a3468848684dde45a89dc7b83a93f00b.ppt
- Количество слайдов: 55
 The latest developments in FIND/GENI projects and their influence on European Networking Jiří Navrátil jiri@cesnet. cz Terena Networking Conference 2007 21 -24. 5. 2007 Lyngby/Denmark
The latest developments in FIND/GENI projects and their influence on European Networking Jiří Navrátil jiri@cesnet. cz Terena Networking Conference 2007 21 -24. 5. 2007 Lyngby/Denmark
 Agenda • Internet expansion and consequences • Fundamental problems of Internet • Next generation of Internet (directions and supporting projects, GENI, FIND) • New network architectures (overlay networking, virtualized GRID) • European projects (One. Lab, Phosphorus, UCLP, FEDERICA)
Agenda • Internet expansion and consequences • Fundamental problems of Internet • Next generation of Internet (directions and supporting projects, GENI, FIND) • New network architectures (overlay networking, virtualized GRID) • European projects (One. Lab, Phosphorus, UCLP, FEDERICA)
 Internet expansion • Web (90 ties), p 2 p (2000), video, IPTV, wireless (today), sensors (tomorrow) • Asia, Europe, North America, …. Africa • Expecting trillion of devices in near future • Problems: technical and social capacity on last mile, guaranteed Bw, path stability, … viruses, attacks, unwanted mail, pishing, etc. • Wide discussion in Internet community about the future, problems in many forms and on many forums NO STRENGTH to change fundamentals of existing Internet • NFS came with the GENI which is trying to find way, how to change Internet from the base (REINVENTING)
Internet expansion • Web (90 ties), p 2 p (2000), video, IPTV, wireless (today), sensors (tomorrow) • Asia, Europe, North America, …. Africa • Expecting trillion of devices in near future • Problems: technical and social capacity on last mile, guaranteed Bw, path stability, … viruses, attacks, unwanted mail, pishing, etc. • Wide discussion in Internet community about the future, problems in many forms and on many forums NO STRENGTH to change fundamentals of existing Internet • NFS came with the GENI which is trying to find way, how to change Internet from the base (REINVENTING)
 Future Internet • Creating the Internet you want in 10, 15 Years • The Internet which society TRUST • Support pervasive computing (from PDA to Supercomputing) • Connecting devices and users with all types communication channels from wireless to optical light paths • Enable accept further developments and innovations
Future Internet • Creating the Internet you want in 10, 15 Years • The Internet which society TRUST • Support pervasive computing (from PDA to Supercomputing) • Connecting devices and users with all types communication channels from wireless to optical light paths • Enable accept further developments and innovations
 Two paths for changes Larry Peterson Princeton University: A Strategy for Continually Reinventing Internet (May 2005) Incremental Clean-Slate (replace Internet with new architecture) many problems on first path (many limits, hard manage, , vulnerability, hostile) there are barriers to second path: Internet ossificated, cannot be replaced Inadequate validation of potential solutions, tesbed dilemma: production testbed = incremental change experimental testbed = no real users ! Why now ? many architectional proposals ( statistics new RFC, papers, etc. ) enabling technology infrastructure exists (NLR, Planetlab, . . GN 2, . . ) research community is ready to making it real Where are the fundamental problems and what is the most actual (first order) problem ? ? ?
Two paths for changes Larry Peterson Princeton University: A Strategy for Continually Reinventing Internet (May 2005) Incremental Clean-Slate (replace Internet with new architecture) many problems on first path (many limits, hard manage, , vulnerability, hostile) there are barriers to second path: Internet ossificated, cannot be replaced Inadequate validation of potential solutions, tesbed dilemma: production testbed = incremental change experimental testbed = no real users ! Why now ? many architectional proposals ( statistics new RFC, papers, etc. ) enabling technology infrastructure exists (NLR, Planetlab, . . GN 2, . . ) research community is ready to making it real Where are the fundamental problems and what is the most actual (first order) problem ? ? ?
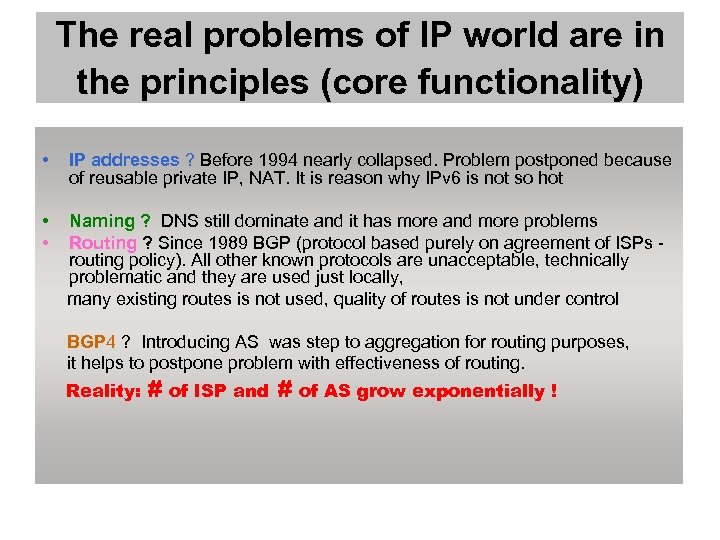 The real problems of IP world are in the principles (core functionality) • IP addresses ? Before 1994 nearly collapsed. Problem postponed because of reusable private IP, NAT. It is reason why IPv 6 is not so hot • • Naming ? DNS still dominate and it has more and more problems Routing ? Since 1989 BGP (protocol based purely on agreement of ISPs routing policy). All other known protocols are unacceptable, technically problematic and they are used just locally, many existing routes is not used, quality of routes is not under control BGP 4 ? Introducing AS was step to aggregation for routing purposes, it helps to postpone problem with effectiveness of routing. Reality: # of ISP and # of AS grow exponentially !
The real problems of IP world are in the principles (core functionality) • IP addresses ? Before 1994 nearly collapsed. Problem postponed because of reusable private IP, NAT. It is reason why IPv 6 is not so hot • • Naming ? DNS still dominate and it has more and more problems Routing ? Since 1989 BGP (protocol based purely on agreement of ISPs routing policy). All other known protocols are unacceptable, technically problematic and they are used just locally, many existing routes is not used, quality of routes is not under control BGP 4 ? Introducing AS was step to aggregation for routing purposes, it helps to postpone problem with effectiveness of routing. Reality: # of ISP and # of AS grow exponentially !
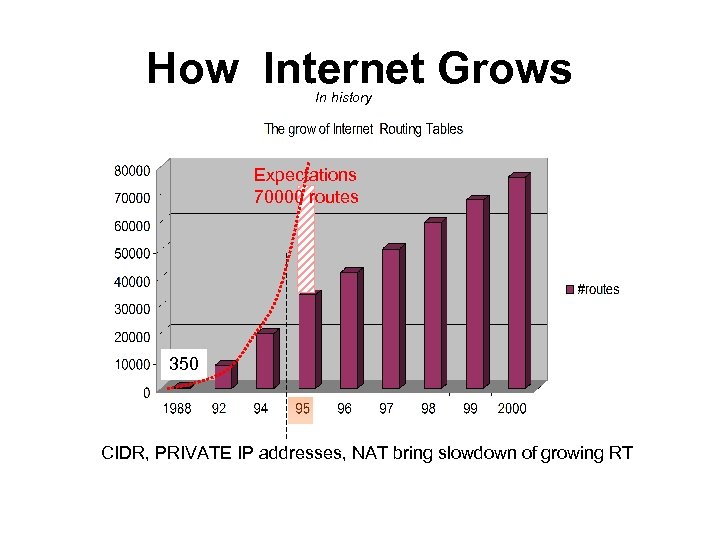 How Internet Grows In history Expectations 70000 routes 350 CIDR, PRIVATE IP addresses, NAT bring slowdown of growing RT
How Internet Grows In history Expectations 70000 routes 350 CIDR, PRIVATE IP addresses, NAT bring slowdown of growing RT
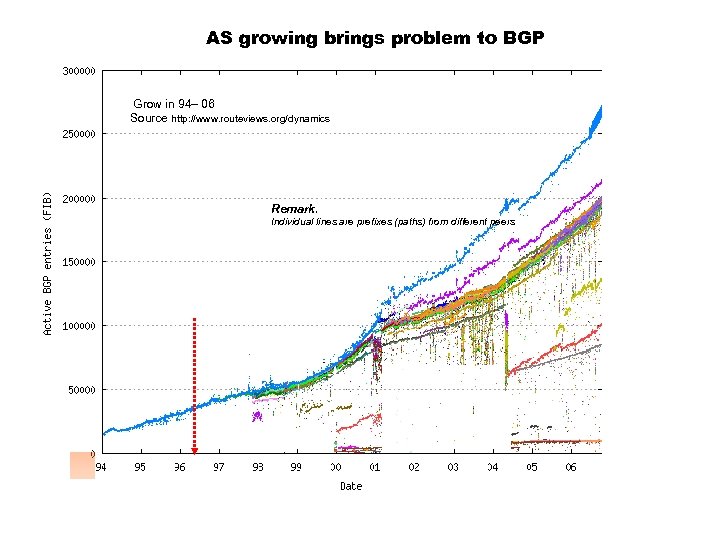 AS growing brings problem to BGP Grow in 94– 06 Source http: //www. routeviews. org/dynamics Remark. Individual lines are prefixes (paths) from different peers
AS growing brings problem to BGP Grow in 94– 06 Source http: //www. routeviews. org/dynamics Remark. Individual lines are prefixes (paths) from different peers
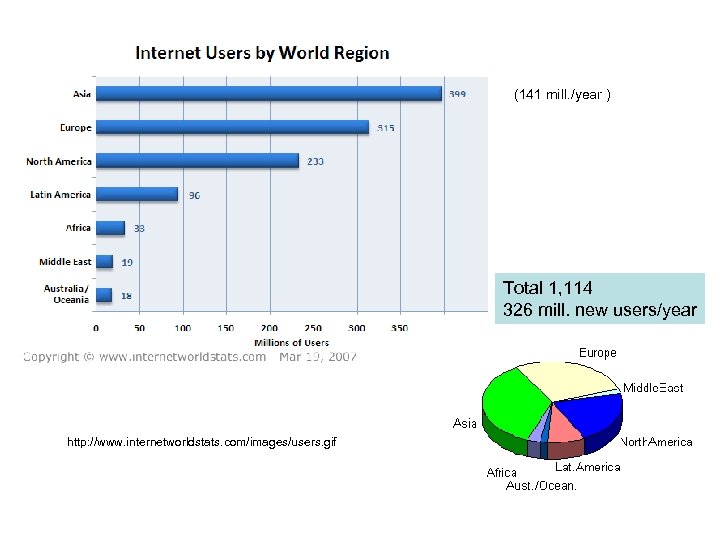 (141 mill. /year ) Total 1, 114 326 mill. new users/year http: //www. internetworldstats. com/images/users. gif
(141 mill. /year ) Total 1, 114 326 mill. new users/year http: //www. internetworldstats. com/images/users. gif
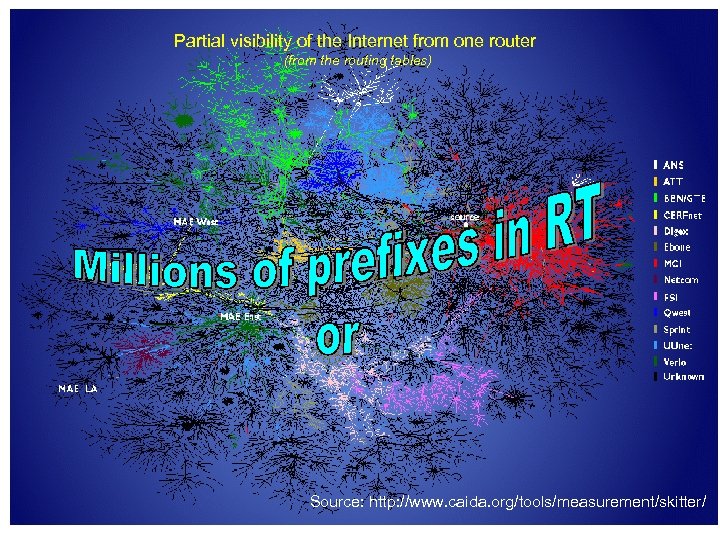 Partial visibility of the Internet from one router BGP table analysis (from the routing tables) Source: http: //www. caida. org/tools/measurement/skitter/
Partial visibility of the Internet from one router BGP table analysis (from the routing tables) Source: http: //www. caida. org/tools/measurement/skitter/
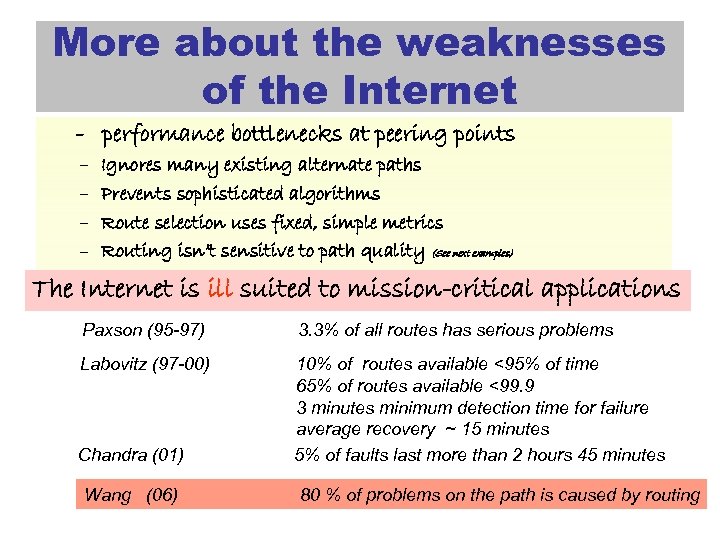 More about the weaknesses of the Internet - performance bottlenecks at peering points – – Ignores many existing alternate paths Prevents sophisticated algorithms Route selection uses fixed, simple metrics Routing isn’t sensitive to path quality (See next examples) The Internet is ill suited to mission-critical applications Paxson (95 -97) 3. 3% of all routes has serious problems Labovitz (97 -00) 10% of routes available <95% of time 65% of routes available <99. 9 3 minutes minimum detection time for failure average recovery ~ 15 minutes 5% of faults last more than 2 hours 45 minutes Chandra (01) Wang (06) 80 % of problems on the path is caused by routing
