16e43d5eea0eabc5974932dfa5dfa7ec.ppt
- Количество слайдов: 86

The Internet CIT 232 ©IFM-CIT Dept
OBJECTIVES Know how the Internet began. Understand the architecture of today’s Internet and its relationship with ISPs. Understand the importance of the TCP/IP protocol suite. Understand the role of IP, UDP, and TCP in the Internet. Understand the difference between the Internet, an intranet, and an extranet. CIT 232 ©IFM-CIT Dept

Internet History The internet traces its origins to a military network called ARPANET was created in response to an increased need for national security, and the need to connect remote computing resources. After ARPARET, other private network sprang up , and eventually all of these networks were connected. The connection of these networks formed what we call the Internet. Read the handout CIT 232 ©IFM-CIT Dept

CIT 232 ©IFM-CIT Dept
Internet Terms 1. Internet 2. Packet Switching Network 3. Modem - Modulator/Demodulator CIT 232 ©IFM-CIT Dept
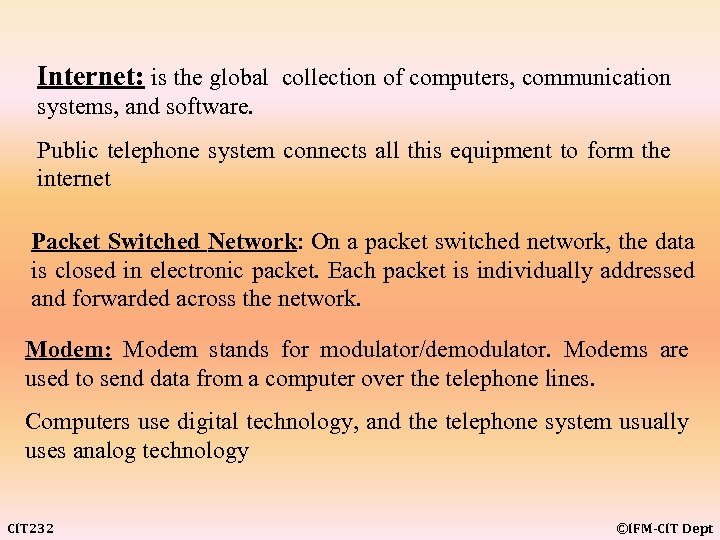
Internet: is the global collection of computers, communication systems, and software. Public telephone system connects all this equipment to form the internet Packet Switched Network: On a packet switched network, the data is closed in electronic packet. Each packet is individually addressed and forwarded across the network. Modem: Modem stands for modulator/demodulator. Modems are used to send data from a computer over the telephone lines. Computers use digital technology, and the telephone system usually uses analog technology CIT 232 ©IFM-CIT Dept
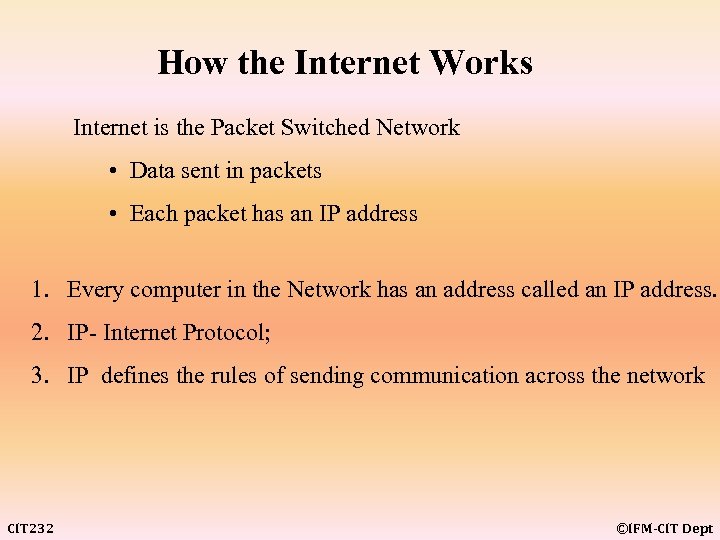
How the Internet Works Internet is the Packet Switched Network • Data sent in packets • Each packet has an IP address 1. Every computer in the Network has an address called an IP address. 2. IP- Internet Protocol; 3. IP defines the rules of sending communication across the network CIT 232 ©IFM-CIT Dept
Internet is the Packet Switched Network 1. Internet is the switched network means data sent over internet is encapsulated in packets 2. The packets are addressed according to their destination 3. Internet database keep track of the addresses and allow networking equipment to forward packet to the correct computer. 4. This analogy to telephone systems. CIT 232 ©IFM-CIT Dept
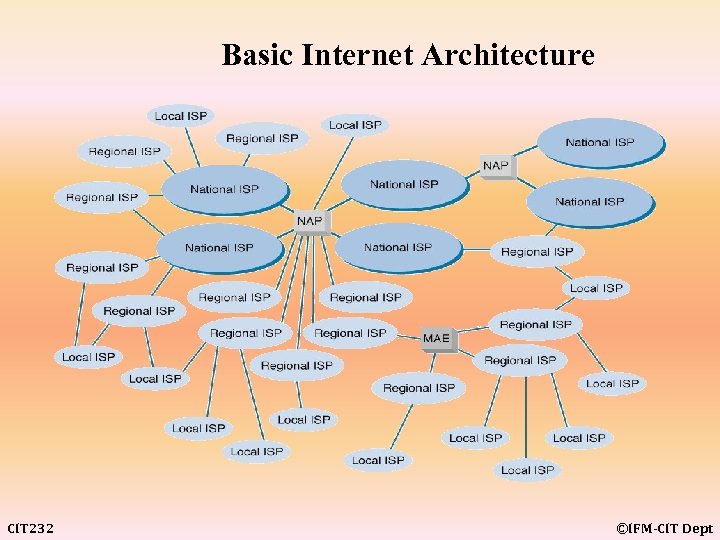
Basic Internet Architecture CIT 232 ©IFM-CIT Dept
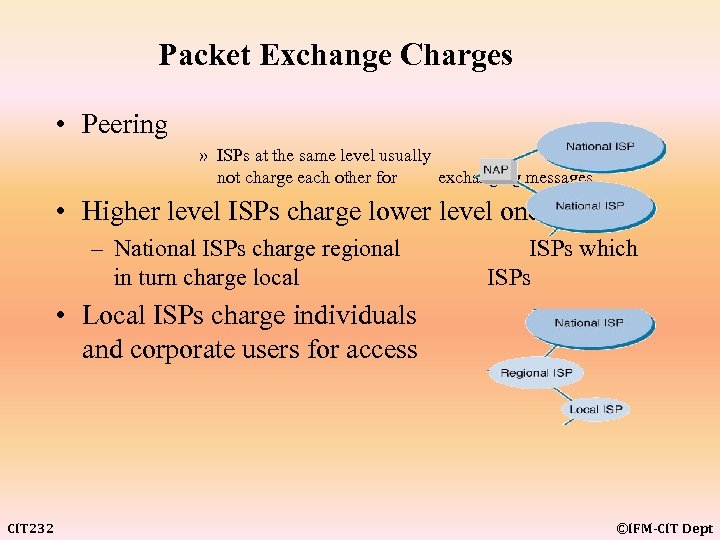
Packet Exchange Charges • Peering » ISPs at the same level usually not charge each other for exchanging messages do • Higher level ISPs charge lower level ones – National ISPs charge regional in turn charge local ISPs which ISPs • Local ISPs charge individuals and corporate users for access CIT 232 ©IFM-CIT Dept
Connecting to an ISP • Done by through ISP’s Point of Presence (POP) – A place ISP provides service to its customers • Individual users – Typically through a dial-up line using the PPP protocol • Handled by the ISP’s modem pool – Userid and password checked by Remote Access Server (RAS) • Once logged in, the user can send packets over the phone line • Corporate users – Typically access the POP using a T-1, T-3 or ATM OC 3 connections provided by a common carrier • Cost = ISP charges + circuit charges CIT 232 ©IFM-CIT Dept
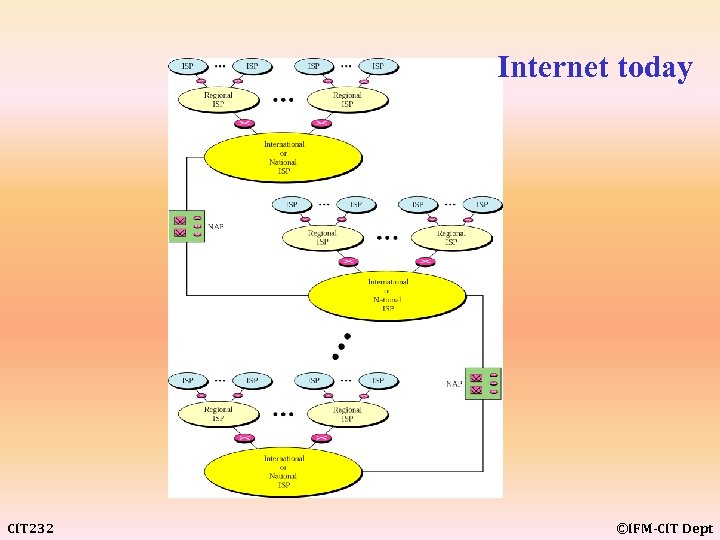
Internet today CIT 232 ©IFM-CIT Dept
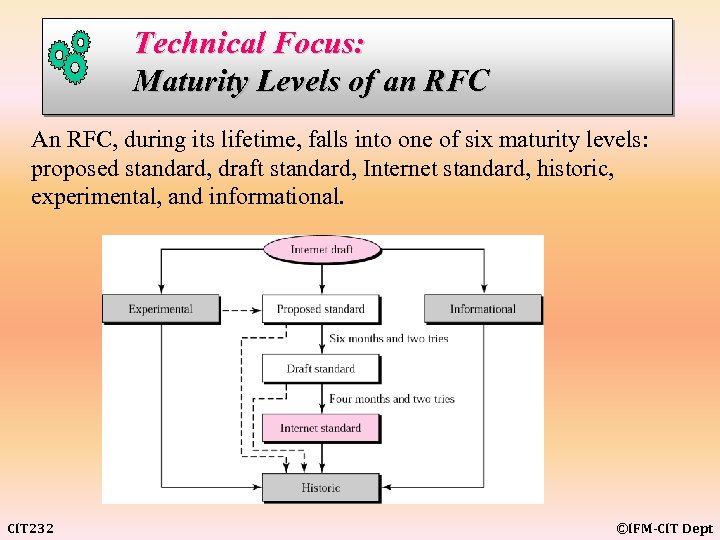
Technical Focus: Maturity Levels of an RFC An RFC, during its lifetime, falls into one of six maturity levels: proposed standard, draft standard, Internet standard, historic, experimental, and informational. CIT 232 ©IFM-CIT Dept
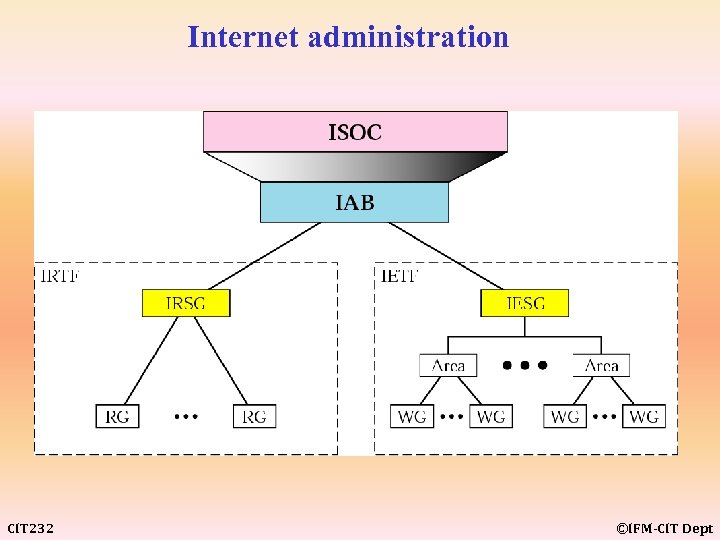
Internet administration CIT 232 ©IFM-CIT Dept

