a9ecbe45ac92980c895fa5dd8bff2220.ppt
- Количество слайдов: 40
 The Endeavour Expedition: Computing and Communications at the e. Xtremes Professor Randy H. Katz CS Division, EECS Department University of California, Berkeley Invited Presentation IBM Pv. CC 2000 Conference 1
The Endeavour Expedition: Computing and Communications at the e. Xtremes Professor Randy H. Katz CS Division, EECS Department University of California, Berkeley Invited Presentation IBM Pv. CC 2000 Conference 1
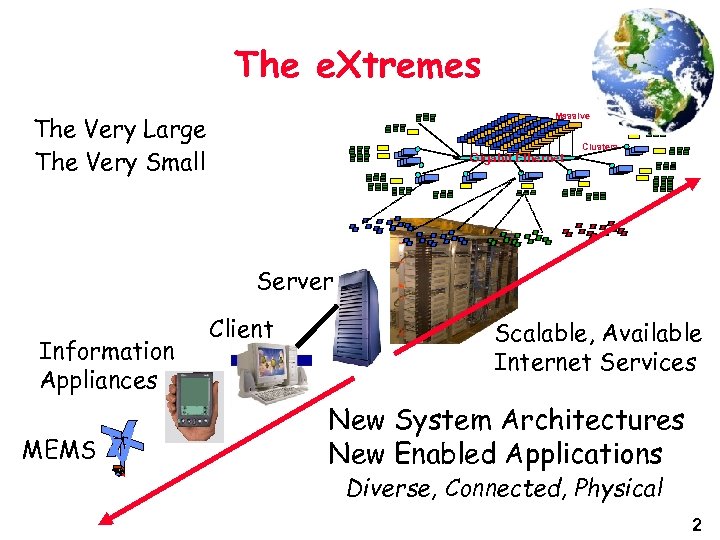 The e. Xtremes The Very Large The Very Small Massive Cluster Gigabit Ethernet Clusters Server Information Appliances MEMS Client Scalable, Available Internet Services New System Architectures New Enabled Applications Diverse, Connected, Physical 2
The e. Xtremes The Very Large The Very Small Massive Cluster Gigabit Ethernet Clusters Server Information Appliances MEMS Client Scalable, Available Internet Services New System Architectures New Enabled Applications Diverse, Connected, Physical 2
 Presentation Outline • Expedition Motivation – The Needed Revolution in Computing and Communications • Packing for the Expedition – Project Organization • Base Exploration plus Extended Expeditions • New Century Distributed System Architecture • Summary and Conclusions 3
Presentation Outline • Expedition Motivation – The Needed Revolution in Computing and Communications • Packing for the Expedition – Project Organization • Base Exploration plus Extended Expeditions • New Century Distributed System Architecture • Summary and Conclusions 3
 Background • PITAC Report: “Information Technology Research--Investing in Our Future” – Create a strategic initiative in long-term information technology R&D – Priorities: Software, Scalable Information Infrastructure, High-End Computing, Socioeconomic Impacts • DARPA (and Industry) as Patron – Chart potential “revolutions” in information technology, with promise to achieve dramatic improvements in computing and applications in 21 st Century – Technology discontinuities drive new computing paradigms, applications, system architectures » E. g. , Project MAC, ARPAnet, Xerox Alto – What will drive the next discontinuity? 4
Background • PITAC Report: “Information Technology Research--Investing in Our Future” – Create a strategic initiative in long-term information technology R&D – Priorities: Software, Scalable Information Infrastructure, High-End Computing, Socioeconomic Impacts • DARPA (and Industry) as Patron – Chart potential “revolutions” in information technology, with promise to achieve dramatic improvements in computing and applications in 21 st Century – Technology discontinuities drive new computing paradigms, applications, system architectures » E. g. , Project MAC, ARPAnet, Xerox Alto – What will drive the next discontinuity? 4
 The Endeavour Expedition: Motivation and Goals • Exploiting IT to enhance understanding – Make it dramatically more convenient for people to interact with information, devices, and other people – Supported by a “planetary-scale” Information Utility » Stress tested by challenging applications in decision making and learning » New methodologies for design, construction, and administration of systems of unprecedented scale and complexity – Figure of merit: how effectively we amplify and leverage human intellect • Technical Approach: Pervasive Information Utility, based on “fluid systems, ” enabling new approaches for problem solving & learning 5
The Endeavour Expedition: Motivation and Goals • Exploiting IT to enhance understanding – Make it dramatically more convenient for people to interact with information, devices, and other people – Supported by a “planetary-scale” Information Utility » Stress tested by challenging applications in decision making and learning » New methodologies for design, construction, and administration of systems of unprecedented scale and complexity – Figure of merit: how effectively we amplify and leverage human intellect • Technical Approach: Pervasive Information Utility, based on “fluid systems, ” enabling new approaches for problem solving & learning 5
 Why “Endeavour”? • To strive or reach; a serious determined effort (Webster’s 7 th New Collegiate Dictionary); British spelling • Captain Cook’s ship from his first voyage of exploration of the great unknown of his day: the southern Pacific Ocean (1768 -1771) – Brought more land wealth to the British Empire than any military campaign – Cook’s lasting contribution: comprehensive knowledge of the people, customs, and ideas that lay across the sea – “He left nothing to his successors other than to marvel at the completeness of his work. ” • Software and resources as a fluid: pools, floods, rivers, eddies, containers, . . . 6
Why “Endeavour”? • To strive or reach; a serious determined effort (Webster’s 7 th New Collegiate Dictionary); British spelling • Captain Cook’s ship from his first voyage of exploration of the great unknown of his day: the southern Pacific Ocean (1768 -1771) – Brought more land wealth to the British Empire than any military campaign – Cook’s lasting contribution: comprehensive knowledge of the people, customs, and ideas that lay across the sea – “He left nothing to his successors other than to marvel at the completeness of his work. ” • Software and resources as a fluid: pools, floods, rivers, eddies, containers, . . . 6
