f2ef9acbc2ba669fc4765d54b85e06b7.ppt
- Количество слайдов: 24

 The Smart Software Symposium: Risk Management, Information Security & Corporate Governance Pierre G. Noel 3 rd of March 2009
The Smart Software Symposium: Risk Management, Information Security & Corporate Governance Pierre G. Noel 3 rd of March 2009
 Agenda The Globally Integrated Enterprise Key Security Trends IBM’s Point of View IBM Security Q&A 3
Agenda The Globally Integrated Enterprise Key Security Trends IBM’s Point of View IBM Security Q&A 3
 Global Crisis - What’s here, what’s ahead Layoffs Back Office, essentially Incidents Increase Internal External Regulators are back with a vengeance Vox Populi, Vox Deii Cost Reduction Conserve Cash Demonstrate financial prudence 4
Global Crisis - What’s here, what’s ahead Layoffs Back Office, essentially Incidents Increase Internal External Regulators are back with a vengeance Vox Populi, Vox Deii Cost Reduction Conserve Cash Demonstrate financial prudence 4
 Welcome to the smart planet… and a smarter infrastructure Globalization and Globally Available Resources Billions of mobile devices accessing the Web Access to streams of information in the Real Time New possibilities. New complexities. New risks. New Forms of Collaboration 5
Welcome to the smart planet… and a smarter infrastructure Globalization and Globally Available Resources Billions of mobile devices accessing the Web Access to streams of information in the Real Time New possibilities. New complexities. New risks. New Forms of Collaboration 5
 Managing risks introduced by new opportunities Emerging technology Virtualization and cloud computing increase infrastructure complexity. Web 2. 0 and SOA style composite applications introduce new challenges with the applications being a vulnerable point for breaches and attack. Data and information explosion Data volumes are doubling every 18 months. * Storage, security, and discovery around information context is becoming increasingly important. Wireless world Mobile platforms are developing as new means of identification. Security technology is many years behind the security used to protect PCs. Supply chain The chain is only as strong as the weakest link… partners need to shoulder their fair share of the load for compliance and the responsibility for failure. Clients expect privacy An assumption or expectation now exists to integrate security into the infrastructure, processes and applications to maintain privacy. Compliance fatigue Organizations are trying to maintain a balance between investing in both the security and compliance postures. *Source: Pyramid Research, October 2007
