49c5841f21ac5f06237c7b15a7048306.ppt
- Количество слайдов: 14
 The E-Authentication Initiative An Overview Peter Alterman, Ph. D. Assistant CIO for e-Authentication, NIH and Chair, Federal PKI Policy Authority
The E-Authentication Initiative An Overview Peter Alterman, Ph. D. Assistant CIO for e-Authentication, NIH and Chair, Federal PKI Policy Authority
 The E-Authentication Initiative HSPD-12 E-Gov Program Management Office u Mandates all Federal Agencies issue ID credentials using FIPS-201 identity proofing procedures beginning 10/05 u Mandates all Federal Agencies begin issuing Smart. Cards with medium assurance digital certs by 10/06 u Authorization remains a local prerogative 2
The E-Authentication Initiative HSPD-12 E-Gov Program Management Office u Mandates all Federal Agencies issue ID credentials using FIPS-201 identity proofing procedures beginning 10/05 u Mandates all Federal Agencies begin issuing Smart. Cards with medium assurance digital certs by 10/06 u Authorization remains a local prerogative 2
 The E-Authentication Initiative Purpose and Function of the EAuthentication Program E-Gov Program Management Office u To provide a single source of identity authentication services for Federal Agency Applications u To develop and promulgate policies and procedures to sustain a common identity federation for the Federal Government in support of e-Gov and HSPD 12 u To partner with Credential Service Providers and other Identity Federations to enable the broadest access to e-Gov services. 3
The E-Authentication Initiative Purpose and Function of the EAuthentication Program E-Gov Program Management Office u To provide a single source of identity authentication services for Federal Agency Applications u To develop and promulgate policies and procedures to sustain a common identity federation for the Federal Government in support of e-Gov and HSPD 12 u To partner with Credential Service Providers and other Identity Federations to enable the broadest access to e-Gov services. 3
 The E-Authentication Initiative Summary of E-Authentication Approach u E-Gov Program Management Office Four Levels of Assurance of Identity (LOA) from Policy n n LOA 1 and 2 are assertion-based: Userid/password, SAML, Shibboleth, etc. LOA 3 and 4 are cryptographically-based: PKI, etc. u LOA required based on standard Risk Assessment u Agency Applications (AAs) autonomous for authorization decisions u AAs rely on credentials issued by external Credential Service Providers who submit to an assessment based on a Credential Assessment Framework u Principle of reusable credentials 4
The E-Authentication Initiative Summary of E-Authentication Approach u E-Gov Program Management Office Four Levels of Assurance of Identity (LOA) from Policy n n LOA 1 and 2 are assertion-based: Userid/password, SAML, Shibboleth, etc. LOA 3 and 4 are cryptographically-based: PKI, etc. u LOA required based on standard Risk Assessment u Agency Applications (AAs) autonomous for authorization decisions u AAs rely on credentials issued by external Credential Service Providers who submit to an assessment based on a Credential Assessment Framework u Principle of reusable credentials 4
 The E-Authentication Initiatives E-Gov Program Management Office u Assessment Framework for Credential evaluating the level of assurance (LOA) of identity of credential service providers u Membership in Liberty Alliance u Frequent meetings with Microsoft u Interfederation Interoperability Project with Cybertrust and Internet 2/Shibboleth team (more slides later on) u Credential Assessment Framework 5
The E-Authentication Initiatives E-Gov Program Management Office u Assessment Framework for Credential evaluating the level of assurance (LOA) of identity of credential service providers u Membership in Liberty Alliance u Frequent meetings with Microsoft u Interfederation Interoperability Project with Cybertrust and Internet 2/Shibboleth team (more slides later on) u Credential Assessment Framework 5
 The E-Authentication Initiative Credential Assessment Framework E-Gov Program Management Office u A structured methodology and procedures for evaluating the LOA of a CSPs credentials u An assessment team that goes out and evaluates CSPs u A process for conflict resolution u Posting CSPs and their credential LOAs to a trust list (unfortunate term) on the website 6