 Signing On to the Expedition • “Difficulties are just things to overcome. ” • "Men [and Women] wanted for Hazardous Journey. Small wages, bitter cold, long months of complete darkness, constant danger, safe return doubtful. Honour and recognition in case of success. " – Sir Ernest Shackleton, Legendary Antarctic explorer who lost not a single person on two highly perilous expeditions to reach the South Pole (which he never reached!) • Business UNusual: Research seminars, experimental courses, new synthesis of existing courses 7
Signing On to the Expedition • “Difficulties are just things to overcome. ” • "Men [and Women] wanted for Hazardous Journey. Small wages, bitter cold, long months of complete darkness, constant danger, safe return doubtful. Honour and recognition in case of success. " – Sir Ernest Shackleton, Legendary Antarctic explorer who lost not a single person on two highly perilous expeditions to reach the South Pole (which he never reached!) • Business UNusual: Research seminars, experimental courses, new synthesis of existing courses 7
 Expedition Assumptions • Human time and attention, not processing or storage, are the limiting factors • Givens: – Vast diversity of computing devices (PDAs, cameras, displays, sensors, actuators, mobile robots, vehicles); No “average” device – Unlimited storage: everything that can be captured, digitized, and stored, will be – Every computing device is connected in proportion to its capacity – Devices are predominately compatible rather than incompatible (plug-and-play enabled by on-the-fly translation/adaptation) • Tremendous innovations in technology; yet a comprehensive system architecture is lacking 8
Expedition Assumptions • Human time and attention, not processing or storage, are the limiting factors • Givens: – Vast diversity of computing devices (PDAs, cameras, displays, sensors, actuators, mobile robots, vehicles); No “average” device – Unlimited storage: everything that can be captured, digitized, and stored, will be – Every computing device is connected in proportion to its capacity – Devices are predominately compatible rather than incompatible (plug-and-play enabled by on-the-fly translation/adaptation) • Tremendous innovations in technology; yet a comprehensive system architecture is lacking 8
 Expedition Challenges • Managing Attention is the Killer App – Not corporate processing but management, analysis, aggregation, dissemination, filtering for the individual • Create Knowledge, not Data – Not management/retrieval of explicitly entered information, but automated extraction and organization of daily activities • Information Technology as a Utility – Continuous service delivery, on a planetary-scale, on top of a highly dynamic information base • Beyond the Desktop – Community computing: infer relationships among information, delegate control, establish authority 9
Expedition Challenges • Managing Attention is the Killer App – Not corporate processing but management, analysis, aggregation, dissemination, filtering for the individual • Create Knowledge, not Data – Not management/retrieval of explicitly entered information, but automated extraction and organization of daily activities • Information Technology as a Utility – Continuous service delivery, on a planetary-scale, on top of a highly dynamic information base • Beyond the Desktop – Community computing: infer relationships among information, delegate control, establish authority 9
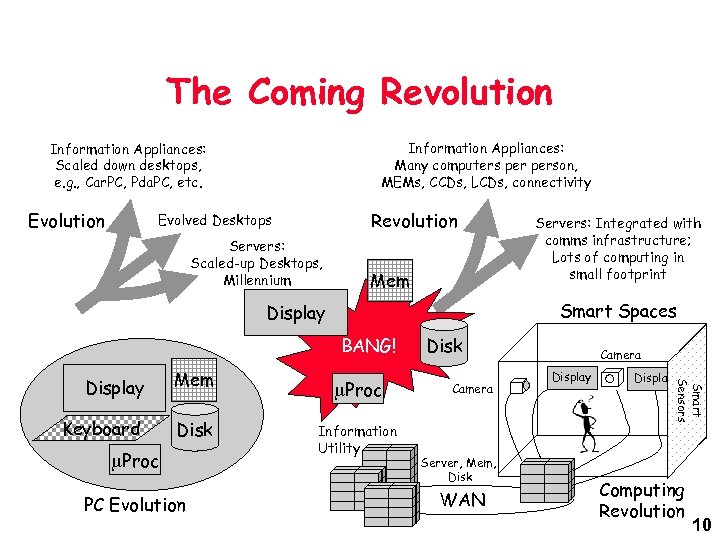 The Coming Revolution Information Appliances: Many computers person, MEMs, CCDs, LCDs, connectivity Information Appliances: Scaled down desktops, e. g. , Car. PC, Pda. PC, etc. Evolution Revolution Evolved Desktops Servers: Scaled-up Desktops, Millennium Mem Smart Spaces Display BANG! Mem Keyboard Disk m. Proc PC Evolution m. Proc Information Utility Disk Camera Server, Mem, Disk WAN Camera Display Smart Sensors Display Servers: Integrated with comms infrastructure; Lots of computing in small footprint Computing Revolution 10
The Coming Revolution Information Appliances: Many computers person, MEMs, CCDs, LCDs, connectivity Information Appliances: Scaled down desktops, e. g. , Car. PC, Pda. PC, etc. Evolution Revolution Evolved Desktops Servers: Scaled-up Desktops, Millennium Mem Smart Spaces Display BANG! Mem Keyboard Disk m. Proc PC Evolution m. Proc Information Utility Disk Camera Server, Mem, Disk WAN Camera Display Smart Sensors Display Servers: Integrated with comms infrastructure; Lots of computing in small footprint Computing Revolution 10
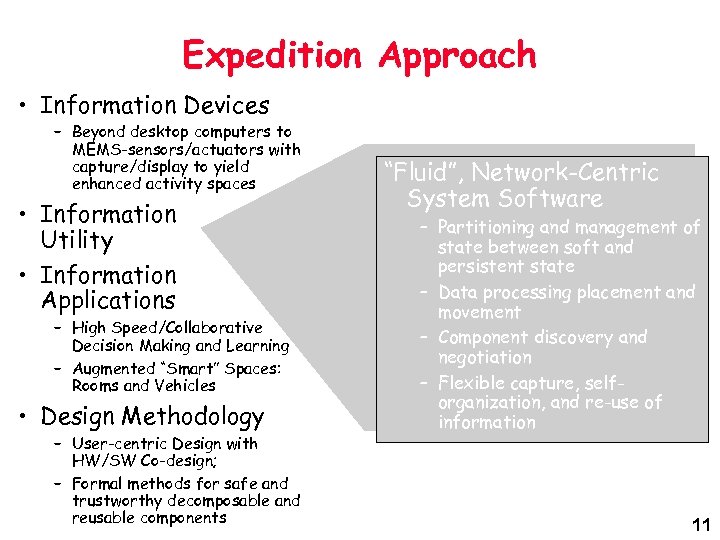 Expedition Approach • Information Devices – Beyond desktop computers to MEMS-sensors/actuators with capture/display to yield enhanced activity spaces • Information Utility • Information Applications – High Speed/Collaborative Decision Making and Learning – Augmented “Smart” Spaces: Rooms and Vehicles • Design Methodology – User-centric Design with HW/SW Co-design; – Formal methods for safe and trustworthy decomposable and reusable components “Fluid”, Network-Centric System Software – Partitioning and management of state between soft and persistent state – Data processing placement and movement – Component discovery and negotiation – Flexible capture, selforganization, and re-use of information 11
