70380cd62d61413b9b6986779f00df9d.ppt
- Количество слайдов: 71
 The IEEE 802. 11 s Mesh Networking Amendment 2011 -03 -14 – IEEE 802 plenary meeting – Singapore IEEE doc. 11 -11 -0380 -00 Dan Harkins Guido R. Hiertz ARUBA NETWORKS Dee Denteneer Kazuyuki Sakoda PHILIPS Guenael Strutt POWERWAVE TECHNOLOGIES PHILIPS SONY Jarkko Kneckt NOKIA Michael Bahr SIEMENS AG
The IEEE 802. 11 s Mesh Networking Amendment 2011 -03 -14 – IEEE 802 plenary meeting – Singapore IEEE doc. 11 -11 -0380 -00 Dan Harkins Guido R. Hiertz ARUBA NETWORKS Dee Denteneer Kazuyuki Sakoda PHILIPS Guenael Strutt POWERWAVE TECHNOLOGIES PHILIPS SONY Jarkko Kneckt NOKIA Michael Bahr SIEMENS AG
 2 Outline Motivation Introduction to 802. 11 s Usage scenarios 802. 11 s architecture The Mesh BSS – Mesh Discovering – Peering – Security Multi hopping – Path selection (reactive) – Power save – Radio resource management MBSS connected to external STAs Wrap up Conclusion
2 Outline Motivation Introduction to 802. 11 s Usage scenarios 802. 11 s architecture The Mesh BSS – Mesh Discovering – Peering – Security Multi hopping – Path selection (reactive) – Power save – Radio resource management MBSS connected to external STAs Wrap up Conclusion
 3 Motivation for the tutorial STA P AP STA L STA M M AP STA M M P STA
3 Motivation for the tutorial STA P AP STA L STA M M AP STA M M P STA
 4 Why a tutorial? 2 nd recirculation Sponsor Ballot completed March 5 with 95% approval rate Timeline targets approval to forward to Ex. Com by July 2011 STA P AP STA L STA M M AP STA M M P STA
4 Why a tutorial? 2 nd recirculation Sponsor Ballot completed March 5 with 95% approval rate Timeline targets approval to forward to Ex. Com by July 2011 STA P AP STA L STA M M AP STA M M P STA
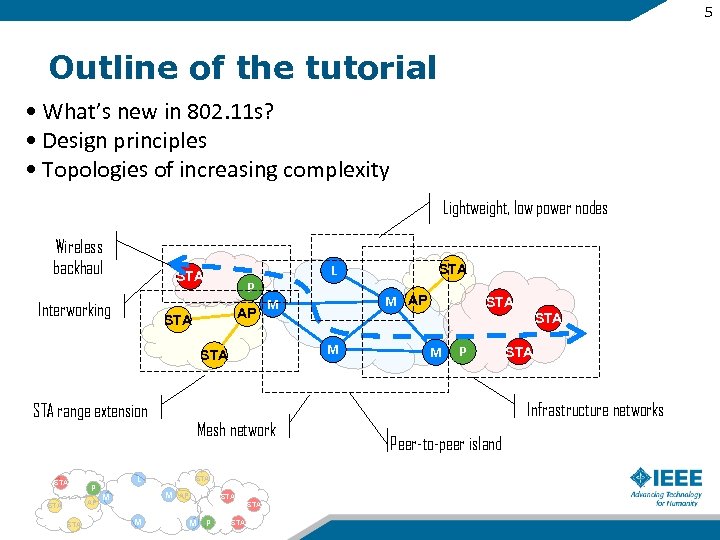 5 Outline of the tutorial • What’s new in 802. 11 s? • Design principles • Topologies of increasing complexity Lightweight, low power nodes Wireless backhaul Interworking P AP STA STA STA M M AP STA M M P STA STA M Mesh network L M AP M STA range extension STA L STA M P STA Infrastructure networks Peer-to-peer island
5 Outline of the tutorial • What’s new in 802. 11 s? • Design principles • Topologies of increasing complexity Lightweight, low power nodes Wireless backhaul Interworking P AP STA STA STA M M AP STA M M P STA STA M Mesh network L M AP M STA range extension STA L STA M P STA Infrastructure networks Peer-to-peer island
 6 Introduction to Mesh STA P AP STA L STA M M AP STA M M P STA
6 Introduction to Mesh STA P AP STA L STA M M AP STA M M P STA
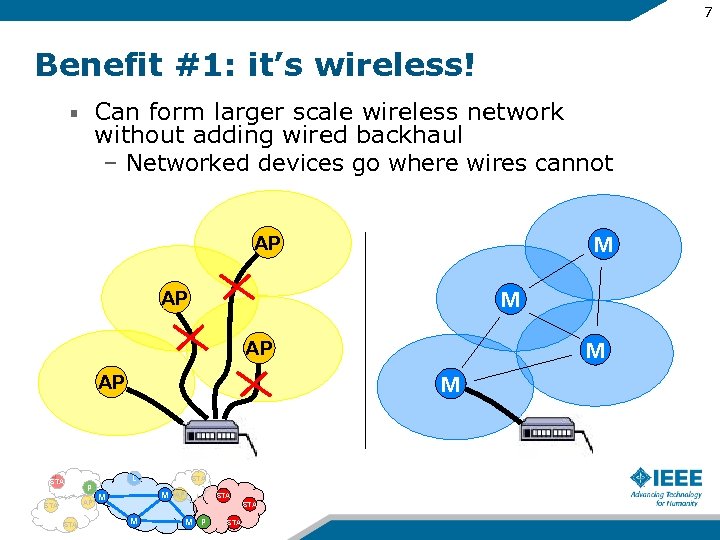 7 Benefit #1: it’s wireless! Can form larger scale wireless network without adding wired backhaul – Networked devices go where wires cannot M AP STA P AP STA L STA M M AP STA M M P STA
7 Benefit #1: it’s wireless! Can form larger scale wireless network without adding wired backhaul – Networked devices go where wires cannot M AP STA P AP STA L STA M M AP STA M M P STA
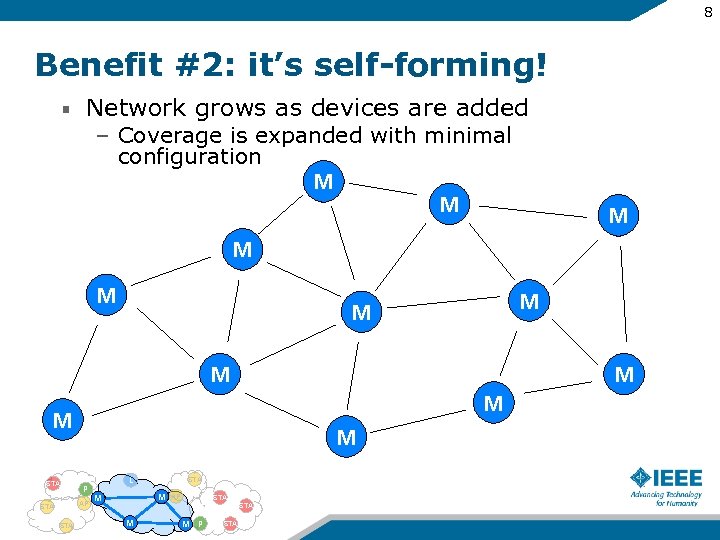 8 Benefit #2: it’s self-forming! Network grows as devices are added – Coverage is expanded with minimal configuration M M M M STA M P AP STA M M L STA M M AP STA M M P STA M
8 Benefit #2: it’s self-forming! Network grows as devices are added – Coverage is expanded with minimal configuration M M M M STA M P AP STA M M L STA M M AP STA M M P STA M
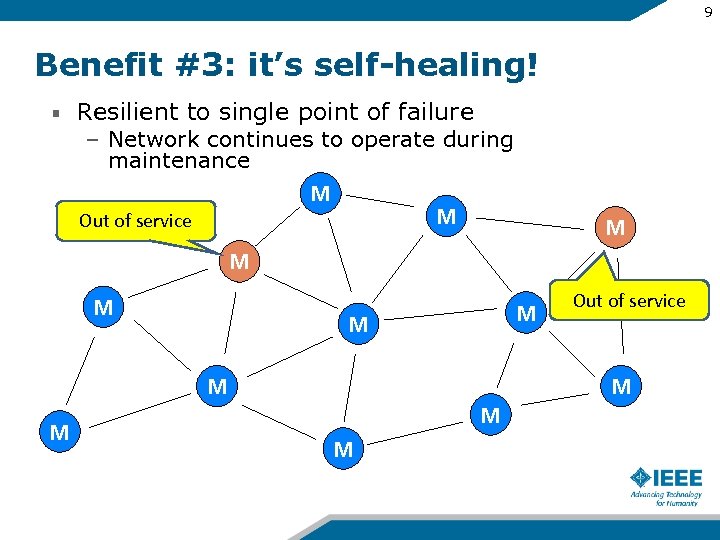 9 Benefit #3: it’s self-healing! Resilient to single point of failure – Network continues to operate during maintenance M M Out of service M M M M M Out of service M
9 Benefit #3: it’s self-healing! Resilient to single point of failure – Network continues to operate during maintenance M M Out of service M M M M M Out of service M
 10 Benefit #4: it has no hierarchy! Can deploy, extend, modify, and pullout the wireless network easily with minimal cost/overhead Mesh stations can be client devices – True ad hoc networking with relaxed range restriction – No (re-)configuration delays because there is no need to define a master station or cluster “Infrastructure” mesh stations can be deployed, upgraded, replaced or removed regardless of role
10 Benefit #4: it has no hierarchy! Can deploy, extend, modify, and pullout the wireless network easily with minimal cost/overhead Mesh stations can be client devices – True ad hoc networking with relaxed range restriction – No (re-)configuration delays because there is no need to define a master station or cluster “Infrastructure” mesh stations can be deployed, upgraded, replaced or removed regardless of role
 11 Usage Scenarios STA P AP STA L STA M M AP STA M M P STA
11 Usage Scenarios STA P AP STA L STA M M AP STA M M P STA
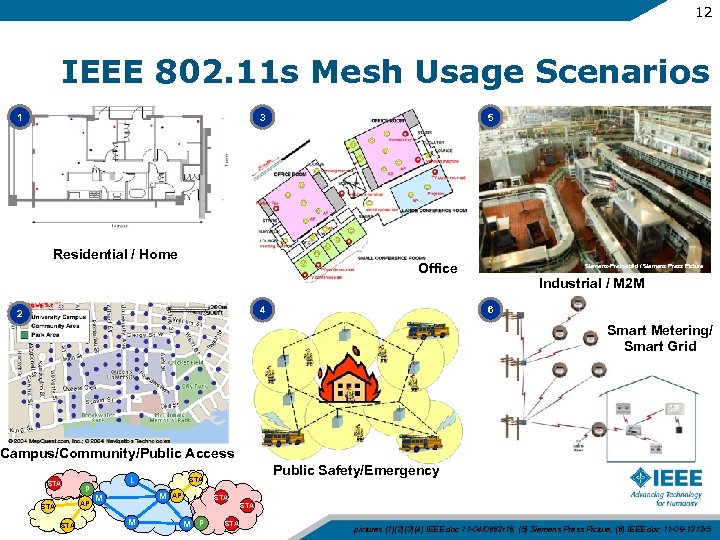 12 IEEE 802. 11 s Mesh Usage Scenarios 1 3 Residential / Home 5 Office 4 2 Siemens-Pressebild / Siemens Press Picture Industrial / M 2 M 6 Smart Metering/ Smart Grid Campus/Community/Public Access STA P AP STA L M M Public Safety/Emergency STA AP STA M M P STA pictures (1)(2)(3)(4) IEEE doc 11 -04/0662 r 16, (5) Siemens Press Picture, (6) IEEE doc 11 -09 -1313 r 5