Managing risks introduced by new opportunities Emerging technology Virtualization and cloud computing increase infrastructure complexity. Web 2. 0 and SOA style composite applications introduce new challenges with the applications being a vulnerable point for breaches and attack. Data and information explosion Data volumes are doubling every 18 months. * Storage, security, and discovery around information context is becoming increasingly important. Wireless world Mobile platforms are developing as new means of identification. Security technology is many years behind the security used to protect PCs. Supply chain The chain is only as strong as the weakest link… partners need to shoulder their fair share of the load for compliance and the responsibility for failure. Clients expect privacy An assumption or expectation now exists to integrate security into the infrastructure, processes and applications to maintain privacy. Compliance fatigue Organizations are trying to maintain a balance between investing in both the security and compliance postures. *Source: Pyramid Research, October 2007
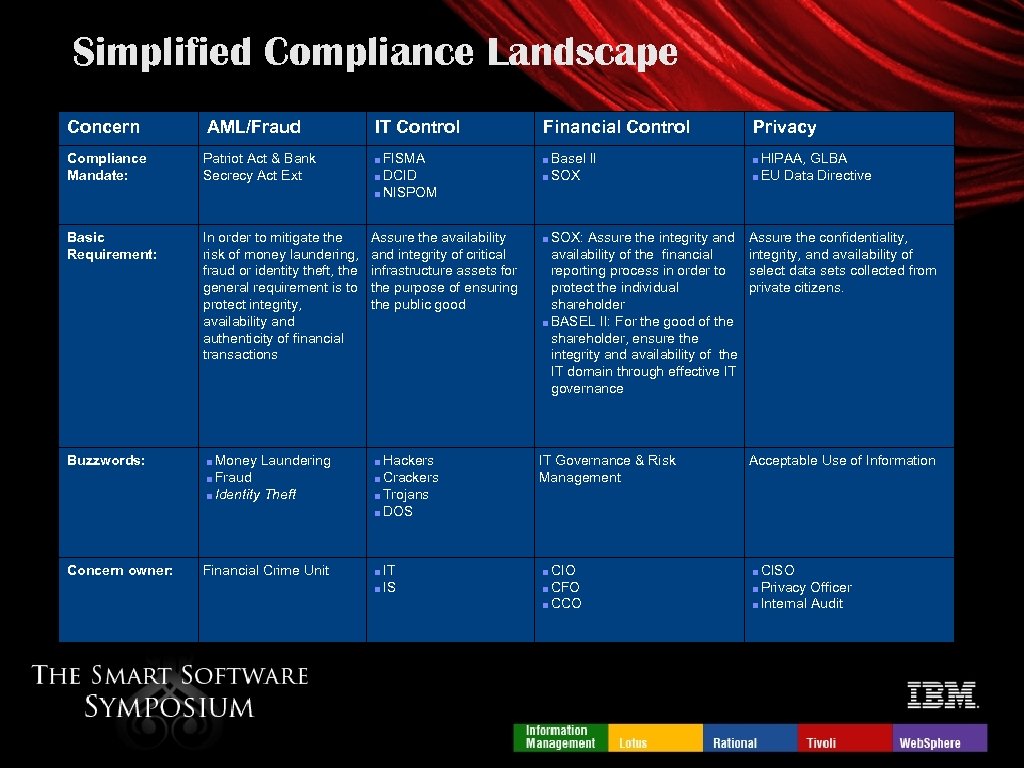 Simplified Compliance Landscape Concern AML/Fraud IT Control Financial Control Privacy Compliance Mandate: Patriot Act & Bank Secrecy Act Ext ■ FISMA ■ DCID ■ NISPOM ■ Basel II ■ SOX ■ HIPAA, GLBA ■ EU Data Directive Basic Requirement: In order to mitigate the risk of money laundering, fraud or identity theft, the general requirement is to protect integrity, availability and authenticity of financial transactions Assure the availability and integrity of critical infrastructure assets for the purpose of ensuring the public good ■ SOX: Assure the integrity and Assure the confidentiality, integrity, and availability of select data sets collected from private citizens. Buzzwords: ■ Money Laundering ■ Fraud ■ Identity Theft ■ Hackers ■ Crackers ■ Trojans ■ DOS IT Governance & Risk Management Acceptable Use of Information Concern owner: Financial Crime Unit ■ IT ■ IS ■ CIO ■ CFO ■ CCO ■ CISO ■ Privacy Officer ■ Internal Audit availability of the financial reporting process in order to protect the individual shareholder ■ BASEL II: For the good of the shareholder, ensure the integrity and availability of the IT domain through effective IT governance
Simplified Compliance Landscape Concern AML/Fraud IT Control Financial Control Privacy Compliance Mandate: Patriot Act & Bank Secrecy Act Ext ■ FISMA ■ DCID ■ NISPOM ■ Basel II ■ SOX ■ HIPAA, GLBA ■ EU Data Directive Basic Requirement: In order to mitigate the risk of money laundering, fraud or identity theft, the general requirement is to protect integrity, availability and authenticity of financial transactions Assure the availability and integrity of critical infrastructure assets for the purpose of ensuring the public good ■ SOX: Assure the integrity and Assure the confidentiality, integrity, and availability of select data sets collected from private citizens. Buzzwords: ■ Money Laundering ■ Fraud ■ Identity Theft ■ Hackers ■ Crackers ■ Trojans ■ DOS IT Governance & Risk Management Acceptable Use of Information Concern owner: Financial Crime Unit ■ IT ■ IS ■ CIO ■ CFO ■ CCO ■ CISO ■ Privacy Officer ■ Internal Audit availability of the financial reporting process in order to protect the individual shareholder ■ BASEL II: For the good of the shareholder, ensure the integrity and availability of the IT domain through effective IT governance
