afe77ad8a2de0718540bc01847153672.ppt
- Количество слайдов: 31

The Good, The Bad and the Ugly: Network Performance in Malicious Environment First steps in Research CS – TAU – 1/2012 Udi Ben-Porat Anat Bremler-Barr Hanoch Levy ETH Zurich, Switzerland IDC Herzliya, Israel Tel-Aviv University, Israel 11/1/2012 First. Steps. In. Research - H. Levy - CS TAU 1
Traditional Network Analysis / Design n Expected Value Analysis q q n Worst Case Analysis q q n Average over a variety of cases Traditional “performance people” Take the worst case scenario Traditionally CS people “The Good” “The Bad” BASIC ASSUMPTION: q USERS WANT THE BEST FOR THEM 11/1/2012 First. Steps. In. Research - H. Levy - CS TAU 2
Today’s Networks n n n Can we still assume: “Users Want the Best for THEM”? Mostly yes… … BUT Not ALL! MALICIOUS USERS: “The UGLY” WANT TO HARM OTHERS’ PERFORMANCE 11/1/2012 First. Steps. In. Research - H. Levy - CS TAU 3 3
“Malicious” Network performance and Design n n “Expected” and “Worst” may not be enough Need to account for the malicious Need a “Malicious” performance methodology WE WANT to Combine “Performance” with “security” This talk: q q How to evaluate effect on Performance How to evaluate SYSTEM VULNERABILITY 11/1/2012 First. Steps. In. Research - H. Levy - CS TAU 4
