62cddd9fa6d54a3d23086f558ba4b80d.ppt
- Количество слайдов: 24
 The Five Phases of Hacking
The Five Phases of Hacking
 • • • Reconnaissance Scanning Gaining Access Maintaining Access Covering Tracks
• • • Reconnaissance Scanning Gaining Access Maintaining Access Covering Tracks
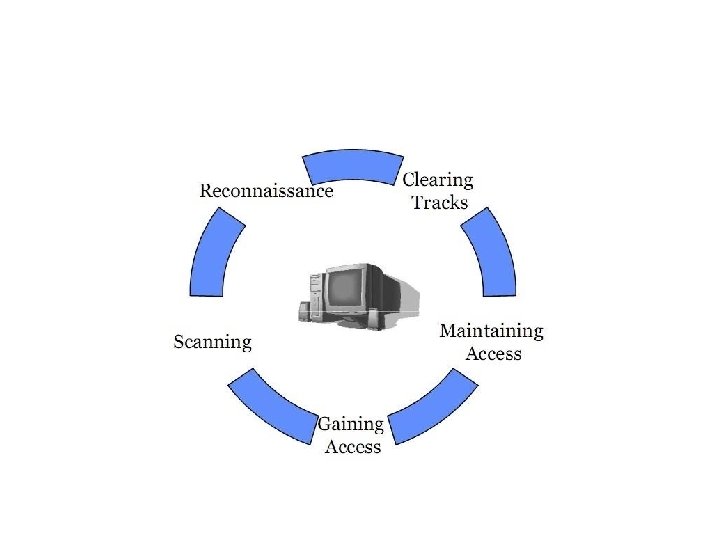
 Reconnaissance • This is the primary phase where the Hacker tries to collect as much information as possible about the target. It includes Identifying the Target, finding out the target's IP Address Range, Network, DNS records, etc.
Reconnaissance • This is the primary phase where the Hacker tries to collect as much information as possible about the target. It includes Identifying the Target, finding out the target's IP Address Range, Network, DNS records, etc.
 Scanning • It involves taking the information discovered during reconnaissance and using it to examine the network. • Tools that a hacker may employ during the scanning phase can include dialers, port scanners, network mappers, sweepers, and vulnerability scanners. • Hackers are seeking any information that can help them perpetrate attack such as computer names, IP addresses, and user accounts.
Scanning • It involves taking the information discovered during reconnaissance and using it to examine the network. • Tools that a hacker may employ during the scanning phase can include dialers, port scanners, network mappers, sweepers, and vulnerability scanners. • Hackers are seeking any information that can help them perpetrate attack such as computer names, IP addresses, and user accounts.
 Gaining Access • After scanning, the hacker designs the blueprint of the network of the target with the help of data collected during Phase 1 and Phase 2. • This is the phase where the real hacking takes place. Vulnerabilities discovered during the reconnaissance and scanning phase are now exploited to gain access. • The method of connection the hacker uses for an exploit can be a local area network (LAN, either wired or wireless), local access to a PC, the Internet, or offline. • Examples include stack based buffer overflows, denial of service (Do. S), and session hijacking. • Gaining access is known in the hacker world as owning the system
Gaining Access • After scanning, the hacker designs the blueprint of the network of the target with the help of data collected during Phase 1 and Phase 2. • This is the phase where the real hacking takes place. Vulnerabilities discovered during the reconnaissance and scanning phase are now exploited to gain access. • The method of connection the hacker uses for an exploit can be a local area network (LAN, either wired or wireless), local access to a PC, the Internet, or offline. • Examples include stack based buffer overflows, denial of service (Do. S), and session hijacking. • Gaining access is known in the hacker world as owning the system
 Maintaining Access • Once a hacker has gained access, they want to keep that access for future exploitation and attacks. Sometimes, hackers harden the system from other hackers or security personnel by securing their exclusive access with backdoors, rootkits, and Trojans. • Once the hacker owns the system, they can use it as a base to launch additional attacks. • In this case, the owned system is sometimes referred to as a zombie system.
Maintaining Access • Once a hacker has gained access, they want to keep that access for future exploitation and attacks. Sometimes, hackers harden the system from other hackers or security personnel by securing their exclusive access with backdoors, rootkits, and Trojans. • Once the hacker owns the system, they can use it as a base to launch additional attacks. • In this case, the owned system is sometimes referred to as a zombie system.
