6a61d947266a104b787a338641e60271.ppt
- Количество слайдов: 31
 THE SECURITY CLASSIFICATION SYSTEM www. ispcert. com
THE SECURITY CLASSIFICATION SYSTEM www. ispcert. com
 CONTENTS • • • Why the Security Classification System How is information classified How is classified information marked Government and contractor responsibilities Test www. ispcert. com
CONTENTS • • • Why the Security Classification System How is information classified How is classified information marked Government and contractor responsibilities Test www. ispcert. com
 CONTENTS v How do classified items receive their designations? v Who is responsible for assigning classification levels? v What recourse do security managers have after discovering a classification error? v Can anything be assigned a classification level by anyone? v These are questions that come to the minds of many who safeguard or work with classified material. Although there is guidance to demonstrate proper control, accountability, documentation, storage, dissemination and destruction of classified material, many practitioners do not understand the fundamentals. Executive Order 13526 provides the history, disposition and future status of classified information. www. ispcert. com
CONTENTS v How do classified items receive their designations? v Who is responsible for assigning classification levels? v What recourse do security managers have after discovering a classification error? v Can anything be assigned a classification level by anyone? v These are questions that come to the minds of many who safeguard or work with classified material. Although there is guidance to demonstrate proper control, accountability, documentation, storage, dissemination and destruction of classified material, many practitioners do not understand the fundamentals. Executive Order 13526 provides the history, disposition and future status of classified information. www. ispcert. com
 WHY ASSIGN CLASSIFICATION SYSTMS For over 18 years John A. Walker, Jr. had sold secrets during and after his career in the Navy. Though entrusted with a security clearance and a “need-to know”, he did not demonstrate the trustworthiness of which his thorough background investigation deemed him worthy. When the opportunity revealed itself, he took advantage of his position and responsibilities to smuggle classified information to his Russian connections. During the investigation into his arrest, authorities discovered a complex spy ring consisting of family members and other recruited operatives. Walker had earned the trust and cooperation of his family to commit one of the most notorious of all cases of espionage. As a result of his crimes, he received a two life terms plus 10 year, his son received 25 years and the damage to the U. S. national security was tremendous. “It has been estimated by some intelligence experts that Mr. Walker provided enough code-data information to alter significantly the balance of power between Russia and the United States” John Oconner, New York Times
WHY ASSIGN CLASSIFICATION SYSTMS For over 18 years John A. Walker, Jr. had sold secrets during and after his career in the Navy. Though entrusted with a security clearance and a “need-to know”, he did not demonstrate the trustworthiness of which his thorough background investigation deemed him worthy. When the opportunity revealed itself, he took advantage of his position and responsibilities to smuggle classified information to his Russian connections. During the investigation into his arrest, authorities discovered a complex spy ring consisting of family members and other recruited operatives. Walker had earned the trust and cooperation of his family to commit one of the most notorious of all cases of espionage. As a result of his crimes, he received a two life terms plus 10 year, his son received 25 years and the damage to the U. S. national security was tremendous. “It has been estimated by some intelligence experts that Mr. Walker provided enough code-data information to alter significantly the balance of power between Russia and the United States” John Oconner, New York Times
 NATIONAL INDUSTRIAL SECURITY PROGRAM NISP is designed Safeguard classified information that has been or may be released to… “current, prospective, or former contractors, licensees, or grantees of United States agencies”. It is also designed to provide for the protection of classified material as outlined in EO 12356 and the Atomic Energy Act of 1954, as amended. www. ispcert. com
NATIONAL INDUSTRIAL SECURITY PROGRAM NISP is designed Safeguard classified information that has been or may be released to… “current, prospective, or former contractors, licensees, or grantees of United States agencies”. It is also designed to provide for the protection of classified material as outlined in EO 12356 and the Atomic Energy Act of 1954, as amended. www. ispcert. com
