725d8b072f7476caa4acc1769e285b86.ppt
- Количество слайдов: 13
 The UCSD Network Telescope A Real-time Monitoring System for Tracking Internet Attacks Stefan Savage David Moore, Geoff Voelker, and Colleen Shannon Department of Computer Science and Engineering & Cooperative Association for Internet Data Analysis (at SDSC) University of California, San Diego
The UCSD Network Telescope A Real-time Monitoring System for Tracking Internet Attacks Stefan Savage David Moore, Geoff Voelker, and Colleen Shannon Department of Computer Science and Engineering & Cooperative Association for Internet Data Analysis (at SDSC) University of California, San Diego
 Context • The Internet has an open communications model – Benefits: Flexible communication, application innovation – Drawbacks: Many opportunities for abuse • The Dark Side to the Internet – – Denial-of-Service Attacks Network Worms and Viruses Automated Scanning/Break-in Tools Etc… • Question: How big a problem is it really? Jacobs School of Engineering – Department of Computer Science and Engineering UCSD CSE COOPERATIVE ASSOCIATION FOR INTERNET DATA ANALYSIS
Context • The Internet has an open communications model – Benefits: Flexible communication, application innovation – Drawbacks: Many opportunities for abuse • The Dark Side to the Internet – – Denial-of-Service Attacks Network Worms and Viruses Automated Scanning/Break-in Tools Etc… • Question: How big a problem is it really? Jacobs School of Engineering – Department of Computer Science and Engineering UCSD CSE COOPERATIVE ASSOCIATION FOR INTERNET DATA ANALYSIS
 Media – “The sky is falling… every day” Jacobs School of Engineering – Department of Computer Science and Engineering UCSD CSE COOPERATIVE ASSOCIATION FOR INTERNET DATA ANALYSIS
Media – “The sky is falling… every day” Jacobs School of Engineering – Department of Computer Science and Engineering UCSD CSE COOPERATIVE ASSOCIATION FOR INTERNET DATA ANALYSIS
 Consulting Groups & Surveys • Consultancy estimates – “Losses … could total more than $1. 2 billion” - Yankee Group report on yr 2000 DDo. S attacks – Cost of Slammer worm $750 M-$1 B - Computer Economics report on yr 2000 DDo. S attacks - Others say numbers are different - Data source, methodology, error, biases unknown - Surveys - E. g. CSI/FBI survey reported 38% of respondents encountered Do. S activity in 2000 - Summary of anecdotes = good data? Jacobs School of Engineering – Department of Computer Science and Engineering UCSD CSE COOPERATIVE ASSOCIATION FOR INTERNET DATA ANALYSIS
Consulting Groups & Surveys • Consultancy estimates – “Losses … could total more than $1. 2 billion” - Yankee Group report on yr 2000 DDo. S attacks – Cost of Slammer worm $750 M-$1 B - Computer Economics report on yr 2000 DDo. S attacks - Others say numbers are different - Data source, methodology, error, biases unknown - Surveys - E. g. CSI/FBI survey reported 38% of respondents encountered Do. S activity in 2000 - Summary of anecdotes = good data? Jacobs School of Engineering – Department of Computer Science and Engineering UCSD CSE COOPERATIVE ASSOCIATION FOR INTERNET DATA ANALYSIS