 Covering Tracks • Once hackers have been able to gain and maintain access, they cover their tracks to avoid detection by security personnel, to continue to use the owned system, to remove evidence of hacking, or to avoid legal action. • Hackers try to remove all traces of the attack, such as log files or intrusion detection system (IDS) alarms. • Examples of activities during this phase of the attack include steganography, the use of tunneling protocols, and altering log files.
Covering Tracks • Once hackers have been able to gain and maintain access, they cover their tracks to avoid detection by security personnel, to continue to use the owned system, to remove evidence of hacking, or to avoid legal action. • Hackers try to remove all traces of the attack, such as log files or intrusion detection system (IDS) alarms. • Examples of activities during this phase of the attack include steganography, the use of tunneling protocols, and altering log files.
 Passive Attacks vs Active Attacks – Basic Principles and Motivations
Passive Attacks vs Active Attacks – Basic Principles and Motivations
 • For classification purposes, methods which use covert and non-disruptive techniques and technologies to gain access to data are deemed as passive. • They are “attacks” in the sense of being information-gathering attempts by unauthorized individuals, organizations, or malware. • The information acquired may be put to use immediately, salted away for analysis, exposure, or sale – or used as a resource in conducting further operations.
• For classification purposes, methods which use covert and non-disruptive techniques and technologies to gain access to data are deemed as passive. • They are “attacks” in the sense of being information-gathering attempts by unauthorized individuals, organizations, or malware. • The information acquired may be put to use immediately, salted away for analysis, exposure, or sale – or used as a resource in conducting further operations.
 • Typically, a passive attack involves a perpetrator eavesdropping on ongoing communications (telecommunication, email, etc. ) or recording network and computer activity. • A classic example is the “war driving” scenario, where an eavesdropper parks their scannerequipped vehicle in the vicinity of an unsecured wireless network, and uses a packet sniffer or other tools to intercept data traffic and listen in.
• Typically, a passive attack involves a perpetrator eavesdropping on ongoing communications (telecommunication, email, etc. ) or recording network and computer activity. • A classic example is the “war driving” scenario, where an eavesdropper parks their scannerequipped vehicle in the vicinity of an unsecured wireless network, and uses a packet sniffer or other tools to intercept data traffic and listen in.
 • Motives driving passive attacks depend on the assailant. • Idle curiosity or gathering materials for investigation (e. g. market research, journalism, etc. ) lie at the less malicious end of the scale, • while more serious operators look to acquire data for sale to interested parties, direct financial gain (e. g. credit card fraud), or its potential to cause damage through exposure.
• Motives driving passive attacks depend on the assailant. • Idle curiosity or gathering materials for investigation (e. g. market research, journalism, etc. ) lie at the less malicious end of the scale, • while more serious operators look to acquire data for sale to interested parties, direct financial gain (e. g. credit card fraud), or its potential to cause damage through exposure.
 • By contrast, active attack methods are almost always malicious (exceptions would include authorized penetration testing, and the like), and can manifest in various forms. • Some use direct action involving tools and technologies like malware, Trojans, password crackers, or the staging of Denial of Service (Do. S) attacks. • Others rely on information gathered from passive reconnaissance activities, or the compromise of existing networks staged by agents or malware previously put in place as “sleepers”.
• By contrast, active attack methods are almost always malicious (exceptions would include authorized penetration testing, and the like), and can manifest in various forms. • Some use direct action involving tools and technologies like malware, Trojans, password crackers, or the staging of Denial of Service (Do. S) attacks. • Others rely on information gathered from passive reconnaissance activities, or the compromise of existing networks staged by agents or malware previously put in place as “sleepers”.
 • In a typical active attack scenario, the perpetrator looks to gain access to information or network resources that may be used for their own benefit, or to disrupt or even cripple a network as an act of sabotage, terrorism, or for purposes of extortion.
• In a typical active attack scenario, the perpetrator looks to gain access to information or network resources that may be used for their own benefit, or to disrupt or even cripple a network as an act of sabotage, terrorism, or for purposes of extortion.
 Passive Preludes to Active • Phased assaults using a combination of passive and active technologies are far from uncommon. Reconnaissance by passive means allows intruders to monitor networks for vulnerabilities, using methods like session capture, while active reconnaissance employs port scanning and other techniques to engage with the targeted system.
Passive Preludes to Active • Phased assaults using a combination of passive and active technologies are far from uncommon. Reconnaissance by passive means allows intruders to monitor networks for vulnerabilities, using methods like session capture, while active reconnaissance employs port scanning and other techniques to engage with the targeted system.
