712c2151a9b72434ced9b5bd711eeb42.ppt
- Количество слайдов: 15
 The Leader in Application Data Security and Compliance Thomas Drews, SE CEEU
The Leader in Application Data Security and Compliance Thomas Drews, SE CEEU
 Security and Compliance Requirements § Full Visibility § Who is accessing your data? § Who has accessed your data? § Granular Controls § Who is attacking your data and how? § Is your data leaking outside the organization? § How do you protect your data? Imperva delivers the industry’s most robust and widely deployed solution for addressing the entire application data security and compliance lifecycle. 3 - CONFIDENTIAL -
Security and Compliance Requirements § Full Visibility § Who is accessing your data? § Who has accessed your data? § Granular Controls § Who is attacking your data and how? § Is your data leaking outside the organization? § How do you protect your data? Imperva delivers the industry’s most robust and widely deployed solution for addressing the entire application data security and compliance lifecycle. 3 - CONFIDENTIAL -
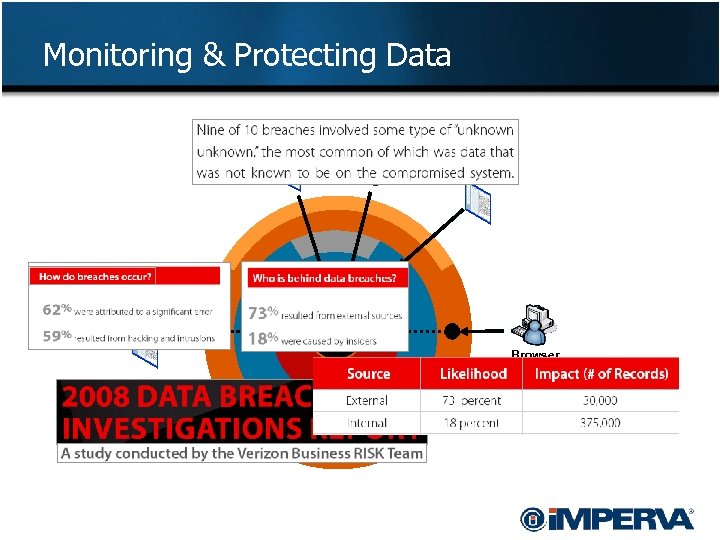 Monitoring & Protecting Data Thick Client 2 Tier App DBA Thin Client 3 Tier Application Interface Data SQL Applications Web/Web services Browser
Monitoring & Protecting Data Thick Client 2 Tier App DBA Thin Client 3 Tier Application Interface Data SQL Applications Web/Web services Browser
 Imperva Overview § Founded in 2002 § The leader in Application Data Security and Compliance § Global company with int’l revenue consisting of 40%+ § § North American HQ in California; International HQ in Israel Local presence in all major markets (EMEA, APAC, Japan) Customers in 30 countries Strong global network of channel partners § 600+ customers and over 4500 organizations protected § Shlomo Kramer, CEO & President § One of 3 founders of Check Point 5 - CONFIDENTIAL -
Imperva Overview § Founded in 2002 § The leader in Application Data Security and Compliance § Global company with int’l revenue consisting of 40%+ § § North American HQ in California; International HQ in Israel Local presence in all major markets (EMEA, APAC, Japan) Customers in 30 countries Strong global network of channel partners § 600+ customers and over 4500 organizations protected § Shlomo Kramer, CEO & President § One of 3 founders of Check Point 5 - CONFIDENTIAL -