More about the weaknesses of the Internet - performance bottlenecks at peering points – – Ignores many existing alternate paths Prevents sophisticated algorithms Route selection uses fixed, simple metrics Routing isn’t sensitive to path quality (See next examples) The Internet is ill suited to mission-critical applications Paxson (95 -97) 3. 3% of all routes has serious problems Labovitz (97 -00) 10% of routes available <95% of time 65% of routes available <99. 9 3 minutes minimum detection time for failure average recovery ~ 15 minutes 5% of faults last more than 2 hours 45 minutes Chandra (01) Wang (06) 80 % of problems on the path is caused by routing
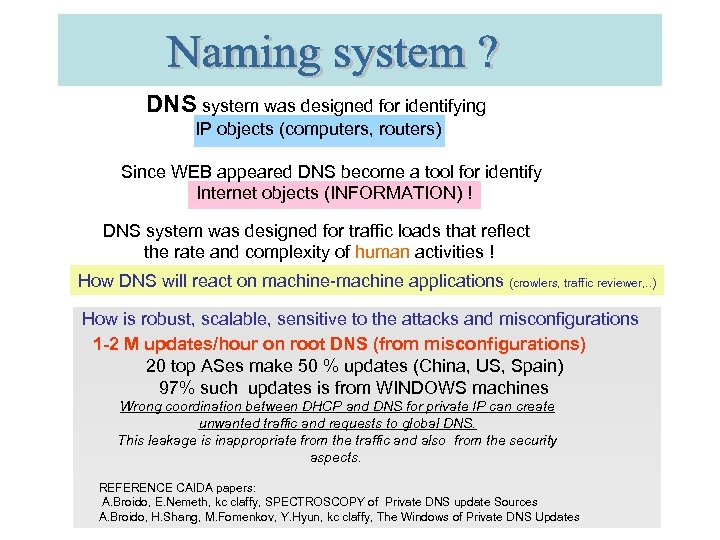 DNS system was designed for identifying IP objects (computers, routers) Since WEB appeared DNS become a tool for identify Internet objects (INFORMATION) ! DNS system was designed for traffic loads that reflect the rate and complexity of human activities ! How DNS will react on machine-machine applications (crowlers, traffic reviewer, . . ) How is robust, scalable, sensitive to the attacks and misconfigurations 1 -2 M updates/hour on root DNS (from misconfigurations) 20 top ASes make 50 % updates (China, US, Spain) 97% such updates is from WINDOWS machines Wrong coordination between DHCP and DNS for private IP can create unwanted traffic and requests to global DNS. This leakage is inappropriate from the traffic and also from the security aspects. REFERENCE CAIDA papers: A. Broido, E. Nemeth, kc claffy, SPECTROSCOPY of Private DNS update Sources A. Broido, H. Shang, M. Fomenkov, Y. Hyun, kc claffy, The Windows of Private DNS Updates
DNS system was designed for identifying IP objects (computers, routers) Since WEB appeared DNS become a tool for identify Internet objects (INFORMATION) ! DNS system was designed for traffic loads that reflect the rate and complexity of human activities ! How DNS will react on machine-machine applications (crowlers, traffic reviewer, . . ) How is robust, scalable, sensitive to the attacks and misconfigurations 1 -2 M updates/hour on root DNS (from misconfigurations) 20 top ASes make 50 % updates (China, US, Spain) 97% such updates is from WINDOWS machines Wrong coordination between DHCP and DNS for private IP can create unwanted traffic and requests to global DNS. This leakage is inappropriate from the traffic and also from the security aspects. REFERENCE CAIDA papers: A. Broido, E. Nemeth, kc claffy, SPECTROSCOPY of Private DNS update Sources A. Broido, H. Shang, M. Fomenkov, Y. Hyun, kc claffy, The Windows of Private DNS Updates
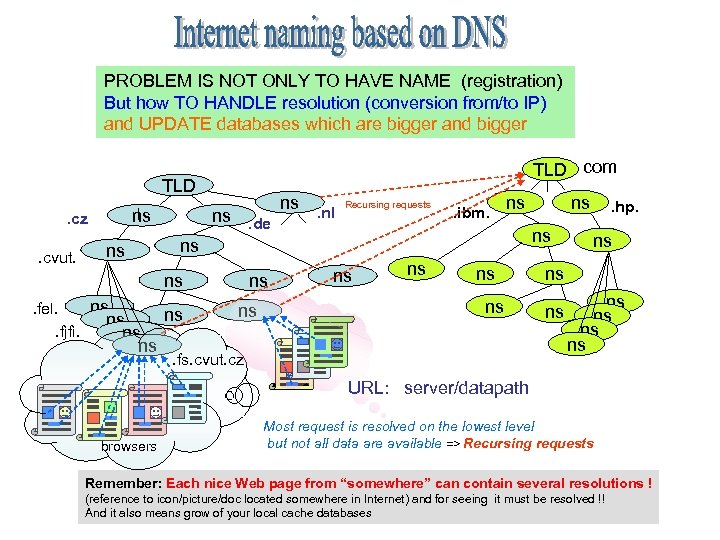 PROBLEM IS NOT ONLY TO HAVE NAME (registration) But how TO HANDLE resolution (conversion from/to IP) and UPDATE databases which are bigger and bigger TLD com TLD ns . cz. cvut. ns. de ns . nl Recursing requests . ibm. ns ns ns. fel. ns. fjfi. ns ns ns . fs. cvut. cz . hp. ns ns URL: server/datapath browsers Most request is resolved on the lowest level but not all data are available => Recursing requests Remember: Each nice Web page from “somewhere” can contain several resolutions ! (reference to icon/picture/doc located somewhere in Internet) and for seeing it must be resolved !! And it also means grow of your local cache databases
PROBLEM IS NOT ONLY TO HAVE NAME (registration) But how TO HANDLE resolution (conversion from/to IP) and UPDATE databases which are bigger and bigger TLD com TLD ns . cz. cvut. ns. de ns . nl Recursing requests . ibm. ns ns ns. fel. ns. fjfi. ns ns ns . fs. cvut. cz . hp. ns ns URL: server/datapath browsers Most request is resolved on the lowest level but not all data are available => Recursing requests Remember: Each nice Web page from “somewhere” can contain several resolutions ! (reference to icon/picture/doc located somewhere in Internet) and for seeing it must be resolved !! And it also means grow of your local cache databases
 DNS is undoubted but more and more actual problem is: Separation data from location ! Van Jacobson on Google http: //video. google. com/videoplay? docid=-6972678839686672840
DNS is undoubted but more and more actual problem is: Separation data from location ! Van Jacobson on Google http: //video. google. com/videoplay? docid=-6972678839686672840
 ( Michael Walfish MIT ) Hostname/pathname structure and DNS resolution http: //www. myhost. edu/doc/pub 1. ps SFR Semantic Free Referencing SFRtag/pathname structure and DHT resolution sfr: //fbcd 1234/doc/pub 1. ps O-record of Metadata SFRtag: 160 bit string, IP address, port, … Contact to traditional web servers: SFR infrastructure strips first part and makes DHT resolution, It replaces the first part (host id) with IP and the rest is same as previous case More flexibility: pathname part of the SFRtag, multiple destinations
( Michael Walfish MIT ) Hostname/pathname structure and DNS resolution http: //www. myhost. edu/doc/pub 1. ps SFR Semantic Free Referencing SFRtag/pathname structure and DHT resolution sfr: //fbcd 1234/doc/pub 1. ps O-record of Metadata SFRtag: 160 bit string, IP address, port, … Contact to traditional web servers: SFR infrastructure strips first part and makes DHT resolution, It replaces the first part (host id) with IP and the rest is same as previous case More flexibility: pathname part of the SFRtag, multiple destinations
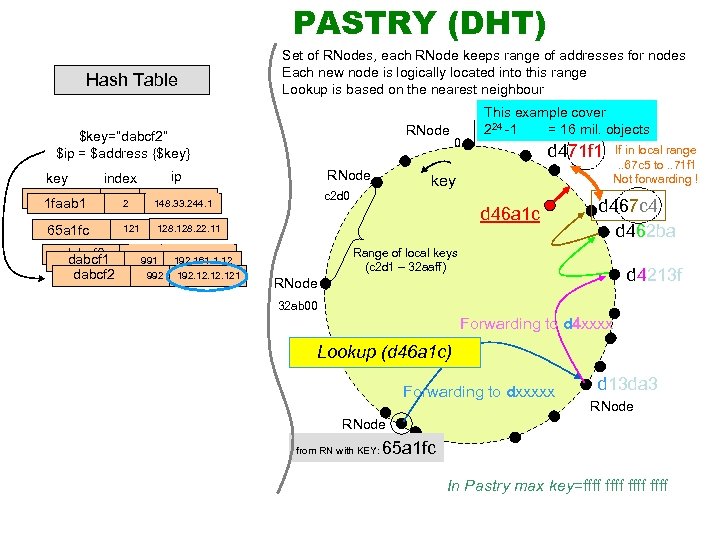 PASTRY (DHT) Hash Table Set of RNodes, each RNode keeps range of addresses for nodes Each new node is logically located into this range Lookup is based on the nearest neighbour RNode $key=“dabcf 2” $ip = $address {$key} key index 1 faab 1 65 a 1 fc dabcf 0 dabcf 1 dabcf 2 RNode ip 1 2 121 128. 22. 11 990 192. 161. 1. 12 991 192. 161. 1. 12 992 192. 12. 121 d 471 f 1 key c 2 d 0 148. 33. 244. 1 0 This example cover 224 -1 = 16 mil. objects d 46 a 1 c If in local range. . 67 c 5 to. . 71 f 1 Not forwarding ! d 467 c 4 d 462 ba Range of local keys (c 2 d 1 – 32 aaff) d 4213 f RNode 32 ab 00 Forwarding to d 4 xxxx Lookup (d 46 a 1 c) Forwarding to dxxxxx d 13 da 3 RNode from RN with KEY: 65 a 1 fc In Pastry max key=ffff
PASTRY (DHT) Hash Table Set of RNodes, each RNode keeps range of addresses for nodes Each new node is logically located into this range Lookup is based on the nearest neighbour RNode $key=“dabcf 2” $ip = $address {$key} key index 1 faab 1 65 a 1 fc dabcf 0 dabcf 1 dabcf 2 RNode ip 1 2 121 128. 22. 11 990 192. 161. 1. 12 991 192. 161. 1. 12 992 192. 12. 121 d 471 f 1 key c 2 d 0 148. 33. 244. 1 0 This example cover 224 -1 = 16 mil. objects d 46 a 1 c If in local range. . 67 c 5 to. . 71 f 1 Not forwarding ! d 467 c 4 d 462 ba Range of local keys (c 2 d 1 – 32 aaff) d 4213 f RNode 32 ab 00 Forwarding to d 4 xxxx Lookup (d 46 a 1 c) Forwarding to dxxxxx d 13 da 3 RNode from RN with KEY: 65 a 1 fc In Pastry max key=ffff
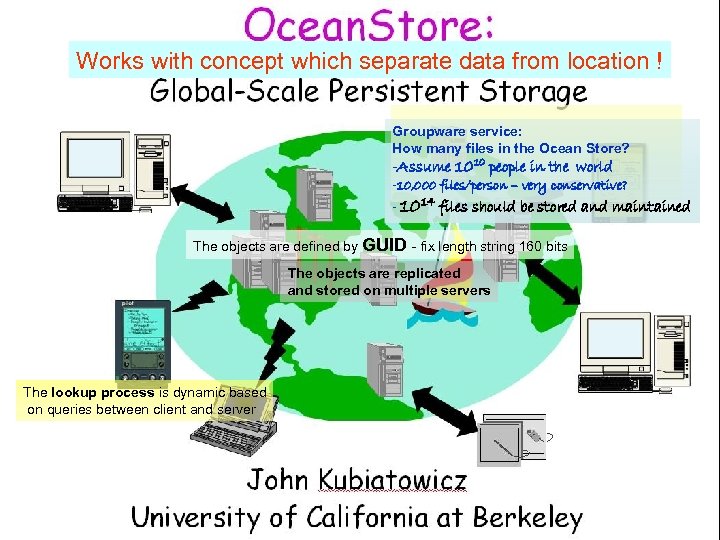 Works with concept which separate data from location ! Groupware service: How many files in the Ocean Store? -Assume 1010 people in the world -10, 000 files/person – very conservative? - 1014 files should be stored and maintained The objects are defined by GUID - fix length string 160 bits The objects are replicated and stored on multiple servers The lookup process is dynamic based on queries between client and server
