ae2902c332b39b90966f3ee70cc45a26.ppt
- Количество слайдов: 13
 The E-Authentication Initiative E-Authentication: The Need for Open-Standards in Implementing E-Government October 6, 2004
The E-Authentication Initiative E-Authentication: The Need for Open-Standards in Implementing E-Government October 6, 2004
 The E-Authentication Initiative E-Government Strategy: Improving Service for Citizens Government to Citizen Managing Partner 1. 2. 3. 4. 5. GSA Treas Do. Ed DOI DOL USA Service IRS Free File E-Loans Recreation One Stop Gov. Benefits Government to Business Managing Partner 1. Federal Asset Sales 2. Online Rulemaking Mgmt 3. Expanding Tax Products for Businesses 4. Consolidated Health Informatics 5. Business Gateway 6. International Trade Process Streamlining GSA EPA Treas HHS SBA DOC E-Authentication Government to Government Managing Partner 1. 2. 3. 4. E-Vital Grants. gov Disaster Mgmt Geospatial One Stop 5. SAFECOM SSA HHS FEMA DOI FEMA Internal Effectiveness & Efficiency Managing Partner 1. 2. 3. 4. 5. 6. 7. 8. E-Training Recruitment One Stop Enterprise HR Integration E-Clearance E-Travel Integrated Acquisition E-Records Management Payroll/HR OPM OPM GSA NARA OPM 2
The E-Authentication Initiative E-Government Strategy: Improving Service for Citizens Government to Citizen Managing Partner 1. 2. 3. 4. 5. GSA Treas Do. Ed DOI DOL USA Service IRS Free File E-Loans Recreation One Stop Gov. Benefits Government to Business Managing Partner 1. Federal Asset Sales 2. Online Rulemaking Mgmt 3. Expanding Tax Products for Businesses 4. Consolidated Health Informatics 5. Business Gateway 6. International Trade Process Streamlining GSA EPA Treas HHS SBA DOC E-Authentication Government to Government Managing Partner 1. 2. 3. 4. E-Vital Grants. gov Disaster Mgmt Geospatial One Stop 5. SAFECOM SSA HHS FEMA DOI FEMA Internal Effectiveness & Efficiency Managing Partner 1. 2. 3. 4. 5. 6. 7. 8. E-Training Recruitment One Stop Enterprise HR Integration E-Clearance E-Travel Integrated Acquisition E-Records Management Payroll/HR OPM OPM GSA NARA OPM 2
 The E-Authentication Initiative What is the E-Authentication Initiative? u E-Authentication provides a blueprint for online identity validation that will enable the American public to access government services in a secure, trusted environment with credentials of their choosing E-Authentication Enables E-Government 3
The E-Authentication Initiative What is the E-Authentication Initiative? u E-Authentication provides a blueprint for online identity validation that will enable the American public to access government services in a secure, trusted environment with credentials of their choosing E-Authentication Enables E-Government 3