Expedition Approach • Information Devices – Beyond desktop computers to MEMS-sensors/actuators with capture/display to yield enhanced activity spaces • Information Utility • Information Applications – High Speed/Collaborative Decision Making and Learning – Augmented “Smart” Spaces: Rooms and Vehicles • Design Methodology – User-centric Design with HW/SW Co-design; – Formal methods for safe and trustworthy decomposable and reusable components “Fluid”, Network-Centric System Software – Partitioning and management of state between soft and persistent state – Data processing placement and movement – Component discovery and negotiation – Flexible capture, selforganization, and re-use of information 11
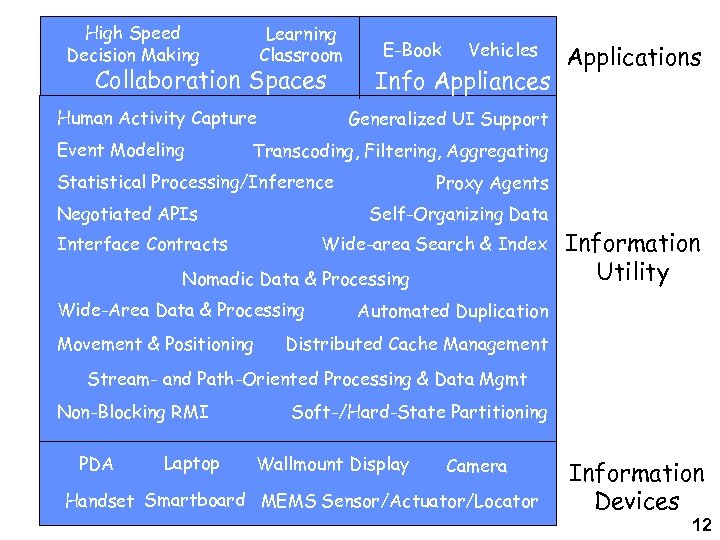 High Speed Decision Making Learning Classroom Collaboration Spaces Human Activity Capture Event Modeling E-Book Vehicles Info Appliances Applications Generalized UI Support Transcoding, Filtering, Aggregating Statistical Processing/Inference Negotiated APIs Proxy Agents Self-Organizing Data Interface Contracts Wide-area Search & Index Nomadic Data & Processing Wide-Area Data & Processing Movement & Positioning Information Utility Automated Duplication Distributed Cache Management Stream- and Path-Oriented Processing & Data Mgmt Non-Blocking RMI PDA Laptop Soft-/Hard-State Partitioning Wallmount Display Camera Handset Smartboard MEMS Sensor/Actuator/Locator Information Devices 12
High Speed Decision Making Learning Classroom Collaboration Spaces Human Activity Capture Event Modeling E-Book Vehicles Info Appliances Applications Generalized UI Support Transcoding, Filtering, Aggregating Statistical Processing/Inference Negotiated APIs Proxy Agents Self-Organizing Data Interface Contracts Wide-area Search & Index Nomadic Data & Processing Wide-Area Data & Processing Movement & Positioning Information Utility Automated Duplication Distributed Cache Management Stream- and Path-Oriented Processing & Data Mgmt Non-Blocking RMI PDA Laptop Soft-/Hard-State Partitioning Wallmount Display Camera Handset Smartboard MEMS Sensor/Actuator/Locator Information Devices 12
 The Endeavournauts: Interdisciplinary, Technology. Centered Expedition Team • • Eric Brewer, OS John Canny, AI David Culler, OS/Arch Michael Franklin, DB Joseph Hellerstein, DB Anthony Joseph, OS Randy Katz, Nets • • John Kubiatowicz, Arch James Landay, UI David Patterson, Arch Kris Pister, Mems Larry Rowe, MM Doug Tygar, Security Robert Wilensky, DL/AI 13
The Endeavournauts: Interdisciplinary, Technology. Centered Expedition Team • • Eric Brewer, OS John Canny, AI David Culler, OS/Arch Michael Franklin, DB Joseph Hellerstein, DB Anthony Joseph, OS Randy Katz, Nets • • John Kubiatowicz, Arch James Landay, UI David Patterson, Arch Kris Pister, Mems Larry Rowe, MM Doug Tygar, Security Robert Wilensky, DL/AI 13
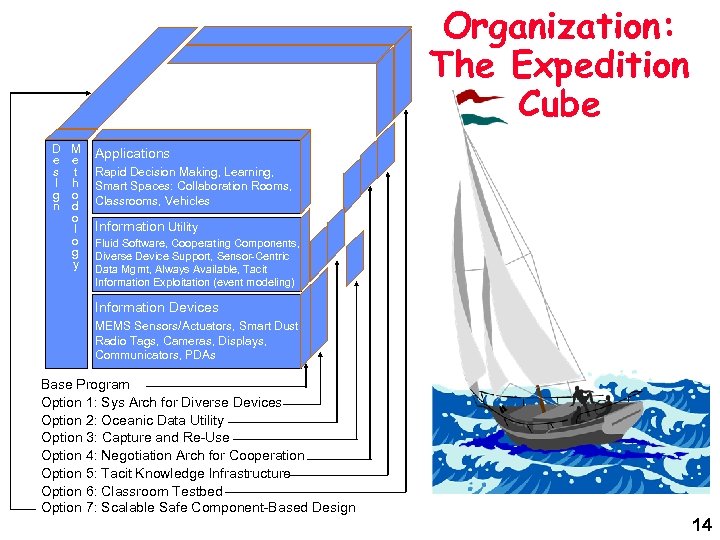 Organization: The Expedition Cube D e s I g n M e t h o d o l o g y Applications Rapid Decision Making, Learning, Smart Spaces: Collaboration Rooms, Classrooms, Vehicles Information Utility Fluid Software, Cooperating Components, Diverse Device Support, Sensor-Centric Data Mgmt, Always Available, Tacit Information Exploitation (event modeling) Information Devices MEMS Sensors/Actuators, Smart Dust, Radio Tags, Cameras, Displays, Communicators, PDAs Base Program Option 1: Sys Arch for Diverse Devices Option 2: Oceanic Data Utility Option 3: Capture and Re-Use Option 4: Negotiation Arch for Cooperation Option 5: Tacit Knowledge Infrastructure Option 6: Classroom Testbed Option 7: Scalable Safe Component-Based Design 14
Organization: The Expedition Cube D e s I g n M e t h o d o l o g y Applications Rapid Decision Making, Learning, Smart Spaces: Collaboration Rooms, Classrooms, Vehicles Information Utility Fluid Software, Cooperating Components, Diverse Device Support, Sensor-Centric Data Mgmt, Always Available, Tacit Information Exploitation (event modeling) Information Devices MEMS Sensors/Actuators, Smart Dust, Radio Tags, Cameras, Displays, Communicators, PDAs Base Program Option 1: Sys Arch for Diverse Devices Option 2: Oceanic Data Utility Option 3: Capture and Re-Use Option 4: Negotiation Arch for Cooperation Option 5: Tacit Knowledge Infrastructure Option 6: Classroom Testbed Option 7: Scalable Safe Component-Based Design 14
 Base Expedition • Broad but necessarily shallow investigation into all technologies/applications of interest – Primary focus on Information Utility » No new HW design: commercially available information devices » Only small-scale testbed in Soda Hall – Fundamental enabling technologies for Fluid Software » Partitioning and management of state between soft and persistent state » Data and processing placement and movement » Component discovery and negotiation » Flexible capture, self-organization, info re-use – Limited Applications – Methodology: Formal Methods & User-Centered Design 15