 Secure. Sphere Dominates Awards Editor’s Choice for Database Extrusion Prevention Imperva Wins e. WEEK Excellence Award §“Right from the start, the Imperva Secure. Sphere Database Security Gateway impressed us with its plethora of features…dynamic user profiling is almost reason enough to choose it. Editor’s Choice for Web Application Firewalls “From beginning to end, Imperva Secure. Sphere is our kind of WAF. ” 6 §“Imperva Secure. Sphere’s … in-line protection for both Web applications and communications with back-end databases is simply unmatched. ” Imperva Wins 2007 Readers’ Choice Award from Security Magazine “Secure. Sphere scored well in every criteria: granularity of access controls and integration with existing infrastructure, scalability and management…” - CONFIDENTIAL - “Imperva's Secure. Sphere Database Security Gateway is a win on both counts. It did a fine job learning our user behavior, and numerous signatures let it handily block known attacks. ”
Secure. Sphere Dominates Awards Editor’s Choice for Database Extrusion Prevention Imperva Wins e. WEEK Excellence Award §“Right from the start, the Imperva Secure. Sphere Database Security Gateway impressed us with its plethora of features…dynamic user profiling is almost reason enough to choose it. Editor’s Choice for Web Application Firewalls “From beginning to end, Imperva Secure. Sphere is our kind of WAF. ” 6 §“Imperva Secure. Sphere’s … in-line protection for both Web applications and communications with back-end databases is simply unmatched. ” Imperva Wins 2007 Readers’ Choice Award from Security Magazine “Secure. Sphere scored well in every criteria: granularity of access controls and integration with existing infrastructure, scalability and management…” - CONFIDENTIAL - “Imperva's Secure. Sphere Database Security Gateway is a win on both counts. It did a fine job learning our user behavior, and numerous signatures let it handily block known attacks. ”
