724f9977de74ca3188c06069cf52d8f8.ppt
- Количество слайдов: 29

The Empowered Branch Webinar Deploying Secure Unified Communications in Branch Networks Christina Hattingh, Technical Marketing Engineer Shashi Kiran, Manager, Network Systems Marketing Presentation_ID © 2007 Cisco Systems, Inc. All rights reserved. Cisco Confidential 1
Agenda Changing Traffic Patterns and models The Secure UC Framework Securing UC in the Branch or Small Office Security Capabilities on the Cisco Integrated Services Router § Cisco Unified Communications Voice Gateways § Cisco Survivable Remote Site Telephony (SRST) § Cisco Unified Communications Manager Express (CME) Summary © 2007 Cisco Systems, Inc. All rights reserved. Cisco Confidential 2
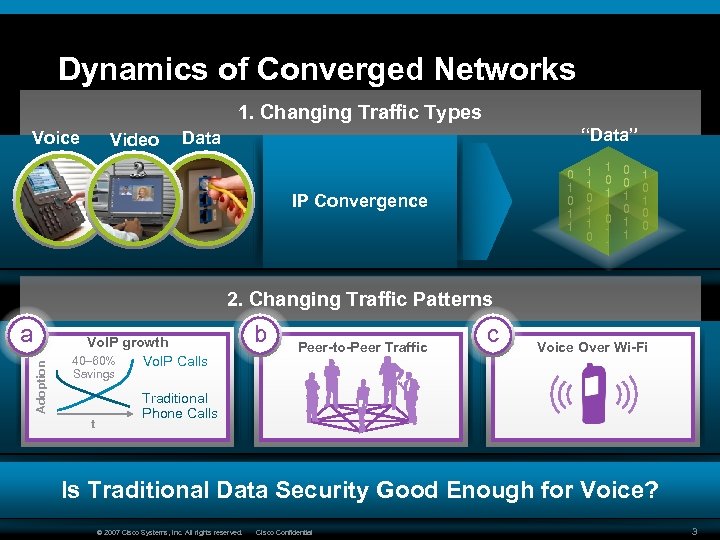
Dynamics of Converged Networks 1. Changing Traffic Types Voice Video “Data” Data 0 1 1 IP Convergence 1 1 0 1 0 1 1 0 0 1 1 1 0 0 2. Changing Traffic Patterns Adoption a Vo. IP growth 40– 60% Vo. IP Calls b Peer-to-Peer Traffic c Voice Over Wi-Fi Savings t Traditional Phone Calls Is Traditional Data Security Good Enough for Voice? © 2007 Cisco Systems, Inc. All rights reserved. Cisco Confidential 3
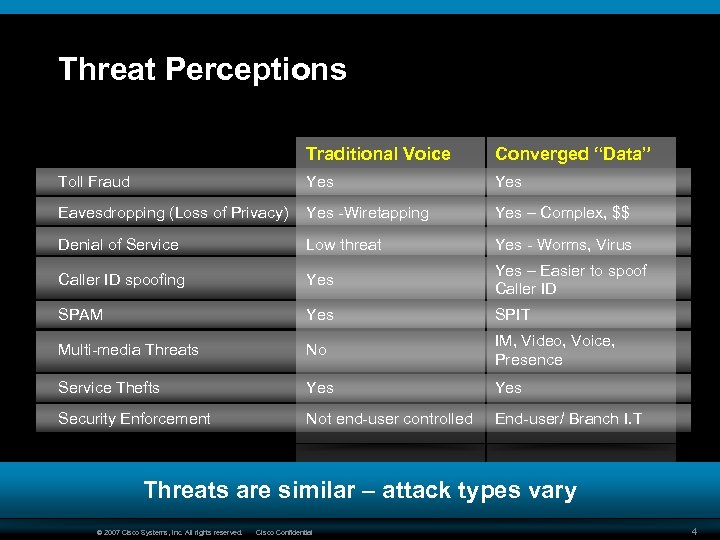
Threat Perceptions Traditional Voice Converged “Data” Toll Fraud Yes Eavesdropping (Loss of Privacy) Yes -Wiretapping Yes – Complex, $$ Denial of Service Low threat Yes - Worms, Virus Caller ID spoofing Yes – Easier to spoof Caller ID SPAM Yes SPIT Multi-media Threats No IM, Video, Voice, Presence Service Thefts Yes Security Enforcement Not end-user controlled End-user/ Branch I. T Threats are similar – attack types vary © 2007 Cisco Systems, Inc. All rights reserved. Cisco Confidential 4