Base Expedition • Broad but necessarily shallow investigation into all technologies/applications of interest – Primary focus on Information Utility » No new HW design: commercially available information devices » Only small-scale testbed in Soda Hall – Fundamental enabling technologies for Fluid Software » Partitioning and management of state between soft and persistent state » Data and processing placement and movement » Component discovery and negotiation » Flexible capture, self-organization, info re-use – Limited Applications – Methodology: Formal Methods & User-Centered Design 15
 System Architecture for Vastly Diverse Devices • Design Issues for “Small Device OS” – Current: managing address spaces, thread scheduling, IP stack, windowing system, device drivers, file system, APIs, power management – How can OSs for tiny devices be made radically simpler, manageable, and automatically composable? • Devices of Interest: Dust Motes 16
System Architecture for Vastly Diverse Devices • Design Issues for “Small Device OS” – Current: managing address spaces, thread scheduling, IP stack, windowing system, device drivers, file system, APIs, power management – How can OSs for tiny devices be made radically simpler, manageable, and automatically composable? • Devices of Interest: Dust Motes 16
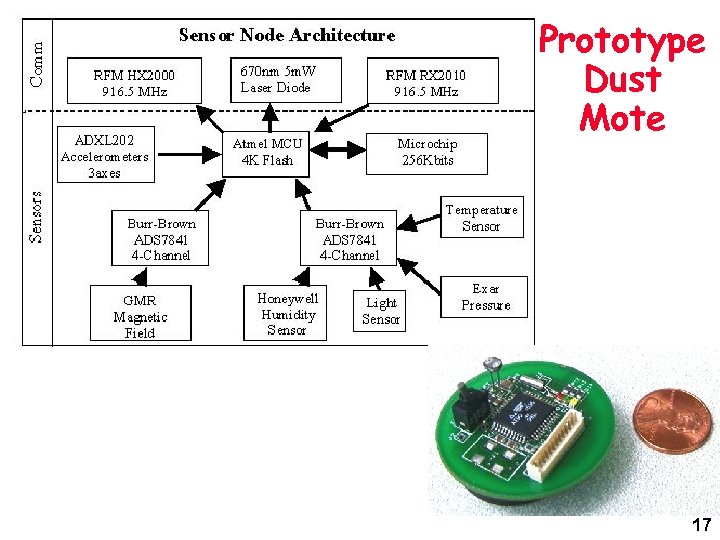 Prototype Dust Mote 17
Prototype Dust Mote 17
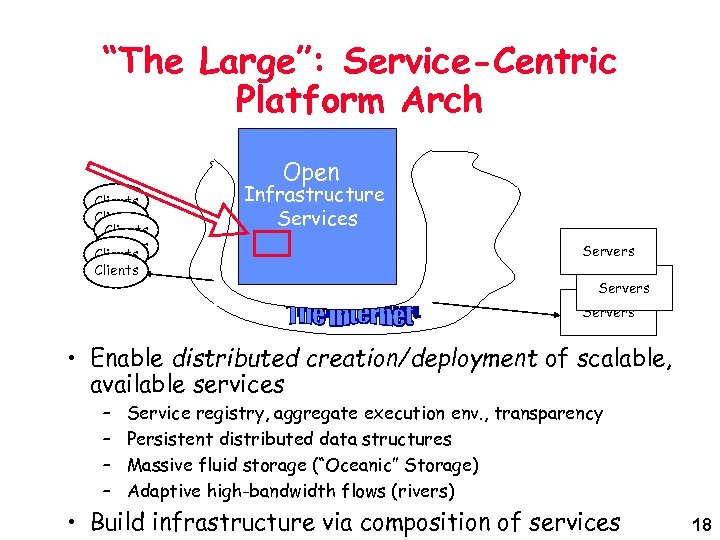 “The Large”: Service-Centric Platform Arch Open Clients Clients Infrastructure Services Servers • Enable distributed creation/deployment of scalable, available services – – Service registry, aggregate execution env. , transparency Persistent distributed data structures Massive fluid storage (“Oceanic” Storage) Adaptive high-bandwidth flows (rivers) • Build infrastructure via composition of services 18
“The Large”: Service-Centric Platform Arch Open Clients Clients Infrastructure Services Servers • Enable distributed creation/deployment of scalable, available services – – Service registry, aggregate execution env. , transparency Persistent distributed data structures Massive fluid storage (“Oceanic” Storage) Adaptive high-bandwidth flows (rivers) • Build infrastructure via composition of services 18
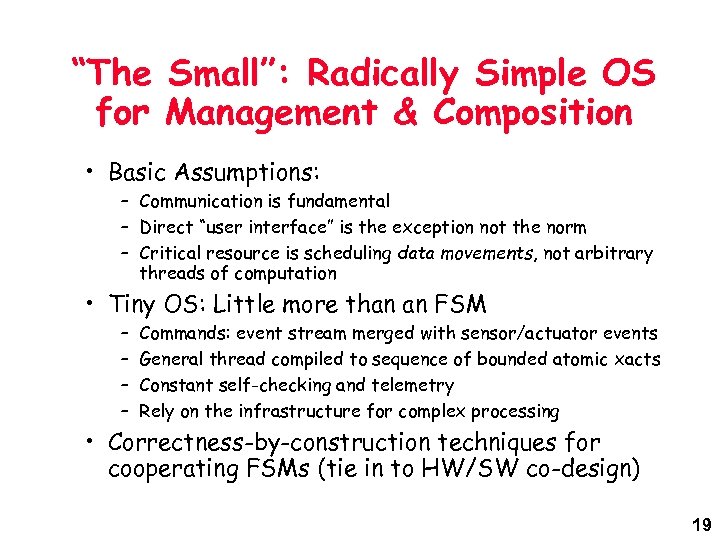 “The Small”: Radically Simple OS for Management & Composition • Basic Assumptions: – Communication is fundamental – Direct “user interface” is the exception not the norm – Critical resource is scheduling data movements, not arbitrary threads of computation • Tiny OS: Little more than an FSM – – Commands: event stream merged with sensor/actuator events General thread compiled to sequence of bounded atomic xacts Constant self-checking and telemetry Rely on the infrastructure for complex processing • Correctness-by-construction techniques for cooperating FSMs (tie in to HW/SW co-design) 19
“The Small”: Radically Simple OS for Management & Composition • Basic Assumptions: – Communication is fundamental – Direct “user interface” is the exception not the norm – Critical resource is scheduling data movements, not arbitrary threads of computation • Tiny OS: Little more than an FSM – – Commands: event stream merged with sensor/actuator events General thread compiled to sequence of bounded atomic xacts Constant self-checking and telemetry Rely on the infrastructure for complex processing • Correctness-by-construction techniques for cooperating FSMs (tie in to HW/SW co-design) 19
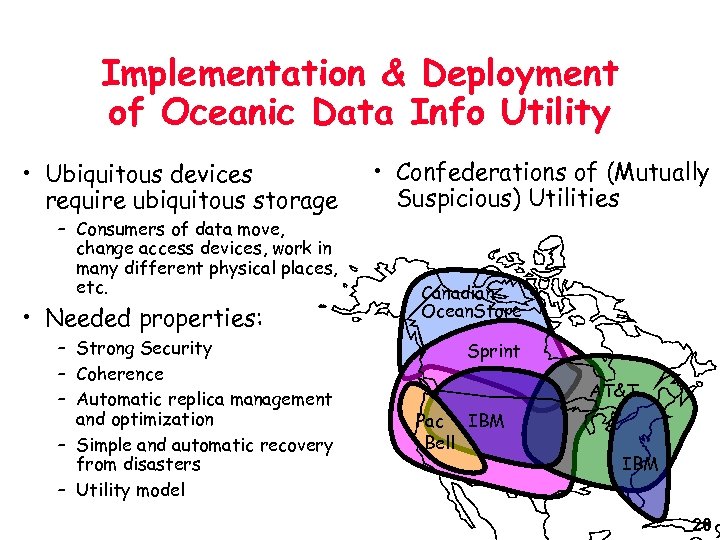 Implementation & Deployment of Oceanic Data Info Utility • Ubiquitous devices require ubiquitous storage – Consumers of data move, change access devices, work in many different physical places, etc. • Needed properties: – Strong Security – Coherence – Automatic replica management and optimization – Simple and automatic recovery from disasters – Utility model • Confederations of (Mutually Suspicious) Utilities Canadian Ocean. Store Sprint AT&T Pac IBM Bell IBM 20
Implementation & Deployment of Oceanic Data Info Utility • Ubiquitous devices require ubiquitous storage – Consumers of data move, change access devices, work in many different physical places, etc. • Needed properties: – Strong Security – Coherence – Automatic replica management and optimization – Simple and automatic recovery from disasters – Utility model • Confederations of (Mutually Suspicious) Utilities Canadian Ocean. Store Sprint AT&T Pac IBM Bell IBM 20
 Ocean. Store Architecture/Technology • Name and Data Location – Issue: Find nearby data without global communication – Approach: Data location is aform of gradient-search of local pools of data (use of attenuated Bloom-filters) • High Availability and Disaster Recovery – Issue: Eliminate backup as independent/fallible technology – Approach: Erasure-codes/mobile replicas provide stable storage for archival copies and snapshots of live data • Introspective Monitoring and Optimization – Issue: Optimize performance on a global scale – Approach: Monitoring and analysis of access/usage relationships • Rapid Update in Untrusted Infrastructure – Issue: Updates should not reveal info to untrusted servers – Approach: Incremental cryptographic techniques/oblivious function techniques to perform update 21