Internet Society ISOC: Is an international, nonprofit organization formed 1992 to provide support for internet standard process. ISOC supports other Internet administrative bodies such as IAB, IETF, IRTF and IANA. ISOC also promotes research and other scholarly activities related to the internet IAB - Internet Architecture Board IETF - Internet Engineering Task Force IRTF - Internet Research Task Force IANA - Internet Assign Number Authority CIT 232 ©IFM-CIT Dept
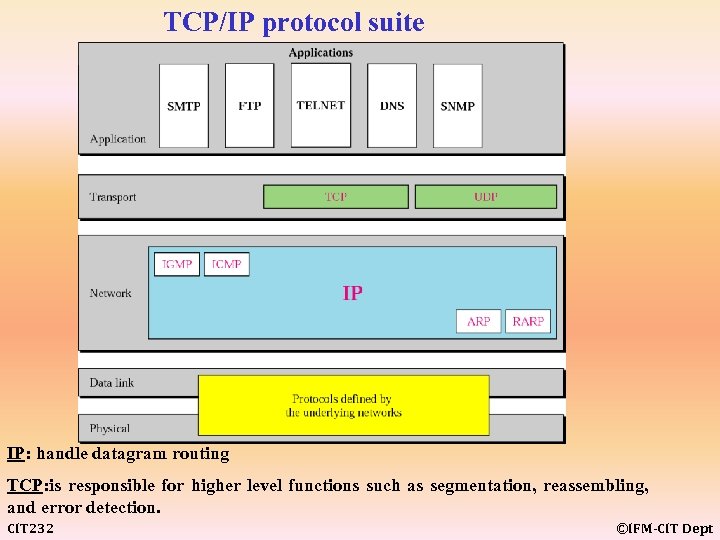
TCP/IP protocol suite IP: handle datagram routing TCP: is responsible for higher level functions such as segmentation, reassembling, and error detection. CIT 232 ©IFM-CIT Dept
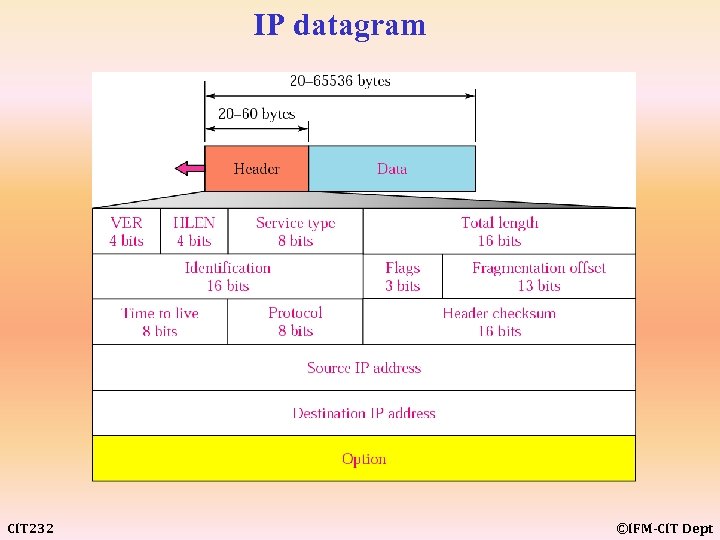
IP datagram CIT 232 ©IFM-CIT Dept

Technical Focus: Inside the Header of an IP Datagram An IP datagram contains several fields. The most important are the source and destination addresses of the datagram (IP addresses). The header also contains fields related to fragmentation. The size of a datagram may be too large for some LAN or WAN protocols. In this case, the datagram is divided into fragments; each fragment carries the same identification number as well as other information to help the receiver assemble the datagram. The header also has two length fields; one defines the length of the header, the other defines the length of the entire packet. One field that can decrease traffic on the Internet holds the number of routers a packet can visit before it is discarded. The header also contains a checksum field to determine the validity of the packet. CIT 232 ©IFM-CIT Dept

IP Address CIT 232 ©IFM-CIT Dept
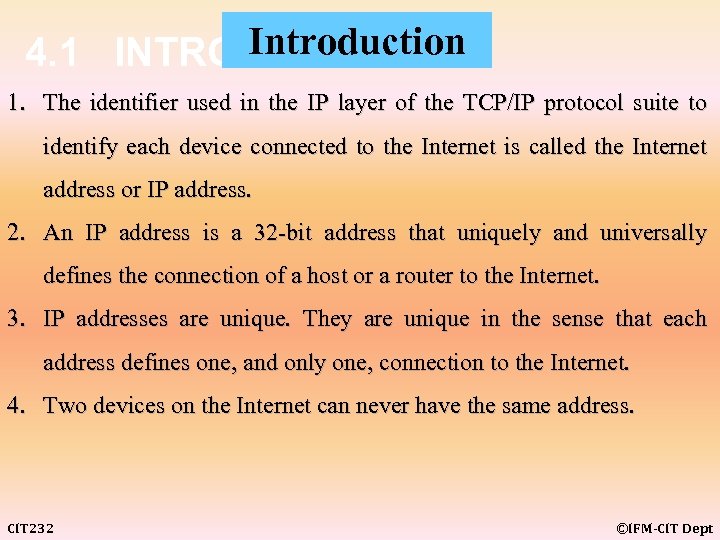
Introduction 4. 1 INTRODUCTION 1. The identifier used in the IP layer of the TCP/IP protocol suite to identify each device connected to the Internet is called the Internet address or IP address. 2. An IP address is a 32 -bit address that uniquely and universally defines the connection of a host or a router to the Internet. 3. IP addresses are unique. They are unique in the sense that each address defines one, and only one, connection to the Internet. 4. Two devices on the Internet can never have the same address. CIT 232 ©IFM-CIT Dept
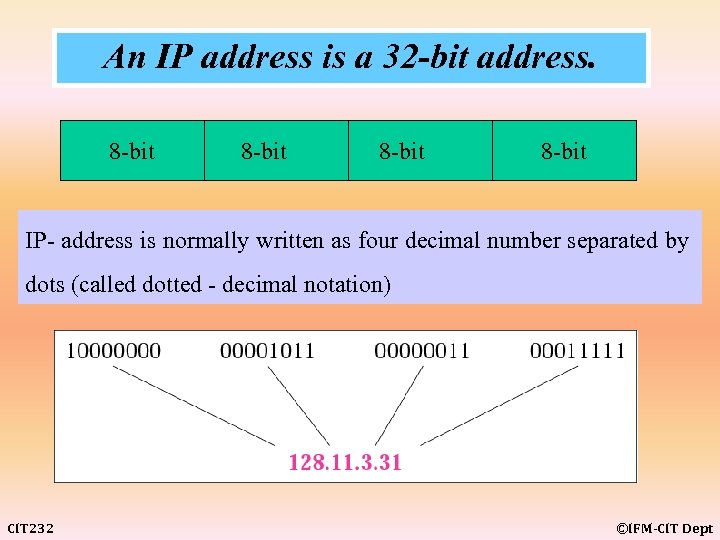
An IP address is a 32 -bit address. 8 -bit IP- address is normally written as four decimal number separated by dots (called dotted - decimal notation) CIT 232 ©IFM-CIT Dept