 Why is this so hard? • Quantitative attack data isn’t available • Inherently hard to acquire – Few content or service providers collect such data – If they do, its usually considered sensitive • Infeasible to collect at Internet scale – How to monitor enough to the Internet to obtain a representative sample? – How to manage thousands of bilateral legal negotiations? • Data would be out of date as soon as collected Jacobs School of Engineering – Department of Computer Science and Engineering UCSD CSE COOPERATIVE ASSOCIATION FOR INTERNET DATA ANALYSIS
Why is this so hard? • Quantitative attack data isn’t available • Inherently hard to acquire – Few content or service providers collect such data – If they do, its usually considered sensitive • Infeasible to collect at Internet scale – How to monitor enough to the Internet to obtain a representative sample? – How to manage thousands of bilateral legal negotiations? • Data would be out of date as soon as collected Jacobs School of Engineering – Department of Computer Science and Engineering UCSD CSE COOPERATIVE ASSOCIATION FOR INTERNET DATA ANALYSIS
 Network Telescopes • A way to observe global network phenomena with only local monitoring • Key observation: large class of attacks use random addresses • Worm’s frequently select new host to infect at random • Many Do. S attacks hide their source by randomizing source addresses • Network Telescope – A monitor that records packets sent to a large range of unused Internet addresses – Since attacks are random, a telescope samples attacks Jacobs School of Engineering – Department of Computer Science and Engineering UCSD CSE COOPERATIVE ASSOCIATION FOR INTERNET DATA ANALYSIS
Network Telescopes • A way to observe global network phenomena with only local monitoring • Key observation: large class of attacks use random addresses • Worm’s frequently select new host to infect at random • Many Do. S attacks hide their source by randomizing source addresses • Network Telescope – A monitor that records packets sent to a large range of unused Internet addresses – Since attacks are random, a telescope samples attacks Jacobs School of Engineering – Department of Computer Science and Engineering UCSD CSE COOPERATIVE ASSOCIATION FOR INTERNET DATA ANALYSIS
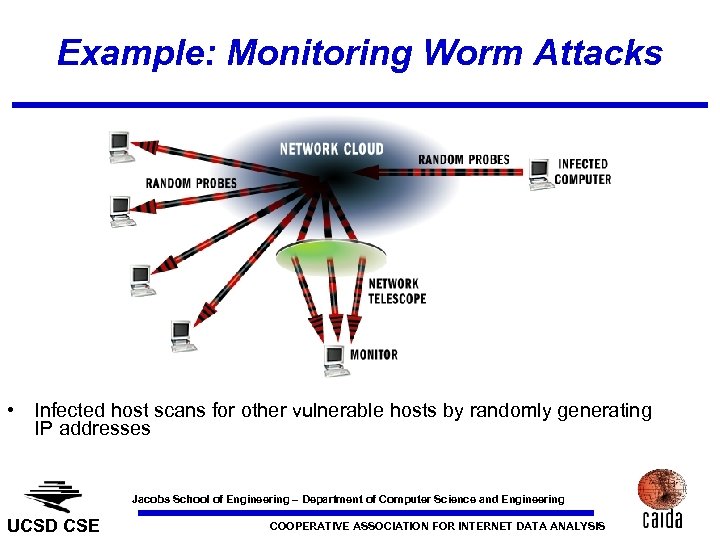 Example: Monitoring Worm Attacks • Infected host scans for other vulnerable hosts by randomly generating IP addresses Jacobs School of Engineering – Department of Computer Science and Engineering UCSD CSE COOPERATIVE ASSOCIATION FOR INTERNET DATA ANALYSIS
Example: Monitoring Worm Attacks • Infected host scans for other vulnerable hosts by randomly generating IP addresses Jacobs School of Engineering – Department of Computer Science and Engineering UCSD CSE COOPERATIVE ASSOCIATION FOR INTERNET DATA ANALYSIS