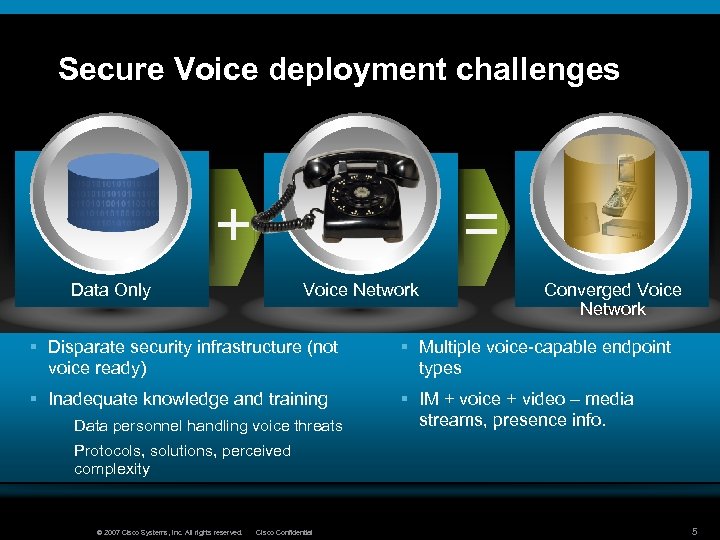
Secure Voice deployment challenges = + Data Only Voice Network Converged Voice Network § Disparate security infrastructure (not voice ready) § Multiple voice-capable endpoint types § Inadequate knowledge and training § IM + voice + video – media streams, presence info. Data personnel handling voice threats Protocols, solutions, perceived complexity © 2007 Cisco Systems, Inc. All rights reserved. Cisco Confidential 5
Secure Unified Communications Secure Telephony Secure Network Secure Unified Communication © 2007 Cisco Systems, Inc. All rights reserved. Cisco Confidential 6
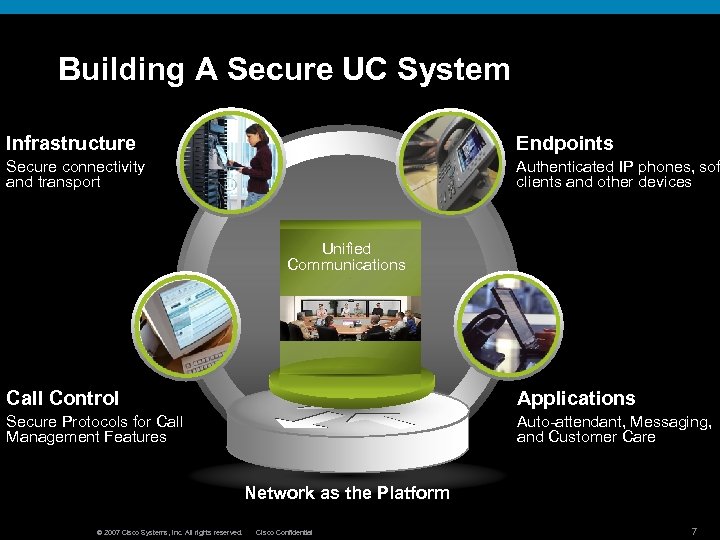
Building A Secure UC System Infrastructure Endpoints Secure connectivity and transport Authenticated IP phones, sof clients and other devices Unified Communications Call Control Applications Secure Protocols for Call Management Features Auto-attendant, Messaging, and Customer Care Network as the Platform © 2007 Cisco Systems, Inc. All rights reserved. Cisco Confidential 7

Determining Security Policy High Banking § Don’t make security an end to itself—determine the security level needed § Rank voice with all data on the network by your business requirements § Evaluate whether your existing data security policy is sufficient for voice Oracle Trading Billing POS Voice, Video Web Traffic E-Mail Directory Low © 2007 Cisco Systems, Inc. All rights reserved. Cisco Confidential 8
