789677f574a58ecd0993b7a3c42eb80a.ppt
- Количество слайдов: 105
 The Next Generation of Wireless Local Area Networks Mark Ciampa
The Next Generation of Wireless Local Area Networks Mark Ciampa
 “Disruptive Technology” Ø Disruptive technology - A radical technology or innovation that fills a new role that an existing device or technology could not Ø Examples: steamships, telephones, automobiles, word processors, and the Internet replacing sailing ships, telegraphs, horses, typewriters, and libraries Ø Disruptive technologies proven have profound impact upon society and how people live, work, and play
“Disruptive Technology” Ø Disruptive technology - A radical technology or innovation that fills a new role that an existing device or technology could not Ø Examples: steamships, telephones, automobiles, word processors, and the Internet replacing sailing ships, telegraphs, horses, typewriters, and libraries Ø Disruptive technologies proven have profound impact upon society and how people live, work, and play
 Wireless Ø Today’s disruptive technology changing our world: wireless Ø Although wireless voice started revolution in 1990 s, wireless data communications driving force in 21 st century Ø Wireless data communications replacing need be tethered by cable to a network to surf Web, check email, or access inventory records Ø Wireless made mobility possible to degree never before possible or rarely even imagined: users access same resources walking across college campus as can sitting at desk
Wireless Ø Today’s disruptive technology changing our world: wireless Ø Although wireless voice started revolution in 1990 s, wireless data communications driving force in 21 st century Ø Wireless data communications replacing need be tethered by cable to a network to surf Web, check email, or access inventory records Ø Wireless made mobility possible to degree never before possible or rarely even imagined: users access same resources walking across college campus as can sitting at desk
 Wireless In Travel Ø Airlines - All domestic air carriers (except Allegiant Air and Spirit) offer or will offer wireless in 2010 Ø Airports - All 219 US airports (except Fairbanks, Van Nuys, Yampa Valley Regional, 5 Hawaii) offer wireless Ø Hotels - Over 25, 000 Ø Trains - San Francisco Bay Area Rapid Transit (BART), Massachusetts Bay Transportation Authority (MBTA) Ø Limousine - Multiple major US metropolitan Ø Washington State Ferry system 4
Wireless In Travel Ø Airlines - All domestic air carriers (except Allegiant Air and Spirit) offer or will offer wireless in 2010 Ø Airports - All 219 US airports (except Fairbanks, Van Nuys, Yampa Valley Regional, 5 Hawaii) offer wireless Ø Hotels - Over 25, 000 Ø Trains - San Francisco Bay Area Rapid Transit (BART), Massachusetts Bay Transportation Authority (MBTA) Ø Limousine - Multiple major US metropolitan Ø Washington State Ferry system 4
 Wireless Changing All Sectors Ø Finance Ø Health Care Ø Manufacturing Ø Retail Ø Logistics Ø Government Ø Military Ø Construction Ø Education 5
Wireless Changing All Sectors Ø Finance Ø Health Care Ø Manufacturing Ø Retail Ø Logistics Ø Government Ø Military Ø Construction Ø Education 5
 Wireless By The Numbers Ø Number of locations where wireless data services are available increasing 40% annually Ø By 2011 over 250 million wireless data devices will be sold (up from 22 million in 2003 and zero in 1999) Ø Virtually all laptop computers sold today have wireless data capabilities as standard equipment 6
Wireless By The Numbers Ø Number of locations where wireless data services are available increasing 40% annually Ø By 2011 over 250 million wireless data devices will be sold (up from 22 million in 2003 and zero in 1999) Ø Virtually all laptop computers sold today have wireless data capabilities as standard equipment 6
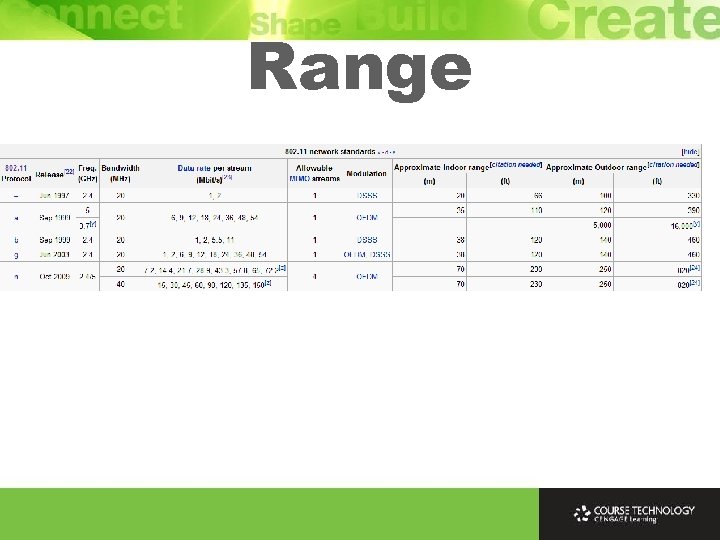
 Wireless LANs ØSame function of standard LAN but without wires ØBased on IEEE standards ØAlso called Wi-Fi ØTypical range 150 -375 feet ØTypical bandwidth 11 -54 Mbps 7
Wireless LANs ØSame function of standard LAN but without wires ØBased on IEEE standards ØAlso called Wi-Fi ØTypical range 150 -375 feet ØTypical bandwidth 11 -54 Mbps 7
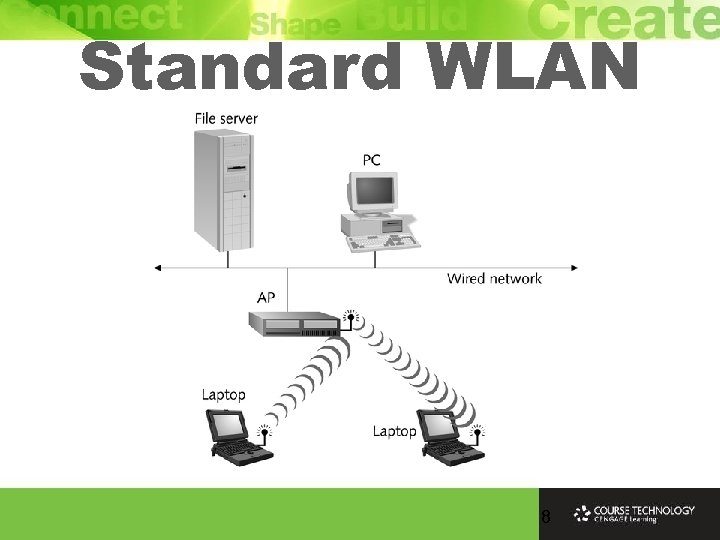 Standard WLAN 8
Standard WLAN 8
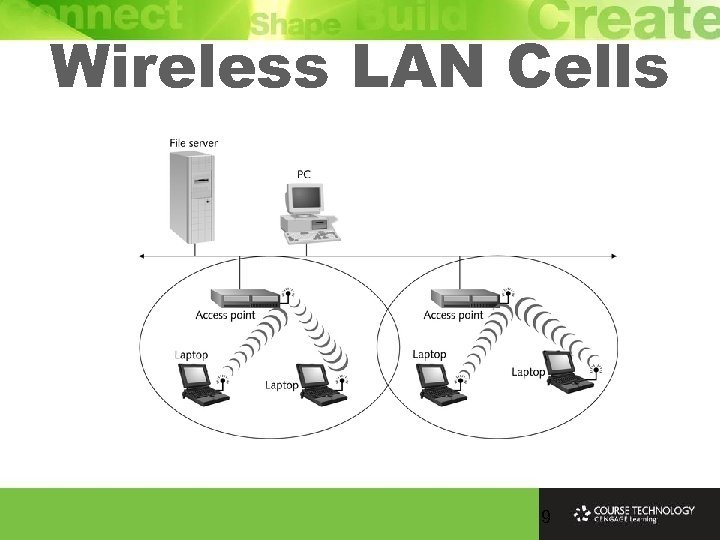 Wireless LAN Cells 9
Wireless LAN Cells 9
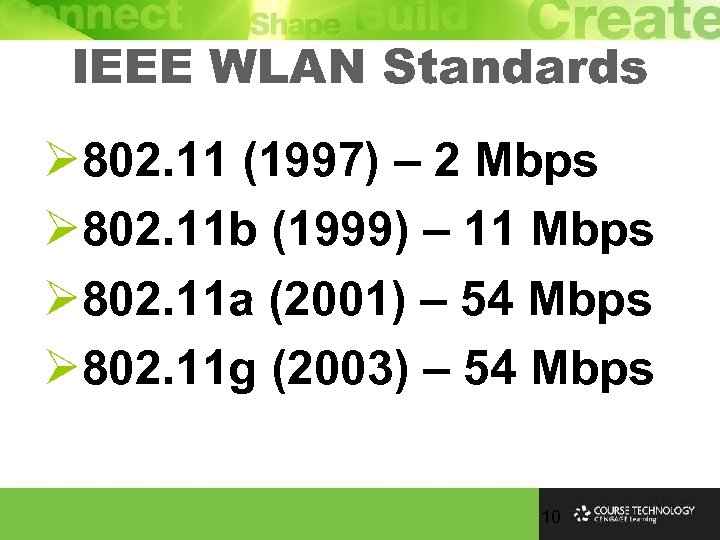 IEEE WLAN Standards Ø 802. 11 (1997) – 2 Mbps Ø 802. 11 b (1999) – 11 Mbps Ø 802. 11 a (2001) – 54 Mbps Ø 802. 11 g (2003) – 54 Mbps 10
IEEE WLAN Standards Ø 802. 11 (1997) – 2 Mbps Ø 802. 11 b (1999) – 11 Mbps Ø 802. 11 a (2001) – 54 Mbps Ø 802. 11 g (2003) – 54 Mbps 10
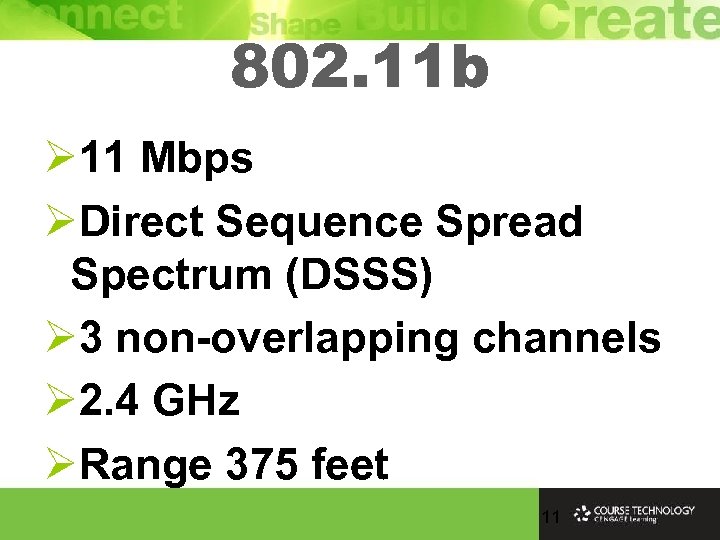 802. 11 b Ø 11 Mbps ØDirect Sequence Spread Spectrum (DSSS) Ø 3 non-overlapping channels Ø 2. 4 GHz ØRange 375 feet 11