Ocean. Store Architecture/Technology • Name and Data Location – Issue: Find nearby data without global communication – Approach: Data location is aform of gradient-search of local pools of data (use of attenuated Bloom-filters) • High Availability and Disaster Recovery – Issue: Eliminate backup as independent/fallible technology – Approach: Erasure-codes/mobile replicas provide stable storage for archival copies and snapshots of live data • Introspective Monitoring and Optimization – Issue: Optimize performance on a global scale – Approach: Monitoring and analysis of access/usage relationships • Rapid Update in Untrusted Infrastructure – Issue: Updates should not reveal info to untrusted servers – Approach: Incremental cryptographic techniques/oblivious function techniques to perform update 21
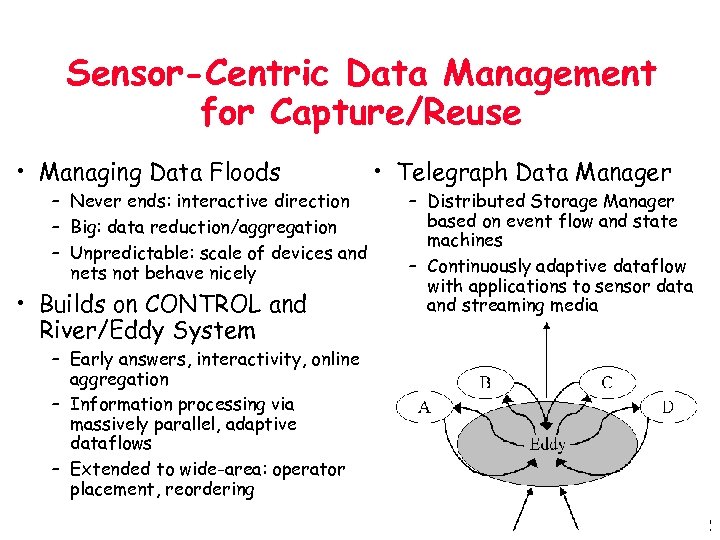 Sensor-Centric Data Management for Capture/Reuse • Managing Data Floods – Never ends: interactive direction – Big: data reduction/aggregation – Unpredictable: scale of devices and nets not behave nicely • Builds on CONTROL and River/Eddy System • Telegraph Data Manager – Distributed Storage Manager based on event flow and state machines – Continuously adaptive dataflow with applications to sensor data and streaming media – Early answers, interactivity, online aggregation – Information processing via massively parallel, adaptive dataflows – Extended to wide-area: operator placement, reordering 22
Sensor-Centric Data Management for Capture/Reuse • Managing Data Floods – Never ends: interactive direction – Big: data reduction/aggregation – Unpredictable: scale of devices and nets not behave nicely • Builds on CONTROL and River/Eddy System • Telegraph Data Manager – Distributed Storage Manager based on event flow and state machines – Continuously adaptive dataflow with applications to sensor data and streaming media – Early answers, interactivity, online aggregation – Information processing via massively parallel, adaptive dataflows – Extended to wide-area: operator placement, reordering 22
 Negotiation Architecture for Cooperating Components • Cooperating Components – Self-administration through auto-discovery and configuration among confederated components – Less brittle/more adaptive systems • Negotiation Architecture – Components announce their needs and services – Service discovery and rendezvous mechanisms to initiate confederations – Negotiated/contractural APIs: contract designing agents – Compliance monitoring/renegotiation/non-compliance recovery – Graceful degradation in response to environmental changes 23
Negotiation Architecture for Cooperating Components • Cooperating Components – Self-administration through auto-discovery and configuration among confederated components – Less brittle/more adaptive systems • Negotiation Architecture – Components announce their needs and services – Service discovery and rendezvous mechanisms to initiate confederations – Negotiated/contractural APIs: contract designing agents – Compliance monitoring/renegotiation/non-compliance recovery – Graceful degradation in response to environmental changes 23
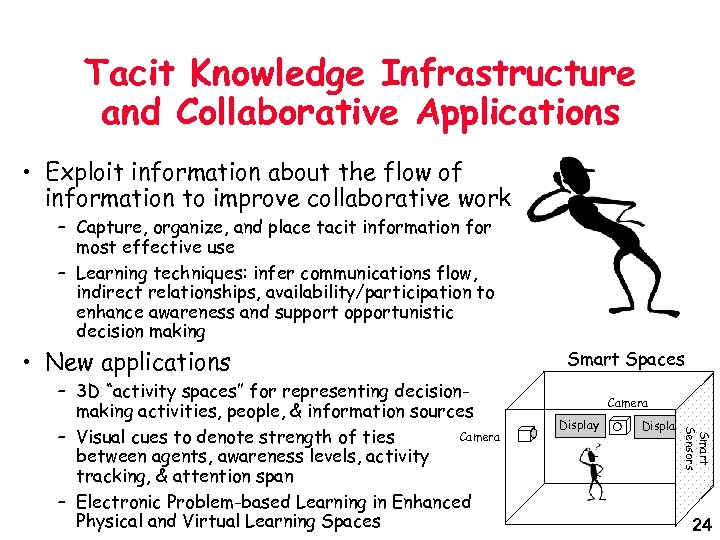 Tacit Knowledge Infrastructure and Collaborative Applications • Exploit information about the flow of information to improve collaborative work – Capture, organize, and place tacit information for most effective use – Learning techniques: infer communications flow, indirect relationships, availability/participation to enhance awareness and support opportunistic decision making • New applications Camera Display Smart Sensors – 3 D “activity spaces” for representing decisionmaking activities, people, & information sources Camera – Visual cues to denote strength of ties between agents, awareness levels, activity tracking, & attention span – Electronic Problem-based Learning in Enhanced Physical and Virtual Learning Spaces Smart Spaces 24
Tacit Knowledge Infrastructure and Collaborative Applications • Exploit information about the flow of information to improve collaborative work – Capture, organize, and place tacit information for most effective use – Learning techniques: infer communications flow, indirect relationships, availability/participation to enhance awareness and support opportunistic decision making • New applications Camera Display Smart Sensors – 3 D “activity spaces” for representing decisionmaking activities, people, & information sources Camera – Visual cues to denote strength of ties between agents, awareness levels, activity tracking, & attention span – Electronic Problem-based Learning in Enhanced Physical and Virtual Learning Spaces Smart Spaces 24
 User Interfaces and Design Tools • Future devices won’t have PC-style UI – Extreme range of devices » Small or embedded in environment » Often w/ “alternative” I/O & w/o screens » Special purpose applications, e. g. , Info Appliances – Lots of devices per user, all working in concert • Key Technologies – Tacit information analysis algorithms – Design tools that integrate » “Sketching” & other low-fidelity techniques » Immediate context & tacit information » Interface models 25