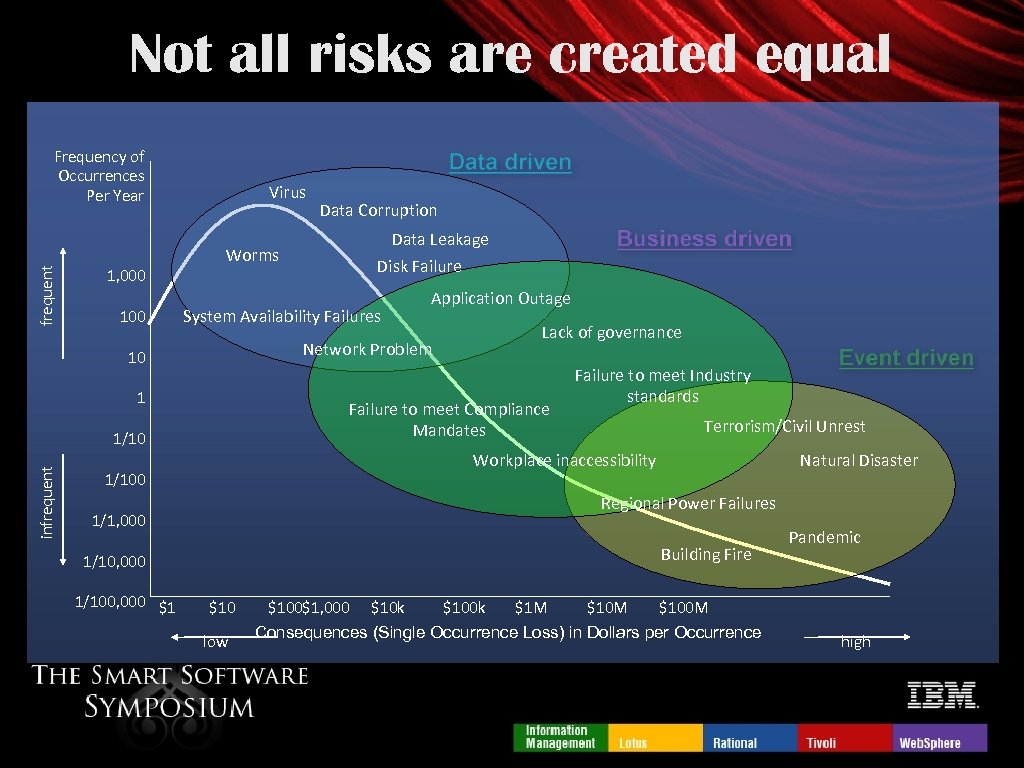 Not all risks are created equal frequent Frequency of Occurrences Per Year 1, 000 100 Virus Data Leakage Disk Failure Worms System Availability Failures Application Outage Lack of governance Network Problem 10 1 Failure to meet Compliance Mandates 1/10 infrequent Data Corruption Failure to meet Industry standards Terrorism/Civil Unrest Workplace inaccessibility 1/100 Regional Power Failures 1/1, 000 Building Fire 1/10, 000 1/100, 000 $1 Natural Disaster $10 low $100$1, 000 $10 k $100 k $1 M $10 M Pandemic $100 M Consequences (Single Occurrence Loss) in Dollars per Occurrence high
Not all risks are created equal frequent Frequency of Occurrences Per Year 1, 000 100 Virus Data Leakage Disk Failure Worms System Availability Failures Application Outage Lack of governance Network Problem 10 1 Failure to meet Compliance Mandates 1/10 infrequent Data Corruption Failure to meet Industry standards Terrorism/Civil Unrest Workplace inaccessibility 1/100 Regional Power Failures 1/1, 000 Building Fire 1/10, 000 1/100, 000 $1 Natural Disaster $10 low $100$1, 000 $10 k $100 k $1 M $10 M Pandemic $100 M Consequences (Single Occurrence Loss) in Dollars per Occurrence high
 Customers Tell Us They Suffer From “Fatigue”… Complexity and confusion keep customers from acting strategically: Extended relationships create a tangle of potential legal liability Compliance requirements are inconsistent within and across geographies Confusion as to where to start, how much security & compliance control is “good enough” Pressure to simply “check the box” has resulted in creation of compliance silos: Silos lead to duplicative efforts and redundant spending as well as reduced visibility The CSO struggles to become a consultant to the business: Without a policy centric, risk based view, this is nearly impossible
Customers Tell Us They Suffer From “Fatigue”… Complexity and confusion keep customers from acting strategically: Extended relationships create a tangle of potential legal liability Compliance requirements are inconsistent within and across geographies Confusion as to where to start, how much security & compliance control is “good enough” Pressure to simply “check the box” has resulted in creation of compliance silos: Silos lead to duplicative efforts and redundant spending as well as reduced visibility The CSO struggles to become a consultant to the business: Without a policy centric, risk based view, this is nearly impossible
 Top IT General Control Deficiencies Classification: Failure to provide an inventory of assets and associated data classifications Change Management: Failure to produce evidence of change mgmt on material systems. Administrative Accounts: The organization does not tie administrative ("root") accounts to specific individuals. Identity Management: The organization cannot show documentation of each user's privilege, or determine that each user has appropriate approved privilege. Log Management: The organization can produce no evidence