 The E-Authentication Initiative What are the Goals of the Initiative? u Build and enable mutual trust needed to support wide-spread use of electronic interactions between the public and Government u Minimize the burden on the public when obtaining trusted electronic services from the Government u Deliver common interoperable authentication solutions, appropriately matching the levels of risk and business needs The Result: Businesses & individuals will be empowered to conduct business with Government at all levels using e-identity credentials provided by trusted institutions 4
The E-Authentication Initiative What are the Goals of the Initiative? u Build and enable mutual trust needed to support wide-spread use of electronic interactions between the public and Government u Minimize the burden on the public when obtaining trusted electronic services from the Government u Deliver common interoperable authentication solutions, appropriately matching the levels of risk and business needs The Result: Businesses & individuals will be empowered to conduct business with Government at all levels using e-identity credentials provided by trusted institutions 4
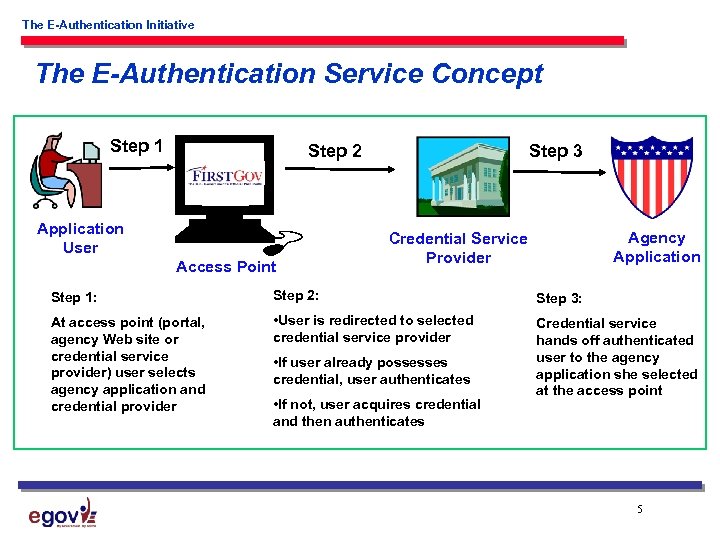 The E-Authentication Initiative The E-Authentication Service Concept Step 1 Step 2 Application User Access Point Step 3 Agency Application Credential Service Provider Step 1: Step 2: Step 3: At access point (portal, agency Web site or credential service provider) user selects agency application and credential provider • User is redirected to selected credential service provider Credential service hands off authenticated user to the agency application she selected at the access point • If user already possesses credential, user authenticates • If not, user acquires credential and then authenticates 5
The E-Authentication Initiative The E-Authentication Service Concept Step 1 Step 2 Application User Access Point Step 3 Agency Application Credential Service Provider Step 1: Step 2: Step 3: At access point (portal, agency Web site or credential service provider) user selects agency application and credential provider • User is redirected to selected credential service provider Credential service hands off authenticated user to the agency application she selected at the access point • If user already possesses credential, user authenticates • If not, user acquires credential and then authenticates 5
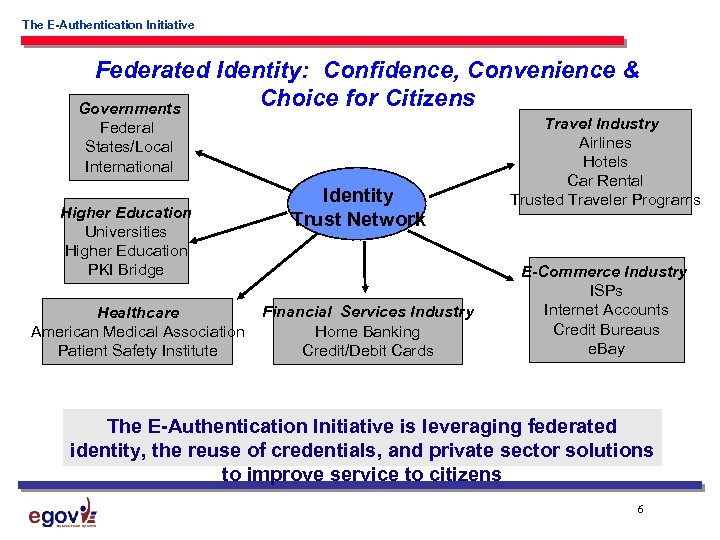 The E-Authentication Initiative Federated Identity: Confidence, Convenience & Choice for Citizens Governments Federal States/Local International Higher Education Universities Higher Education PKI Bridge Healthcare American Medical Association Patient Safety Institute Identity Trust Network Financial Services Industry Home Banking Credit/Debit Cards Travel Industry Airlines Hotels Car Rental Trusted Traveler Programs E-Commerce Industry ISPs Internet Accounts Credit Bureaus e. Bay The E-Authentication Initiative is leveraging federated identity, the reuse of credentials, and private sector solutions to improve service to citizens 6