12 IEEE 802. 11 s Mesh Usage Scenarios 1 3 Residential / Home 5 Office 4 2 Siemens-Pressebild / Siemens Press Picture Industrial / M 2 M 6 Smart Metering/ Smart Grid Campus/Community/Public Access STA P AP STA L M M Public Safety/Emergency STA AP STA M M P STA pictures (1)(2)(3)(4) IEEE doc 11 -04/0662 r 16, (5) Siemens Press Picture, (6) IEEE doc 11 -09 -1313 r 5
 13 Backhaul Mesh • Campus/ Community/Public 2 Access 3 • Office • Industrial 5 • Smart Metering/ Smart Grid 6
13 Backhaul Mesh • Campus/ Community/Public 2 Access 3 • Office • Industrial 5 • Smart Metering/ Smart Grid 6
 14 Client Mesh • Home Networks • Emergency/Public Safety • Industrial/M 2 M • Smart Metering/Smart Grid 1 4 5 6
14 Client Mesh • Home Networks • Emergency/Public Safety • Industrial/M 2 M • Smart Metering/Smart Grid 1 4 5 6
 15 Mixed (backhaul & client) Mesh • Home Networks • Office • Emergency/ Public Safety STA P AP STA L STA M M AP STA M M P STA 1 3 4
15 Mixed (backhaul & client) Mesh • Home Networks • Office • Emergency/ Public Safety STA P AP STA L STA M M AP STA M M P STA 1 3 4
 16 The 802. 11 s architecture Extensions required for multi-hop communications STA P AP STA L STA M M AP STA M M P STA
16 The 802. 11 s architecture Extensions required for multi-hop communications STA P AP STA L STA M M AP STA M M P STA
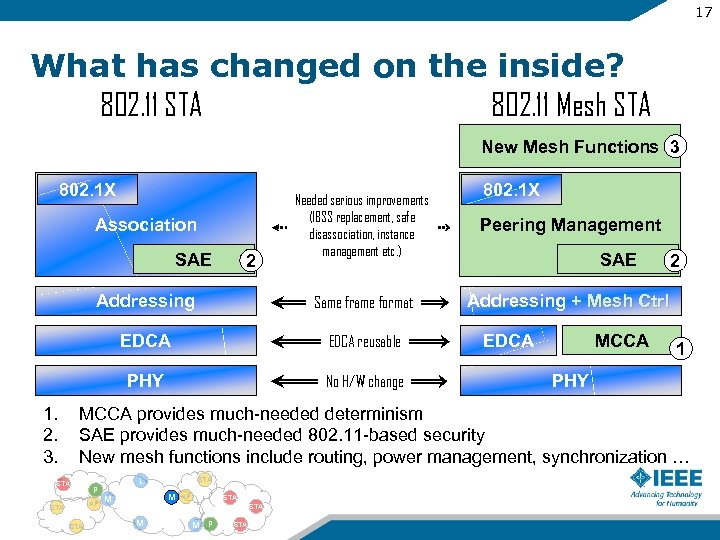 17 What has changed on the inside? 802. 11 STA 802. 11 Mesh STA New Mesh Functions 3 802. 1 X Needed serious improvements (IBSS replacement, safe disassociation, instance management etc. ) Peering Management Addressing Same frame format Addressing + Mesh Ctrl EDCA reusable PHY No H/W change Association SAE 1. 2. 3. 2 SAE MCCA EDCA 2 1 PHY MCCA provides much-needed determinism SAE provides much-needed 802. 11 -based security New mesh functions include routing, power management, synchronization … STA P AP STA L STA M M AP STA M M P STA
17 What has changed on the inside? 802. 11 STA 802. 11 Mesh STA New Mesh Functions 3 802. 1 X Needed serious improvements (IBSS replacement, safe disassociation, instance management etc. ) Peering Management Addressing Same frame format Addressing + Mesh Ctrl EDCA reusable PHY No H/W change Association SAE 1. 2. 3. 2 SAE MCCA EDCA 2 1 PHY MCCA provides much-needed determinism SAE provides much-needed 802. 11 -based security New mesh functions include routing, power management, synchronization … STA P AP STA L STA M M AP STA M M P STA
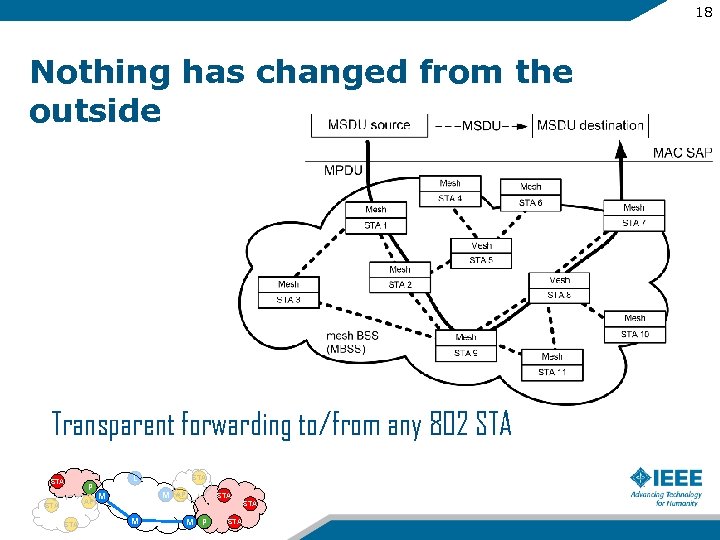 18 Nothing has changed from the outside Transparent forwarding to/from any 802 STA P AP STA L STA M M AP STA M M P STA
18 Nothing has changed from the outside Transparent forwarding to/from any 802 STA P AP STA L STA M M AP STA M M P STA
 19 The Mesh BSS Mesh Discovery Peering Mesh Security
19 The Mesh BSS Mesh Discovery Peering Mesh Security
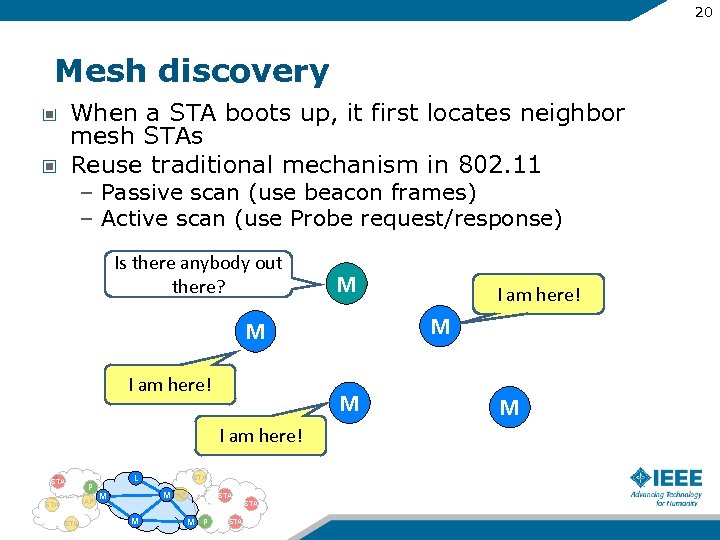 20 Mesh discovery When a STA boots up, it first locates neighbor mesh STAs Reuse traditional mechanism in 802. 11 – Passive scan (use beacon frames) – Active scan (use Probe request/response) Is there anybody out there? M M M I am here! STA P AP STA L STA M M AP STA M M P STA I am here! M
20 Mesh discovery When a STA boots up, it first locates neighbor mesh STAs Reuse traditional mechanism in 802. 11 – Passive scan (use beacon frames) – Active scan (use Probe request/response) Is there anybody out there? M M M I am here! STA P AP STA L STA M M AP STA M M P STA I am here! M
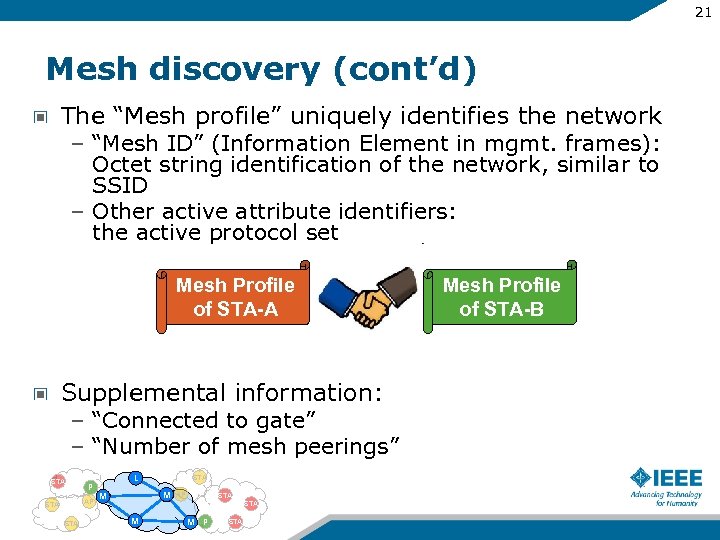 21 Mesh discovery (cont’d) The “Mesh profile” uniquely identifies the network – “Mesh ID” (Information Element in mgmt. frames): Octet string identification of the network, similar to SSID – Other active attribute identifiers: the active protocol set Mesh Profile of STA-A Supplemental information: – “Connected to gate” – “Number of mesh peerings” STA P AP STA L STA M M AP STA M M P STA Mesh Profile of STA-B
21 Mesh discovery (cont’d) The “Mesh profile” uniquely identifies the network – “Mesh ID” (Information Element in mgmt. frames): Octet string identification of the network, similar to SSID – Other active attribute identifiers: the active protocol set Mesh Profile of STA-A Supplemental information: – “Connected to gate” – “Number of mesh peerings” STA P AP STA L STA M M AP STA M M P STA Mesh Profile of STA-B
 22 Mesh Peering A distributed, non-hierarchical, and non-exclusive agreement to communicate Each mesh STA manages its own peerings with other mesh STAs Peering Establishing Protocol – A true peer-to-peer protocol – Each side offers and agrees to parameters that define the terms of the peering and govern communication – Two modes for secured peering (AMPE) or unsecured peering (MPM) STA P AP STA L STA M M AP STA M M P STA