802. 11 b Ø 11 Mbps ØDirect Sequence Spread Spectrum (DSSS) Ø 3 non-overlapping channels Ø 2. 4 GHz ØRange 375 feet 11
 802. 11 a Ø 54 Mbps ØOrthogonal frequency-division multiplexing (OFDM) Ø 8 non-overlapping channels Ø 5 GHz ØRange 150 feet 12
802. 11 a Ø 54 Mbps ØOrthogonal frequency-division multiplexing (OFDM) Ø 8 non-overlapping channels Ø 5 GHz ØRange 150 feet 12
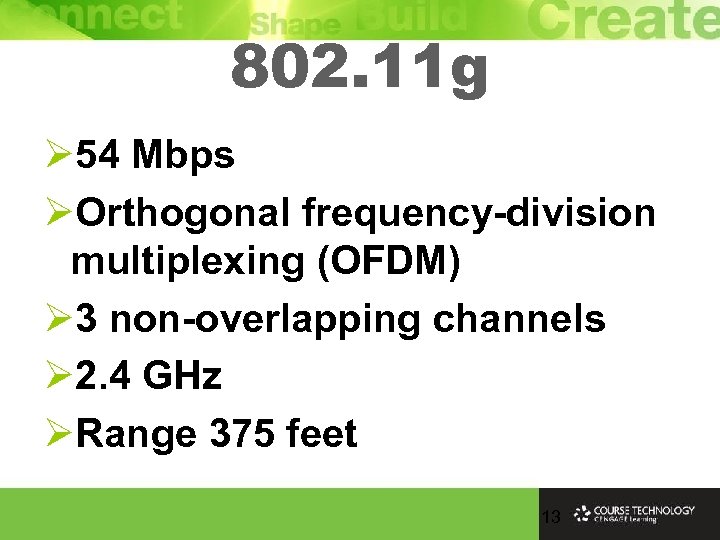 802. 11 g Ø 54 Mbps ØOrthogonal frequency-division multiplexing (OFDM) Ø 3 non-overlapping channels Ø 2. 4 GHz ØRange 375 feet 13
802. 11 g Ø 54 Mbps ØOrthogonal frequency-division multiplexing (OFDM) Ø 3 non-overlapping channels Ø 2. 4 GHz ØRange 375 feet 13
 Limitations 802. 11 a/b/g ØSpeed – Only 11 to 54 Mbps ØCoverage area – Limited ØInterference – Most popular 802. 11 b/g 2. 4 GHz crowded ØSecurity – Useless WEP and weak WPA 14
Limitations 802. 11 a/b/g ØSpeed – Only 11 to 54 Mbps ØCoverage area – Limited ØInterference – Most popular 802. 11 b/g 2. 4 GHz crowded ØSecurity – Useless WEP and weak WPA 14
 Next Generation WLAN ØSpeed – Up to 600 Mbps ØCoverage area – Double indoor range, triple outdoor range ØInterference – Use either 2. 4 GHz or 5 GHz ØSecurity – Require WPA 2 15
Next Generation WLAN ØSpeed – Up to 600 Mbps ØCoverage area – Double indoor range, triple outdoor range ØInterference – Use either 2. 4 GHz or 5 GHz ØSecurity – Require WPA 2 15
 IEEE 802. 11 n-2009
IEEE 802. 11 n-2009
 Next Generation WLAN ØDevelopment of 802. 11 n Ø 802. 11 n PHY layer Ø 802. 11 n MAC layer Ø 802. 11 n Security ØDeployment strategies 17
Next Generation WLAN ØDevelopment of 802. 11 n Ø 802. 11 n PHY layer Ø 802. 11 n MAC layer Ø 802. 11 n Security ØDeployment strategies 17
 The Next Generation of Wireless Local Area Networks Development of 802. 11 n-2009
The Next Generation of Wireless Local Area Networks Development of 802. 11 n-2009
 IEEE Standard Bodies Ø WLAN standards set by Institute of Electrical and Electronics Engineers (IEEE) Ø IEEE uses 2 different internal groups Ø Working groups (WG), such as 802. 3 (Ethernet), 802. 15 (WPANs), WLANs (802. 11) Ø Task Groups (TG), designated by a letter following number of WG (802. 11 b) Ø Function TG to produce draft standard, recommended practice, guideline, or supplement to present to WG Ø After TG’s work made public by creating a publication, function of TG complete and charter expires
IEEE Standard Bodies Ø WLAN standards set by Institute of Electrical and Electronics Engineers (IEEE) Ø IEEE uses 2 different internal groups Ø Working groups (WG), such as 802. 3 (Ethernet), 802. 15 (WPANs), WLANs (802. 11) Ø Task Groups (TG), designated by a letter following number of WG (802. 11 b) Ø Function TG to produce draft standard, recommended practice, guideline, or supplement to present to WG Ø After TG’s work made public by creating a publication, function of TG complete and charter expires
 IEEE 802. 11 -2007 Ø Since 1997 IEEE approved 4 standards for WLANs (IEEE 802. 11, 802. 11 b, 802. 11 a, 802. 11 g) and several amendments (802. 11 d, 802. 11 h, etc. ) Ø To reduce “alphabet soup” in 2007 combined standards and amendments into 1 single standard Ø IEEE 802. 11 -2007, called the IEEE Standard for Information Technology—Telecommunications and information exchange between systems—Local and metropolitan area network— Specific requirements—Part 11: Wireless LAN Medium Access Control (MAC) and Physical Layer (PHY) specifications Ø Document officially retires all previous standards (802. 11, 802. 11 a, 802. 11 b, 802. 11 d, 802. 11 g, 802. 11 h, 802. 11 i, 802. 11 j, 802. 11 e) Ø Combines into 1 comprehensive document
IEEE 802. 11 -2007 Ø Since 1997 IEEE approved 4 standards for WLANs (IEEE 802. 11, 802. 11 b, 802. 11 a, 802. 11 g) and several amendments (802. 11 d, 802. 11 h, etc. ) Ø To reduce “alphabet soup” in 2007 combined standards and amendments into 1 single standard Ø IEEE 802. 11 -2007, called the IEEE Standard for Information Technology—Telecommunications and information exchange between systems—Local and metropolitan area network— Specific requirements—Part 11: Wireless LAN Medium Access Control (MAC) and Physical Layer (PHY) specifications Ø Document officially retires all previous standards (802. 11, 802. 11 a, 802. 11 b, 802. 11 d, 802. 11 g, 802. 11 h, 802. 11 i, 802. 11 j, 802. 11 e) Ø Combines into 1 comprehensive document
 IEEE 802. 11 TGn Ø Sep 11 2004 IEEE formed Task Group n (TGn) begin work on dramatically new WLAN standard that increase speed, range, and reliability Ø Original estimate 802. 11 n ratified 2006 Ø TGn initially evaluated 62 different proposals Ø Due to delay Wi-Fi Alliance in Jun 2007 began certifying vendor products based Draft 2. 0 and certified 500+ products including 80+ enterprise products in 2 years (not same as “Pre-n”) Ø “Anticipated” that products based on final 802. 11 n standard be backward compatible with Draft 2. 0 devices