User Interfaces and Design Tools • Future devices won’t have PC-style UI – Extreme range of devices » Small or embedded in environment » Often w/ “alternative” I/O & w/o screens » Special purpose applications, e. g. , Info Appliances – Lots of devices per user, all working in concert • Key Technologies – Tacit information analysis algorithms – Design tools that integrate » “Sketching” & other low-fidelity techniques » Immediate context & tacit information » Interface models 25
 Safe Component Design • Correctness by Construction – Safe partitionings of communicating subcomponents placed in wide-area – Builds on on-going work in embedded systems design • Compositions of Third Party Components – Safety enforcement technologies – Design and development methodologies – Builds on Necula’s Proof Carrying Code • Trust and Assurance – Integrated use of secure tokens for rights management, economic protocols/auctions, support for mobile code, . . . – Secure protocol design & deployment based on super -fast model-checking/automatic generation from requirements 26
Safe Component Design • Correctness by Construction – Safe partitionings of communicating subcomponents placed in wide-area – Builds on on-going work in embedded systems design • Compositions of Third Party Components – Safety enforcement technologies – Design and development methodologies – Builds on Necula’s Proof Carrying Code • Trust and Assurance – Integrated use of secure tokens for rights management, economic protocols/auctions, support for mobile code, . . . – Secure protocol design & deployment based on super -fast model-checking/automatic generation from requirements 26
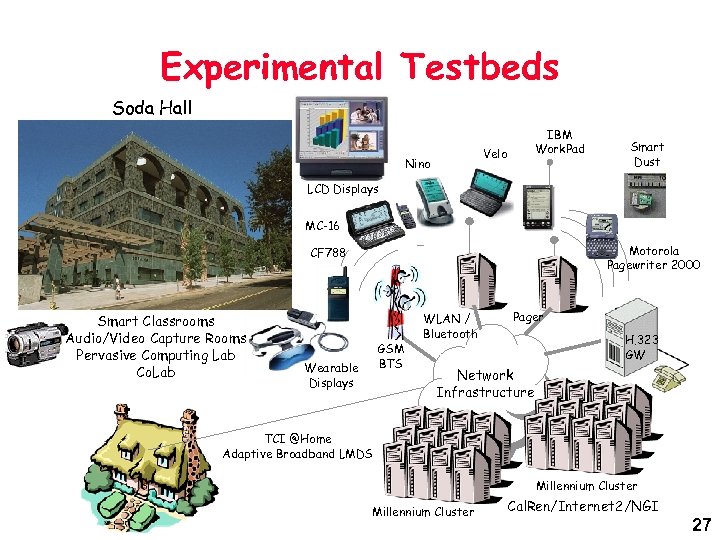 Experimental Testbeds Soda Hall Velo Nino IBM Work. Pad Smart Dust LCD Displays MC-16 Motorola Pagewriter 2000 CF 788 Smart Classrooms Audio/Video Capture Rooms Pervasive Computing Lab Co. Lab GSM BTS Wearable Displays WLAN / Bluetooth Pager H. 323 GW Network Infrastructure TCI @Home Adaptive Broadband LMDS Millennium Cluster Cal. Ren/Internet 2/NGI 27
Experimental Testbeds Soda Hall Velo Nino IBM Work. Pad Smart Dust LCD Displays MC-16 Motorola Pagewriter 2000 CF 788 Smart Classrooms Audio/Video Capture Rooms Pervasive Computing Lab Co. Lab GSM BTS Wearable Displays WLAN / Bluetooth Pager H. 323 GW Network Infrastructure TCI @Home Adaptive Broadband LMDS Millennium Cluster Cal. Ren/Internet 2/NGI 27
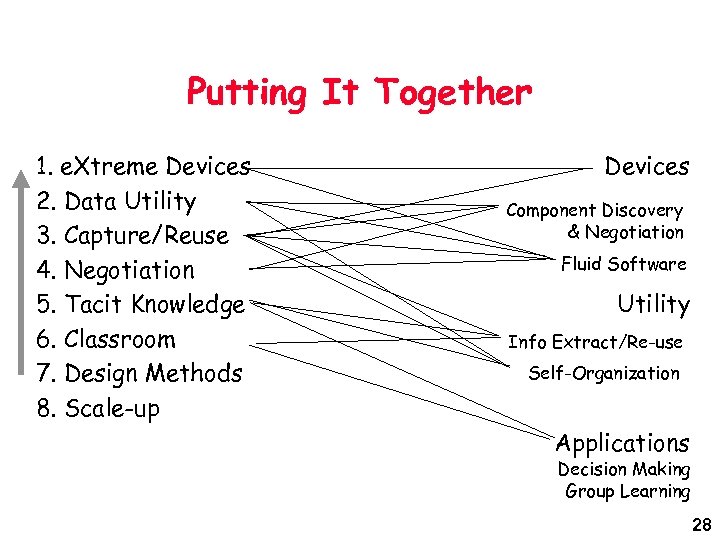 Putting It Together 1. e. Xtreme Devices 2. Data Utility 3. Capture/Reuse 4. Negotiation 5. Tacit Knowledge 6. Classroom 7. Design Methods 8. Scale-up Devices Component Discovery & Negotiation Fluid Software Utility Info Extract/Re-use Self-Organization Applications Decision Making Group Learning 28
Putting It Together 1. e. Xtreme Devices 2. Data Utility 3. Capture/Reuse 4. Negotiation 5. Tacit Knowledge 6. Classroom 7. Design Methods 8. Scale-up Devices Component Discovery & Negotiation Fluid Software Utility Info Extract/Re-use Self-Organization Applications Decision Making Group Learning 28
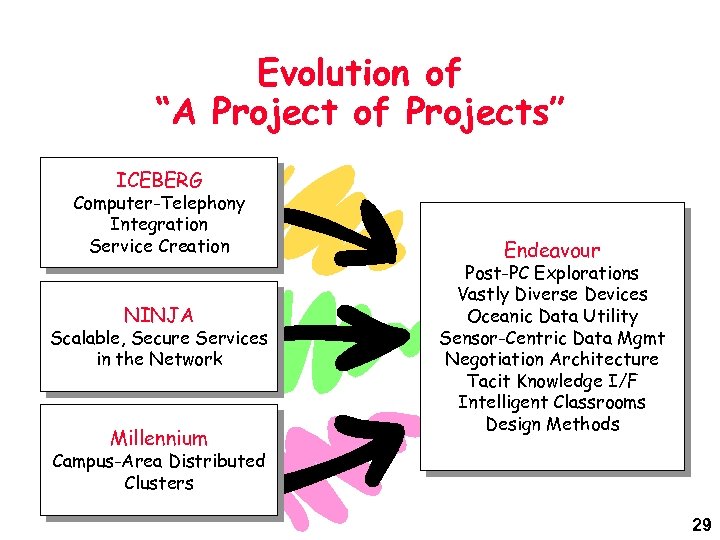 Evolution of “A Project of Projects” ICEBERG Computer-Telephony Integration Service Creation NINJA Scalable, Secure Services in the Network Millennium Endeavour Post-PC Explorations Vastly Diverse Devices Oceanic Data Utility Sensor-Centric Data Mgmt Negotiation Architecture Tacit Knowledge I/F Intelligent Classrooms Design Methods Campus-Area Distributed Clusters 29
Evolution of “A Project of Projects” ICEBERG Computer-Telephony Integration Service Creation NINJA Scalable, Secure Services in the Network Millennium Endeavour Post-PC Explorations Vastly Diverse Devices Oceanic Data Utility Sensor-Centric Data Mgmt Negotiation Architecture Tacit Knowledge I/F Intelligent Classrooms Design Methods Campus-Area Distributed Clusters 29
 Millennium Goals • Enable major advances in Computational Science and Engineering – Simulation, Modeling, and Information Processing becoming ubiquitous • Explore novel design techniques for large, complex systems – Fundamental Computer Science problems ahead are problems of scale – Computational Economy: decentralized resource allocation based on perceived value • Develop fundamentally better ways of assimilating and interacting with large volumes of information – and with each other • Explore emerging technologies – networking, OS, devices 30
Millennium Goals • Enable major advances in Computational Science and Engineering – Simulation, Modeling, and Information Processing becoming ubiquitous • Explore novel design techniques for large, complex systems – Fundamental Computer Science problems ahead are problems of scale – Computational Economy: decentralized resource allocation based on perceived value • Develop fundamentally better ways of assimilating and interacting with large volumes of information – and with each other • Explore emerging technologies – networking, OS, devices 30
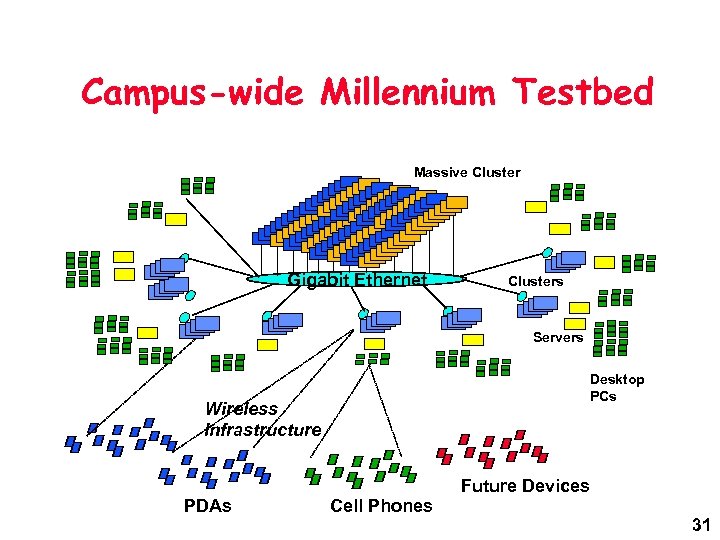 Campus-wide Millennium Testbed Massive Cluster Gigabit Ethernet Clusters Servers Desktop PCs Wireless Infrastructure PDAs Cell Phones Future Devices 31