22 Mesh Peering A distributed, non-hierarchical, and non-exclusive agreement to communicate Each mesh STA manages its own peerings with other mesh STAs Peering Establishing Protocol – A true peer-to-peer protocol – Each side offers and agrees to parameters that define the terms of the peering and govern communication – Two modes for secured peering (AMPE) or unsecured peering (MPM) STA P AP STA L STA M M AP STA M M P STA
 23 How is peering done Capability check via profile matching A peering has attributes that must be agreed upon – Each side must make an offer of attributes to use for a potential peering – Each side must confirm the agreed-upon attributes that define the peering After each side has offered and confirmed agreement, the peering is established Each side can initiate a peering and both sides can initiate the peering simultaneously STA P AP STA L STA M M AP STA M M P STA
23 How is peering done Capability check via profile matching A peering has attributes that must be agreed upon – Each side must make an offer of attributes to use for a potential peering – Each side must confirm the agreed-upon attributes that define the peering After each side has offered and confirmed agreement, the peering is established Each side can initiate a peering and both sides can initiate the peering simultaneously STA P AP STA L STA M M AP STA M M P STA
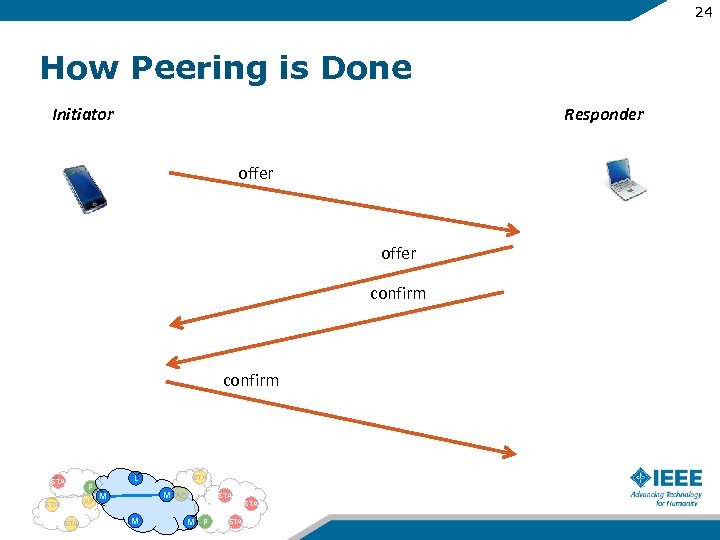 24 How Peering is Done Initiator Responder offer confirm STA P AP STA L STA M M AP STA M M P STA
24 How Peering is Done Initiator Responder offer confirm STA P AP STA L STA M M AP STA M M P STA
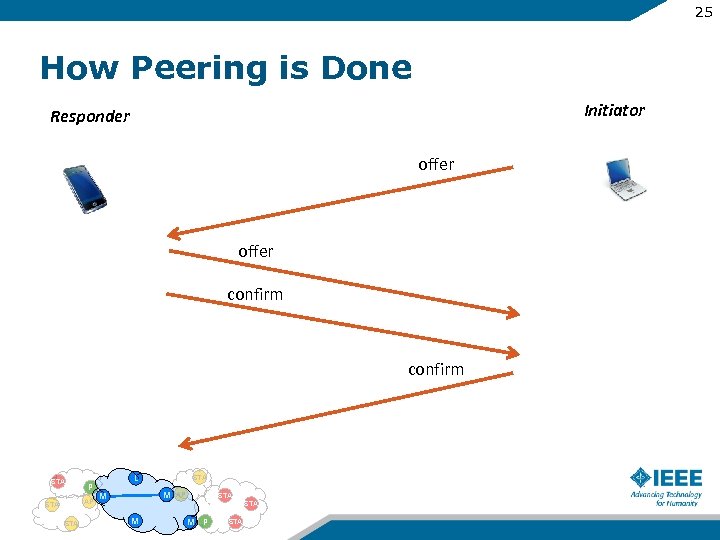 25 How Peering is Done Initiator Responder offer confirm STA P AP STA L STA M M AP STA M M P STA
25 How Peering is Done Initiator Responder offer confirm STA P AP STA L STA M M AP STA M M P STA
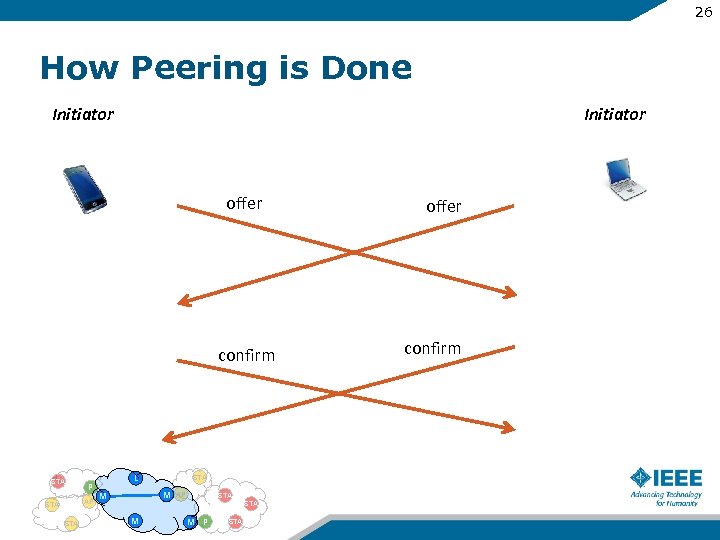 26 How Peering is Done Initiator offer confirm STA P AP STA L STA M M AP STA M M P STA offer confirm
26 How Peering is Done Initiator offer confirm STA P AP STA L STA M M AP STA M M P STA offer confirm
 27 Mesh Security– Simultaneous Authentication of Equals (SAE) Peer-to-Peer – Non-hierarchical, mutual authentication Uses only a password Resistant to attack – Can use short, easy-to -remember, weak passwords – Sharing a password among mesh points does not lessen security STA P AP STA L STA M M AP STA M M P STA Distributed – No centralized server Robust security – Misuse-resistant A standard RSN authentication method for all of 802. 11 – Can be as a drop-in replacement to WPA(2) -PSK in BSS, IBSS, and PBSS networks – Fixes well-known security problem!
27 Mesh Security– Simultaneous Authentication of Equals (SAE) Peer-to-Peer – Non-hierarchical, mutual authentication Uses only a password Resistant to attack – Can use short, easy-to -remember, weak passwords – Sharing a password among mesh points does not lessen security STA P AP STA L STA M M AP STA M M P STA Distributed – No centralized server Robust security – Misuse-resistant A standard RSN authentication method for all of 802. 11 – Can be as a drop-in replacement to WPA(2) -PSK in BSS, IBSS, and PBSS networks – Fixes well-known security problem!
 28 How SAE is performed AKM advertising support for SAE in RSN IE in beacons and probe responses SAE is after discovery but before peering or association Uses 802. 11 authentication frames Simple two message exchange – Same type of exchange used for peering § Each side first commits to a guess of the password § Each side then confirms its guess and verifies the peer’s guess – Successful termination results in a PMK – Unsuccessful termination does not leak any information about the password
28 How SAE is performed AKM advertising support for SAE in RSN IE in beacons and probe responses SAE is after discovery but before peering or association Uses 802. 11 authentication frames Simple two message exchange – Same type of exchange used for peering § Each side first commits to a guess of the password § Each side then confirms its guess and verifies the peer’s guess – Successful termination results in a PMK – Unsuccessful termination does not leak any information about the password
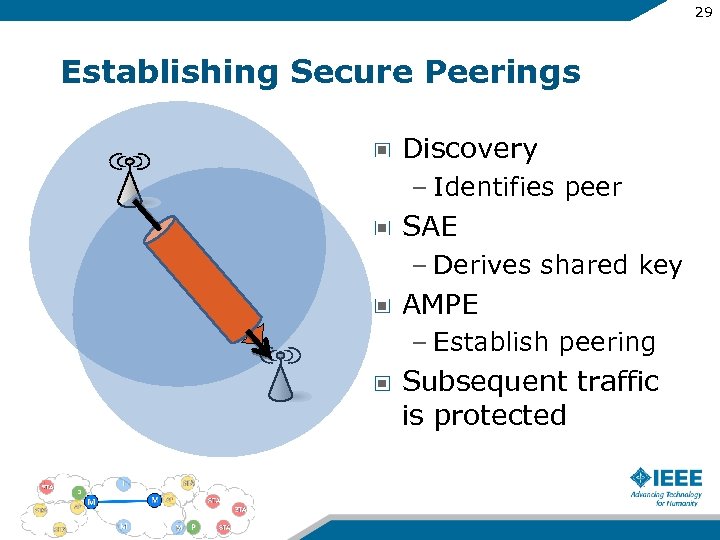 29 Establishing Secure Peerings Discovery – Identifies peer SAE – Derives shared key AMPE – Establish peering Subsequent traffic is protected
29 Establishing Secure Peerings Discovery – Identifies peer SAE – Derives shared key AMPE – Establish peering Subsequent traffic is protected
 30 Mesh Peering: A Better Approach to Peer-to-peer networking Better than Bluetooth – Easy-to-use, ad-hoc, auto-discovery – Secure peering with short key – High speed data transfer between peers Secure, direct, link establishment – No pre-provisioning or “protected setup” necessary – Link is directly established between the peers without need for role determination – The right tool for the right job STA P AP STA L STA M M § No need to implement functionality of multiple roles (e. g. STA and AP) § Security is integrated into link establishment AP STA M M P STA