IEEE 802. 11 TGn Ø Sep 11 2004 IEEE formed Task Group n (TGn) begin work on dramatically new WLAN standard that increase speed, range, and reliability Ø Original estimate 802. 11 n ratified 2006 Ø TGn initially evaluated 62 different proposals Ø Due to delay Wi-Fi Alliance in Jun 2007 began certifying vendor products based Draft 2. 0 and certified 500+ products including 80+ enterprise products in 2 years (not same as “Pre-n”) Ø “Anticipated” that products based on final 802. 11 n standard be backward compatible with Draft 2. 0 devices
 IEEE 802. 11 n-2009 Ø IEEE 802. 11 n-2009 ratified Sep 11 2009 Ø Amendment to IEEE 802. 11 -2007 Ø 802. 11 n significantly improved over previous standards Ø Major impact is increase in maximum raw data rate from 54 Mbps to of 600 Mbps using multiple techniques
IEEE 802. 11 n-2009 Ø IEEE 802. 11 n-2009 ratified Sep 11 2009 Ø Amendment to IEEE 802. 11 -2007 Ø 802. 11 n significantly improved over previous standards Ø Major impact is increase in maximum raw data rate from 54 Mbps to of 600 Mbps using multiple techniques
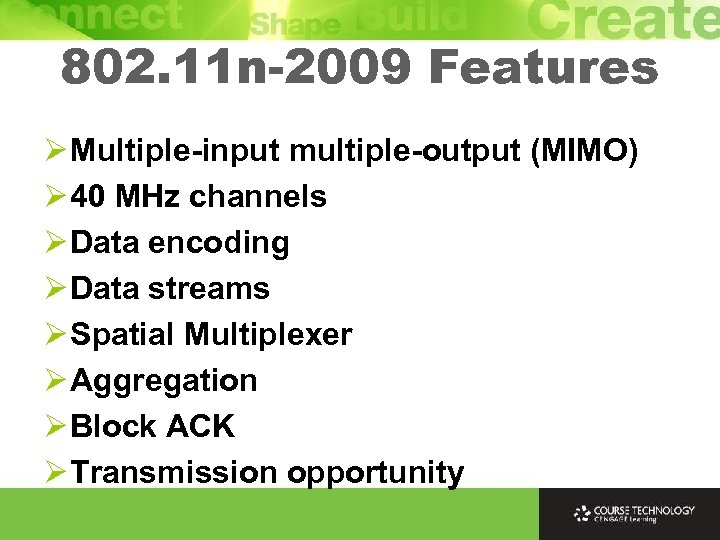 802. 11 n-2009 Features Ø Multiple-input multiple-output (MIMO) Ø 40 MHz channels Ø Data encoding Ø Data streams Ø Spatial Multiplexer Ø Aggregation Ø Block ACK Ø Transmission opportunity
802. 11 n-2009 Features Ø Multiple-input multiple-output (MIMO) Ø 40 MHz channels Ø Data encoding Ø Data streams Ø Spatial Multiplexer Ø Aggregation Ø Block ACK Ø Transmission opportunity
 The Next Generation of Wireless Local Area Networks 802. 11 n-2009 PHY Layer
The Next Generation of Wireless Local Area Networks 802. 11 n-2009 PHY Layer
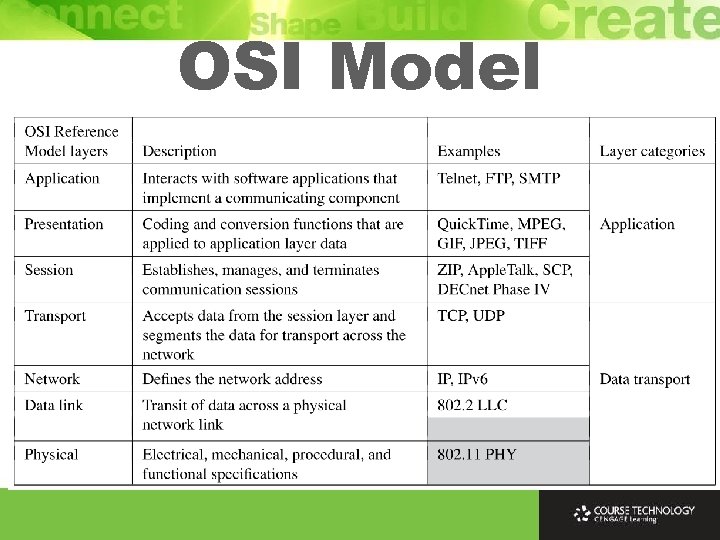 OSI Model
OSI Model
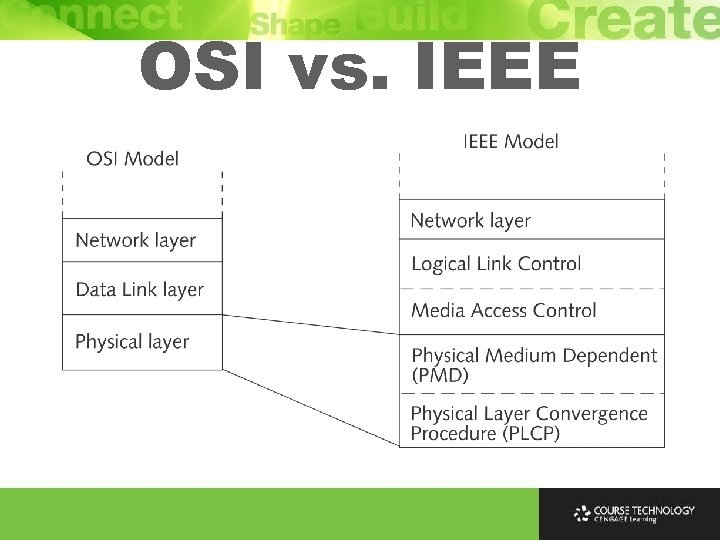 OSI vs. IEEE
OSI vs. IEEE
 PHY Enhancements ØMultiple-Input Multiple. Output (MIMO) ØSpatial Multiplexing ØChannel width
PHY Enhancements ØMultiple-Input Multiple. Output (MIMO) ØSpatial Multiplexing ØChannel width
 The Next Generation of Wireless Local Area Networks 802. 11 n-2009 PHY Layer Multiple-Input Multiple-Output (MIMO)
The Next Generation of Wireless Local Area Networks 802. 11 n-2009 PHY Layer Multiple-Input Multiple-Output (MIMO)
 Tenn Genetic Defect
Tenn Genetic Defect
 Multiple-Lane Road
Multiple-Lane Road
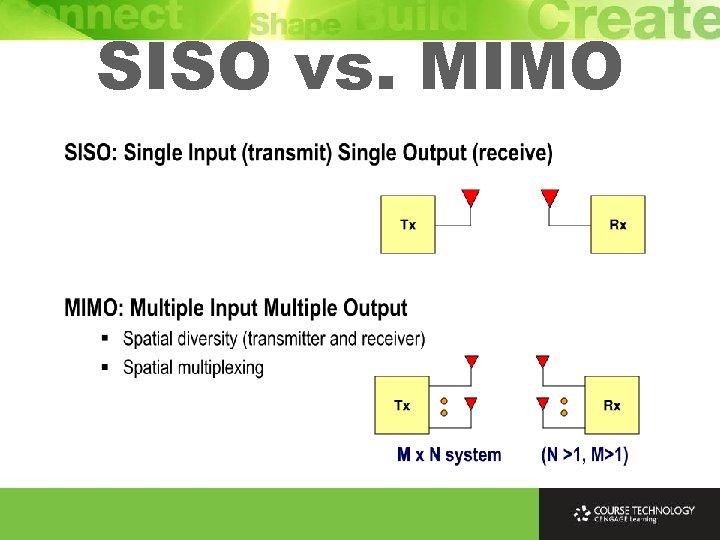
 SISO Ø SISO (Single-Input Single-Output) - Uses 1 transmit (TX) antenna and 1 receive (RX) antenna Ø IEEE 802. 11 a/b/g access points (APs) choose best antenna to send or receive a packet, but still uses 1 antenna at a given moment
SISO Ø SISO (Single-Input Single-Output) - Uses 1 transmit (TX) antenna and 1 receive (RX) antenna Ø IEEE 802. 11 a/b/g access points (APs) choose best antenna to send or receive a packet, but still uses 1 antenna at a given moment
 Best Antenna
Best Antenna
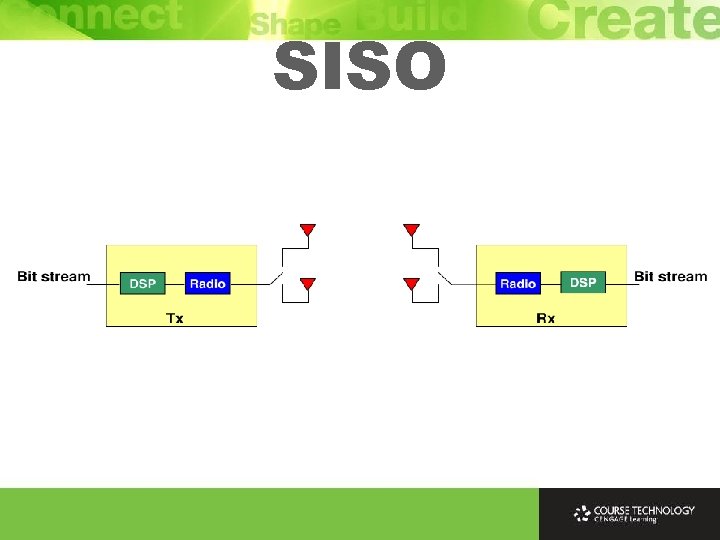 SISO
SISO
 MIMO Ø Long been known that multiple receive (RX) antennas can improve reception through selection of stronger signal or combination of individual signals at receiver Ø In mid-1990 s research predicted large performance gains from using multiple antennas at both transmit (TX) and receive (RX), called MIMO (Multiple-Input Multiple-Output) Ø Using multiple antennas at receiver and transmitter has revolutionized wireless communications Ø Most high-rate wireless systems use MIMO technologies (802. 11 n, 4 G mobile phone technology LTE, Wi. MAX)
MIMO Ø Long been known that multiple receive (RX) antennas can improve reception through selection of stronger signal or combination of individual signals at receiver Ø In mid-1990 s research predicted large performance gains from using multiple antennas at both transmit (TX) and receive (RX), called MIMO (Multiple-Input Multiple-Output) Ø Using multiple antennas at receiver and transmitter has revolutionized wireless communications Ø Most high-rate wireless systems use MIMO technologies (802. 11 n, 4 G mobile phone technology LTE, Wi. MAX)
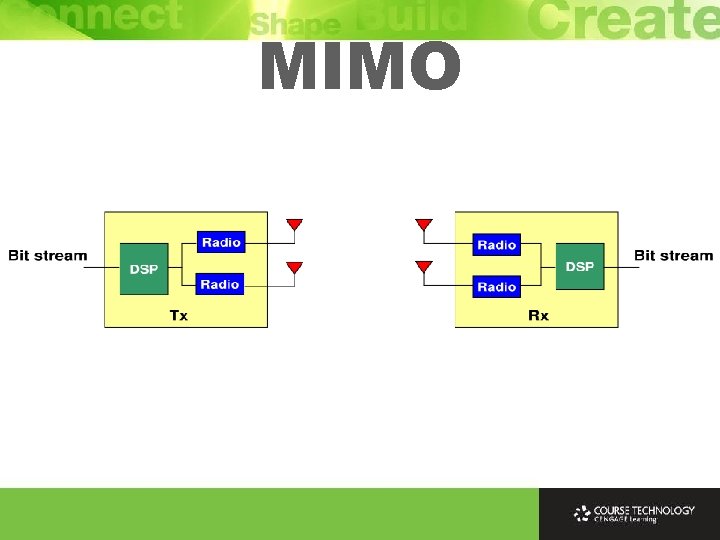 MIMO
MIMO
 The Next Generation of Wireless Local Area Networks 802. 11 n-2009 PHY Layer Spatial Multiplexing
The Next Generation of Wireless Local Area Networks 802. 11 n-2009 PHY Layer Spatial Multiplexing
 Multiple Antenna Techniques Ø Adding antennas can increase capacity even though antennas transmit and receive on same frequency band simultaneously Ø Changes fundamental relationship between power and capacity per second per Hz Ø 2 techniques can be used to take advantage of multiple streams
Multiple Antenna Techniques Ø Adding antennas can increase capacity even though antennas transmit and receive on same frequency band simultaneously Ø Changes fundamental relationship between power and capacity per second per Hz Ø 2 techniques can be used to take advantage of multiple streams