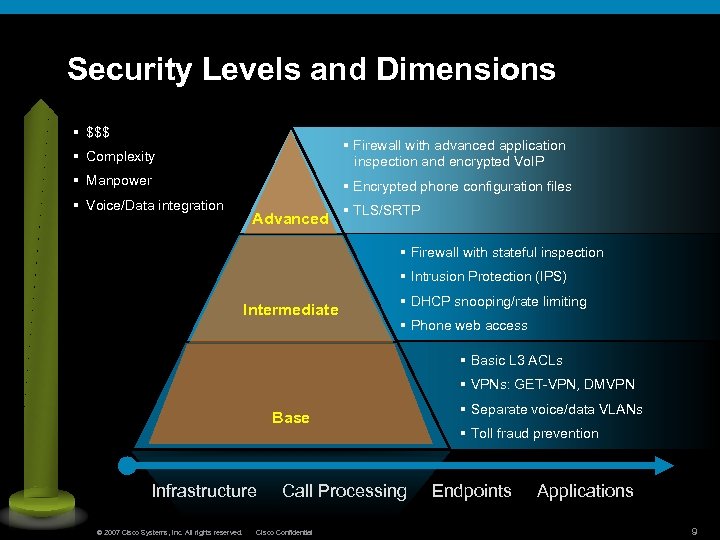
Security Levels and Dimensions § $$$ § Complexity § Firewall with advanced application inspection and encrypted Vo. IP § Manpower § Encrypted phone configuration files § Voice/Data integration Advanced § TLS/SRTP § Firewall with stateful inspection § Intrusion Protection (IPS) Intermediate § DHCP snooping/rate limiting § Phone web access § Basic L 3 ACLs § VPNs: GET-VPN, DMVPN Base Infrastructure © 2007 Cisco Systems, Inc. All rights reserved. Call Processing Cisco Confidential § Separate voice/data VLANs § Toll fraud prevention Endpoints Applications 9
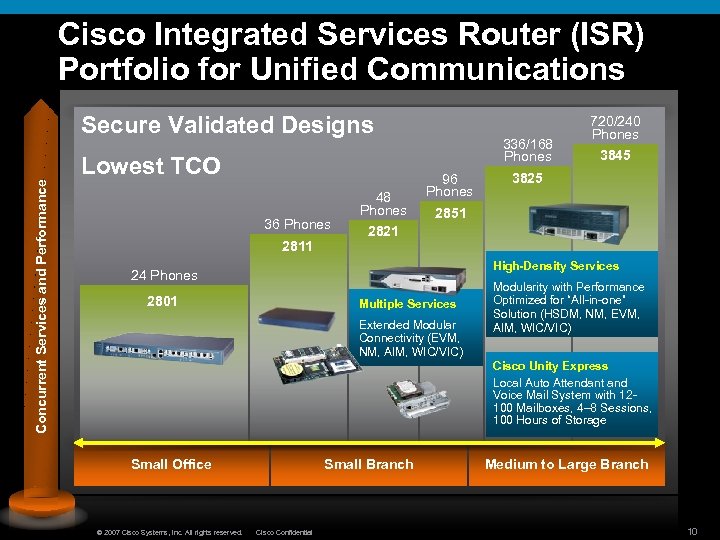
Cisco Integrated Services Router (ISR) Portfolio for Unified Communications Concurrent Services and Performance Secure Validated Designs Lowest TCO 36 Phones 2811 48 Phones 336/168 Phones 96 Phones 720/240 Phones 3845 3825 2851 2821 High-Density Services 24 Phones 2801 Multiple Services Extended Modular Connectivity (EVM, NM, AIM, WIC/VIC) Modularity with Performance Optimized for “All-in-one” Solution (HSDM, NM, EVM, AIM, WIC/VIC) Cisco Unity Express Local Auto Attendant and Voice Mail System with 12100 Mailboxes, 4– 8 Sessions, 100 Hours of Storage Small Office © 2007 Cisco Systems, Inc. All rights reserved. Small Branch Cisco Confidential Medium to Large Branch 10