The address space of IPv 4 is 232 or 4, 294, 967, 296. CIT 232 ©IFM-CIT Dept

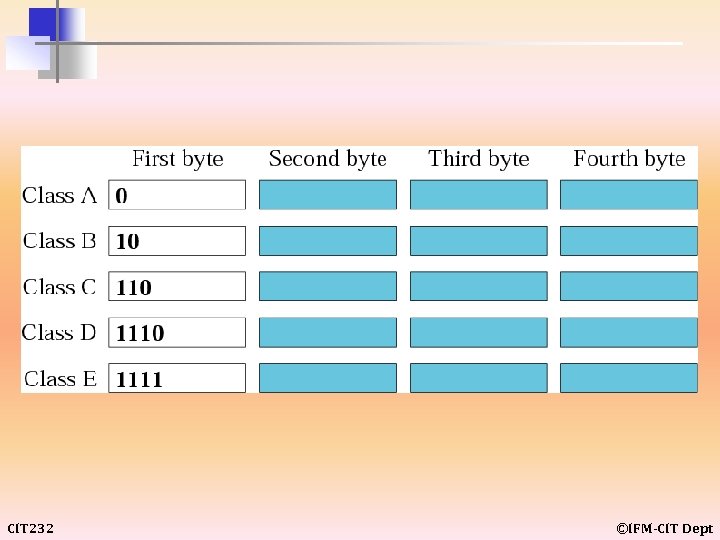
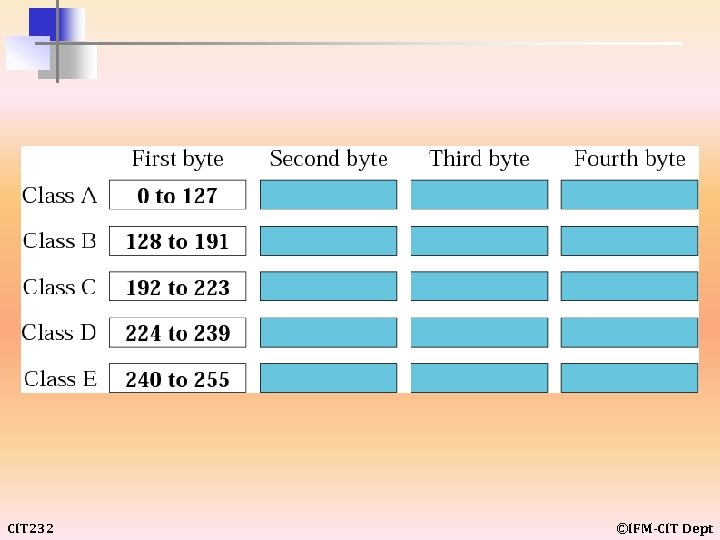
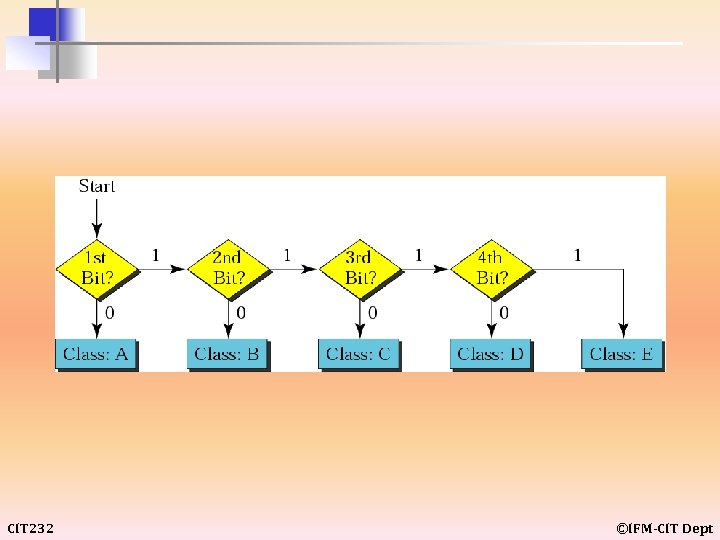
CLASSFUL ADDRESSING Classful addressing includes the following: • • Netid and Hostid • Classes and Blocks • Network Addresses • Sufficient Information • CIT 232 Recognizing Classes Mask ©IFM-CIT Dept
CIT 232 ©IFM-CIT Dept
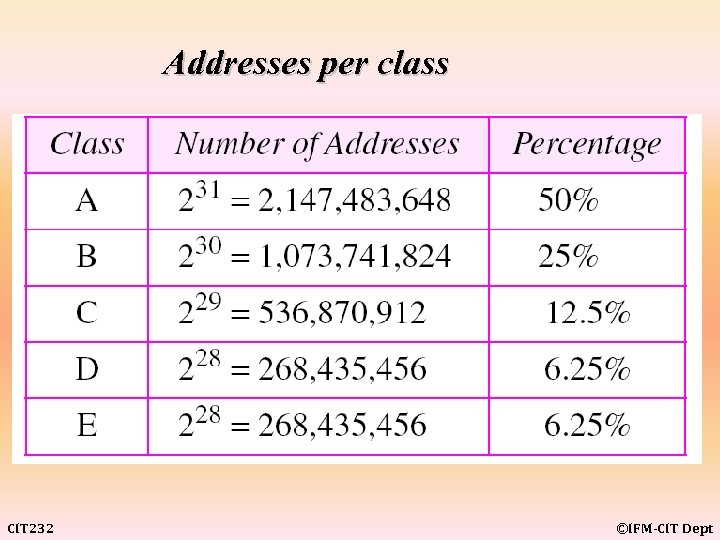
Addresses per class CIT 232 ©IFM-CIT Dept
CIT 232 ©IFM-CIT Dept
CIT 232 ©IFM-CIT Dept
CIT 232 ©IFM-CIT Dept

example 7 Find the class of each address: Solution a. The first byte is 227 (between 224 and 239); the class is D. b. The first byte is 193 (between 192 and 223); the class is C. c. The first byte is 14 (between 0 and 127); the class is A. d. The first byte is 252 (between 240 and 255); the class is E. e. The first byte is 134 (between 128 and 191); the class is B. CIT 232 ©IFM-CIT Dept
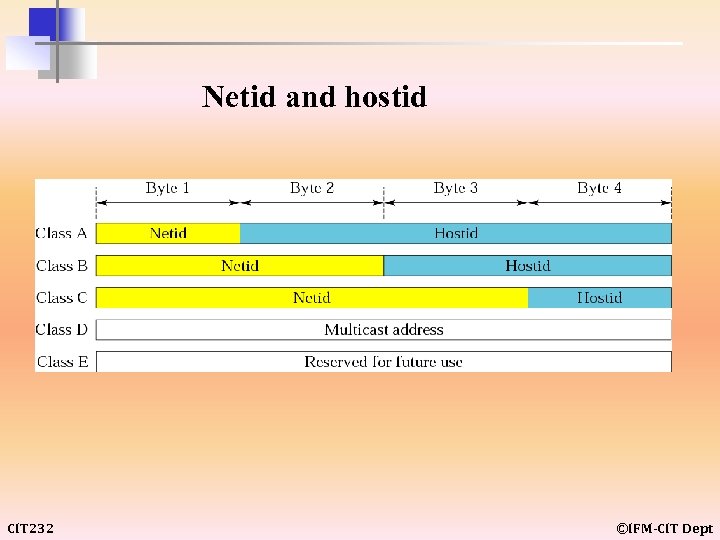
Netid and hostid CIT 232 ©IFM-CIT Dept
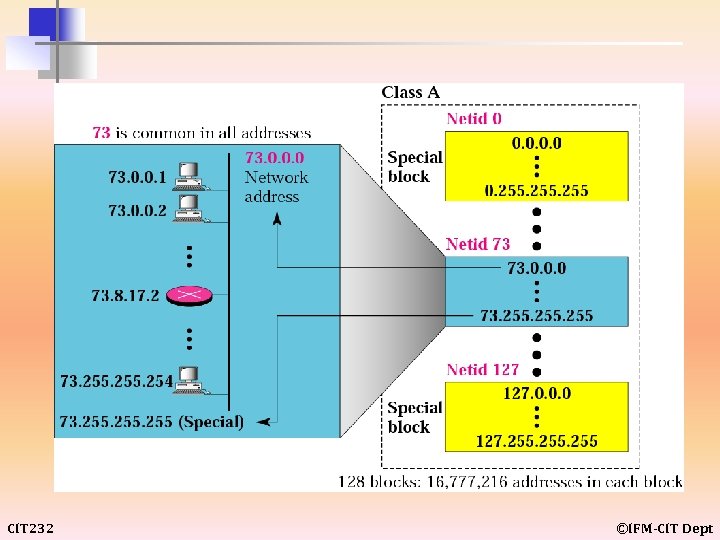
CIT 232 ©IFM-CIT Dept
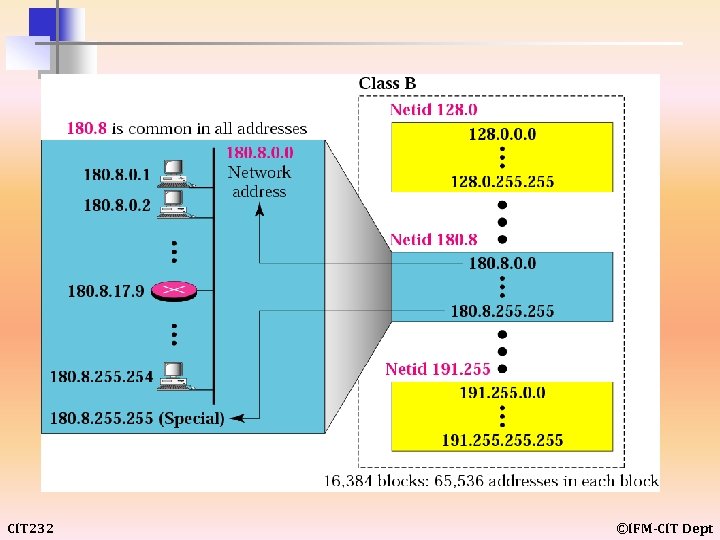
CIT 232 ©IFM-CIT Dept
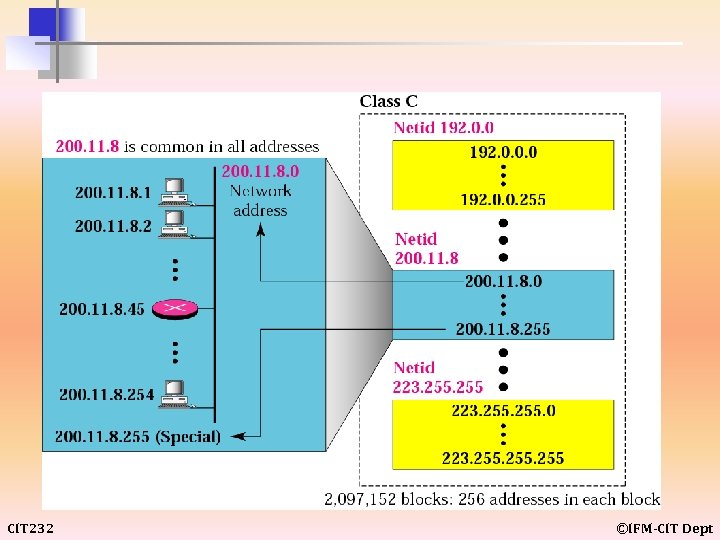
CIT 232 ©IFM-CIT Dept