of log collection and analysis. Segregation of Duties: The organization fails to appropriately segregate duties Physical Access: Physical access to the data center is not appropriately controlled BCDR: The organization has no documented, current, relevant business continuity and/or disaster recovery plan, nor evidence of internal controls requiring the periodic updating and review of such plans Chain of Custody: The organization's agreements (contracts, MSAs, SLAs) with business partners and third-party service providers do not specifically address data protection requirements. Training & Awareness: The organization can produce no evidence that employees know and understand corporate information security policies *Source: Publication Date: 2 October 2007/ID Number: G 0015216 10 © 2009 IBM Corporation
Top IT General Control Deficiencies Classification: Failure to provide an inventory of assets and associated data classifications Change Management: Failure to produce evidence of change mgmt on material systems. Administrative Accounts: The organization does not tie administrative ("root") accounts to specific individuals. Identity Management: The organization cannot show documentation of each user's privilege, or determine that each user has appropriate approved privilege. Log Management: The organization can produce no evidence of log collection and analysis. Segregation of Duties: The organization fails to appropriately segregate duties Physical Access: Physical access to the data center is not appropriately controlled BCDR: The organization has no documented, current, relevant business continuity and/or disaster recovery plan, nor evidence of internal controls requiring the periodic updating and review of such plans Chain of Custody: The organization's agreements (contracts, MSAs, SLAs) with business partners and third-party service providers do not specifically address data protection requirements. Training & Awareness: The organization can produce no evidence that employees know and understand corporate information security policies *Source: Publication Date: 2 October 2007/ID Number: G 0015216 10 © 2009 IBM Corporation
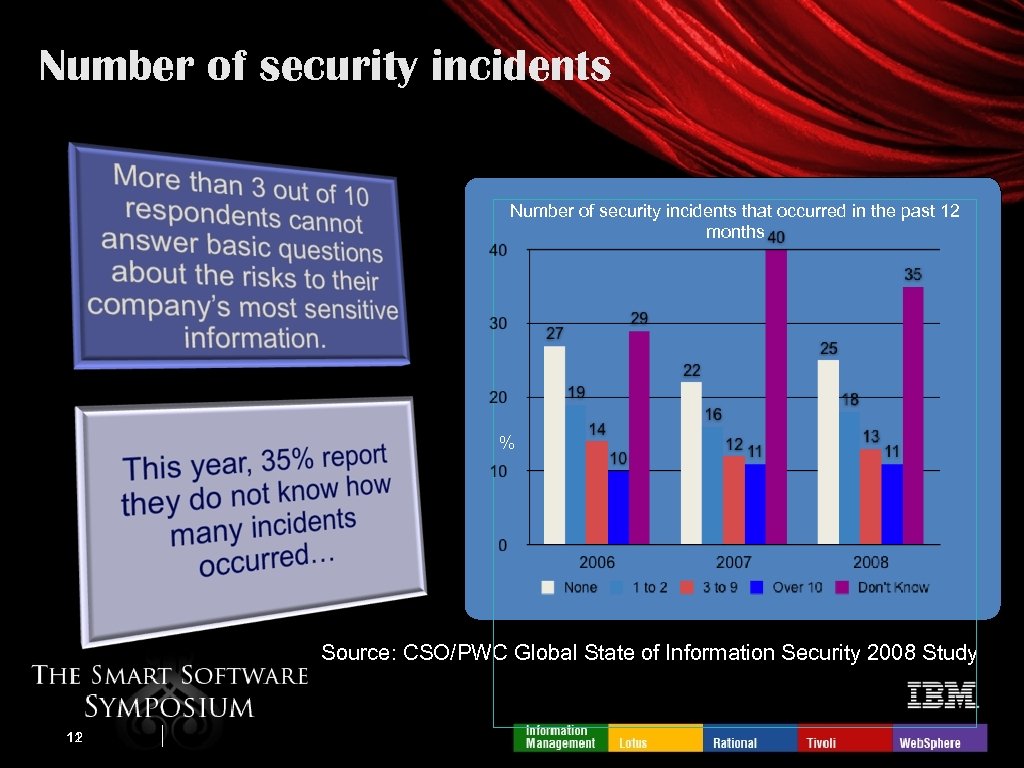 Number of security incidents that occurred in the past 12 months % Source: CSO/PWC Global State of Information Security 2008 Study 11 12
Number of security incidents that occurred in the past 12 months % Source: CSO/PWC Global State of Information Security 2008 Study 11 12
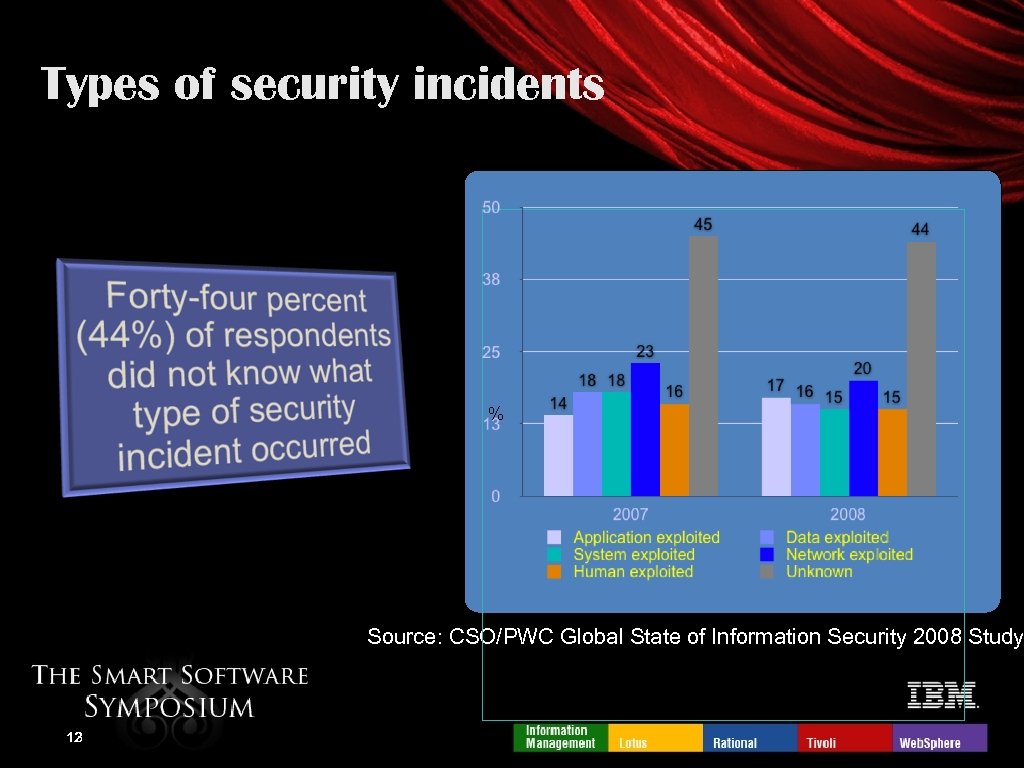 Types of security incidents % Source: CSO/PWC Global State of Information Security 2008 Study 12 13
Types of security incidents % Source: CSO/PWC Global State of Information Security 2008 Study 12 13
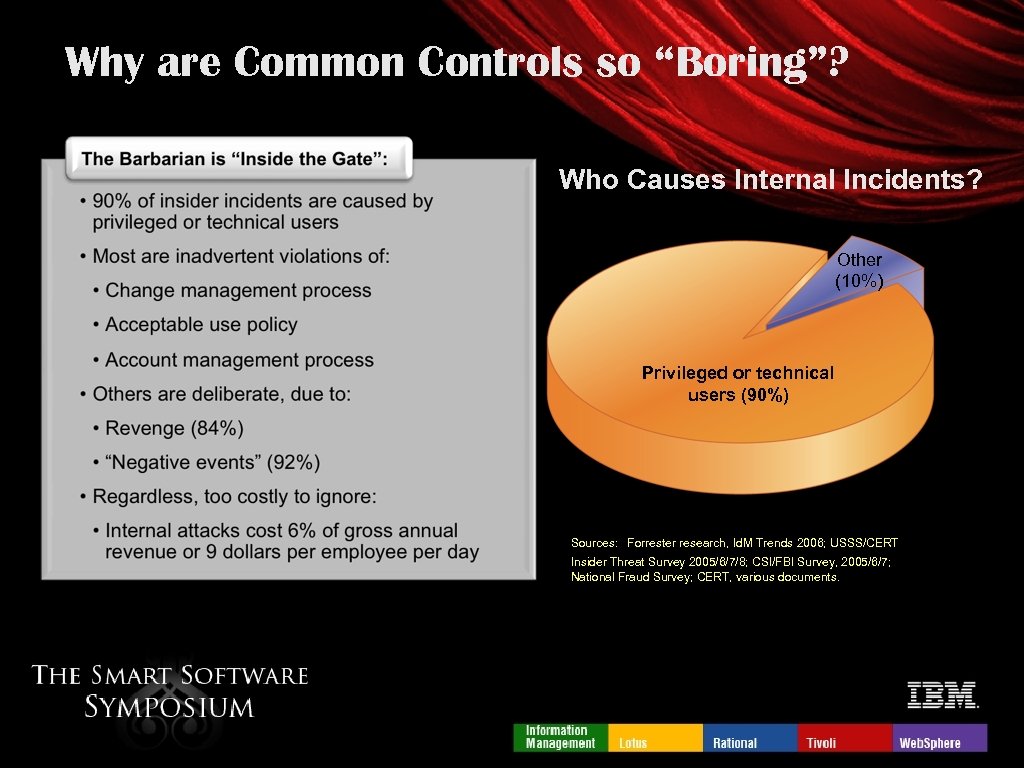 Why are Common Controls so “Boring”? Who Causes Internal Incidents? Other (10%) Privileged or technical users (90%) Sources: Forrester research, Id. M Trends 2006; USSS/CERT Insider Threat Survey 2005/6/7/8; CSI/FBI Survey, 2005/6/7; National Fraud Survey; CERT, various documents.