The E-Authentication Initiative Federated Identity: Confidence, Convenience & Choice for Citizens Governments Federal States/Local International Higher Education Universities Higher Education PKI Bridge Healthcare American Medical Association Patient Safety Institute Identity Trust Network Financial Services Industry Home Banking Credit/Debit Cards Travel Industry Airlines Hotels Car Rental Trusted Traveler Programs E-Commerce Industry ISPs Internet Accounts Credit Bureaus e. Bay The E-Authentication Initiative is leveraging federated identity, the reuse of credentials, and private sector solutions to improve service to citizens 6
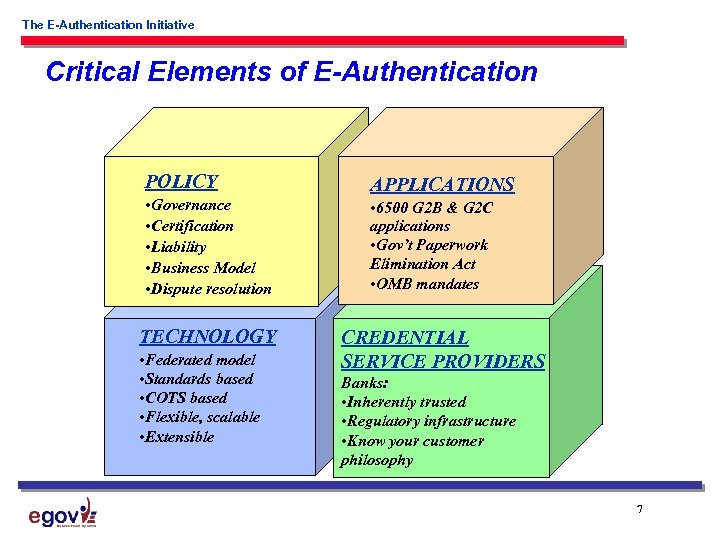 The E-Authentication Initiative Critical Elements of E-Authentication POLICY • Governance • Certification • Liability • Business Model • Dispute resolution TECHNOLOGY • Federated model • Standards based • COTS based • Flexible, scalable • Extensible APPLICATIONS • 6500 G 2 B & G 2 C applications • Gov’t Paperwork Elimination Act • OMB mandates CREDENTIAL SERVICE PROVIDERS Banks: • Inherently trusted • Regulatory infrastructure • Know your customer philosophy 7
The E-Authentication Initiative Critical Elements of E-Authentication POLICY • Governance • Certification • Liability • Business Model • Dispute resolution TECHNOLOGY • Federated model • Standards based • COTS based • Flexible, scalable • Extensible APPLICATIONS • 6500 G 2 B & G 2 C applications • Gov’t Paperwork Elimination Act • OMB mandates CREDENTIAL SERVICE PROVIDERS Banks: • Inherently trusted • Regulatory infrastructure • Know your customer philosophy 7
 The E-Authentication Initiative E-Authentication’s Architecture u Open Standards-based, federated identity management u Security Assertion Markup Language (SAML) 1. 0 in place now, SAML 2. 0 support planned, as soon as is practical u Liberty Alliance and WS-Federation support is also planned u Interoperability Lab in place to identify products, test products and credential services and track the evolution of the technology 8
The E-Authentication Initiative E-Authentication’s Architecture u Open Standards-based, federated identity management u Security Assertion Markup Language (SAML) 1. 0 in place now, SAML 2. 0 support planned, as soon as is practical u Liberty Alliance and WS-Federation support is also planned u Interoperability Lab in place to identify products, test products and credential services and track the evolution of the technology 8
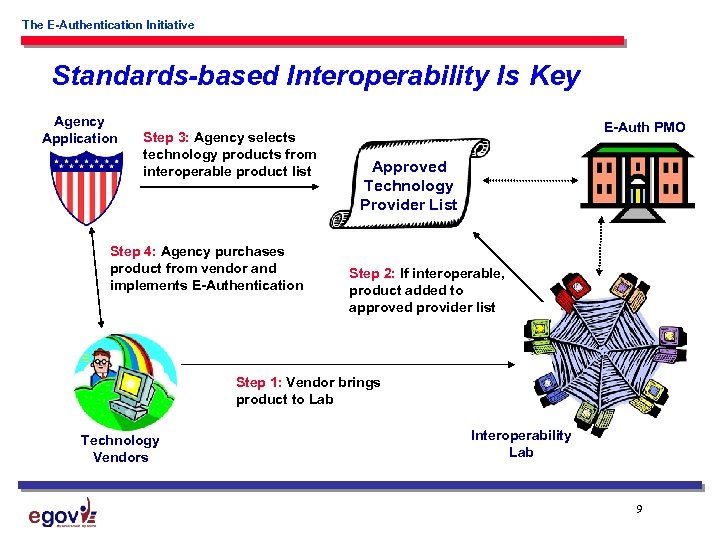 The E-Authentication Initiative Standards-based Interoperability Is Key Agency Application Step 3: Agency selects technology products from interoperable product list Step 4: Agency purchases product from vendor and implements E-Authentication E-Auth PMO Approved Technology Provider List Step 2: If interoperable, product added to approved provider list Step 1: Vendor brings product to Lab Technology Vendors Interoperability Lab 9
The E-Authentication Initiative Standards-based Interoperability Is Key Agency Application Step 3: Agency selects technology products from interoperable product list Step 4: Agency purchases product from vendor and implements E-Authentication E-Auth PMO Approved Technology Provider List Step 2: If interoperable, product added to approved provider list Step 1: Vendor brings product to Lab Technology Vendors Interoperability Lab 9