Securing UC in the Branch or Small Office Presentation_ID © 2007 Cisco Systems, Inc. All rights reserved. Cisco Confidential 11
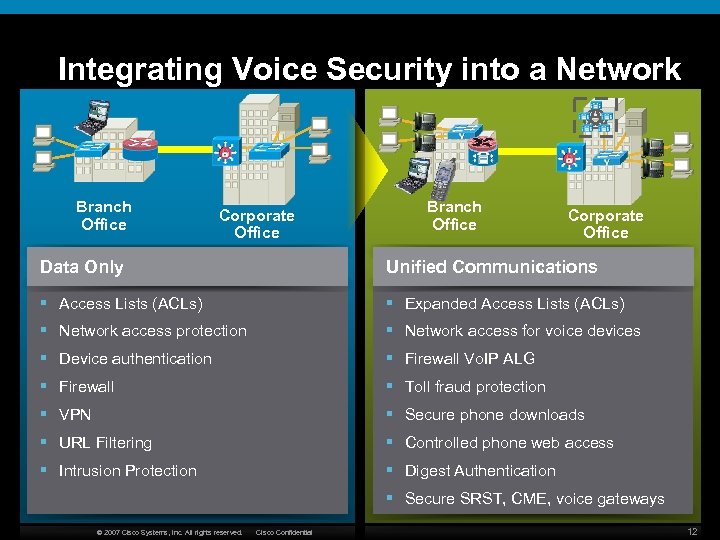
Integrating Voice Security into a Network Branch Office Corporate Office Data Only Unified Communications § Access Lists (ACLs) § Expanded Access Lists (ACLs) § Network access protection § Network access for voice devices § Device authentication § Firewall Vo. IP ALG § Firewall § Toll fraud protection § VPN § Secure phone downloads § URL Filtering § Controlled phone web access § Intrusion Protection § Digest Authentication § Secure SRST, CME, voice gateways © 2007 Cisco Systems, Inc. All rights reserved. Cisco Confidential 12
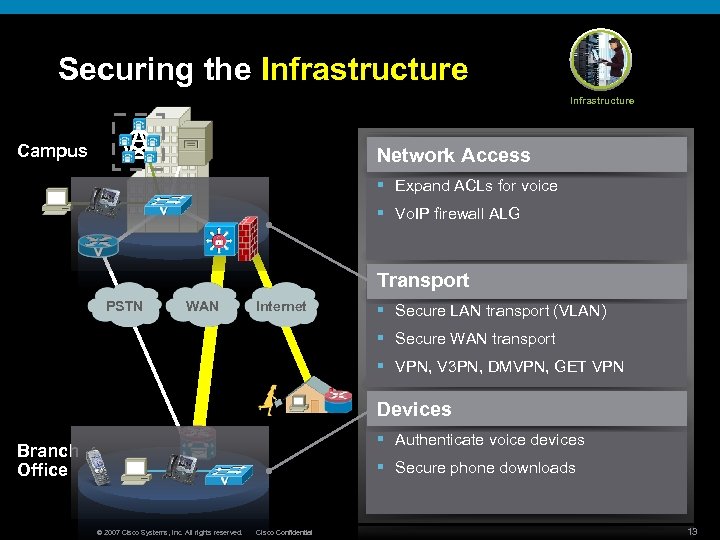
Securing the Infrastructure A Campus Network Access § Expand ACLs for voice § Vo. IP firewall ALG Transport PSTN WAN Internet § Secure LAN transport (VLAN) § Secure WAN transport § VPN, V 3 PN, DMVPN, GET VPN Devices § Authenticate voice devices Branch Office § Secure phone downloads © 2007 Cisco Systems, Inc. All rights reserved. Cisco Confidential 13
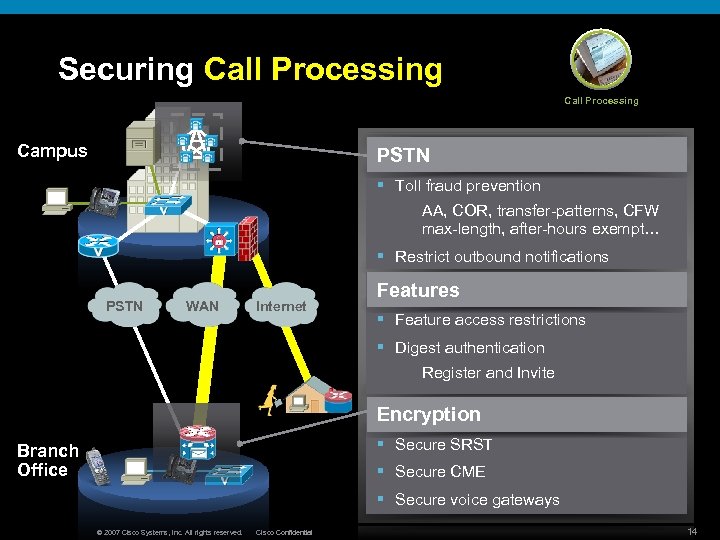
Securing Call Processing A Campus PSTN § Toll fraud prevention AA, COR, transfer-patterns, CFW max-length, after-hours exempt… § Restrict outbound notifications PSTN WAN Internet Features § Feature access restrictions § Digest authentication Register and Invite Encryption § Secure SRST Branch Office § Secure CME § Secure voice gateways © 2007 Cisco Systems, Inc. All rights reserved. Cisco Confidential 14