 Spatial Diversity Ø Spatial diversity techniques increase reliability and range by sending/receiving redundant streams in parallel along different spatial paths between transmit and receive antennas Ø Use of extra paths improves reliability because unlikely all of the paths will be degraded at the same time Ø Spatial diversity can also improve range and some performance increase (gather larger amount of signal at receiver)
Spatial Diversity Ø Spatial diversity techniques increase reliability and range by sending/receiving redundant streams in parallel along different spatial paths between transmit and receive antennas Ø Use of extra paths improves reliability because unlikely all of the paths will be degraded at the same time Ø Spatial diversity can also improve range and some performance increase (gather larger amount of signal at receiver)
 Spatial Diversity
Spatial Diversity
 RF Loss Ø Radio Frequency (RF) signals bounce impacted by types of objects and surfaces encounter Ø Many copies of the signal arrive at the receiver at different times having traveled along many different paths Ø Delay is enough cause significant degradation of signal at a single antenna because all copies interfere with first signal to arrive
RF Loss Ø Radio Frequency (RF) signals bounce impacted by types of objects and surfaces encounter Ø Many copies of the signal arrive at the receiver at different times having traveled along many different paths Ø Delay is enough cause significant degradation of signal at a single antenna because all copies interfere with first signal to arrive
 Absorption 41
Absorption 41
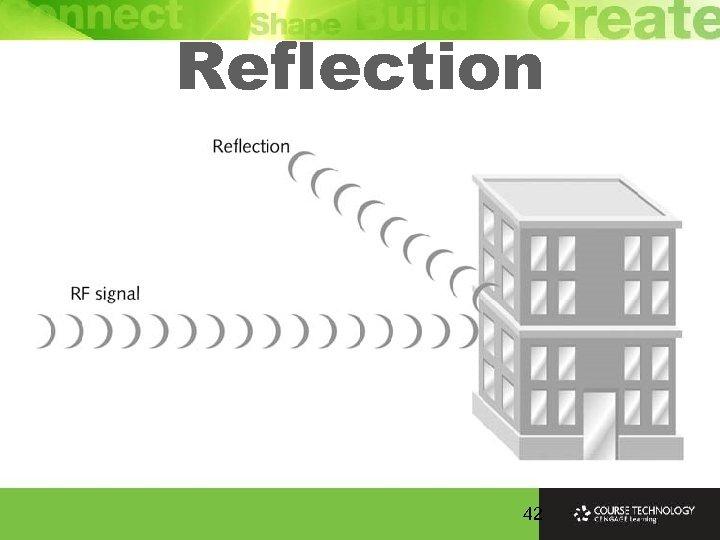 Reflection 42
Reflection 42
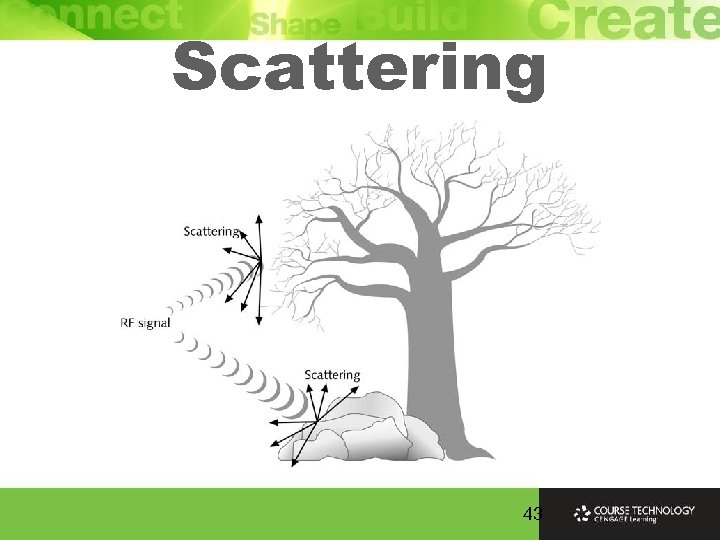 Scattering 43
Scattering 43
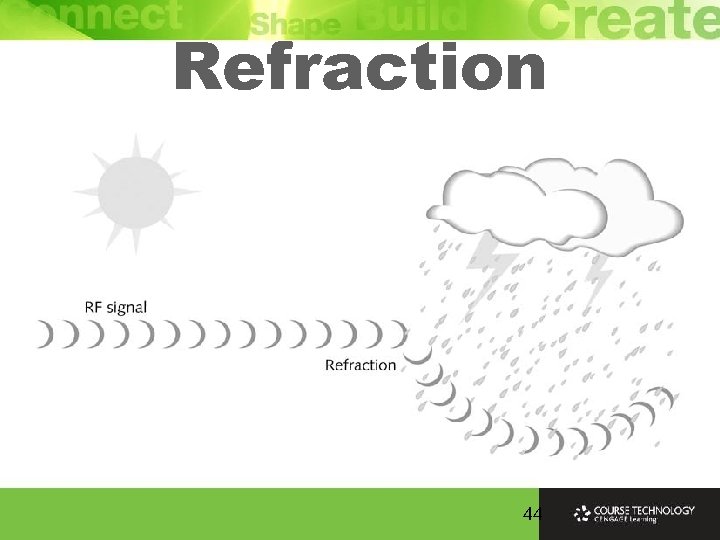 Refraction 44
Refraction 44
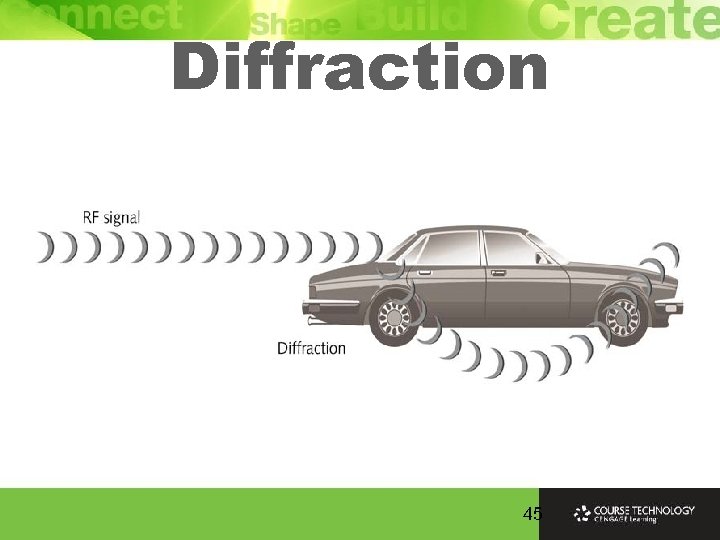 Diffraction 45
Diffraction 45
 Spatial Diversity Ø Spatial diversity can address RF loss Ø Each spatial stream sent from own antenna using its own transmitter Ø Because some space (10 centimeters) between each antennae, each signal follows slightly different path to receiver Ø Spatial diversity can address RF loss
Spatial Diversity Ø Spatial diversity can address RF loss Ø Each spatial stream sent from own antenna using its own transmitter Ø Because some space (10 centimeters) between each antennae, each signal follows slightly different path to receiver Ø Spatial diversity can address RF loss
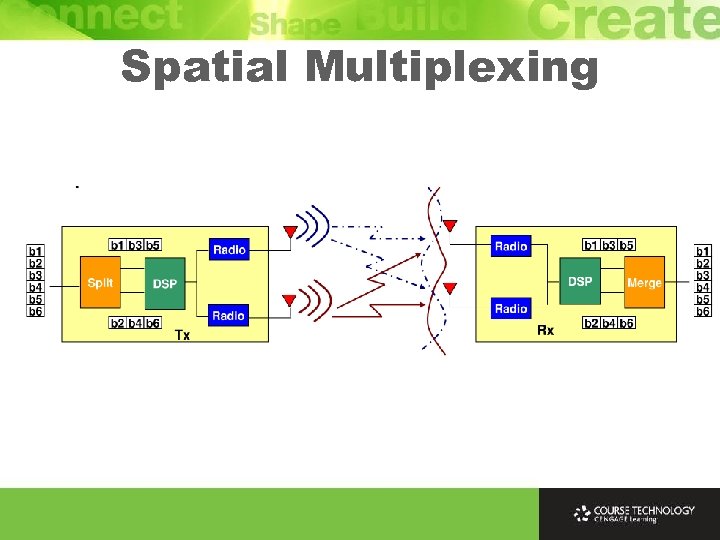
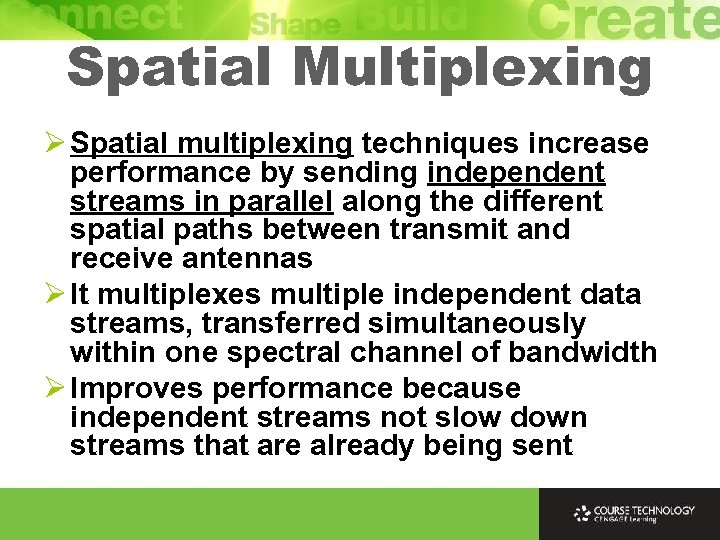 Spatial Multiplexing Ø Spatial multiplexing techniques increase performance by sending independent streams in parallel along the different spatial paths between transmit and receive antennas Ø It multiplexes multiple independent data streams, transferred simultaneously within one spectral channel of bandwidth Ø Improves performance because independent streams not slow down streams that are already being sent
Spatial Multiplexing Ø Spatial multiplexing techniques increase performance by sending independent streams in parallel along the different spatial paths between transmit and receive antennas Ø It multiplexes multiple independent data streams, transferred simultaneously within one spectral channel of bandwidth Ø Improves performance because independent streams not slow down streams that are already being sent
 Spatial Multiplexing
Spatial Multiplexing
 SISO vs. MIMO
SISO vs. MIMO
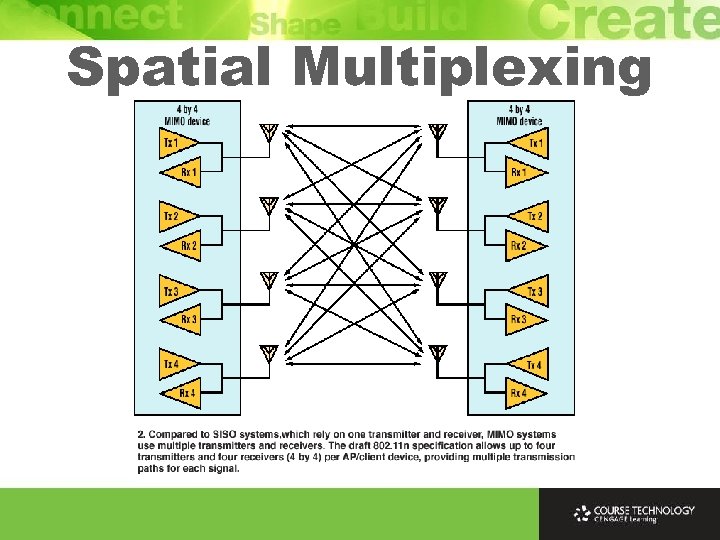
 Spatial Multiplexing Ø Independent paths between multiple antennas can be used to much greater effect than simply for diversity to overcome RF loss Ø Spatial multiplexing uses independent spatial paths to send independent streams of information at same time over the same frequencies Ø Streams will become combined as pass across channel Ø Receiver will separate and decode
Spatial Multiplexing Ø Independent paths between multiple antennas can be used to much greater effect than simply for diversity to overcome RF loss Ø Spatial multiplexing uses independent spatial paths to send independent streams of information at same time over the same frequencies Ø Streams will become combined as pass across channel Ø Receiver will separate and decode
 Spatial Multiplexing
Spatial Multiplexing
 Notation - 2 x 3: 2 Ø 2 - Maximum number of transmit antennas that can be used by the radio Ø 3 - Maximum number of receive antennas that can be used by the radio Ø 2 - Maximum number of data spatial streams the radio can use Ø Radio that can transmit on 2 antennas and receive on 3 but can only send or receive 2 data streams