Why are Common Controls so “Boring”? Who Causes Internal Incidents? Other (10%) Privileged or technical users (90%) Sources: Forrester research, Id. M Trends 2006; USSS/CERT Insider Threat Survey 2005/6/7/8; CSI/FBI Survey, 2005/6/7; National Fraud Survey; CERT, various documents.
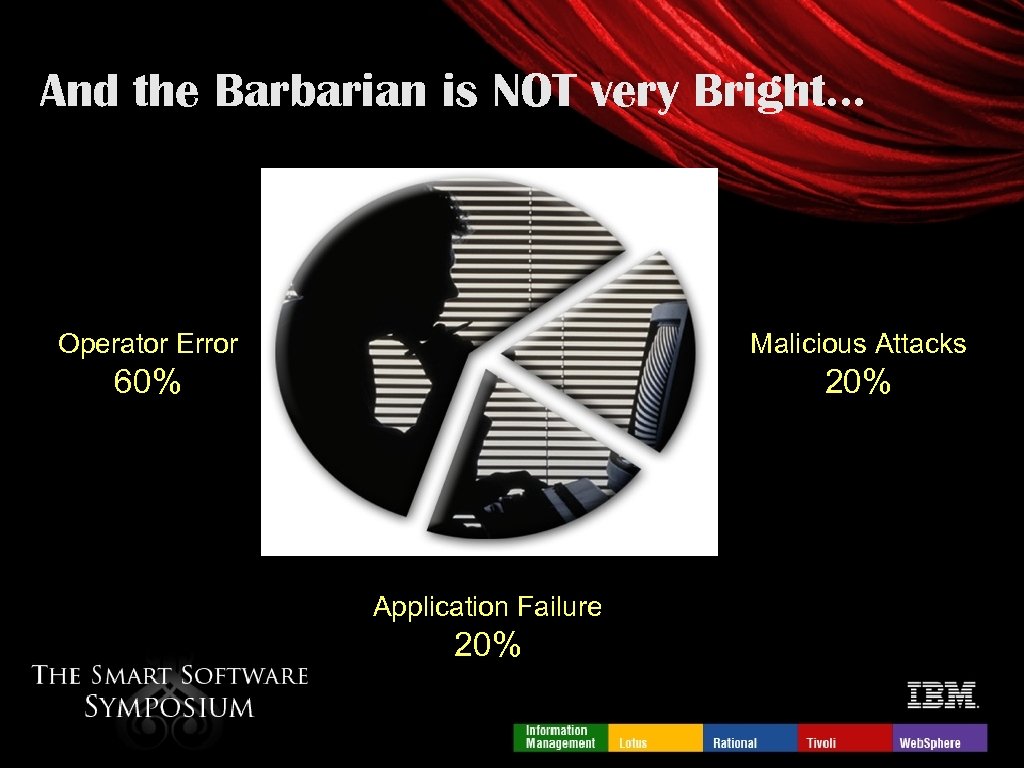 And the Barbarian is NOT very Bright… Operator Error Malicious Attacks 60% 20% Application Failure 20%
And the Barbarian is NOT very Bright… Operator Error Malicious Attacks 60% 20% Application Failure 20%
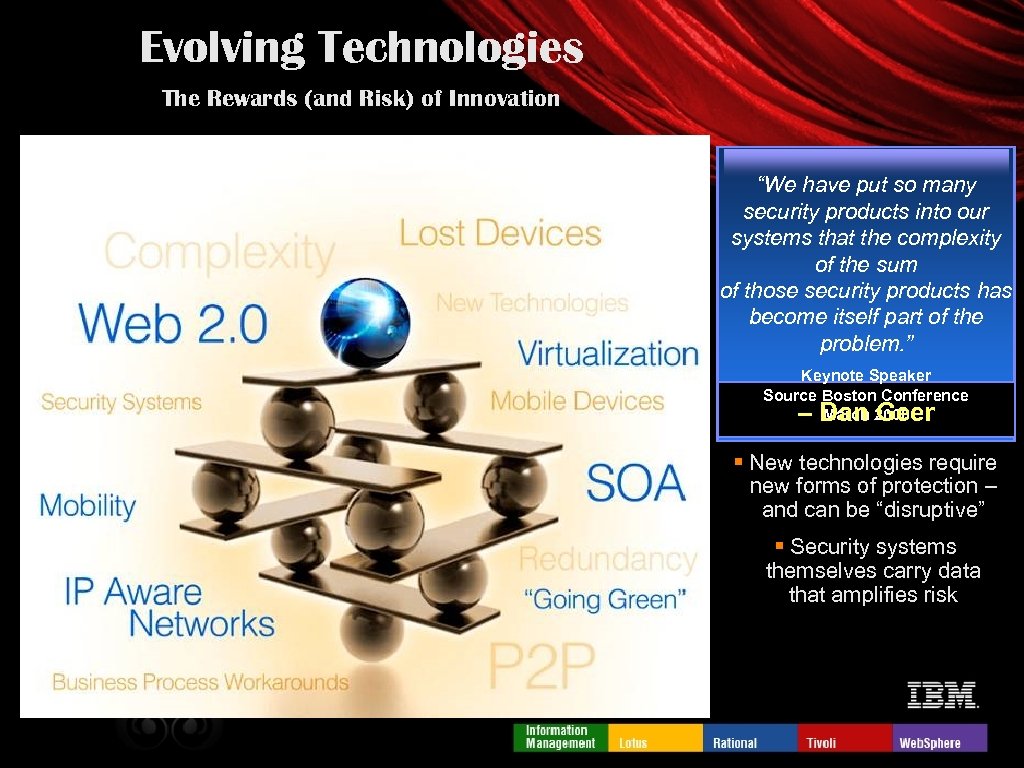 Evolving Technologies The Rewards (and Risk) of Innovation “We have put so many security products into our systems that the complexity of the sum of those security products has become itself part of the problem. ” Keynote Speaker Source Boston Conference March 2008 – Dan Geer § New technologies require new forms of protection – and can be “disruptive” § Security systems themselves carry data that amplifies risk
Evolving Technologies The Rewards (and Risk) of Innovation “We have put so many security products into our systems that the complexity of the sum of those security products has become itself part of the problem. ” Keynote Speaker Source Boston Conference March 2008 – Dan Geer § New technologies require new forms of protection – and can be “disruptive” § Security systems themselves carry data that amplifies risk
 Security foundation…critical controls pave the way Critical Control Description Manage Identity & Access Process for assuring access to enterprise resources has been given to the right people, at the right time Protect Data & Information Capability that allows for granular protection of both unstructured and structured data, as well as leak prevention & acceptable use policy monitoring. Manage SW & Application Releases Process for assuring efficiency and integrity of the software development lifecycle Manage Change & Configuration Process for assuring routine, emergency and out-of-band changes are made efficiently, and in such a manner as to prevent operational outages. Address Threat & Vulnerability Process and capabilities designed to protect the enterprise infrastructure from new and emerging threats Manage Security Event Log management capabilities designed to automate the process of auditing, monitoring and reporting on security and compliance posture across the enterprise Manage Problem & Incident Automated workflow and Service Desk designed to assure incidents are escalated and addressed in a timely manner. Forensics teams ready to respond to an emergency
Security foundation…critical controls pave the way Critical Control Description Manage Identity & Access Process for assuring access to enterprise resources has been given to the right people, at the right time Protect Data & Information Capability that allows for granular protection of both unstructured and structured data, as well as leak prevention & acceptable use policy monitoring. Manage SW & Application Releases Process for assuring efficiency and integrity of the software development lifecycle Manage Change & Configuration Process for assuring routine, emergency and out-of-band changes are made efficiently, and in such a manner as to prevent operational outages. Address Threat & Vulnerability Process and capabilities designed to protect the enterprise infrastructure from new and emerging threats Manage Security Event Log management capabilities designed to automate the process of auditing, monitoring and reporting on security and compliance posture across the enterprise Manage Problem & Incident Automated workflow and Service Desk designed to assure incidents are escalated and addressed in a timely manner. Forensics teams ready to respond to an emergency