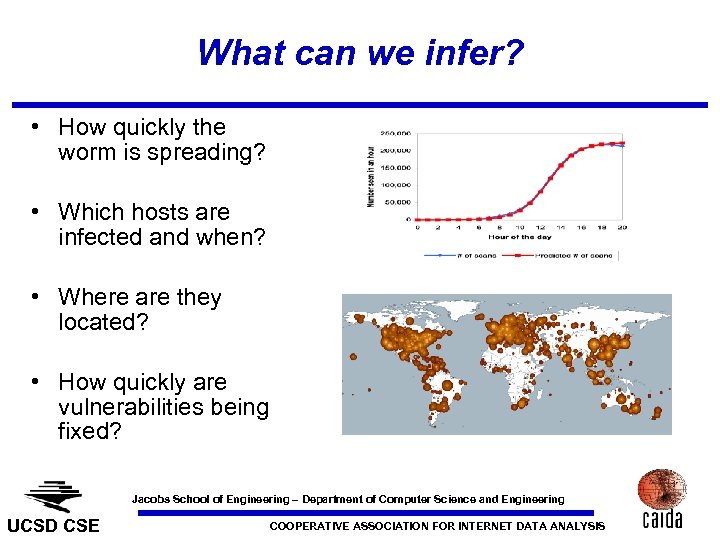 What can we infer? • How quickly the worm is spreading? • Which hosts are infected and when? • Where are they located? • How quickly are vulnerabilities being fixed? Jacobs School of Engineering – Department of Computer Science and Engineering UCSD CSE COOPERATIVE ASSOCIATION FOR INTERNET DATA ANALYSIS
What can we infer? • How quickly the worm is spreading? • Which hosts are infected and when? • Where are they located? • How quickly are vulnerabilities being fixed? Jacobs School of Engineering – Department of Computer Science and Engineering UCSD CSE COOPERATIVE ASSOCIATION FOR INTERNET DATA ANALYSIS
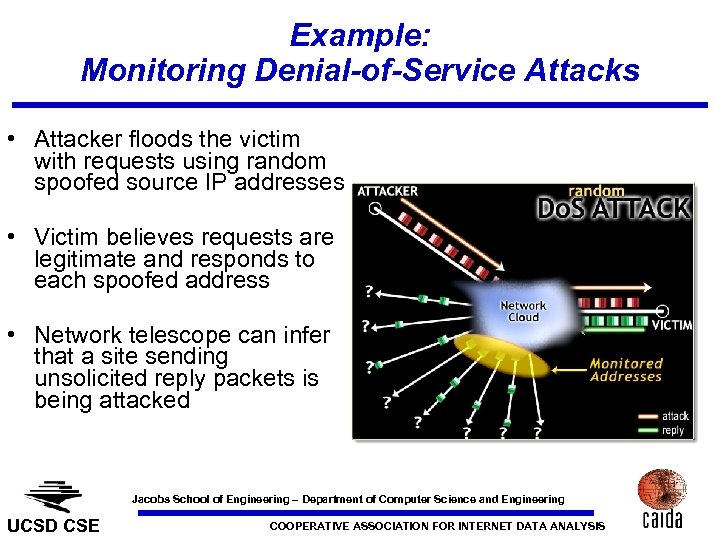 Example: Monitoring Denial-of-Service Attacks • Attacker floods the victim with requests using random spoofed source IP addresses • Victim believes requests are legitimate and responds to each spoofed address • Network telescope can infer that a site sending unsolicited reply packets is being attacked Jacobs School of Engineering – Department of Computer Science and Engineering UCSD CSE COOPERATIVE ASSOCIATION FOR INTERNET DATA ANALYSIS
Example: Monitoring Denial-of-Service Attacks • Attacker floods the victim with requests using random spoofed source IP addresses • Victim believes requests are legitimate and responds to each spoofed address • Network telescope can infer that a site sending unsolicited reply packets is being attacked Jacobs School of Engineering – Department of Computer Science and Engineering UCSD CSE COOPERATIVE ASSOCIATION FOR INTERNET DATA ANALYSIS
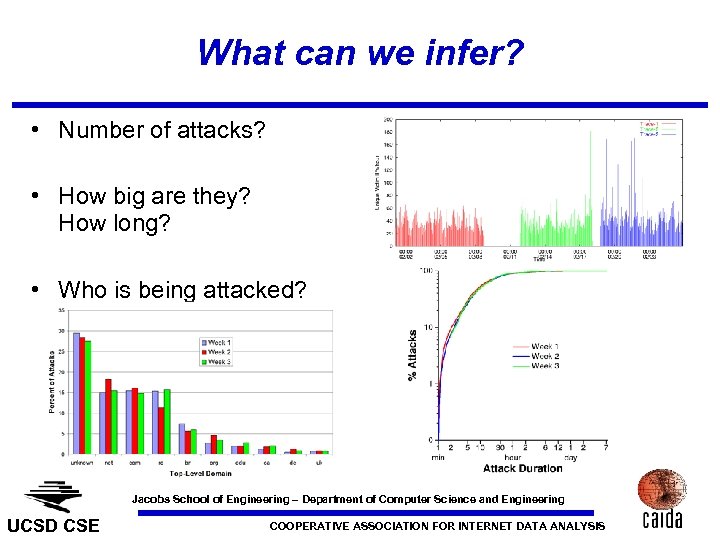 What can we infer? • Number of attacks? • How big are they? How long? • Who is being attacked? Jacobs School of Engineering – Department of Computer Science and Engineering UCSD CSE COOPERATIVE ASSOCIATION FOR INTERNET DATA ANALYSIS
What can we infer? • Number of attacks? • How big are they? How long? • Who is being attacked? Jacobs School of Engineering – Department of Computer Science and Engineering UCSD CSE COOPERATIVE ASSOCIATION FOR INTERNET DATA ANALYSIS
 What’s special about the UCSD Network Telescope? • Our Telescope is very large and size does matter – The more addresses monitored, the more accurate, quick and precise the results • We have access to more than 1/256 of all Internet addresses (> 16 M IP addresses) – Unprecedented insight into global attack activity – Can detect new attacks and worms in seconds with low error Special thanks to Jim Madden & Brian Kantor from UCSD Network Operations whose support makes this research possible Jacobs School of Engineering – Department of Computer Science and Engineering UCSD CSE COOPERATIVE ASSOCIATION FOR INTERNET DATA ANALYSIS