Works with concept which separate data from location ! Groupware service: How many files in the Ocean Store? -Assume 1010 people in the world -10, 000 files/person – very conservative? - 1014 files should be stored and maintained The objects are defined by GUID - fix length string 160 bits The objects are replicated and stored on multiple servers The lookup process is dynamic based on queries between client and server
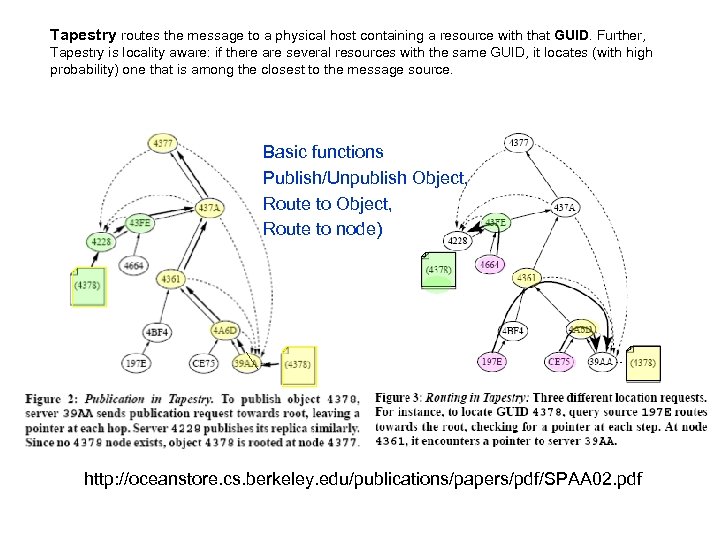 Tapestry routes the message to a physical host containing a resource with that GUID. Further, Tapestry is locality aware: if there are several resources with the same GUID, it locates (with high probability) one that is among the closest to the message source. Basic functions Publish/Unpublish Object, Route to node) http: //oceanstore. cs. berkeley. edu/publications/papers/pdf/SPAA 02. pdf
Tapestry routes the message to a physical host containing a resource with that GUID. Further, Tapestry is locality aware: if there are several resources with the same GUID, it locates (with high probability) one that is among the closest to the message source. Basic functions Publish/Unpublish Object, Route to node) http: //oceanstore. cs. berkeley. edu/publications/papers/pdf/SPAA 02. pdf
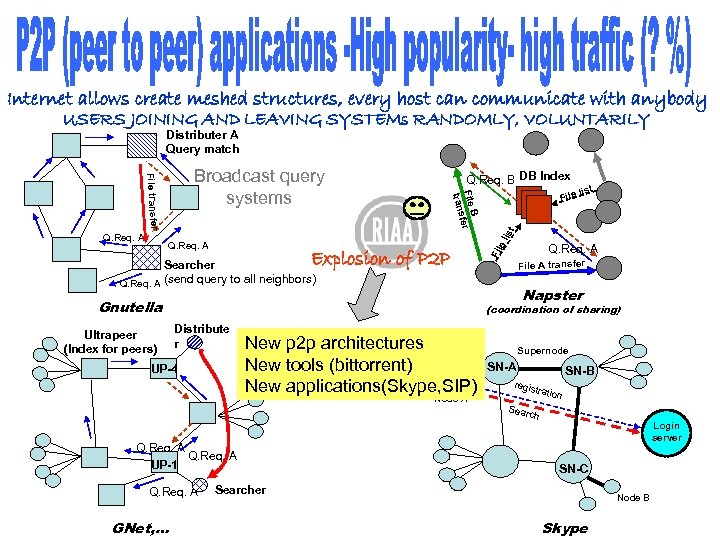 Internet allows create meshed structures, every host can communicate with anybody USERS JOINING AND LEAVING SYSTEMs RANDOMLY, VOLUNTARILY Distributer A Query match Explosion of P 2 P Searcher Q. Req. A (send query to all neighbors) ist list Q. Req. A File A transfer Napster Gnutella Ultrapeer (Index for peers) el Q. Req. A File Fil Q. Req. A Q. Req. B DB Index B File fer s tran File transfer Broadcast query systems (coordination of sharing) Distribute r UP-4 New p 2 p architectures New tools (bittorrent) New applications(Skype, SIP) Node A Supernode SN-A SN-B regis tratio n Sear ch Q. Req. A UP-1 Q. Req. A GNet, … Login server SN-C Searcher Node B Skype
Internet allows create meshed structures, every host can communicate with anybody USERS JOINING AND LEAVING SYSTEMs RANDOMLY, VOLUNTARILY Distributer A Query match Explosion of P 2 P Searcher Q. Req. A (send query to all neighbors) ist list Q. Req. A File A transfer Napster Gnutella Ultrapeer (Index for peers) el Q. Req. A File Fil Q. Req. A Q. Req. B DB Index B File fer s tran File transfer Broadcast query systems (coordination of sharing) Distribute r UP-4 New p 2 p architectures New tools (bittorrent) New applications(Skype, SIP) Node A Supernode SN-A SN-B regis tratio n Sear ch Q. Req. A UP-1 Q. Req. A GNet, … Login server SN-C Searcher Node B Skype
 from Darleen Fisher and Guru Parulkar NSF-CISE presentation
from Darleen Fisher and Guru Parulkar NSF-CISE presentation
 from Darleen Fisher and Guru Parulkar NSF-CISE presentation
from Darleen Fisher and Guru Parulkar NSF-CISE presentation
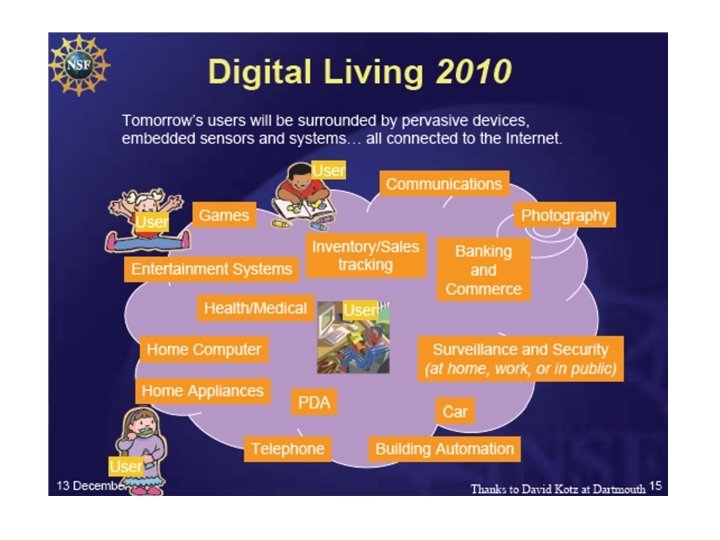 from Darleen Fisher and Guru Parulkar NSF-CISE presentation
from Darleen Fisher and Guru Parulkar NSF-CISE presentation
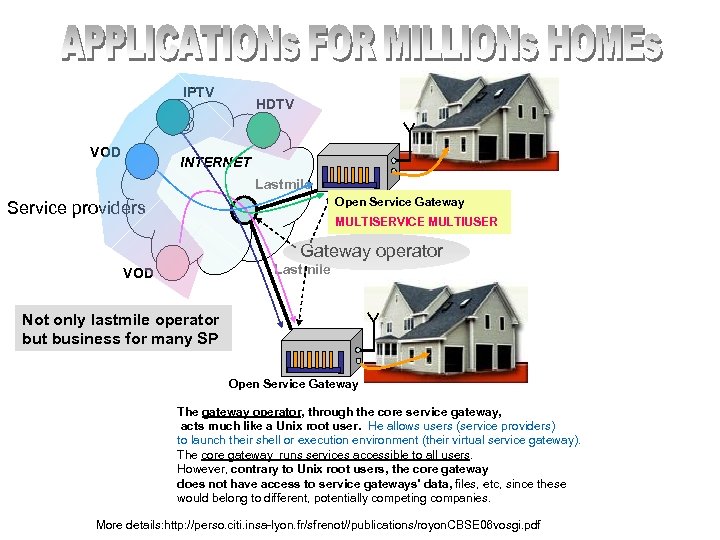 IPTV VOD HDTV INTERNET Lastmile Open Service Gateway Service providers MULTISERVICE MULTIUSER Gateway operator Lastmile VOD Not only lastmile operator but business for many SP Open Service Gateway The gateway operator, through the core service gateway, acts much like a Unix root user. He allows users (service providers) to launch their shell or execution environment (their virtual service gateway). The core gateway runs services accessible to all users. However, contrary to Unix root users, the core gateway does not have access to service gateways' data, files, etc, since these would belong to different, potentially competing companies. More details: http: //perso. citi. insa-lyon. fr/sfrenot//publications/royon. CBSE 06 vosgi. pdf
IPTV VOD HDTV INTERNET Lastmile Open Service Gateway Service providers MULTISERVICE MULTIUSER Gateway operator Lastmile VOD Not only lastmile operator but business for many SP Open Service Gateway The gateway operator, through the core service gateway, acts much like a Unix root user. He allows users (service providers) to launch their shell or execution environment (their virtual service gateway). The core gateway runs services accessible to all users. However, contrary to Unix root users, the core gateway does not have access to service gateways' data, files, etc, since these would belong to different, potentially competing companies. More details: http: //perso. citi. insa-lyon. fr/sfrenot//publications/royon. CBSE 06 vosgi. pdf
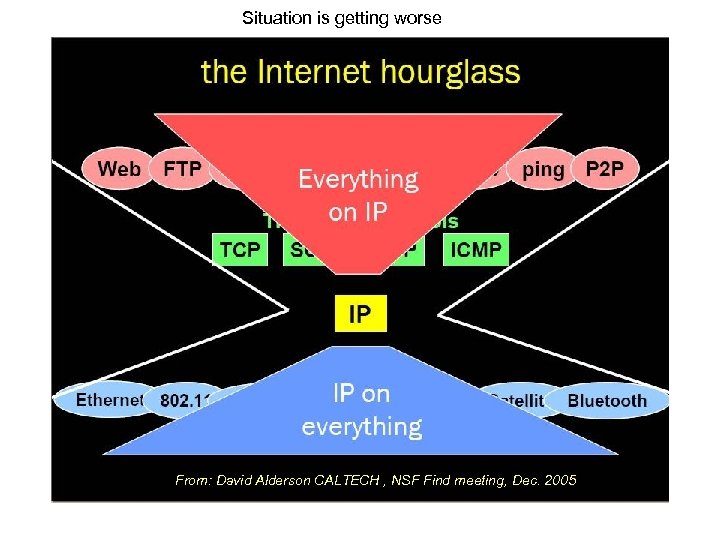 Situation is getting worse From: David Alderson CALTECH , NSF Find meeting, Dec. 2005
Situation is getting worse From: David Alderson CALTECH , NSF Find meeting, Dec. 2005
 GIobal Environment for network Innovations – GENI Reaction of NSF to existing Internet problems • August 25, 2005: NSF announces the GENI Initiative at SIGCOMM. • Since 2006 NFS (CISE) divided GENI to program FIND – Future Internet Design and the program of construction GENI facility • During 2 years was many working meetings and it was prepared nearly 50 GDD (Geni Design Documents) http: //www. geni. net/documents_nav. php The most complex is GENI Research plan GDD-06 -28 vers. 4. 5 from April 2007 in which defines detail frame for GENI research
GIobal Environment for network Innovations – GENI Reaction of NSF to existing Internet problems • August 25, 2005: NSF announces the GENI Initiative at SIGCOMM. • Since 2006 NFS (CISE) divided GENI to program FIND – Future Internet Design and the program of construction GENI facility • During 2 years was many working meetings and it was prepared nearly 50 GDD (Geni Design Documents) http: //www. geni. net/documents_nav. php The most complex is GENI Research plan GDD-06 -28 vers. 4. 5 from April 2007 in which defines detail frame for GENI research
 GENI Research program The GENI Initiative will support research, design, and development of new networking and distributed systems capabilities by: • Creating new core functionality: Going beyond existing paradigms of datagram, packet and circuit switching; designing new naming, addressing, and overall identity architectures, and new paradigms of network management; • Developing enhanced capabilities: Building security into the architecture; designing for high availability; balancing privacy and accountability; designing for regional difference and local values; • Deploying and validating new architectures: Designing new architectures that incorporate emerging technologies (e. g. , new wireless and optical technologies) and new computing paradigms enabled by pervasive devices; • Building higher-level service abstractions: Using, for example, information objects, location-based services, and identity frameworks; • Building new services and applications: Making large-scale distributed applications secure, robust and manageable; developing principles and patterns for distributed applications; • Developing new network architecture theories: Investigating network complexity, scalability, and economic incentives.