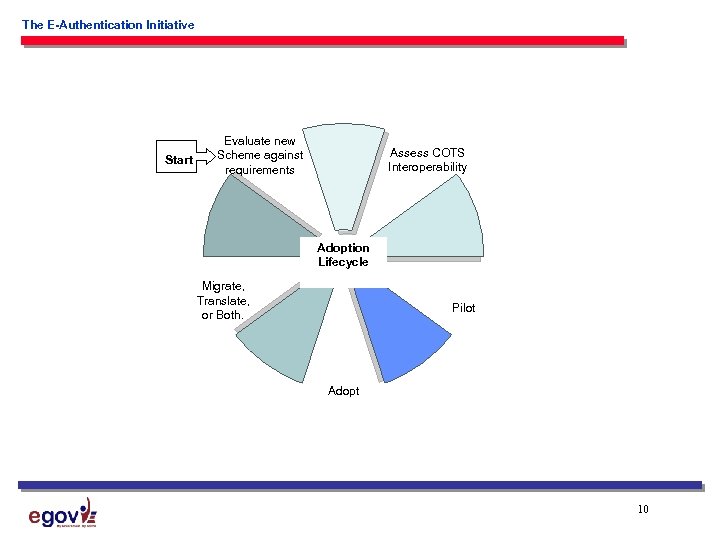 The E-Authentication Initiative Start Evaluate new Scheme against requirements Assess COTS Interoperability Adoption Lifecycle Migrate, Translate, or Both. Pilot Adopt 10
The E-Authentication Initiative Start Evaluate new Scheme against requirements Assess COTS Interoperability Adoption Lifecycle Migrate, Translate, or Both. Pilot Adopt 10
 The E-Authentication Initiative Accomplishments to Date u Published E-Authentication Architecture n n u Trusted Credential Service Providers (CSPs) n n u We have driven interoperability within SAML 1. 0 market List of seven approved, interoperable products 12 CSPs currently on the E-Authentication Federal Trust List Actively pursuing reuse of financial institution credentials Applications n n n Multiple pilots in progress Additional pilots ready to roll out More than 100 applications are near-term targets 11
The E-Authentication Initiative Accomplishments to Date u Published E-Authentication Architecture n n u Trusted Credential Service Providers (CSPs) n n u We have driven interoperability within SAML 1. 0 market List of seven approved, interoperable products 12 CSPs currently on the E-Authentication Federal Trust List Actively pursuing reuse of financial institution credentials Applications n n n Multiple pilots in progress Additional pilots ready to roll out More than 100 applications are near-term targets 11
 The E-Authentication Initiative What OASIS Can Do for E-Authentication u Continue to aid development of open standards, like SAML 2. 0 u Build/Implement standards testing lab or service – we built it for SAML 1. 0 because there wasn’t one we could use u Support our work in key areas: n n n Developing business rules Policy Business models Cultivating CSPs Driving standards 12
The E-Authentication Initiative What OASIS Can Do for E-Authentication u Continue to aid development of open standards, like SAML 2. 0 u Build/Implement standards testing lab or service – we built it for SAML 1. 0 because there wasn’t one we could use u Support our work in key areas: n n n Developing business rules Policy Business models Cultivating CSPs Driving standards 12
 The E-Authentication Initiative For More Information Phone E-mail Steve Timchak Program Manager 703 -872 -8604 stephen. timchak@gsa. gov Georgia Marsh Deputy Program Manager 703 -872 -8614 georgiak. marsh@gsa. gov Websites http: //cio. gov/eauthentication http: //www. eapartnership. org/ http: //cio. gov/fpkipa
The E-Authentication Initiative For More Information Phone E-mail Steve Timchak Program Manager 703 -872 -8604 stephen. timchak@gsa. gov Georgia Marsh Deputy Program Manager 703 -872 -8614 georgiak. marsh@gsa. gov Websites http: //cio. gov/eauthentication http: //www. eapartnership. org/ http: //cio. gov/fpkipa


