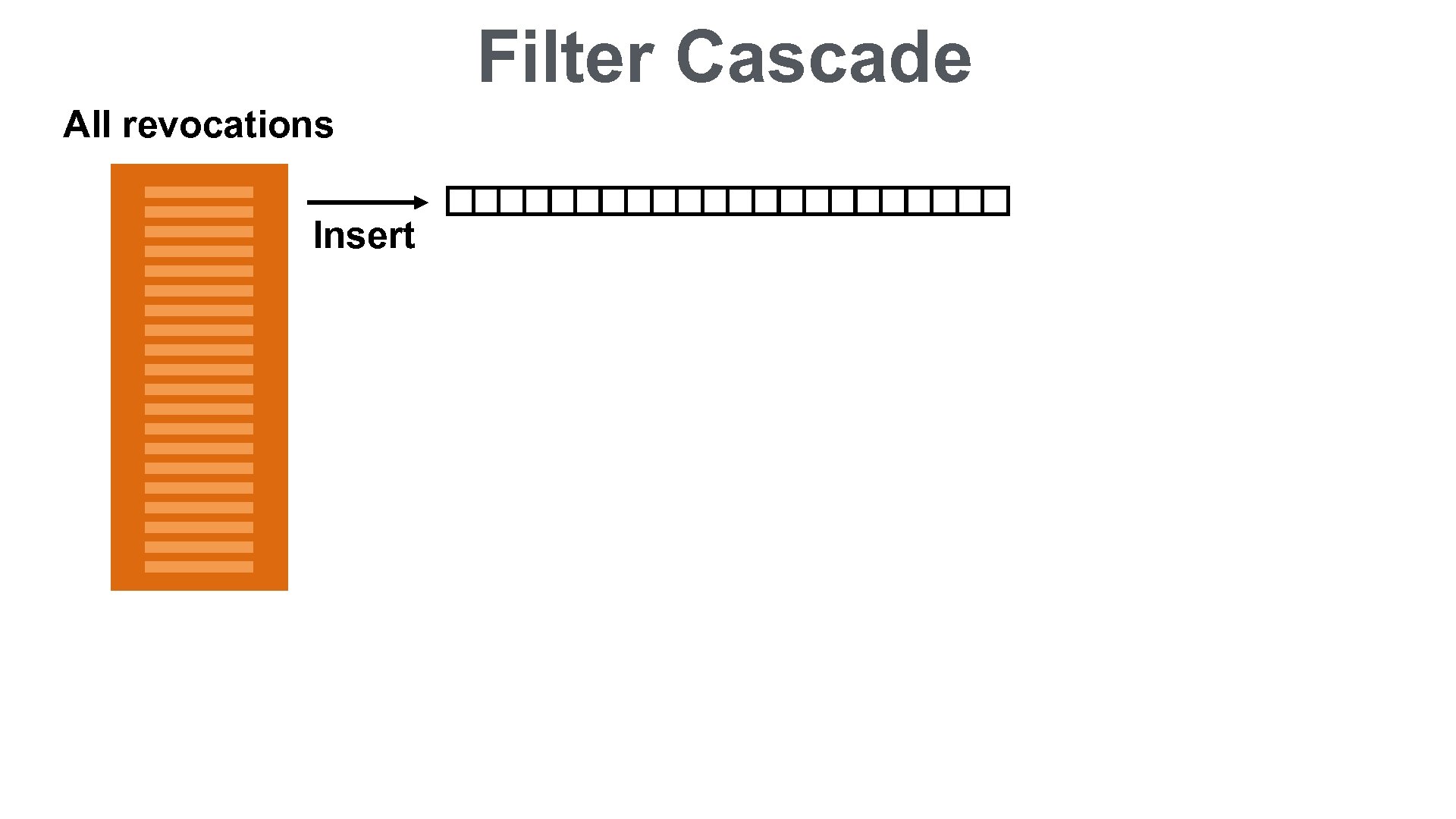
Filter Cascade All revocations Insert
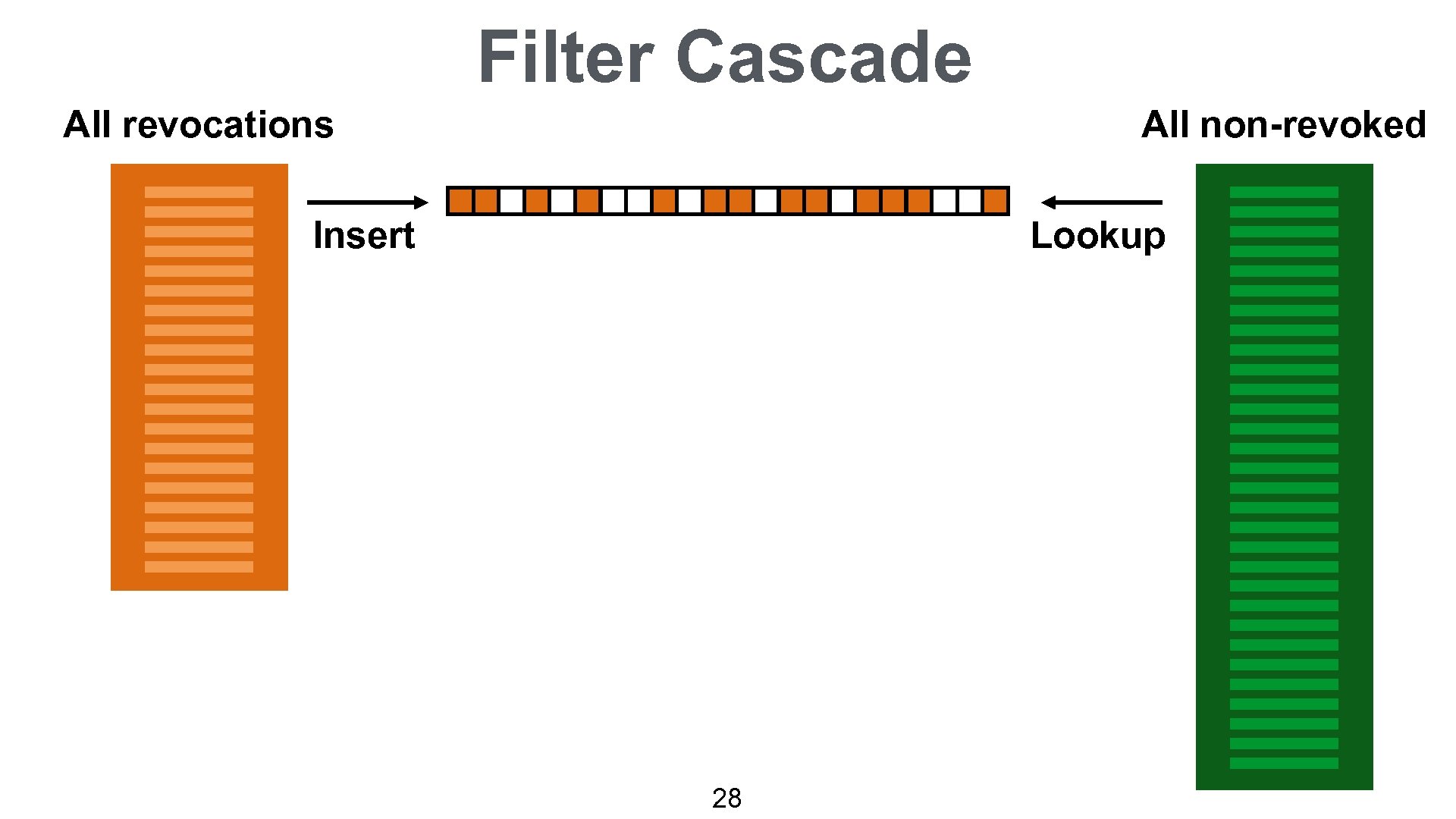
Filter Cascade All revocations All non-revoked Insert Lookup 28
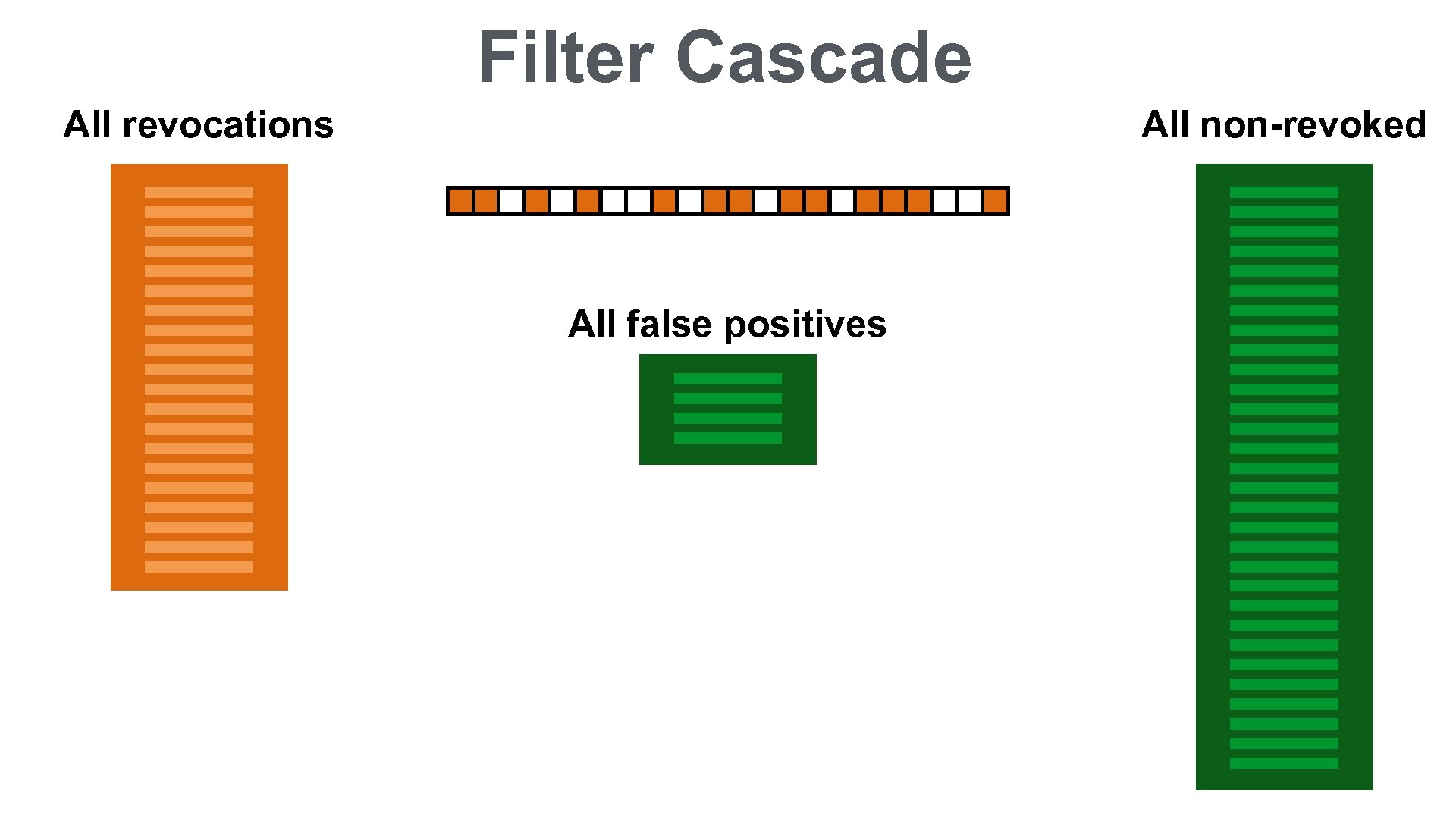