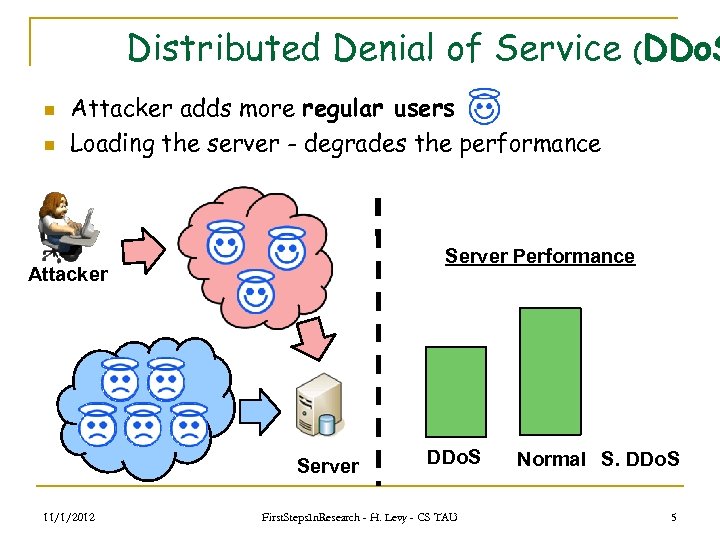
Distributed Denial of Service (DDo. S n n Attacker adds more regular users Loading the server - degrades the performance Server Performance Attacker Server 11/1/2012 DDo. S First. Steps. In. Research - H. Levy - CS TAU Normal S. DDo. S 5
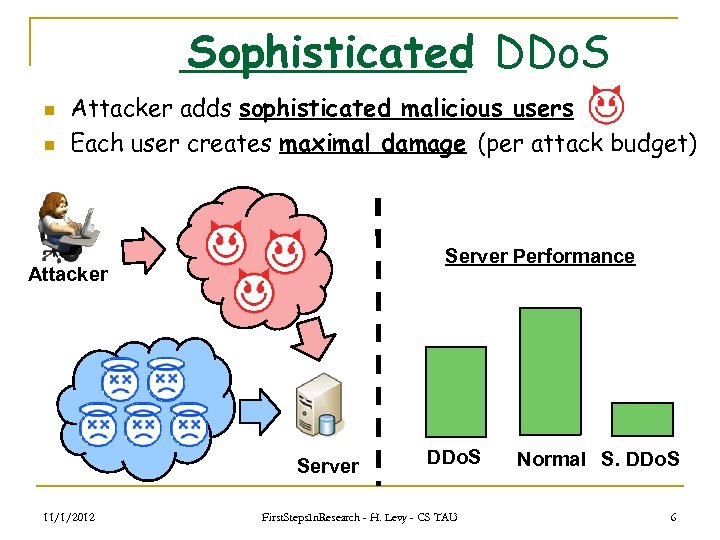
Sophisticated DDo. S n n Attacker adds sophisticated malicious users Each user creates maximal damage (per attack budget) Server Performance Attacker Server 11/1/2012 DDo. S First. Steps. In. Research - H. Levy - CS TAU Normal S. DDo. S 6
Study Objective Propose a DDo. S Vulnerability performance metric n q q Vulnerability Measure To be used in addition to traditional system performance metrics Understand the vulnerability of various systems to attacks n This Talk n n n Examples Describe DDo. S Vulnerability performance metric Demonstrate Metric impact q q q Hash Table: Very Common in networking Performance (traditional) : OPEN equivalent CLOSED Vulnerability analysis: OPEN << CLOSED!! 11/1/2012 First. Steps. In. Research - H. Levy - CS TAU 7
This Talk (cont) n Demonstrate Vulnerability in a distributed environment q Attacking the CDF Scheduling by collaboration 11/1/2012 First. Steps. In. Research - H. Levy - CS TAU 8