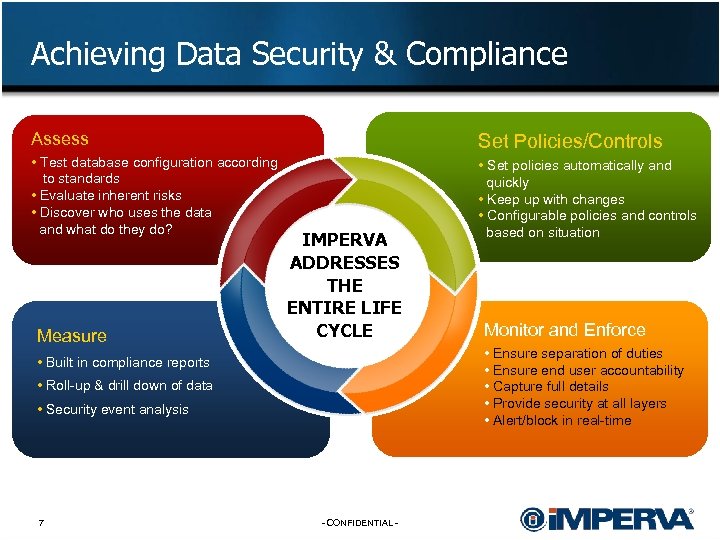 Achieving Data Security & Compliance Assess Set Policies/Controls • Test database configuration according to standards • Evaluate inherent risks • Discover who uses the data and what do they do? • Set policies automatically and quickly • Keep up with changes • Configurable policies and controls based on situation Measure IMPERVA ADDRESSES THE ENTIRE LIFE CYCLE • Ensure separation of duties • Ensure end user accountability • Capture full details • Provide security at all layers • Alert/block in real-time • Built in compliance reports • Roll-up & drill down of data • Security event analysis 7 Monitor and Enforce - CONFIDENTIAL -
Achieving Data Security & Compliance Assess Set Policies/Controls • Test database configuration according to standards • Evaluate inherent risks • Discover who uses the data and what do they do? • Set policies automatically and quickly • Keep up with changes • Configurable policies and controls based on situation Measure IMPERVA ADDRESSES THE ENTIRE LIFE CYCLE • Ensure separation of duties • Ensure end user accountability • Capture full details • Provide security at all layers • Alert/block in real-time • Built in compliance reports • Roll-up & drill down of data • Security event analysis 7 Monitor and Enforce - CONFIDENTIAL -
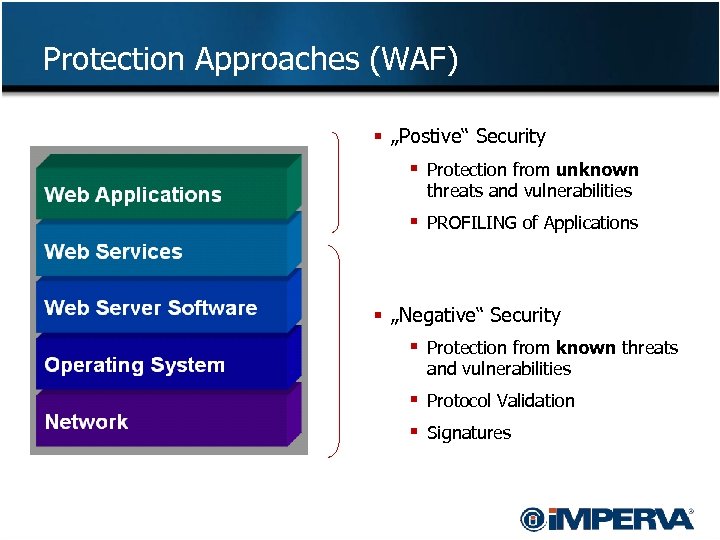 Protection Approaches (WAF) § „Postive“ Security § Protection from unknown threats and vulnerabilities § PROFILING of Applications § „Negative“ Security § Protection from known threats and vulnerabilities § Protocol Validation § Signatures
Protection Approaches (WAF) § „Postive“ Security § Protection from unknown threats and vulnerabilities § PROFILING of Applications § „Negative“ Security § Protection from known threats and vulnerabilities § Protocol Validation § Signatures
 Efficient Deployment and Operations No Impact to IT, Easily Managed, Low TCO
Efficient Deployment and Operations No Impact to IT, Easily Managed, Low TCO