 • Physical methods of detection like dumpster diving can supplement scanning technology, and yield information to facilitate their infiltration of systems and networks. • Masquerade attacks enable intruders to use stolen credentials and passwords to gain authorized access and network privileges that allow them to monitor network traffic without raising undue suspicion.
• Physical methods of detection like dumpster diving can supplement scanning technology, and yield information to facilitate their infiltration of systems and networks. • Masquerade attacks enable intruders to use stolen credentials and passwords to gain authorized access and network privileges that allow them to monitor network traffic without raising undue suspicion.
 Exploiting Passive Gains • Passive system monitoring can yield a trove of knowledge that intruders may use directly or indirectly. • Having an “inside man” (or woman), or remote and privileged access to a corporate network enables perpetrators to play a long game, whereby trade secrets, user credentials, or financial information may be gathered over time for future sale or deployment in fraud schemes, identity theft, etc.
Exploiting Passive Gains • Passive system monitoring can yield a trove of knowledge that intruders may use directly or indirectly. • Having an “inside man” (or woman), or remote and privileged access to a corporate network enables perpetrators to play a long game, whereby trade secrets, user credentials, or financial information may be gathered over time for future sale or deployment in fraud schemes, identity theft, etc.
 • For those seeking to commit further acts of cyber-assault, passwords and credentials gained by passive means can allow the perpetrators direct access to their target networks, while a knowledge of the vulnerabilities within a target system may provide the key to the exploits needed to stage a more direct attack.
• For those seeking to commit further acts of cyber-assault, passwords and credentials gained by passive means can allow the perpetrators direct access to their target networks, while a knowledge of the vulnerabilities within a target system may provide the key to the exploits needed to stage a more direct attack.
 Defensive Measures • Internet connectivity today demands an accompanying suite of security defenses that includes personal and internet firewalls, intrusion prevention systems (IPS), spam filters, and anti-malware/anti-virus software. • These are of necessity passive and sometimes reactive technologies which meet assaults in a rules-based, and case-by-case response.
Defensive Measures • Internet connectivity today demands an accompanying suite of security defenses that includes personal and internet firewalls, intrusion prevention systems (IPS), spam filters, and anti-malware/anti-virus software. • These are of necessity passive and sometimes reactive technologies which meet assaults in a rules-based, and case-by-case response.
 • Automated event log analysis should be instituted by network administrators and security officers, to flag assaults in progress or activities like multiple login attempts that might indicate an attempted breach. • Such passive monitoring must of course be supplemented by an active response on the part of security personnel and the network tools used for threat isolation and remediation.
• Automated event log analysis should be instituted by network administrators and security officers, to flag assaults in progress or activities like multiple login attempts that might indicate an attempted breach. • Such passive monitoring must of course be supplemented by an active response on the part of security personnel and the network tools used for threat isolation and remediation.
 • Port scanning to verify network security remains an active procedure that’s a doubleedged sword, as hackers may also use the technique to detect open active ports and exploit any vulnerabilities detected there. Penetration tests authorized by an enterprise and conducted by security professionals remain an active security awareness and defense option.
• Port scanning to verify network security remains an active procedure that’s a doubleedged sword, as hackers may also use the technique to detect open active ports and exploit any vulnerabilities detected there. Penetration tests authorized by an enterprise and conducted by security professionals remain an active security awareness and defense option.
 • Encrypted communication between network hosts remains an effective hedge against packet or network sniffing – and encryption is highly recommended for all transmissions of sensitive data over publicly accessible networks.
• Encrypted communication between network hosts remains an effective hedge against packet or network sniffing – and encryption is highly recommended for all transmissions of sensitive data over publicly accessible networks.
 The Importance of Security Awareness • The weak link in the security chain so often presented by human ignorance and error may be best addressed through periodic sessions of security awareness training. • In addition to strong password and authentication policies, issues of email and social media/social engineering etiquette should be addressed – together with updates on emerging security techniques, prevailing threats, and best practices.
The Importance of Security Awareness • The weak link in the security chain so often presented by human ignorance and error may be best addressed through periodic sessions of security awareness training. • In addition to strong password and authentication policies, issues of email and social media/social engineering etiquette should be addressed – together with updates on emerging security techniques, prevailing threats, and best practices.
 • Passive reconnaissance is an attempt to gain information about targeted computers and networks without actively engaging with the systems. • In active reconnaissance, in contrast, the attacker engages with the target system, typically conducting a port scan to determine find any open ports.
• Passive reconnaissance is an attempt to gain information about targeted computers and networks without actively engaging with the systems. • In active reconnaissance, in contrast, the attacker engages with the target system, typically conducting a port scan to determine find any open ports.


