6b99db445b748fca6aec9656feba65a8.ppt
- Количество слайдов: 36

The LDAP Protocol

Agenda n n Background and Motivation Understanding LDAP n n n n Information Structure Naming Functions/Operations Security Protocol Model Mapping onto Transport Services Protocol Element Encoding Discussion

Background and Motivation n n Increased reliance on networked computers Need in information n n n Functionality Ease-of-Use Administration (Application specific dirs) Clear and consistent organization Integrity Confidentiality
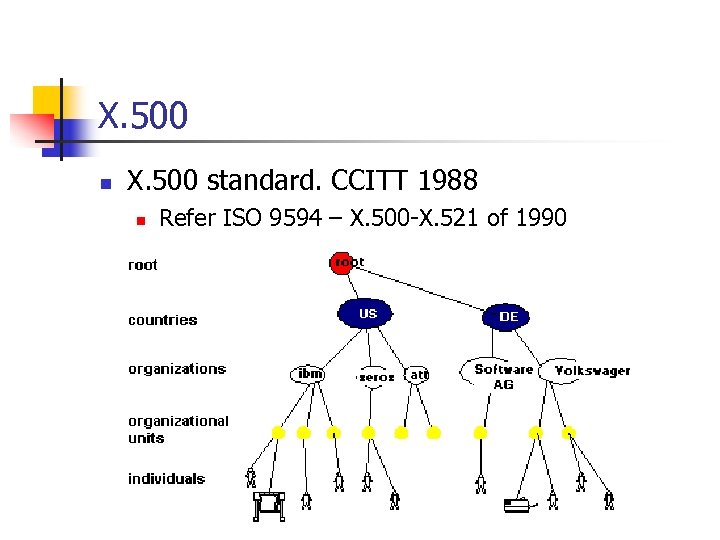
X. 500 n X. 500 standard. CCITT 1988 n Refer ISO 9594 – X. 500 -X. 521 of 1990

X. 500 n n n Organizes directory entries into a hierarchical namespace Powerful search capabilities Often used for interfacing incompatible directory services Used DAP for c/s communication DAP (App. Layer) requires ENTIRE OSI stack to operate Too heavy for small environments

What is LDAP? n n Lightweight Directory Access Protocol Used to access and update information in a directory built on the X. 500 model Specification defines the content of messages between the client and the server Includes operations to establish and disconnect a session from the server
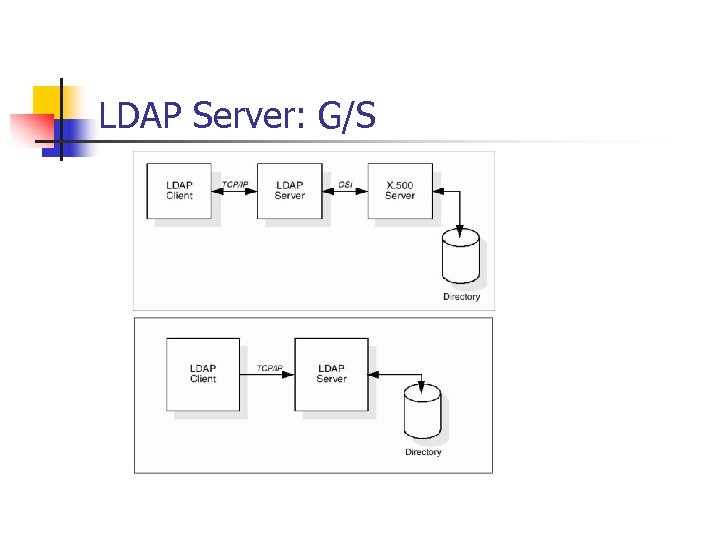
LDAP Server: G/S

Understanding LDAP n n Lightweight alternative to DAP Uses TCP/IP instead of OSI stack Simplifies certain functions and omits others… Uses strings rather than DAP’s ASN. 1 notation to represent data.