30 Mesh Peering: A Better Approach to Peer-to-peer networking Better than Bluetooth – Easy-to-use, ad-hoc, auto-discovery – Secure peering with short key – High speed data transfer between peers Secure, direct, link establishment – No pre-provisioning or “protected setup” necessary – Link is directly established between the peers without need for role determination – The right tool for the right job STA P AP STA L STA M M § No need to implement functionality of multiple roles (e. g. STA and AP) § Security is integrated into link establishment AP STA M M P STA
 31 Multi-hopping in the Mesh BSS Path selection (reactive) Power save Radio resource management Wireless Mesh network = multi-hop topology ≠ master-slave topology
31 Multi-hopping in the Mesh BSS Path selection (reactive) Power save Radio resource management Wireless Mesh network = multi-hop topology ≠ master-slave topology
 32 Path Selection Determines paths from source mesh STA to destination mesh STA in an MBSS, possibly over multiple hops Paths are stored in forwarding information HWMP, the Hybrid Wireless Mesh Protocol, is the mandatory default path selection protocol Path selection extensibility framework for use of other path selection protocols Active path selection protocol indicated by path selection protocol identifier in Mesh Configuration IE HWMP can be always configured for interoperability STA P AP STA L STA M M AP STA M M P STA
32 Path Selection Determines paths from source mesh STA to destination mesh STA in an MBSS, possibly over multiple hops Paths are stored in forwarding information HWMP, the Hybrid Wireless Mesh Protocol, is the mandatory default path selection protocol Path selection extensibility framework for use of other path selection protocols Active path selection protocol indicated by path selection protocol identifier in Mesh Configuration IE HWMP can be always configured for interoperability STA P AP STA L STA M M AP STA M M P STA
 33 Hybrid Wireless Mesh Protocol (HWMP) Default Routing protocol in 802. 11 s Reactive path selection as basic path selection mechanism (always available) – path is only established if needed (on-demand) – no path selection control traffic if no data is sent – on-demand path discovery mechanism – works with arbitrary path selection metrics Proactive path selection tree to designated mesh STAs (can be configured at root mesh STAs) ® described later STA P AP STA L STA M M AP STA M M P STA
33 Hybrid Wireless Mesh Protocol (HWMP) Default Routing protocol in 802. 11 s Reactive path selection as basic path selection mechanism (always available) – path is only established if needed (on-demand) – no path selection control traffic if no data is sent – on-demand path discovery mechanism – works with arbitrary path selection metrics Proactive path selection tree to designated mesh STAs (can be configured at root mesh STAs) ® described later STA P AP STA L STA M M AP STA M M P STA
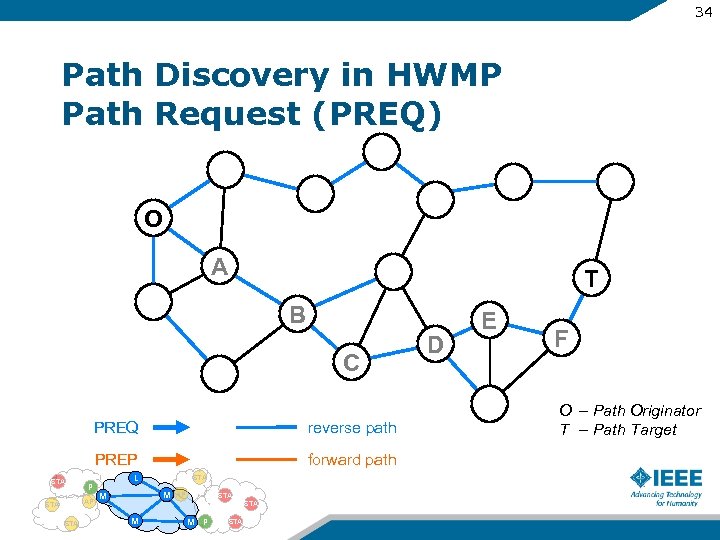 34 Path Discovery in HWMP Path Request (PREQ) O A T B C PREQ reverse path PREP STA P AP STA forward path L STA M M AP STA M M P STA D E F O – Path Originator T – Path Target
34 Path Discovery in HWMP Path Request (PREQ) O A T B C PREQ reverse path PREP STA P AP STA forward path L STA M M AP STA M M P STA D E F O – Path Originator T – Path Target
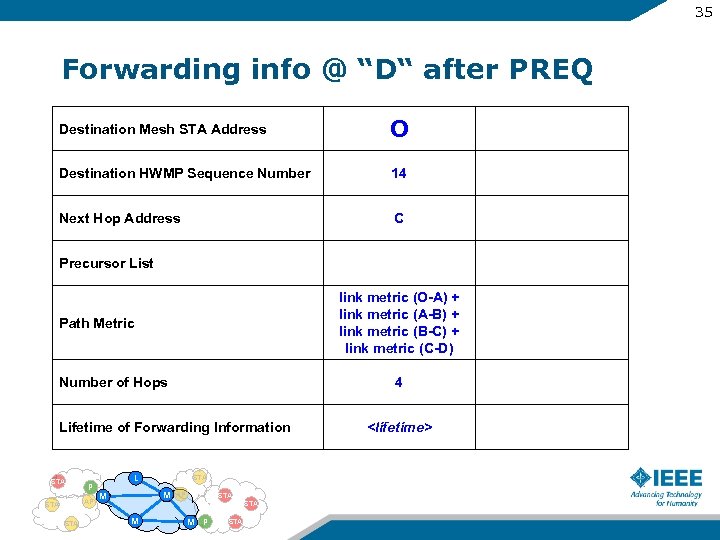 35 Forwarding info @ “D“ after PREQ Destination Mesh STA Address O Destination HWMP Sequence Number 14 Next Hop Address C Precursor List link metric (O-A) + link metric (A-B) + link metric (B-C) + link metric (C-D) Path Metric Number of Hops 4 Lifetime of Forwarding Information STA P AP STA L STA M M AP STA M M P STA
35 Forwarding info @ “D“ after PREQ Destination Mesh STA Address O Destination HWMP Sequence Number 14 Next Hop Address C Precursor List link metric (O-A) + link metric (A-B) + link metric (B-C) + link metric (C-D) Path Metric Number of Hops 4 Lifetime of Forwarding Information STA P AP STA L STA M M AP STA M M P STA
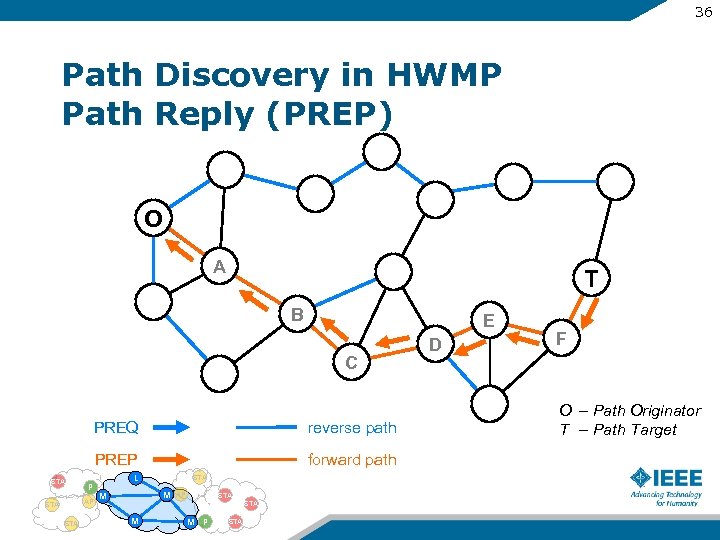 36 Path Discovery in HWMP Path Reply (PREP) O A T B E C PREQ reverse path PREP STA P AP STA forward path L STA M M AP STA M M P STA D F O – Path Originator T – Path Target
36 Path Discovery in HWMP Path Reply (PREP) O A T B E C PREQ reverse path PREP STA P AP STA forward path L STA M M AP STA M M P STA D F O – Path Originator T – Path Target
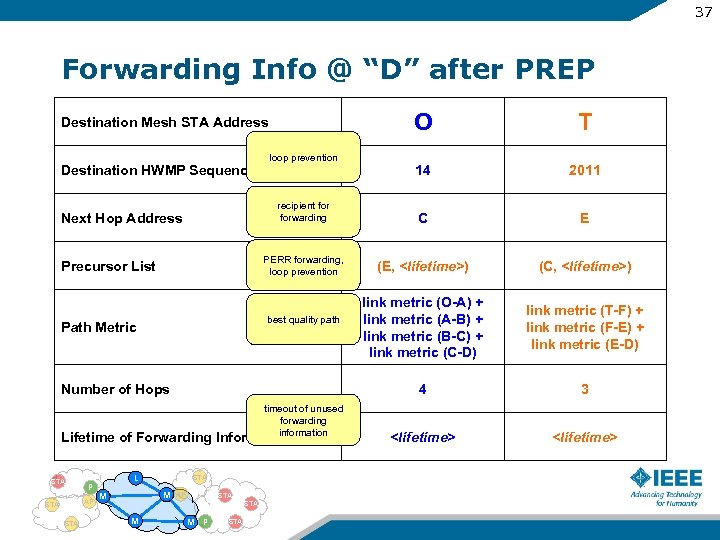 37 Forwarding Info @ “D” after PREP O T 14 2011 recipient forwarding C E PERR forwarding, loop prevention (E,
37 Forwarding Info @ “D” after PREP O T 14 2011 recipient forwarding C E PERR forwarding, loop prevention (E,
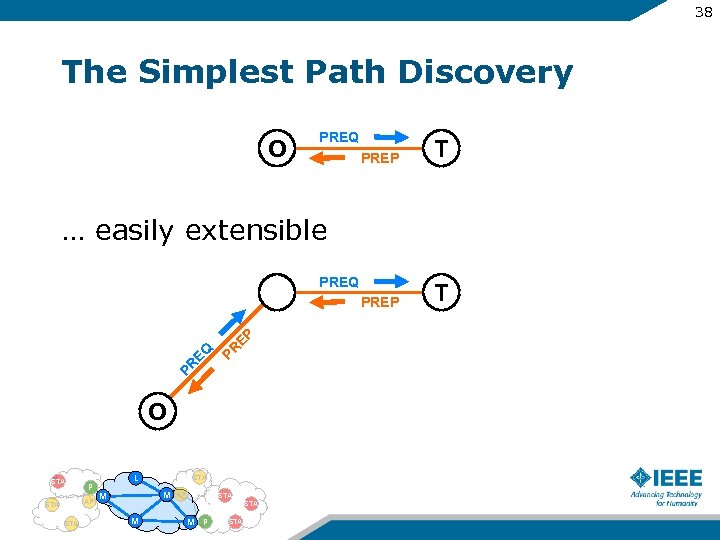 38 The Simplest Path Discovery O PREQ PREP T … easily extensible PR PR EQ EP PREQ O STA P AP STA L STA M M AP STA M M P STA
38 The Simplest Path Discovery O PREQ PREP T … easily extensible PR PR EQ EP PREQ O STA P AP STA L STA M M AP STA M M P STA