Filter Cascade All revocations All non-revoked All false positives
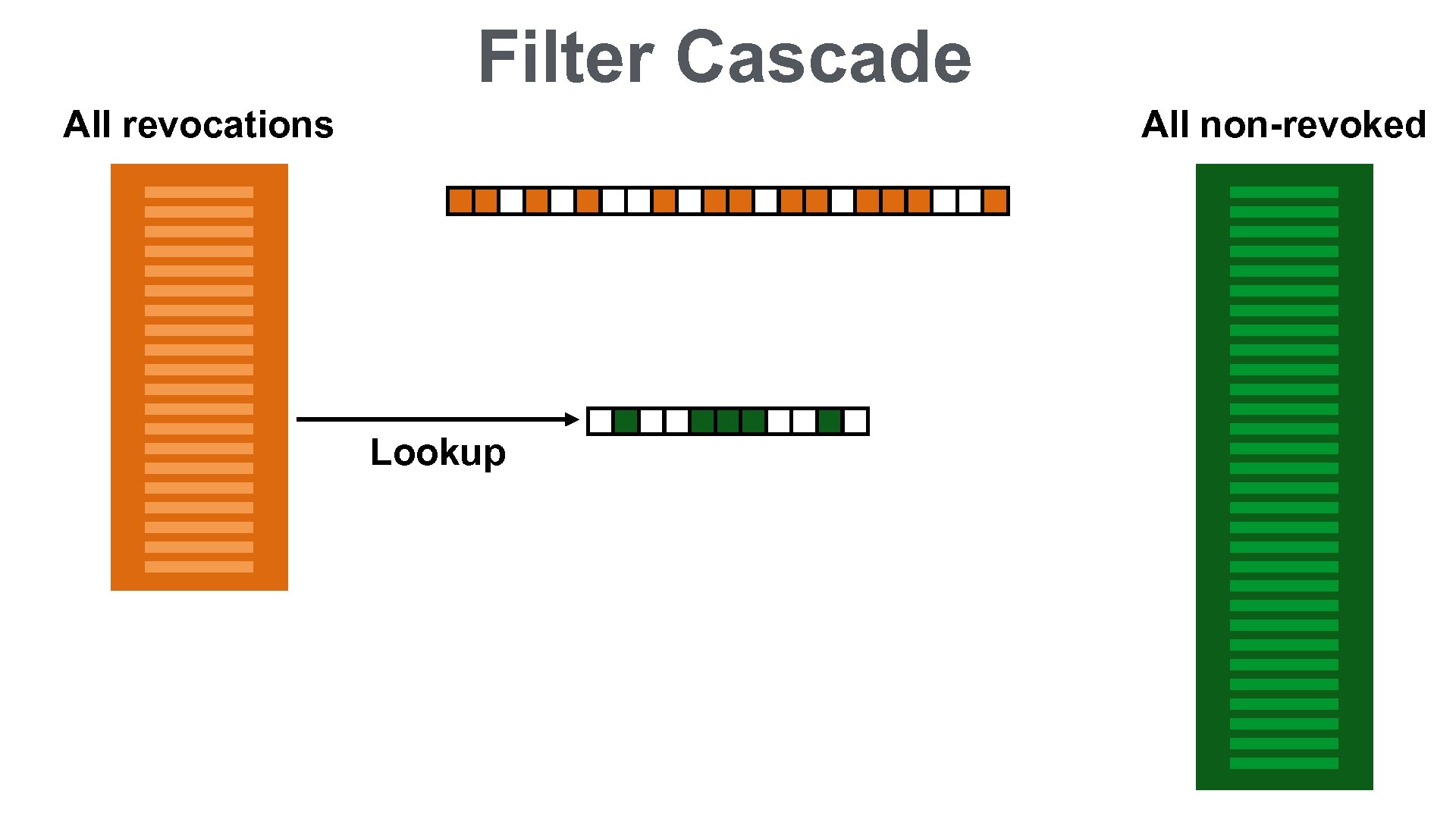
Filter Cascade All revocations All non-revoked Lookup
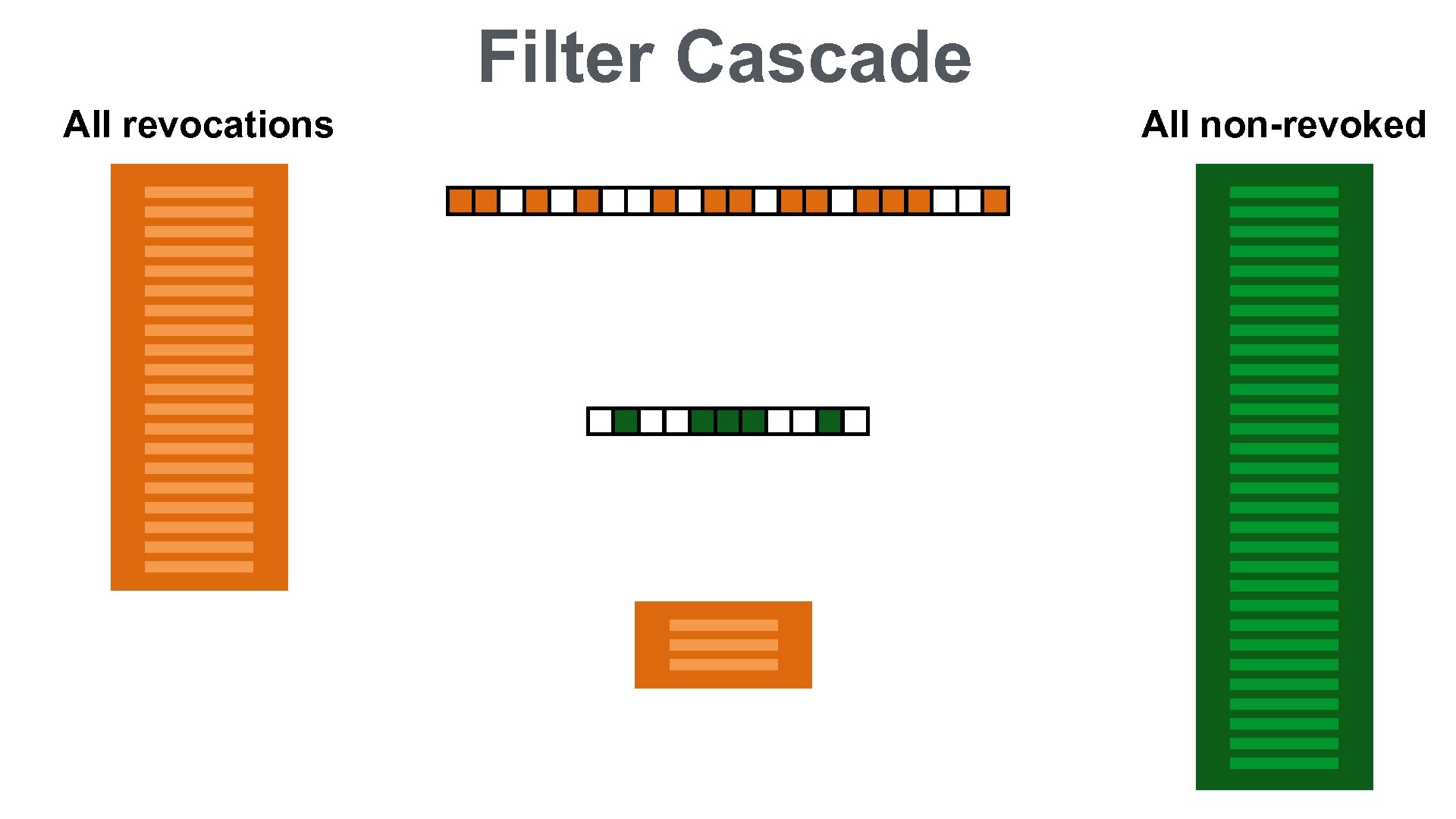
Filter Cascade All revocations All non-revoked