 NISPOM v The NISPOM is the primary regulatory reference for performing industrial security v The Department of Defense consults with Secretary of Energy, the Nuclear Regulatory Commission and the Director of Central Intelligence to issue and maintain the NISPOM v It is up to the contractor and each agency work together to meet the NISPOM’s intent The NISPOM provides restrictions, rules, guidelines and procedures for preventing unauthorized disclosure of classified material; it is the primary regulatory reference for performing industrial security. www. ispcert. com
NISPOM v The NISPOM is the primary regulatory reference for performing industrial security v The Department of Defense consults with Secretary of Energy, the Nuclear Regulatory Commission and the Director of Central Intelligence to issue and maintain the NISPOM v It is up to the contractor and each agency work together to meet the NISPOM’s intent The NISPOM provides restrictions, rules, guidelines and procedures for preventing unauthorized disclosure of classified material; it is the primary regulatory reference for performing industrial security. www. ispcert. com
 NISPOM v The Secretary of Energy and the Nuclear Regulatory Commission have the lead in detailing requirements for protecting classified information identified in the Atomic Energy Act of 1954 v The Director of Central Intelligence will provide a section for intelligence sources and methods, to include Sensitive Compartmented Information (SCI) v However, in this coordination each agency maintains its authority v The NISPOM applies to authorized users of classified information and equips those working on classified contracts with critical instruction on how to implement the NISP in their organizations v It is up to the contractor and the oversight agency to work together to provide accurate interpretation of the guidelines to the specific classified contract requirements. www. ispcert. com
NISPOM v The Secretary of Energy and the Nuclear Regulatory Commission have the lead in detailing requirements for protecting classified information identified in the Atomic Energy Act of 1954 v The Director of Central Intelligence will provide a section for intelligence sources and methods, to include Sensitive Compartmented Information (SCI) v However, in this coordination each agency maintains its authority v The NISPOM applies to authorized users of classified information and equips those working on classified contracts with critical instruction on how to implement the NISP in their organizations v It is up to the contractor and the oversight agency to work together to provide accurate interpretation of the guidelines to the specific classified contract requirements. www. ispcert. com
 NATIONAL INDUSTRIAL SECURITY PROGRAM (NISPOM) All agencies apply three factors to the concept of Risk Management 1. Damage to national security 2. Existing or anticipated threat to disclosure of information. 3. Short and long term costs of the requirements, restrictions, and other safeguards The second and third factors aren’t spelled out in the NISPOM, but are recognized as legitimate concerns to prevent the NISP from becoming a burden to industry www. ispcert. com
NATIONAL INDUSTRIAL SECURITY PROGRAM (NISPOM) All agencies apply three factors to the concept of Risk Management 1. Damage to national security 2. Existing or anticipated threat to disclosure of information. 3. Short and long term costs of the requirements, restrictions, and other safeguards The second and third factors aren’t spelled out in the NISPOM, but are recognized as legitimate concerns to prevent the NISP from becoming a burden to industry www. ispcert. com
 NATIONAL INDUSTRIAL SECURITY PROGRAM (NISPOM) v The Secretary of Defense and the other identified agencies apply the concept of Risk Management while implementing the NISPOM v Astute Industrial Security managers develop risk management analysis to better interpret the risk and discover the potential impact. They will also develop solutions to reduce the risk and the predicted damage. The bottom line is to reduce the probability of unauthorized disclosure of classified information www. ispcert. com
NATIONAL INDUSTRIAL SECURITY PROGRAM (NISPOM) v The Secretary of Defense and the other identified agencies apply the concept of Risk Management while implementing the NISPOM v Astute Industrial Security managers develop risk management analysis to better interpret the risk and discover the potential impact. They will also develop solutions to reduce the risk and the predicted damage. The bottom line is to reduce the probability of unauthorized disclosure of classified information www. ispcert. com
 EXECUTIVE ORDER 13526 v Provides Classified National Security Information and delivers a cohesive method for designation classification v The Government has designed stringent policy to ensure that classified material is protected at the level necessary to prevent unauthorized disclosure. www. ispcert. com