 PEOPLE AND IDENTITY Issues Manage Identities and Access § Understanding the identity risk gap § Cost of administering users and identities in-house § Privileged user activity unmonitored § Dormant IDs or shared identities being used to inappropriately access resources § Failing an audit IBM Security Offerings § Identity Lifecycle Management: Tivoli Identity and Access Management solutions, § High-Assurance Digital Identities: Trusted Identity Initiative § Identity Audit: Tivoli Security Compliance Insight Manager, Tivoli z. Secure Audit § Identity & Access Design and Implementation Services § ISS Managed Identity Services § GBS Security Services “How can my business benefit from management of digital identity? ” Values § Reduces the cost, increases efficiency and enables audit-ability of managing flow of users entering, using, and leaving the organization § Decreases risk of internal fraud, data leak, or operational outage § Supports globalization of operations § Enables shift from traditional brick & mortar sales to delivery of on-line services to customers and partners across the globe § Improves end-user experience with Web-based business applications by enabling such activities such as single sign-on
PEOPLE AND IDENTITY Issues Manage Identities and Access § Understanding the identity risk gap § Cost of administering users and identities in-house § Privileged user activity unmonitored § Dormant IDs or shared identities being used to inappropriately access resources § Failing an audit IBM Security Offerings § Identity Lifecycle Management: Tivoli Identity and Access Management solutions, § High-Assurance Digital Identities: Trusted Identity Initiative § Identity Audit: Tivoli Security Compliance Insight Manager, Tivoli z. Secure Audit § Identity & Access Design and Implementation Services § ISS Managed Identity Services § GBS Security Services “How can my business benefit from management of digital identity? ” Values § Reduces the cost, increases efficiency and enables audit-ability of managing flow of users entering, using, and leaving the organization § Decreases risk of internal fraud, data leak, or operational outage § Supports globalization of operations § Enables shift from traditional brick & mortar sales to delivery of on-line services to customers and partners across the globe § Improves end-user experience with Web-based business applications by enabling such activities such as single sign-on
 DATA AND INFORMATION Issues Protect Data and Information “How can I reduce the cost and pain associated with tracking and controlling who touched what data when? How do I assure that my data is available to the business, today and tomorrow? ” § Data stored on removable media that can be lost/stolen § Data stored in the clear is easily accessible § Inconsistent data policies § Unstructured data § Legal, regulatory and ethical exposure for the organization § Costs of data breaches, notification, brand value § Failing an audit IBM Security Offerings § ISS Data Security and Data Loss Prevention solution § SIEM: Tivoli Compliance Insight Manager, ISS Site. Protector, ISS Managed Security Services § Data Encryption: Tivoli Key Lifecycle Manager, encrypted tape and disk drives § Data Classification: Info. Sphere Information Analyzer, Cognos, Enterprise Content Management, Discovery and Classification § Unstructured Data Security: Tivoli Access Manager § Data Privacy and Masking: Optim Data Privacy Solution § GBS Security Services Values § Reduces the cost, increases ability to meet audit and compliance mandates § Provides a cost-effective way to meet legal discovery, hold and retention requirements § Assures data is available to the right people, at the right time § Assures data is not deliberately or inadvertently taken, leaked, or damaged § Decreases number and complexity of controls integrated within the enterprise
DATA AND INFORMATION Issues Protect Data and Information “How can I reduce the cost and pain associated with tracking and controlling who touched what data when? How do I assure that my data is available to the business, today and tomorrow? ” § Data stored on removable media that can be lost/stolen § Data stored in the clear is easily accessible § Inconsistent data policies § Unstructured data § Legal, regulatory and ethical exposure for the organization § Costs of data breaches, notification, brand value § Failing an audit IBM Security Offerings § ISS Data Security and Data Loss Prevention solution § SIEM: Tivoli Compliance Insight Manager, ISS Site. Protector, ISS Managed Security Services § Data Encryption: Tivoli Key Lifecycle Manager, encrypted tape and disk drives § Data Classification: Info. Sphere Information Analyzer, Cognos, Enterprise Content Management, Discovery and Classification § Unstructured Data Security: Tivoli Access Manager § Data Privacy and Masking: Optim Data Privacy Solution § GBS Security Services Values § Reduces the cost, increases ability to meet audit and compliance mandates § Provides a cost-effective way to meet legal discovery, hold and retention requirements § Assures data is available to the right people, at the right time § Assures data is not deliberately or inadvertently taken, leaked, or damaged § Decreases number and complexity of controls integrated within the enterprise