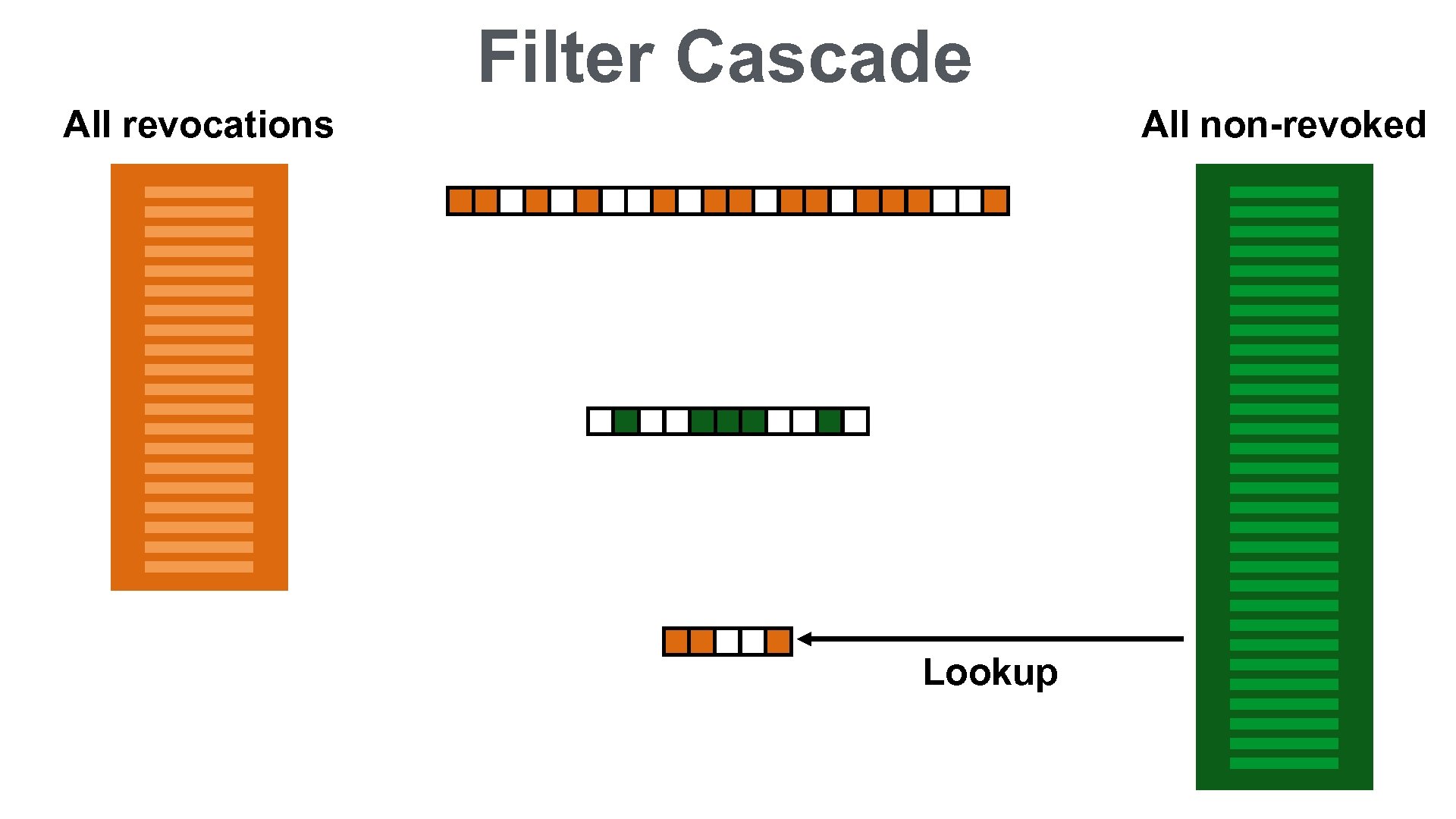
Filter Cascade All revocations All non-revoked Lookup
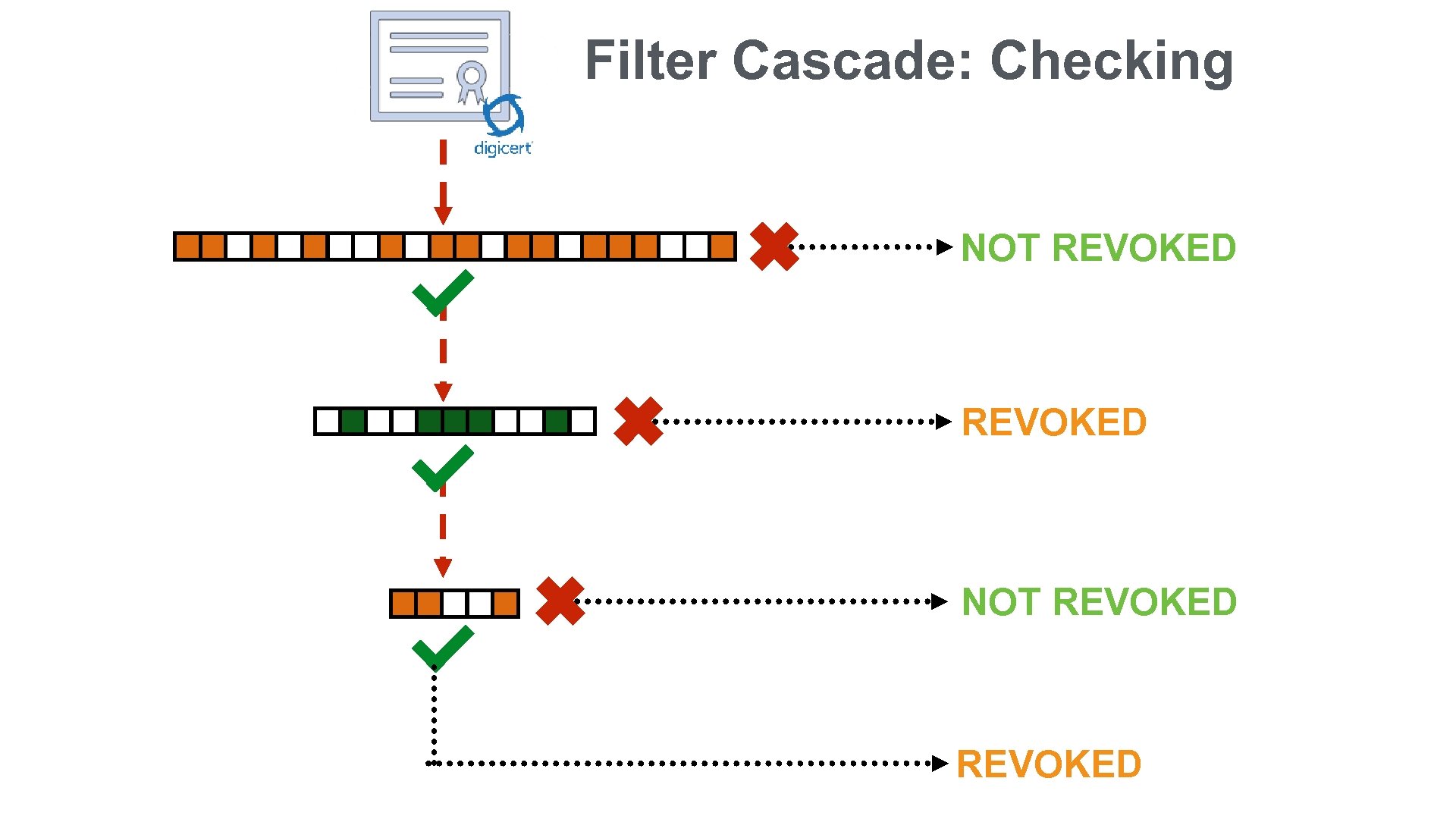
Filter Cascade: Checking NOT REVOKED
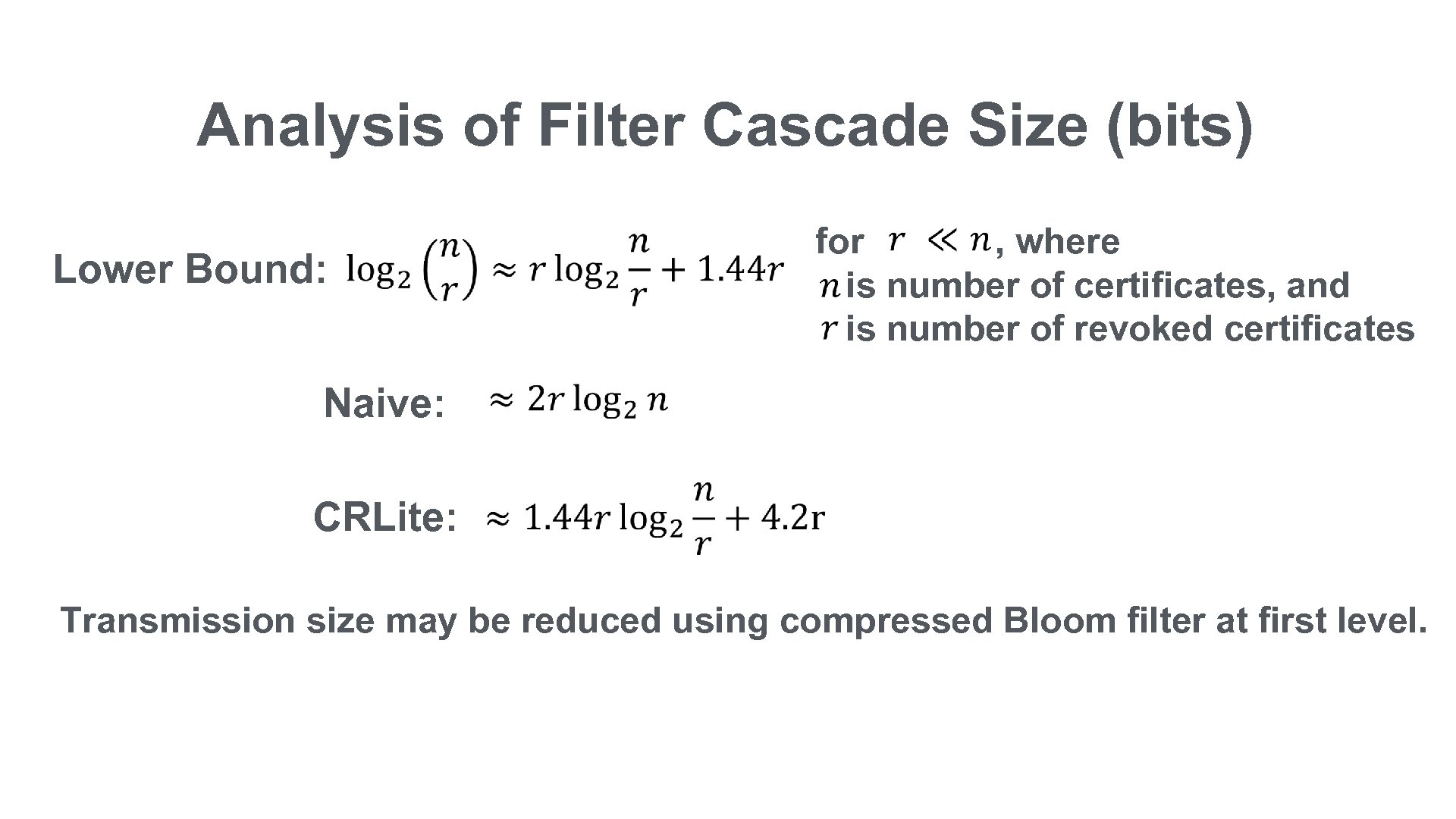
Analysis of Filter Cascade Size (bits) for , where is number of certificates, and is number of revoked certificates Lower Bound: Naive: CRLite: Transmission size may be reduced using compressed Bloom filter at first level.