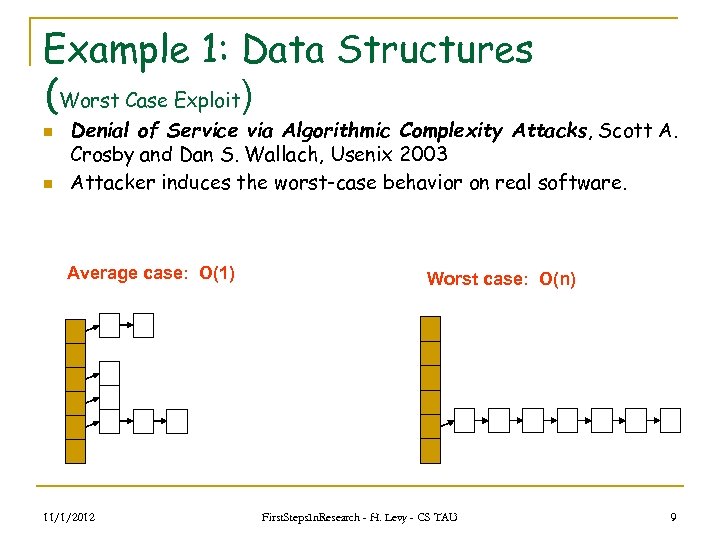
Example 1: Data Structures (Worst Case Exploit) n n Denial of Service via Algorithmic Complexity Attacks, Scott A. Crosby and Dan S. Wallach, Usenix 2003 Attacker induces the worst-case behavior on real software. Average case: O(1) 11/1/2012 Worst case: O(n) First. Steps. In. Research - H. Levy - CS TAU 9
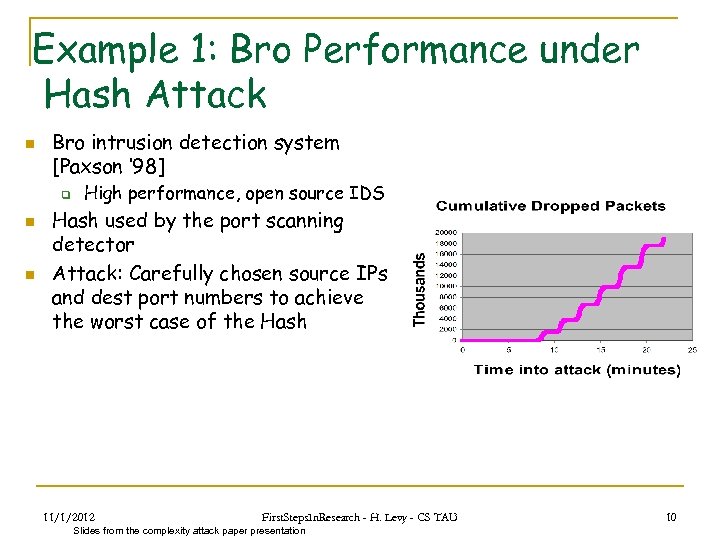
Example 1: Bro Performance under Hash Attack n Bro intrusion detection system [Paxson ‘ 98] q n n High performance, open source IDS Hash used by the port scanning detector Attack: Carefully chosen source IPs and dest port numbers to achieve the worst case of the Hash 11/1/2012 First. Steps. In. Research - H. Levy - CS TAU Slides from the complexity attack paper presentation 10
Example 2: Attack on Admission Control Mechanism (Traffic Pattern Exploit) n n Reduction of Quality (Ro. Q) Attacks on Internet End. Systems, Mina Guirguis, Azer Bestavros, Ibrahim Matta and Yuting Zhang, INFOCOM 2005 Reduction of Quality attack - targets the adaptation mechanisms prevent convergrnce to steady-state. 11/1/2012 First. Steps. In. Research - H. Levy - CS TAU 11
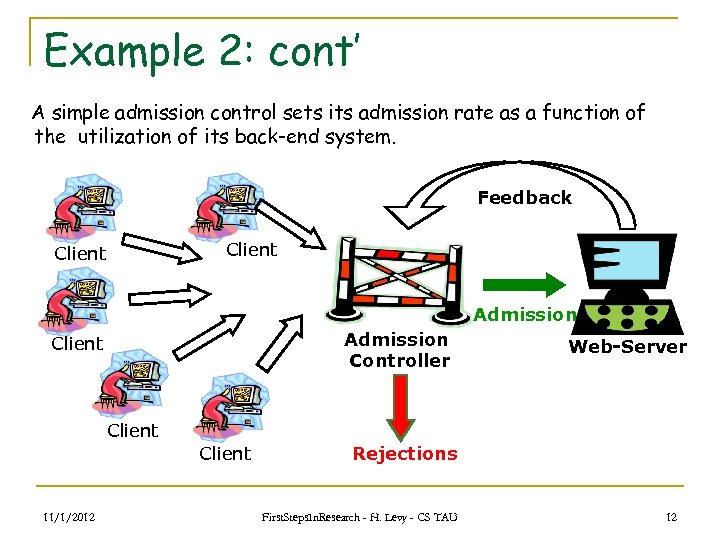