 39 Further Features of HWMP Path repair – If path gets disrupted, Path Error (PERR) is generated at link break and propagated towards source mesh STA – Source mesh STA set ups new path to destination mesh STA – PERR used for indication of different error conditions STA P AP STA L STA M M AP STA M M P STA Non-forwarding mesh STA – Is only mesh source or mesh destination but does not forward frames for other mesh STAs – Participates in HWMP, but does not propagate HWMP control messages – Increases the risk of disconnected MBSS
39 Further Features of HWMP Path repair – If path gets disrupted, Path Error (PERR) is generated at link break and propagated towards source mesh STA – Source mesh STA set ups new path to destination mesh STA – PERR used for indication of different error conditions STA P AP STA L STA M M AP STA M M P STA Non-forwarding mesh STA – Is only mesh source or mesh destination but does not forward frames for other mesh STAs – Participates in HWMP, but does not propagate HWMP control messages – Increases the risk of disconnected MBSS
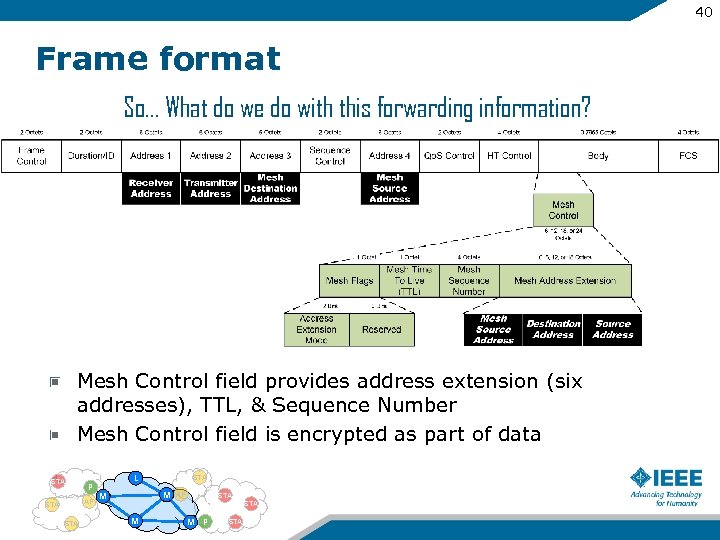 40 Frame format So… What do we do with this forwarding information? Mesh Control field provides address extension (six addresses), TTL, & Sequence Number Mesh Control field is encrypted as part of data STA P AP STA L STA M M AP STA M M P STA
40 Frame format So… What do we do with this forwarding information? Mesh Control field provides address extension (six addresses), TTL, & Sequence Number Mesh Control field is encrypted as part of data STA P AP STA L STA M M AP STA M M P STA
 41 Multi-hopping in the Mesh BSS Power save in the Mesh BSS Wireless Mesh network = multi-hop topology ≠ master-slave topology
41 Multi-hopping in the Mesh BSS Power save in the Mesh BSS Wireless Mesh network = multi-hop topology ≠ master-slave topology
 42 Power save Optimized power consumption for the whole network – Any device may operate in power save – Power constrained devices limit forwarding and minimize power consumption Instant power-up Relaxed transition to sleep – Deep & light sleep – Good responsiveness of the network STA P AP STA L STA M M AP STA M M P STA
42 Power save Optimized power consumption for the whole network – Any device may operate in power save – Power constrained devices limit forwarding and minimize power consumption Instant power-up Relaxed transition to sleep – Deep & light sleep – Good responsiveness of the network STA P AP STA L STA M M AP STA M M P STA
 43 Interaction between power save and forwarding Frames are buffered for Power save mesh STAs Power saving mesh STAs can limit participation in forwarding: – Mesh STA may limit the amount of peerings – Mesh STA may operate in non-forwarding mode § Only create paths for own traffic – Link metrics may account for power constraints STA P AP STA L STA M M AP STA M M P STA
43 Interaction between power save and forwarding Frames are buffered for Power save mesh STAs Power saving mesh STAs can limit participation in forwarding: – Mesh STA may limit the amount of peerings – Mesh STA may operate in non-forwarding mode § Only create paths for own traffic – Link metrics may account for power constraints STA P AP STA L STA M M AP STA M M P STA
 44 Power save and peerings Each mesh peering consists of two mesh power modes: – Local mesh power mode, a promise to the peer – Peer mesh power mode, a promise by the peer Power modes of different mesh peerings are independent from each other Mesh STA may operate in Doze state (radio off) only if no peering requires operation in Awake state (radio on) STA P AP STA L STA M M AP STA M M P STA
44 Power save and peerings Each mesh peering consists of two mesh power modes: – Local mesh power mode, a promise to the peer – Peer mesh power mode, a promise by the peer Power modes of different mesh peerings are independent from each other Mesh STA may operate in Doze state (radio off) only if no peering requires operation in Awake state (radio on) STA P AP STA L STA M M AP STA M M P STA
 45 Mesh power modes Mesh STAs communicate their mesh power mode for each link: – Active mode § Mesh STA available at any time – Light sleep mode § Monitoring peer STA beacons § Responsible to fetch buffered data – Deep sleep mode § Not monitoring peer STA beacons § Not responsible for fetching buffered data STA P AP STA L STA M M AP STA M M P STA
45 Mesh power modes Mesh STAs communicate their mesh power mode for each link: – Active mode § Mesh STA available at any time – Light sleep mode § Monitoring peer STA beacons § Responsible to fetch buffered data – Deep sleep mode § Not monitoring peer STA beacons § Not responsible for fetching buffered data STA P AP STA L STA M M AP STA M M P STA
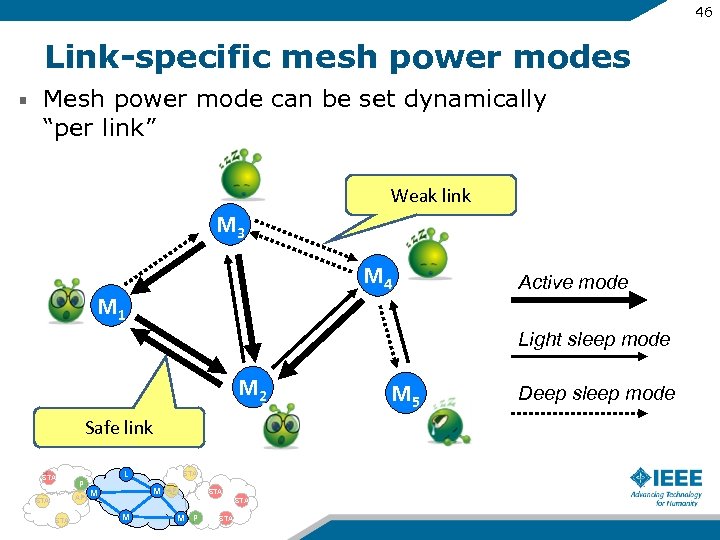 46 Link-specific mesh power modes Mesh power mode can be set dynamically “per link” Weak link M 3 M 4 M 1 Active mode Light sleep mode M 2 Safe link STA P AP STA L STA M M AP STA M M P STA M 5 Deep sleep mode