The number of addresses in class C is smaller than the needs of most organizations. CIT 232 ©IFM-CIT Dept

Class D addresses are used for multicasting; there is only one block in this class. CIT 232 ©IFM-CIT Dept

Class E addresses are reserved for future purposes; most of the block is wasted. CIT 232 ©IFM-CIT Dept

In classful addressing, the network address (the first address in the block) is the one that is assigned to the organization. The range of addresses can automatically be inferred from the network address. CIT 232 ©IFM-CIT Dept
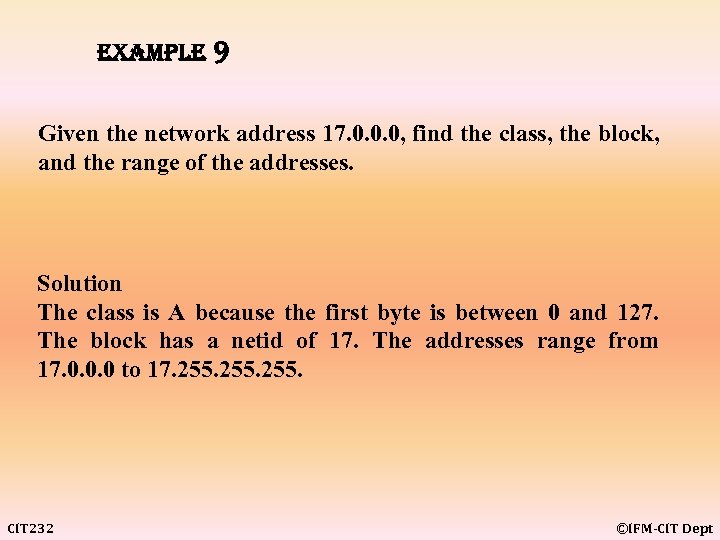
example 9 Given the network address 17. 0. 0. 0, find the class, the block, and the range of the addresses. Solution The class is A because the first byte is between 0 and 127. The block has a netid of 17. The addresses range from 17. 0. 0. 0 to 17. 255. CIT 232 ©IFM-CIT Dept

example 10 Given the network address 132. 21. 0. 0, find the class, the block, and the range of the addresses. Solution The class is B because the first byte is between 128 and 191. The block has a netid of 132. 21. The addresses range from 132. 21. 0. 0 to 132. 21. 255. CIT 232 ©IFM-CIT Dept
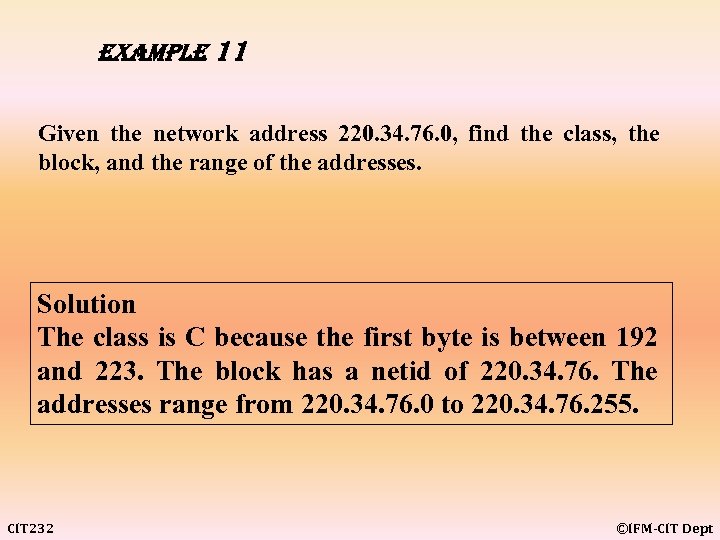
example 11 Given the network address 220. 34. 76. 0, find the class, the block, and the range of the addresses. Solution The class is C because the first byte is between 192 and 223. The block has a netid of 220. 34. 76. The addresses range from 220. 34. 76. 0 to 220. 34. 76. 255. CIT 232 ©IFM-CIT Dept
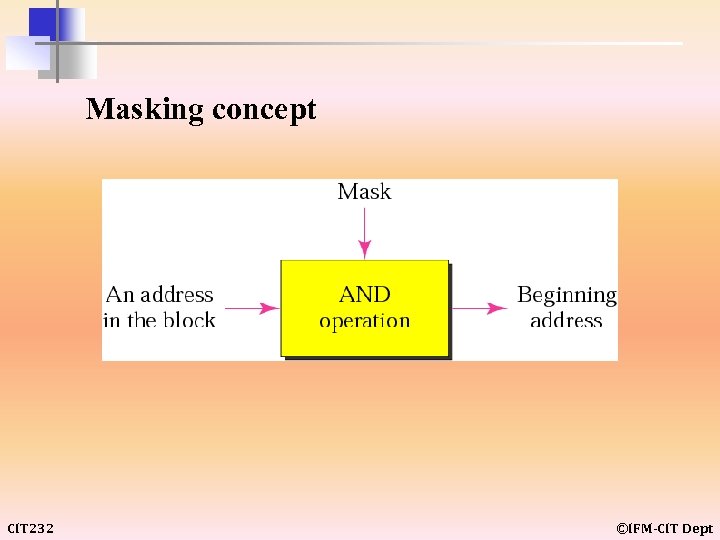
Masking concept CIT 232 ©IFM-CIT Dept
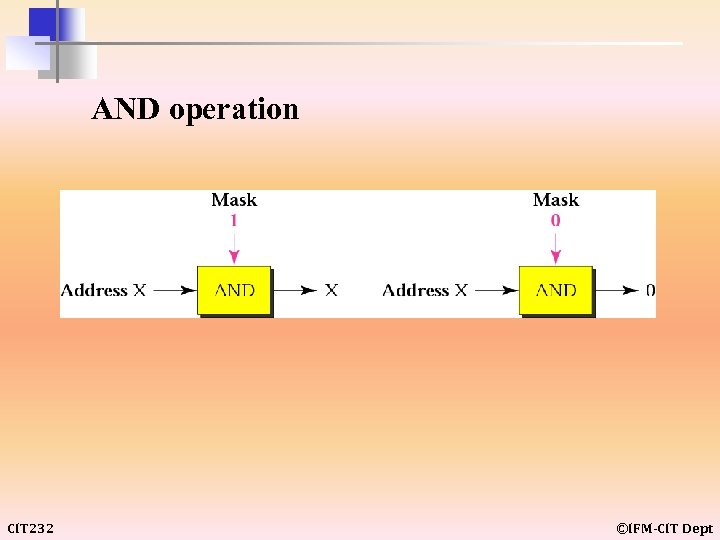
AND operation CIT 232 ©IFM-CIT Dept

Default masks CIT 232 ©IFM-CIT Dept

The network address is the beginning address of each block. It can be found by applying the default mask to any of the addresses in the block (including itself). It retains the netid of the block and sets the hostid to zero. CIT 232 ©IFM-CIT Dept

example Given the address 23. 56. 7. 91, find the beginning address (network address). Solution The default mask is 255. 0. 0. 0, which means that only the first byte is preserved and the other 3 bytes are set to 0 s. The network address is 23. 0. 0. 0. CIT 232 ©IFM-CIT Dept

exampl e Given the address 132. 6. 17. 85, find the beginning address (network address). Solution The default mask is 255. 0. 0, which means that the first 2 bytes are preserved and the other 2 bytes are set to 0 s. The network address is 132. 6. 0. 0. CIT 232 ©IFM-CIT Dept

example 14 Given the address 201. 180. 56. 5, find the beginning address (network address). Solution The default mask is 255. 0, which means that the first 3 bytes are preserved and the last byte is set to 0. The network address is 201. 180. 56. 0. CIT 232 ©IFM-CIT Dept

Note: Note that we must not apply the default mask of one class to an address belonging to another class. CIT 232 ©IFM-CIT Dept