Example 2: cont’ A simple admission control sets its admission rate as a function of the utilization of its back-end system. Feedback Client Admission Controller Client Web-Server Client 11/1/2012 Rejections First. Steps. In. Research - H. Levy - CS TAU 12
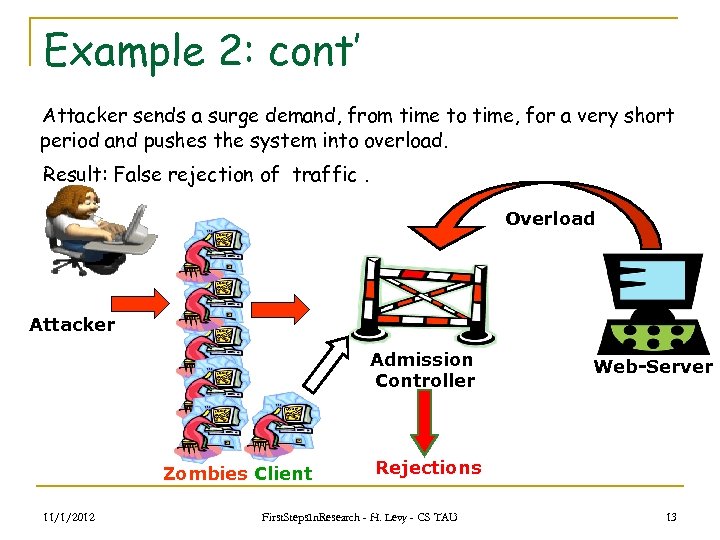
Example 2: cont’ Attacker sends a surge demand, from time to time, for a very short period and pushes the system into overload. Result: False rejection of traffic. Overload Attacker Admission Controller Zombies Client 11/1/2012 Web-Server Rejections First. Steps. In. Research - H. Levy - CS TAU 13
Example 3: Attack on TCP Retransmission (Traffic Pattern Exploit) n n Shrews: Low-Rate TCP-Targeted Denial of Service Attacks, A. Kuzmanovic and E. W. Knightly, Sigcomm 2003 Attacks exploit the timeout mechanism of TCP resulting in a complete denial of service. Shrew 11/1/2012 First. Steps. In. Research - H. Levy - CS TAU 14
Multiple Access Protocols (Protocol Deviation Exploit) n Ethernet like protocol q q q 11/1/2012 Shared channel, a set of nodes send and receive frames over the same channel, only one node can transmit at a time Each node runs a collision avoiding algorithm. Attackers disobey collision avoidance disturb the transmission over the channel First. Steps. In. Research - H. Levy - CS TAU 15