What’s special about the UCSD Network Telescope? • Our Telescope is very large and size does matter – The more addresses monitored, the more accurate, quick and precise the results • We have access to more than 1/256 of all Internet addresses (> 16 M IP addresses) – Unprecedented insight into global attack activity – Can detect new attacks and worms in seconds with low error Special thanks to Jim Madden & Brian Kantor from UCSD Network Operations whose support makes this research possible Jacobs School of Engineering – Department of Computer Science and Engineering UCSD CSE COOPERATIVE ASSOCIATION FOR INTERNET DATA ANALYSIS
 Summary • High quality global estimates on Internet security events (Worms, DDo. S) – ~4000 Do. S attacks per week; attacks on network infrastructure – Have observed worms spreading faster than 50 M hosts per second • Collecting ongoing longitudinal data set (20 GB/day) • Impact of data & methodology – Research: widely used in modeling network attacks and designing defenses – Operational Practice: identifies infected hosts and sites being attacked; variant of backscatter analysis now used by top ISPs – Policy: helps justify and prioritize resources appropriately Jacobs School of Engineering – Department of Computer Science and Engineering UCSD CSE COOPERATIVE ASSOCIATION FOR INTERNET DATA ANALYSIS
Summary • High quality global estimates on Internet security events (Worms, DDo. S) – ~4000 Do. S attacks per week; attacks on network infrastructure – Have observed worms spreading faster than 50 M hosts per second • Collecting ongoing longitudinal data set (20 GB/day) • Impact of data & methodology – Research: widely used in modeling network attacks and designing defenses – Operational Practice: identifies infected hosts and sites being attacked; variant of backscatter analysis now used by top ISPs – Policy: helps justify and prioritize resources appropriately Jacobs School of Engineering – Department of Computer Science and Engineering UCSD CSE COOPERATIVE ASSOCIATION FOR INTERNET DATA ANALYSIS
 Current Work • Network Honeyfarm – Cluster of dummy servers whose sole purpose is to be infected and observed – Collect detailed analysis of new attacks – Can be extended to capture non-random attacks (e. g. e -mail, instant messenger) which is weakness of telescope • Automated network defenses – Automatically detect, characterize and suppress new network attacks or outbreaks – Respond orders of magnitude more quickly humans can Jacobs School of Engineering – Department of Computer Science and Engineering UCSD CSE COOPERATIVE ASSOCIATION FOR INTERNET DATA ANALYSIS
Current Work • Network Honeyfarm – Cluster of dummy servers whose sole purpose is to be infected and observed – Collect detailed analysis of new attacks – Can be extended to capture non-random attacks (e. g. e -mail, instant messenger) which is weakness of telescope • Automated network defenses – Automatically detect, characterize and suppress new network attacks or outbreaks – Respond orders of magnitude more quickly humans can Jacobs School of Engineering – Department of Computer Science and Engineering UCSD CSE COOPERATIVE ASSOCIATION FOR INTERNET DATA ANALYSIS