4. 3 OTHER ISSUES In this section, we discuss some other issues that are related to addressing in general and classful addressing in particular. The topics discussed in this section include: Multihomed Devices Location, Not Names Special Addresses Private Addresses Unicast, Multicast, and Broadcast Addresses CIT 232 ©IFM-CIT Dept
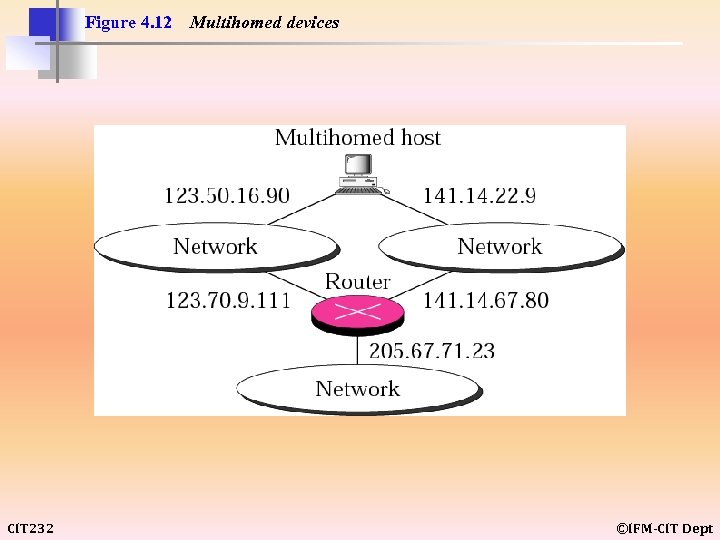
Figure 4. 12 CIT 232 Multihomed devices ©IFM-CIT Dept
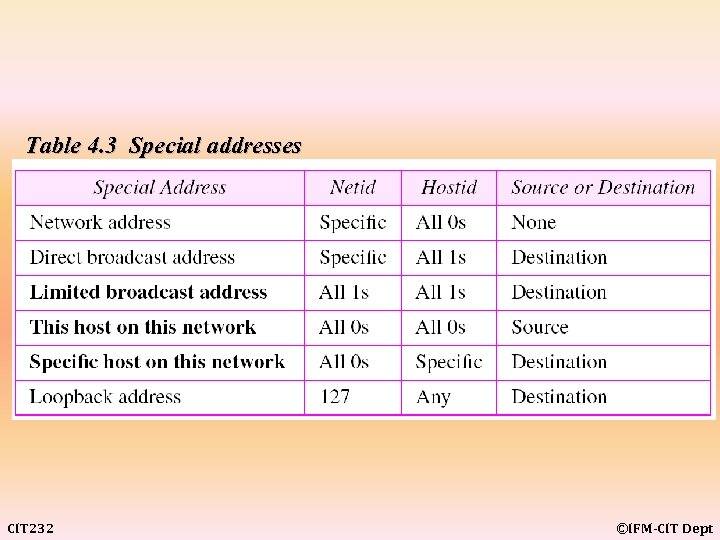
Table 4. 3 Special addresses CIT 232 ©IFM-CIT Dept
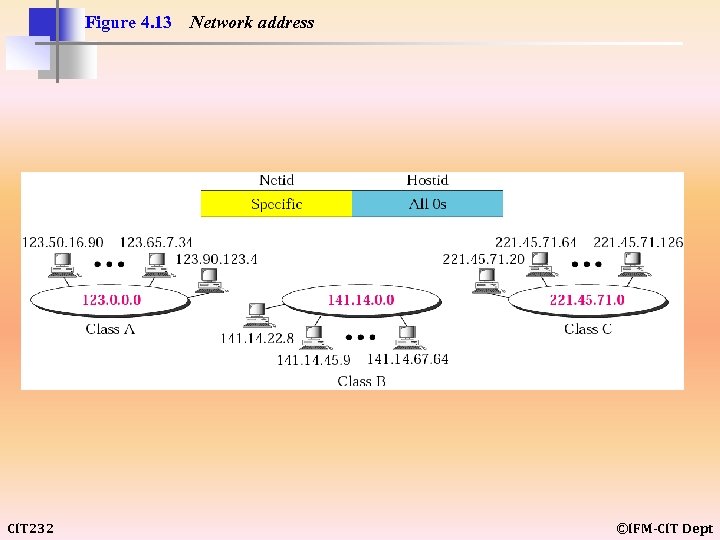
Figure 4. 13 CIT 232 Network address ©IFM-CIT Dept
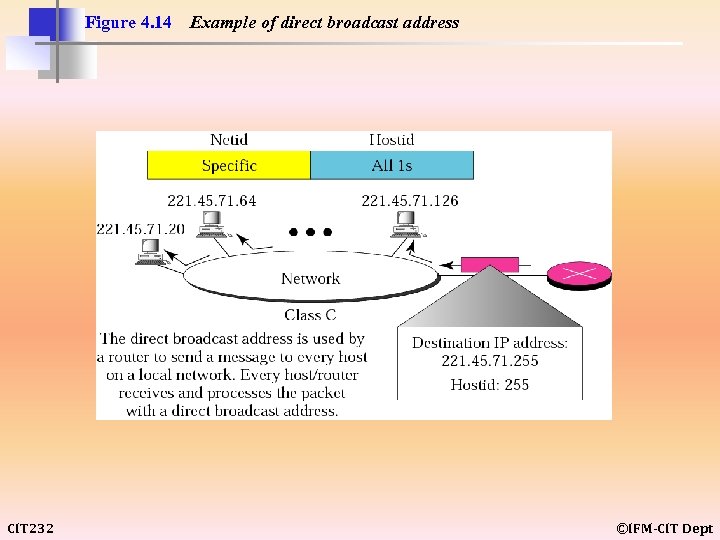
Figure 4. 14 CIT 232 Example of direct broadcast address ©IFM-CIT Dept
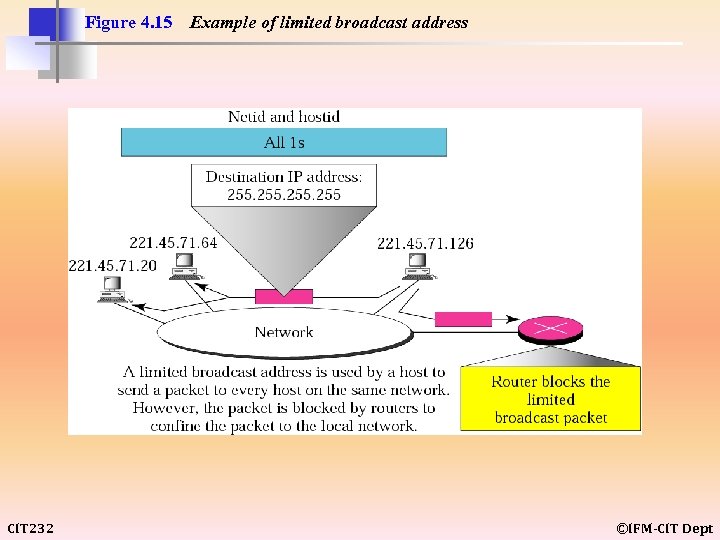
Figure 4. 15 CIT 232 Example of limited broadcast address ©IFM-CIT Dept
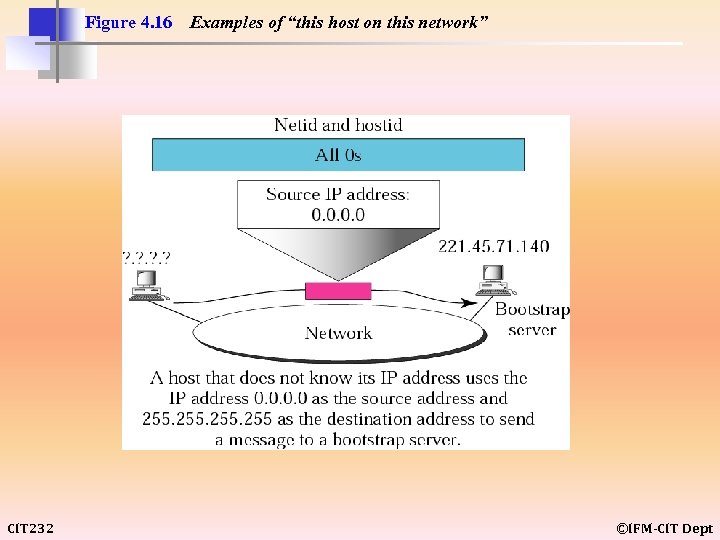
Figure 4. 16 CIT 232 Examples of “this host on this network” ©IFM-CIT Dept
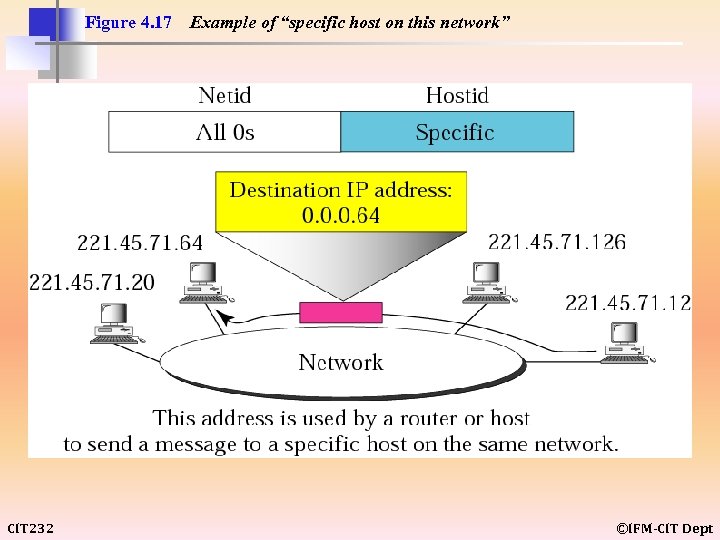
Figure 4. 17 CIT 232 Example of “specific host on this network” ©IFM-CIT Dept
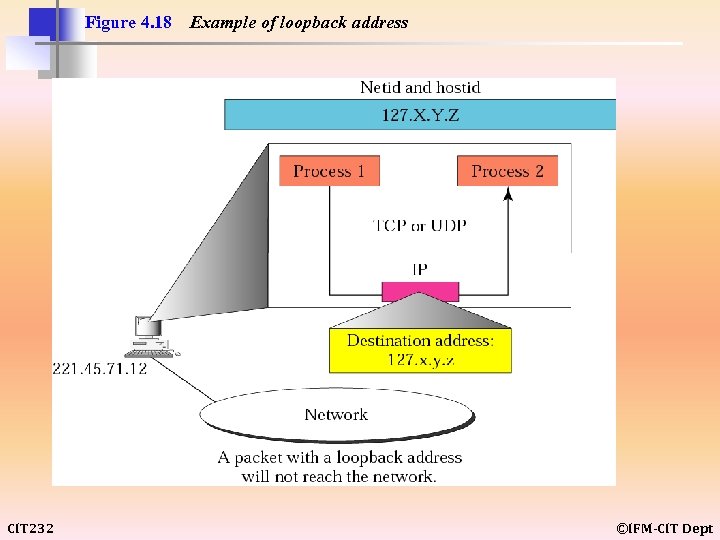
Figure 4. 18 CIT 232 Example of loopback address ©IFM-CIT Dept
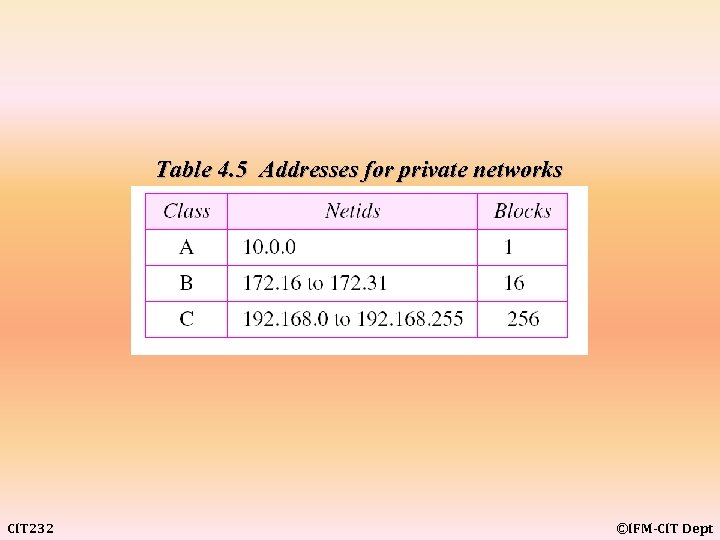
Table 4. 5 Addresses for private networks CIT 232 ©IFM-CIT Dept