Our goal n Proposing a Vulnerability measurement for all sophisticated DDo. S attacks q q n Vulnerability Measurement How easy it is to degrade your users performance Understanding the vulnerability of different systems to sophisticated attacks 11/1/2012 First. Steps. In. Research - H. Levy - CS TAU 16
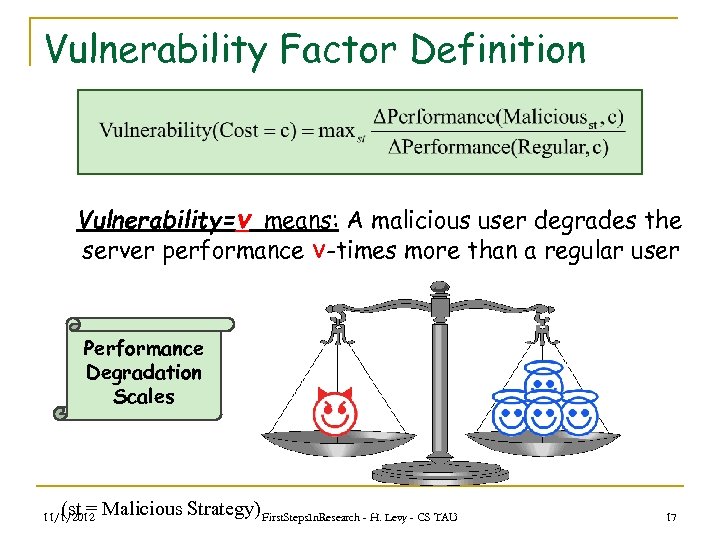
Vulnerability Factor Definition Vulnerability=v means: A malicious user degrades the server performance v-times more than a regular user Performance Degradation Scales (st = Malicious Strategy) First. Steps. In. Research - H. Levy - CS TAU 11/1/2012 17
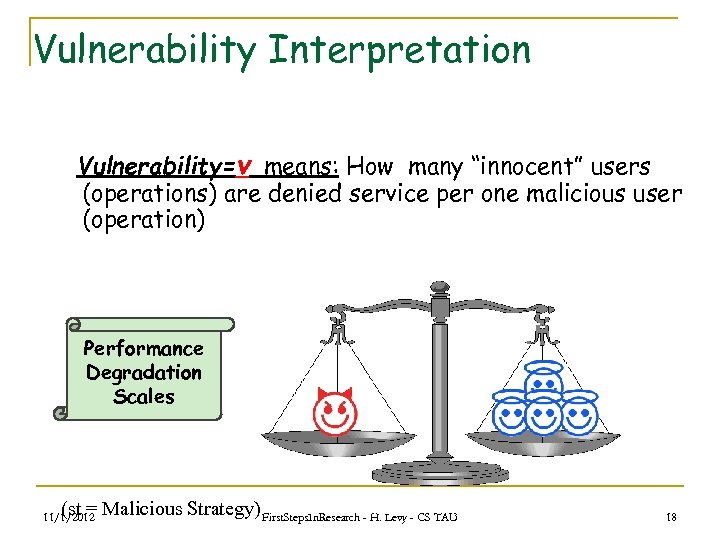
Vulnerability Interpretation Vulnerability=v means: How many “innocent” users (operations) are denied service per one malicious user (operation) Performance Degradation Scales (st = Malicious Strategy) First. Steps. In. Research - H. Levy - CS TAU 11/1/2012 18
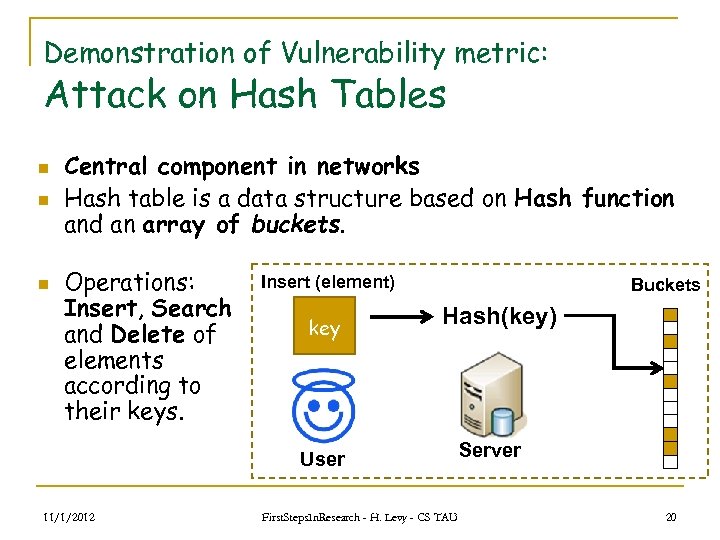
Demonstration of Vulnerability metric: Attack on Hash Tables n n n Central component in networks Hash table is a data structure based on Hash function and an array of buckets. Operations: Insert, Search and Delete of elements according to their keys. Insert (element) key Buckets Hash(key) User 11/1/2012 First. Steps. In. Research - H. Levy - CS TAU Server 20