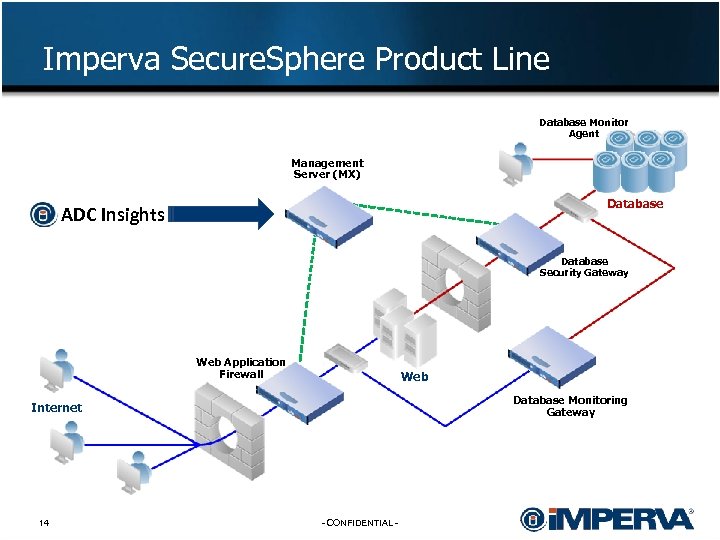 Imperva Secure. Sphere Product Line Database Monitor Agent Management Server (MX) Database ADC Insights Database Security Gateway Web Application Firewall Web Database Monitoring Gateway Internet 14 - CONFIDENTIAL -
Imperva Secure. Sphere Product Line Database Monitor Agent Management Server (MX) Database ADC Insights Database Security Gateway Web Application Firewall Web Database Monitoring Gateway Internet 14 - CONFIDENTIAL -
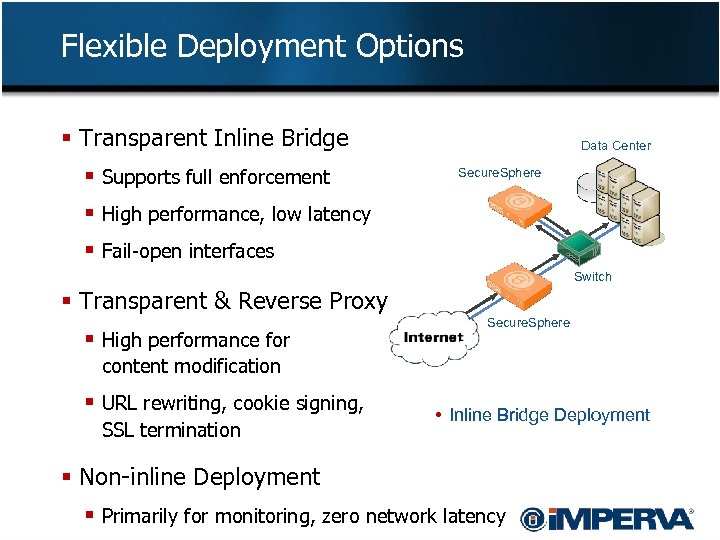 Flexible Deployment Options § Transparent Inline Bridge § Supports full enforcement Data Center Secure. Sphere § High performance, low latency § Fail-open interfaces Switch § Transparent & Reverse Proxy § High performance for Secure. Sphere content modification § URL rewriting, cookie signing, SSL termination • Reverse Proxy Deployment • • Inline Bridge Deployment Non-Inline Deployment § Non-inline Deployment § Primarily for monitoring, zero network latency
Flexible Deployment Options § Transparent Inline Bridge § Supports full enforcement Data Center Secure. Sphere § High performance, low latency § Fail-open interfaces Switch § Transparent & Reverse Proxy § High performance for Secure. Sphere content modification § URL rewriting, cookie signing, SSL termination • Reverse Proxy Deployment • • Inline Bridge Deployment Non-Inline Deployment § Non-inline Deployment § Primarily for monitoring, zero network latency
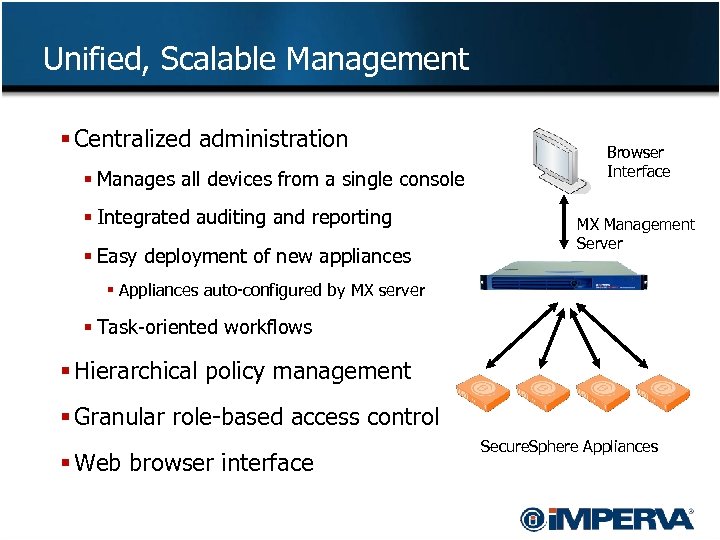 Unified, Scalable Management § Centralized administration § Manages all devices from a single console § Integrated auditing and reporting § Easy deployment of new appliances Browser Interface MX Management Server § Appliances auto-configured by MX server § Task-oriented workflows § Hierarchical policy management § Granular role-based access control § Web browser interface Secure. Sphere Appliances
Unified, Scalable Management § Centralized administration § Manages all devices from a single console § Integrated auditing and reporting § Easy deployment of new appliances Browser Interface MX Management Server § Appliances auto-configured by MX server § Task-oriented workflows § Hierarchical policy management § Granular role-based access control § Web browser interface Secure. Sphere Appliances