EXECUTIVE ORDER 13526 v Provides Classified National Security Information and delivers a cohesive method for designation classification v The Government has designed stringent policy to ensure that classified material is protected at the level necessary to prevent unauthorized disclosure. www. ispcert. com
 THREE DESINGNATIONS FOR CLASSIFIED v CONFIDENTIAL information could reasonably be expected cause damage v SECRET could reasonably be expected to cause serious damage v TOP SECRET could reasonably be expected to cause exceptionally grave damage to national security Caution: Classified information should not be confused with the proprietary information sometimes referred to as company confidential or secret. www. ispcert. com
THREE DESINGNATIONS FOR CLASSIFIED v CONFIDENTIAL information could reasonably be expected cause damage v SECRET could reasonably be expected to cause serious damage v TOP SECRET could reasonably be expected to cause exceptionally grave damage to national security Caution: Classified information should not be confused with the proprietary information sometimes referred to as company confidential or secret. www. ispcert. com
 CONDITIONS FOR CLASSIFICATION Classifications are not assigned unless: v An original classification authority (OCR) is applying the classification level v The U. S. Government owns, is producing, or is controlling the information v Information meets one of eight categories v The OCR determines unauthorized disclosure could cause damage to national security to include transnational terrorism and they can identify or describe the damage. www. ispcert. com
CONDITIONS FOR CLASSIFICATION Classifications are not assigned unless: v An original classification authority (OCR) is applying the classification level v The U. S. Government owns, is producing, or is controlling the information v Information meets one of eight categories v The OCR determines unauthorized disclosure could cause damage to national security to include transnational terrorism and they can identify or describe the damage. www. ispcert. com
 CONDITIONS FOR CLASSIFICATION v According to a report from the Chairman of the House National Security Subcommittee, 10% of secrets should have never been classified and that nearly 90% of classified information has been overclassified v A Defense Security Services report stated in 2003 nearly $6. 5 billion was spent to classify information v To prevent such abuse, the Executive Order provides guidance to train and prevent classification authorities from arbitrarily assigned a classification level www. ispcert. com
CONDITIONS FOR CLASSIFICATION v According to a report from the Chairman of the House National Security Subcommittee, 10% of secrets should have never been classified and that nearly 90% of classified information has been overclassified v A Defense Security Services report stated in 2003 nearly $6. 5 billion was spent to classify information v To prevent such abuse, the Executive Order provides guidance to train and prevent classification authorities from arbitrarily assigned a classification level www. ispcert. com
 WHAT ARE THE EIGHT CATEGORIES 1. Military plans, weapons systems or operations v The U. S. armed forces not only safeguards, but provides instructions for protecting the specifics of their weapons and plans. If these strategies and operations were released to the wrong hands, the information would damage national security and adversely affect our ability to defend ourselves. 2. Foreign government information v This knowledge includes what the U. S. Government may already know about other governments. This gives the U. S. the advantage of knowing information that another country thinks is protected. www. ispcert. com
WHAT ARE THE EIGHT CATEGORIES 1. Military plans, weapons systems or operations v The U. S. armed forces not only safeguards, but provides instructions for protecting the specifics of their weapons and plans. If these strategies and operations were released to the wrong hands, the information would damage national security and adversely affect our ability to defend ourselves. 2. Foreign government information v This knowledge includes what the U. S. Government may already know about other governments. This gives the U. S. the advantage of knowing information that another country thinks is protected. www. ispcert. com
 WHAT ARE THE EIGHT CATEGORIES 3. www. ispcert. com Intelligence activities, sources, or methods or cryptology v One can imagine what damage could take place if any intelligence gathering sources, methods or activities were compromised. The suspecting adversary could become aware of the threat and cease their activity or design countermeasures designed to thwart future efforts.
WHAT ARE THE EIGHT CATEGORIES 3. www. ispcert. com Intelligence activities, sources, or methods or cryptology v One can imagine what damage could take place if any intelligence gathering sources, methods or activities were compromised. The suspecting adversary could become aware of the threat and cease their activity or design countermeasures designed to thwart future efforts.