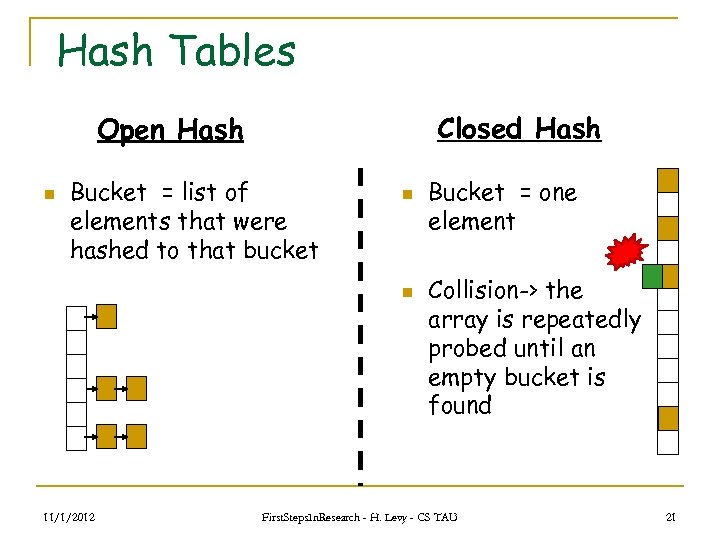
Hash Tables Closed Hash Open Hash n Bucket = list of elements that were hashed to that bucket n n 11/1/2012 Bucket = one element Collision-> the array is repeatedly probed until an empty bucket is found First. Steps. In. Research - H. Levy - CS TAU 21
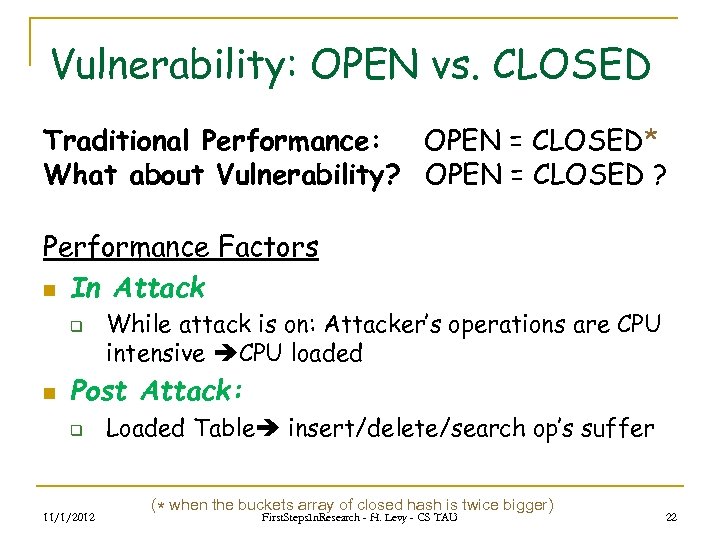
Vulnerability: OPEN vs. CLOSED Traditional Performance: OPEN = CLOSED* What about Vulnerability? OPEN = CLOSED ? Performance Factors n In Attack q n While attack is on: Attacker’s operations are CPU intensive CPU loaded Post Attack: q 11/1/2012 Loaded Table insert/delete/search op’s suffer (* when the buckets array of closed hash is twice bigger) First. Steps. In. Research - H. Levy - CS TAU 22
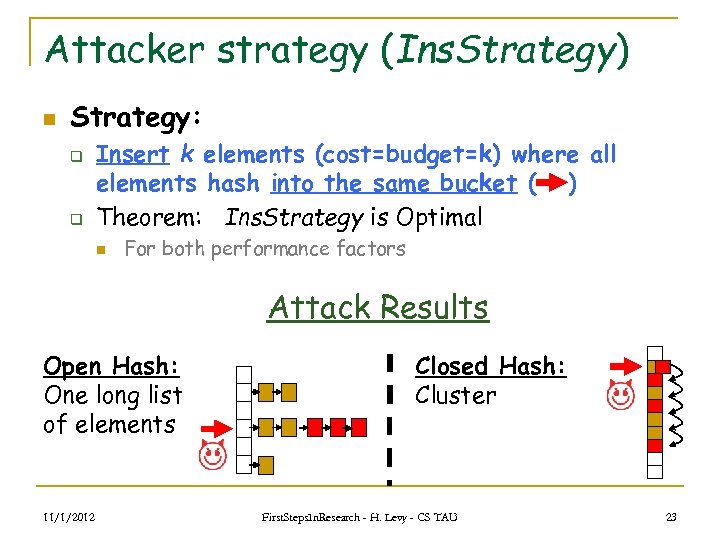
Attacker strategy (Ins. Strategy) n Strategy: q q Insert k elements (cost=budget=k) where all elements hash into the same bucket ( ) Theorem: Ins. Strategy is Optimal n For both performance factors Attack Results Open Hash: One long list of elements 11/1/2012 Closed Hash: Cluster First. Steps. In. Research - H. Levy - CS TAU 23
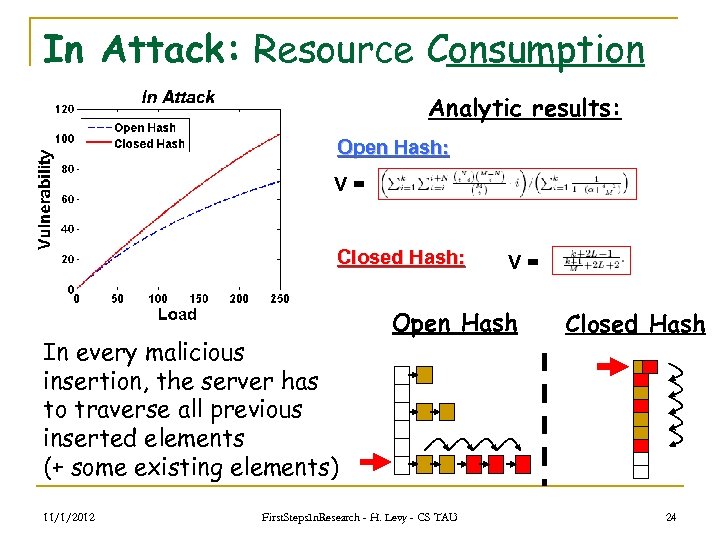