Notation - 2 x 3: 2 Ø 2 - Maximum number of transmit antennas that can be used by the radio Ø 3 - Maximum number of receive antennas that can be used by the radio Ø 2 - Maximum number of data spatial streams the radio can use Ø Radio that can transmit on 2 antennas and receive on 3 but can only send or receive 2 data streams
 IEEE 802. 11 n Ø 802. 11 n allows up to 4 x 4: 4 ØCommon configurations of 11 n devices are 2 x 2: 2, 2 x 3: 2, 3 x 3: 2 Ø 3 x 3: 3 is becoming common because higher throughput due to additional data stream ØImprovements beyond 3 x 3 are small
IEEE 802. 11 n Ø 802. 11 n allows up to 4 x 4: 4 ØCommon configurations of 11 n devices are 2 x 2: 2, 2 x 3: 2, 3 x 3: 2 Ø 3 x 3: 3 is becoming common because higher throughput due to additional data stream ØImprovements beyond 3 x 3 are small
 The Next Generation of Wireless Local Area Networks 802. 11 n-2009 PHY Layer Channels
The Next Generation of Wireless Local Area Networks 802. 11 n-2009 PHY Layer Channels
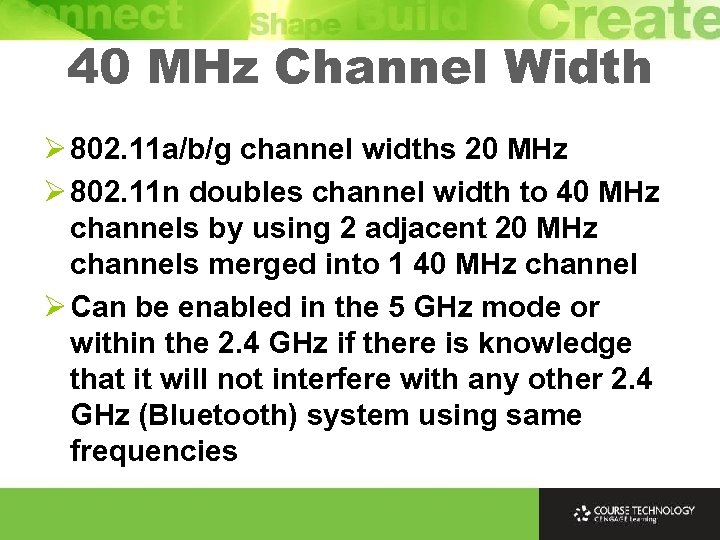 40 MHz Channel Width Ø 802. 11 a/b/g channel widths 20 MHz Ø 802. 11 n doubles channel width to 40 MHz channels by using 2 adjacent 20 MHz channels merged into 1 40 MHz channel Ø Can be enabled in the 5 GHz mode or within the 2. 4 GHz if there is knowledge that it will not interfere with any other 2. 4 GHz (Bluetooth) system using same frequencies
40 MHz Channel Width Ø 802. 11 a/b/g channel widths 20 MHz Ø 802. 11 n doubles channel width to 40 MHz channels by using 2 adjacent 20 MHz channels merged into 1 40 MHz channel Ø Can be enabled in the 5 GHz mode or within the 2. 4 GHz if there is knowledge that it will not interfere with any other 2. 4 GHz (Bluetooth) system using same frequencies
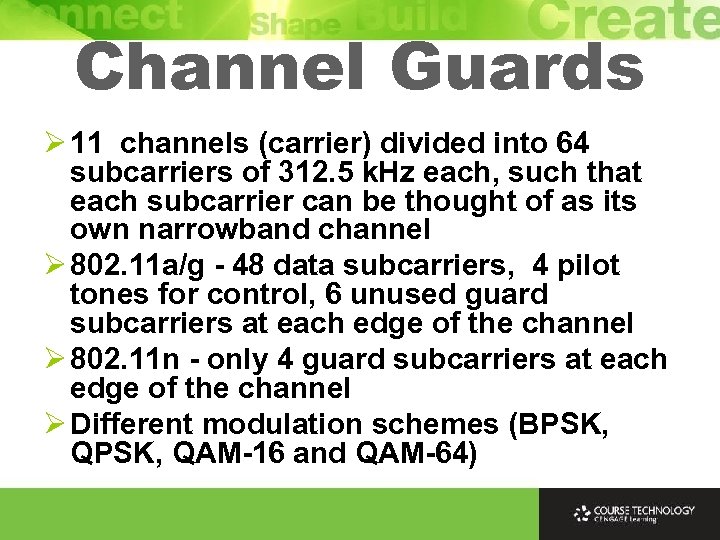 Channel Guards Ø 11 channels (carrier) divided into 64 subcarriers of 312. 5 k. Hz each, such that each subcarrier can be thought of as its own narrowband channel Ø 802. 11 a/g - 48 data subcarriers, 4 pilot tones for control, 6 unused guard subcarriers at each edge of the channel Ø 802. 11 n - only 4 guard subcarriers at each edge of the channel Ø Different modulation schemes (BPSK, QPSK, QAM-16 and QAM-64)
Channel Guards Ø 11 channels (carrier) divided into 64 subcarriers of 312. 5 k. Hz each, such that each subcarrier can be thought of as its own narrowband channel Ø 802. 11 a/g - 48 data subcarriers, 4 pilot tones for control, 6 unused guard subcarriers at each edge of the channel Ø 802. 11 n - only 4 guard subcarriers at each edge of the channel Ø Different modulation schemes (BPSK, QPSK, QAM-16 and QAM-64)
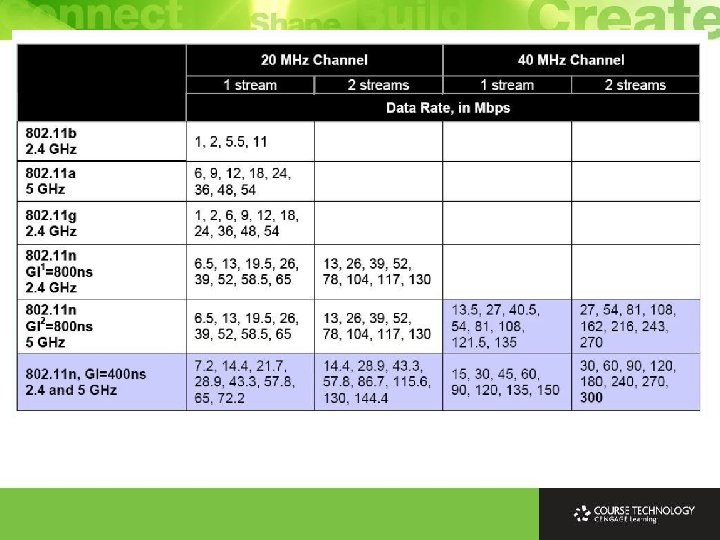
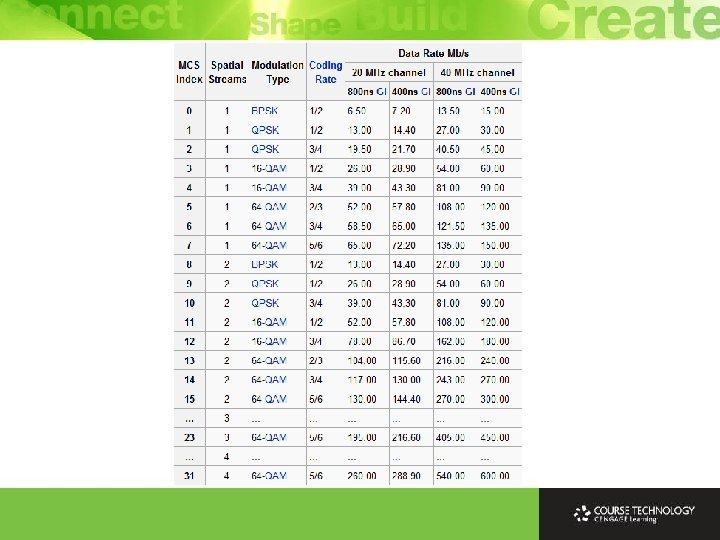
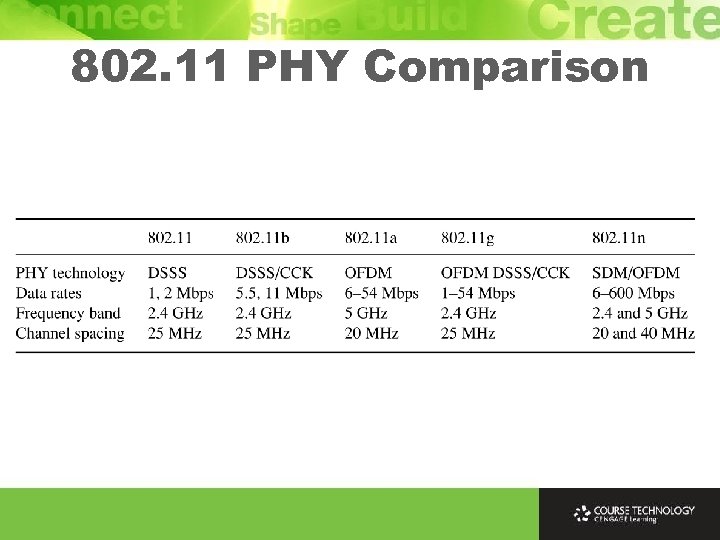 802. 11 PHY Comparison
802. 11 PHY Comparison
 The Next Generation of Wireless Local Area Networks 802. 11 n-2009 MAC Layer
The Next Generation of Wireless Local Area Networks 802. 11 n-2009 MAC Layer
 MAC Enhancements ØAggregation ØBlock acknowledgement ØTransmission opportunity
MAC Enhancements ØAggregation ØBlock acknowledgement ØTransmission opportunity
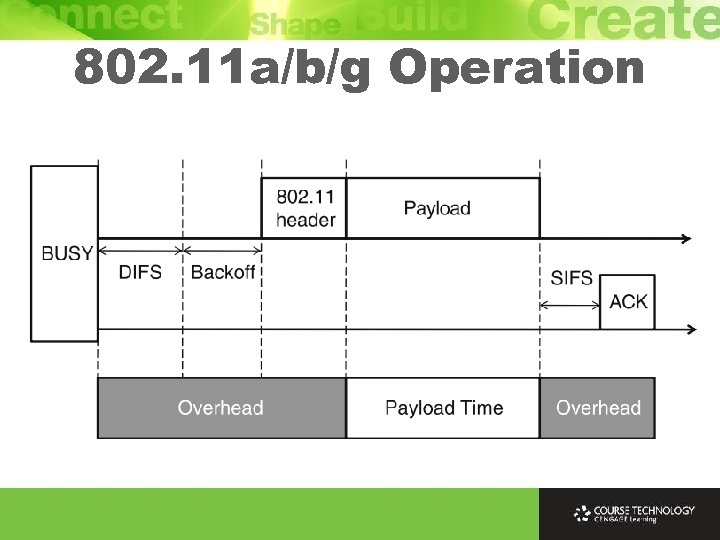 802. 11 a/b/g Operation
802. 11 a/b/g Operation
 The Next Generation of Wireless Local Area Networks 802. 11 n-2009 MAC Layer Aggregation
The Next Generation of Wireless Local Area Networks 802. 11 n-2009 MAC Layer Aggregation
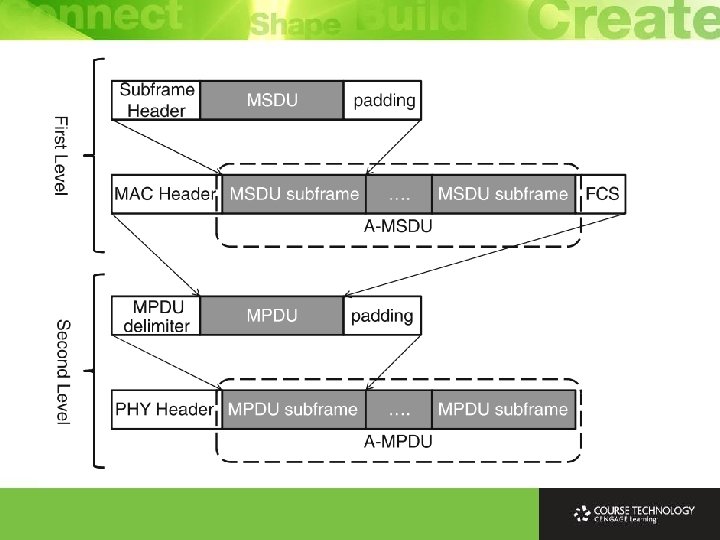
 Aggregation Ø Aggregation combines multiple data packets from upper layer into 1 larger aggregated data frame for transmission Ø Overhead in multiple frame transmissions reduced since header overhead and interframe time is saved
Aggregation Ø Aggregation combines multiple data packets from upper layer into 1 larger aggregated data frame for transmission Ø Overhead in multiple frame transmissions reduced since header overhead and interframe time is saved
 Aggregation Ø Aggregation of MAC Service Data Units (MSDUs) at top of the MAC (MSDU aggregation or A-MSDU) Ø Aggregation of MAC Protocol Data Units (MPDUs) at bottom of the MAC (MPDU aggregation or A-MPDU) Ø Aggregation packs multiple MSDUs or MPDUs together to reduce overheads and average them over multiple frames to increase data rate
Aggregation Ø Aggregation of MAC Service Data Units (MSDUs) at top of the MAC (MSDU aggregation or A-MSDU) Ø Aggregation of MAC Protocol Data Units (MPDUs) at bottom of the MAC (MPDU aggregation or A-MPDU) Ø Aggregation packs multiple MSDUs or MPDUs together to reduce overheads and average them over multiple frames to increase data rate
 A-MSDU & A-MPDU Ø A-MSDU is composed with multiple MSDUs Ø Created when MSDUs are received by the MAC layer Ø Multiple MPDUs are aggregated into a A-MPDU Ø A-MPDUs are created before sending to PHY layer for transmission.
A-MSDU & A-MPDU Ø A-MSDU is composed with multiple MSDUs Ø Created when MSDUs are received by the MAC layer Ø Multiple MPDUs are aggregated into a A-MPDU Ø A-MPDUs are created before sending to PHY layer for transmission.