The E-Authentication Initiative Credential Assessment Framework E-Gov Program Management Office u A structured methodology and procedures for evaluating the LOA of a CSPs credentials u An assessment team that goes out and evaluates CSPs u A process for conflict resolution u Posting CSPs and their credential LOAs to a trust list (unfortunate term) on the website 6
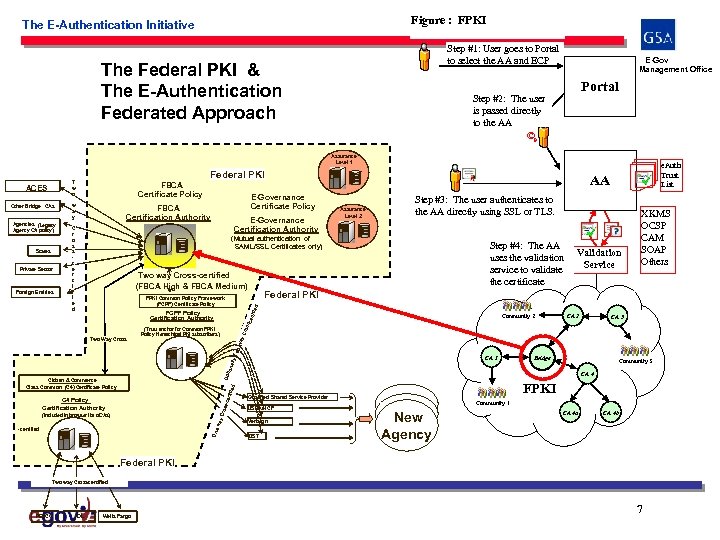 Figure : FPKI The E-Authentication Initiative Step #1: User goes to Portal to select the AA and ECP The Federal PKI & The E-Authentication Federated Approach E-Gov Program Management Office Portal Step #2: The user is passed directly to the AA ©p Assurance Level 1 Federal PKI T w o Foreign Entities E-Governance Certification Authority Step #3: The user authenticates to the AA directly using SSL or TLS. (Mutual authentication of SAML/SSL Certificates only) Two way Cross-certified (FBCA High & FBCA Medium) Validation Service Federal PKI FPKI Common Policy Framework (FCPF) Certificate Policy FCPF Policy Certification Authority (Trust anchor for Common FPKI Policy hierarchical PKI subscribers) Community 2 CA 3 Tw o. W Two Way Cross Step #4: The AA uses the validation service to validate the certificate XKMS OCSP CAM SOAP Others d Private Sector C r o s s c e r t i f i e d Assurance Level 2 tifie States FBCA Certification Authority AA ss -ce r Agencies (Legacy Agency CA policy) w a y E-Governance Certificate Policy Cro Other Bridge CAs FBCA Certificate Policy ay ACES e. Auth Trust List Op tion ally CA 1 ertif Cro ss -c C 4 Policy Certification Authority way (Included in browser list of. CAs) One -certified Community 3 CA 4 FPKI ied Citizen & Commerce Class Common (C 4) Certificate Policy Bridge Qualified Shared Service Provider USDA/NCF Verisign DST Community 1 New Agency CA 4 a CA 4 b Federal PKI Two way Cross -certified PEPCO AOL Wells Fargo 7
Figure : FPKI The E-Authentication Initiative Step #1: User goes to Portal to select the AA and ECP The Federal PKI & The E-Authentication Federated Approach E-Gov Program Management Office Portal Step #2: The user is passed directly to the AA ©p Assurance Level 1 Federal PKI T w o Foreign Entities E-Governance Certification Authority Step #3: The user authenticates to the AA directly using SSL or TLS. (Mutual authentication of SAML/SSL Certificates only) Two way Cross-certified (FBCA High & FBCA Medium) Validation Service Federal PKI FPKI Common Policy Framework (FCPF) Certificate Policy FCPF Policy Certification Authority (Trust anchor for Common FPKI Policy hierarchical PKI subscribers) Community 2 CA 3 Tw o. W Two Way Cross Step #4: The AA uses the validation service to validate the certificate XKMS OCSP CAM SOAP Others d Private Sector C r o s s c e r t i f i e d Assurance Level 2 tifie States FBCA Certification Authority AA ss -ce r Agencies (Legacy Agency CA policy) w a y E-Governance Certificate Policy Cro Other Bridge CAs FBCA Certificate Policy ay ACES e. Auth Trust List Op tion ally CA 1 ertif Cro ss -c C 4 Policy Certification Authority way (Included in browser list of. CAs) One -certified Community 3 CA 4 FPKI ied Citizen & Commerce Class Common (C 4) Certificate Policy Bridge Qualified Shared Service Provider USDA/NCF Verisign DST Community 1 New Agency CA 4 a CA 4 b Federal PKI Two way Cross -certified PEPCO AOL Wells Fargo 7
 The E-Authentication Initiative Interfederation Interoperability u Assertion-level trust transactions require federation-to -federation policy and technology interoperability initiatives n u E-Gov Program Management Office Under way with in. Common (Internet 2) Crypto-level trust transactions mediated by Federal Bridge n Under way with Higher Education Bridge, Pharmaceutical Industry Bridge, Aerospace Bridge 8
The E-Authentication Initiative Interfederation Interoperability u Assertion-level trust transactions require federation-to -federation policy and technology interoperability initiatives n u E-Gov Program Management Office Under way with in. Common (Internet 2) Crypto-level trust transactions mediated by Federal Bridge n Under way with Higher Education Bridge, Pharmaceutical Industry Bridge, Aerospace Bridge 8
 The E-Authentication Initiative What Happens When Two Federations Want to Interoperate? E-Gov Program Management Office u Enable technical interoperability between members of different federations u Develop mutually agreed-upon mappings for trusting identity credentials and elements of credentials u Develop mutually agreed-upon mappings for business rules u Develop peer-based conflict resolution mechanisms 9