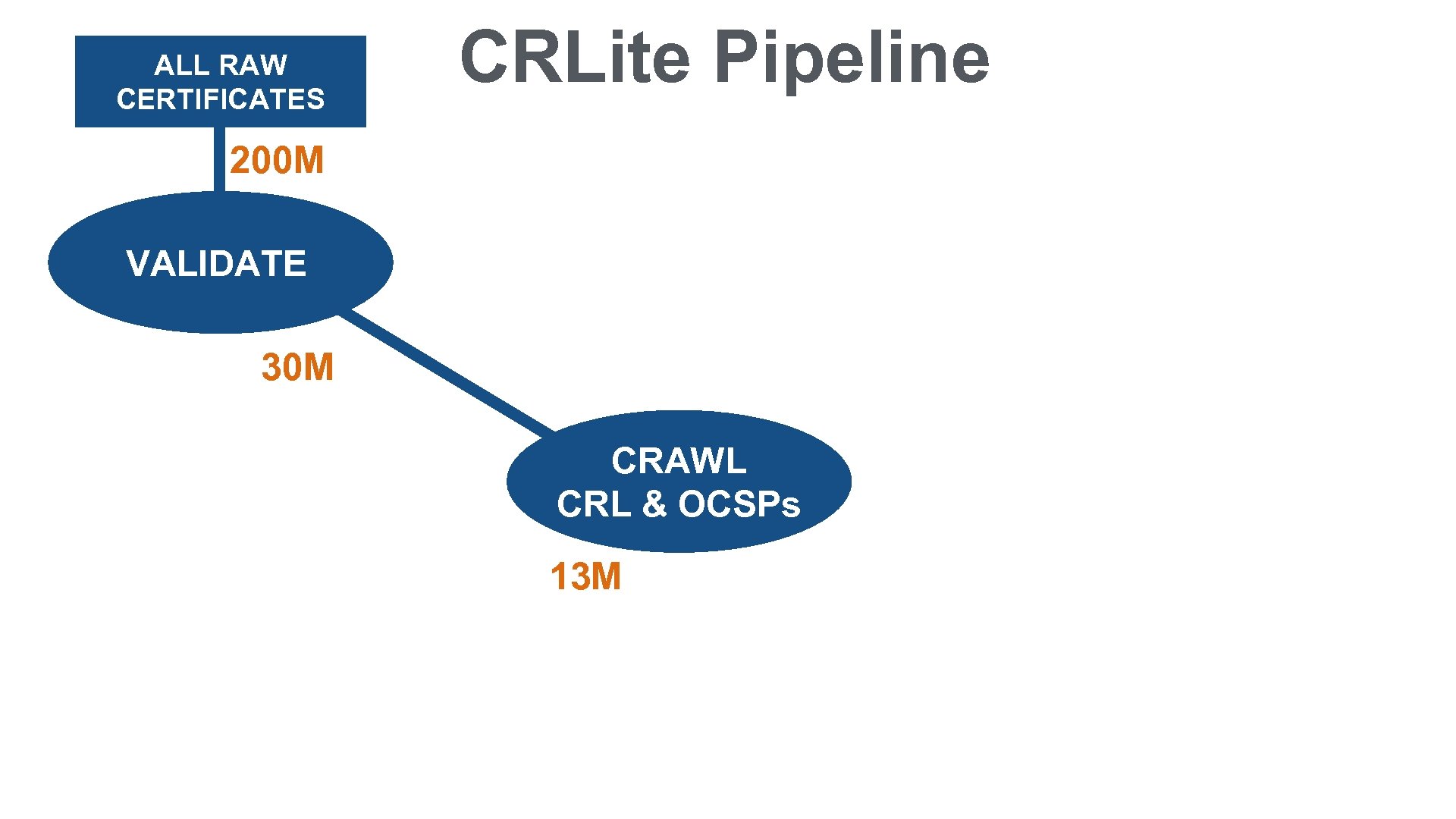
ALL RAW CERTIFICATES CRLite Pipeline 200 M VALIDATE 30 M CRAWL CRL & OCSPs 13 M
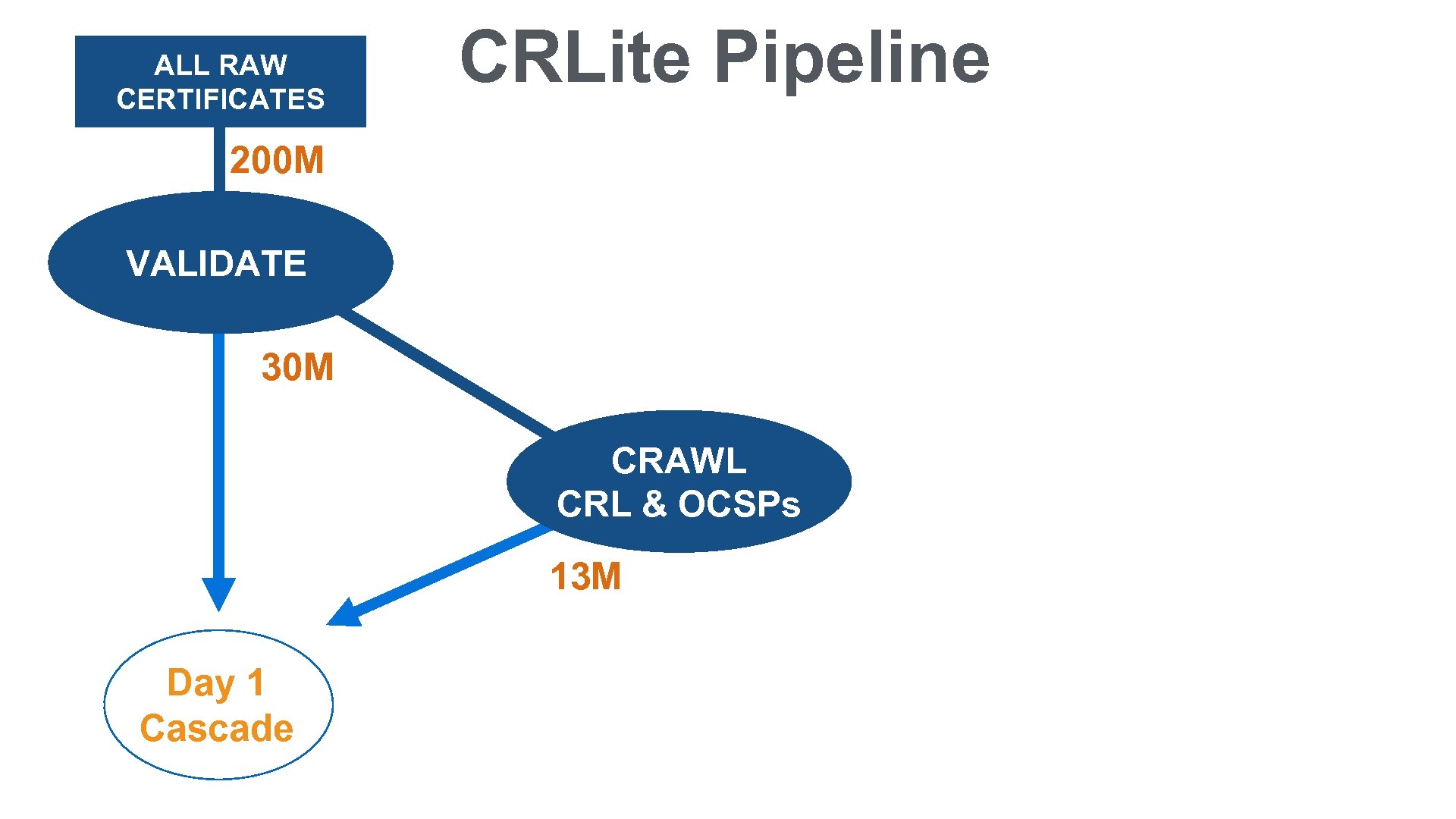
ALL RAW CERTIFICATES CRLite Pipeline 200 M VALIDATE 30 M CRAWL CRL & OCSPs 13 M Day 1 Cascade
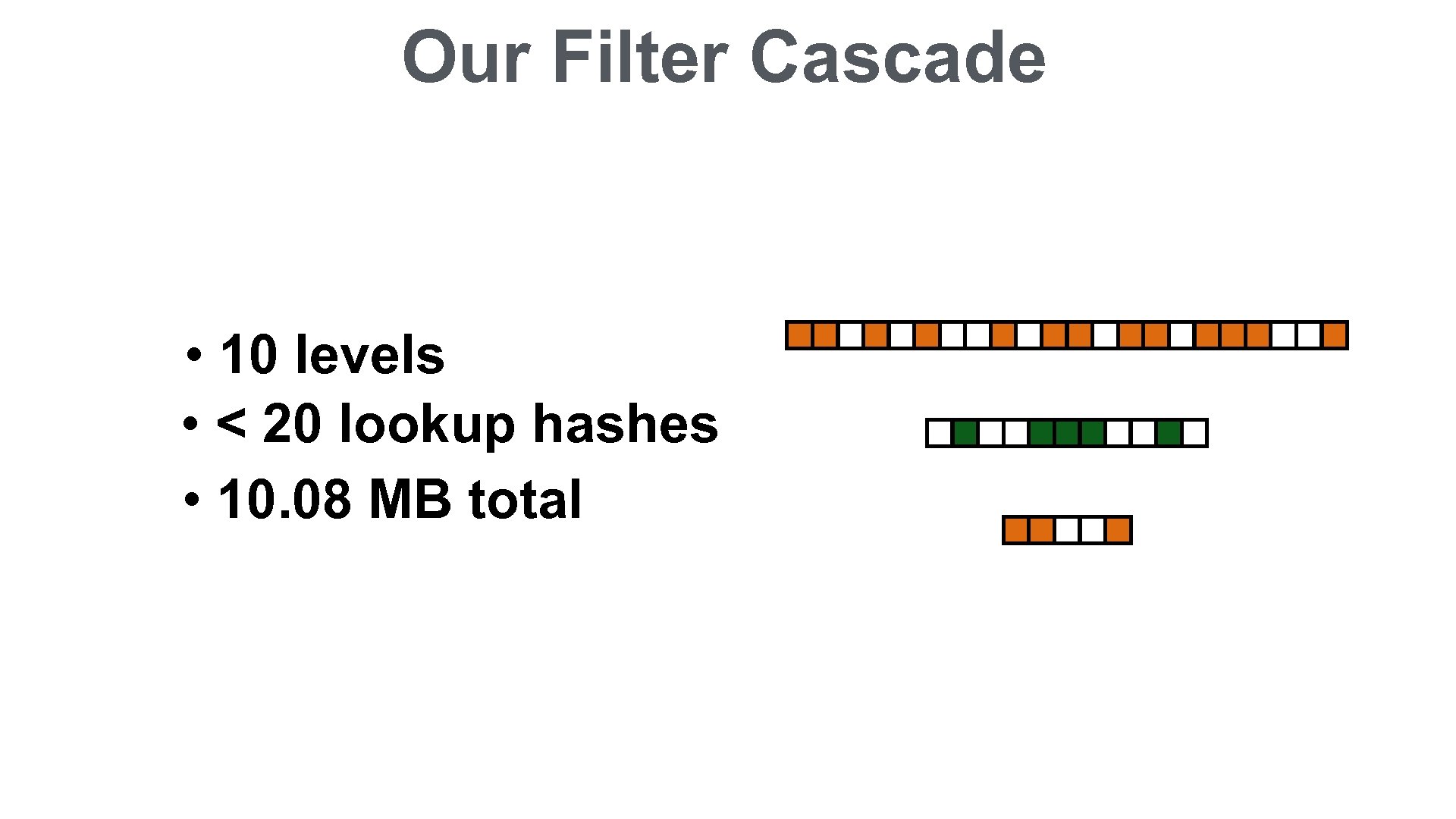
Our Filter Cascade • 10 levels • < 20 lookup hashes • 10. 08 MB total