 APPLICATION AND PROCESS Issues § Web applications #1 target of hackers seeking to exploit Secure Web Applications “How can my business benefit from management of application security? ” vulnerabilities § Applications are deployed with vulnerabilities § Poor security configs expose clients to business loss § PCI regulatory requirements mandate application security § 80% of development costs spent on identifying and fixing defects § Real and/or private data exposed to anyone with access to development and test environments, including contractors and outsourcers IBM Security Offerings § Application Vulnerabilities: Rational App. Scan, ISS Managed Security Services, ISS Application Risk Assessment services § Application Access Controls: Tivoli Access Manager § Messaging Security: Lotus Domino Messaging, IBM ISS Mail security solutions § Security for SOA: Web. Sphere Data. Power, Tivoli Security Policy Manager, Tivoli Federated Identity Manager § Application Security Assessment services § GBS Security Services Values § Reduce risk of outage, defacement or data theft associated with web applications § Assess and monitor enterprise-wide security policy compliance § Improve compliance with industry standards and regulatory requirements (e. g. , PCI, GLBA, HIPAA, FISMA…) § Improve ability to integrate business critical applications § Automated testing and governance throughout the development lifecycle, reducing long-term security costs
APPLICATION AND PROCESS Issues § Web applications #1 target of hackers seeking to exploit Secure Web Applications “How can my business benefit from management of application security? ” vulnerabilities § Applications are deployed with vulnerabilities § Poor security configs expose clients to business loss § PCI regulatory requirements mandate application security § 80% of development costs spent on identifying and fixing defects § Real and/or private data exposed to anyone with access to development and test environments, including contractors and outsourcers IBM Security Offerings § Application Vulnerabilities: Rational App. Scan, ISS Managed Security Services, ISS Application Risk Assessment services § Application Access Controls: Tivoli Access Manager § Messaging Security: Lotus Domino Messaging, IBM ISS Mail security solutions § Security for SOA: Web. Sphere Data. Power, Tivoli Security Policy Manager, Tivoli Federated Identity Manager § Application Security Assessment services § GBS Security Services Values § Reduce risk of outage, defacement or data theft associated with web applications § Assess and monitor enterprise-wide security policy compliance § Improve compliance with industry standards and regulatory requirements (e. g. , PCI, GLBA, HIPAA, FISMA…) § Improve ability to integrate business critical applications § Automated testing and governance throughout the development lifecycle, reducing long-term security costs
 NETWORK, SERVER AND END POINT Issues § Mass commercialization and automation of threats § Parasitic, stealthier, more damaging attacks § Poor understanding of risks in new technologies and Manage Infrastructure Security applications, including virtualization and cloud § Weak application controls § Lack of skills to monitor and manage security inputs § Compounding cost of managing an ever increasing array of security technologies § Undetected breaches due to privilege access misuse and downtime from incidents § Inability to establish forensic evidence or demonstrate compliance IBM Security Offerings § Threat Mitigation: ISS Network, Server and Endpoint Intrusion ® Detection and