GENI Research program The GENI Initiative will support research, design, and development of new networking and distributed systems capabilities by: • Creating new core functionality: Going beyond existing paradigms of datagram, packet and circuit switching; designing new naming, addressing, and overall identity architectures, and new paradigms of network management; • Developing enhanced capabilities: Building security into the architecture; designing for high availability; balancing privacy and accountability; designing for regional difference and local values; • Deploying and validating new architectures: Designing new architectures that incorporate emerging technologies (e. g. , new wireless and optical technologies) and new computing paradigms enabled by pervasive devices; • Building higher-level service abstractions: Using, for example, information objects, location-based services, and identity frameworks; • Building new services and applications: Making large-scale distributed applications secure, robust and manageable; developing principles and patterns for distributed applications; • Developing new network architecture theories: Investigating network complexity, scalability, and economic incentives.
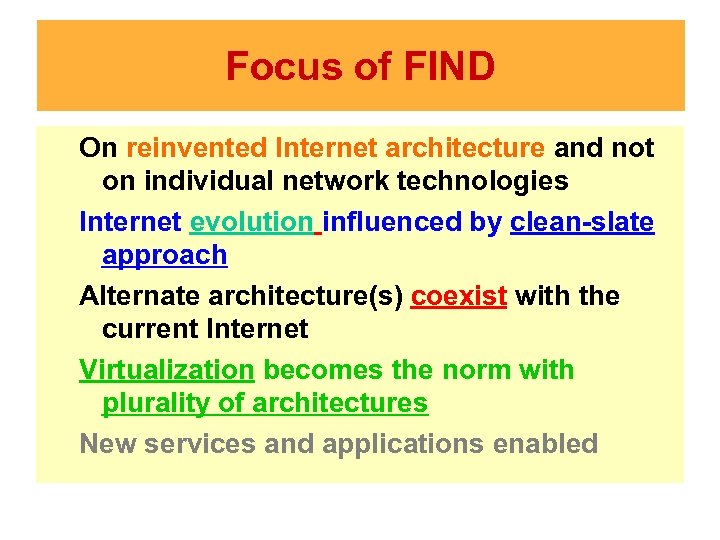 Focus of FIND On reinvented Internet architecture and not on individual network technologies Internet evolution influenced by clean-slate approach Alternate architecture(s) coexist with the current Internet Virtualization becomes the norm with plurality of architectures New services and applications enabled
Focus of FIND On reinvented Internet architecture and not on individual network technologies Internet evolution influenced by clean-slate approach Alternate architecture(s) coexist with the current Internet Virtualization becomes the norm with plurality of architectures New services and applications enabled
 Status of FIND in 2007 The whole FIND program is currently in initial phase. NSF has created a FIND Planning Committee, which is working with NSF to organize a series of meetings among FIND grant recipients to identify and refine overarching concepts for a network of the future. It is a continuation of GENI talks that started in 2005 FIND will in 2007 operate with 40 millions US $ and it is expected that from this budget would award at about 60 -80 teams. The kickoff meeting was held in November 2006. http: //www. nets-find. net/ Ne. TS - Division of Computer & Network Systems funds research and education projects in four basic areas: Programmable Wireless Networks (Ne. TS-Pro. Win) Networking of Sensor Systems (Ne. TS-NOSS) Networking Broadly Defined (Ne. TS-NBD) Future Internet Design (Ne. TS-FIND) 16 30 27 15 – (5, 2 M US)
Status of FIND in 2007 The whole FIND program is currently in initial phase. NSF has created a FIND Planning Committee, which is working with NSF to organize a series of meetings among FIND grant recipients to identify and refine overarching concepts for a network of the future. It is a continuation of GENI talks that started in 2005 FIND will in 2007 operate with 40 millions US $ and it is expected that from this budget would award at about 60 -80 teams. The kickoff meeting was held in November 2006. http: //www. nets-find. net/ Ne. TS - Division of Computer & Network Systems funds research and education projects in four basic areas: Programmable Wireless Networks (Ne. TS-Pro. Win) Networking of Sensor Systems (Ne. TS-NOSS) Networking Broadly Defined (Ne. TS-NBD) Future Internet Design (Ne. TS-FIND) 16 30 27 15 – (5, 2 M US)
 FIND - Scope of Research – Core functionalities (Reconsideration of basics including packets and other modes of – – – multiplexing and data delivery, addressing, naming and identity; routing and delivery; support for mobility; overlay networks, and services required to support overlays; architectural implications of performance objectives; and other elements of network services. ) Security and robustness (prevent attack, flooding, blocking unwanted traffic, dealing with „zombies“ and „botnets“, design new safe protocols and frameworks for applications, end nodes security) Social aspects - privacy and accountability (balancing privacy/identity, problematic of identity tracking, increase mutual trust between users and authorities, responsibility for malicious behavior, access to emergency services) Manageability and usability (facilitate network management, automated networks configurations, fault reporting and diagnostics, architectures cross region coordinations) Implications of new Wireless and sensor networks (mobility of subnets, dynamic resource location, data driven routing, ) Optical network architectures and their implications (integrated internet/optical management, dynamic allocation of capacities, aggregation in backbones ) High level conceptualization (closer to the user, what they want, location based services, search based on localities, information context etc. ) Theoretical foundations (investigating network complexities, scalability, robustnes) – – Support for applications design (How applications and services should be design to exploit new architectures, deveoloping distributed applications including economical incentives)
FIND - Scope of Research – Core functionalities (Reconsideration of basics including packets and other modes of – – – multiplexing and data delivery, addressing, naming and identity; routing and delivery; support for mobility; overlay networks, and services required to support overlays; architectural implications of performance objectives; and other elements of network services. ) Security and robustness (prevent attack, flooding, blocking unwanted traffic, dealing with „zombies“ and „botnets“, design new safe protocols and frameworks for applications, end nodes security) Social aspects - privacy and accountability (balancing privacy/identity, problematic of identity tracking, increase mutual trust between users and authorities, responsibility for malicious behavior, access to emergency services) Manageability and usability (facilitate network management, automated networks configurations, fault reporting and diagnostics, architectures cross region coordinations) Implications of new Wireless and sensor networks (mobility of subnets, dynamic resource location, data driven routing, ) Optical network architectures and their implications (integrated internet/optical management, dynamic allocation of capacities, aggregation in backbones ) High level conceptualization (closer to the user, what they want, location based services, search based on localities, information context etc. ) Theoretical foundations (investigating network complexities, scalability, robustnes) – – Support for applications design (How applications and services should be design to exploit new architectures, deveoloping distributed applications including economical incentives)
 The GENI Facility As envisioned, the GENI Facility will enable: – Shared use through slicing and virtualization in time and space – – domains (i. e. , where "slice" denotes the subset of resources bound to a particular experiment); Access to physical facilities through programmable platforms (e. g. , via customized protocol stacks); Large-scale user participation by "user opt-in" and IP tunnels; Protection and collaboration among researchers by controlled isolation and connection among slices; A broad range of investigations using new classes of platforms and networks, a variety of access circuits and technologies, and global control and management software; – Interconnection of independent facilities via federated design. The GENI Facility will leverage the best ideas and capabilities from existing network testbeds such as Planet. Lab, ORBIT, WHYNET, Emulab, X-Bone, DETER and others. The GENI Facilty will need to extend beyond these testbeds to create an experimental infrastructure capable of supporting the ambitious research goals of the GENI Initiative.