In Attack: Resource Consumption Analytic results: Open Hash: V= Closed Hash: In every malicious insertion, the server has to traverse all previous inserted elements (+ some existing elements) 11/1/2012 V= Open Hash First. Steps. In. Research - H. Levy - CS TAU Closed Hash 24
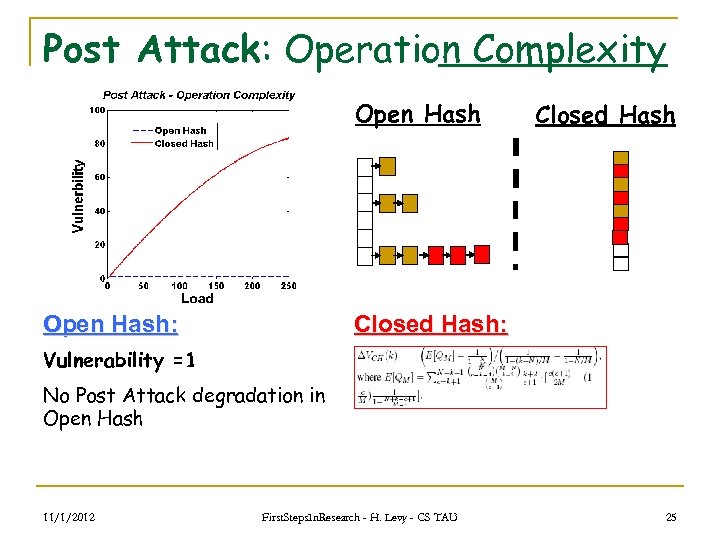
Post Attack: Operation Complexity Open Hash: Closed Hash: Vulnerability =1 No Post Attack degradation in Open Hash 11/1/2012 First. Steps. In. Research - H. Levy - CS TAU 25
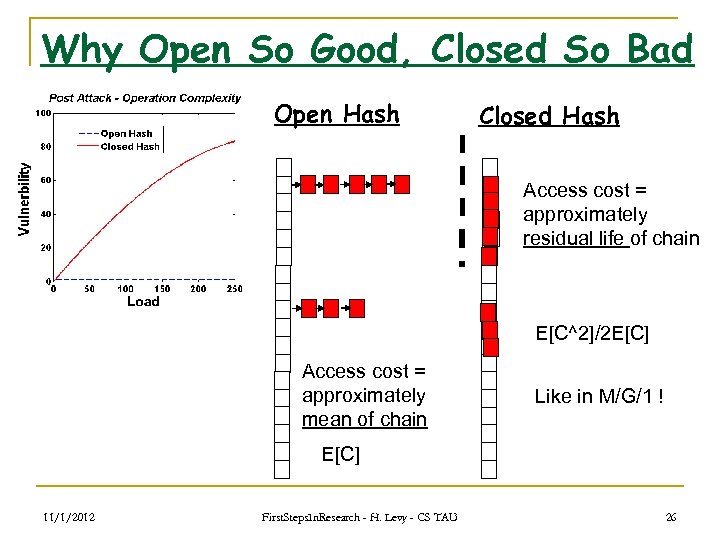
Why Open So Good, Closed So Bad Open Hash Closed Hash Access cost = approximately residual life of chain E[C^2]/2 E[C] Access cost = approximately mean of chain Like in M/G/1 ! E[C] 11/1/2012 First. Steps. In. Research - H. Levy - CS TAU 26
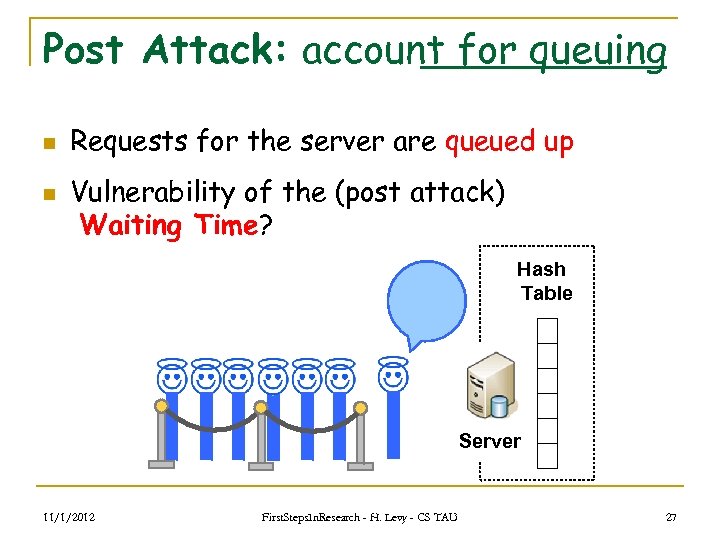
Post Attack: account for queuing n n Requests for the server are queued up Vulnerability of the (post attack) Waiting Time? Hash Table Server 11/1/2012 First. Steps. In. Research - H. Levy - CS TAU 27
![Queue Analysis (M/G/1) n n Waiting time is proportional to E[S^2] / E[s] S Queue Analysis (M/G/1) n n Waiting time is proportional to E[S^2] / E[s] S](https://present5.com/presentation/afe77ad8a2de0718540bc01847153672/image-27.jpg)
