46ebc49a1db1a77b12d195d2c0c0cc77.ppt
- Количество слайдов: 8
 The Interdisciplinary Center Herzliya, Dec 3 rd 2007 Ofer Shezaf, CTO, Breach Security ofers@breach. com Copyright © The OWASP Foundation Permission is granted to copy, distribute and/or modify this document under the terms of the OWASP License. The OWASP Foundation http: //www. owasp. org. il
The Interdisciplinary Center Herzliya, Dec 3 rd 2007 Ofer Shezaf, CTO, Breach Security ofers@breach. com Copyright © The OWASP Foundation Permission is granted to copy, distribute and/or modify this document under the terms of the OWASP License. The OWASP Foundation http: //www. owasp. org. il
 Thanks! < To our Sponsors: < To the Speakers < And to these wonderful people: 4 Dr. Anat Bremler-Bar, Our host today. 4 Shay Shuker and Avi Aminov who helped organize things. 4 Bat-Sheva Shezaf who volunteered to be the photographer. OWASP 2
Thanks! < To our Sponsors: < To the Speakers < And to these wonderful people: 4 Dr. Anat Bremler-Bar, Our host today. 4 Shay Shuker and Avi Aminov who helped organize things. 4 Bat-Sheva Shezaf who volunteered to be the photographer. OWASP 2
 What is OWASP? The Open Web Application Security Project
What is OWASP? The Open Web Application Security Project
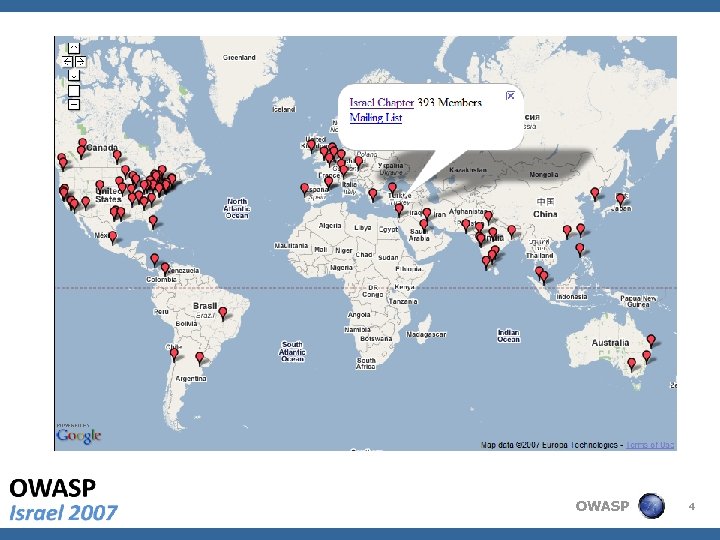 OWASP 4
OWASP 4
 OWASP IL
OWASP IL
 Announcing: OWASP IL Scholarships Program < Application security got a lot of attention from the industry and much less from the Academic world. We would like to push for more Academic research in this field. < The program calls for companies to provide grants for academic projects related to application security. < Program Guidance: 4 Dr. Anat Bremler-Bar will be the academic director of the program. 4 A steering committee would include representatives from other universities and the industry. < Program details: 4 Research projects submitted must be active projects, proposed by either the Academia or the industry. 4 The steering committee will review the proposals and select the appropriate ones. 4 Each project will submit a paper following OWASP conference. 4 Each grant will be 5000 shekels, for any use, half at start and half on paper submission. 4 A more detailed program plan would be distributed shortly. < We are looking for universities and companies who would like to participate or sponsor the scholarship. OWASP 6
Announcing: OWASP IL Scholarships Program < Application security got a lot of attention from the industry and much less from the Academic world. We would like to push for more Academic research in this field. < The program calls for companies to provide grants for academic projects related to application security. < Program Guidance: 4 Dr. Anat Bremler-Bar will be the academic director of the program. 4 A steering committee would include representatives from other universities and the industry. < Program details: 4 Research projects submitted must be active projects, proposed by either the Academia or the industry. 4 The steering committee will review the proposals and select the appropriate ones. 4 Each project will submit a paper following OWASP conference. 4 Each grant will be 5000 shekels, for any use, half at start and half on paper submission. 4 A more detailed program plan would be distributed shortly. < We are looking for universities and companies who would like to participate or sponsor the scholarship. OWASP 6
 Announcing: Computer for Every Student < Nothing to do with application security: 4 But takes advantage of the relationship between industry and Academia that we create. 4 And doing something for the community (and the environment) is always good. < We encourage companies to contribute computers phased out to students who need them: 4 Must be working computers. 4 Can be old. Just need to be able to run Office and be able to connect to the Internet. 4 Software and support will be handled by the University (which is the reason we focus on this segment). < We already started: 4 Breach Security is contributing computers to Tel-Hai Academic College. OWASP 7
Announcing: Computer for Every Student < Nothing to do with application security: 4 But takes advantage of the relationship between industry and Academia that we create. 4 And doing something for the community (and the environment) is always good. < We encourage companies to contribute computers phased out to students who need them: 4 Must be working computers. 4 Can be old. Just need to be able to run Office and be able to connect to the Internet. 4 Software and support will be handled by the University (which is the reason we focus on this segment). < We already started: 4 Breach Security is contributing computers to Tel-Hai Academic College. OWASP 7
 The Program < Cross Site Request Forgery, Ofer Shezaf, OWASP IL chapter leader, Breach Security < Defeating Web 2. 0 Attacks without Recoding Applications, Amichai Shulman, CTO, Imperva 4 This talk was presented in OWASP 2007 in San Jose. < Hunting Down XSS Vulnerabilities, Erez Metula, Application Security Department Manager, 2 Bsecure < 10 minutes about the National Information Security Forum, Avi Weissman, CEO, See-Security < How Dangerous Is It Out There? Dror Paz, Director of Professional Services, Breach Security < SOA security, Iris Levari, Amdocs < The PKI Lie - Attacking Certificate-Based Authentication, Ofer Maor, CTO, Hacktics 4 This talk was presented in OWASP 2007 in San Jose. < Harvesting Skype Super-Nodes, Omer Dekel, IDC 4 This talk is based on a research project done with Dr. Anat Bremler-Barr (IDC) & Prof. Hanoch Levy (ETH) < Smuggling SQL injection attacks, Avi Douglen, Com. Sec 4 This is a new research work presented for the first time in OWASP Israel 2007. OWASP 8
The Program < Cross Site Request Forgery, Ofer Shezaf, OWASP IL chapter leader, Breach Security < Defeating Web 2. 0 Attacks without Recoding Applications, Amichai Shulman, CTO, Imperva 4 This talk was presented in OWASP 2007 in San Jose. < Hunting Down XSS Vulnerabilities, Erez Metula, Application Security Department Manager, 2 Bsecure < 10 minutes about the National Information Security Forum, Avi Weissman, CEO, See-Security < How Dangerous Is It Out There? Dror Paz, Director of Professional Services, Breach Security < SOA security, Iris Levari, Amdocs < The PKI Lie - Attacking Certificate-Based Authentication, Ofer Maor, CTO, Hacktics 4 This talk was presented in OWASP 2007 in San Jose. < Harvesting Skype Super-Nodes, Omer Dekel, IDC 4 This talk is based on a research project done with Dr. Anat Bremler-Barr (IDC) & Prof. Hanoch Levy (ETH) < Smuggling SQL injection attacks, Avi Douglen, Com. Sec 4 This is a new research work presented for the first time in OWASP Israel 2007. OWASP 8