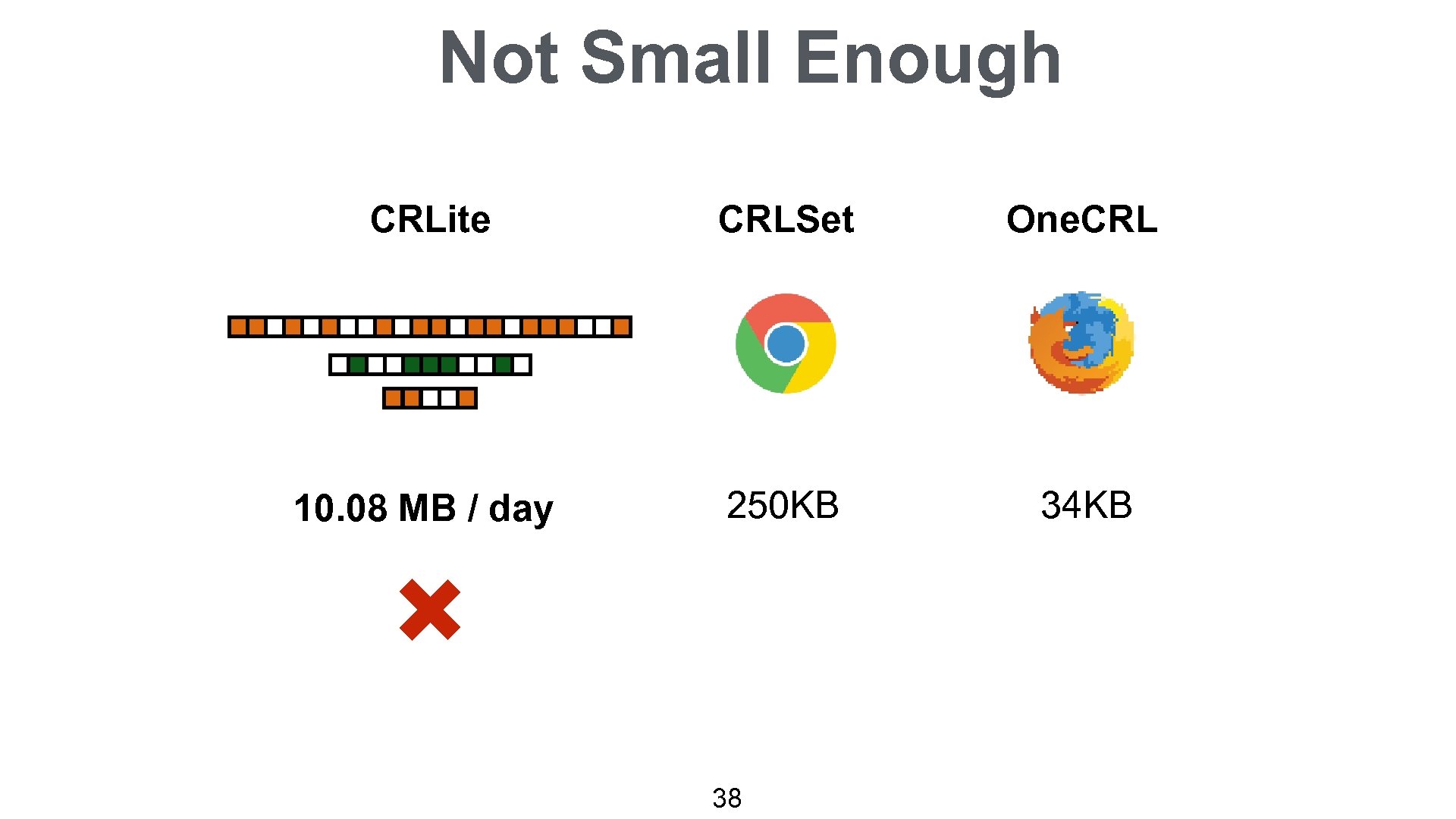
Not Small Enough CRLite CRLSet One. CRL 10. 08 MB / day 250 KB 34 KB 38
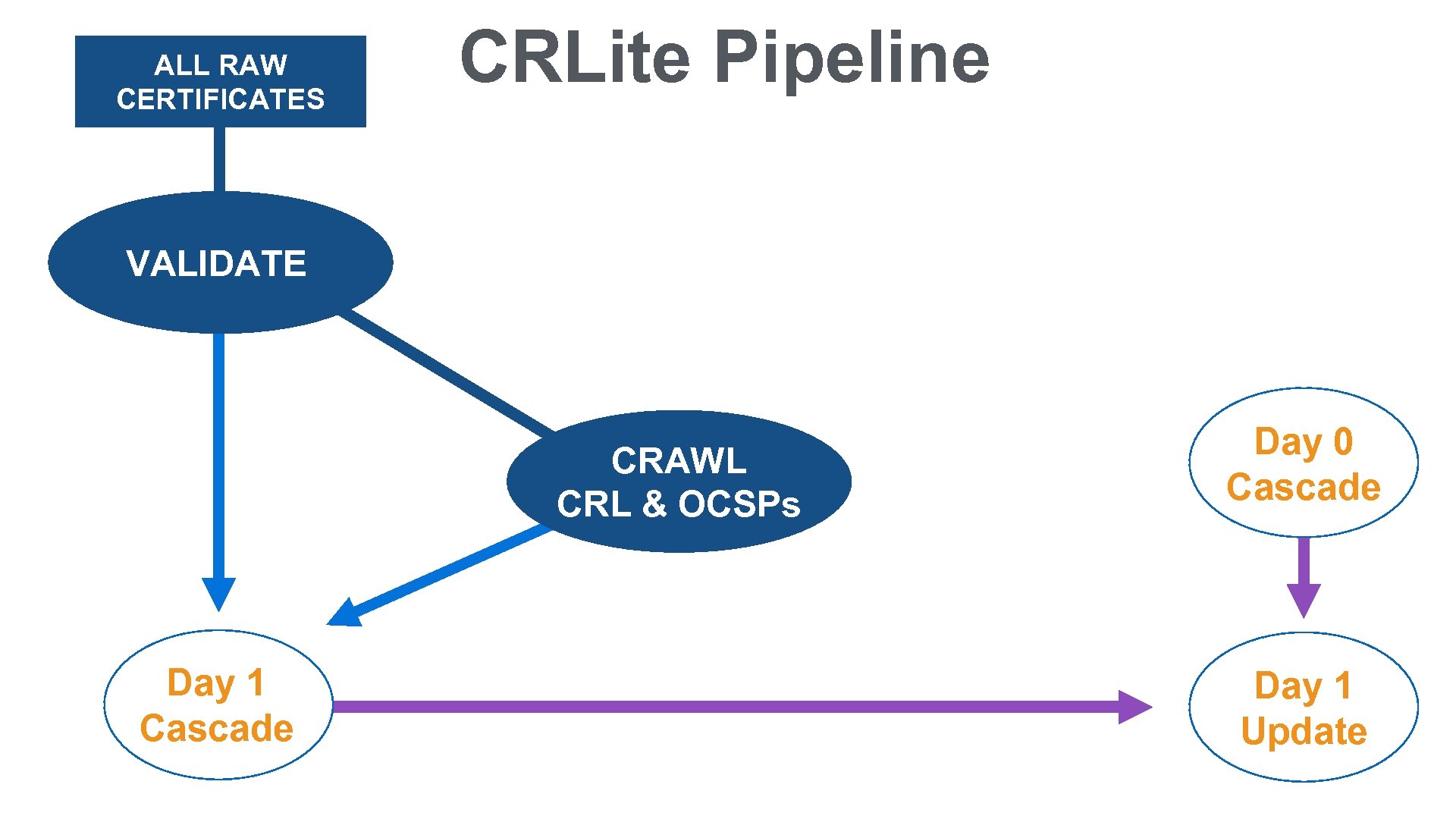
ALL RAW CERTIFICATES CRLite Pipeline VALIDATE CRAWL CRL & OCSPs Day 1 Cascade Day 0 Cascade Day 1 Update
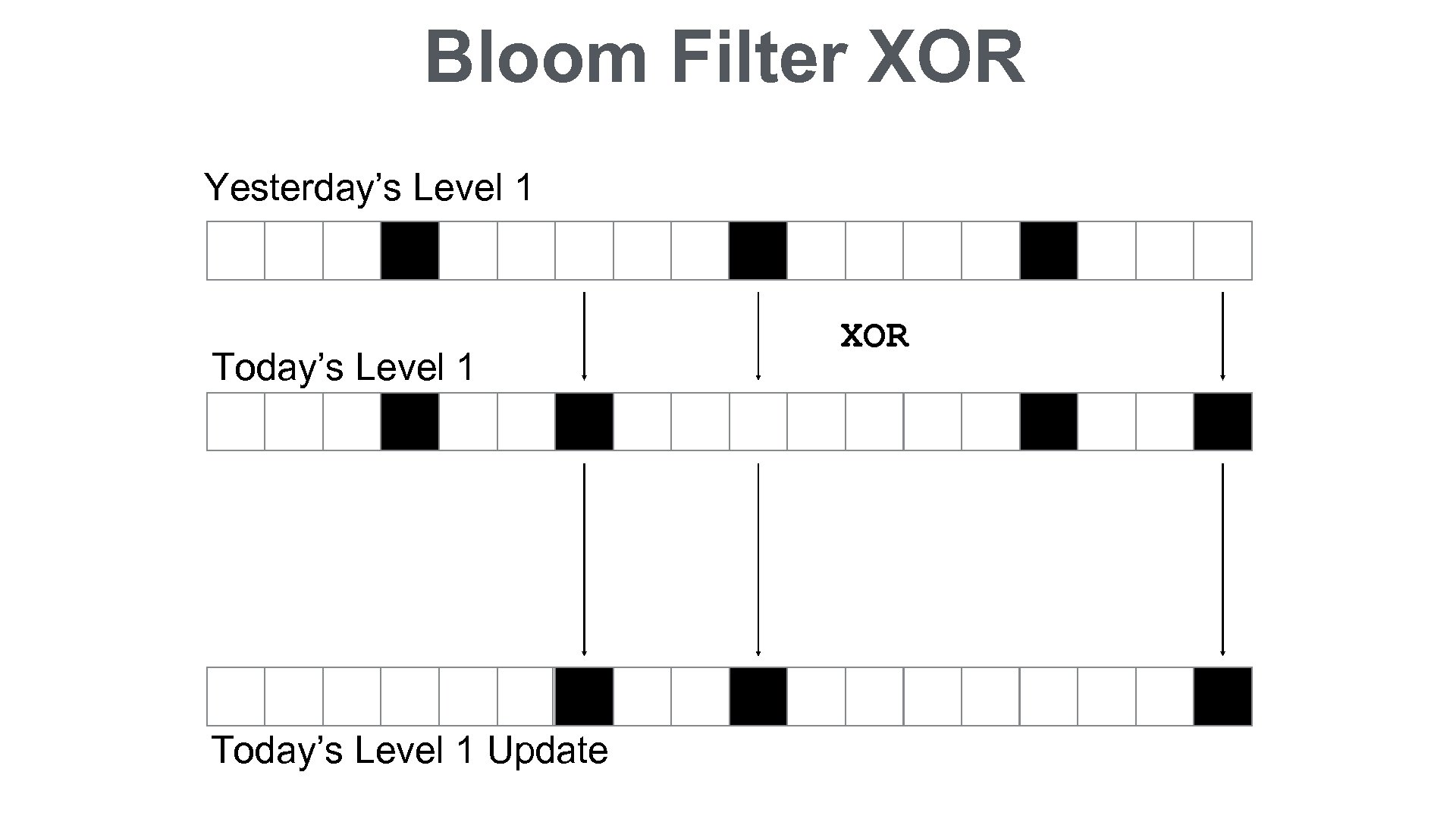