The E-Authentication Initiative What Happens When Two Federations Want to Interoperate? E-Gov Program Management Office u Enable technical interoperability between members of different federations u Develop mutually agreed-upon mappings for trusting identity credentials and elements of credentials u Develop mutually agreed-upon mappings for business rules u Develop peer-based conflict resolution mechanisms 9
 The E-Authentication Initiative Report: Status of Interfederation Interoperability Work Group u in. Common Higher Education Identity Federation n n u E-Gov Program Management Office Using Shibboleth middleware technical protocols Policy-light E-Authentication US Identity Federation n n Using a variety of technical protocols Policy intensive 10
The E-Authentication Initiative Report: Status of Interfederation Interoperability Work Group u in. Common Higher Education Identity Federation n n u E-Gov Program Management Office Using Shibboleth middleware technical protocols Policy-light E-Authentication US Identity Federation n n Using a variety of technical protocols Policy intensive 10
 The E-Authentication Initiative Accomplishments to Date E-Gov Program Management Office u Demonstration of proof of concept for technical interoperability of identity credentials and utilities: E-Authentication SAML 1. 0 and Shibboleth 1. 2 u Production-level interoperability built into Shibboleth 1. 3 (in beta) u Extensive groundwork done on identifying policy and procedure mapping/treaty requirements u Credential Assessment of 4 Universities 11
The E-Authentication Initiative Accomplishments to Date E-Gov Program Management Office u Demonstration of proof of concept for technical interoperability of identity credentials and utilities: E-Authentication SAML 1. 0 and Shibboleth 1. 2 u Production-level interoperability built into Shibboleth 1. 3 (in beta) u Extensive groundwork done on identifying policy and procedure mapping/treaty requirements u Credential Assessment of 4 Universities 11
 The E-Authentication Initiative Work in Progress E-Gov Program Management Office u Development of common SAML 2. 0 schemes u Development of common USPerson profile and profile management infrastructure u Development of production-quality scheme translator u Ongoing work to enable cross-federation trust and interoperability u NSF Fast. Lane to accept 4 universities’ Shibboleth-based identity and attribute credentials 12
The E-Authentication Initiative Work in Progress E-Gov Program Management Office u Development of common SAML 2. 0 schemes u Development of common USPerson profile and profile management infrastructure u Development of production-quality scheme translator u Ongoing work to enable cross-federation trust and interoperability u NSF Fast. Lane to accept 4 universities’ Shibboleth-based identity and attribute credentials 12
 The E-Authentication Initiative Unresolved Issues E-Gov Program Management Office u Mapping null attributes u Ensuring privacy of attribute information in a variety of instances u Portal integration u Scaling issues for listing credential providers u Issues of transitivity across federations u Multiple authoritative sources/conflicting authoritative sources u Vocabulary and “data dictionary” issues u Liability and indemnification issues 13
The E-Authentication Initiative Unresolved Issues E-Gov Program Management Office u Mapping null attributes u Ensuring privacy of attribute information in a variety of instances u Portal integration u Scaling issues for listing credential providers u Issues of transitivity across federations u Multiple authoritative sources/conflicting authoritative sources u Vocabulary and “data dictionary” issues u Liability and indemnification issues 13
 The E-Authentication Initiative More Information u peter. alterman@nih. gov u http: //csrc. nist. gov u http: //www. cio. gov/fbca u http: //www. cio. gov/eauthentication u E-Gov Program Management Office http: //www. cio. gov/fpkipa 14
The E-Authentication Initiative More Information u peter. alterman@nih. gov u http: //csrc. nist. gov u http: //www. cio. gov/fbca u http: //www. cio. gov/eauthentication u E-Gov Program Management Office http: //www. cio. gov/fpkipa 14