Queue Analysis (M/G/1) n n Waiting time is proportional to E[S^2] / E[s] S = service time (Random variable) Hash Table Server 11/1/2012 First. Steps. In. Research - H. Levy - CS TAU 28
![Post Attack Waiting Time Open Hash: Service times proportional to chain length E[S] = Post Attack Waiting Time Open Hash: Service times proportional to chain length E[S] =](https://present5.com/presentation/afe77ad8a2de0718540bc01847153672/image-28.jpg)
Post Attack Waiting Time Open Hash: Service times proportional to chain length E[S] = 1 E[S^2] > 1 Stability Point OPEN n 11/1/2012 Now is VULNERABLE !! First. Steps. In. Research - H. Levy - CS TAU 29
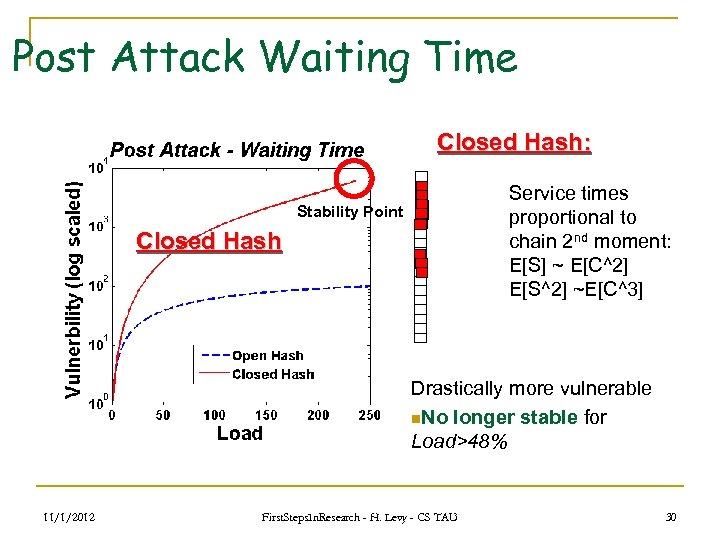
Post Attack Waiting Time Closed Hash: Service times proportional to chain 2 nd moment: E[S] ~ E[C^2] E[S^2] ~E[C^3] Stability Point Closed Hash Drastically more vulnerable n. No longer stable for Load>48% 11/1/2012 First. Steps. In. Research - H. Levy - CS TAU 30
Conclusions n HASH: q q n Normal performance: Closed hash = Open Hash Under attack Closed hash >> Open Hash Malicious Performance: q q 11/1/2012 Need Performance evaluation to account for attacks Can use the vulnerability metric First. Steps. In. Research - H. Levy - CS TAU 31

Questions? 11/1/2012 First. Steps. In. Research - H. Levy - CS TAU 32
afe77ad8a2de0718540bc01847153672.ppt