 WHAT ARE THE EIGHT CATEGORIES 4. Foreign relations or activities of the United States including confidential sources v This information is specified U. S. foreign policy activities and sources friendly to U. S. efforts and U. S. organizations. Such is protected to ensure the safety of the relations and success of the activities. Compromise of any of the sources could cause damage to National Security as they are denied further access. 5. Scientific, technological, or economic matters relating to national security, including defense against transnational terrorism v Unauthorized access to national security-related U. S. scientific, technological, and economic data could compromise plans, production, and strategies and leave certain vulnerabilities. www. ispcert. com
WHAT ARE THE EIGHT CATEGORIES 4. Foreign relations or activities of the United States including confidential sources v This information is specified U. S. foreign policy activities and sources friendly to U. S. efforts and U. S. organizations. Such is protected to ensure the safety of the relations and success of the activities. Compromise of any of the sources could cause damage to National Security as they are denied further access. 5. Scientific, technological, or economic matters relating to national security, including defense against transnational terrorism v Unauthorized access to national security-related U. S. scientific, technological, and economic data could compromise plans, production, and strategies and leave certain vulnerabilities. www. ispcert. com
 WHAT ARE THE EIGHT CATEGORIES 6. U. S. programs for safeguarding nuclear materials or facilities v For nuclear activities, the Department of Energy and the Nuclear Regulation Commission provide specific guidance to ensure the best protection. Vulnerabilities and strengths are assessed to ensure the best possible measures are in place to protect these items. Plans, strategies and programs are only effective if enforced AND access is limited. www. ispcert. com
WHAT ARE THE EIGHT CATEGORIES 6. U. S. programs for safeguarding nuclear materials or facilities v For nuclear activities, the Department of Energy and the Nuclear Regulation Commission provide specific guidance to ensure the best protection. Vulnerabilities and strengths are assessed to ensure the best possible measures are in place to protect these items. Plans, strategies and programs are only effective if enforced AND access is limited. www. ispcert. com
 WHAT ARE THE EIGHT CATEGORIES 7. Vulnerabilities of systems, installations, infrastructures, projects, plans or protection services related to national security including terrorism v Security managers assess strengths and to ensure the best possible measures are in place to protect these items. Plans, strategies and programs are only effective if enforced AND access is limited. An adversary could use the programs to gain advantages, steal, damage or destroy systems, installations, infrastructures, projects, plans or protection services. 8. Weapons of Mass Destruction v Information fitting this category is classified to prevent unauthorized disclosure. Such unauthorized disclosure could make the U. S. vulnerable to adversaries to include transnational terrorists. www. ispcert. com
WHAT ARE THE EIGHT CATEGORIES 7. Vulnerabilities of systems, installations, infrastructures, projects, plans or protection services related to national security including terrorism v Security managers assess strengths and to ensure the best possible measures are in place to protect these items. Plans, strategies and programs are only effective if enforced AND access is limited. An adversary could use the programs to gain advantages, steal, damage or destroy systems, installations, infrastructures, projects, plans or protection services. 8. Weapons of Mass Destruction v Information fitting this category is classified to prevent unauthorized disclosure. Such unauthorized disclosure could make the U. S. vulnerable to adversaries to include transnational terrorists. www. ispcert. com
 CLASSIFICATION MARKINGS v Classified material should always display proper markings at all times v The classified information will have markings displayed in a specific manner based on the type of media (compact disk, cassette, book, map and etc. ) v Furthermore, the classification should identify which pages, paragraphs and portions are classified and unclassified. www. ispcert. com
CLASSIFICATION MARKINGS v Classified material should always display proper markings at all times v The classified information will have markings displayed in a specific manner based on the type of media (compact disk, cassette, book, map and etc. ) v Furthermore, the classification should identify which pages, paragraphs and portions are classified and unclassified. www. ispcert. com
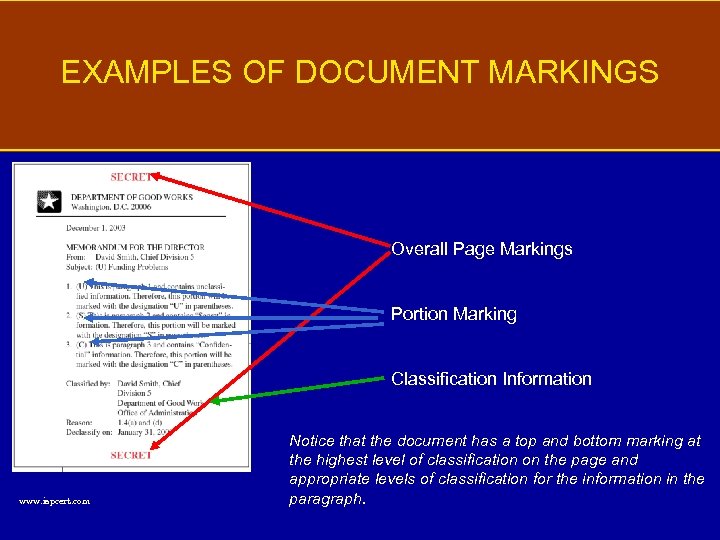 EXAMPLES OF DOCUMENT MARKINGS Overall Page Markings Portion Marking Classification Information www. ispcert. com Notice that the document has a top and bottom marking at the highest level of classification on the page and appropriate levels of classification for the information in the paragraph.