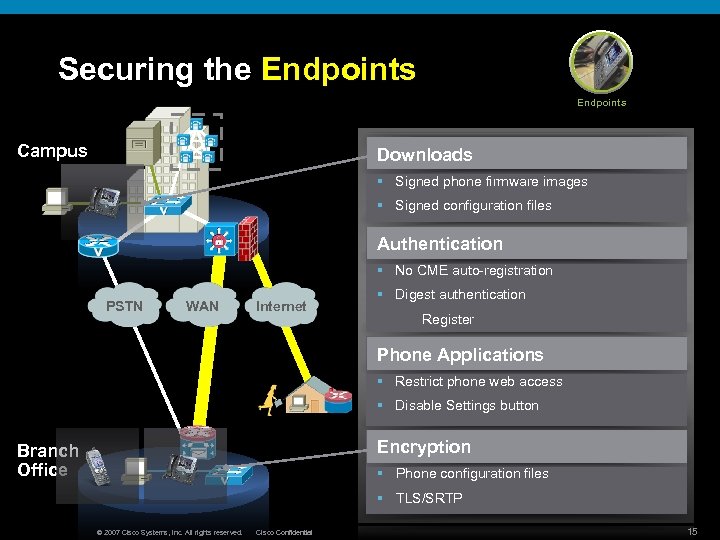
Securing the Endpoints A Campus Downloads § Signed phone firmware images § Signed configuration files Authentication § No CME auto-registration PSTN WAN Internet § Digest authentication Register Phone Applications § Restrict phone web access § Disable Settings button Encryption Branch Office § Phone configuration files § TLS/SRTP © 2007 Cisco Systems, Inc. All rights reserved. Cisco Confidential 15
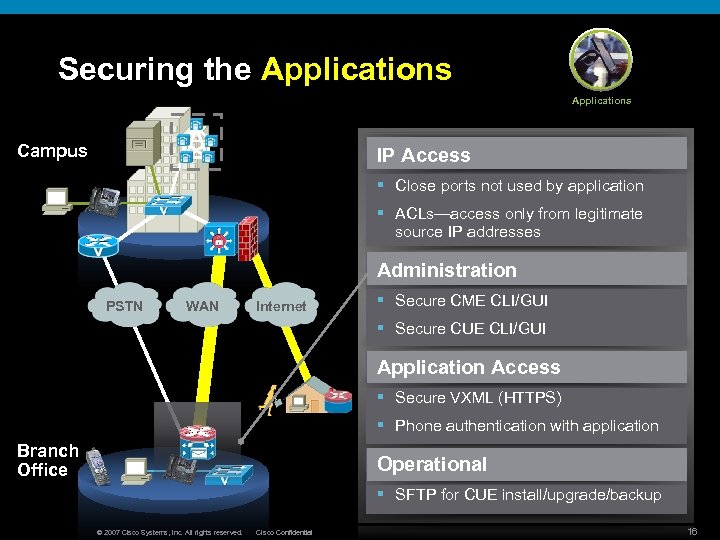
Securing the Applications A Campus IP Access § Close ports not used by application § ACLs—access only from legitimate source IP addresses Administration PSTN WAN Internet § Secure CME CLI/GUI § Secure CUE CLI/GUI Application Access § Secure VXML (HTTPS) § Phone authentication with application Branch Office Operational § SFTP for CUE install/upgrade/backup © 2007 Cisco Systems, Inc. All rights reserved. Cisco Confidential 16

Secure UC capabilities on the Cisco Integrated Services Router © 2007 Cisco Systems, Inc. All rights reserved. Cisco Confidential 17
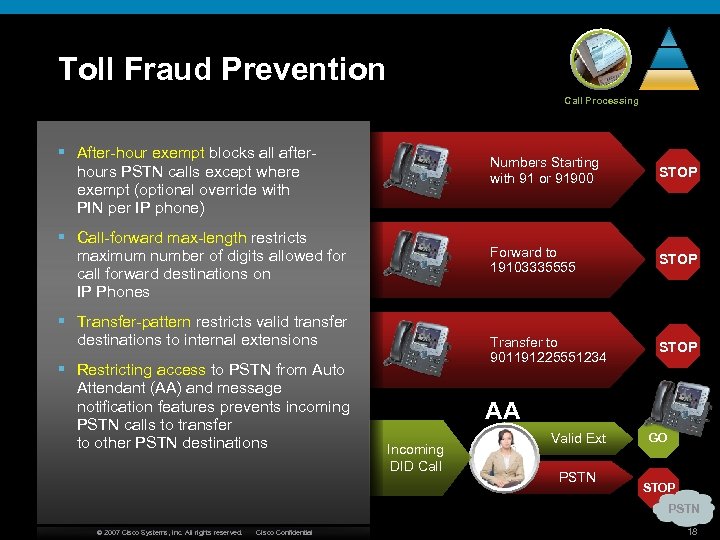
Toll Fraud Prevention Call Processing § After-hour exempt blocks all afterhours PSTN calls except where exempt (optional override with PIN per IP phone) Numbers Starting with 91 or 91900 Forward to 19103335555 § Transfer-pattern restricts valid transfer destinations to internal extensions § Restricting access to PSTN from Auto Attendant (AA) and message notification features