The GENI Facility As envisioned, the GENI Facility will enable: – Shared use through slicing and virtualization in time and space – – domains (i. e. , where "slice" denotes the subset of resources bound to a particular experiment); Access to physical facilities through programmable platforms (e. g. , via customized protocol stacks); Large-scale user participation by "user opt-in" and IP tunnels; Protection and collaboration among researchers by controlled isolation and connection among slices; A broad range of investigations using new classes of platforms and networks, a variety of access circuits and technologies, and global control and management software; – Interconnection of independent facilities via federated design. The GENI Facility will leverage the best ideas and capabilities from existing network testbeds such as Planet. Lab, ORBIT, WHYNET, Emulab, X-Bone, DETER and others. The GENI Facilty will need to extend beyond these testbeds to create an experimental infrastructure capable of supporting the ambitious research goals of the GENI Initiative.
 Relation FIND/GENI Stages of Research 2007 and Later Architectures as they emerge will be made operational and tested via: • Simulation (ns-2, …) • Emulation (Planetlab, Emulab, …) • Run on a large-scale GENI facility When ?
Relation FIND/GENI Stages of Research 2007 and Later Architectures as they emerge will be made operational and tested via: • Simulation (ns-2, …) • Emulation (Planetlab, Emulab, …) • Run on a large-scale GENI facility When ?
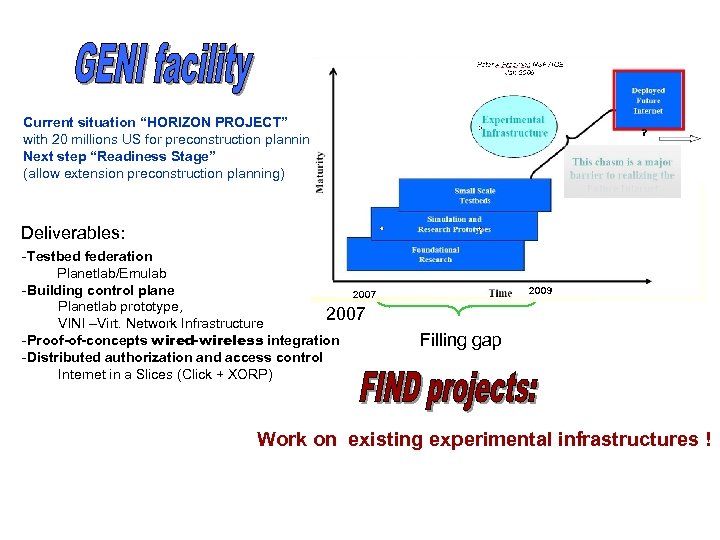 ? Current situation “HORIZON PROJECT” with 20 millions US for preconstruction planning Next step “Readiness Stage” (allow extension preconstruction planning) Deliverables: -Testbed federation Planetlab/Emulab -Building control plane Planetlab prototype, 2007 VINI –Virt. Network Infrastructure -Proof-of-concepts wired-wireless integration -Distributed authorization and access control Internet in a Slices (Click + XORP) 2009 Filling gap Work on existing experimental infrastructures !
? Current situation “HORIZON PROJECT” with 20 millions US for preconstruction planning Next step “Readiness Stage” (allow extension preconstruction planning) Deliverables: -Testbed federation Planetlab/Emulab -Building control plane Planetlab prototype, 2007 VINI –Virt. Network Infrastructure -Proof-of-concepts wired-wireless integration -Distributed authorization and access control Internet in a Slices (Click + XORP) 2009 Filling gap Work on existing experimental infrastructures !

 http: //www. planet-lab. org
http: //www. planet-lab. org
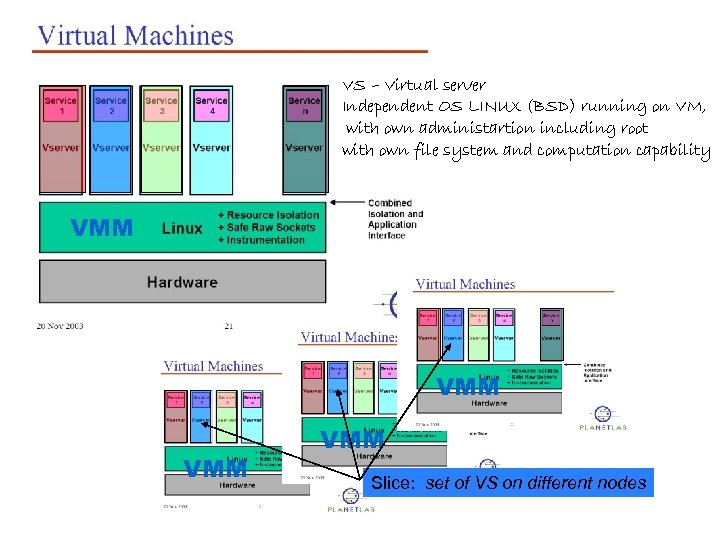 VS – Virtual server Independent OS LINUX (BSD) running on VM, with own administartion including root with own file system and computation capability VMM VMM Slice: set of VS on different nodes
VS – Virtual server Independent OS LINUX (BSD) running on VM, with own administartion including root with own file system and computation capability VMM VMM Slice: set of VS on different nodes
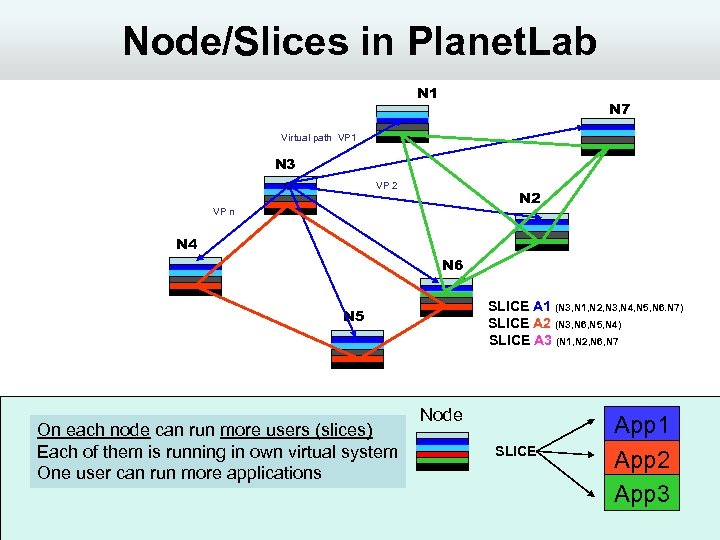 Node/Slices in Planet. Lab N 1 N 7 Virtual path VP 1 N 3 VP 2 N 2 VP n N 4 N 6 SLICE A 1 (N 3, N 1, N 2, N 3, N 4, N 5, N 6. N 7) SLICE A 2 (N 3, N 6, N 5, N 4) SLICE A 3 (N 1, N 2, N 6, N 7 N 5 On each node can run more users (slices) Each of them is running in own virtual system One user can run more applications Node SLICE App 1 App 2 App 3
Node/Slices in Planet. Lab N 1 N 7 Virtual path VP 1 N 3 VP 2 N 2 VP n N 4 N 6 SLICE A 1 (N 3, N 1, N 2, N 3, N 4, N 5, N 6. N 7) SLICE A 2 (N 3, N 6, N 5, N 4) SLICE A 3 (N 1, N 2, N 6, N 7 N 5 On each node can run more users (slices) Each of them is running in own virtual system One user can run more applications Node SLICE App 1 App 2 App 3
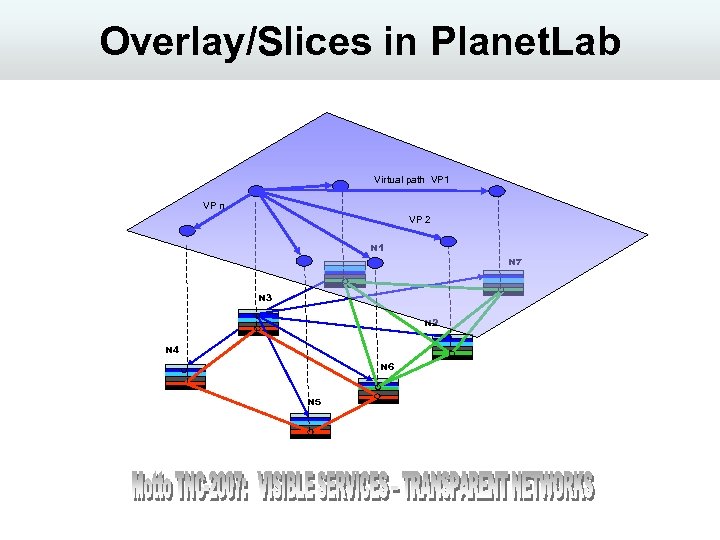 Overlay/Slices in Planet. Lab Virtual path VP 1 VP n VP 2 N 1 N 7 N 3 N 2 N 4 N 6 N 5
Overlay/Slices in Planet. Lab Virtual path VP 1 VP n VP 2 N 1 N 7 N 3 N 2 N 4 N 6 N 5