Note: Multicast delivery will be discussed in depth in Chapter 15. CIT 232 ©IFM-CIT Dept
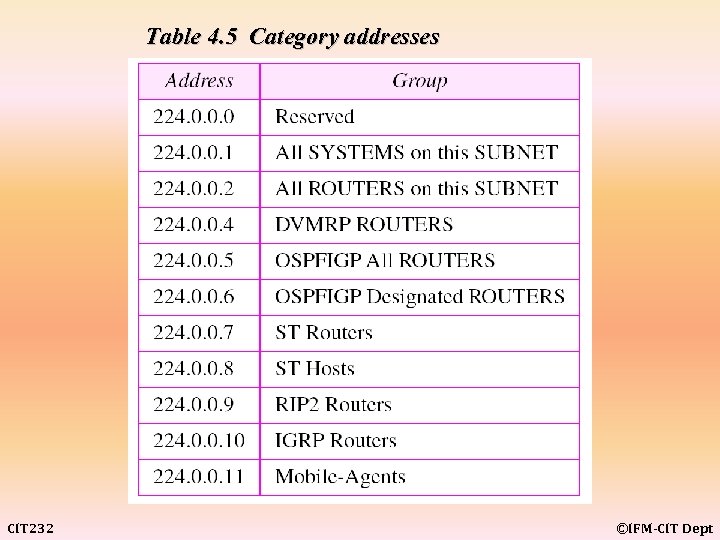
Table 4. 5 Category addresses CIT 232 ©IFM-CIT Dept
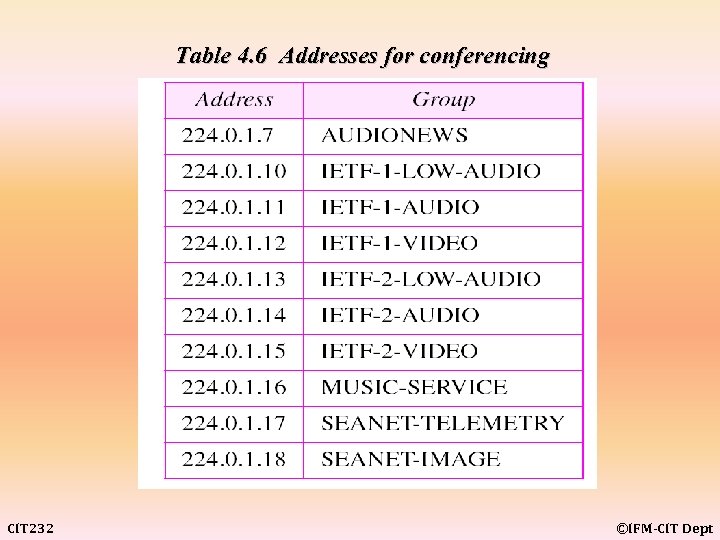
Table 4. 6 Addresses for conferencing CIT 232 ©IFM-CIT Dept
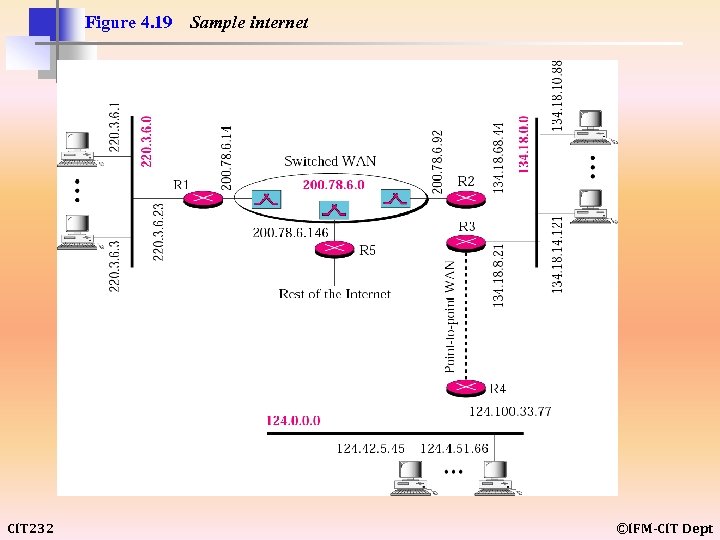
Figure 4. 19 CIT 232 Sample internet ©IFM-CIT Dept
4. 4 SUBNETTING AND SUPERNETTING In the previous sections we discussed the problems associated with classful addressing. Specifically, the network addresses available for assignment to organizations are close to depletion. This is coupled with the ever-increasing demand for addresses from organizations that want connection to the Internet. In this section we briefly discuss two solutions: subnetting and supernetting. The topics discussed in this section include: Subnetting Supernet Mask Obsolescence CIT 232 ©IFM-CIT Dept
Note: IP addresses are designed with two levels of hierarchy. CIT 232 ©IFM-CIT Dept
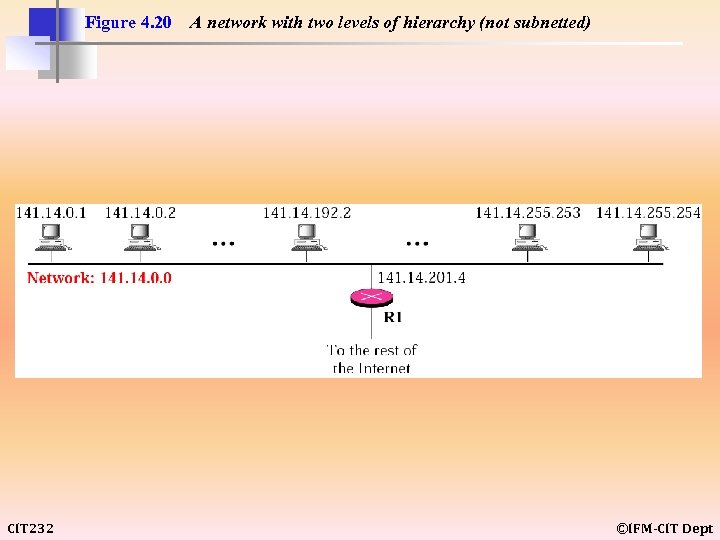
Figure 4. 20 CIT 232 A network with two levels of hierarchy (not subnetted) ©IFM-CIT Dept
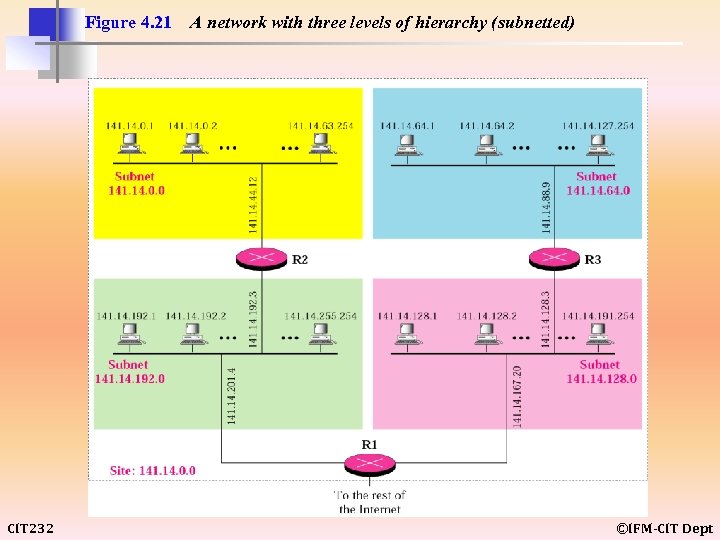
Figure 4. 21 CIT 232 A network with three levels of hierarchy (subnetted) ©IFM-CIT Dept
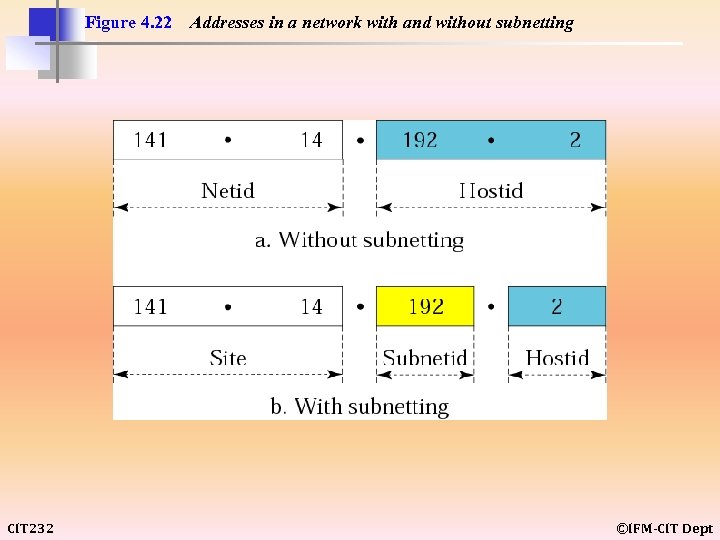
Figure 4. 22 CIT 232 Addresses in a network with and without subnetting ©IFM-CIT Dept
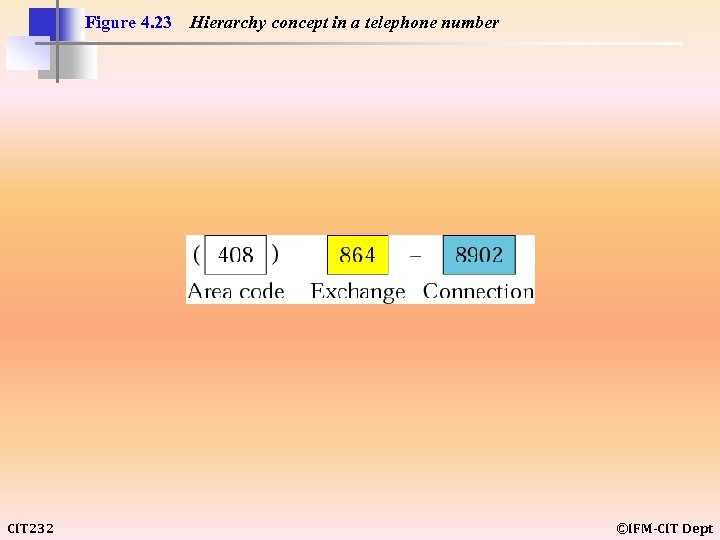
Figure 4. 23 CIT 232 Hierarchy concept in a telephone number ©IFM-CIT Dept
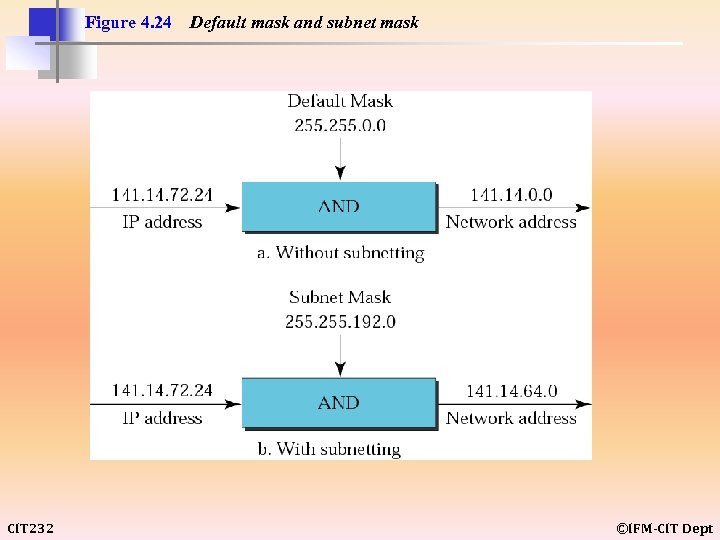
Figure 4. 24 CIT 232 Default mask and subnet mask ©IFM-CIT Dept