prevents incoming PSTN calls to transfer to other PSTN destinations STOP Transfer to 901191225551234 § Call-forward max-length restricts maximum number of digits allowed for call forward destinations on IP Phones STOP AA Incoming DID Call Valid Ext PSTN GO STOP PSTN © 2007 Cisco Systems, Inc. All rights reserved. Cisco Confidential 18
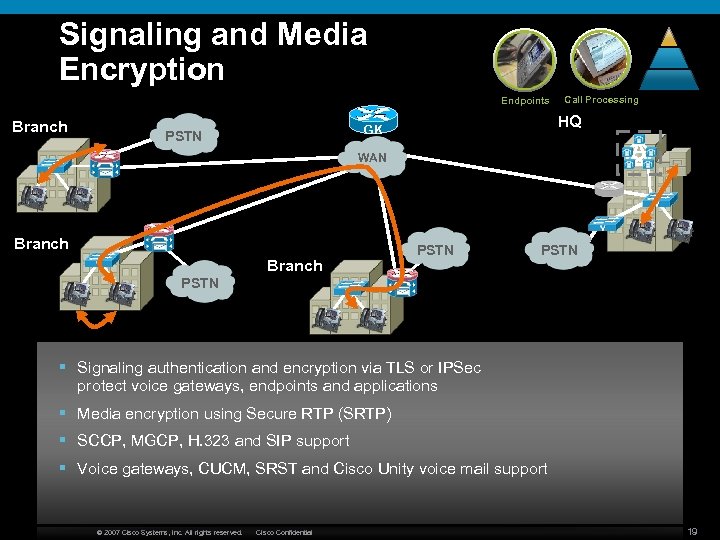
Signaling and Media Encryption Endpoints Branch HQ GK PSTN Call Processing A WAN Branch PSTN § Signaling authentication and encryption via TLS or IPSec protect voice gateways, endpoints and applications § Media encryption using Secure RTP (SRTP) § SCCP, MGCP, H. 323 and SIP support § Voice gateways, CUCM, SRST and Cisco Unity voice mail support © 2007 Cisco Systems, Inc. All rights reserved. Cisco Confidential 19
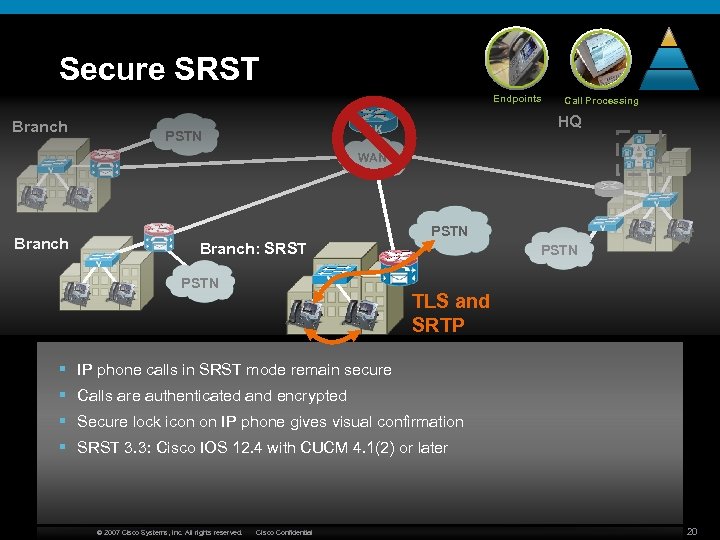
Secure SRST Endpoints Branch HQ GK PSTN Call Processing A WAN Branch PSTN Branch: SRST PSTN TLS and SRTP § IP phone calls in SRST mode remain secure § Calls are authenticated and encrypted § Secure lock icon on IP phone gives visual confirmation § SRST 3. 3: Cisco IOS 12. 4 with CUCM 4. 1(2) or later © 2007 Cisco Systems, Inc. All rights reserved. Cisco Confidential 20
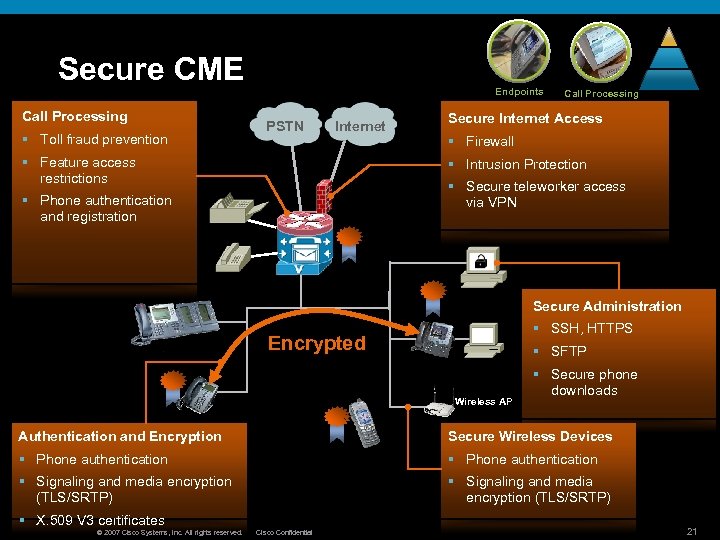
Secure CME Call Processing § Toll fraud prevention Endpoints PSTN Internet § Feature access restrictions Call Processing Secure Internet Access § Firewall § Intrusion Protection § Secure teleworker access via VPN § Phone authentication and registration