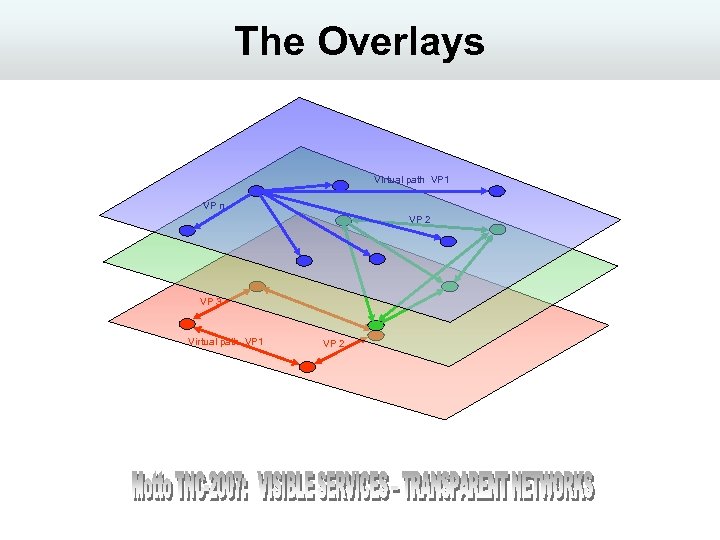 The Overlays Virtual path VP 1 VP n VP 2 VP 3 Virtual path VP 1 VP 2
The Overlays Virtual path VP 1 VP n VP 2 VP 3 Virtual path VP 1 VP 2
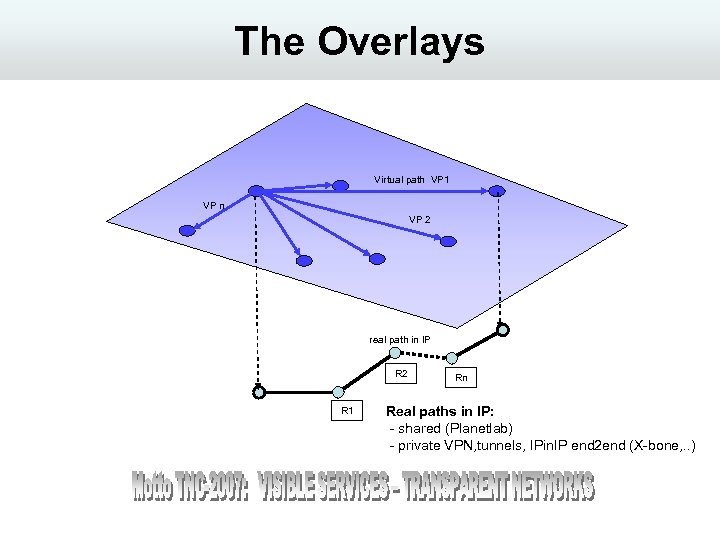 The Overlays Virtual path VP 1 VP n VP 2 real path in IP R 2 R 1 Rn Real paths in IP: - shared (Planetlab) - private VPN, tunnels, IPin. IP end 2 end (X-bone, . . )
The Overlays Virtual path VP 1 VP n VP 2 real path in IP R 2 R 1 Rn Real paths in IP: - shared (Planetlab) - private VPN, tunnels, IPin. IP end 2 end (X-bone, . . )
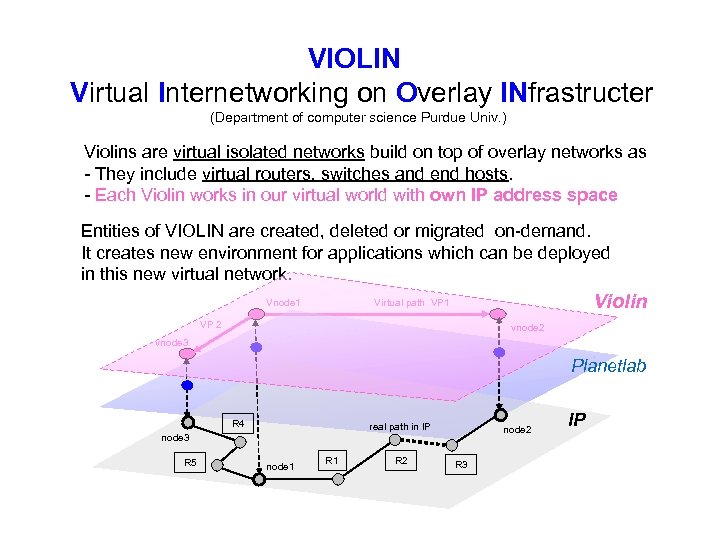 VIOLIN Virtual Internetworking on Overlay INfrastructer (Department of computer science Purdue Univ. ) Violins are virtual isolated networks build on top of overlay networks as - They include virtual routers, switches and end hosts. - Each Violin works in our virtual world with own IP address space Entities of VIOLIN are created, deleted or migrated on-demand. It creates new environment for applications which can be deployed in this new virtual network. Vnode 1 Violin Virtual path VP 1 VP 2 vnode 3 Planetlab R 4 real path in IP node 3 R 5 node 1 R 2 node 2 R 3 IP
VIOLIN Virtual Internetworking on Overlay INfrastructer (Department of computer science Purdue Univ. ) Violins are virtual isolated networks build on top of overlay networks as - They include virtual routers, switches and end hosts. - Each Violin works in our virtual world with own IP address space Entities of VIOLIN are created, deleted or migrated on-demand. It creates new environment for applications which can be deployed in this new virtual network. Vnode 1 Violin Virtual path VP 1 VP 2 vnode 3 Planetlab R 4 real path in IP node 3 R 5 node 1 R 2 node 2 R 3 IP
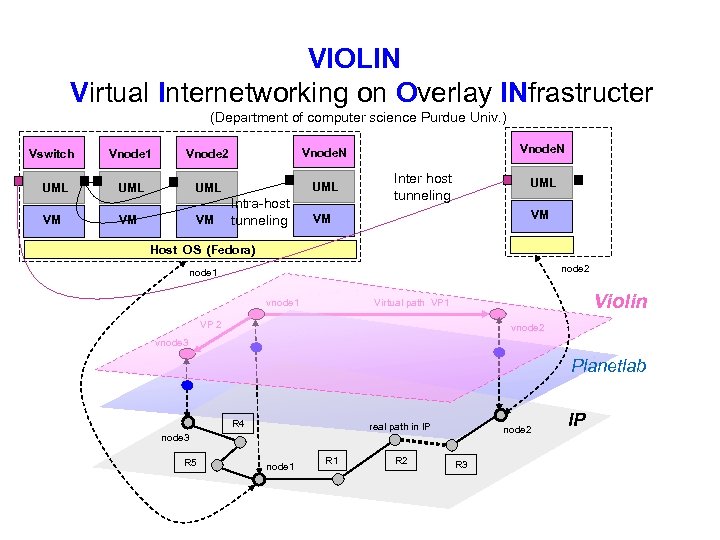 VIOLIN Virtual Internetworking on Overlay INfrastructer (Department of computer science Purdue Univ. ) Vswitch Vnode 1 Vnode 2 UML UML VM VM VM Vnode. N Intra-host tunneling Inter host tunneling UML VM VM Host OS (Fedora) node 2 node 1 vnode 1 Violin Virtual path VP 1 VP 2 vnode 3 Planetlab R 4 real path in IP node 3 R 5 node 1 R 2 node 2 R 3 IP
VIOLIN Virtual Internetworking on Overlay INfrastructer (Department of computer science Purdue Univ. ) Vswitch Vnode 1 Vnode 2 UML UML VM VM VM Vnode. N Intra-host tunneling Inter host tunneling UML VM VM Host OS (Fedora) node 2 node 1 vnode 1 Violin Virtual path VP 1 VP 2 vnode 3 Planetlab R 4 real path in IP node 3 R 5 node 1 R 2 node 2 R 3 IP
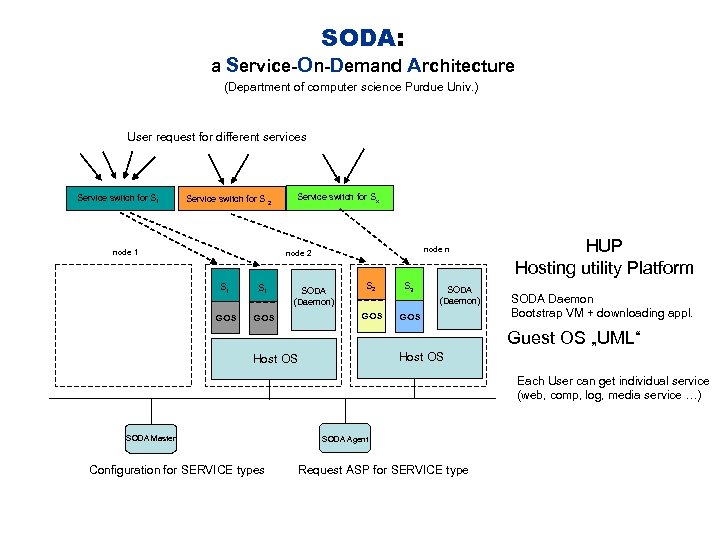 SODA: a Service-On-Demand Architecture (Department of computer science Purdue Univ. ) User request for different services Service switch for S 1 Service switch for S 2 node 1 Service switch for Sx node n node 2 S 1 G-OS S 2 S 3 G-OS SODA (Daemon) HUP Hosting utility Platform SODA Daemon Bootstrap VM + downloading appl. Guest OS „UML“ Host OS Each User can get individual service (web, comp, log, media service …) SODA Master Configuration for SERVICE types SODA Agent Request ASP for SERVICE type
SODA: a Service-On-Demand Architecture (Department of computer science Purdue Univ. ) User request for different services Service switch for S 1 Service switch for S 2 node 1 Service switch for Sx node n node 2 S 1 G-OS S 2 S 3 G-OS SODA (Daemon) HUP Hosting utility Platform SODA Daemon Bootstrap VM + downloading appl. Guest OS „UML“ Host OS Each User can get individual service (web, comp, log, media service …) SODA Master Configuration for SERVICE types SODA Agent Request ASP for SERVICE type
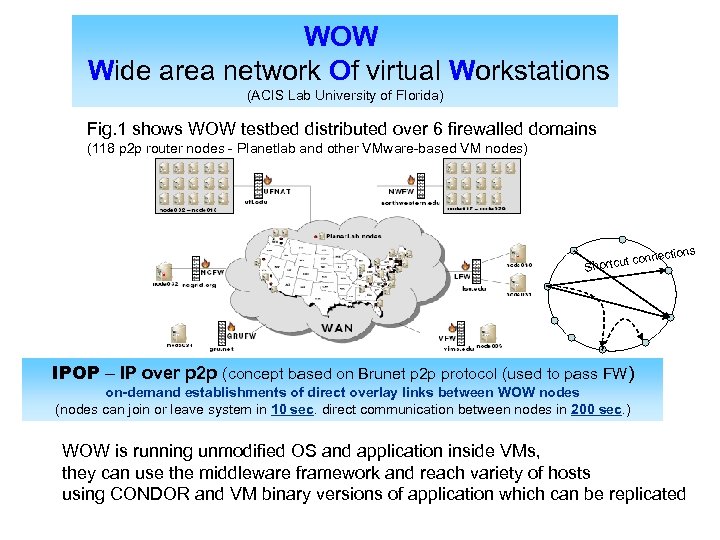 WOW Wide area network Of virtual Workstations (ACIS Lab University of Florida) Fig. 1 shows WOW testbed distributed over 6 firewalled domains (118 p 2 p router nodes - Planetlab and other VMware-based VM nodes) t con Shortcu s nection IPOP – IP over p 2 p (concept based on Brunet p 2 p protocol (used to pass FW) on-demand establishments of direct overlay links between WOW nodes (nodes can join or leave system in 10 sec. direct communication between nodes in 200 sec. ) WOW is running unmodified OS and application inside VMs, they can use the middleware framework and reach variety of hosts using CONDOR and VM binary versions of application which can be replicated