LDAP n Information n n Naming n n How information is organized and identified. Functional / Operations n n Structure of information stored in an LDAP directory. Describes what operations can be performed on the information stored in an LDAP directory. Security n Describes how the information can be protected from unauthorized access.
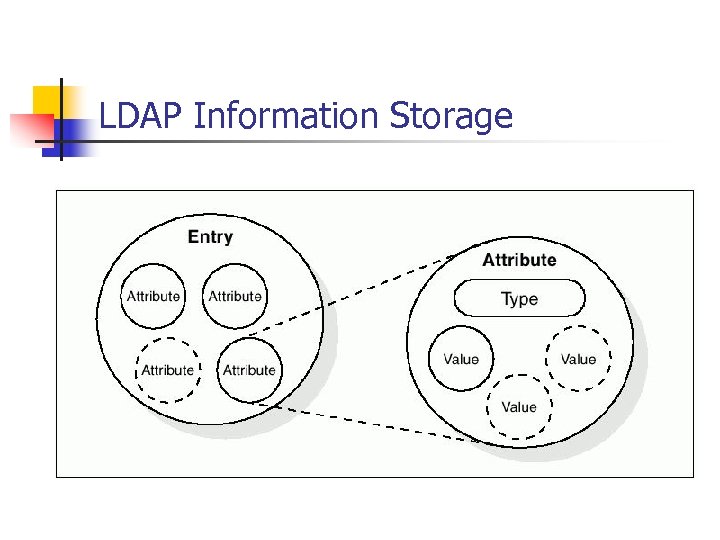
LDAP Information Storage

LDAP Information Storage n n Each attribute has a type/syntax and a value Can define how values behave during searches/directory operations Syntax: bin, ces, cis, tel, dn etc. Usage limits: ssn – only one, jpeg. Photo – 10 K

LDAP Information Storage n Each ‘entry’ describes an object (Class) n n Example Entry: n n Person, Server, Printer etc. Inet. Org. Person(cn, sn, Object. Class) Example Attributes: n cn (cis), sn (cis), telephone. Number (tel), ou (cis), owner (dn), jpeg. Photo (bin)

LDAP Naming n DNs consist of sequence of Relative DN n n n cn=John Smith, ou=Austin, o=IBM, c=US (Leaf 2 Root) (~use for special) Directory Information Tree (DIT) Follow geographical or organizational scheme Aliases: Tree-like, Aliases can link non-leaf nodes

LDAP Naming n n Referrals: May not store entire DIT (v 3) Referrals n n object. Class=referral, attribute=ref, value=LDAPurl Implementation differs n Refferals/Chaining (vendor) n RFC 1777: server chaining is expected.
LDAP Naming n Schema n n n n Defines what object classes allowed Where they are stored What attributes they have (object. Class) Which attributes are optional (object. Class) Type/syntax of each attribute (object. Class) Query server for info: zero-length DN LDAP schema must be readable by the client
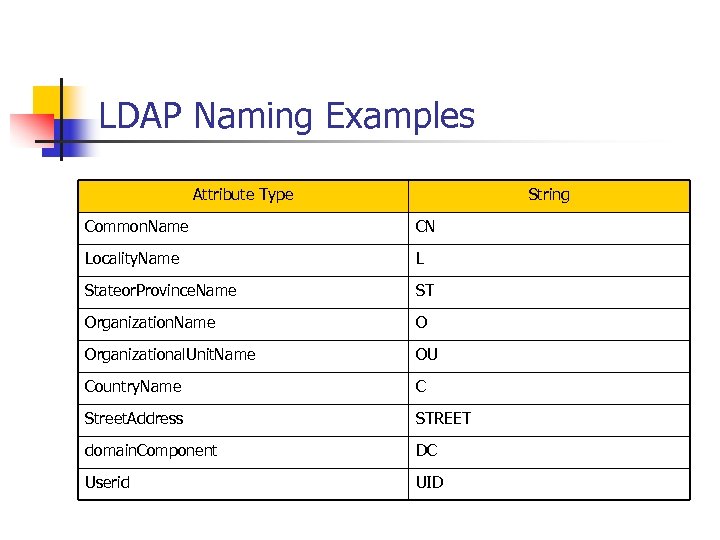
LDAP Naming Examples Attribute Type String Common. Name CN Locality. Name L Stateor. Province. Name ST Organization. Name O Organizational. Unit. Name OU Country. Name C Street. Address STREET domain. Component DC Userid UID