 Aggregation
Aggregation
 The Next Generation of Wireless Local Area Networks 802. 11 n-2009 MAC Layer Block Acknowledgement
The Next Generation of Wireless Local Area Networks 802. 11 n-2009 MAC Layer Block Acknowledgement
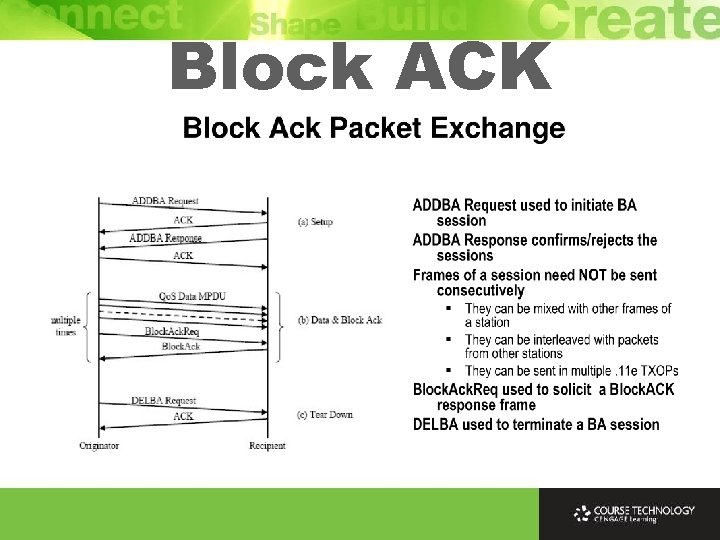
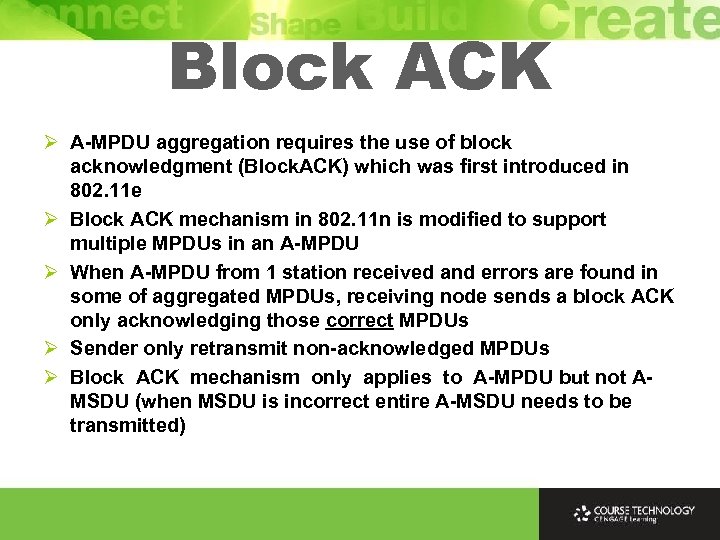 Block ACK Ø A-MPDU aggregation requires the use of block acknowledgment (Block. ACK) which was first introduced in 802. 11 e Ø Block ACK mechanism in 802. 11 n is modified to support multiple MPDUs in an A-MPDU Ø When A-MPDU from 1 station received and errors are found in some of aggregated MPDUs, receiving node sends a block ACK only acknowledging those correct MPDUs Ø Sender only retransmit non-acknowledged MPDUs Ø Block ACK mechanism only applies to A-MPDU but not AMSDU (when MSDU is incorrect entire A-MSDU needs to be transmitted)
Block ACK Ø A-MPDU aggregation requires the use of block acknowledgment (Block. ACK) which was first introduced in 802. 11 e Ø Block ACK mechanism in 802. 11 n is modified to support multiple MPDUs in an A-MPDU Ø When A-MPDU from 1 station received and errors are found in some of aggregated MPDUs, receiving node sends a block ACK only acknowledging those correct MPDUs Ø Sender only retransmit non-acknowledged MPDUs Ø Block ACK mechanism only applies to A-MPDU but not AMSDU (when MSDU is incorrect entire A-MSDU needs to be transmitted)
 Block ACK
Block ACK
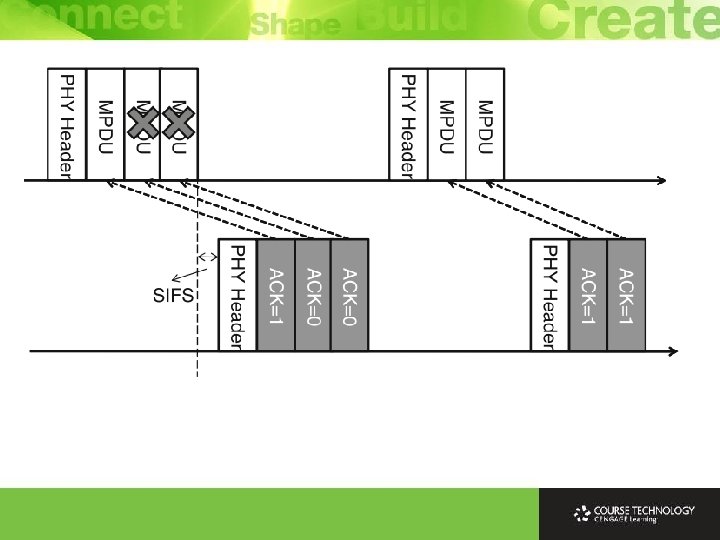
 Compressed Block ACK Ø Original Block ACK message in 802. 11 e contains Block ACK field with 64 × 2 bytes (2 bytes record fragment number of the MSDUs to be acknowledged) Ø Fragmentation MSDU is not allowed in 802. 11 n A-MPDU Ø 2 bytes can be reduced to 1 byte, and the block ACK bitmap is compressed to 64 bytes Ø Called compressed block ACK (overhead of block ACK is reduced) Ø Maximum number of MPDUs in 1 A-MPDU limited to 64 (1 block ACK can only acknowledge maximum 64) Ø Station transmitting multiple data frames can request one block ACK for all frames instead of using legacy acknowledgments to each frame
Compressed Block ACK Ø Original Block ACK message in 802. 11 e contains Block ACK field with 64 × 2 bytes (2 bytes record fragment number of the MSDUs to be acknowledged) Ø Fragmentation MSDU is not allowed in 802. 11 n A-MPDU Ø 2 bytes can be reduced to 1 byte, and the block ACK bitmap is compressed to 64 bytes Ø Called compressed block ACK (overhead of block ACK is reduced) Ø Maximum number of MPDUs in 1 A-MPDU limited to 64 (1 block ACK can only acknowledge maximum 64) Ø Station transmitting multiple data frames can request one block ACK for all frames instead of using legacy acknowledgments to each frame
 The Next Generation of Wireless Local Area Networks 802. 11 n-2009 MAC Layer Transmission Opportunity (TXOP) (Reverse Direction)
The Next Generation of Wireless Local Area Networks 802. 11 n-2009 MAC Layer Transmission Opportunity (TXOP) (Reverse Direction)
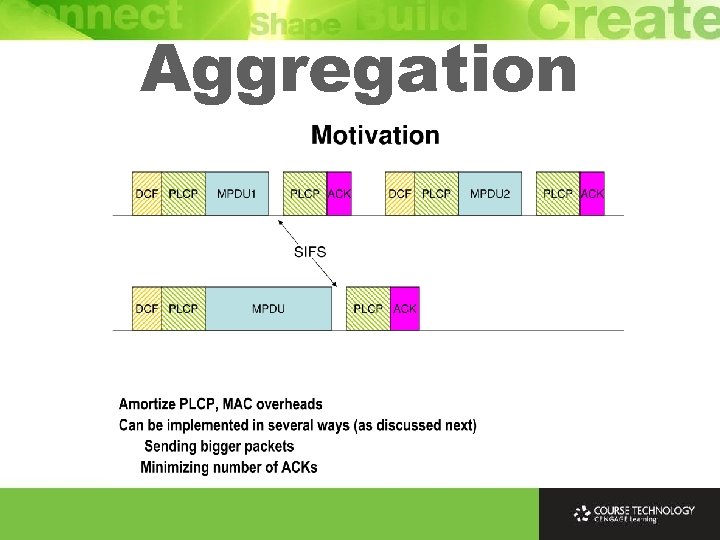
 CSMA/CA Ø 802. 11 standard uses Carrier Sense Multiple Access with Collision Avoidance (CSMA/CA) that attempts to avoid collisions Ø The time most collisions occur is immediately after a station completes its transmission, because all other stations wanting to transmit have been waiting to for medium to clear Ø Once medium is clear they all try to transmit at same time, which results in more collisions and delays Ø CMSA/CA has all stations wait a random amount of time (backoff interval) after medium is clear (slot time)
CSMA/CA Ø 802. 11 standard uses Carrier Sense Multiple Access with Collision Avoidance (CSMA/CA) that attempts to avoid collisions Ø The time most collisions occur is immediately after a station completes its transmission, because all other stations wanting to transmit have been waiting to for medium to clear Ø Once medium is clear they all try to transmit at same time, which results in more collisions and delays Ø CMSA/CA has all stations wait a random amount of time (backoff interval) after medium is clear (slot time)
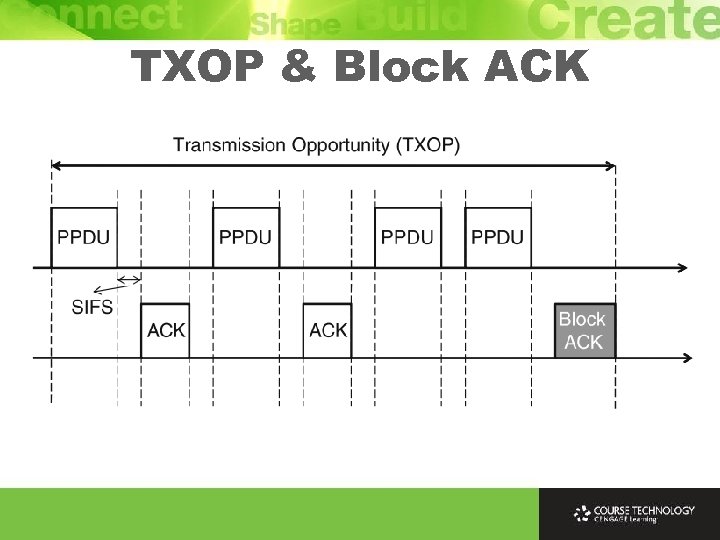
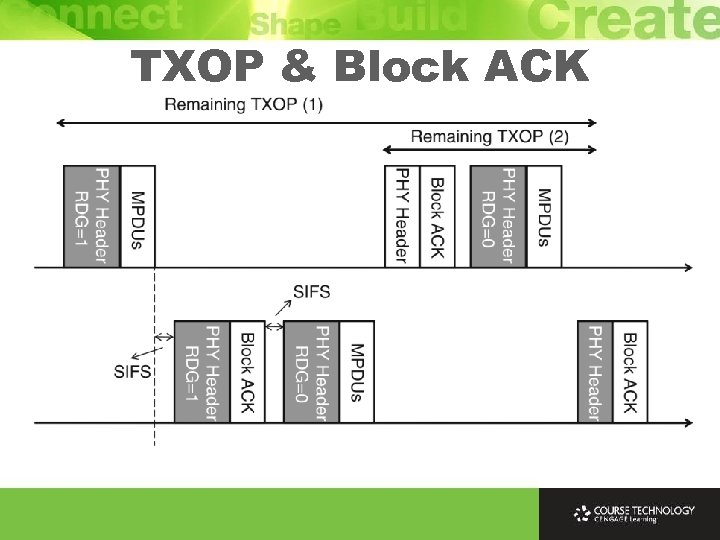
 Transmission Opportunity Ø Transmission opportunity (TXOP) defines period of time for station accessing channel to transmit multiple data frames Ø During TXOP period, station can transmit multiple data frames without entering backoff procedure Ø Reduces overhead due to contention and backoff and enhances efficiency of channel utilization
Transmission Opportunity Ø Transmission opportunity (TXOP) defines period of time for station accessing channel to transmit multiple data frames Ø During TXOP period, station can transmit multiple data frames without entering backoff procedure Ø Reduces overhead due to contention and backoff and enhances efficiency of channel utilization
 TXOP & Block ACK
TXOP & Block ACK
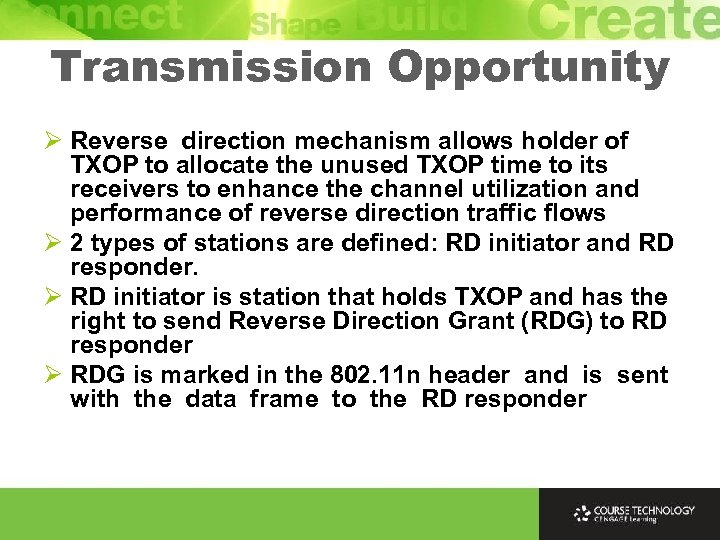 Transmission Opportunity Ø Reverse direction mechanism allows holder of TXOP to allocate the unused TXOP time to its receivers to enhance the channel utilization and performance of reverse direction traffic flows Ø 2 types of stations are defined: RD initiator and RD responder. Ø RD initiator is station that holds TXOP and has the right to send Reverse Direction Grant (RDG) to RD responder Ø RDG is marked in the 802. 11 n header and is sent with the data frame to the RD responder
Transmission Opportunity Ø Reverse direction mechanism allows holder of TXOP to allocate the unused TXOP time to its receivers to enhance the channel utilization and performance of reverse direction traffic flows Ø 2 types of stations are defined: RD initiator and RD responder. Ø RD initiator is station that holds TXOP and has the right to send Reverse Direction Grant (RDG) to RD responder Ø RDG is marked in the 802. 11 n header and is sent with the data frame to the RD responder
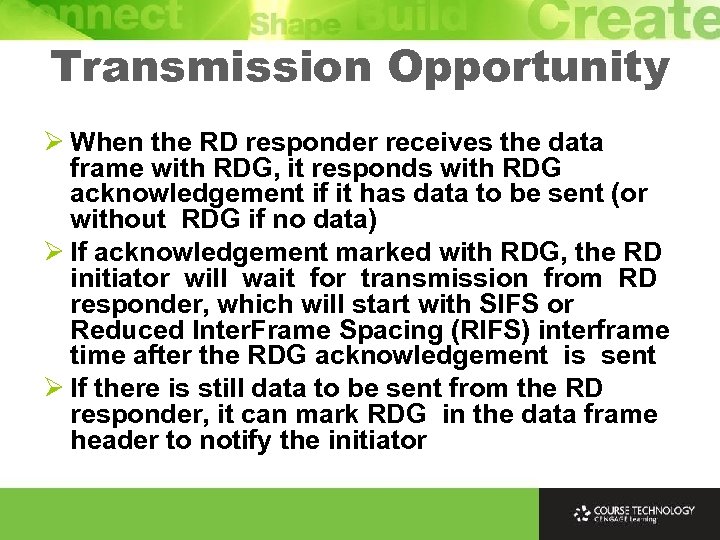 Transmission Opportunity Ø When the RD responder receives the data frame with RDG, it responds with RDG acknowledgement if it has data to be sent (or without RDG if no data) Ø If acknowledgement marked with RDG, the RD initiator will wait for transmission from RD responder, which will start with SIFS or Reduced Inter. Frame Spacing (RIFS) interframe time after the RDG acknowledgement is sent Ø If there is still data to be sent from the RD responder, it can mark RDG in the data frame header to notify the initiator
Transmission Opportunity Ø When the RD responder receives the data frame with RDG, it responds with RDG acknowledgement if it has data to be sent (or without RDG if no data) Ø If acknowledgement marked with RDG, the RD initiator will wait for transmission from RD responder, which will start with SIFS or Reduced Inter. Frame Spacing (RIFS) interframe time after the RDG acknowledgement is sent Ø If there is still data to be sent from the RD responder, it can mark RDG in the data frame header to notify the initiator
 TXOP & Block ACK
TXOP & Block ACK
 Transmission Opportunity Ø The RD initiator still has the right to accept the request Ø To reject the new RDG request, the initiator just ignores it Ø The major enhancement in reverse direction mechanism is the delay time reduction in reverse link traffic Ø Reverse direction data packets do not need to wait in queue until the station holds TXOP but can be transmitted immediately when the RD responder is allocated for the remaining TXOP Ø This feature can benefit a delay-sensitive service like Vo. IP