example 15 What is the subnetwork address if the destination address is 200. 45. 34. 56 and the subnet mask is 255. 240. 0? Solution We apply the AND operation on the address and the subnet mask. Address ➡ 11001000 00101101 0010 00111000 Subnet Mask ➡ 111111110000 Subnetwork Address ➡ 11001000 00101101 00100000. CIT 232 ©IFM-CIT Dept
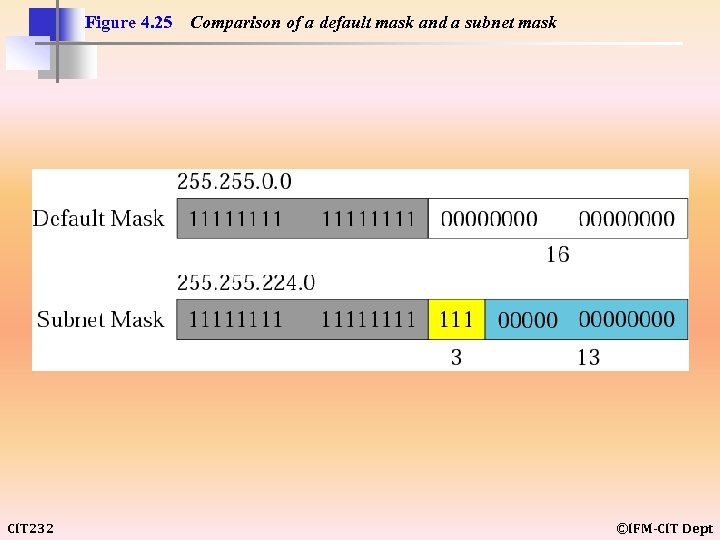
Figure 4. 25 CIT 232 Comparison of a default mask and a subnet mask ©IFM-CIT Dept
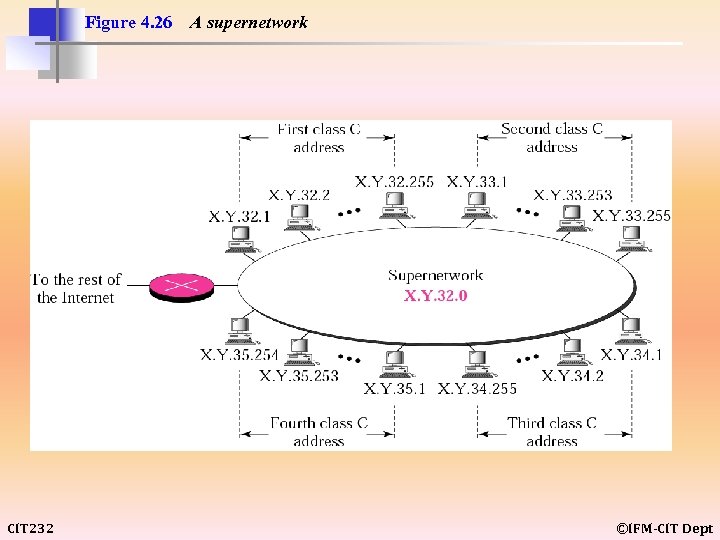
Figure 4. 26 CIT 232 A supernetwork ©IFM-CIT Dept

Note: In subnetting, we need the first address of the subnet and the subnet mask to define the range of addresses. In supernetting, we need the first address of the supernet and the supernet mask to define the range of addresses. CIT 232 ©IFM-CIT Dept
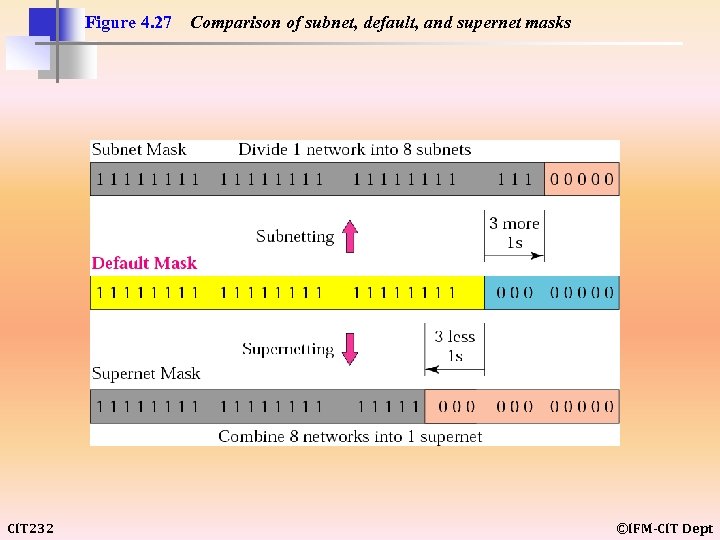
Figure 4. 27 CIT 232 Comparison of subnet, default, and supernet masks ©IFM-CIT Dept
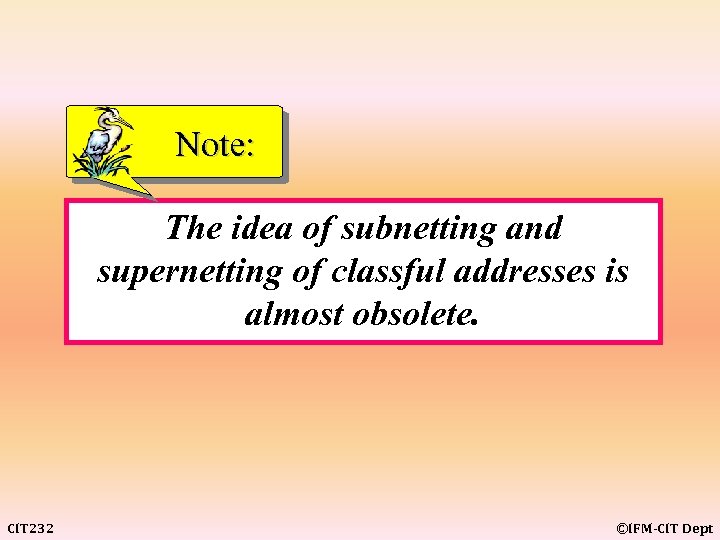
Note: The idea of subnetting and supernetting of classful addresses is almost obsolete. CIT 232 ©IFM-CIT Dept
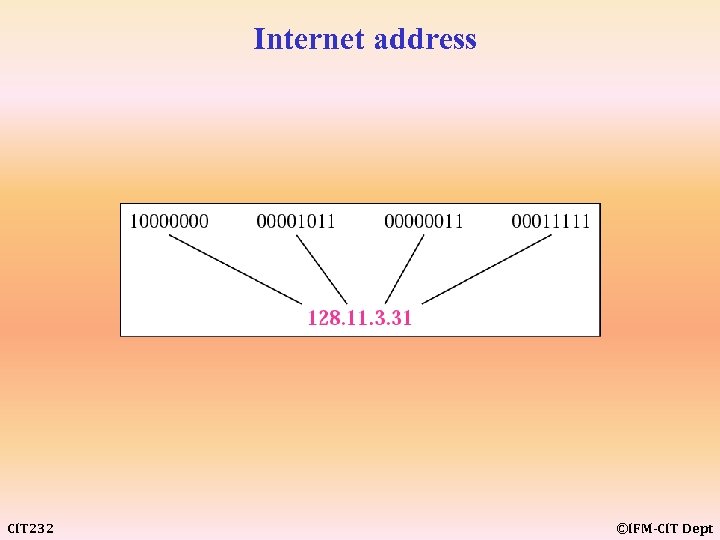
Internet address CIT 232 ©IFM-CIT Dept