WOW Wide area network Of virtual Workstations (ACIS Lab University of Florida) Fig. 1 shows WOW testbed distributed over 6 firewalled domains (118 p 2 p router nodes - Planetlab and other VMware-based VM nodes) t con Shortcu s nection IPOP – IP over p 2 p (concept based on Brunet p 2 p protocol (used to pass FW) on-demand establishments of direct overlay links between WOW nodes (nodes can join or leave system in 10 sec. direct communication between nodes in 200 sec. ) WOW is running unmodified OS and application inside VMs, they can use the middleware framework and reach variety of hosts using CONDOR and VM binary versions of application which can be replicated
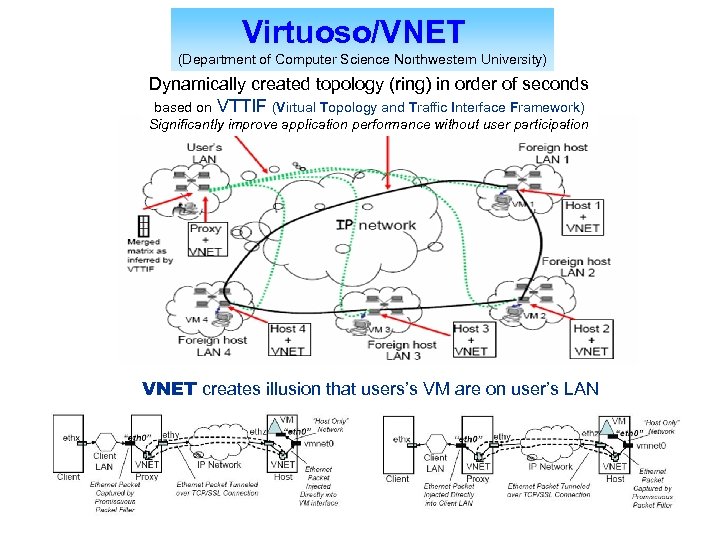 Virtuoso/VNET (Department of Computer Science Northwestern University) Dynamically created topology (ring) in order of seconds based on VTTIF (Virtual Topology and Traffic Interface Framework) Significantly improve application performance without user participation VNET creates illusion that users’s VM are on user’s LAN
Virtuoso/VNET (Department of Computer Science Northwestern University) Dynamically created topology (ring) in order of seconds based on VTTIF (Virtual Topology and Traffic Interface Framework) Significantly improve application performance without user participation VNET creates illusion that users’s VM are on user’s LAN
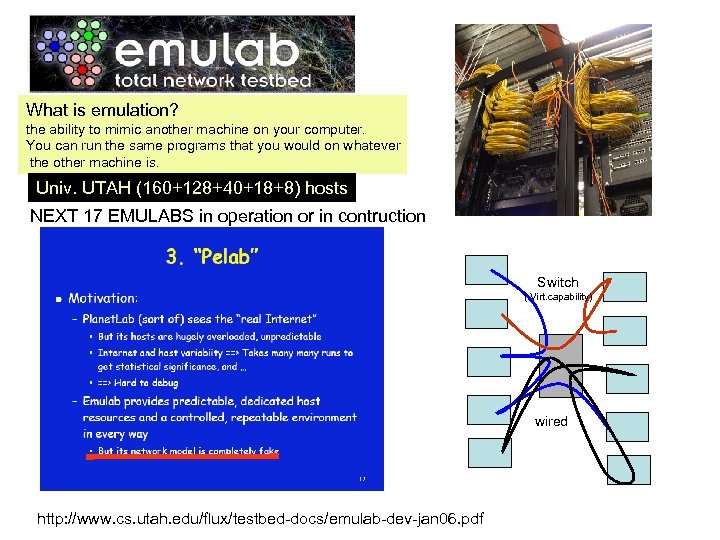 What is emulation? the ability to mimic another machine on your computer. You can run the same programs that you would on whatever the other machine is. Univ. UTAH (160+128+40+18+8) hosts NEXT 17 EMULABS in operation or in contruction Switch ( Virt. capability) wired http: //www. cs. utah. edu/flux/testbed-docs/emulab-dev-jan 06. pdf
What is emulation? the ability to mimic another machine on your computer. You can run the same programs that you would on whatever the other machine is. Univ. UTAH (160+128+40+18+8) hosts NEXT 17 EMULABS in operation or in contruction Switch ( Virt. capability) wired http: //www. cs. utah. edu/flux/testbed-docs/emulab-dev-jan 06. pdf
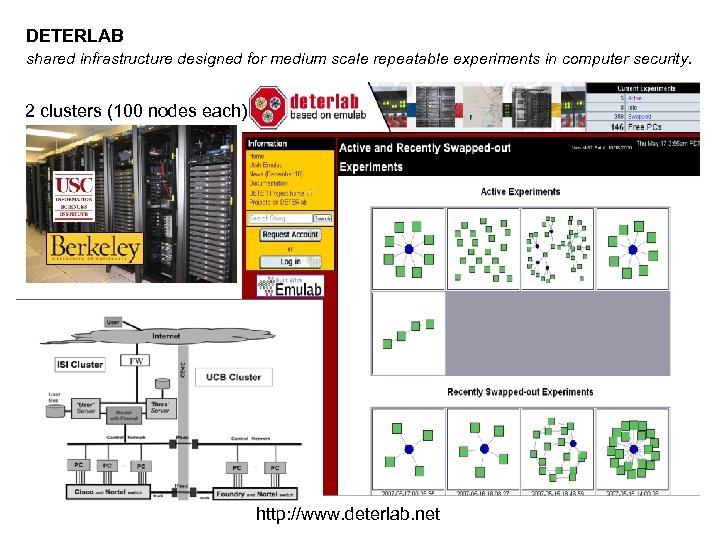 DETERLAB shared infrastructure designed for medium scale repeatable experiments in computer security. 2 clusters (100 nodes each) http: //www. deterlab. net
DETERLAB shared infrastructure designed for medium scale repeatable experiments in computer security. 2 clusters (100 nodes each) http: //www. deterlab. net
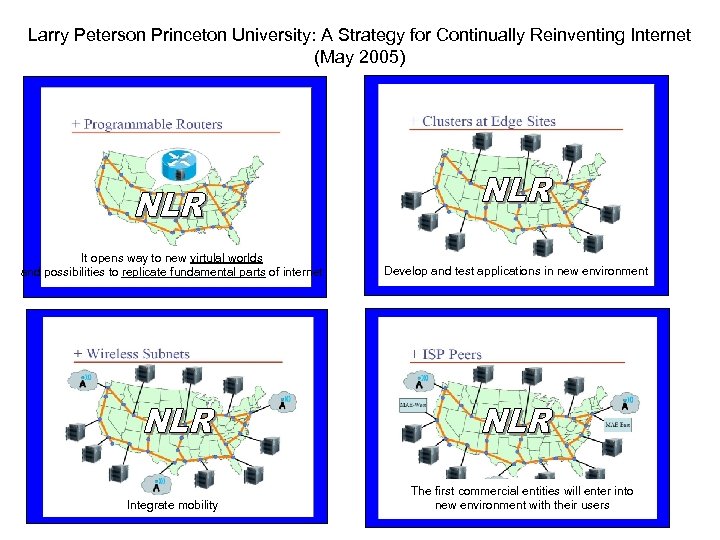 Larry Peterson Princeton University: A Strategy for Continually Reinventing Internet (May 2005) It opens way to new virtulal worlds and possibilities to replicate fundamental parts of internet Integrate mobility Develop and test applications in new environment The first commercial entities will enter into new environment with their users
Larry Peterson Princeton University: A Strategy for Continually Reinventing Internet (May 2005) It opens way to new virtulal worlds and possibilities to replicate fundamental parts of internet Integrate mobility Develop and test applications in new environment The first commercial entities will enter into new environment with their users
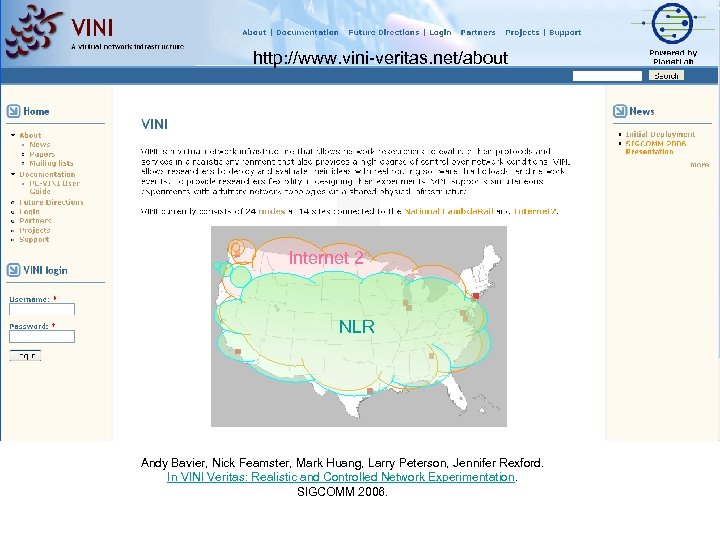 http: //www. vini-veritas. net/about Internet 2 NLR Andy Bavier, Nick Feamster, Mark Huang, Larry Peterson, Jennifer Rexford. In VINI Veritas: Realistic and Controlled Network Experimentation. SIGCOMM 2006.
http: //www. vini-veritas. net/about Internet 2 NLR Andy Bavier, Nick Feamster, Mark Huang, Larry Peterson, Jennifer Rexford. In VINI Veritas: Realistic and Controlled Network Experimentation. SIGCOMM 2006.