LDAP Functions/Operations n Authentication n Query n n n BIND/UNBIND ABANDON Search Compare entry Update n n n Add an entry Delete an entry (Only Leaf nodes, no aliases) Modify an entry, Modify DN/RDN
Client and Server Interaction n Client establishes session with server (BIND) n n Hostname/IP and port number Security n n Client performs operations n n User-id/password based authentication Anonymous connection - default access rights Encryption/Kerberos also supported Read/Update/Search SELECT X, Y, Z FROM PART_OF_DIRECTORY Client ends the session (UNBIND) Client can ABANDON the session

BIND/UNBIND/ABANDON n Request includes LDAP version, the name the client wants to bind as, authentication type n n n Server responds with a status indication UNBIND: Terminates a protocol session n n Simple (clear text passwords, anonymous) Kerberos v 4 to the LDAP server (krbv 42 LDAP) Kerberos v 4 to the DSA server (krbv 42 DSA) Unbind. Request : : = [APPLICATION 2] NULL ABANDON: n Message. ID to abandon

Search/Compare n Request includes n n n n n base. Object: an LDAPDN Scope: how many levels to be searched deref. Aliases: handling of aliases size. Limit: max number of entries returned time. Limit: max time allowed for search attrs. Only: return attribute types OR values also Filter: cond. to be fulfilled when searching Attributes: List of entry’s attributes to be returned Read and List implemented as searches Compare: similar to search but returns T/F

ADD/MODIFY/DELETE n ADD request n n n Entry: LDAPDN List of Attributes and values (or sets of values) MODIFY request n n Used to add, delete, modify attributes Request includes n n n DELETE request n n Object: LDAPDN List of modifications (atomic) n Add, Delete, Replace Object: LDAPDN MODIFY RDN: LDAPDN, new. RDN, DEL_FLAG