Secure Administration § SSH, HTTPS Encrypted § SFTP Wireless AP § Secure phone downloads Authentication and Encryption Secure Wireless Devices § Phone authentication § Signaling and media encryption (TLS/SRTP) § X. 509 V 3 certificates © 2007 Cisco Systems, Inc. All rights reserved. Cisco Confidential 21
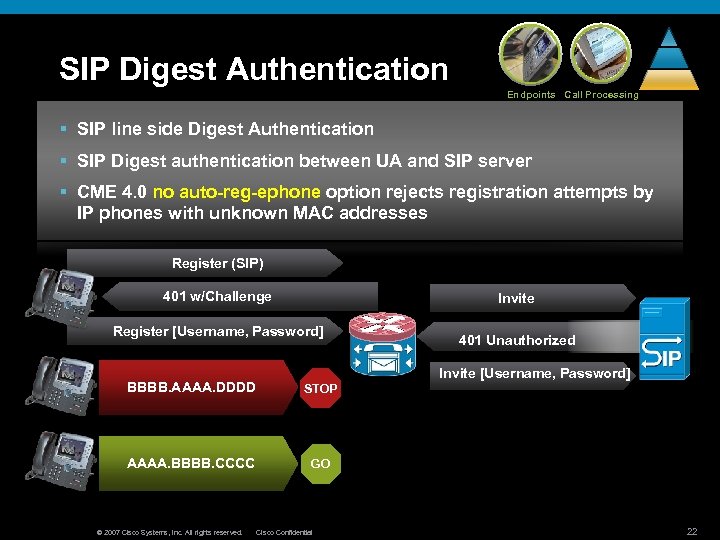
SIP Digest Authentication Endpoints Call Processing § SIP line side Digest Authentication § SIP Digest authentication between UA and SIP server § CME 4. 0 no auto-reg-ephone option rejects registration attempts by IP phones with unknown MAC addresses Register (SIP) 401 w/Challenge Invite Register [Username, Password] 401 Unauthorized Invite [Username, Password] BBBB. AAAA. DDDD STOP AAAA. BBBB. CCCC GO © 2007 Cisco Systems, Inc. All rights reserved. Cisco Confidential 22
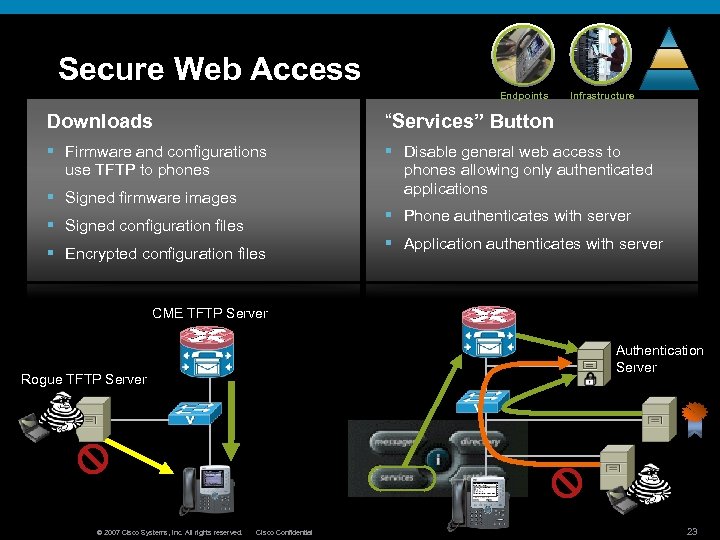
Secure Web Access Endpoints Infrastructure Downloads “Services” Button § Firmware and configurations use TFTP to phones § Disable general web access to phones allowing only authenticated applications § Signed firmware images § Phone authenticates with server § Signed configuration files § Encrypted configuration files § Application authenticates with server CME TFTP Server Authentication Server Rogue TFTP Server © 2007 Cisco Systems, Inc. All rights reserved. Cisco Confidential 23
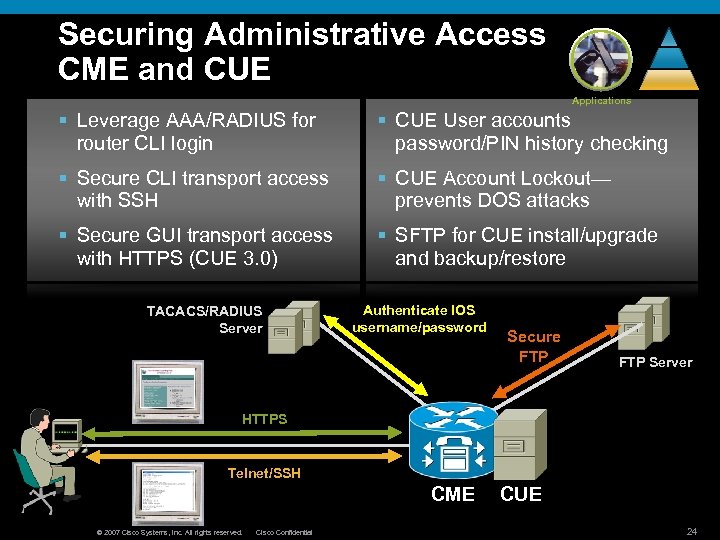