Campus-wide Millennium Testbed Massive Cluster Gigabit Ethernet Clusters Servers Desktop PCs Wireless Infrastructure PDAs Cell Phones Future Devices 31
 Ninja Goals • Create a framework that enables programmatic generation and composition of services from strongly typed reusable components • Key Elements – Structured architecture with a careful partitioning of state » Bases, Active Proxies, and Units – Wide-area paths formed out of strongly-typed components » Operators and Connectors – Execution environments with efficient, but powerful communication primitives » Active Messages + capsules » TACC + persistence + customization 32
Ninja Goals • Create a framework that enables programmatic generation and composition of services from strongly typed reusable components • Key Elements – Structured architecture with a careful partitioning of state » Bases, Active Proxies, and Units – Wide-area paths formed out of strongly-typed components » Operators and Connectors – Execution environments with efficient, but powerful communication primitives » Active Messages + capsules » TACC + persistence + customization 32
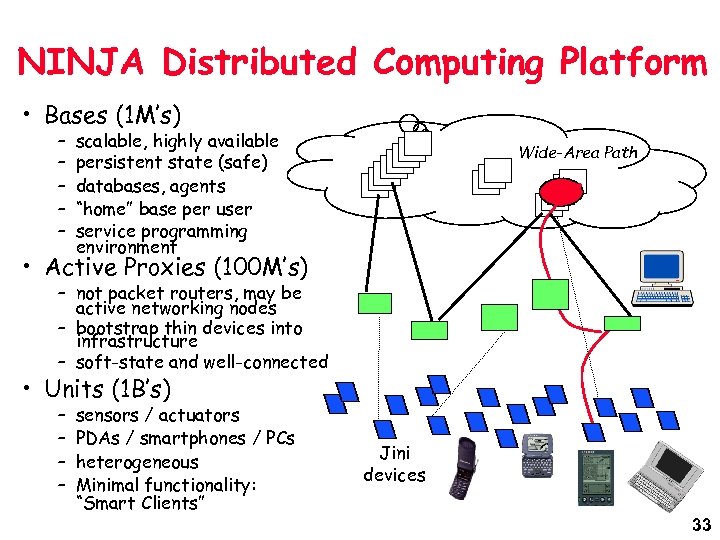 NINJA Distributed Computing Platform • Bases (1 M’s) – – – scalable, highly available persistent state (safe) databases, agents “home” base per user service programming environment Wide-Area Path • Active Proxies (100 M’s) – not packet routers, may be active networking nodes – bootstrap thin devices into infrastructure – soft-state and well-connected • Units (1 B’s) – – sensors / actuators PDAs / smartphones / PCs heterogeneous Minimal functionality: “Smart Clients” Jini devices 33
NINJA Distributed Computing Platform • Bases (1 M’s) – – – scalable, highly available persistent state (safe) databases, agents “home” base per user service programming environment Wide-Area Path • Active Proxies (100 M’s) – not packet routers, may be active networking nodes – bootstrap thin devices into infrastructure – soft-state and well-connected • Units (1 B’s) – – sensors / actuators PDAs / smartphones / PCs heterogeneous Minimal functionality: “Smart Clients” Jini devices 33
 ICEBERG Goals • Demonstrate ease of new service deployment – Packet voice for computer-telephony integration – Speech- and location-enabled applications – Complete interoperation of speech, text, fax/image across the four P’s: PDAs, pads, pagers, phones) – Mobility and generalized routing redirection • Demonstrate new system architecture to support innovative applications – Personal Information Management » Universal In-box: e-mail, news, fax, voice mail » Notification redirection: e. g. , e-mail, pager – Home networking and control of “smart” spaces, sensor/actuator integration » Build on experience with A/V equipped rooms in Soda Hall 34
ICEBERG Goals • Demonstrate ease of new service deployment – Packet voice for computer-telephony integration – Speech- and location-enabled applications – Complete interoperation of speech, text, fax/image across the four P’s: PDAs, pads, pagers, phones) – Mobility and generalized routing redirection • Demonstrate new system architecture to support innovative applications – Personal Information Management » Universal In-box: e-mail, news, fax, voice mail » Notification redirection: e. g. , e-mail, pager – Home networking and control of “smart” spaces, sensor/actuator integration » Build on experience with A/V equipped rooms in Soda Hall 34
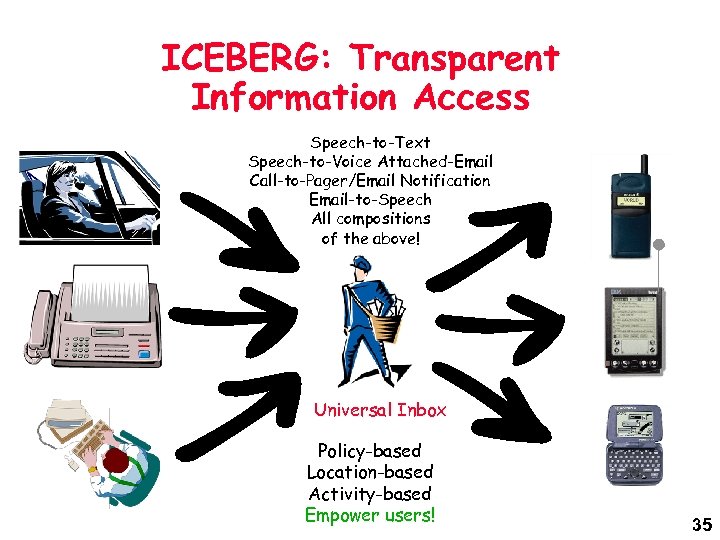 ICEBERG: Transparent Information Access Speech-to-Text Speech-to-Voice Attached-Email Call-to-Pager/Email Notification Email-to-Speech All compositions of the above! Universal Inbox Policy-based Location-based Activity-based Empower users! 35
ICEBERG: Transparent Information Access Speech-to-Text Speech-to-Voice Attached-Email Call-to-Pager/Email Notification Email-to-Speech All compositions of the above! Universal Inbox Policy-based Location-based Activity-based Empower users! 35
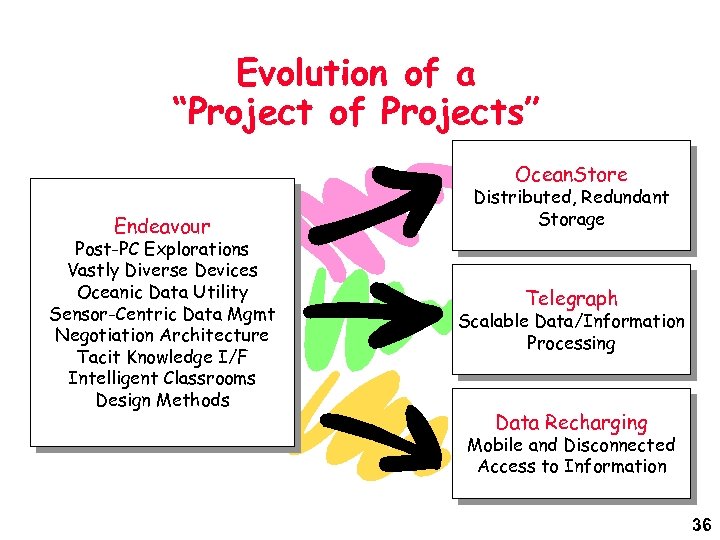 Evolution of a “Project of Projects” Ocean. Store Endeavour Post-PC Explorations Vastly Diverse Devices Oceanic Data Utility Sensor-Centric Data Mgmt Negotiation Architecture Tacit Knowledge I/F Intelligent Classrooms Design Methods Distributed, Redundant Storage Telegraph Scalable Data/Information Processing Data Recharging Mobile and Disconnected Access to Information 36
Evolution of a “Project of Projects” Ocean. Store Endeavour Post-PC Explorations Vastly Diverse Devices Oceanic Data Utility Sensor-Centric Data Mgmt Negotiation Architecture Tacit Knowledge I/F Intelligent Classrooms Design Methods Distributed, Redundant Storage Telegraph Scalable Data/Information Processing Data Recharging Mobile and Disconnected Access to Information 36