Protocol Elements n LDAPMessage (Message. ID unique)
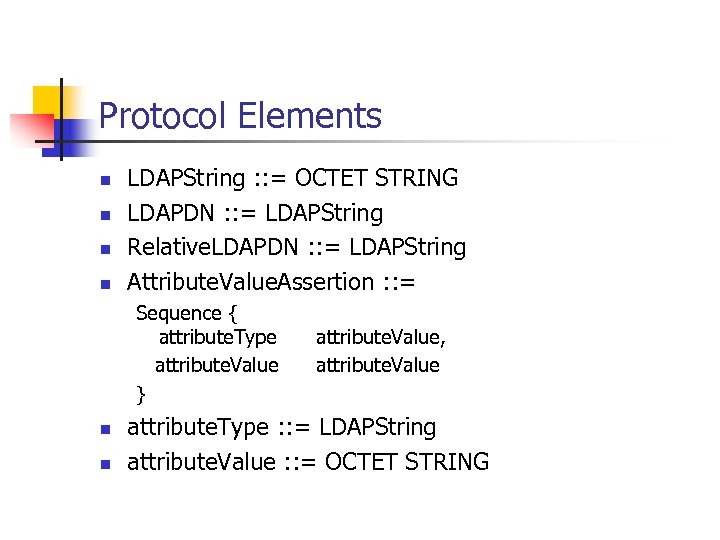
Protocol Elements n n LDAPString : : = OCTET STRING LDAPDN : : = LDAPString Relative. LDAPDN : : = LDAPString Attribute. Value. Assertion : : = Sequence { attribute. Type attribute. Value } n n attribute. Value, attribute. Value attribute. Type : : = LDAPString attribute. Value : : = OCTET STRING
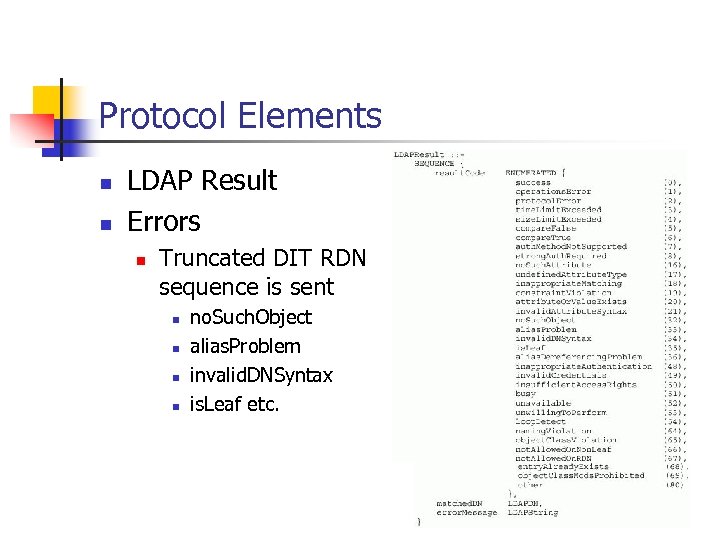
Protocol Elements n n LDAP Result Errors n Truncated DIT RDN sequence is sent n n no. Such. Object alias. Problem invalid. DNSyntax is. Leaf etc.
LDAP Security n Current LDAP version supports n n Clear text passwords KERBEROS version 4 authentication Other authentication methods possible in future versions (March 1995) SASL support added in version 3 n Kerberos deemed stronger than SASL…
LDAP Security n n Security based on the BIND model Clear text ver 1 Kerberos ver 1, 2, 3 (depr) SASL ver 3 n n n Simple Authentication and Security Layer uses one of many authentication methods Proposal for Transport Layer Security n Based on SSL v 3 from Netscape

LDAP Security n n No Authentication Basic Authentication n DN and password provided Clear-text or Base 64 encoded SASL (RFC 2222) n n n Parameters: DN, mechanism, credentials Provides cross protocol authentication calls Encryption can be optionally negotiated ldap_sasl_bind() (ver 3 call) Ldap: //<ldap_server>/? supportedsaslmechanisms
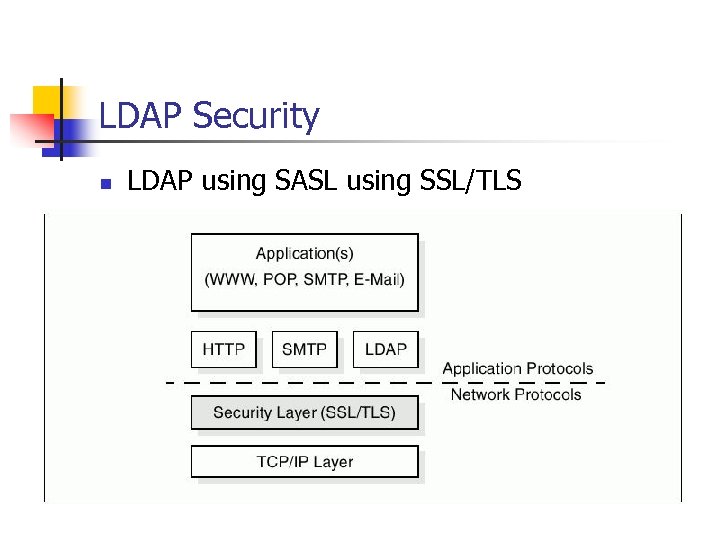
LDAP Security n LDAP using SASL using SSL/TLS
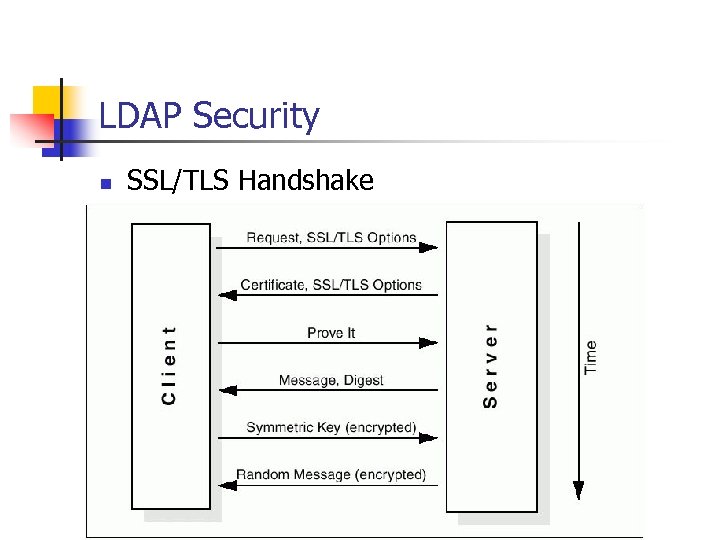
LDAP Security n SSL/TLS Handshake