46 Link-specific mesh power modes Mesh power mode can be set dynamically “per link” Weak link M 3 M 4 M 1 Active mode Light sleep mode M 2 Safe link STA P AP STA L STA M M AP STA M M P STA M 5 Deep sleep mode
 47 Power save details Going to active mode is safe – Transmissions cannot be missed, i. e. signaling is done with group- and individually-addressed frames Going to power save is less safe – Transmissions may be missed if peer is assumed to be available, i. e. individually-addressed frames are used The service periods maintain power saving devices available during the individually addressed data transmission STA P AP STA L STA M M AP STA M M P STA
47 Power save details Going to active mode is safe – Transmissions cannot be missed, i. e. signaling is done with group- and individually-addressed frames Going to power save is less safe – Transmissions may be missed if peer is assumed to be available, i. e. individually-addressed frames are used The service periods maintain power saving devices available during the individually addressed data transmission STA P AP STA L STA M M AP STA M M P STA
 48 Multi-hopping in the Mesh BSS Topics in radio resource management Wireless Mesh network = multi-hop topology ≠ master-slave topology
48 Multi-hopping in the Mesh BSS Topics in radio resource management Wireless Mesh network = multi-hop topology ≠ master-slave topology
 49 Radio resource management Main challenges: – Hidden node problem mitigation – Distributed management – Minimize and localize the effect of topology dynamics Some topics from 802. 11 s radio resource management – Robust neighbor discovery – Distributed resource reservation – Synchronization STA P AP STA L STA M M AP STA M M P STA
49 Radio resource management Main challenges: – Hidden node problem mitigation – Distributed management – Minimize and localize the effect of topology dynamics Some topics from 802. 11 s radio resource management – Robust neighbor discovery – Distributed resource reservation – Synchronization STA P AP STA L STA M M AP STA M M P STA
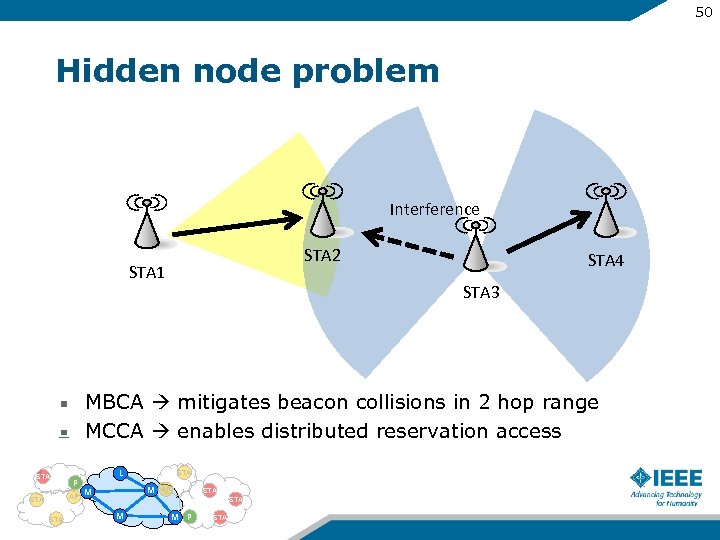 50 Hidden node problem Interference STA 2 STA 1 STA 4 STA 3 MBCA mitigates beacon collisions in 2 hop range MCCA enables distributed reservation access STA P AP STA L STA M M AP STA M M P STA
50 Hidden node problem Interference STA 2 STA 1 STA 4 STA 3 MBCA mitigates beacon collisions in 2 hop range MCCA enables distributed reservation access STA P AP STA L STA M M AP STA M M P STA
 51 Mesh Beacon Collision Avoidance (MBCA) Beacon protection from hidden nodes – Passive scan, power management, and distributed reservation (MCCA) rely on Beacon frames – Need to protect from the interference from hidden nodes – MBCA provides a tool for the mitigation – MBCA reports on Beacon frames even beyond the MBSS STA P AP STA L STA M M AP STA M M P STA
51 Mesh Beacon Collision Avoidance (MBCA) Beacon protection from hidden nodes – Passive scan, power management, and distributed reservation (MCCA) rely on Beacon frames – Need to protect from the interference from hidden nodes – MBCA provides a tool for the mitigation – MBCA reports on Beacon frames even beyond the MBSS STA P AP STA L STA M M AP STA M M P STA
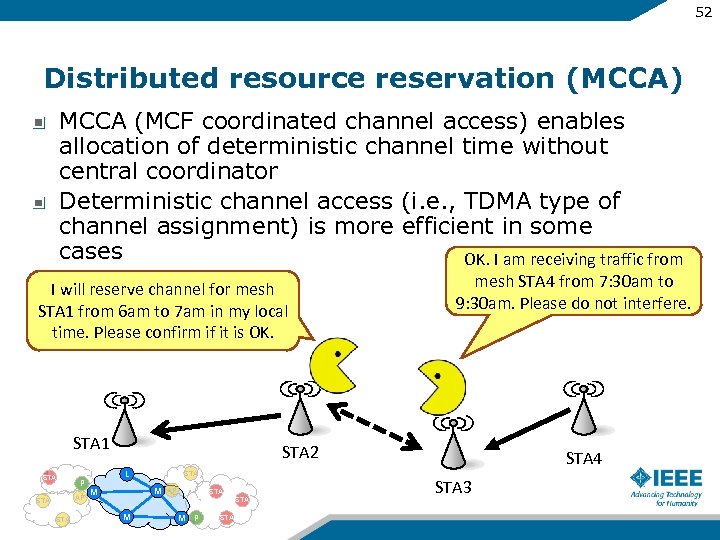 52 Distributed resource reservation (MCCA) MCCA (MCF coordinated channel access) enables allocation of deterministic channel time without central coordinator Deterministic channel access (i. e. , TDMA type of channel assignment) is more efficient in some cases OK. I am receiving traffic from I will reserve channel for mesh STA 1 from 6 am to 7 am in my local time. Please confirm if it is OK. STA 1 STA P AP STA mesh STA 4 from 7: 30 am to 9: 30 am. Please do not interfere. STA 2 L STA M M AP STA M M P STA 4 STA 3
52 Distributed resource reservation (MCCA) MCCA (MCF coordinated channel access) enables allocation of deterministic channel time without central coordinator Deterministic channel access (i. e. , TDMA type of channel assignment) is more efficient in some cases OK. I am receiving traffic from I will reserve channel for mesh STA 1 from 6 am to 7 am in my local time. Please confirm if it is OK. STA 1 STA P AP STA mesh STA 4 from 7: 30 am to 9: 30 am. Please do not interfere. STA 2 L STA M M AP STA M M P STA 4 STA 3
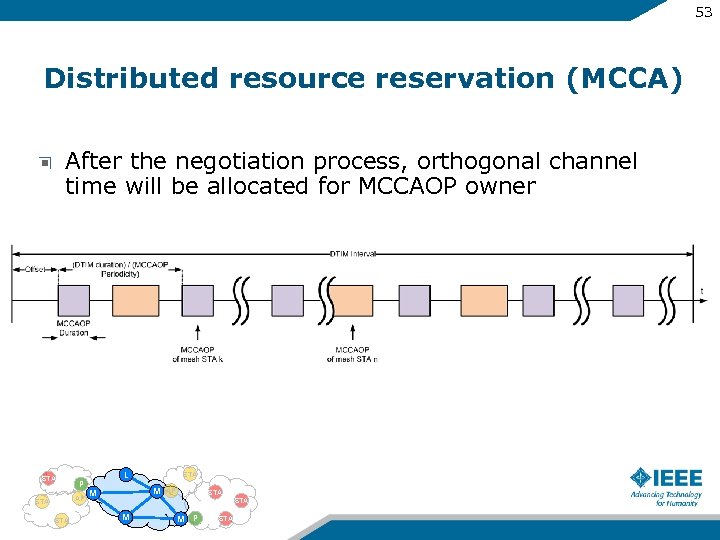 53 Distributed resource reservation (MCCA) After the negotiation process, orthogonal channel time will be allocated for MCCAOP owner STA P AP STA L STA M M AP STA M M P STA
53 Distributed resource reservation (MCCA) After the negotiation process, orthogonal channel time will be allocated for MCCAOP owner STA P AP STA L STA M M AP STA M M P STA
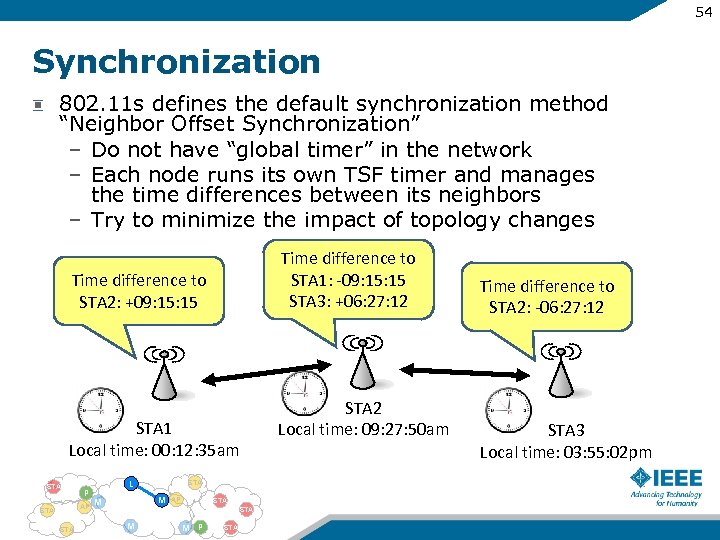 54 Synchronization 802. 11 s defines the default synchronization method “Neighbor Offset Synchronization” – Do not have “global timer” in the network – Each node runs its own TSF timer and manages the time differences between its neighbors – Try to minimize the impact of topology changes Time difference to STA 1: -09: 15 STA 3: +06: 27: 12 Time difference to STA 2: +09: 15 STA 1 Local time: 00: 12: 35 am STA P AP STA L STA M M AP STA M M P STA 2 Local time: 09: 27: 50 am Time difference to STA 2: -06: 27: 12 STA 3 Local time: 03: 55: 02 pm