EXAMPLES OF DOCUMENT MARKINGS Overall Page Markings Portion Marking Classification Information www. ispcert. com Notice that the document has a top and bottom marking at the highest level of classification on the page and appropriate levels of classification for the information in the paragraph.
 LET’S CLASSIFY IT ALL JUST TO BE SURE v Limits to classification v. A classification cannot be assigned to hide legal violations, inefficiencies or mistakes v. Nor can the classification authorities assigned to prevent embarrassment, prevent or restrict competition or delay the release of information that hasn’t previously required such a level of protection www. ispcert. com Users of Classified material have an obligation to challenge classification that violate any of the above
LET’S CLASSIFY IT ALL JUST TO BE SURE v Limits to classification v. A classification cannot be assigned to hide legal violations, inefficiencies or mistakes v. Nor can the classification authorities assigned to prevent embarrassment, prevent or restrict competition or delay the release of information that hasn’t previously required such a level of protection www. ispcert. com Users of Classified material have an obligation to challenge classification that violate any of the above
 CAN’T WE JUST CLASSIFY IT ALL JUST TO BE SURE v Holders of classified information may discover that the classification level may be inappropriate or unnecessary. These holders have a duty to report their beliefs. v Such reports are to be handled with the agency authorities and reviewed for a decision. v The agency heads or senior officials also need to ensure there is no retribution for the report as well as notifying the individuals that they have a right to appeal the agency decisions to the Interagency Security Classification Appeals Panel. Users of Classified material have an obligation to challenge classification that violate any of the above www. ispcert. com
CAN’T WE JUST CLASSIFY IT ALL JUST TO BE SURE v Holders of classified information may discover that the classification level may be inappropriate or unnecessary. These holders have a duty to report their beliefs. v Such reports are to be handled with the agency authorities and reviewed for a decision. v The agency heads or senior officials also need to ensure there is no retribution for the report as well as notifying the individuals that they have a right to appeal the agency decisions to the Interagency Security Classification Appeals Panel. Users of Classified material have an obligation to challenge classification that violate any of the above www. ispcert. com
 CLEARANCE AND “NEED TO KNOW” v Anyone desiring access to classified information must possess a security clearance and have “need to know” v Security clearances are issued after a favorable investigation and a determination is made. www. ispcert. com
CLEARANCE AND “NEED TO KNOW” v Anyone desiring access to classified information must possess a security clearance and have “need to know” v Security clearances are issued after a favorable investigation and a determination is made. www. ispcert. com
 WE ARE PROVIDED INSTRUCIONS OF USE v Classified users are trained in proper safeguarding and sanctions imposed on those who fail to protect it from unauthorized disclosure v Each originating agency must provide instructions on the proper protection, use, storage, transmission and destruction of the information www. ispcert. com
WE ARE PROVIDED INSTRUCIONS OF USE v Classified users are trained in proper safeguarding and sanctions imposed on those who fail to protect it from unauthorized disclosure v Each originating agency must provide instructions on the proper protection, use, storage, transmission and destruction of the information www. ispcert. com