 Introducing Secure. Sphere § Only complete solution for enterprise data that includes: § Data activity monitoring § Real-time data protection § Full visibility and granular control of data usage § From end user through application and into database § Full stack protection § Unmatched ease-of-use and ease-of-deployment
Introducing Secure. Sphere § Only complete solution for enterprise data that includes: § Data activity monitoring § Real-time data protection § Full visibility and granular control of data usage § From end user through application and into database § Full stack protection § Unmatched ease-of-use and ease-of-deployment
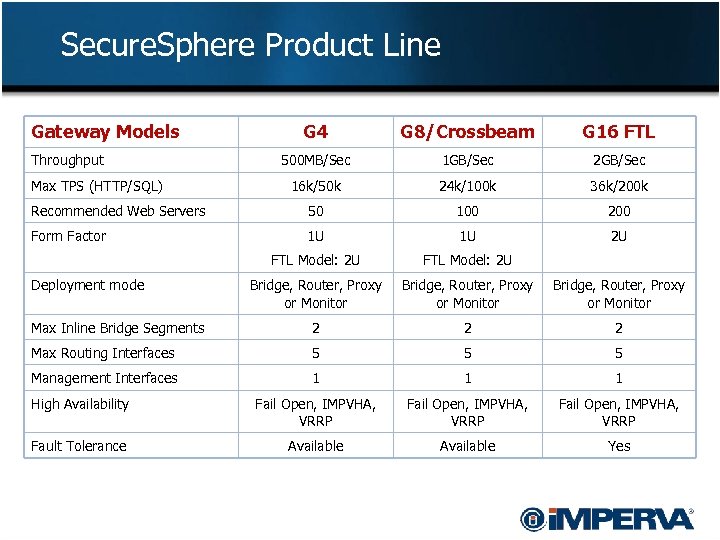 Secure. Sphere Product Line Gateway Models G 4 G 8/Crossbeam G 16 FTL 500 MB/Sec 1 GB/Sec 2 GB/Sec 16 k/50 k 24 k/100 k 36 k/200 k Recommended Web Servers 50 100 200 Form Factor 1 U 1 U 2 U FTL Model: 2 U Bridge, Router, Proxy or Monitor Max Inline Bridge Segments 2 2 2 Max Routing Interfaces 5 5 5 Management Interfaces 1 1 1 High Availability Fail Open, IMPVHA, VRRP Fault Tolerance Available Yes Throughput Max TPS (HTTP/SQL) Deployment mode
Secure. Sphere Product Line Gateway Models G 4 G 8/Crossbeam G 16 FTL 500 MB/Sec 1 GB/Sec 2 GB/Sec 16 k/50 k 24 k/100 k 36 k/200 k Recommended Web Servers 50 100 200 Form Factor 1 U 1 U 2 U FTL Model: 2 U Bridge, Router, Proxy or Monitor Max Inline Bridge Segments 2 2 2 Max Routing Interfaces 5 5 5 Management Interfaces 1 1 1 High Availability Fail Open, IMPVHA, VRRP Fault Tolerance Available Yes Throughput Max TPS (HTTP/SQL) Deployment mode
 Demo Imperva, Inc. 950 Tower Lane, Suite 1550, Foster City, CA 94404 Sales: +1 -866 -926 -4678 www. imperva. com
Demo Imperva, Inc. 950 Tower Lane, Suite 1550, Foster City, CA 94404 Sales: +1 -866 -926 -4678 www. imperva. com
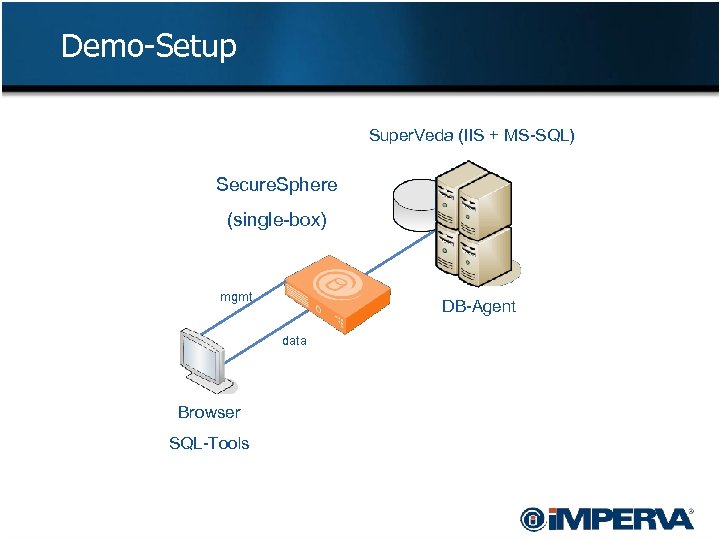 Demo-Setup Super. Veda (IIS + MS-SQL) Secure. Sphere (single-box) mgmt DB-Agent data Browser SQL-Tools
Demo-Setup Super. Veda (IIS + MS-SQL) Secure. Sphere (single-box) mgmt DB-Agent data Browser SQL-Tools