Agenda n n Background and Motivation Understanding LDAP n n n n Information Structure Naming Functions/Operations Security Protocol Model Mapping onto Transport Services Protocol Element Encoding Discussion

Protocol Model n Clients performing protocol operations against servers n n Client sends protocol request to server Server performs operation on directory Server returns response (results/errors) Asynchronous Server Behavior
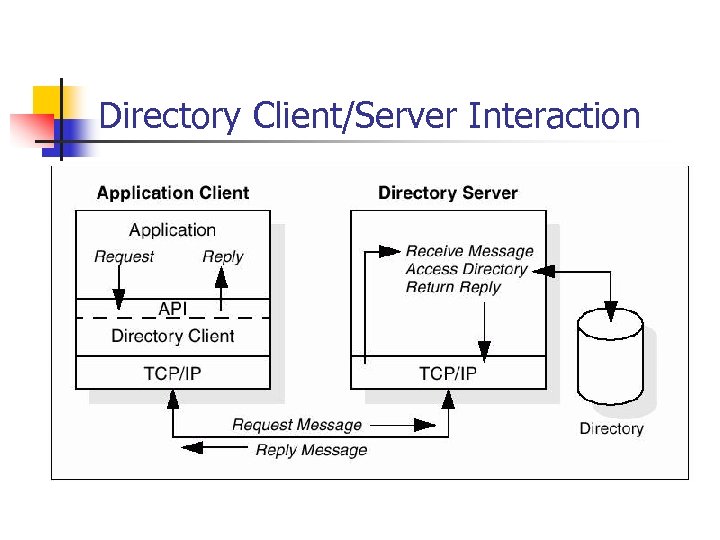
Directory Client/Server Interaction
Mapping onto Transport n n Uses Connection-oriented, reliable transport TCP n n n LDAPMessage PDU mapped onto TCP byte stream LDAP listener on port 389 Connection Oriented Transport Service (COTS) n LDAP PDU is mapped directly onto T-Data
Protocol Element Encoding n n n Encoded for Exchange using BER (Basic Encoding Rules) BER defined in Abstract Syntax Notation One (ASN. 1) High Overhead for BER n Restrictions imposed to improve perf. n n Definite form of length encoding only Bit Strings/ Octet Strings and all character string types encoded in primitive form only
LDAP Implementations n C Library API n n n LDAPv 2 - RFC 1823 ‘The LDAP API’ LDAPv 3 – In Internet Draft stage Java JNDI LDAP v 3 uses the UTF-8 encoding of the Unicode character set. HTTP to LDAP gateway LDAP to X. 500 gateway – ldapd

Version 2 v/s Version 3 n Referrals n n Security n n Extensible authentication using Simple Authentication and Security Layer (SASL) Internationalization n n A server that does not store the requested data can refer the client to another server. UTF-8 support for international characters. Extensibility n New object types and operations can be dynamically defined and schema published in a standard manner.
6b99db445b748fca6aec9656feba65a8.ppt