54 Synchronization 802. 11 s defines the default synchronization method “Neighbor Offset Synchronization” – Do not have “global timer” in the network – Each node runs its own TSF timer and manages the time differences between its neighbors – Try to minimize the impact of topology changes Time difference to STA 1: -09: 15 STA 3: +06: 27: 12 Time difference to STA 2: +09: 15 STA 1 Local time: 00: 12: 35 am STA P AP STA L STA M M AP STA M M P STA 2 Local time: 09: 27: 50 am Time difference to STA 2: -06: 27: 12 STA 3 Local time: 03: 55: 02 pm
 55 MBSS with mesh gates connected to external STAs Proactive path selection Mesh gate & proxy 6 -address frame format
55 MBSS with mesh gates connected to external STAs Proactive path selection Mesh gate & proxy 6 -address frame format
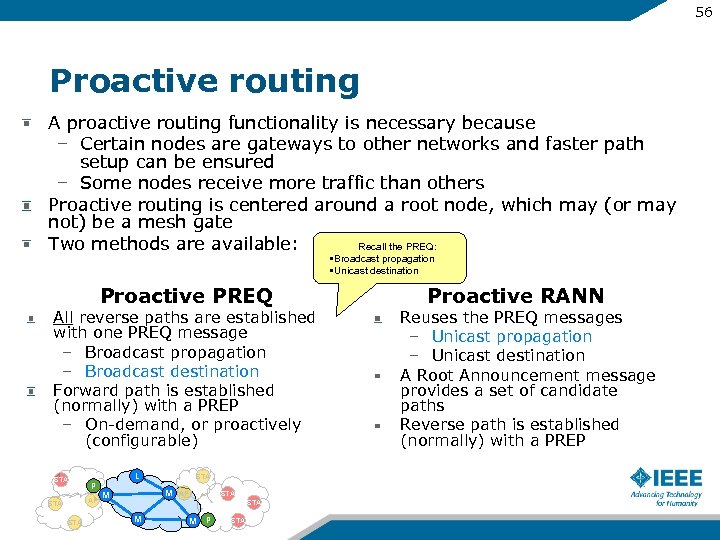 56 Proactive routing A proactive routing functionality is necessary because – Certain nodes are gateways to other networks and faster path setup can be ensured – Some nodes receive more traffic than others Proactive routing is centered around a root node, which may (or may not) be a mesh gate Recall the PREQ: Two methods are available: • Broadcast propagation • Unicast destination Proactive PREQ All reverse paths are established with one PREQ message – Broadcast propagation – Broadcast destination Forward path is established (normally) with a PREP – On-demand, or proactively (configurable) STA P AP STA L STA M M AP STA M M P STA Proactive RANN Reuses the PREQ messages – Unicast propagation – Unicast destination A Root Announcement message provides a set of candidate paths Reverse path is established (normally) with a PREP
56 Proactive routing A proactive routing functionality is necessary because – Certain nodes are gateways to other networks and faster path setup can be ensured – Some nodes receive more traffic than others Proactive routing is centered around a root node, which may (or may not) be a mesh gate Recall the PREQ: Two methods are available: • Broadcast propagation • Unicast destination Proactive PREQ All reverse paths are established with one PREQ message – Broadcast propagation – Broadcast destination Forward path is established (normally) with a PREP – On-demand, or proactively (configurable) STA P AP STA L STA M M AP STA M M P STA Proactive RANN Reuses the PREQ messages – Unicast propagation – Unicast destination A Root Announcement message provides a set of candidate paths Reverse path is established (normally) with a PREP
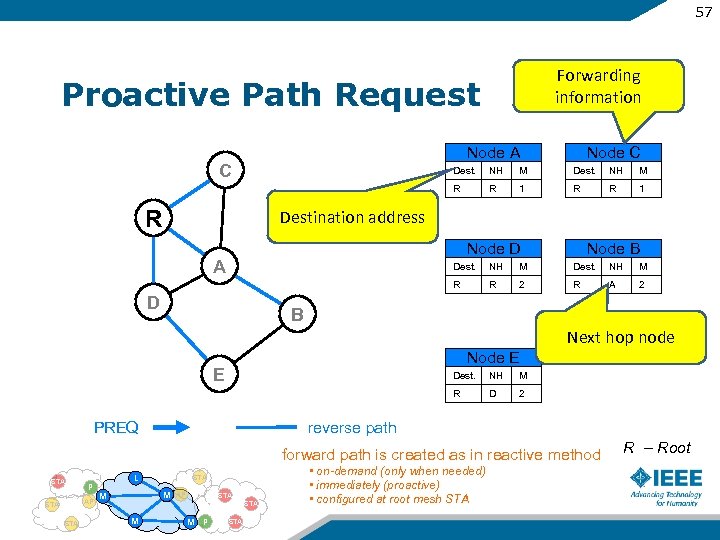 57 Forwarding information Proactive Path Request Node A C Node C Dest. M Dest. NH M R R NH R 1 R R 1 Destination address Node D A Node B Dest. M Dest. NH M R D NH R 2 R A 2 B Next hop node Node E E Dest. M R PREQ NH D 2 reverse path forward path is created as in reactive method STA P AP STA L STA M M AP STA M M P STA • on-demand (only when needed) • immediately (proactive) • configured at root mesh STA R – Root
57 Forwarding information Proactive Path Request Node A C Node C Dest. M Dest. NH M R R NH R 1 R R 1 Destination address Node D A Node B Dest. M Dest. NH M R D NH R 2 R A 2 B Next hop node Node E E Dest. M R PREQ NH D 2 reverse path forward path is created as in reactive method STA P AP STA L STA M M AP STA M M P STA • on-demand (only when needed) • immediately (proactive) • configured at root mesh STA R – Root
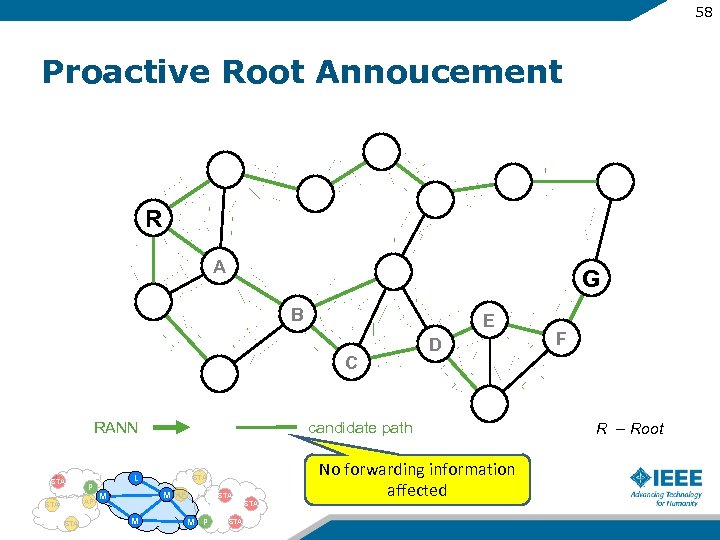 58 Proactive Root Annoucement R A G B E C RANN STA P AP STA candidate path L STA M M AP STA M D M P STA No forwarding information affected F R – Root
58 Proactive Root Annoucement R A G B E C RANN STA P AP STA candidate path L STA M M AP STA M D M P STA No forwarding information affected F R – Root
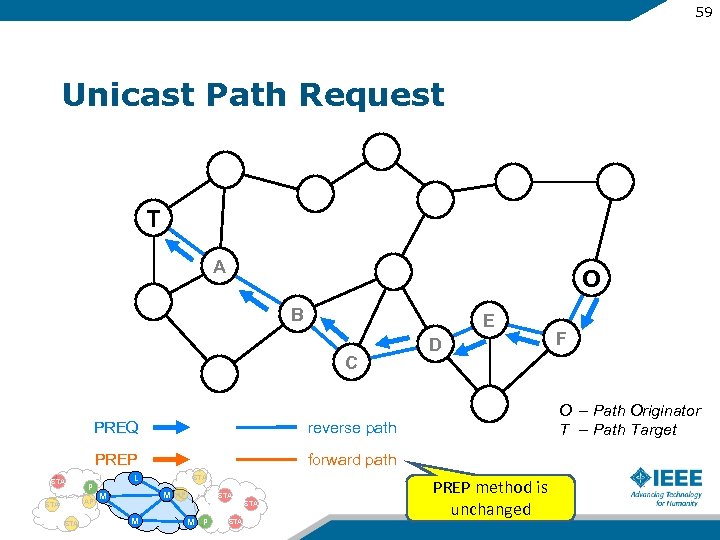 59 Unicast Path Request T A O B E C PREQ P AP STA forward path L STA M M AP STA M M P STA F O – Path Originator T – Path Target reverse path PREP STA D PREP method is unchanged
59 Unicast Path Request T A O B E C PREQ P AP STA forward path L STA M M AP STA M M P STA F O – Path Originator T – Path Target reverse path PREP STA D PREP method is unchanged
 60 Proxy STAs that are outside the MBSS are reached through a proxy Mesh STA (gate) Proxy information is carried through PREQs and PREPs – The originator STA does not know whether the target is inside or outside the MBSS until the PREP is received Proxy information can also be communicated via Proxy Updates STA P AP STA L STA M M M AP STA M P STA
60 Proxy STAs that are outside the MBSS are reached through a proxy Mesh STA (gate) Proxy information is carried through PREQs and PREPs – The originator STA does not know whether the target is inside or outside the MBSS until the PREP is received Proxy information can also be communicated via Proxy Updates STA P AP STA L STA M M M AP STA M P STA