Transmission Opportunity Ø The RD initiator still has the right to accept the request Ø To reject the new RDG request, the initiator just ignores it Ø The major enhancement in reverse direction mechanism is the delay time reduction in reverse link traffic Ø Reverse direction data packets do not need to wait in queue until the station holds TXOP but can be transmitted immediately when the RD responder is allocated for the remaining TXOP Ø This feature can benefit a delay-sensitive service like Vo. IP
 The Next Generation of Wireless Local Area Networks 802. 11 n-2009 Security
The Next Generation of Wireless Local Area Networks 802. 11 n-2009 Security
 Wi-Fi Protected Access 2 (WPA 2) Ø Wi-Fi Alliance introduced Wi-Fi Protected Access 2 (WPA 2) in Sep 2004 Ø WPA 2 based on the final IEEE 802. 11 i Ø WPA 2 uses AES for data encryption and supports authentication server or PSK technology Ø WPA 2 allows both AES and TKIP clients to operate in the same WLAN; IEEE 802. 11 i only recognizes AES 84
Wi-Fi Protected Access 2 (WPA 2) Ø Wi-Fi Alliance introduced Wi-Fi Protected Access 2 (WPA 2) in Sep 2004 Ø WPA 2 based on the final IEEE 802. 11 i Ø WPA 2 uses AES for data encryption and supports authentication server or PSK technology Ø WPA 2 allows both AES and TKIP clients to operate in the same WLAN; IEEE 802. 11 i only recognizes AES 84
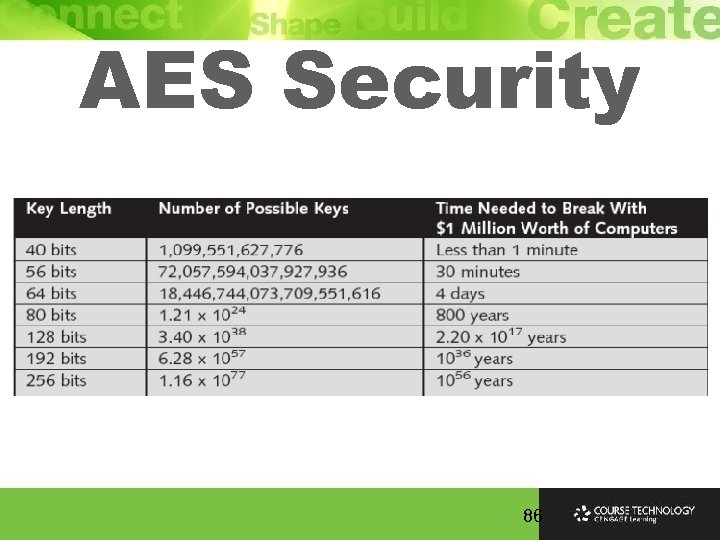
 AES Ø AES algorithm processes blocks of 128 bits, yet the length of the cipher keys and number of rounds can vary, depending upon the level of security that is required Ø Available key lengths are of 128, 192 and 256 bits, and the number of available rounds are 10, 12, and 14 Ø Only the 128 -bit key and 128 -bit block are mandatory for WPA 2 Ø It is recommended that AES encryption and decryption be performed in hardware because of the computationally intensive nature of AES 85
AES Ø AES algorithm processes blocks of 128 bits, yet the length of the cipher keys and number of rounds can vary, depending upon the level of security that is required Ø Available key lengths are of 128, 192 and 256 bits, and the number of available rounds are 10, 12, and 14 Ø Only the 128 -bit key and 128 -bit block are mandatory for WPA 2 Ø It is recommended that AES encryption and decryption be performed in hardware because of the computationally intensive nature of AES 85
 AES Security 86
AES Security 86
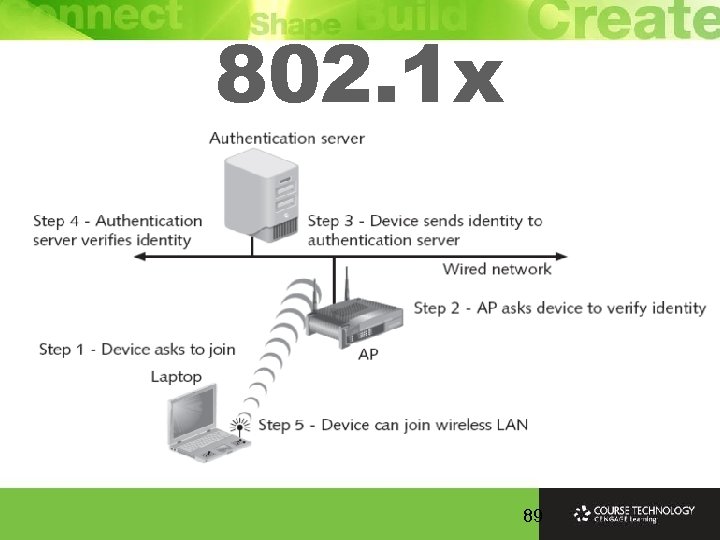
 802. 1 x Ø IEEE 802. 11 i authentication and key management uses IEEE 802. 1 x (originally developed for wired networks) Ø 802. 1 x port security (device requests access to network prevented from receiving any traffic until its identity can be verified) Ø 802. 1 x blocks all traffic on port-by-port basis until the client is authenticated using credentials stored on authentication server 87
802. 1 x Ø IEEE 802. 11 i authentication and key management uses IEEE 802. 1 x (originally developed for wired networks) Ø 802. 1 x port security (device requests access to network prevented from receiving any traffic until its identity can be verified) Ø 802. 1 x blocks all traffic on port-by-port basis until the client is authenticated using credentials stored on authentication server 87
 802. 1 x Authentication Ø The supplicant is device which requires secure network access and sends request to an authenticator that serves as an intermediary device (authenticator can be an access point on a wireless network or a switch on a wired network) Ø The authenticator sends request from supplicant to authentication server, which accepts/rejects the supplicant’s request and sends that information back to the authenticator, which in turn grants or denies access to the supplicant Ø Strength of the 802. 1 x protocol is that supplicant never has direct communication with authentication server 88
802. 1 x Authentication Ø The supplicant is device which requires secure network access and sends request to an authenticator that serves as an intermediary device (authenticator can be an access point on a wireless network or a switch on a wired network) Ø The authenticator sends request from supplicant to authentication server, which accepts/rejects the supplicant’s request and sends that information back to the authenticator, which in turn grants or denies access to the supplicant Ø Strength of the 802. 1 x protocol is that supplicant never has direct communication with authentication server 88
 802. 1 x 89
802. 1 x 89
 802. 11 n Security Ø All 802. 11 n products are required to support WPA 2 Ø Advanced Encryption Standard (AES) Ø Pre-shared key (PSK) or 802. 1 X authentication Ø Caveat Ø WLANs that must support both 802. 11 a/b/g and 802. 11 n clients may be forced to permit TKIP Ø Doing so makes it possible for older non-AES clients to connect securely. Ø 802. 11 n prohibits high-throughput data rates when using TKIP
802. 11 n Security Ø All 802. 11 n products are required to support WPA 2 Ø Advanced Encryption Standard (AES) Ø Pre-shared key (PSK) or 802. 1 X authentication Ø Caveat Ø WLANs that must support both 802. 11 a/b/g and 802. 11 n clients may be forced to permit TKIP Ø Doing so makes it possible for older non-AES clients to connect securely. Ø 802. 11 n prohibits high-throughput data rates when using TKIP
 Adding Clients Ø 3 new methods for securely adding clients to 802. 11 n network Ø Shifts security setup responsibility from the user to the network itself Ø Avoids end-user configuration of security parameters reduces confusion and error Ø Can eliminate the need for manual WLAN configuration interfaces Ø Called Wi-Fi Protected Setup (WPS)
Adding Clients Ø 3 new methods for securely adding clients to 802. 11 n network Ø Shifts security setup responsibility from the user to the network itself Ø Avoids end-user configuration of security parameters reduces confusion and error Ø Can eliminate the need for manual WLAN configuration interfaces Ø Called Wi-Fi Protected Setup (WPS)
 Personal Information Number (PIN) Ø All devices are associated with a unique number printed on device or its packaging, or displayed by device Ø To enroll a device, its PIN is entered into a "WPS registrar“ (usually configuration page on AP) Ø Registrar and device complete a secure over-the-air WPS handshake, during which registrar assigns random PSK to the device Ø The device then self-enables WPA 2 -PSK, using those WPS-supplied SSID and PSK values
Personal Information Number (PIN) Ø All devices are associated with a unique number printed on device or its packaging, or displayed by device Ø To enroll a device, its PIN is entered into a "WPS registrar“ (usually configuration page on AP) Ø Registrar and device complete a secure over-the-air WPS handshake, during which registrar assigns random PSK to the device Ø The device then self-enables WPA 2 -PSK, using those WPS-supplied SSID and PSK values
 Push-Button Configuration (PBC) Ø Physical WPS buttons must be pushed simultaneously on AP and device to be registered Ø For a short period, the AP listens for and accepts any nearby device requesting WPS enrollment Ø Method eliminates PIN entry but creates a brief window of opportunity during which unauthorized devices might conceivably be added