 WE ARE PROVIDED INSTRUCIONS OF USE v DON’T BEGIN CLASSIFIED WORK WITHOUT v DDFORM 254 -Provides instructions on how, when and where to perform on a classified contract v SECURITY CLASSIFICATION GUIDEDesigned to notify what is classified and to what level. A security classification guide is assigned to each classified project. www. ispcert. com
WE ARE PROVIDED INSTRUCIONS OF USE v DON’T BEGIN CLASSIFIED WORK WITHOUT v DDFORM 254 -Provides instructions on how, when and where to perform on a classified contract v SECURITY CLASSIFICATION GUIDEDesigned to notify what is classified and to what level. A security classification guide is assigned to each classified project. www. ispcert. com
 SUMMARY v The NISP is created to protect classified information v Three factors are considered before implementing the NISPOM: v level of damage to national security v existing or anticipate threat to disclosure v long and short term costs v Presidential Executive Order 13526 delivers a cohesive method for designation classification, protecting and declassifying national security information v Classified material should always be marked with the correct level
SUMMARY v The NISP is created to protect classified information v Three factors are considered before implementing the NISPOM: v level of damage to national security v existing or anticipate threat to disclosure v long and short term costs v Presidential Executive Order 13526 delivers a cohesive method for designation classification, protecting and declassifying national security information v Classified material should always be marked with the correct level
 REFERENCES • • www. ispcert. com O’Connor, John, “TV View; American Spies In Pursuit Of The American Dream”, New York Times, NY, 1990 http: //query. nytimes. com/gst/fullpage. html? res=9 C 0 CE 6 DA 133 BF 937 A 35751 C 0 A 9 66958260, Feb 4, 2008 The President, Executive Order 12829—National Industrial Security Program (Federal Register, Jan 1993) pg. 3 -2. The President, Executive Order 13292, Further Amendment to Executive Order 13526, As Amended, Classified National Security Information—National Industrial Security Program (Federal Register, Mar 2003) Sec. 1 -2 “Too Many Secrets: Overclassification As A Barrier To Critical Information Sharing”, (Hearing Before The Subcommittee On National Security, Emerging Threats And International Relations Of The Committee On Government Reform House Of Representatives One Hundred Eighth Congress Second Session August 24, 2004) Serial No. 108 -263, Available Via The World Wide Web: Http: //www. Gpo. Gov/Congress/House and Http: //www. House. Gov/Reform. “Secrecy Report Card, Quantitative Indicators in Secrecy of the Federal Government”, (http: //www. openthegovernment. org/otg/SRC 2006. pdf, August 2004).
REFERENCES • • www. ispcert. com O’Connor, John, “TV View; American Spies In Pursuit Of The American Dream”, New York Times, NY, 1990 http: //query. nytimes. com/gst/fullpage. html? res=9 C 0 CE 6 DA 133 BF 937 A 35751 C 0 A 9 66958260, Feb 4, 2008 The President, Executive Order 12829—National Industrial Security Program (Federal Register, Jan 1993) pg. 3 -2. The President, Executive Order 13292, Further Amendment to Executive Order 13526, As Amended, Classified National Security Information—National Industrial Security Program (Federal Register, Mar 2003) Sec. 1 -2 “Too Many Secrets: Overclassification As A Barrier To Critical Information Sharing”, (Hearing Before The Subcommittee On National Security, Emerging Threats And International Relations Of The Committee On Government Reform House Of Representatives One Hundred Eighth Congress Second Session August 24, 2004) Serial No. 108 -263, Available Via The World Wide Web: Http: //www. Gpo. Gov/Congress/House and Http: //www. House. Gov/Reform. “Secrecy Report Card, Quantitative Indicators in Secrecy of the Federal Government”, (http: //www. openthegovernment. org/otg/SRC 2006. pdf, August 2004).