Securing Administrative Access CME and CUE Applications § Leverage AAA/RADIUS for router CLI login § CUE User accounts password/PIN history checking § Secure CLI transport access with SSH § CUE Account Lockout— prevents DOS attacks § Secure GUI transport access with HTTPS (CUE 3. 0) § SFTP for CUE install/upgrade and backup/restore TACACS/RADIUS Server Authenticate IOS username/password Secure FTP Server HTTPS Telnet/SSH CME © 2007 Cisco Systems, Inc. All rights reserved. Cisco Confidential CUE 24
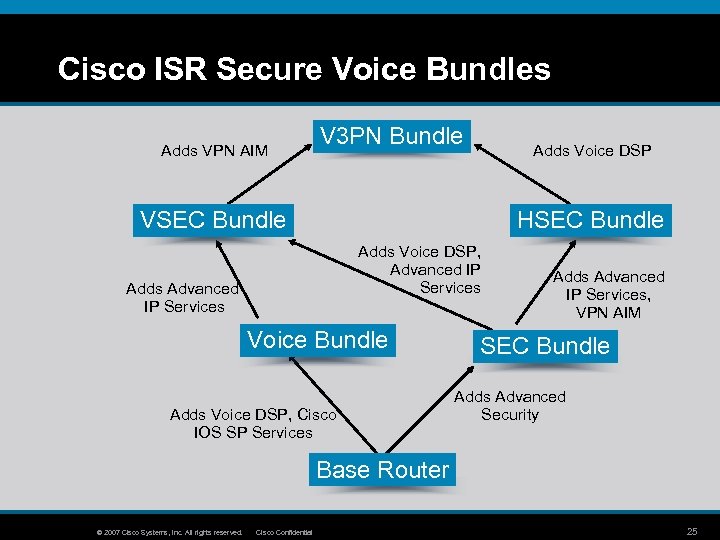
Cisco ISR Secure Voice Bundles Adds VPN AIM V 3 PN Bundle Adds Voice DSP VSEC Bundle HSEC Bundle Adds Voice DSP, Advanced IP Services Adds Advanced IP Services Voice Bundle Adds Voice DSP, Cisco IOS SP Services Adds Advanced IP Services, VPN AIM SEC Bundle Adds Advanced Security Base Router © 2007 Cisco Systems, Inc. All rights reserved. Cisco Confidential 25

Summary Align Voice and Data Security Policies; Secure UC Requires Incremental Voice-specific Features Build a Layered, Tolerant Security Model; The Cisco Secure UC With the Cisco ISR Offers Multi -layered Protection Balance Risk Avoidance, Cost and Performance © 2007 Cisco Systems, Inc. All rights reserved. Cisco Confidential 26

Resources Cisco. com/go/ipc Cisco. com/go/isr Cisco. com/go/ipcsecurity Cisco. com/go/cube Cisco. com/go/netpro © 2007 Cisco Systems, Inc. All rights reserved. Cisco Confidential 27

Q&A © 2007 Cisco Systems, Inc. All rights reserved. Cisco Confidential 28

© 2007 Cisco Systems, Inc. All rights reserved. Cisco Confidential 29
724f9977de74ca3188c06069cf52d8f8.ppt