Push-Button Configuration (PBC) Ø Physical WPS buttons must be pushed simultaneously on AP and device to be registered Ø For a short period, the AP listens for and accepts any nearby device requesting WPS enrollment Ø Method eliminates PIN entry but creates a brief window of opportunity during which unauthorized devices might conceivably be added
 Near-Field Communication (NFC) Ø When NFC-enabled client device is placed within 10 centimeters of the NFC "target mark" on AP, the WPS registrar uses NFC communication to read client's identity from a token embedded in device Ø Once approved, that device is given the SSID and PSK that it needs to complete automated WPA 2 -PSK setup and join the WLAN
Near-Field Communication (NFC) Ø When NFC-enabled client device is placed within 10 centimeters of the NFC "target mark" on AP, the WPS registrar uses NFC communication to read client's identity from a token embedded in device Ø Once approved, that device is given the SSID and PSK that it needs to complete automated WPA 2 -PSK setup and join the WLAN
 The Next Generation of Wireless Local Area Networks Deployment Strategies & Summary
The Next Generation of Wireless Local Area Networks Deployment Strategies & Summary
 Operation Modes Ø 3 modes of operation ØNon-HT = Follows 802. 11 a/b/g mode ØGreenfield = No backward compatibility ØMixed = Addresses compatibility with legacy 802. 11 a/b/g devices
Operation Modes Ø 3 modes of operation ØNon-HT = Follows 802. 11 a/b/g mode ØGreenfield = No backward compatibility ØMixed = Addresses compatibility with legacy 802. 11 a/b/g devices
 Mixed Mode Ø Backward compatibility with existing 802. 11 a/b/g devices that allows older devices to understand information necessary to allow 802. 11 n devices to operate in same area Ø Mixed mode protection mechanism for 802. 11 n similar to protection mechanism of 802. 11 g Ø 802. 11 n transmits a radio preamble and signal field (control frame) in 20 MHz can be decoded by 802. 11 a/g and gives enough information allow a/g to know another transmission on air and how long transmission will last Ø After sending this legacy preamble and signal field 802. 11 n device sends remaining information using 802. 11 n rates and its multiple spatial streams, including an 802. 11 n preamble and signal field Ø Performance impact on 802. 11 n devices
Mixed Mode Ø Backward compatibility with existing 802. 11 a/b/g devices that allows older devices to understand information necessary to allow 802. 11 n devices to operate in same area Ø Mixed mode protection mechanism for 802. 11 n similar to protection mechanism of 802. 11 g Ø 802. 11 n transmits a radio preamble and signal field (control frame) in 20 MHz can be decoded by 802. 11 a/g and gives enough information allow a/g to know another transmission on air and how long transmission will last Ø After sending this legacy preamble and signal field 802. 11 n device sends remaining information using 802. 11 n rates and its multiple spatial streams, including an 802. 11 n preamble and signal field Ø Performance impact on 802. 11 n devices
 Wi-Fi Draft 2 Certification Ø IEEE ratified 802. 11 n standard Sep 2009 Ø Wi-Fi Alliance certifying products based on Draft 2. 0 since 2007 Ø Covers both 20 MHz and 40 MHz wide channels Ø Maximum 2 spatial streams Ø Maximum throughputs of 144. 4 Mbps for 20 MHz and 300 Mbps for 40 MHz Ø “Wi-Fi CERTIFIED n products must be backward compatible. . . However, keep in mind that Wi-Fi CERTIFIED 802. 11 n draft 2. 0 devices may not include some of the advanced features included in Wi-Fi CERTIFIED n products. ”
Wi-Fi Draft 2 Certification Ø IEEE ratified 802. 11 n standard Sep 2009 Ø Wi-Fi Alliance certifying products based on Draft 2. 0 since 2007 Ø Covers both 20 MHz and 40 MHz wide channels Ø Maximum 2 spatial streams Ø Maximum throughputs of 144. 4 Mbps for 20 MHz and 300 Mbps for 40 MHz Ø “Wi-Fi CERTIFIED n products must be backward compatible. . . However, keep in mind that Wi-Fi CERTIFIED 802. 11 n draft 2. 0 devices may not include some of the advanced features included in Wi-Fi CERTIFIED n products. ”
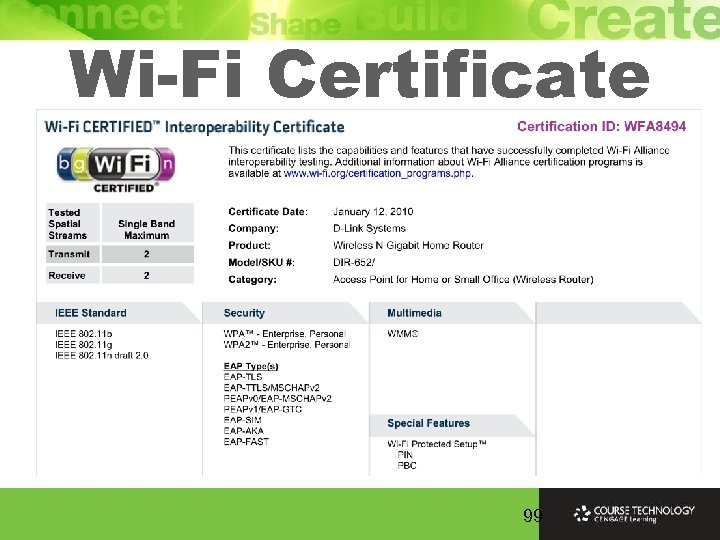 Wi-Fi Certificate 99
Wi-Fi Certificate 99
 Device Categories Ø Low (under $90) - Don't need maximum performance, but who can benefit from 802. 11 n's improved range and speed Ø Midrange ($90 -$150) – Fast wireless speeds and Gigabit Ethernet Ø High ($150 -$200) - Dual-band routers that support both 2. 4 GHz and 5 GHz for networked multimedia devices that need uncluttered bandwidth to stream media
Device Categories Ø Low (under $90) - Don't need maximum performance, but who can benefit from 802. 11 n's improved range and speed Ø Midrange ($90 -$150) – Fast wireless speeds and Gigabit Ethernet Ø High ($150 -$200) - Dual-band routers that support both 2. 4 GHz and 5 GHz for networked multimedia devices that need uncluttered bandwidth to stream media
 Deployment Strategies Ø To achieve maximum output pure 802. 11 n 5 GHz network is recommended (has substantial capacity due to many non-overlapping radio channels and less radio interference) Ø Yet 802. 11 n-only network may be impractical because requires replacement of 802. 11 b/g wireless NIC adapters Ø May be more practical in short term to operate mixed wireless network Ø Use 802. 11 n dual-band router and put older 802. 11 b/g traffic on 2. 4 GHz and newer 802. 11 n traffic on 5 GHz
Deployment Strategies Ø To achieve maximum output pure 802. 11 n 5 GHz network is recommended (has substantial capacity due to many non-overlapping radio channels and less radio interference) Ø Yet 802. 11 n-only network may be impractical because requires replacement of 802. 11 b/g wireless NIC adapters Ø May be more practical in short term to operate mixed wireless network Ø Use 802. 11 n dual-band router and put older 802. 11 b/g traffic on 2. 4 GHz and newer 802. 11 n traffic on 5 GHz
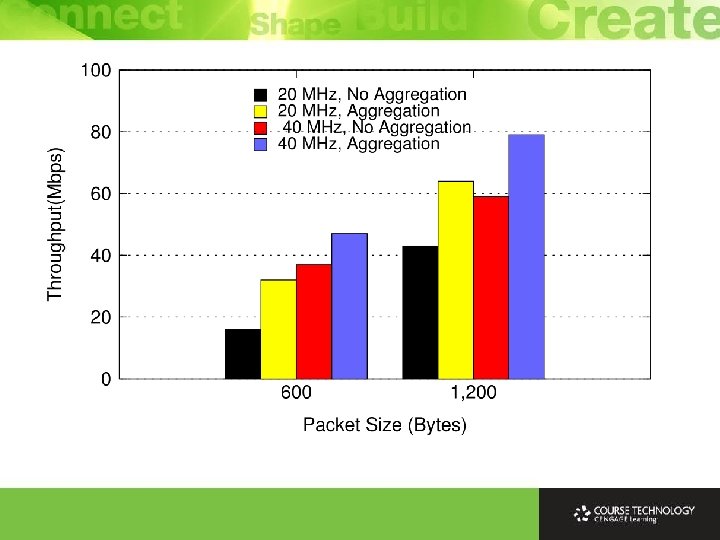
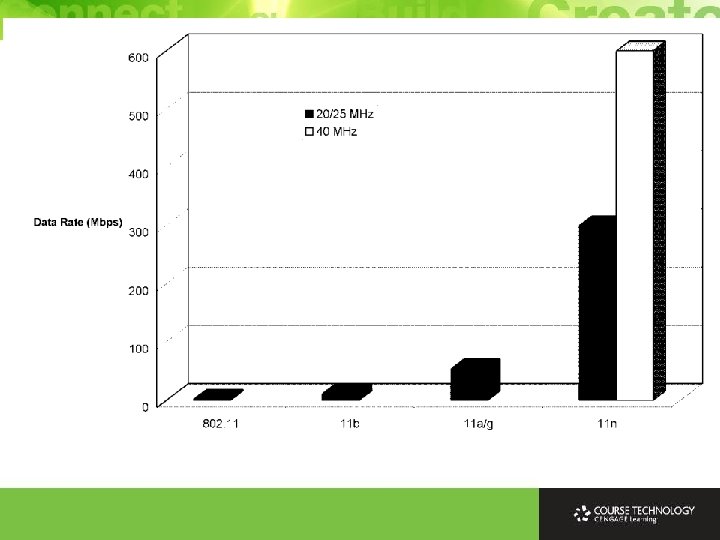
 Throughput Increases Ø Highest data rate in 802. 11 a/g is 54 Mbps vs. highest data rate in 802. 11 n is 600 Mbps Ø Increase of a factor of 11 Ø 40% - Use of 4 antennas Ø 20% - Double width channels of 40 MHz Ø 40% - Tweaking coding to reduce overhead. Ø Yet many devices may not have 4 antennas Ø Up to 3 antennas are commonly supported by NICs Ø Expected that clients will tend to have fewer antennas for space and power reasons, while APs will tend to have more antennas for performance reasons
Throughput Increases Ø Highest data rate in 802. 11 a/g is 54 Mbps vs. highest data rate in 802. 11 n is 600 Mbps Ø Increase of a factor of 11 Ø 40% - Use of 4 antennas Ø 20% - Double width channels of 40 MHz Ø 40% - Tweaking coding to reduce overhead. Ø Yet many devices may not have 4 antennas Ø Up to 3 antennas are commonly supported by NICs Ø Expected that clients will tend to have fewer antennas for space and power reasons, while APs will tend to have more antennas for performance reasons
 Range
Range
 The Next Generation of Wireless Local Area Networks Mark Ciampa Mark. Ciampa@wku. edu
The Next Generation of Wireless Local Area Networks Mark Ciampa Mark. Ciampa@wku. edu