Bloom Filter XOR Yesterday’s Level 1 Today’s Level 1 Update XOR
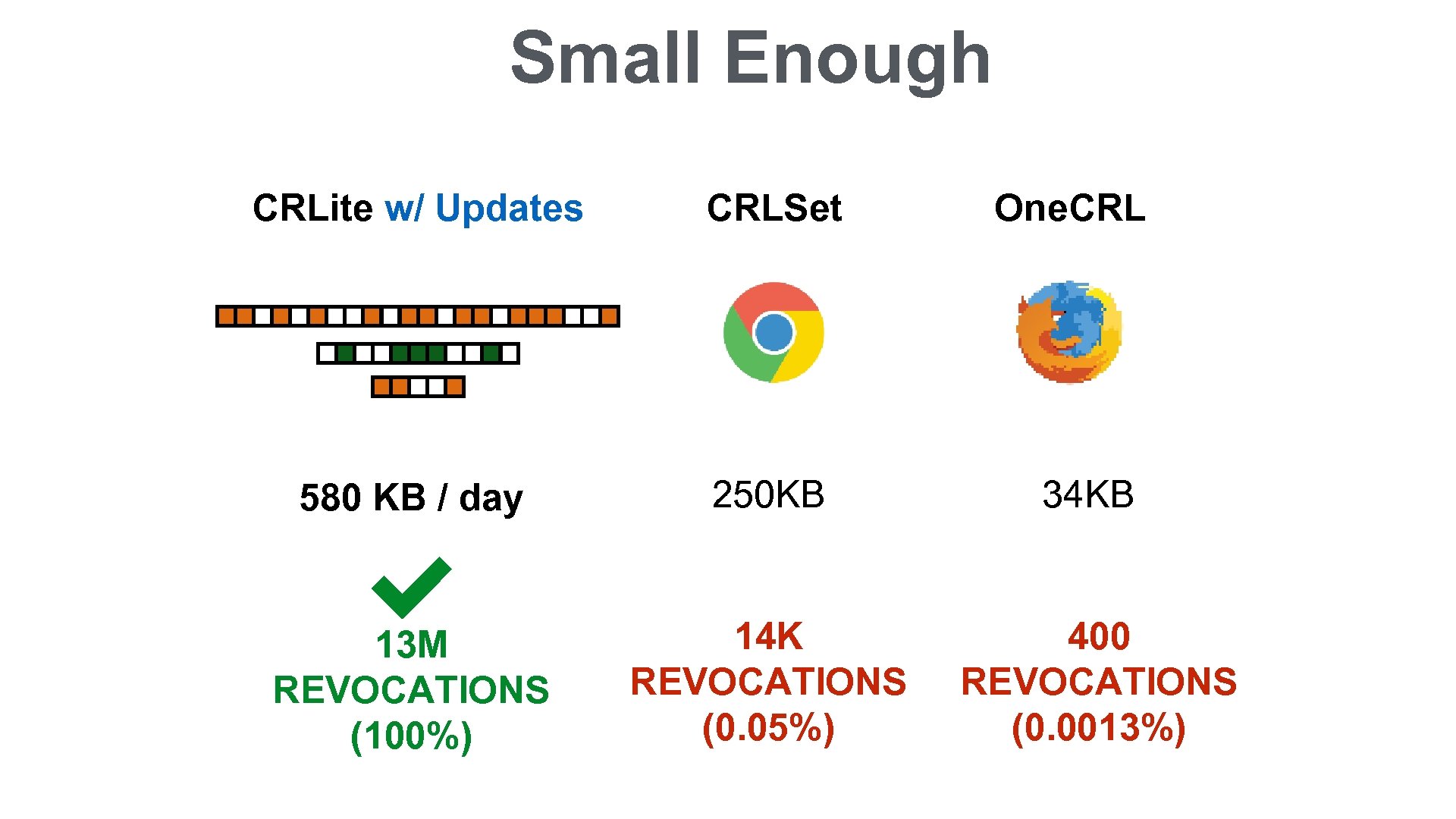
Small Enough CRLite w/ Updates CRLSet One. CRL 580 KB / day 250 KB 34 KB 13 M REVOCATIONS (100%) 14 K REVOCATIONS (0. 05%) 400 REVOCATIONS (0. 0013%)
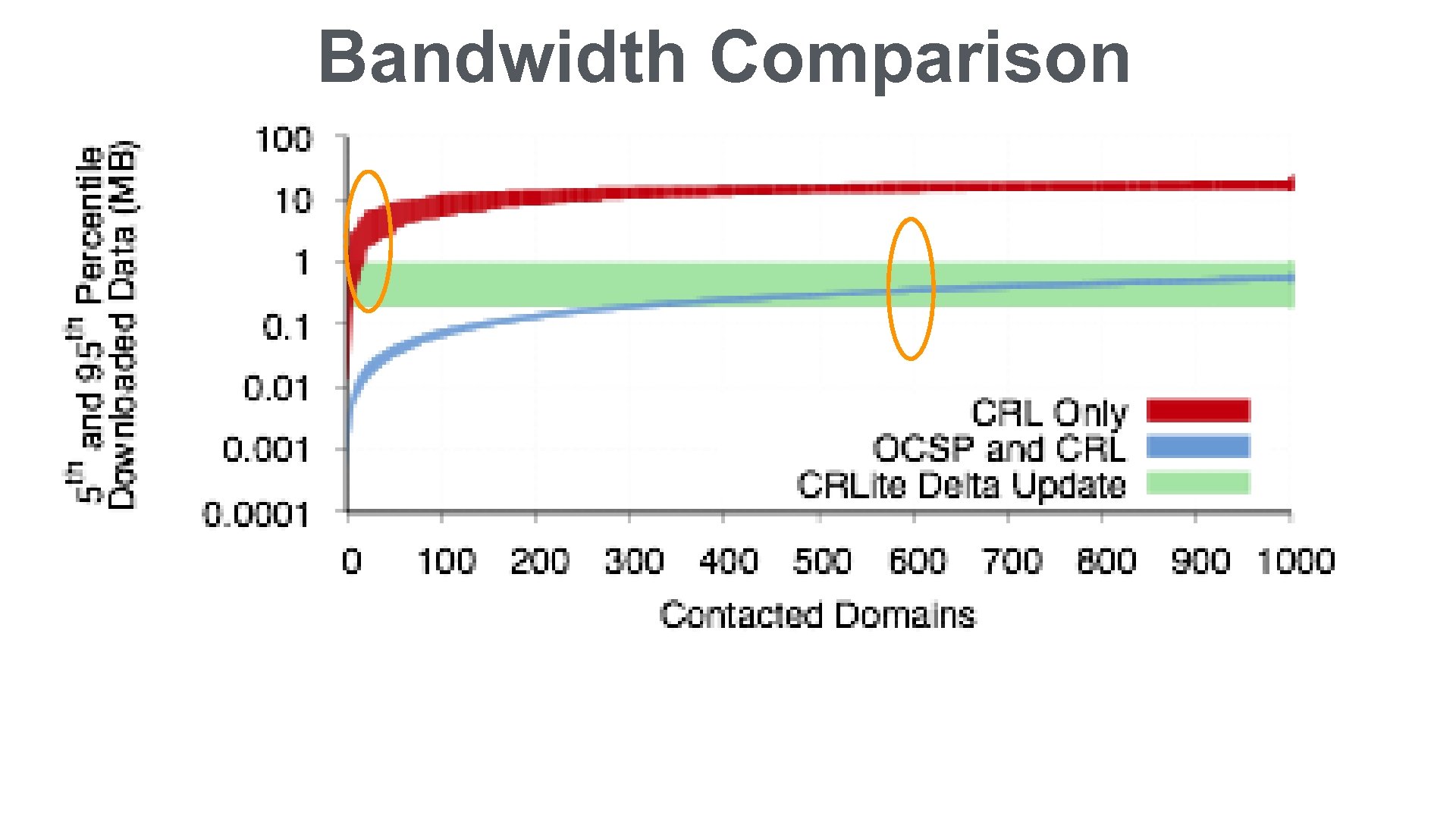
Bandwidth Comparison
Deployment We implemented CRLite as a Firefox extension. Initial discussion with Chrome developers was disappointing: we’ll wait for OCSP stapling Initial discussion with Mozilla developers: 580 KB/day per browser would be a lot of bandwidth for Mozilla to pay for. Perhaps certificate authorities would host their own updates?
1ca2ba5054bc1d3eca8a11139ece9c0c.ppt