 TEST • Click on the correct answers www. ispcert. com
TEST • Click on the correct answers www. ispcert. com
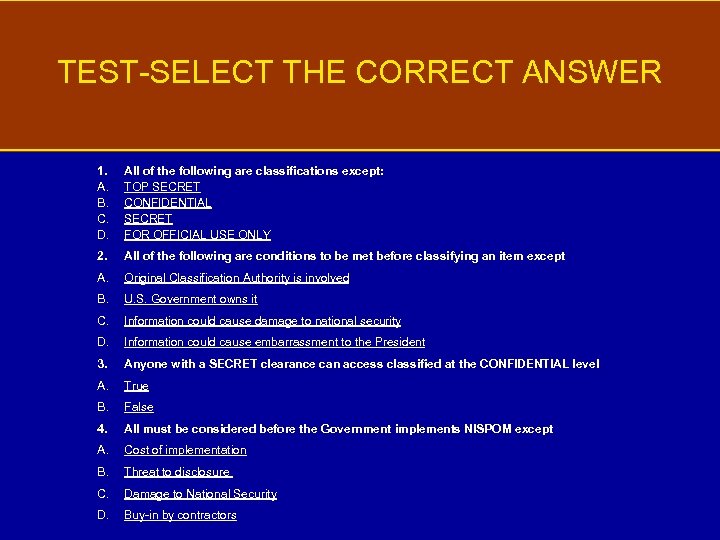 TEST-SELECT THE CORRECT ANSWER 1. A. B. C. D. All of the following are classifications except: TOP SECRET CONFIDENTIAL SECRET FOR OFFICIAL USE ONLY 2. All of the following are conditions to be met before classifying an item except A. Original Classification Authority is involved B. U. S. Government owns it C. Information could cause damage to national security D. Information could cause embarrassment to the President 3. Anyone with a SECRET clearance can access classified at the CONFIDENTIAL level A. True B. False 4. All must be considered before the Government implements NISPOM except A. Cost of implementation B. Threat to disclosure C. Damage to National Security D. Buy-in by contractors
TEST-SELECT THE CORRECT ANSWER 1. A. B. C. D. All of the following are classifications except: TOP SECRET CONFIDENTIAL SECRET FOR OFFICIAL USE ONLY 2. All of the following are conditions to be met before classifying an item except A. Original Classification Authority is involved B. U. S. Government owns it C. Information could cause damage to national security D. Information could cause embarrassment to the President 3. Anyone with a SECRET clearance can access classified at the CONFIDENTIAL level A. True B. False 4. All must be considered before the Government implements NISPOM except A. Cost of implementation B. Threat to disclosure C. Damage to National Security D. Buy-in by contractors
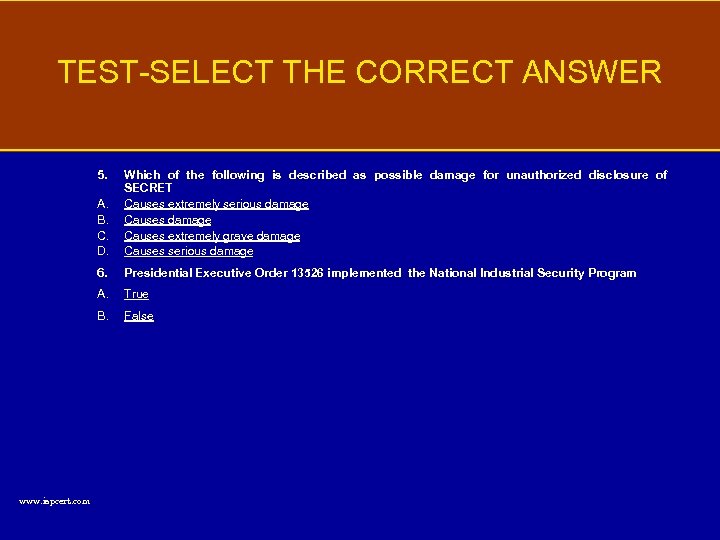 TEST-SELECT THE CORRECT ANSWER 5. A. B. C. D. 6. Presidential Executive Order 13526 implemented the National Industrial Security Program A. True B. www. ispcert. com Which of the following is described as possible damage for unauthorized disclosure of SECRET Causes extremely serious damage Causes extremely grave damage Causes serious damage False
TEST-SELECT THE CORRECT ANSWER 5. A. B. C. D. 6. Presidential Executive Order 13526 implemented the National Industrial Security Program A. True B. www. ispcert. com Which of the following is described as possible damage for unauthorized disclosure of SECRET Causes extremely serious damage Causes extremely grave damage Causes serious damage False
 CERTIFICATE I HAVE RECEIVED TRAINING AND UNDERSTAND THE CONTENTS OF: Classification System ANY QUESTIONS THAT I HAVE RAISED WERE ADDRESSED BY THE FSO : NAME: DATE: FSO Verification: www. ispcert. com
CERTIFICATE I HAVE RECEIVED TRAINING AND UNDERSTAND THE CONTENTS OF: Classification System ANY QUESTIONS THAT I HAVE RAISED WERE ADDRESSED BY THE FSO : NAME: DATE: FSO Verification: www. ispcert. com