Prevention products powered by X-Force , Managed Intrusion Prevention and Detection, Network Mail Security, Managed firewall services, Vulnerability Management and Scanning § SIEM: Tivoli Compliance Insight Manager, Security Event and Log Management services § Security Governance: Regulatory assessments and remediation solutions, Security architecture and policy development § Incident Response: Incident Management and Emergency Response services § Consulting and Professional Security Services: Security Intelligence and Advisory Services § GBS Consulting Services Systems Storage Virtual Network “How does my business benefit from infrastructure security protection? ” Values § Reduces cost of ongoing management of security operations § Improves operational availability and assures performance against SLA, backed by industry’s only guaranteed SLA for managed protection services § Increases productivity by decreasing risk of virus, worm and malcode infestation § Decreases volume of incoming spam § Drill down on specific violations to quickly address resolution § Readily show status against major regulations
NETWORK, SERVER AND END POINT Issues § Mass commercialization and automation of threats § Parasitic, stealthier, more damaging attacks § Poor understanding of risks in new technologies and Manage Infrastructure Security applications, including virtualization and cloud § Weak application controls § Lack of skills to monitor and manage security inputs § Compounding cost of managing an ever increasing array of security technologies § Undetected breaches due to privilege access misuse and downtime from incidents § Inability to establish forensic evidence or demonstrate compliance IBM Security Offerings § Threat Mitigation: ISS Network, Server and Endpoint Intrusion ® Detection and Prevention products powered by X-Force , Managed Intrusion Prevention and Detection, Network Mail Security, Managed firewall services, Vulnerability Management and Scanning § SIEM: Tivoli Compliance Insight Manager, Security Event and Log Management services § Security Governance: Regulatory assessments and remediation solutions, Security architecture and policy development § Incident Response: Incident Management and Emergency Response services § Consulting and Professional Security Services: Security Intelligence and Advisory Services § GBS Consulting Services Systems Storage Virtual Network “How does my business benefit from infrastructure security protection? ” Values § Reduces cost of ongoing management of security operations § Improves operational availability and assures performance against SLA, backed by industry’s only guaranteed SLA for managed protection services § Increases productivity by decreasing risk of virus, worm and malcode infestation § Decreases volume of incoming spam § Drill down on specific violations to quickly address resolution § Readily show status against major regulations
 IBM provides the business answers you need Manage risk end-to-end for all infrastructure domains
IBM provides the business answers you need Manage risk end-to-end for all infrastructure domains
 IBM Global Security Reach IBM has the unmatched global and local expertise to deliver complete solutions – and manage the cost and complexity of security
IBM Global Security Reach IBM has the unmatched global and local expertise to deliver complete solutions – and manage the cost and complexity of security
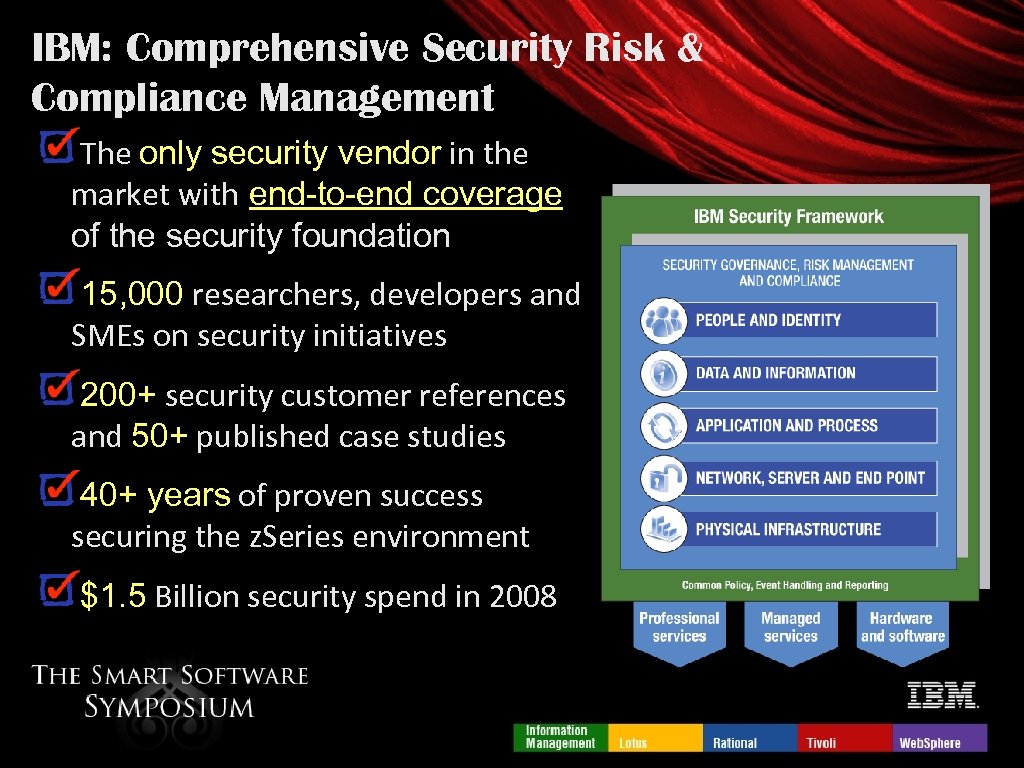 IBM: Comprehensive Security Risk & Compliance Management The only security vendor in the market with end-to-end coverage of the security foundation 15, 000 researchers, developers and SMEs on security initiatives 200+ security customer references and 50+ published case studies 40+ years of proven success securing the z. Series environment $1. 5 Billion security spend in 2008
IBM: Comprehensive Security Risk & Compliance Management The only security vendor in the market with end-to-end coverage of the security foundation 15, 000 researchers, developers and SMEs on security initiatives 200+ security customer references and 50+ published case studies 40+ years of proven success securing the z. Series environment $1. 5 Billion security spend in 2008