Technical Focus: Classful versus Classless Addressing With more and more organizations wanting to use the Internet, the Internet authorities are running out of IP addresses. Internet addresses were originally designed as classful addresses. By this, we mean that the total number of 32 -bit addresses was divided unevenly into five classes: A, B, C, D, and E. Class A and B contain blocks of addresses with a very large range. Each block is granted to one organization, but most of these organizations never use their allotted number of addresses. This is a tremendous waste of addresses. Recently, a new design called classless addressing has been implemented. In this design, all available addresses are put into a big pool; each organization is granted a range of addresses according to its need. CIT 232 ©IFM-CIT Dept
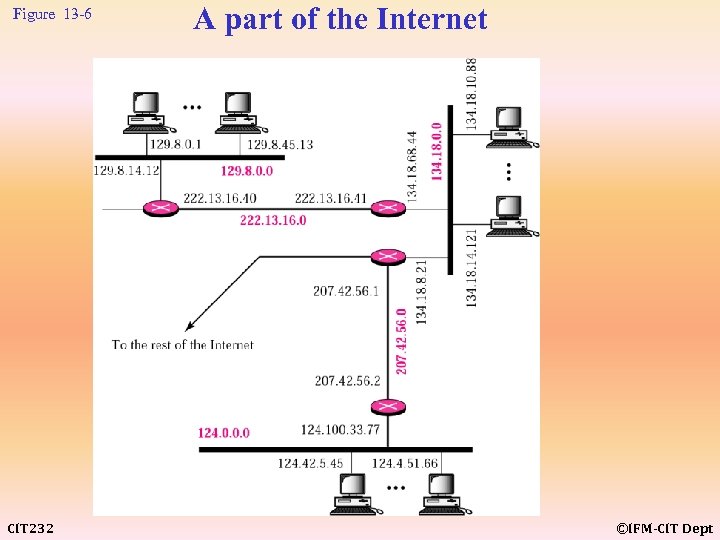
Figure 13 -6 CIT 232 A part of the Internet ©IFM-CIT Dept
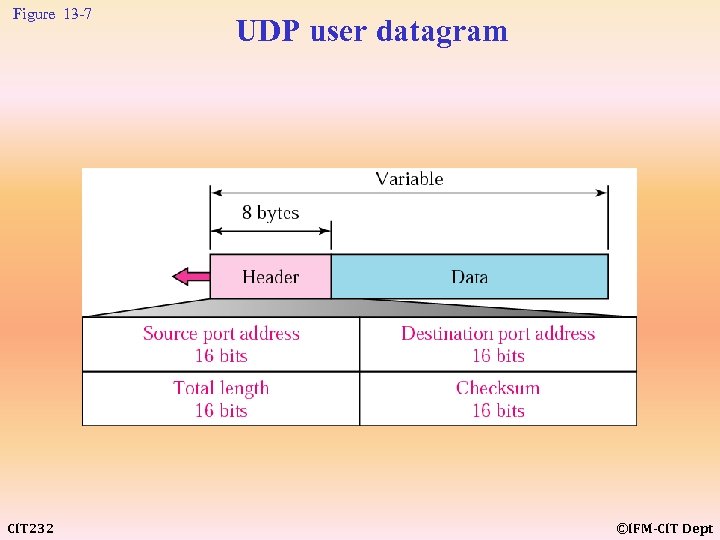
Figure 13 -7 CIT 232 UDP user datagram ©IFM-CIT Dept
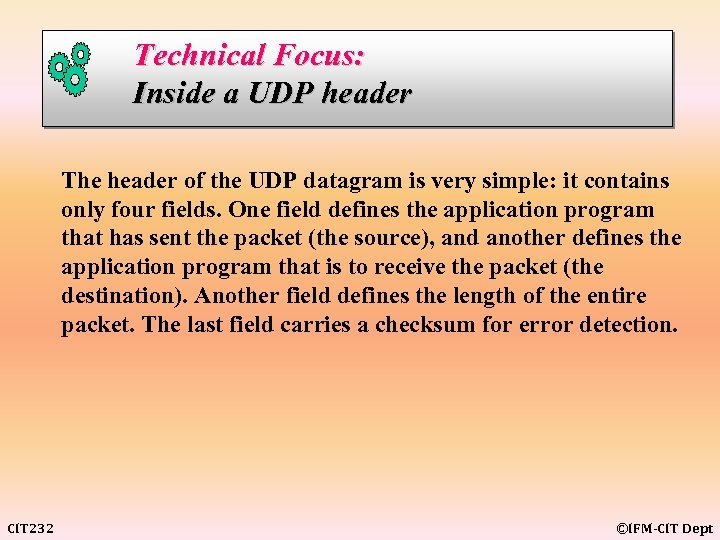
Technical Focus: Inside a UDP header The header of the UDP datagram is very simple: it contains only four fields. One field defines the application program that has sent the packet (the source), and another defines the application program that is to receive the packet (the destination). Another field defines the length of the entire packet. The last field carries a checksum for error detection. CIT 232 ©IFM-CIT Dept
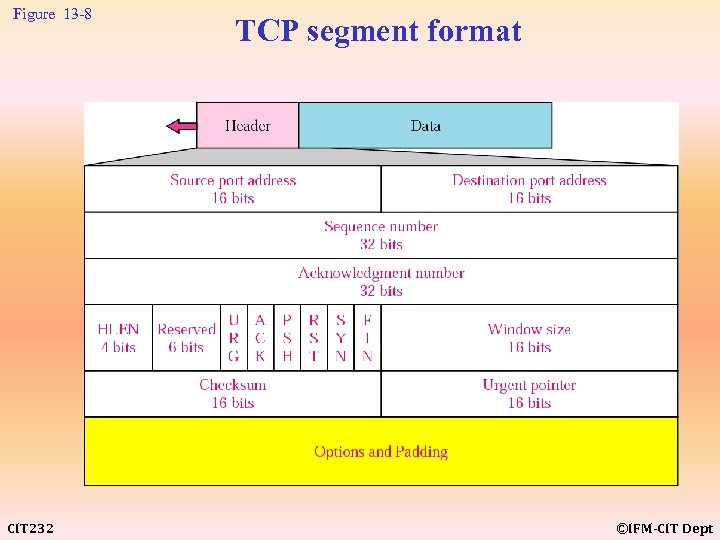
Figure 13 -8 CIT 232 TCP segment format ©IFM-CIT Dept

Technical Focus: Inside a TCP Segment Header CIT 232 The header of a segment is very complicated and contains optional as well as mandatory fields. We briefly discuss just the required fields. One pair of fields defines the source and destination application programs. Another pair is used for error and flow control; one holds the unique sequence number, and the other holds the acknowledgment number. One field defines the size of the sliding window in the transport layer. The sliding window in the transport layer uses the same concept as the one in the data link layer (see Chapter 5). There also flags that define the purpose of the segment (for connection establishment, for termination, for acknowledgment, and so on). The last required field carries a checksum for error detection. ©IFM-CIT Dept

13. 3 NEXT GENERATION CIT 232 ©IFM-CIT Dept

13. 4 ACCESS TO THE INTERNET CIT 232 ©IFM-CIT Dept
13. 5 PRIVATE NETWORKS: INTRANET AND EXTRANET CIT 232 ©IFM-CIT Dept
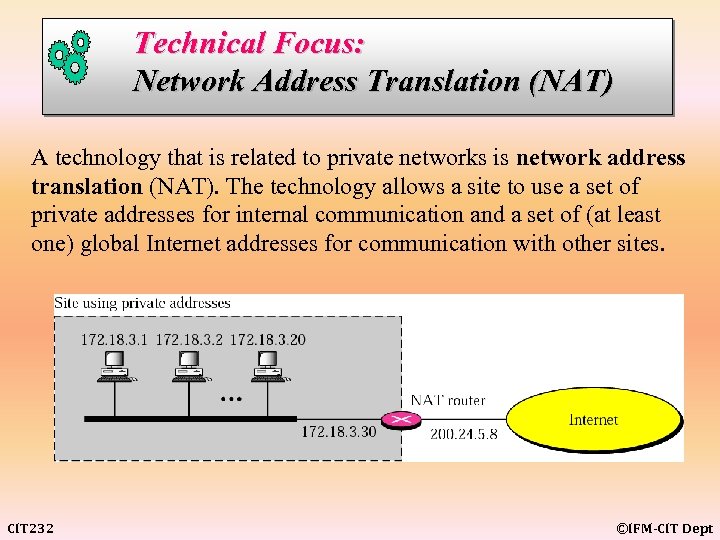
Technical Focus: Network Address Translation (NAT) A technology that is related to private networks is network address translation (NAT). The technology allows a site to use a set of private addresses for internal communication and a set of (at least one) global Internet addresses for communication with other sites. CIT 232 ©IFM-CIT Dept
16e43d5eea0eabc5974932dfa5dfa7ec.ppt