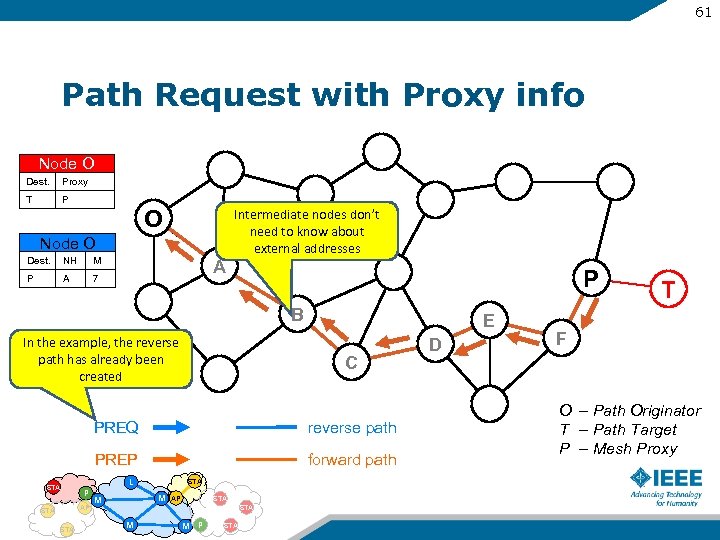 61 Path Request with Proxy info Node O Dest. Proxy T P O Intermediate nodes don’t need to know about external addresses Node O Dest. NH M P A 7 A P B In the example, the reverse path has already been created E C PREQ PREP STA P AP STA reverse path forward path L STA M M M AP STA M P STA D T F O – Path Originator T – Path Target P – Mesh Proxy
61 Path Request with Proxy info Node O Dest. Proxy T P O Intermediate nodes don’t need to know about external addresses Node O Dest. NH M P A 7 A P B In the example, the reverse path has already been created E C PREQ PREP STA P AP STA reverse path forward path L STA M M M AP STA M P STA D T F O – Path Originator T – Path Target P – Mesh Proxy
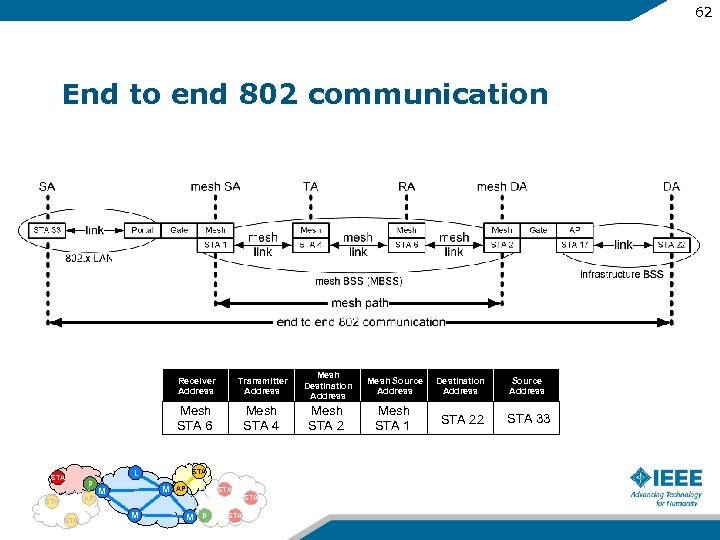 62 End to end 802 communication Receiver Address P AP STA Mesh Destination Address Mesh Source Address Destination Address Source Address Mesh STA 6 STA Transmitter Address Mesh STA 4 Mesh STA 2 Mesh STA 1 STA 22 STA 33 L STA M M M AP STA M P STA
62 End to end 802 communication Receiver Address P AP STA Mesh Destination Address Mesh Source Address Destination Address Source Address Mesh STA 6 STA Transmitter Address Mesh STA 4 Mesh STA 2 Mesh STA 1 STA 22 STA 33 L STA M M M AP STA M P STA
 63 Wrap Up
63 Wrap Up
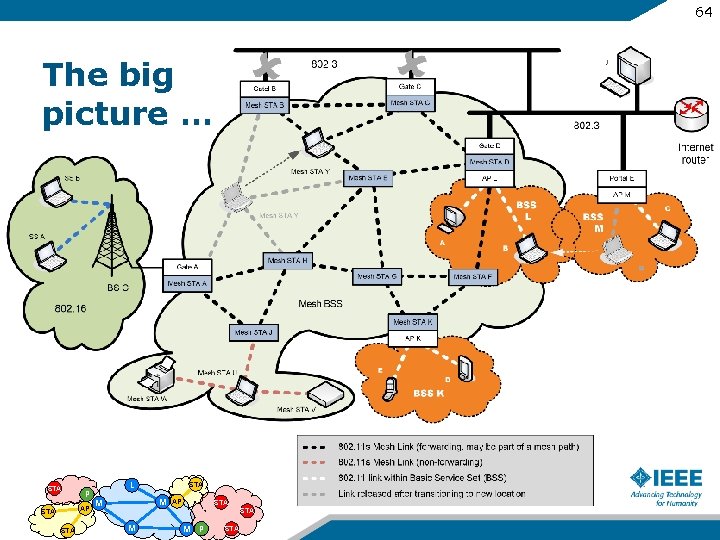 64 The big picture … STA P AP STA L STA M M AP STA M M P STA
64 The big picture … STA P AP STA L STA M M AP STA M M P STA
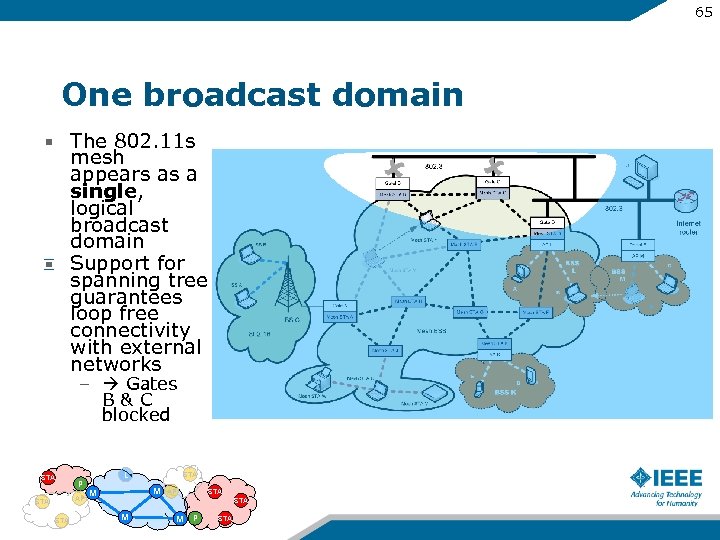 65 One broadcast domain The 802. 11 s mesh appears as a single, logical broadcast domain Support for spanning tree guarantees loop free connectivity with external networks – Gates B&C blocked STA P AP STA L STA M M AP STA M M P STA
65 One broadcast domain The 802. 11 s mesh appears as a single, logical broadcast domain Support for spanning tree guarantees loop free connectivity with external networks – Gates B&C blocked STA P AP STA L STA M M AP STA M M P STA
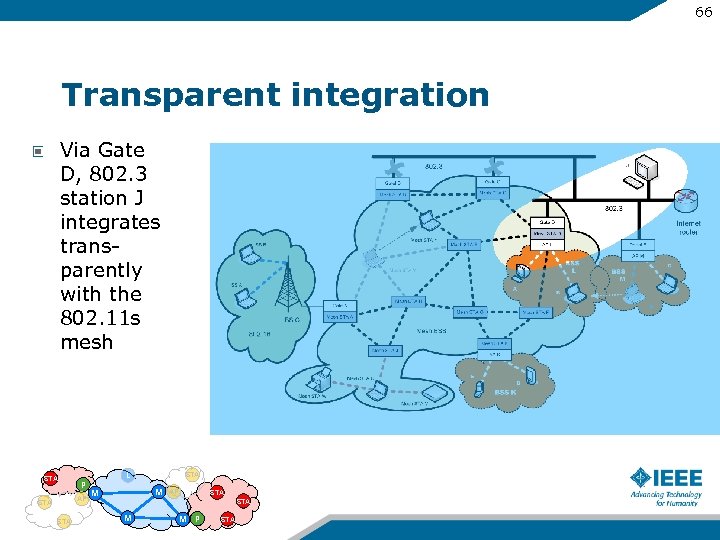 66 Transparent integration Via Gate D, 802. 3 station J integrates transparently with the 802. 11 s mesh STA P AP STA L STA M M AP STA M M P STA
66 Transparent integration Via Gate D, 802. 3 station J integrates transparently with the 802. 11 s mesh STA P AP STA L STA M M AP STA M M P STA
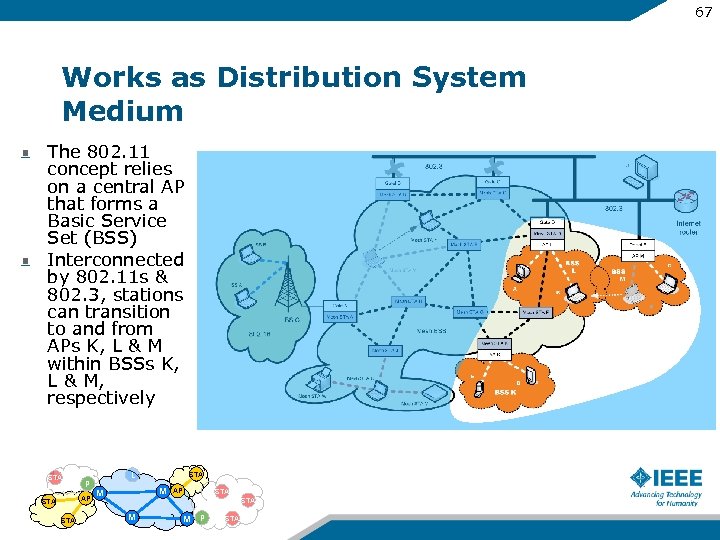 67 Works as Distribution System Medium The 802. 11 concept relies on a central AP that forms a Basic Service Set (BSS) Interconnected by 802. 11 s & 802. 3, stations can transition to and from APs K, L & M within BSSs K, L & M, respectively STA P AP STA L STA M M M AP STA M P STA
67 Works as Distribution System Medium The 802. 11 concept relies on a central AP that forms a Basic Service Set (BSS) Interconnected by 802. 11 s & 802. 3, stations can transition to and from APs K, L & M within BSSs K, L & M, respectively STA P AP STA L STA M M M AP STA M P STA
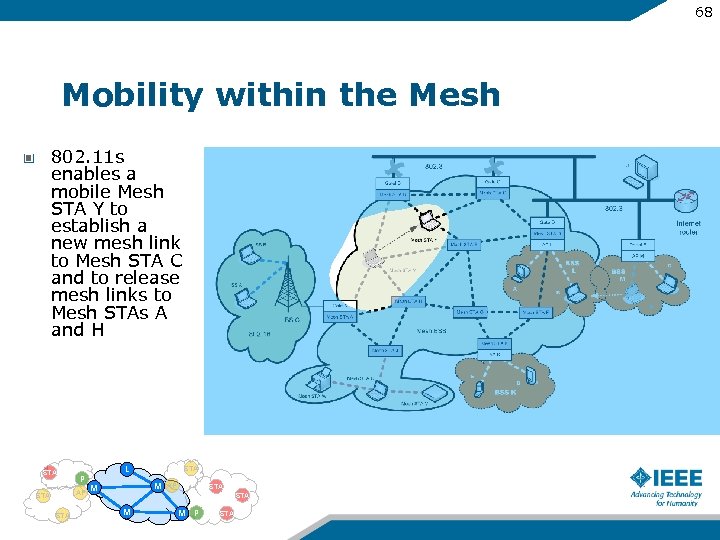 68 Mobility within the Mesh 802. 11 s enables a mobile Mesh STA Y to establish a new mesh link to Mesh STA C and to release mesh links to Mesh STAs A and H STA P AP STA L STA M M AP STA M M P STA
68 Mobility within the Mesh 802. 11 s enables a mobile Mesh STA Y to establish a new mesh link to Mesh STA C and to release mesh links to Mesh STAs A and H STA P AP STA L STA M M AP STA M M P STA
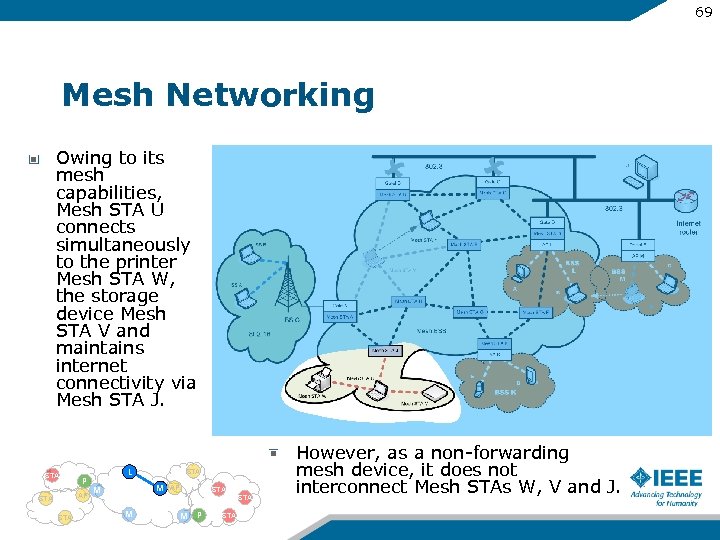 69 Mesh Networking Owing to its mesh capabilities, Mesh STA U connects simultaneously to the printer Mesh STA W, the storage device Mesh STA V and maintains internet connectivity via Mesh STA J. STA P AP STA L STA M M AP STA M M P STA However, as a non-forwarding mesh device, it does not interconnect Mesh STAs W, V and J.
69 Mesh Networking Owing to its mesh capabilities, Mesh STA U connects simultaneously to the printer Mesh STA W, the storage device Mesh STA V and maintains internet connectivity via Mesh STA J. STA P AP STA L STA M M AP STA M M P STA However, as a non-forwarding mesh device, it does not interconnect Mesh STAs W, V and J.
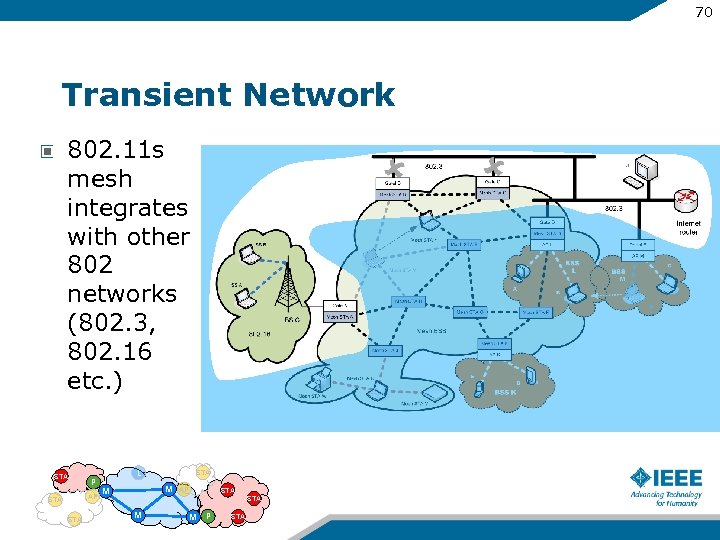 70 Transient Network 802. 11 s mesh integrates with other 802 networks (802. 3, 802. 16 etc. ) STA P AP STA L STA M M AP STA M M P STA
70 Transient Network 802. 11 s mesh integrates with other 802 networks (802. 3, 802. 16 etc. ) STA P AP STA L STA M M AP STA M M P STA
 71 Conclusion Transparent integration of other 802 networks Minimal manual configuration needed No change to 802. 11 hardware – All-software solution STA P AP STA L STA M M AP STA M M P STA Opens up new markets – Standardized range extension – Collaborative networks Truly ad hoc Solves old problems – Peer-to-peer – Authentication
71 Conclusion Transparent integration of other 802 networks Minimal manual configuration needed No change to 802. 11 hardware – All-software solution STA P AP STA L STA M M AP STA M M P STA Opens up new markets – Standardized range extension – Collaborative networks Truly ad hoc Solves old problems – Peer-to-peer – Authentication