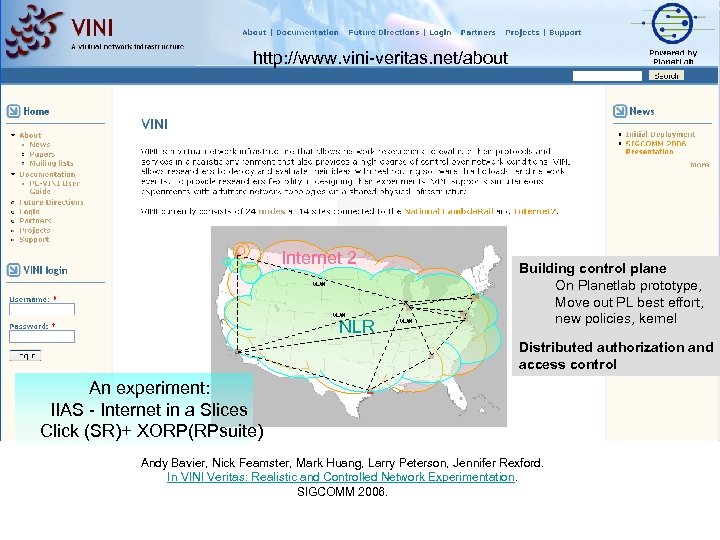 http: //www. vini-veritas. net/about Internet 2 VLAN NLR VLAN Building control plane On Planetlab prototype, Move out PL best effort, new policies, kernel Distributed authorization and access control An experiment: IIAS - Internet in a Slices Click (SR)+ XORP(RPsuite) Andy Bavier, Nick Feamster, Mark Huang, Larry Peterson, Jennifer Rexford. In VINI Veritas: Realistic and Controlled Network Experimentation. SIGCOMM 2006.
http: //www. vini-veritas. net/about Internet 2 VLAN NLR VLAN Building control plane On Planetlab prototype, Move out PL best effort, new policies, kernel Distributed authorization and access control An experiment: IIAS - Internet in a Slices Click (SR)+ XORP(RPsuite) Andy Bavier, Nick Feamster, Mark Huang, Larry Peterson, Jennifer Rexford. In VINI Veritas: Realistic and Controlled Network Experimentation. SIGCOMM 2006.
 The main objective of the Euro NGI network is to create the European center of excellence in Next Generation Internet design and engineering, acting as a "Collective Intelligence Think Tank", representing a major support for the European Information Society industry and leading towards a European leadership in this domain.
The main objective of the Euro NGI network is to create the European center of excellence in Next Generation Internet design and engineering, acting as a "Collective Intelligence Think Tank", representing a major support for the European Information Society industry and leading towards a European leadership in this domain.
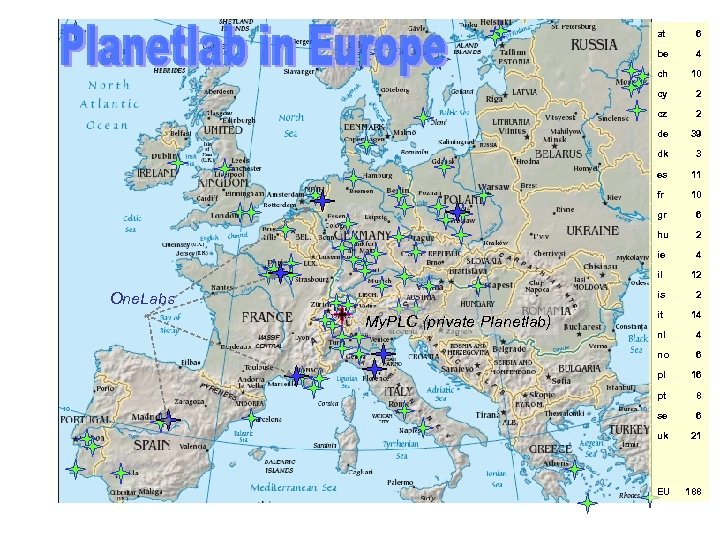 at be 10 cy 2 cz 2 de 39 dk 3 es 11 fr 10 gr 6 hu 2 ie 4 il 12 is My. PLC (private Planetlab) 4 ch One. Labs 6 2 it 14 nl 4 no 6 pl 16 pt 8 se 6 uk 21 EU 188
at be 10 cy 2 cz 2 de 39 dk 3 es 11 fr 10 gr 6 hu 2 ie 4 il 12 is My. PLC (private Planetlab) 4 ch One. Labs 6 2 it 14 nl 4 no 6 pl 16 pt 8 se 6 uk 21 EU 188
 One. Lab Goals Extend Planet. Lab into new environments, beyond the traditional wired internet. Deepen Planet. Lab’s monitoring capabilities. Federate - Provide a European administration for Planet. Lab nodes in Europe.
One. Lab Goals Extend Planet. Lab into new environments, beyond the traditional wired internet. Deepen Planet. Lab’s monitoring capabilities. Federate - Provide a European administration for Planet. Lab nodes in Europe.
 FP 6 projects • MUPBED creates an experimental environment to assess the proposed network solutions, and that will be offered as an open test platform to other European research projects and users. The test bed will represent a multi-layer network based on IP/MPLS and ASON/GMPLS technologies, equipped with a unified control plane and designed to support the highly demanding applications of the European research community. • • MUSE creates an experimental environment for low cost multi-service access network. (internet to homes) NETQo. S - project proposes an autonomous policy-based management for wired/wireless heterogeneous communications networks aimed to provide enhanced end-to-end Qo. S and efficient resource utilization. • One. Lab will extend the highly successful and widely used Planet. Lab infrastructure by enabling deployment of • PANLAB – This will serve as a Technology Roadmap and as a Strategic Development Guideline for • Phosphorus - High capacity optical networking can satisfy bandwidth and latency requirements, but software • WEIRD is integrated project aiming at implementing research test-beds using the Wi. MAX technology in order to allow isolated or impervious areas to get connection to the GEANT 2 research network. • WWI Ambient Networks project will create the network solutions for mobile and wireless systems beyond 3 G. It will enable scalable and affordable wireless networking while providing rich and easy to use communication services for all. Ambient Networks offers a fundamentally new vision based on the dynamic composition of networks to avoid adding to the growing patchwork of extensions to existing architectures. Planet. Lab nodes in new wireless environments. European and global telecommunications. tools and frameworks for end-to-end, on-demand provisioning of network services need to be developed in coordination with other resources (CPU and storage) and need to span multiple administrative and network technology domains.
FP 6 projects • MUPBED creates an experimental environment to assess the proposed network solutions, and that will be offered as an open test platform to other European research projects and users. The test bed will represent a multi-layer network based on IP/MPLS and ASON/GMPLS technologies, equipped with a unified control plane and designed to support the highly demanding applications of the European research community. • • MUSE creates an experimental environment for low cost multi-service access network. (internet to homes) NETQo. S - project proposes an autonomous policy-based management for wired/wireless heterogeneous communications networks aimed to provide enhanced end-to-end Qo. S and efficient resource utilization. • One. Lab will extend the highly successful and widely used Planet. Lab infrastructure by enabling deployment of • PANLAB – This will serve as a Technology Roadmap and as a Strategic Development Guideline for • Phosphorus - High capacity optical networking can satisfy bandwidth and latency requirements, but software • WEIRD is integrated project aiming at implementing research test-beds using the Wi. MAX technology in order to allow isolated or impervious areas to get connection to the GEANT 2 research network. • WWI Ambient Networks project will create the network solutions for mobile and wireless systems beyond 3 G. It will enable scalable and affordable wireless networking while providing rich and easy to use communication services for all. Ambient Networks offers a fundamentally new vision based on the dynamic composition of networks to avoid adding to the growing patchwork of extensions to existing architectures. Planet. Lab nodes in new wireless environments. European and global telecommunications. tools and frameworks for end-to-end, on-demand provisioning of network services need to be developed in coordination with other resources (CPU and storage) and need to span multiple administrative and network technology domains.
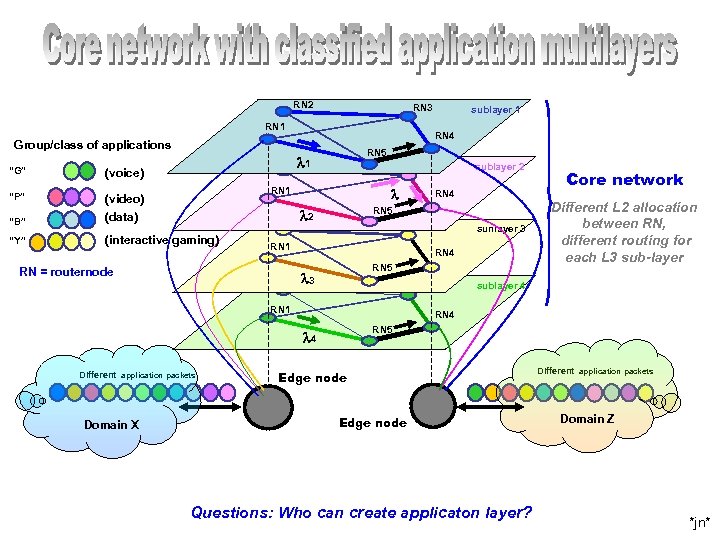 RN 2 RN 3 RN 1 RN 4 Group/class of applications “G” RN 5 l 1 (voice) sublayer 2 RN 1 “P” (video) “B” (data) “Y” (interactive gaming) l sunlayer 3 RN 1 RN = routernode RN 4 RN 5 l 3 Core network Different L 2 allocation between RN, different routing for each L 3 sub-layer sublayer 4 RN 1 RN 4 RN 5 l 4 Domain X RN 4 RN 5 l 2 Different application packets sublayer 1 Edge node Questions: Who can create applicaton layer? Different application packets Domain Z *jn*
RN 2 RN 3 RN 1 RN 4 Group/class of applications “G” RN 5 l 1 (voice) sublayer 2 RN 1 “P” (video) “B” (data) “Y” (interactive gaming) l sunlayer 3 RN 1 RN = routernode RN 4 RN 5 l 3 Core network Different L 2 allocation between RN, different routing for each L 3 sub-layer sublayer 4 RN 1 RN 4 RN 5 l 4 Domain X RN 4 RN 5 l 2 Different application packets sublayer 1 Edge node Questions: Who can create applicaton layer? Different application packets Domain Z *jn*
 Thank You for your attention
Thank You for your attention