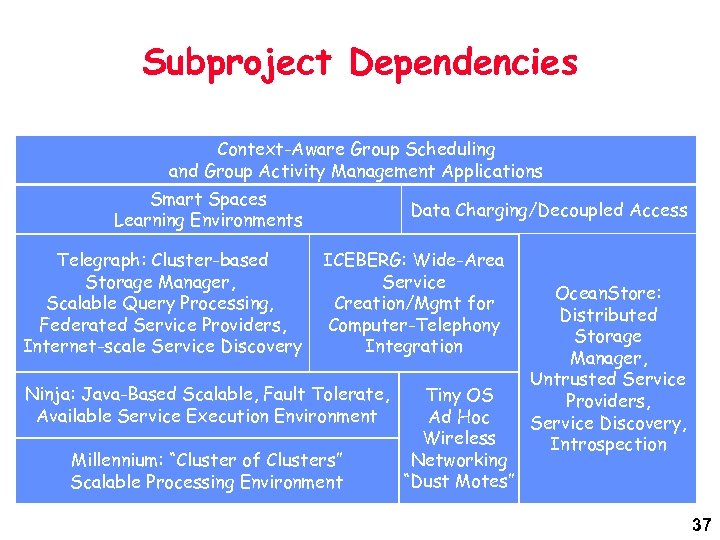 Subproject Dependencies Context-Aware Group Scheduling and Group Activity Management Applications Smart Spaces Learning Environments Telegraph: Cluster-based Storage Manager, Scalable Query Processing, Federated Service Providers, Internet-scale Service Discovery Data Charging/Decoupled Access ICEBERG: Wide-Area Service Creation/Mgmt for Computer-Telephony Integration Ninja: Java-Based Scalable, Fault Tolerate, Available Service Execution Environment Millennium: “Cluster of Clusters” Scalable Processing Environment Tiny OS Ad Hoc Wireless Networking “Dust Motes” Ocean. Store: Distributed Storage Manager, Untrusted Service Providers, Service Discovery, Introspection 37
Subproject Dependencies Context-Aware Group Scheduling and Group Activity Management Applications Smart Spaces Learning Environments Telegraph: Cluster-based Storage Manager, Scalable Query Processing, Federated Service Providers, Internet-scale Service Discovery Data Charging/Decoupled Access ICEBERG: Wide-Area Service Creation/Mgmt for Computer-Telephony Integration Ninja: Java-Based Scalable, Fault Tolerate, Available Service Execution Environment Millennium: “Cluster of Clusters” Scalable Processing Environment Tiny OS Ad Hoc Wireless Networking “Dust Motes” Ocean. Store: Distributed Storage Manager, Untrusted Service Providers, Service Discovery, Introspection 37
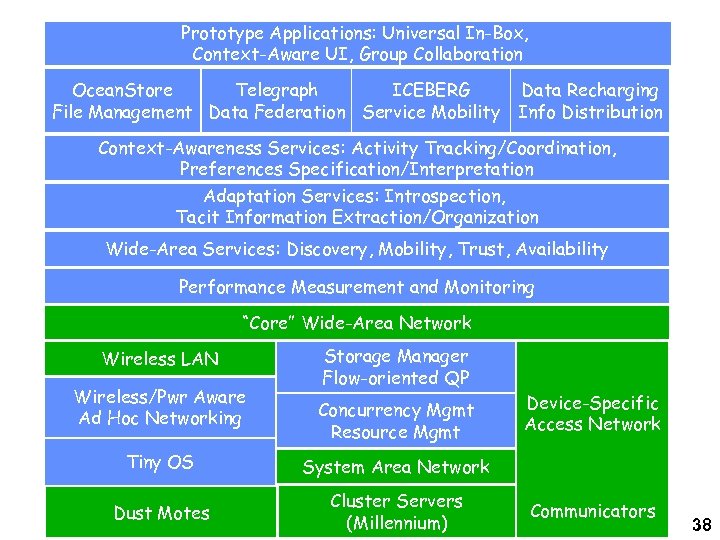 Prototype Applications: Universal In-Box, Context-Aware UI, Group Collaboration Ocean. Store Telegraph ICEBERG Data Recharging File Management Data Federation Service Mobility Info Distribution Context-Awareness Services: Activity Tracking/Coordination, Preferences Specification/Interpretation Adaptation Services: Introspection, Tacit Information Extraction/Organization Wide-Area Services: Discovery, Mobility, Trust, Availability Performance Measurement and Monitoring “Core” Wide-Area Network Wireless LAN Wireless/Pwr Aware Ad Hoc Networking Storage Manager Flow-oriented QP Concurrency Mgmt Resource Mgmt Tiny OS System Area Network Dust Motes Cluster Servers (Millennium) Device-Specific Access Network Communicators 38
Prototype Applications: Universal In-Box, Context-Aware UI, Group Collaboration Ocean. Store Telegraph ICEBERG Data Recharging File Management Data Federation Service Mobility Info Distribution Context-Awareness Services: Activity Tracking/Coordination, Preferences Specification/Interpretation Adaptation Services: Introspection, Tacit Information Extraction/Organization Wide-Area Services: Discovery, Mobility, Trust, Availability Performance Measurement and Monitoring “Core” Wide-Area Network Wireless LAN Wireless/Pwr Aware Ad Hoc Networking Storage Manager Flow-oriented QP Concurrency Mgmt Resource Mgmt Tiny OS System Area Network Dust Motes Cluster Servers (Millennium) Device-Specific Access Network Communicators 38
 Summary and Conclusions • 21 st Century Computing – Making people’s exploitation of information more effective – Encompassing e. Xtreme diversity, distribution, and scale – Computing you can depend on • Key Support Technologies – – – “Fluid software” computational paradigms System and UI support for e. Xtreme devices Pervasive, planetary-scale system utility functionality Active, adaptive, safe and trusted components New “power tool” applications that leverage community activity • Broad multidisciplinary team spanning the needed applications, evaluation, and system technology skills – Culture of large-scale, industry-relevant high impact research projects 39
Summary and Conclusions • 21 st Century Computing – Making people’s exploitation of information more effective – Encompassing e. Xtreme diversity, distribution, and scale – Computing you can depend on • Key Support Technologies – – – “Fluid software” computational paradigms System and UI support for e. Xtreme devices Pervasive, planetary-scale system utility functionality Active, adaptive, safe and trusted components New “power tool” applications that leverage community activity • Broad multidisciplinary team spanning the needed applications, evaluation, and system technology skills – Culture of large-scale, industry-relevant high impact research projects 39
 Summary and Conclusions • Emerging Network-centric Distributed Architecture spanning processing and access • Open, composable services architecture--the wide-area “operating system” of the 21 st Century • Beyond the desktop PC: information appliances supported by infrastructure services--multicast realtime media plus proxies for any-to-any format translation and delivery to diverse devices • Common network core: optimized for data, based on IP, enabling packetized voice, supporting user, terminal, and service mobility • New capability and applications focus: MEMS devices, sensor applications, smart spaces, tacit info extraction 40
Summary and Conclusions • Emerging Network-centric Distributed Architecture spanning processing and access • Open, composable services architecture--the wide-area “operating system” of the 21 st Century • Beyond the desktop PC: information appliances supported by infrastructure services--multicast realtime media plus proxies for any-to-any format translation and delivery to diverse devices • Common network core: optimized for data, based on IP, enabling packetized voice, supporting user, terminal, and service mobility • New capability and applications focus: MEMS devices, sensor applications, smart spaces, tacit info extraction 40


